Preventing Return Fraud in Reverse Logistics—A Case Study of ESPRES Solution by Ethereum
Abstract
:1. Introduction
2. Preliminary
2.1. Reverse Logistics
- Economy: The most direct reason is to reduce the use of raw materials and the cost of disposal, and to create added value for the final product. The indirect reason is demonstrating environmentally friendly and responsible behaviors to promote customer relations.
- Law: In many countries such as the European Union, companies must be responsible for the recycling and related disposal of waste generated by the products produced or distributed by companies.
- Society: Society realizes the importance of protecting the environment and the concept of sustainability, which leads to the companies’ responsibility such as controlling carbon emissions and waste disposal.
2.2. Return/Exchange Fraud
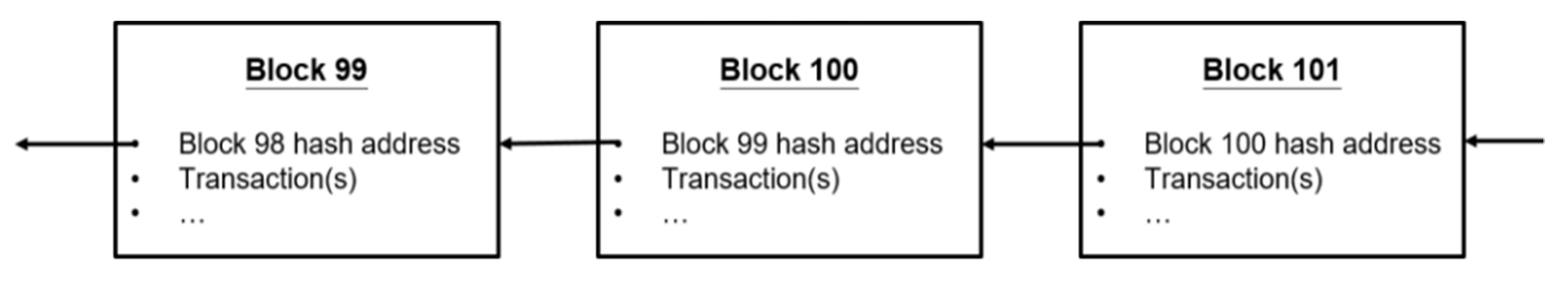
2.3. Blockchain Technology
- Bitcoin: Nakamoto [23] explained Bitcoin’s mathematical logic, basic technical concepts, and how to use P2P networks to create electronic transaction systems that do not require dependence and trust. Bitcoin uses P2P architecture and cryptography principles to maintain the security of the entire Bitcoin network. P2P networks do not have a main server to operate. Participants of Bitcoin are user-end nodes with two roles: user and miner. The user can send and execute Bitcoin transactions. The miner is responsible for calculating the proof of work, broadcasting the output block to other nodes for verification, and then getting the corresponding amount of Bitcoin as a reward. The block is composed of multiple transactions. The transaction will be collected by the miners, and the address of the next block will be calculated and verified using the proof of work to generate a new block.
- 2.
- Ethereum: Ethereum [24] is one of the widely used blockchain networks in which a currency called Ether (ETH) is in circulation. Smart Contracts in Ethereum can be freely developed and executed in the blockchain. Smart contracts must be executed in the Ethereum Virtual Machine (EVM) connected to the Ethereum node and written in Solidity language. The user passes the transaction to the Ethereum network in order to create a new contract, invoke the function of the contract, and transfer ether to the contract or other users. All transactions will be recorded in the public additional data structure of the blockchain. The order of transactions on the blockchain determines the state of each contract and the balance of each user. Unlike the Bitcoin network, there are two types of accounts on Ethereum: the Externally Owned Account (EOA) and the Contract Account (CA). The EOA is an account held by a user with information such as the address and account balance. The CA is an account attached to the contract, which contains the address and balance like the EOA. The CA must be created by the user through the EOA transaction creation.
2.4. Research Questions
2.5. Large Household Appliances
3. Proposed ESPRES System
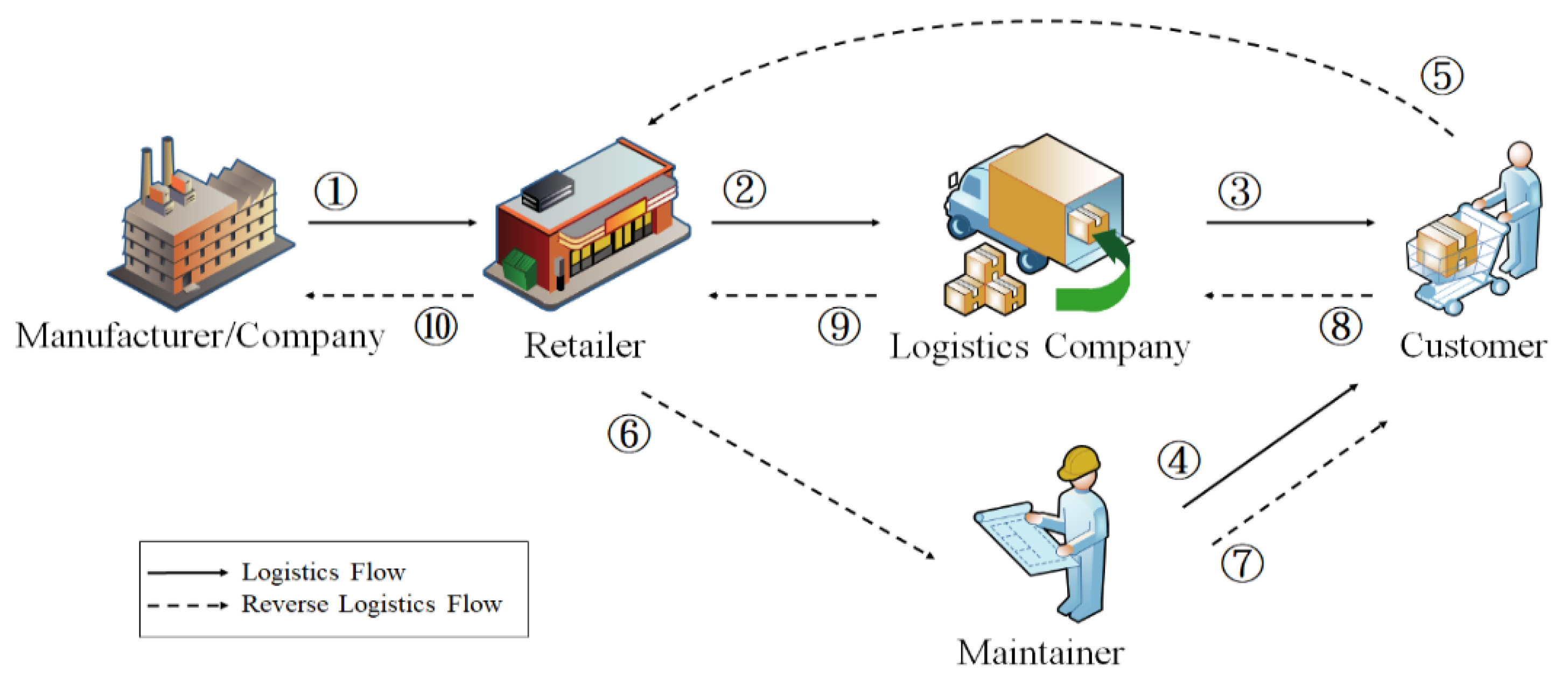
3.1. Delivery and Return Scenarios of Large Home Appliances
- The product is delivered by the manufacturer to the retailer.
- After the manufacturer sends the large appliances to the retailer, the retailer sells them to the consumer.
- After consumers purchase goods from retailers, they are distributed by logistics companies and delivered to designated locations.
- After the large home appliances are delivered to the designated location, maintenance personnel will install them.
- During the re-appreciation period, if the consumer finds that the purchased product is faulty or inconsistent with the original, the consumer can perform the return and exchange procedure through the e-commerce platform.
- After the consumer applies for a return, the retailer will notify the maintenance staff to go to the designated place for disassembly.
- After receiving the notice, the maintenance will go to the designated place for disassembly procedures.
- After the dismantling of the goods is completed, the logistics company will take it back to the designated location.
- The logistics company ships the large appliances back to retailers.
- The retailer sends the goods returned by the consumer back to the manufacturer for testing.
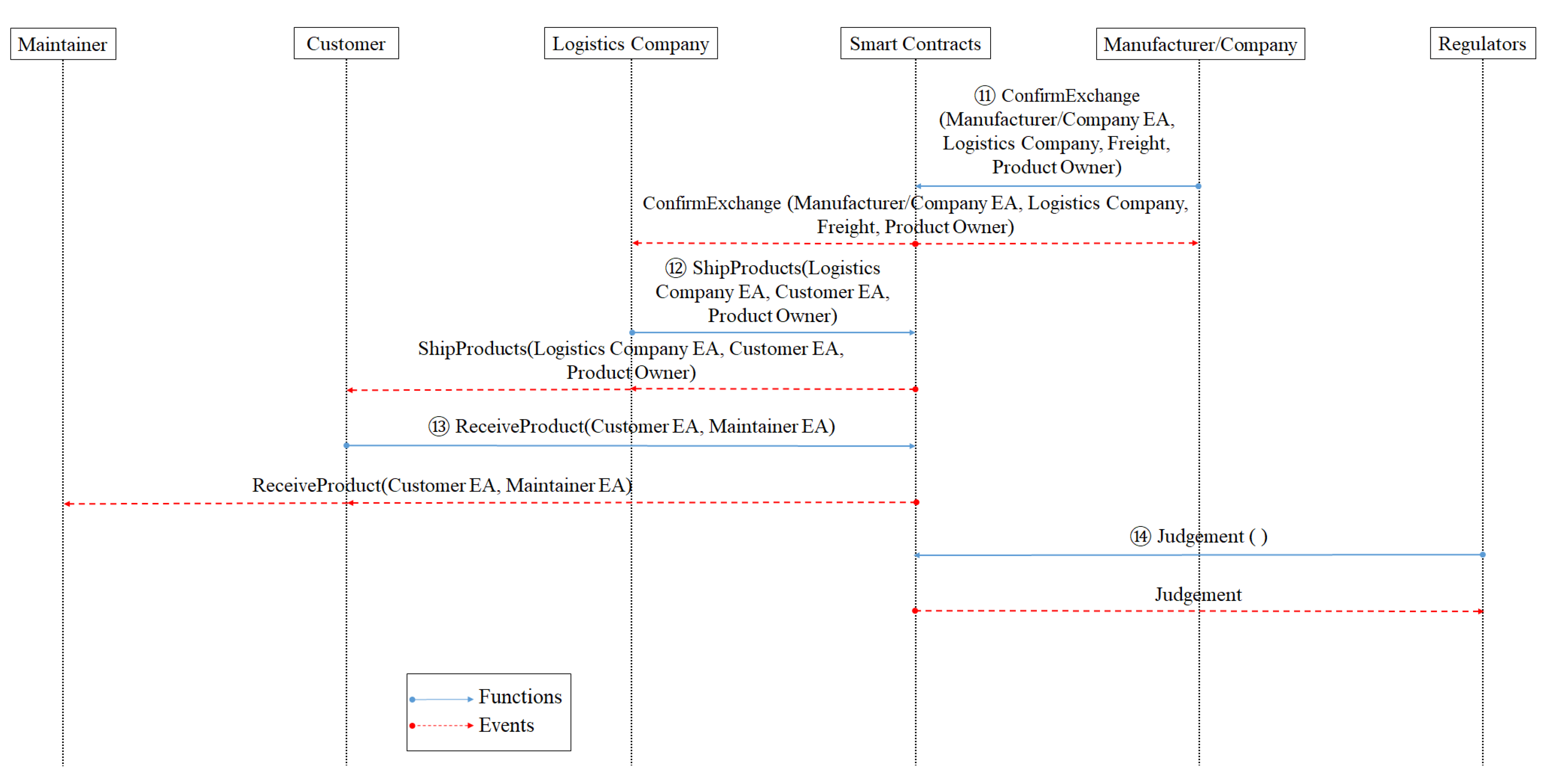
3.2. ESPRES System
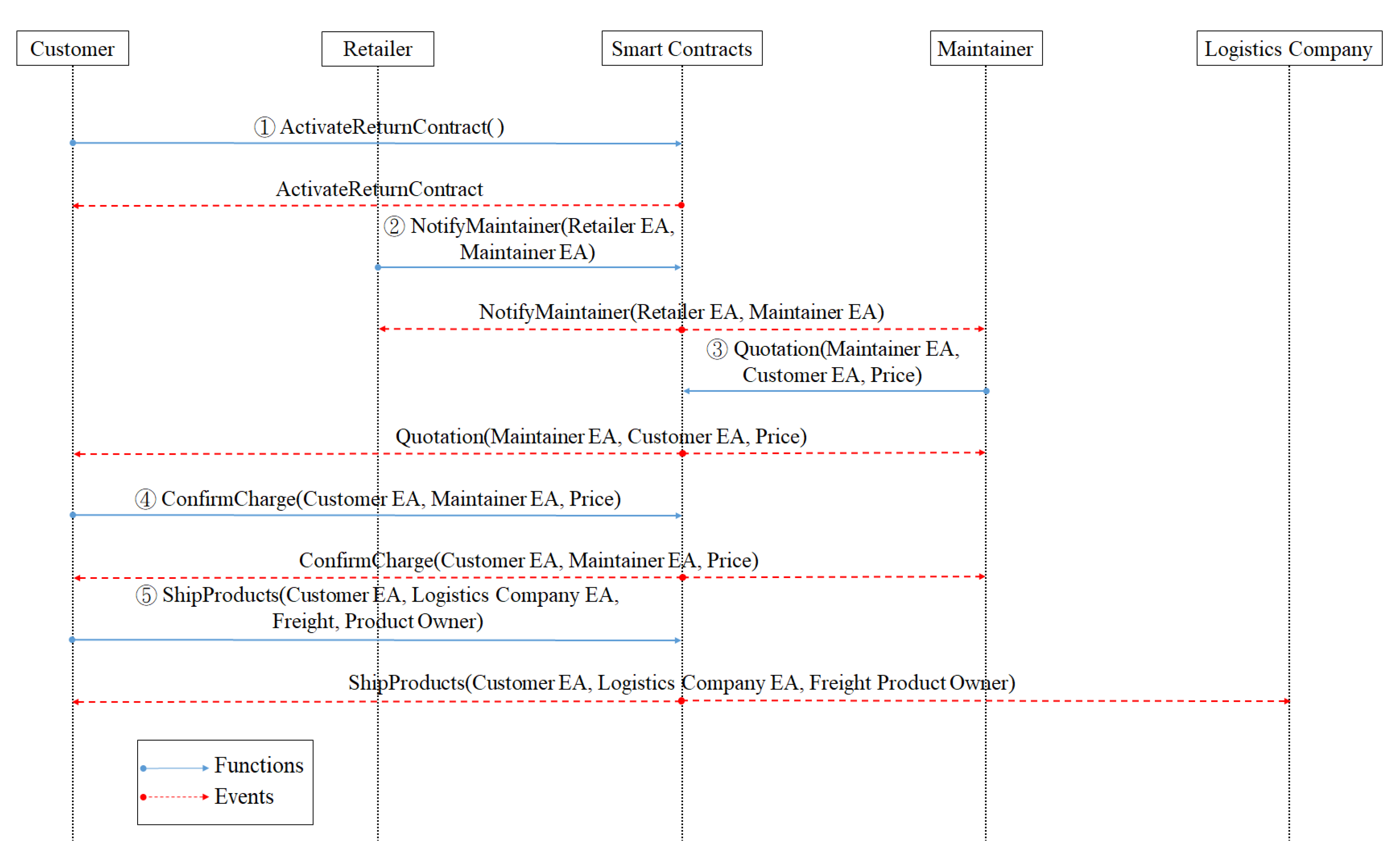
- When customers are dissatisfied with the products or have defects or malfunctions during the appreciation period, they will request a return or exchange, which activates the return smart contract.
- After receiving the customer’s return application, the retailer will notify the maintainer.
- The maintainer will go to the place designated by the customer for disassembly, assembly, and to quote the cost to the customer.
- After the customer confirms the quotation for the disassembly and assembly costs of the maintainer, the payment is made.
- The customer makes requests for delivery, such as delivery time, logistics company, etc.
- The logistics company incorporates the delivery requirements and puts the customer’s requirement into the PROMETHEE [32] decision.
- PROMETHEE sorts and provides customers with the most suitable shipping method and freight.
- Customers confirm and pay the freight to the logistics company.
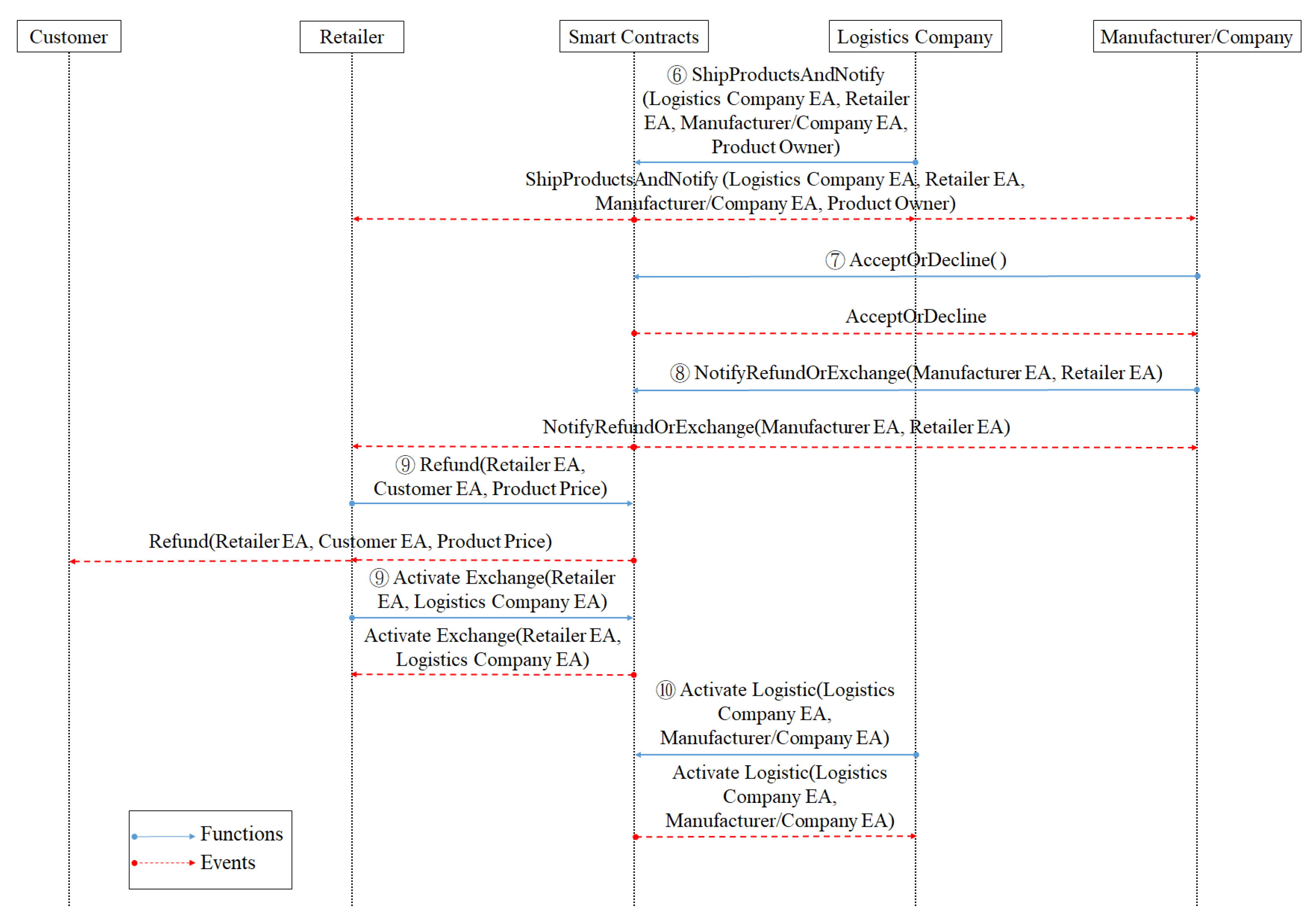
- The logistics company sends the large household electrical appliances back to the manufacturer at the place designated by the customer.
- The logistics company informs the retailer and the manufacturer.
- After the manufacturer receives the returned goods and conducts inspections, they will decide whether to accept the returned goods or not.
- If the manufacturer accepts, it will notify the retailer to refund the customer. If the manufacturer accepts the exchange, it will notify the retailer to proceed with the following replacement procedure.
- If the retailer receives the manufacturer’s refund notification, it will refund the money to the customer; if it receives the manufacturer’s replacement notification, the replacement procedure will be initiated.
- If the retailer initiates the replacement procedure, the logistics company will receive the replacement notification.
- The logistics company starts the logistics to deliver the goods, and collects the goods to be replaced or repaired to the manufacturer.
- The manufacturer confirms the exchange, pays the freight to the logistics company, and the logistics company will deliver the goods to customers.
- If the customer receives the replaced product, they will notify the maintainer.
- After receiving the notice from the customer, the maintainer will reinstall the large household appliances at the place designated by the customer, and the transaction will end.
- When there are disputes in the process of return and exchange, the regulators will evaluate and judge.
- The judged result will be transmitted back to the party who brought the dispute.
- Relevant information will be backed up to the Inter Planetary File System (IPFS). IPFS is a network transmission protocol designed to establish persistent and distributed storage and sharing of files.
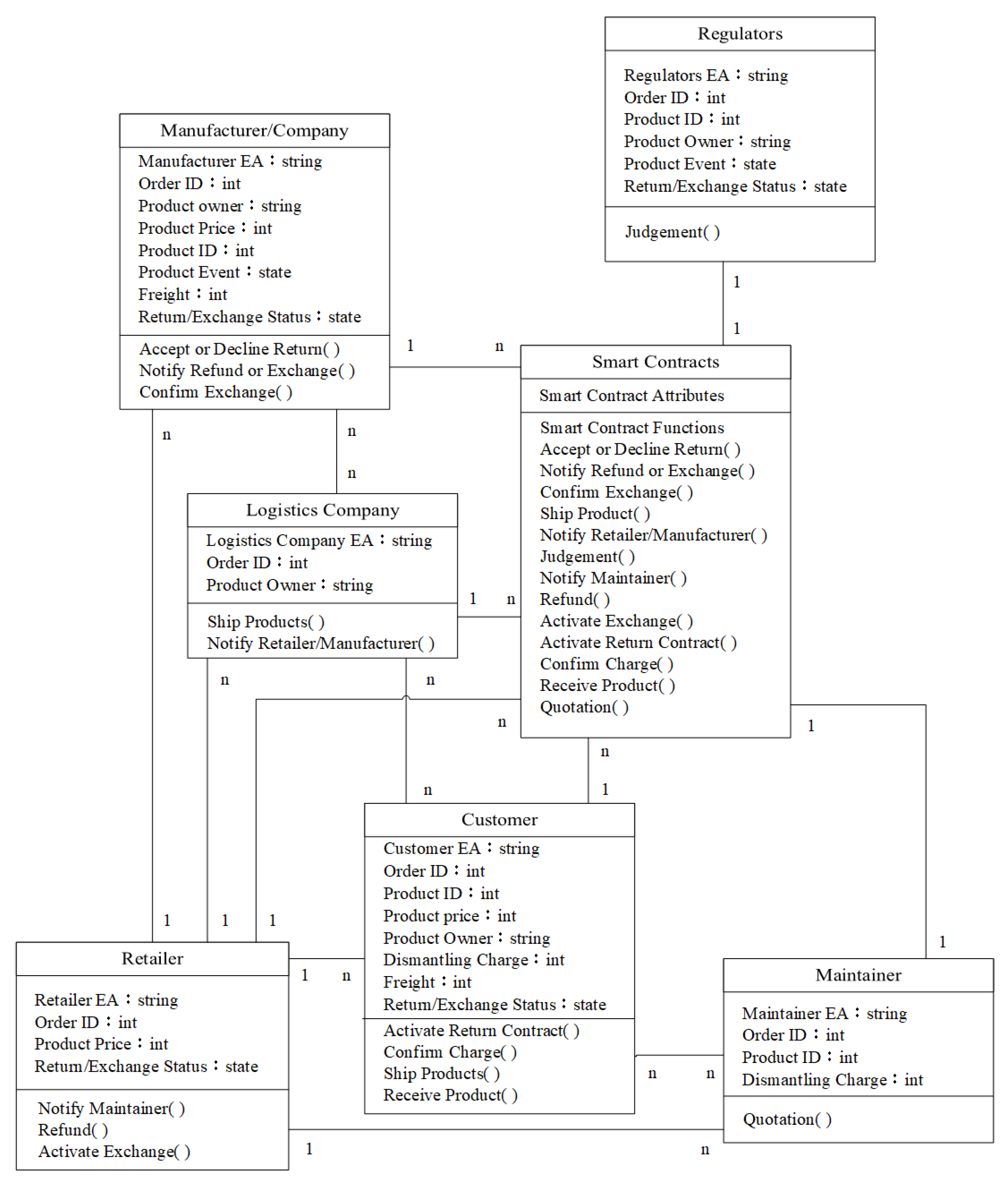
3.3. Implemented Contracts
| Algorithm1 Activate |
| Input: Ethereumaddress(EA) of Customer Ethereumaddress(EA) of Retailer Ethereumaddress(EA) of Logistics Company OrderNumber, ProductID, ProductOwner 1. Contractstate is Created 2. Restrict access to only Customer, Retailer, or Logistics Company 3. if Customer access = agree then 4. if OrderNumber = 0 then 5. str = OrderNumber no register!! 6. else 7. if ProductID = 0 then 8. str = ProductID no register!! 9. else 10. Contract state changes to Activated 11. Create a notification message stating Return 12. end 13. end 14. else if Retailer access = agree then 15. if OrderNumber = 0 then 16. str = OrderNumber no register!! 17. else 18. Contract state changes to Activated 19. Create a notification message stating Exchange 20. end 21. else if Logistics Company access = agree then 22. if OrderNumber = 0 then 23. str = OrderNumber no register!! 24. else 25. if ProductID = 0 then 26. str = ProductID no register!! 27. else 28. if ProductOwner = Manufacturer then 29. Contract state changes to Activated 30. Create a notification message stating Logistics 31. end 32. end 33. end 34. else 35. Revert contract state and show an error 36. end |
| Algorithm 2 Notify |
| Input: Ethereumaddress(EA) of Retailer Ethereumaddress(EA) of Logistics Company Ethereumaddress(EA) of Manufacturer Ethereumaddress(EA) of Customer Ethereumaddress(EA) of Maintainer Notification 1. Restrict access to only Retailer, Logistics Company, Manufacturer, Customer 2. if Retailer access = agree then 3. Create a notification message stating Maintainer Dismantling Products 4. else if Logistics Company access = agree then 5. Create a notification message stating Shipping Product to Manufacturer 6. else if Manufacturer access = agree then 7. if Return = accept then 8. Create a notification message stating Retailer Refund 9. else if Exchange = accept then 10. Create a notification message stating Retailer Exchange 11. end 12. else if Customer access = agree then 13. Create a notification message stating Maintainer Reinstall Products 14. else 15. Revert contract state and show an error 16. end |
| Algorithm 3 Dismantling Charge Quoted Price |
| Input: Ethereumaddress(EA) of Maintainer Ethereumaddress(EA) of Customer OrderNumber, ProductID, DismantlingCharge 1. Contractstate is Activated 2. Restrict access to only Maintainer 3. if Maintainer access = agree then 4. if OrderNumber = 0 then 5. str = OrderNumber no register!! 6. else 7. if ProductID = 0 then 8. str = ProductID no register!! 9. else 10. Contract state changes to Dismantled 11. Create a notification message stating Dismantling Charge 12. end 13. end 14. else 15. Revert contract state and show an error 16. end |
| Algorithm 4 Freight Decision |
| Input: Ethereumaddress(EA) of Logistics Company Ethereumaddress(EA) of Customer 1. Contractstate is Activated 2. Restrict access to only Customer 3. if Customer access = agree then 4. Plans_sorce = function decision(Logistics Companys, Transportation Time, Distance, Product Volume) 5. print (Plans_sorce) 6. else 7. Revert contract state and show an error 8. end |
| Algorithm 5 Charge |
| Input: Ethereumaddress(EA) of Customer Ethereumaddress(EA) of Maintainer Ethereumaddress(EA) of Logistics Company Ethereumaddress(EA) of Retailer Ethereumaddress(EA) of Manufacturer OrderNumber, ProductID, DismantlingCharge, Freight, ProductPrice 1. Restrict access to only Customer, Retailer, Manufacturer 2. if Customer access = agree then 3. if OrderNumber = 0 then 4. str = OrderNumber no register!! 5. else 6. if ProductID = 0 then 7. str = ProductID no register!! 8. else 9. if DismantlingCharge = paid then 10. Create a notification message stating Payment Dismantling Charge 11. else if Freight = paid then 12. Create a notification message stating Payment Freight 13. end 14. end 15. end 16. else if Retailer access = agree then 17. if OrderNumber = 0 then 18. str = OrderNumber no register!! 19. else 20. if ProductPrice = paid then 21. Create a notification message stating Refund 22. end 23. else if Manufacturer access = agree then 24. if OrderNumber = 0 then 25. str = OrderNumber no register!! 26. else 27. if Freight = paid then 28. Create a notification message stating Payment Freight 29. end 30. end 31. else 32. Revert contract state and show an error 33. end |
| Algorithm 6 Transfer Product Owner |
| Input: Ethereumaddress(EA) of Customer Ethereumaddress(EA) of Logistics Company Ethereumaddress(EA) of Manufacturer OrderNumber, ProductID, ProductOwner 1. Contractstate is Dismantled 2. Restrict access to only Customer, Logistics Company, Manufacturer 3. if Customer access = agree and Freight = paid then 4. if OrderNumber = 0 then 5. str = OrderNumber no register!! 6. else 7. if ProductID = 0 then 8. str = ProductID no register!! 9. else 10. Contract state changes to Transferred 11. Transfer Product Owner to Logistics Company 12. Create a notification message stating Transferred Product Owner 13. end 14. end 15. else if Logistics Company access = agree then 16. if OrderNumber = 0 then 17. str = OrderNumber no register!! 18. else 19. if ProductID = 0 then 20. str = ProductID no register!! 21. else 22. if Customer Freight = received then 23. Contract state changes to Transferred 24. Transfer Product Owner to Manufacturer 25. Create a notification message stating Transferred Product Owner 26. else 27. if Manufacturer Freight = received then 28. Contract state changes to Transferred 29. Transfer Product Owner to Customer 30. Create a notification message stating Transferred Product Owner 31. else 32. Revert contract state and show an error 33. end 34. end 35. end 36. end 37. else if Manufacturer access = agree and Freight = paid then 38. if OrderNumber = 0 then 39. str = OrderNumber no register!! 40. else 41. if ProductID = 0 then 42. str = ProductID no register!! 43. else 44. Contract state changes to Transferred 45. Transfer Product Owner to Logistics Company 46. Create a notification message stating Transferred Product Owner 47. end 48. end 49. else 50. Revert contract state and show an error 51. end |
| Algorithm 7 Company Decision |
| Input: Ethereumaddress(EA) of Manufacturer OrderNumber, ProductID 1. Contractstate is Transferred 2. Restrict access to only Manufacturer 3. if Manufacturer access = agree then 4. if OrderNumber = 0 then 5. str = OrderNumber no register!! 6. else 7. if ProductID = 0 then 8. str = ProductID no register!! 9. else 10. Contract state changes to Decided 11. Create a notification message stating Accepted or Declined Return 12. end 13. end 14. else 15. Revert contract state and show an error 16. end |
| Algorithm 8 Argument |
| Input: Ethereumaddress(EA) of Regulator OrderNumber, ProductID 1. Restrict access to only Regulator 2. if Regulator access = agree then 3. if OrderNumber = 0 then 4. str = OrderNumber no register!! 5. else 6. if ProductID = 0 then 7. str = ProductID no register!! 8. else 9. Contract state changes to Judged 10. Transfer the Product Contract balance to Regulator 11. end 12. end 13. else 14. Revert contract state and show an error 15. end |
4. Security Analysis and Comparison
- Reentrancy Vulnerability: When a smart contract uses functions related to remittances, it is possible that Reentrancy Vulnerability may be generated due to processing order issues in the design. In other words, if the remittance is performed before the storage status is changed, a malicious attacker will create a new contract through the loophole to steal the Ether in the victim contract. In June 2016, a German startup company DAO, was a victim of this loophole and a market value of approximately US$50 million was stolen. As long as the remittance process is involved, the issue of Reentrancy must be taken seriously. There is a design pattern called the checks-effects-interactions pattern that can solve this problem. First, in the Checks phase, the designer must determine whether the conditions are met, such as the use of the require() function. The second stage, Effects, is to update the state in the contract. In the final Interactions stage, remittance instructions or exchange messages with other contracts or accounts are used.
- Transaction-Ordering Dependence: Since the order in which the transactions are included in the block depends on the miners, sometimes the transactions cannot be executed in the planned order. This problem is called Transaction-Ordering Dependence (TOD).
- Mishandled Exceptions: If an exception occurs when calling a function in Ethereum, the contract must be aborted and the recovery state returns false. However, the design may have abnormal behavior that will not be directly returned to the user.
- Timestamp Dependency: In smart contract design,” block.timestamp” or “now” is often used to obtain the timestamp of the block. When using these numbers for calculations, miners have a certain degree of ability to master the write time. For example: using block.timestamp to calculate a random number lottery, as long as a miner has the ability to mine a block at a specific time, it can be rewarded by participating in the lottery.
- Cryptolojacking Lifecycle: One-third of the Cryptojacking samples disappear within 15 days with frequent updates [35].
4.1. Cost Analysis
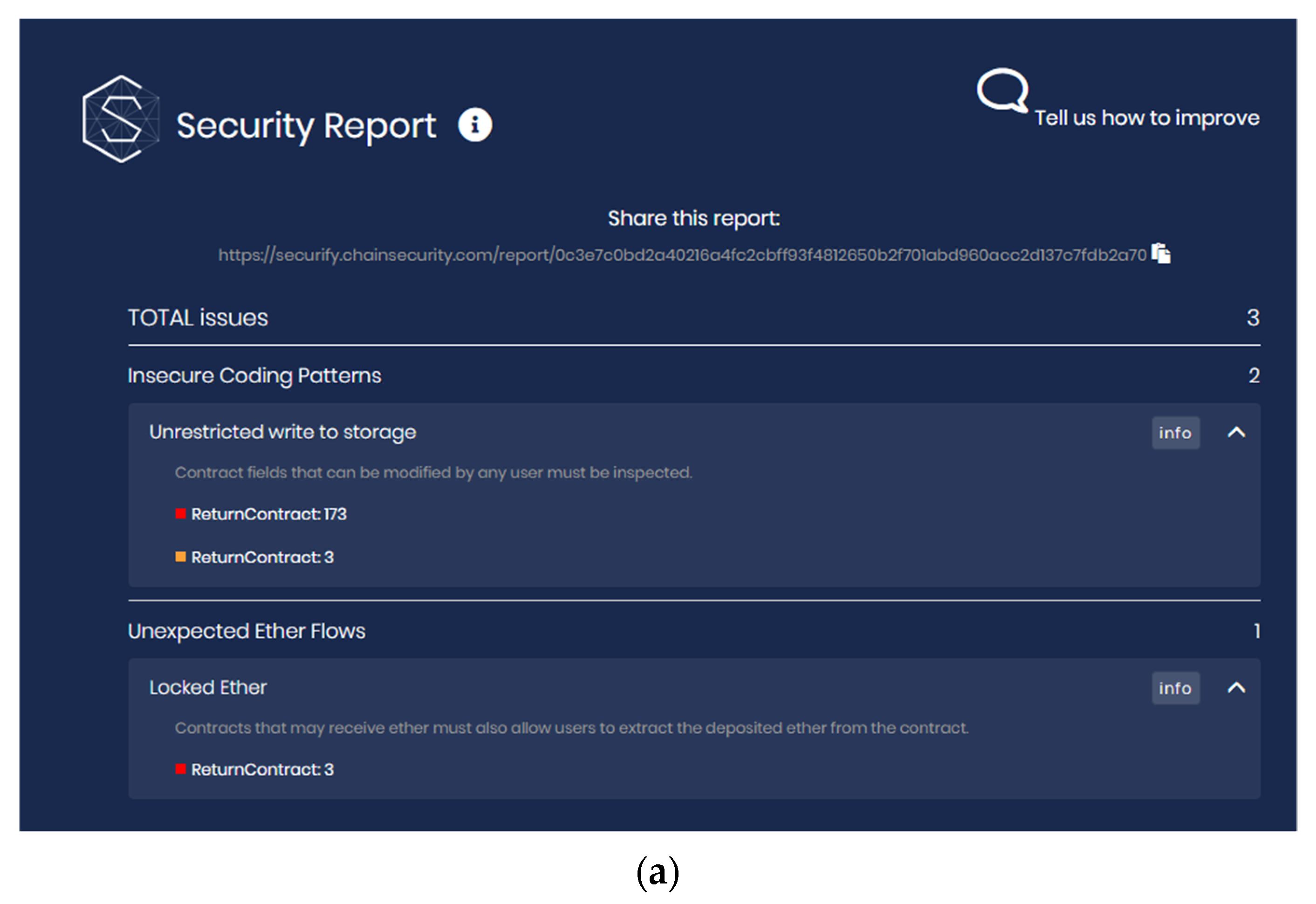
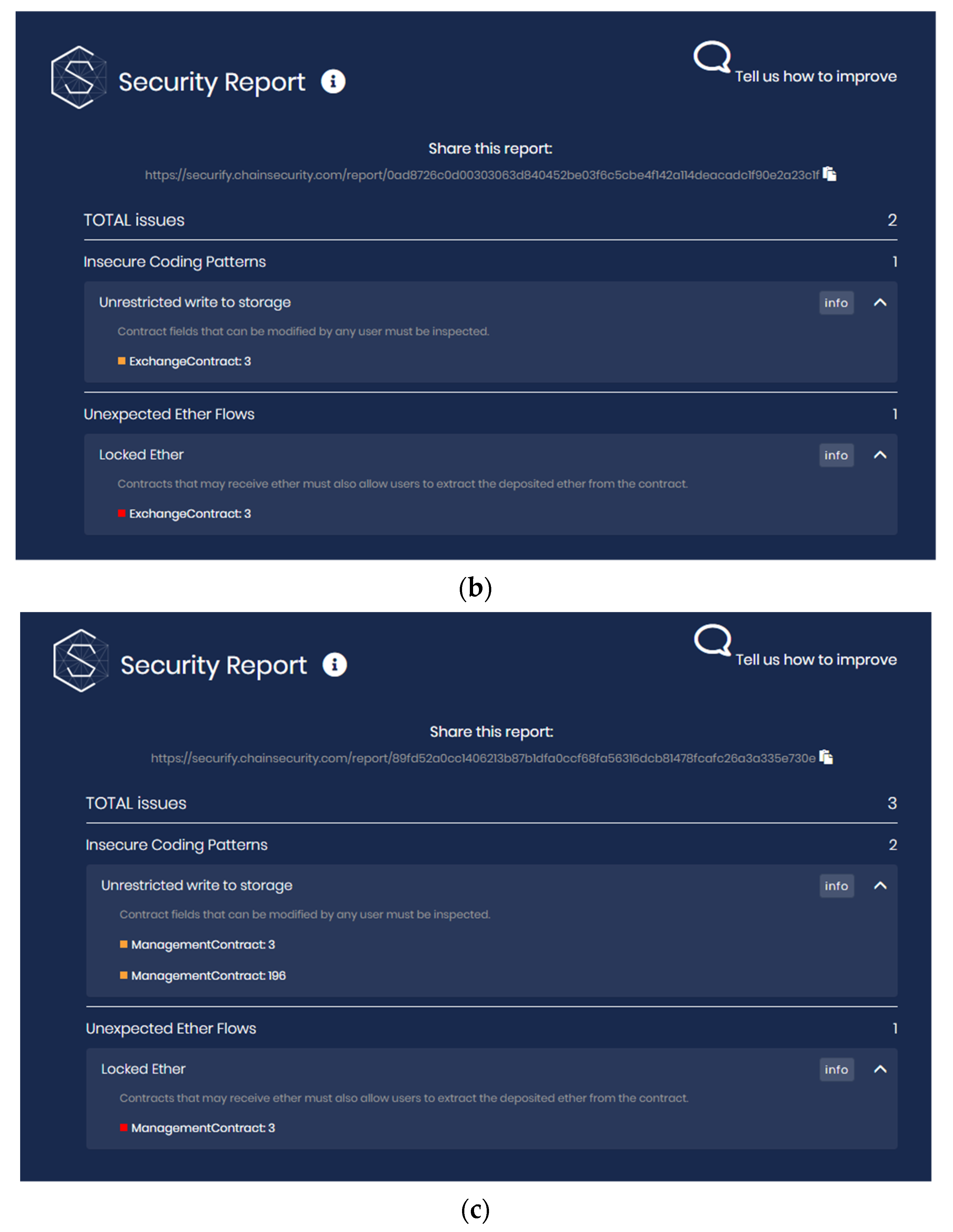
4.2. Security Analysis Report
4.3. Comparison
5. Framework Discussion
- Consumers perform return fraud through fake invoices.
- Consumers try to execute return fraud through parallel imports.
- Consumers try to collude with maintenance workers for return and exchange fraud.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Verhoef, P.C.; Kannan, P.K.; Inman, J.J. From multi-channel retailing to omni-channel retailing: Introduction to the special issue on multi-channel retailing. J. Retail. 2015, 91, 174–181. [Google Scholar] [CrossRef]
- Reitblat, M. Returns Abuse: A $24 Billion Problem, TotalRetail. 2020. Available online: https://www.mytotalretail.com/article/returns-abuse-a-24-billion-problem/ (accessed on 14 April 2021).
- Daniel Parisi, Return Fraud Represents $2.2 Billion in Lost Sales—Omnichannel Retailers Are Particularly Vulnerable. December 2015. Available online: https://geomarketing.com/return-fraud-represents-2-2-billion-in-lost-sales-omnichannel-retailers-are-particularly-vulnerable (accessed on 25 May 2021).
- Schmidt, R.A.; Sturrock, F.; Ward, P.; Lea-Greenwood, G. Deshopping—The art of illicit consumption. Int. J. Retail Distrib. Manag. 1999, 27, 290–301. [Google Scholar] [CrossRef]
- King, T.; Dennis, C.; McHendry, J. The management of deshopping and its effects on service: A mass market case study. Int. J. Retail Distrib. Manag. 2007, 35, 720–733. [Google Scholar] [CrossRef] [Green Version]
- Speights, D.; Hilinski, M. Return fraud and abuse: How to protect profits. Retail. Issues Lett. 2005, 17, 1–6. [Google Scholar]
- Zhuravlev, Y.; Dokukin, A.; Senko, O.; Stefanovskiy, D. Use of Clusterization Technique to Highlight Groups of Related Goods by Digital Traces in Retail Trade. In Proceedings of the 2019 9th International Conference on Advanced Computer Information Technologies (ACIT), Ceske Budejovice, Czech Republic, 5–7 June 2019; pp. 84–88. [Google Scholar]
- Pagés, R.; Amplianitis, K.; Monaghan, D.; Ondřej, J.; Smolić, A. Affordable content creation for free-viewpoint video and VR/AR applications. J. Vis. Commun. Image Represent. 2018, 53, 192–201. [Google Scholar] [CrossRef]
- Henderson, R. Using graph databases to detect financial fraud. Comput. Fraud Secur. 2020, 2020, 6–10. [Google Scholar] [CrossRef]
- Del Mar Roldán-García, M.; García-Nieto, J.; Aldana-Montes, J.F. Enhancing semantic consistency in anti-fraud rule-based expert systems. Expert Syst. Appl. 2017, 90, 332–343. [Google Scholar] [CrossRef] [Green Version]
- Toyoda, K.; Mathiopoulos, P.T.; Sasase, I.; Ohtsuki, T. A novel blockchain-based product ownership management system (POMS) for anti-counterfeits in the post supply chain. IEEE Access 2017, 5, 17465–17477. [Google Scholar] [CrossRef]
- Bower, A.B.; Maxham, J.G. Return shipping policies of online retailers: Normative assumptions and the long-term consequences of fee and free returns. J. Market. 2012, 76, 110–124. [Google Scholar] [CrossRef]
- Vitasek, K. Supply Chain Management Terms and Glossary; Supply Chain Visions: Bellevue, WA, USA, 2009. [Google Scholar]
- Fleischmann, M. Quantitative Models for Reverse Logistics; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2001; Volume 501. [Google Scholar]
- Rubio, S.; Jiménez-Parra, B. Reverse logistics: Overview and challenges for supply chain management. Int. J. Eng. Bus. Manag. 2014, 6, 12. [Google Scholar] [CrossRef]
- Prajapati, H.; Kant, R.; Shankar, R. Bequeath life to death: State-of-art review on reverse logistics. J. Clean. Prod. 2019, 211, 503–520. [Google Scholar] [CrossRef]
- Wilkes, R.E. Fraudulent Behavior by Consumers: The other Side of Fraud in the Marketplace: Consumer-Initiated Fraud against Business. J. Market. 1978, 42, 67–75. [Google Scholar] [CrossRef]
- King, T. To Examine the Phenomenon of Deshopping and Retail Policies Preventing Deshopping. Master’s Thesis, Manchester Metropolitan University, Manchester, UK, 1999. [Google Scholar]
- King, T. An analysis of the Phenomenon of Deshopping of Garments in Women’s Wear Retailing. Ph.D. Thesis, Brunnel University, Brunel, UK, 2004. [Google Scholar]
- Jendruszak, B. Ecommerce’s Dirty Secret: The Growing Problem of Return Fraud and How to Fight It. Available online: https://seon.io/resources/how-to-fight-return-fraud/ (accessed on 5 May 2021).
- Li, J.; Wang, X. Research on the Application of Blockchain in the Traceability System of Agricultural Products. In Proceedings of the 2018 2nd IEEE Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Xi’an, China, 25–27 May 2018; pp. 2637–2640. [Google Scholar]
- Lin, I.C.; Liao, T.C. A Survey of Blockchain Security Issues and Challenges. Int. J. Netw. Secur. 2017, 19, 653–659. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: Bitcoin.org/bitcoin.pdf (accessed on 5 May 2021).
- Wood, G. Ethereum: A secure decentralized generalized transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Sunny, J.; Undralla, N.; Pillai, V.M. Supply chain transparency through blockchain-based traceability: An overview with demonstration. Comput. Ind. Eng. 2020, 9, 106895. [Google Scholar] [CrossRef]
- Bhatt, P.C.; Kumar, V.; Lu, T.C.; Daim, T. Technology convergence assessment: Case of blockchain within the IR 4.0 platform. Technol. Soc. 2021, 67, 101709. [Google Scholar] [CrossRef]
- Kassen, M. Blockchain and e-government innovation: Automation of public information processes. Inf. Syst. 2021, 103, 101862. [Google Scholar] [CrossRef]
- Gong, Y.; van Engelenburg, S.; Janssen, M. A Reference Architecture for Blockchain-Based Crowdsourcing Platforms. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 937–958. [Google Scholar] [CrossRef]
- Wessling, F.; Ehmke, C.; Hesenius, M.; Gruhn, V. How much blockchain do you need? Towards a concept for building hybrid dapp architectures. In Proceedings of the 2018 IEEE/ACM 1st International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Gothenburg, Sweden, 27 May–3 June 2018; pp. 44–47. [Google Scholar]
- Wüst, K.; Gervais, A. Do you need a Blockchain? In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018; pp. 45–54. [Google Scholar]
- Luhmann, N. Trust and Power; John Wiley & Sons: Hoboken, NJ, USA, 2018. [Google Scholar]
- Brans, J.P.; Mareschal, B. Promethee Methods. In Multiple Criteria Decision Analysis: State of the Art Surveys; International Series in Operations Research & Management Science; Springer: New York, NY, USA, 2005; Volume 78. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, W.; Chen, X.; Weng, J.; Imran, M. An overview on smart contracts: Challenges, advances and platforms. Future Gener. Comput. Syst. 2020, 105, 475–491. [Google Scholar] [CrossRef] [Green Version]
- Luu, L.; Chu, D.H.; Olickel, H.; Saxena, P.; Hobor, A. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 254–269. [Google Scholar]
- Hong, G.; Yang, Z.; Yang, S.; Lei, Z.; Nan, Y.; Zhang, Z.; Duan, H. How You Get Shot in the Back: A Systematical Study about Cryptojacking in the Real World. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 1701–1713. [Google Scholar]
- Li, H.; Han, D. EduRSS: A Blockchain-Based Educational Records Secure Storage and Sharing Scheme. IEEE Access 2019, 7, 179273–179289. [Google Scholar] [CrossRef]
- Tsankov, P.; Dan, A.; Drachsler-Cohen, D.; Gervais, A.; Buenzli, F.; Vechev, M. Securify: Practical security analysis of smart contracts. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 67–82. [Google Scholar]
- Chen, L. Research of E-commerce Supply Chain Management with CreditRisk+ Model. In Proceedings of the 2012 International Conference on Management of e-Commerce and e-Government, Beijing, China, 20–21 October 2012; pp. 353–355. [Google Scholar]
- Xu, L.; Chen, L.; Gao, Z.; Lu, Y.; Shi, W. Coc: Secure supply chain management system based on public ledger. In Proceedings of the 2017 26th International Conference on Computer Communication and Networks (ICCCN), Vancouver, BC, Canada, 31 July–3 August 2017; pp. 1–6. [Google Scholar]
- Kostyuk, P.; Kudryashov, S.; Madhwal, Y.; Maslov, I.; Tkachenko, V.; Yanovich, Y. Blockchain-Based Solution to Prevent Plastic Pipes Fraud. In Proceedings of the 2020 Seventh International Conference on Software Defined Systems (SDS), Paris, France, 20–23 April 2020; pp. 208–213. [Google Scholar]
- Cueva-Sánchez, J.J.; Coyco-Ordemar, A.J.; Ugarte, W. A blockchain-based technological solution to ensure data transparency of the wood supply chain. In Proceedings of the 2020 IEEE ANDESCON, Quito, Ecuador, 13–16 October 2020; pp. 1–6. [Google Scholar]
- Cai, Y.; Zhu, D. Fraud detections for online businesses: A perspective from blockchain technology. Financ. Innov. 2016, 2, 1–10. [Google Scholar] [CrossRef] [Green Version]
- Akın, Y.; Dikkollu, C.; Kaplan, B.B.; Yayan, U.; Yolaçan, E.N. Ethereum Blockchain Network-based Electrical Vehicle Charging Platform with Multi-Criteria Decision Support System. In Proceedings of the 2019 1st International Informatics and Software Engineering Conference (UBMYK), Ankara, Turkey, 6–7 November 2019; pp. 1–5. [Google Scholar]
- Farida, Y.; Khasanah, Z.S.U. Analisis Performa Mata Uang Virtual (Cryptocurrency) Menggunakan Preference Ranking Organization Method for Enrichment Evaluation (Promethee). Rekayasa 2021, 14, 1–9. [Google Scholar] [CrossRef]
- Sarkis, J. Supply chain sustainability: Learning from the COVID-19 pandemic. Int. J. Oper. Prod. Manag. 2020, 41, 63–73. [Google Scholar] [CrossRef]
- Singh, M.; Aujla, G.S.; Bali, R.S.; Vashisht, S.; Singh, A.; Jindal, A. Blockchain-enabled secure communication for drone delivery: A case study in COVID-like scenarios. In Proceedings of the 2nd ACM MobiCom Workshop on Drone Assisted Wireless Communications for 5G and beyond, London, UK, 25 September 2020; pp. 25–30. [Google Scholar]
- Siriwardhana, Y.; De Alwis, C.; Gür, G.; Ylianttila, M.; Liyanage, M. The fight against the COVID-19 pandemic with 5G technologies. IEEE Eng. Manag. Rev. 2020, 48, 72–84. [Google Scholar] [CrossRef]
- Kumar, M.S.; Raut, R.D.; Narwane, V.S.; Narkhede, B.E. Applications of industry 4.0 to overcome the COVID-19 operational challenges. Diabetes Metab. Syndr. Clin. Res. Rev. 2020, 14, 1283–1289. [Google Scholar] [CrossRef] [PubMed]
- Nandi, S.; Sarkis, J.; Hervani, A.A.; Helms, M.M. Redesigning supply chains using blockchain-enabled circular economy and COVID-19 experiences. Sustain. Prod. Consum. 2021, 27, 10–22. [Google Scholar] [CrossRef]
- Oltra-Badenes, R.; Gil-Gomez, H.; Guerola-Navarro, V.; Vicedo, P. Is It Possible to Manage the Product Recovery Processes in an ERP? Analysis of Functional Needs. Sustainability 2019, 11, 4380. [Google Scholar] [CrossRef] [Green Version]

| Account | Address |
|---|---|
| M | 0x7881A5C6014bC25C43458f41eBFD16249c87BdB9 |
| R | 0xc9e13c75d044B1F4b0bCDeB7a828705be5d958BD |
| L | 0xcF8d3353A98140bf3A5e9E722C9eCCa1B01e4682 |
| m | 0x1D697fd294CAbE52396aD0afbF2dAcBfb3234Ad5 |
| C | 0x6B0614189C986e39298590E0eAF31707371d54ab |
| r | 0x456Fb86e15AF1a226fAF106bF6716Af80F585336 |
| Function Name | Transaction Cost | Execution Cost | USD |
|---|---|---|---|
| activate() | 47,675 | 24,227 | 0.0114 |
| notify() | 26,293 | 4638 | 0.0063 |
| quotedprice() | 27,332 | 5478 | 0.0065 |
| charge() | 163,627 | 141,734 | 0.0390 |
| transferproductowner() | 86,875 | 98,415 | 0.0207 |
| companydecision() | 27,428 | 5237 | 0.0065 |
| argue() | 93,425 | 85,859 | 0.0223 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shih, D.-H.; Huang, F.-C.; Chieh, C.-Y.; Shih, M.-H.; Wu, T.-W. Preventing Return Fraud in Reverse Logistics—A Case Study of ESPRES Solution by Ethereum. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 2170-2191. https://doi.org/10.3390/jtaer16060121
Shih D-H, Huang F-C, Chieh C-Y, Shih M-H, Wu T-W. Preventing Return Fraud in Reverse Logistics—A Case Study of ESPRES Solution by Ethereum. Journal of Theoretical and Applied Electronic Commerce Research. 2021; 16(6):2170-2191. https://doi.org/10.3390/jtaer16060121
Chicago/Turabian StyleShih, Dong-Her, Feng-Chuan Huang, Chia-Yi Chieh, Ming-Hung Shih, and Ting-Wei Wu. 2021. "Preventing Return Fraud in Reverse Logistics—A Case Study of ESPRES Solution by Ethereum" Journal of Theoretical and Applied Electronic Commerce Research 16, no. 6: 2170-2191. https://doi.org/10.3390/jtaer16060121
APA StyleShih, D.-H., Huang, F.-C., Chieh, C.-Y., Shih, M.-H., & Wu, T.-W. (2021). Preventing Return Fraud in Reverse Logistics—A Case Study of ESPRES Solution by Ethereum. Journal of Theoretical and Applied Electronic Commerce Research, 16(6), 2170-2191. https://doi.org/10.3390/jtaer16060121







