Robust Consensus of Networked Evolutionary Games with Attackers and Forbidden Profiles † †
Abstract
:1. Introduction
2. Problem Formulation
- Network graph , where N denotes the set of vertices (players), and E denotes the set of edges. Let with , , where is the set of ordinary players, is the set of pseudo players who can control the evolutionary game, and is the set of attackers (In an NEG, attackers are selfish nodes in the network graph who use the network but do not cooperate. Attacker is different from stochastic player in NEGs with “Fermi rule", where stochastic player is also an ordinary player who may cooperate.) who may destroy the evolutionary game. Set , and .
- Fundamental networked game, G, such that if , then i and j play the FNG repetitively with the strategy set S. Without loss of generality, for , we let . Denote the strategies of each player in , and at time t by , and , respectively, where , and .
- Strategy updating rule, . Denote the -th step neighborhood of each player by . When , we briefly denote by the one step neighborhood of . At each time instance, each player plays the FNG with its neighbors in , and its average payoff, denoted by , has the following form:where denotes the payoff of playing with its neighbor . Throughout this paper, the strategy updating rule is described by the following fundamental evolutionary equation:where is determined by the following SUR (Unconditional Imitation with Fixed Priority): is selected as the best strategy from strategies of its neighbors in at time t. Precisely, if , then . When the neighbors with maximum payoff are not unique, say, , we choose .
- (i)
- holds for , and ;
- (ii)
- holds for , and .
3. Main Results
- (i)
- is said to be one step robustly reachable from , if there exists a control such that holds for any .
- (ii)
- A nonempty set is said to be one step robustly reachable from , if there exist a control and (depending on ξ) such that holds for any .
- (i)
- is one step robustly reachable from , if and only if there exists a positive integer such that
- (ii)
- A nonempty set is one step robustly reachable from , if and only if there exists a positive integer such that
- (i)
- When , there exists such that
- (ii)
- When , there exists such that
- (1)
- Calculate , .
- (2)
- For any which corresponds to a unique integer such that , let be such that
- (3)
- A state feedback gain matrix under which the NEG with attackers and forbidden profiles achieves consensus at η can be designed as , where
- (i)
- is one step robustly reachable from itself in one step.
- (ii)
- There exists a positive integer such that is robustly reachable from any at the -th step.
4. An Illustrative Example
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Smith, J.M.; Price, G.R. The logic of animal conflict. Nature 1973, 246, 15–18. [Google Scholar] [CrossRef]
- Alexander, J.M. Random Boolean networks and evolutionary game theory. Philos. Sci. 2003, 70, 1289–1304. [Google Scholar] [CrossRef]
- Brown, J.S.; Vincent, T.L. A theory for the evolutionary game. Theor. Popul. Biol. 1987, 31, 140–166. [Google Scholar] [CrossRef]
- Nowark, M.A.; May, R.M. Evolutionary games and spatial chaos. Nature 1992, 359, 826–829. [Google Scholar] [CrossRef]
- Hauert, C.; Doebeli, M. Spatial structure often inhibits the evolution of cooperation in the snowdrift game. Nature 2004, 428, 643–646. [Google Scholar] [CrossRef] [PubMed]
- Li, Y.; Zhang, J.; Perc, M. Effects of compassion on the evolution of cooperation in spatial social dilemmas. Appl. Math. Comput. 2018, 320, 437–443. [Google Scholar] [CrossRef]
- Perc, M.; Jordan, J.; Rand, D.; Wang, Z.; Boccaletti, S. Statistical physics of human cooperation. Phys. Rep. 2017, 687, 1–51. [Google Scholar] [CrossRef]
- Santos, F.C.; Santos, M.D.; Pacheco, J.M. Social diversity promotes the emergence of cooperation in public goods games. Nature 2008, 454, 213–216. [Google Scholar] [CrossRef] [PubMed]
- Tembine, H.; Altman, E.; Azouzi, R.E.; Hayel, Y. Evolutionary game in wireless networks. IEEE Trans. Syst. Man Cybern. 2010, 40, 634–646. [Google Scholar] [CrossRef] [PubMed]
- Szolnoki, A.; Perc, M.; Danku, Z. Making new connections towards cooperation in the prisoner’s dilemma game. J. Funct. Anal. 2010, 21, 88–121. [Google Scholar]
- Perc, M.; Szolnoki, A.; Szabo, G. Restricted connections among distinguished players support cooperation. Phys. Rev. E 2008, 78, 066101. [Google Scholar] [CrossRef] [PubMed]
- Wang, Z.; Wang, L.; Szolnoki, A.; Perc, M. Evolutionary games on multilayer networks: A colloquium. Eur. Phys. J. B 2015, 88, 124. [Google Scholar] [CrossRef]
- Perc, M.; Szolnoki, A. Coevolutionary games—A mini review. Biosyst. 2010, 99, 109–125. [Google Scholar] [CrossRef] [PubMed]
- Cheng, D.; He, F.; Qi, H.; Xu, T. Modeling, analysis and control of networked evolutionary games. IEEE Trans. Autom. Control 2015, 60, 2402–2415. [Google Scholar] [CrossRef]
- Boyer, K.K.; Mcdermott, C. Strategic consensus in operations strategy. J. Oper. Manag. 1999, 17, 289–305. [Google Scholar] [CrossRef]
- Perc, M. Evolution of cooperation on scale-free networks subject to error and attack. New J. Phys. 2009, 11, 033027. [Google Scholar] [CrossRef]
- Sun, W.; Kong, X.; He, D.; You, X. Research on attack and deference in information security based on evolutionary game. Inf. Sci. 2008, 26, 1408–1412. [Google Scholar]
- Chassang, S.; Takahashi, S. Robustness to incomplete information in repeated games. Theor. Econ. 2011, 6, 49–93. [Google Scholar] [CrossRef]
- Shen, S.; Li, Y.; Xu, H.; Cao, Q. Signaling game based strategy of intrusion detection in wireless sensor networks. Comput. Math. Appl. 2011, 62, 2404–2416. [Google Scholar] [CrossRef]
- Agah, A.; Das, S. Preventing DoS attacks in wireless sensor networks: a repeated game theory approach. Int. J. Netw. Secur. 2007, 5, 145–153. [Google Scholar]
- Zhang, X.; Hao, Y.; Cheng, D. Incomplete-profile potential games. J. Frankl. Inst. 2017, in press. [Google Scholar] [CrossRef]
- Cheng, D.; Qi, H.; Li, Z. Analysis and Control of Boolean Networks: A Semi-Tensor Product Approach; Springer: London, UK, 2011. [Google Scholar]
- Cheng, D.; Qi, H.; Zhao, Y. An Introduction to Semi-Tensor Product of Matrices and Its Applications; World Scientific: Singapore, 2012. [Google Scholar]
- Li, H.; Zhao, G.; Meng, M.; Feng, J. A survey on applications of semi-tensor product method in engineering. Sci. China Inf. Sci. 2017, 61, 010202. [Google Scholar] [CrossRef]
- Lu, J.; Li, H.; Liu, Y.; Li, F. Survey on semi-tensor product method with its applications in logical networks and other finite-valued systems. IET Control Theory Appl. 2017, 11, 2040–2047. [Google Scholar] [CrossRef]
- Lu, J.; Zhong, J.; Huang, C.; Cao, J. On pinning controllability of Boolean control networks. IEEE Trans. Autom. Control 2016, 61, 1658–1663. [Google Scholar] [CrossRef]
- Chen, H.; Sun, J. Stability and stabilisation of context-sensitive probabilistic Boolean networks. IET Control Theory Appl. 2014, 8, 2115–2121. [Google Scholar] [CrossRef]
- Fornasini, E.; Valcher, M.E. Observability, reconstructibility and state observers of Boolean control networks. IEEE Trans. Autom. Control 2013, 58, 1390–1401. [Google Scholar] [CrossRef]
- Guo, Y.; Wang, P.; Gui, W.; Yang, C. Set stability and set stabilization of Boolean control networks based on invariant subsets. Automatica 2015, 61, 106–112. [Google Scholar] [CrossRef]
- Laschov, D.; Margaliot, M. A maximum principle for single-input Boolean control networks. IEEE Trans. Autom. Control 2011, 56, 913–917. [Google Scholar] [CrossRef]
- Li, F.; Tang, Y. Set stabilization for switched Boolean control networks. Automatica 2017, 78, 223–230. [Google Scholar] [CrossRef]
- Li, H.; Wang, Y.; Xie, L. Output tracking control of Boolean control networks via state feedback: Constant reference signal case. Automatica 2015, 59, 54–59. [Google Scholar] [CrossRef]
- Li, H.; Xie, L.; Wang, Y. On robust control invariance of Boolean control networks. Automatica 2016, 68, 392–396. [Google Scholar] [CrossRef]
- Li, H.; Song, P.; Yang, Q. Pinning control design for robust output tracking of k-valued logical networks. J. Frankl. Inst. 2017, 354, 3039–3053. [Google Scholar] [CrossRef]
- Liu, Y.; Chen, H.; Wu, B. Controllability of Boolean control networks with impulsive effects and forbidden states. Mathe. Methods Appl. Sci. 2014, 37, 1–9. [Google Scholar] [CrossRef]
- Meng, M.; Feng, J. Topological structure and the disturbance decoupling problem of singular Boolean networks. IET Control Theory Appl. 2014, 8, 1247–1255. [Google Scholar] [CrossRef]
- Xu, X.; Hong, Y. Matrix approach to model matching of asynchronous sequential machines. IEEE Trans. Autom. Control 2013, 58, 2974–2979. [Google Scholar] [CrossRef]
- Yang, M.; Li, R.; Chu, T. Controller design for disturbance decoupling of Boolean control networks. Automatica 2013, 49, 273–277. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, K. Controllability and observability of Boolean control networks with time-variant delays in states. IEEE Trans. Neural Netw. Learn. Syst. 2013, 24, 1478–1484. [Google Scholar] [CrossRef] [PubMed]
- Zhao, Y.; Cheng, D. On controllability and stabilizability of probabilistic Boolean control networks. Sci. China Inf. Sci. 2014, 57, 012202. [Google Scholar] [CrossRef]
- Zhong, J.; Lu, J.; Liu, Y.; Cao, J. Synchronization in an array of output-coupled Boolean networks with time delay. IEEE Trans. Neural Netw. Learn. Syst. 2014, 25, 2288–2294. [Google Scholar] [CrossRef] [PubMed]
- Zou, Y.; Zhu, J. Kalman decomposition for Boolean control networks. Automatica 2015, 54, 65–71. [Google Scholar] [CrossRef]
- Cheng, D. On finite potential games. Automatica 2014, 50, 1793–1801. [Google Scholar] [CrossRef]
- Guo, P.; Wang, Y.; Li, H. Algebraic formulation and strategy optimization for a class of evolutionary network games via semi-tensor product method. Automatica 2013, 49, 3384–3389. [Google Scholar] [CrossRef]
- Liu, X.; Zhu, J. On potential equations of finite games. Automatica 2015, 68, 245–253. [Google Scholar] [CrossRef]
- Zhu, B.; Xia, X.; Wu, Z. Evolutionary game theoretic demand-side management and control for a class of networked smart grid. Automatica 2016, 70, 94–100. [Google Scholar] [CrossRef]
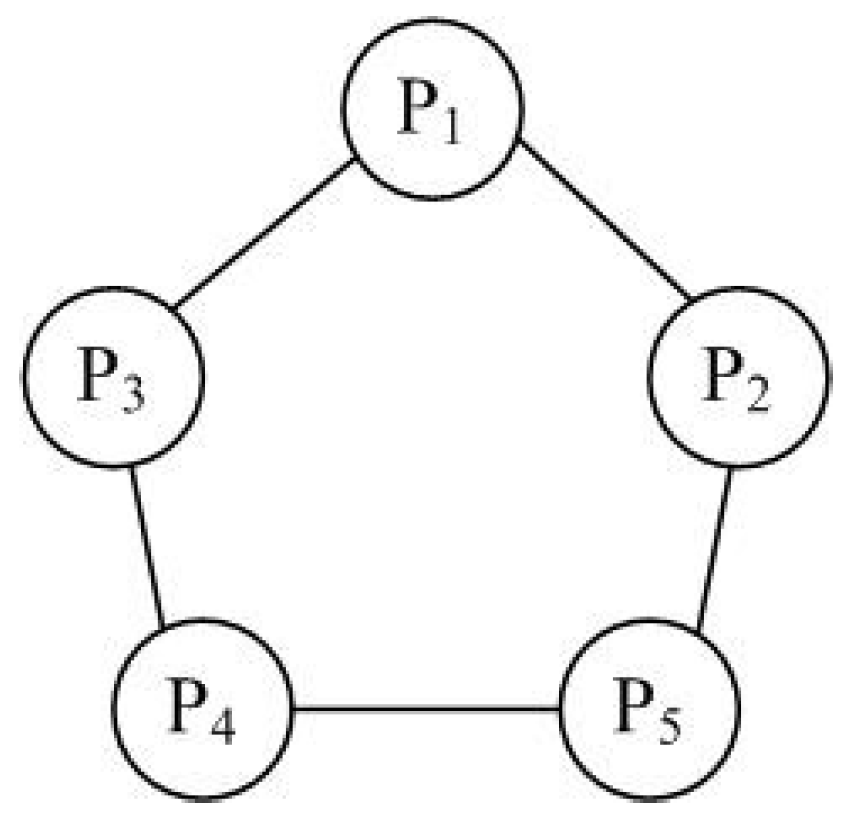
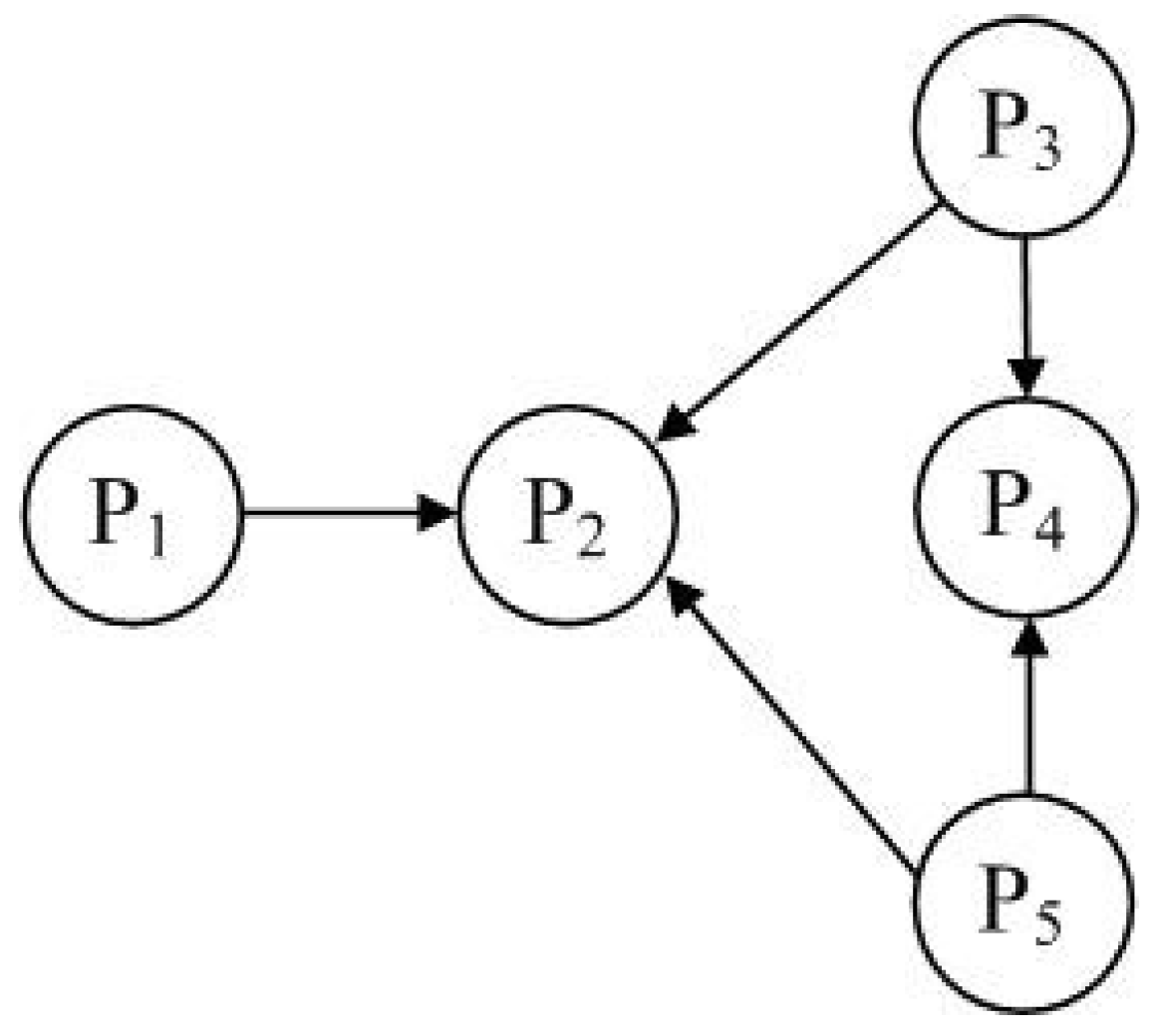
| \ | 1 | 2 |
|---|---|---|
| 1 | (3, 3) | (2, 4) |
| 2 | (4, 2) | (0, 0) |
| Profile | 11111 | 111112 | 11121 | 11122 | 11211 | 11212 | 11221 | 11222 |
| 6 | 5 | 5 | 4 | 8 | 4 | 4 | 0 | |
| 6 | 6 | 8 | 8 | 5 | 5 | 4 | 4 | |
| 6 | 8 | 6 | 8 | 5 | 4 | 5 | 4 | |
| 6 | 5 | 6 | 5 | 6 | 5 | 6 | 5 | |
| 6 | 6 | 5 | 5 | 6 | 5 | 5 | 5 | |
| 1 | 2 | 2 | 2 | 2 | 1 | 1 | 2 | |
| 1 | 1 | 2 | 2 | 2 | 1 | 1 | 1 | |
| 1 | 2 | 1 | 2 | 2 | 1 | 1 | 1 | |
| Profile | 12111 | 12112 | 12121 | 12122 | 12211 | 12212 | 12221 | 12222 |
| 6 | 5 | 5 | 4 | 8 | 4 | 4 | 0 | |
| 6 | 6 | 8 | 8 | 5 | 5 | 4 | 4 | |
| 5 | 4 | 5 | 4 | 4 | 0 | 4 | 0 | |
| 8 | 4 | 8 | 4 | 8 | 4 | 8 | 4 | |
| 5 | 5 | 4 | 4 | 4 | 5 | 4 | 4 | |
| 1 | 1 | 2 | 2 | 2 | 1 | 2 | 2 | |
| 1 | 1 | 2 | 2 | 2 | 1 | 2 | 2 | |
| 2 | 1 | 2 | 2 | 2 | 2 | 2 | 1 | |
| Profile | 21111 | 21112 | 21121 | 21122 | 21211 | 21212 | 21221 | 21222 |
| 6 | 5 | 5 | 4 | 8 | 4 | 4 | 0 | |
| 5 | 5 | 4 | 4 | 4 | 4 | 0 | 0 | |
| 6 | 8 | 6 | 8 | 5 | 4 | 5 | 4 | |
| 5 | 4 | 5 | 4 | 5 | 4 | 5 | 4 | |
| 8 | 8 | 4 | 4 | 8 | 8 | 4 | 4 | |
| 1 | 2 | 1 | 2 | 2 | 2 | 1 | 2 | |
| 2 | 2 | 1 | 2 | 2 | 2 | 2 | 2 | |
| 1 | 2 | 1 | 2 | 2 | 2 | 1 | 2 | |
| Profile | 22111 | 22112 | 22121 | 22122 | 22211 | 22212 | 22221 | 22222 |
| 6 | 5 | 5 | 4 | 8 | 4 | 4 | 0 | |
| 5 | 5 | 4 | 4 | 4 | 4 | 4 | 0 | |
| 5 | 4 | 5 | 4 | 4 | 0 | 4 | 0 | |
| 4 | 0 | 4 | 0 | 4 | 0 | 4 | 0 | |
| 4 | 4 | 0 | 0 | 4 | 4 | 0 | 0 | |
| 1 | 1 | 1 | 1 | 2 | 2 | 2 | 2 | |
| 1 | 1 | 1 | 2 | 2 | 1 | 2 | 2 | |
| 1 | 1 | 1 | 2 | 2 | 2 | 1 | 2 |
| \ | 1 | 2 |
|---|---|---|
| 1 | (1, 5) | (−1, 9) |
| 2 | (4, 4) | (0, 0) |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Y.; Ding, X.; Li, H. Robust Consensus of Networked Evolutionary Games with Attackers and Forbidden Profiles †. Entropy 2018, 20, 15. https://doi.org/10.3390/e20010015
Li Y, Ding X, Li H. Robust Consensus of Networked Evolutionary Games with Attackers and Forbidden Profiles †. Entropy. 2018; 20(1):15. https://doi.org/10.3390/e20010015
Chicago/Turabian StyleLi, Yalu, Xueying Ding, and Haitao Li. 2018. "Robust Consensus of Networked Evolutionary Games with Attackers and Forbidden Profiles †" Entropy 20, no. 1: 15. https://doi.org/10.3390/e20010015
APA StyleLi, Y., Ding, X., & Li, H. (2018). Robust Consensus of Networked Evolutionary Games with Attackers and Forbidden Profiles †. Entropy, 20(1), 15. https://doi.org/10.3390/e20010015






