On the Detection of Fake Certificates via Attribute Correlation
Abstract
:1. Introduction
- We have designed SSLight, a novel attribute dependency-based detection mechanism, to enhance SSL/TLS’s authentication. SSLight is capable of exposing fake certificates issued from trusted, but compromised, CAs.
- SSLight is built on a training set with 830,306 legitimate certificate samples. We have conducted extensive experiments to evaluate SSLight’s detection capability. The experimental results show that SSLight can detect the vast majority of fake certificates issued from any compromised CA with a relatively low false positive rate.
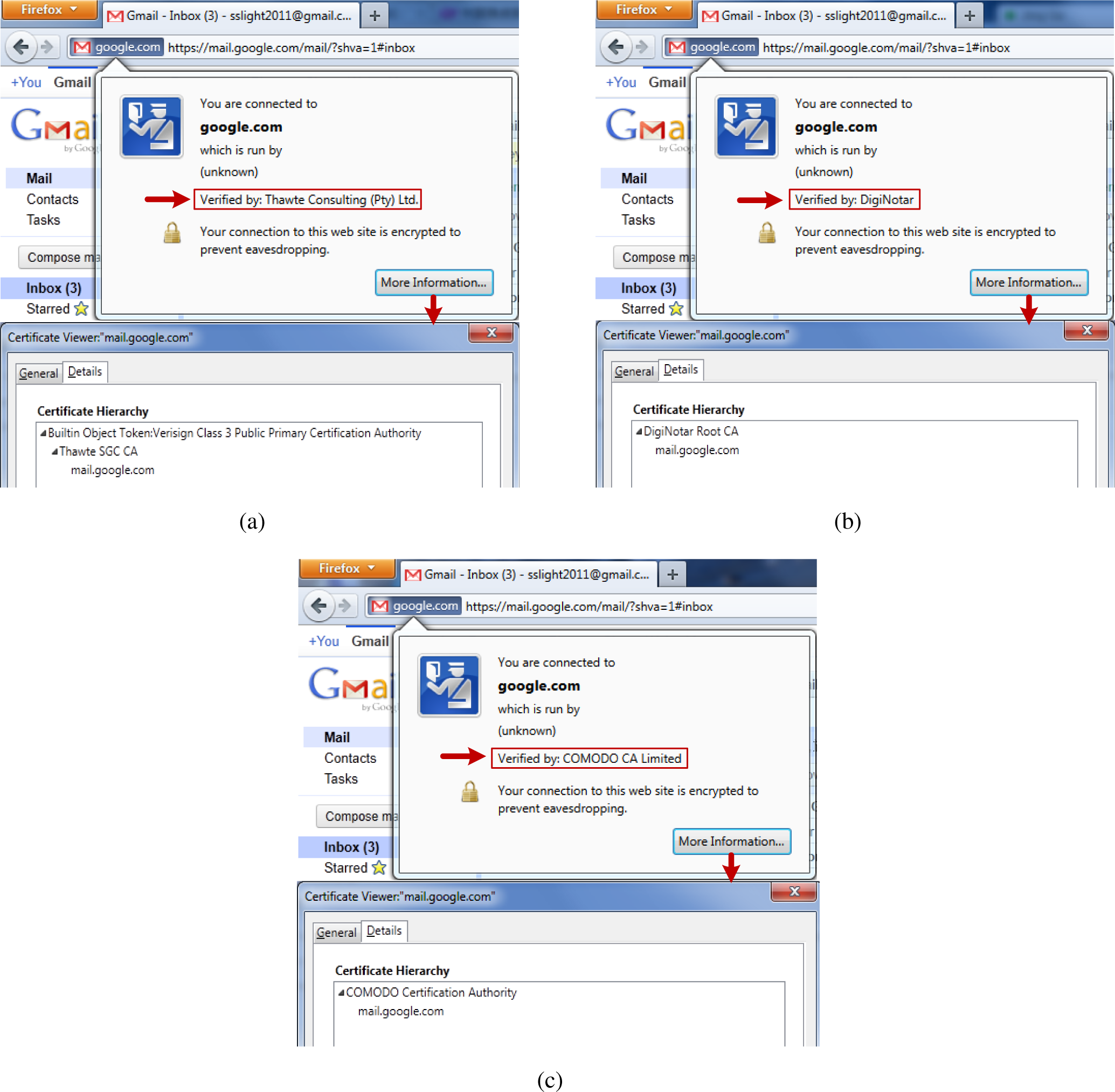
- We have implemented SSLight as a Firefox add-on and use it to detect real-world fake certificates from DigiNotar and Comodo, both of which have made a catastrophic impact around the world. SSLight achieves a relatively high detection rate on these real-world examples.
2. Background
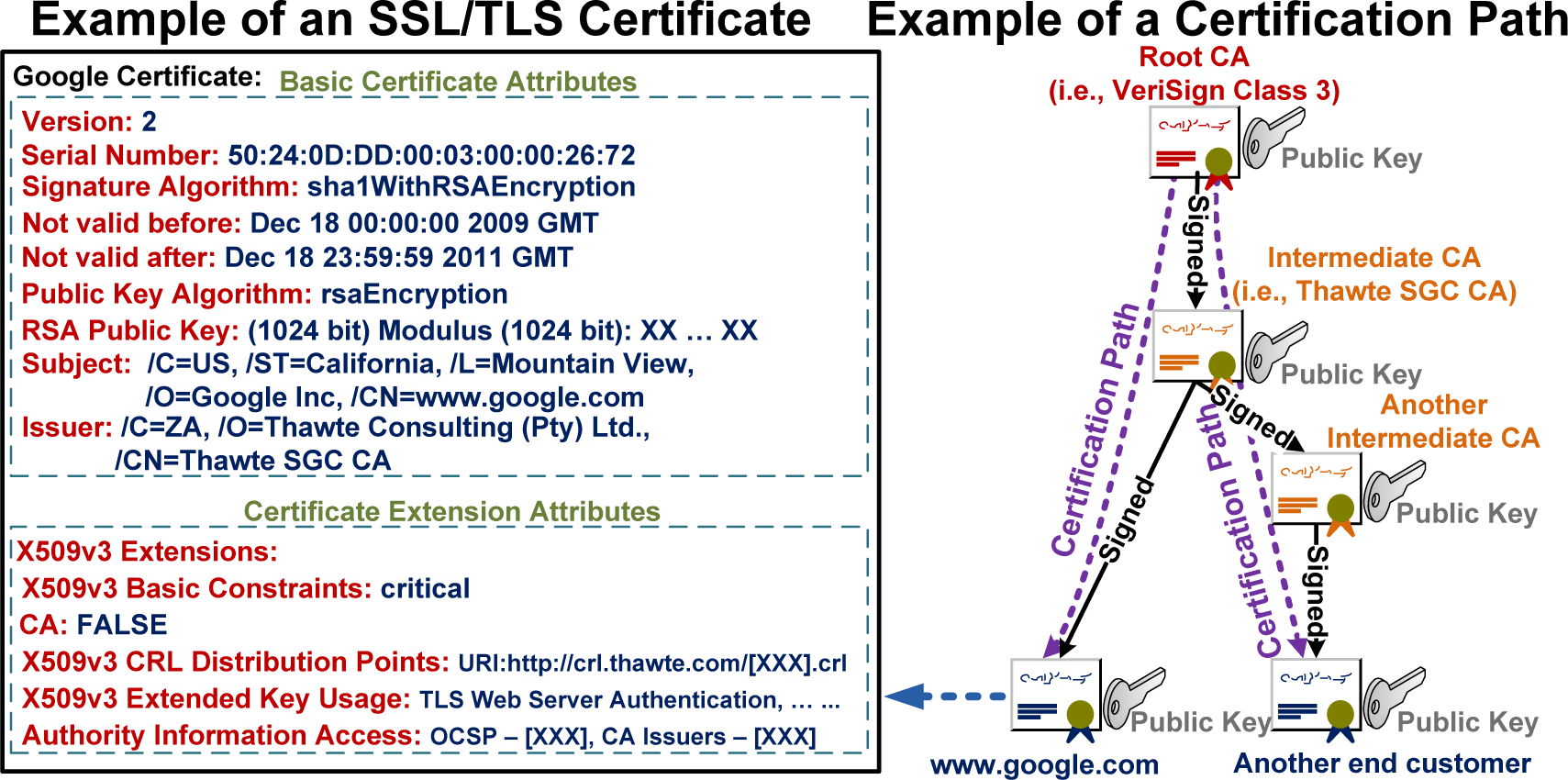
2.1. Attributes in X.509 Certificates
2.2. Attribute Dependency
3. Threat Model
- cannot do any modification in the trusted CA certificates;
- can duplicate attributes from legitimate certificates to the corresponding fake ones;
- can issue any number of intermediate CAs with arbitrary attributes using the trusted, but compromised, CA;
- can hijack or block any connections to and from the browsers.
4. SSLight
4.1. Probabilistic Model
4.2. SSLight Design
4.2.1. Detection Algorithm
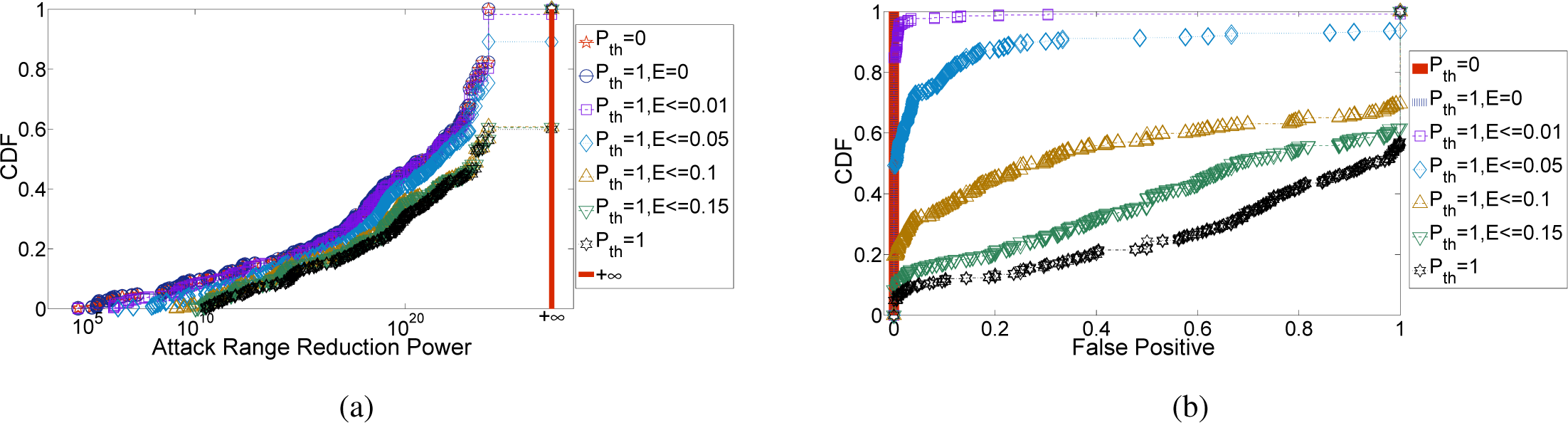
4.2.2. Attack Range Reduction
| Input: and |
| 1: ; |
| 2: for all Jx, Jy, in do |
| 3: if then |
| 4: ; |
| 5: end if |
| 6: end for |
| 7: if then |
| 8: return is a fake certificate issued by ; |
| 9: else |
| 10: return is a legitimate one issued by ; |
| 11: end if |
4.2.3. False Positive
4.3. Theoretical Analysis
5. Evaluation
5.1. Experiment Setup
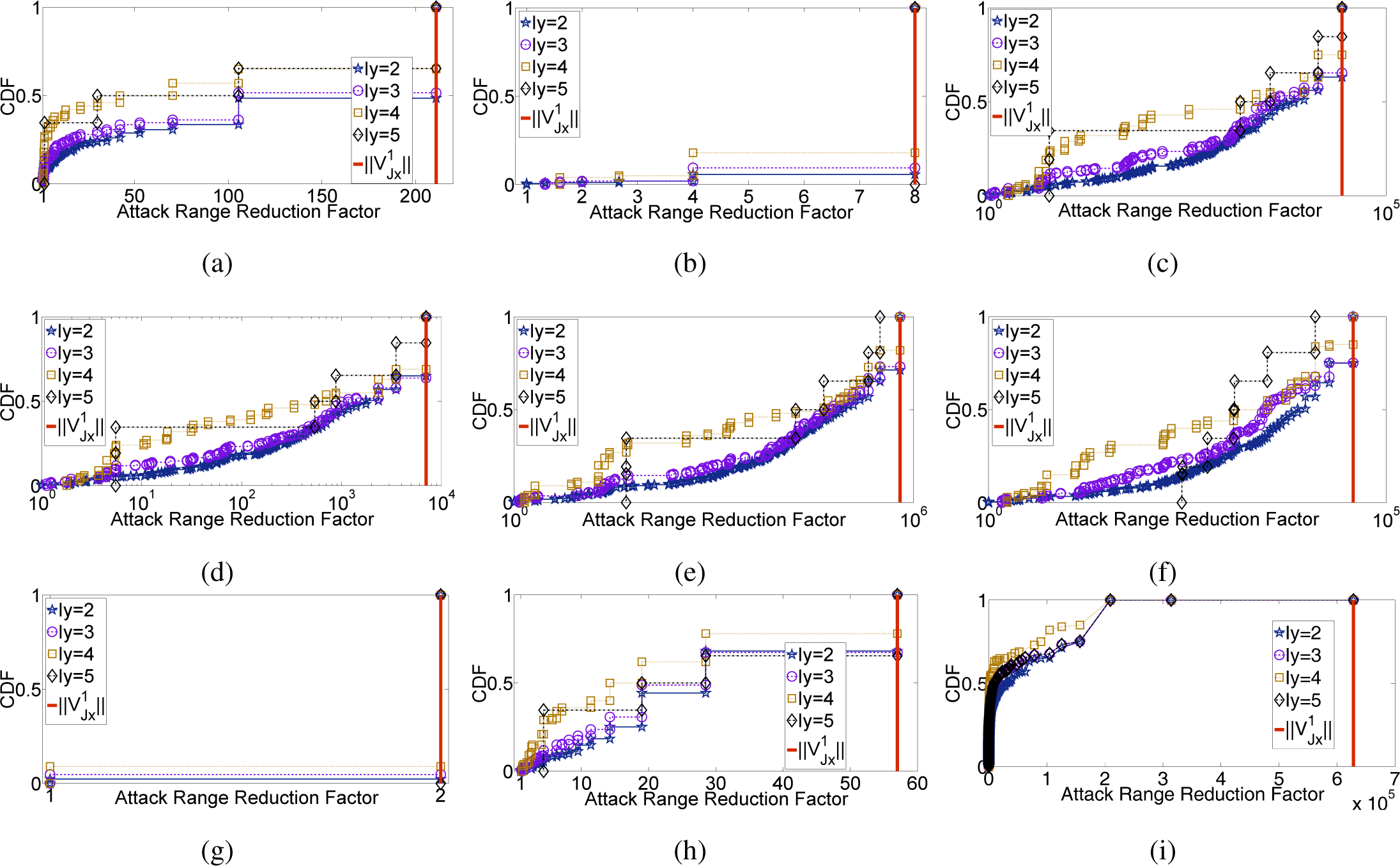
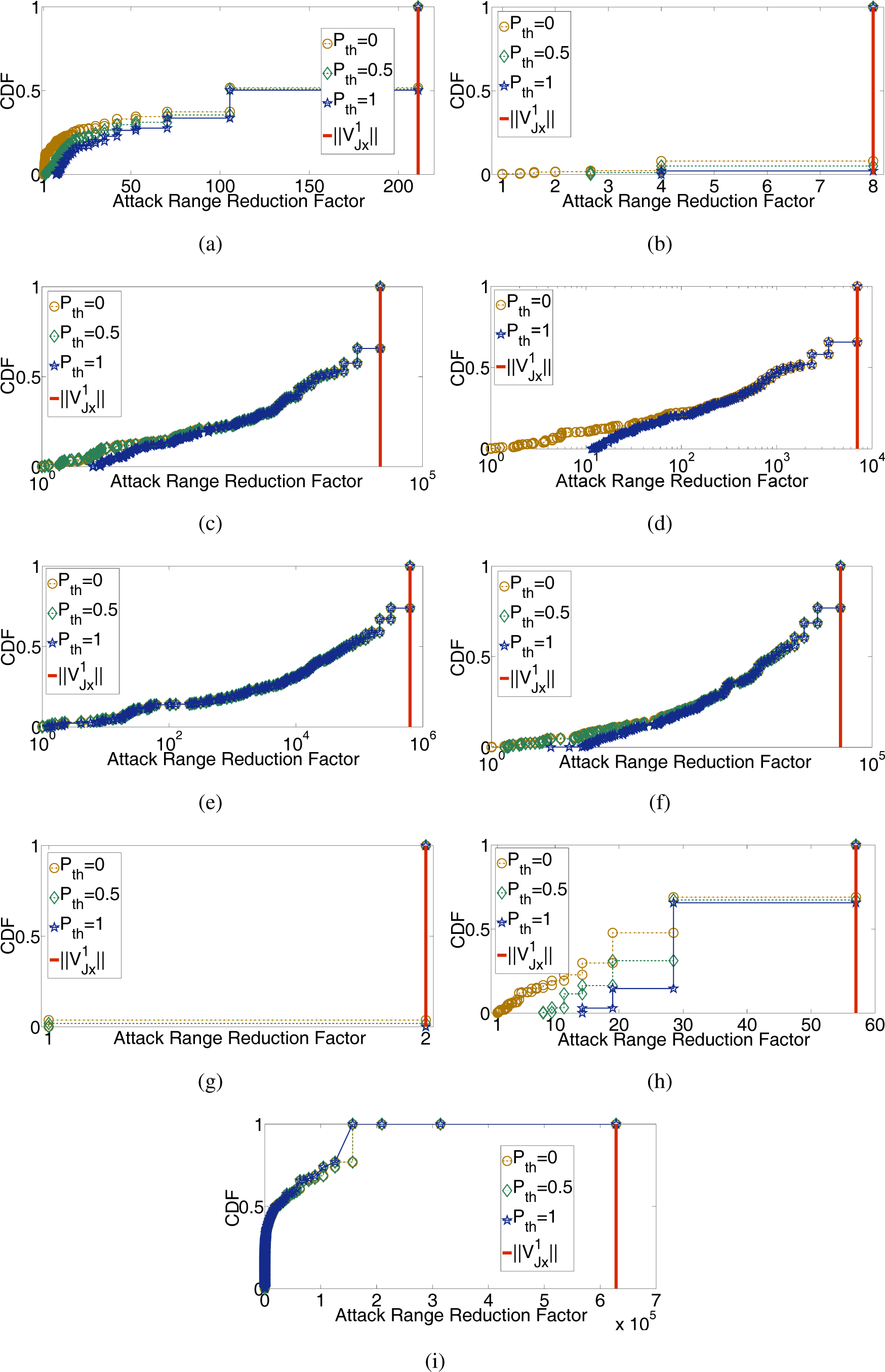
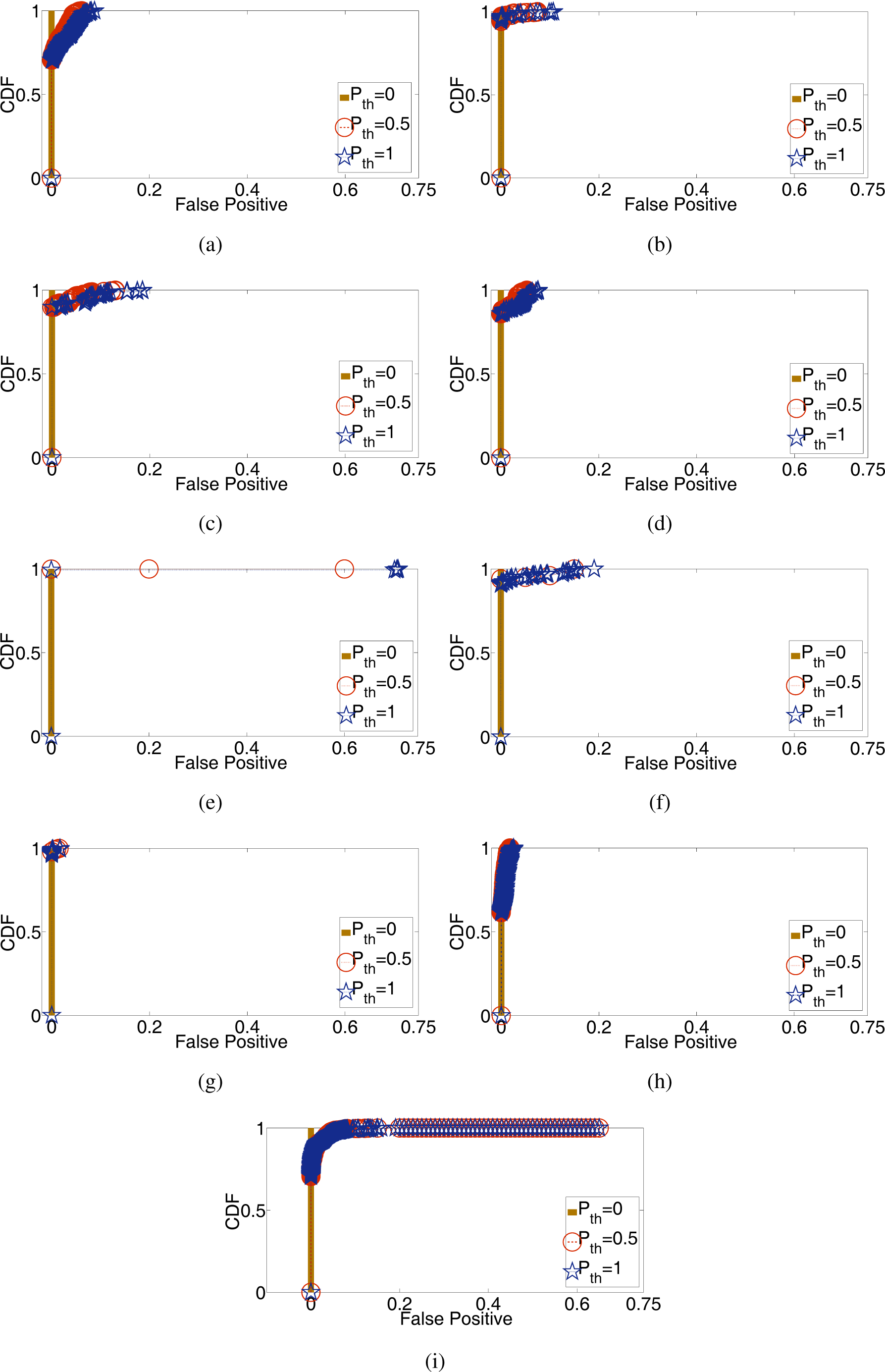
5.2. Feature Evaluation
5.3. SSLight Evaluation
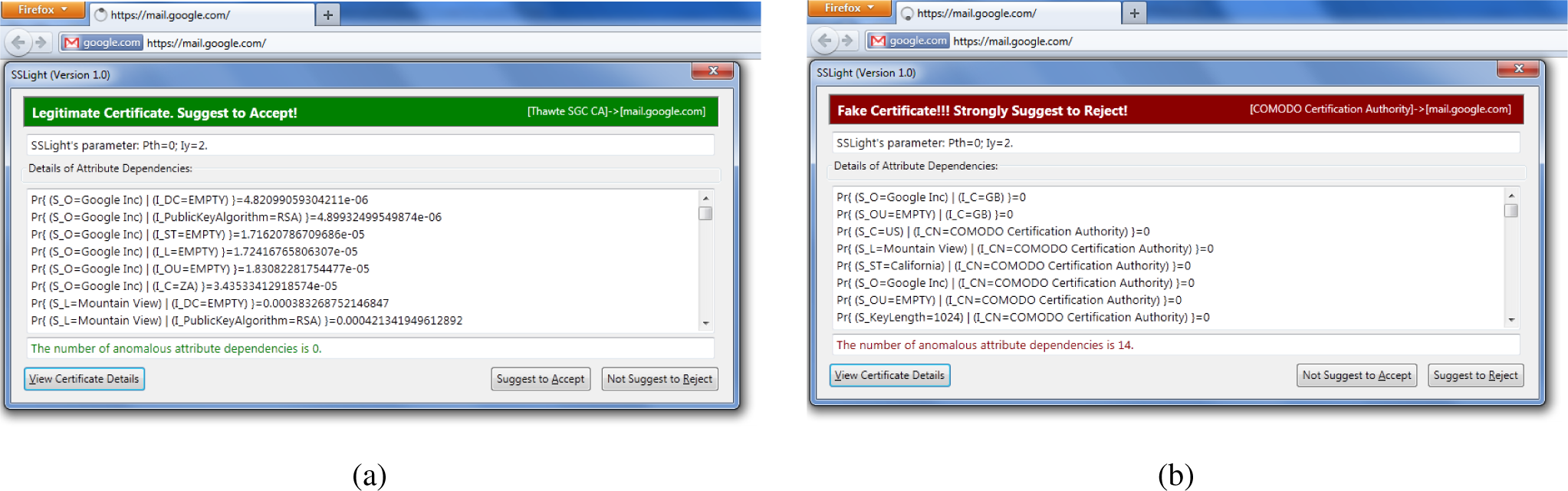
5.4. Firefox Add-On and Real-World Examples
6. Discussion
7. Related Work
8. Conclusions
Acknowledgments
A. Appendix
1.1. The Proof of Proposition 2
1.2. The Proof of Corollary 1
1.3. The Proof of Corollary 2
1.4. The Proof of Corollary 3
1.5. The Proof of Corollary 4
1.6. The Proof of Corollary 5
1.7. The Proof of Corollary 6
1.8. An Example of Excluded Attribute Dependencies
| Iy | E | |||
|---|---|---|---|---|
| CommonName | 2 | UTN-USERFirst-Hardware | Locality | 0.154 |
| Locality | 2 | Salt Lake City | Locality | 0.185 |
| Organization | 2 | The USERTRUSTNetwork | Locality | 0.185 |
| OrganizationUnit | 2 | http://www.usertrust.com | Locality | 0.153 |
| StateOrProvince | 2 | UT | Locality | 0.185 |
| Description | 2 | EMPTY | Organization | 0.707 |
| PublicKeyAlgorithm | 2 | RSA | Organization | 0.702 |
| Country | 2 | ZA | OrganizationUnit | 0.159 |
| Thawte Premium Server | ||||
| CommonName | 2 | OrganizationUnit | 0.191 | |
| CA/emailAddress | ||||
| CommonName | 2 | DigiCert High Assurance CA-3 | OrganizationUnit | 0.151 |
| CommonName | 3 | DigiCert High Assurance EV Root CA | OrganizationUnit | 0.151 |
| Organization | 3 | DigiCert Inc | OrganizationUnit | 0.151 |
| OrganizationUnit | 3 | www.digicert.com | OrganizationUnit | 0.151 |
| Description | 3 | EMPTY | Organization | 0.709 |
| PublicKeyAlgorithm | 3 | RSA | Organization | 0.709 |
| Country | 3 | SE | Locality | 0.175 |
| CommonName | 3 | AddTrust External CA Root | Locality | 0.175 |
| Organization | 3 | AddTrust AB | Locality | 0.175 |
| OrganizationUnit | 3 | AddTrust External TTPNetwork | Locality | 0.175 |
1.9. The Proof of Proposition 3
1.10. The Proof of Corollary 7
1.11. The Proof of Corollary 8
1.12. The Proof of Corollary 9
Author Contributions
Conflicts of Interest
References
- Vatra, N. Public key infrastructure overview. Sci. Stud. Res. Ser. Math. Inform. 2009, 19, 471–478. [Google Scholar]
- Solo, D.; Housley, R.; Ford, W. Internet X. 509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile; The Internet Society: Reston, VA, USA, 2002. [Google Scholar]
- Dierks, T. The Transport Layer Security (TLS) Protocol Version 1.2; The Internet Society: Reston, VA, USA, 2008. [Google Scholar]
- Soghoian, C.; Stamm, S. Certified lies: Detecting and defeating government interception attacks against SSL (short paper). In Financial Cryptography and Data Security; Springer: Berlin, Germany, 2012; pp. 250–259. [Google Scholar]
- Callegati, F.; Cerroni, W.; Ramilli, M. Man-in-the-middle attack to the HTTPS protocol. IEEE Secur. Priv. 2009, 7, 78–81. [Google Scholar]
- Foundation, E.F. The EFF SSL Observatory. 2014. Available online: http://www.eff.org/observatory accessed on 4 June 2015.
- Foundation, E.F. The EFF Color Map of CAs. 2014. Available online: http://www.eff.org/files/colour_map_of_CAs.pdf accessed on 4 June 2015.
- Advisory, M.S. Fraudulent Digital Certificates Could Allow Spoofing. 2011. Available online: http://technet.microsoft.com/en-us/security/advisory/2607712 accessed on 4 June 2015.
- Nightingale, J. Diginotar Removal Follow Up. 2011. Available online: http://blog.mozilla.com/security/2011/09/02/diginotar-removal-follow-up/ accessed on 4 June 2015.
- Fisher, D. New Versions of Chrome and Firefox Disable Diginotar Root. 2011. Available online: https://threatpost.com/new-versions-chrome-and-firefox-disable-diginotar-root-083111/75600 accessed on 4 June 2015.
- M. S. Blog Comodo certificate issue follow up. 2011. Available online: https://blog.mozilla.com/security/2011/03/25/comodo-certificate-issue-follow-up/ accessed on 4 June 2015.
- Wendlandt, D.; Andersen, D.G.; Perrig, A. Perspectives: Improving SSH-style host authentication with multi-path probing. Proceedings of the USENIX Annual Technical Conference, Boston, MA, USA, 22–27 June 2008; pp. 321–334.
- Tor Project HTTPS Everywhere. 2011. Available online: https://trac.torproject.org/projects/tor/wiki/doc/HTTPSEverywhere/SSLObservatorySubmission(accessed accessed on 4 June 2015.
- Laurie, B. Improving SSL Certificate Security. 2011. Available online: http://googleonlinesecurity.blogspot.com/2011/04/improving-ssl-certificate-security.html accessed on 4 June 2015.
- Foundation, E.F. The Sovereign Keys Project. 2011. Available online: https://www.eff.org/zh-hans/sovereign-keys accessed on 4 June 2015.
- International Telecommunication Union. Information Technology ASN.1 Encoding Rules: Specification of Basic Encoding Rules (BER), Canonical Encoding Rules (CER) and Distinguished Encoding Rules (DER). 2002. Available online: http://www.itu.int/ITU-T/studygroups/com17/languages/X.690-0207.pdf accessed on 4 June 2015.
- International Telecommunication Union. Information Technology Open Systems Interconnection the Directory: Selected Attribute Types. 2002. Available online: http://www.itu.int/rec/T-REC-X.520-200811-I/en accessed on 1 July 2012.
- Nystrom, M.; Kaliski, B. Certification Request Syntax Specification Version 1.7. 2008. Available online: http://tools.ietf.org/html/rfc2986 accessed on 4 June 2015.
- Nightingale, J. Fraudulent *.google.com Certificate. 2011. Available online: http://blog.mozilla.com/security/2011/08/29/fraudulent-google-com-certificate/ accessed on 4 June 2015.
- Nightingale, J. Diginotar Removal Follow up. 2011. Available online: http://blog.mozilla.com/security/2011/09/02/diginotar-removal-follow-up/ accessed on 4 June 2015.
- Boneh, D. SSL Man in the Middle Proxy. 2007. Available online: http://crypto.stanford.edu/ssl-mitm/ accessed on 4 June 2015.
- Foundation, E.F. Observatory Certificate Database. 2007. Available online: http://www.eff.org/files/observatory-dec-2010.sql.lzma.torrent accessed on 4 June 2015.
- SSL MITM Attack by Iranian Government. 2011. Available online: http://pastebin.com/ff7Yg663 accessed on 4 June 2015.
- Comodo fraud incident. 2011. Available online: https://www.comodo.com/Comodo-Fraud-Incident-2011-03-23.html accessed on 4 June 2015.
- Durumeric, Z.; Wustrow, E.; Halderman, J.A. ZMap: Fast Internet-wide scanning and its security applications. Proceedings of the 22nd USENIX Security Symposium, Washington, DC, USA, 14–16 August 2013; pp. 605–620.
- Cho, J.H.; Swami, A.; Chen, R. A survey on trust management for mobile ad hoc networks. IEEE Commun. Surv. Tutor. 2011, 13, 562–583. [Google Scholar]
- Zhou, P.; Jiang, S.; Irissappane, A.A.; Zhang, J.; Zhou, J.; Teo, J.C.M. Toward energy-efficient trust system through watchdog optimization for WSNs. IEEE Trans. Inf. Forens. Secur. 2015, 10, 613–625. [Google Scholar]
- Eirinaki, M.; Louta, M.D.; Varlamis, I. A Trust-aware system for personalized user recommendations in social networks. IEEE Trans. Syst. Man Cybern. 2014, 44, 409–421. [Google Scholar]
- Huynh, T.D.; Jennings, N.R.; Shadbolt, N.R. An integrated trust and reputation model for open multi-agent systems. Autono. Agents Multi-Agent Syst. 2006, 13, 119–154. [Google Scholar]
- Zhou, P.; Luo, X.; Chen, A.; Chang, R.K. SGor: Trust graph based onion routing. Comput. Netw. 2013, 57, 3522–3544. [Google Scholar]
- Zhou, P.; Luo, X.; Chang, R.K. Inference attacks against trust-based onion routing: Trust degree to the rescue. Comput. Secur. 2013, 39, 431–446. [Google Scholar]
- Lee, H.K.; Malkin, T.; Nahum, E. Cryptographic strength of SSL/TLS servers: Current and recent practices. Proceedings of the 7th ACM SIGCOMM Conference on Internet Measurement, San Diego, CA, USA, 24–26 October 2007; pp. 83–92.
- Yilek, S.; Rescorla, E.; Shacham, H.; Enright, B.; Savage, S. When private keys are public: Results from the 2008 Debian OpenSSL vulnerability. Proceedings of the 9th ACM SIGCOMM Conference on Internet Measurement, Chicago, IL, USA, 4–6 November 2009; pp. 15–27.
- Ristic, I. Internet SSL survey. 2010. Available online: http://media.blackhat.com/bh-us-10/presentations/Ristic/BlackHat-USA-2010-Ristic-Qualys-SSL-Survey-HTTP-Rating-Guide-slides.pdf accessed on 4 June 2015.
- Eckersley, P.; Burns, J. Is the SSLiverse a Safe Place? 2010. Available online: http://www.eff.org/files/ccc2010.pdf accessed on 4 June 2015.
- Holz, R.; Braun, L.; Kammenhuber, N.; Carle, G. The SSL landscape: A thorough analysis of the X.509 PKI using active and passive measurements. Proceedings of the 2011 ACM SIGCOMM Conference on Internet Measurement Conference, Berlin, Germany, 2–4 November 2011; pp. 427–444.
- Fung, A.P.; Cheung, K. SSLock: Sustaining the trust on entities brought by SSL. Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security, Beijing, China, 13–16 April 2010; pp. 204–213.
- Adelsbach, A.; Gajek, S.; Schwenk, J. Visual spoofing of SSL protected web sites and effective countermeasures. In Information Security Practice and Experience; Springer: Berlin, Germany, 2005; pp. 204–216. [Google Scholar]
- Xia, H.; Brustoloni, J.C. Hardening web browsers against man-in-the-middle and eavesdropping attacks. Proceedings of the 14th International Conference on World Wide Web, Chiba, Japan, 10–14 May 2005; pp. 489–498.

| Name | Abbreviation | |||
|---|---|---|---|---|
| N/A | CommonName | CN | N/A | |
| Country | C | 211 | ||
| Description | DC | 8 | ||
| Locality | L | 27, 947 | ||
| StateOrProvince | ST | 7020 | ||
| Organization | O | 628, 401 | ||
| OrganizationUnit | OU | 38, 606 | ||
| PublicKeyAlgorithm | N/A | 2 | ||
| N/A | KeyLength | N/A | 57 |
| DN | CA | Iy | Result | CA | Iy | Result | CA | Iy | Result | |||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ➀ | 3 | 2 | 0 | Legitimate | 2 | 16 | Fake! | 2 | 14 | Fake! | ||||
| 3 | 0 | Legitimate | 3 | 18 | Fake! | 3 | 6 | Fake! | ||||||
| ➁ | 3 | 2 | 0 | Legitimate | 2 | 17 | Fake! | 2 | 13 | Fake! | ||||
| 3 | 0 | Legitimate | 3 | 18 | Fake! | 3 | 5 | Fake! | ||||||
| ➂ | 3 | 2 | 0 | Legitimate | 2 | 18 | Fake! | 2 | 11 | Fake! | ||||
| Legitimate | 3 | 0 | Legitimate | DigiNotar | 3 | 19 | Fake! | Comodo | 3 | 6 | Fake! | |||
| ➃ | 4 | 2 | 0 | Legitimate | 2 | 18 | Fake! | 2 | 14 | Fake! | ||||
| 3 | 0 | Legitimate | 3 | 19 | Fake! | 3 | 6 | Fake! | ||||||
| 4 | 0 | Legitimate | 4 | 24 | Fake! | 4 | 44 | Fake! | ||||||
| ➄ | 3 | 2 | 32 | Fake! | 2 | 24 | Fake! | 2 | 16 | Fake! | ||||
| 3 | 18 | Fake! | 3 | 24 | Fake! | 3 | 13 | Fake! | ||||||
© 2015 by the authors; licensee MDPI, Basel, Switzerland This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gu, X.; Gu, X. On the Detection of Fake Certificates via Attribute Correlation. Entropy 2015, 17, 3806-3837. https://doi.org/10.3390/e17063806
Gu X, Gu X. On the Detection of Fake Certificates via Attribute Correlation. Entropy. 2015; 17(6):3806-3837. https://doi.org/10.3390/e17063806
Chicago/Turabian StyleGu, Xiaojing, and Xingsheng Gu. 2015. "On the Detection of Fake Certificates via Attribute Correlation" Entropy 17, no. 6: 3806-3837. https://doi.org/10.3390/e17063806
APA StyleGu, X., & Gu, X. (2015). On the Detection of Fake Certificates via Attribute Correlation. Entropy, 17(6), 3806-3837. https://doi.org/10.3390/e17063806





