Multiplexed Internet of Things Data Transmission and Visualization Utilizing Wireless LAN Authentication and Privacy Infrastructure Protocol in Smart Factories
Abstract
:1. Introduction
2. Related Work
2.1. Secure Communication Architectures in Industrial IoT
2.2. Multicast Communication and Network Efficiency
2.3. IoT and Edge Computing Integration
2.4. Wireless Technologies in Smart Manufacturing
2.5. Data Visualization and Middle Platforms
2.6. Comparative Insight
3. A Diversified IoT Data Transmission Based on WAPI
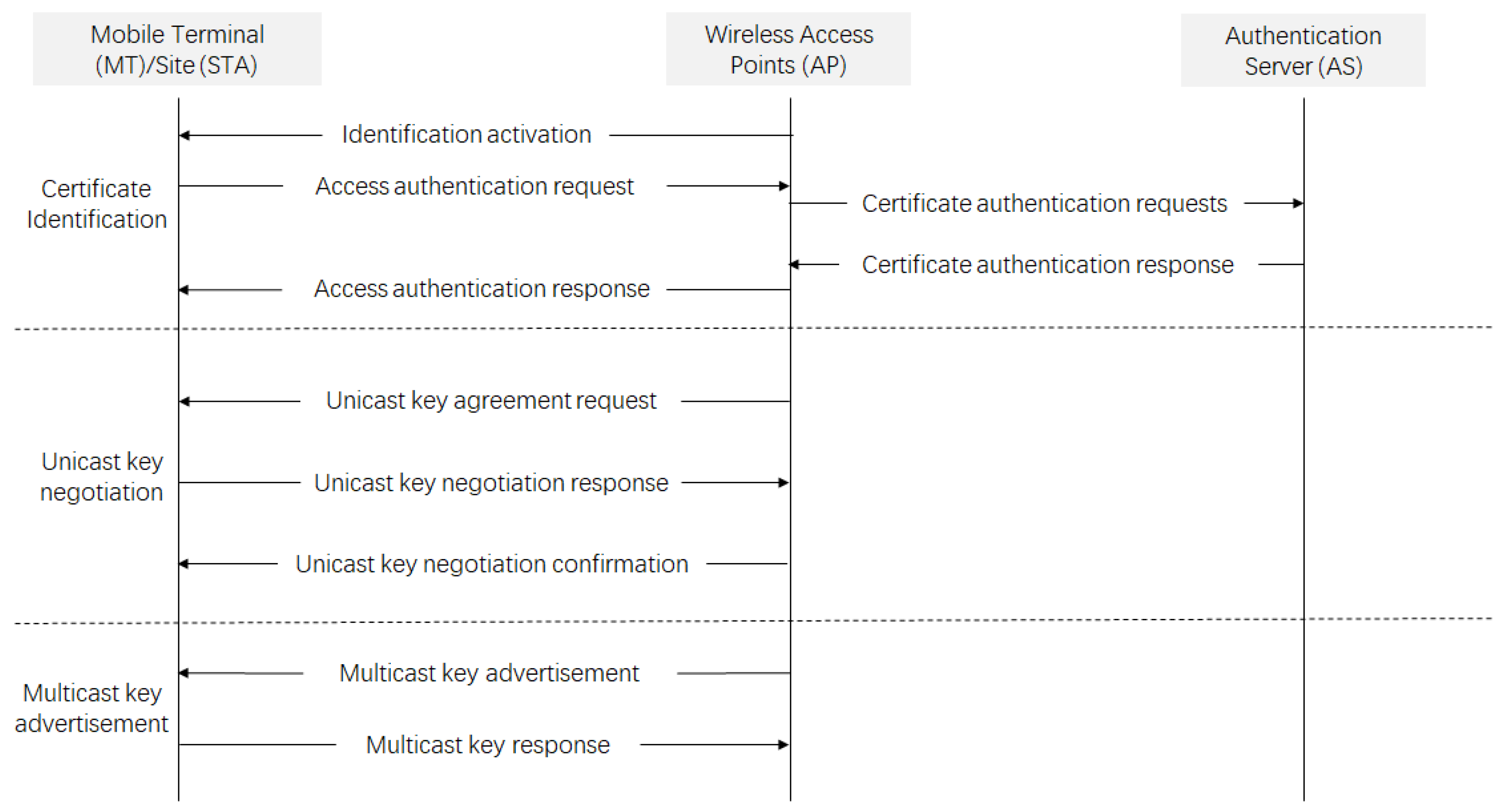
3.1. Protocol Authentication Process
- Certificate verification: This step involves mutual authentication between the terminal device (STA) and the access point (AP). Initially, an authentication request is sent by the STA to the AP, which includes its digital certificate. Upon receiving the request, a certificate validation request is forwarded by the AP to the Authentication Server (AS). The validity of the certificates from both the STA and the AP is verified by the AS. Based on the verification results, feedback is provided to the AP by the AS, which then decides whether to allow the STA to access the network.
- Unicast key negotiation: Following successful certificate verification, a unicast key is negotiated between the STA and AP. This key is critical for encrypting communication between the STA and AP, ensuring the confidentiality and integrity of the transmitted data. The unicast key is unique to each STA–AP pair, enhancing security by isolating communication sessions from one another.
- Multicast key distribution: The AP generates a multicast key and securely distributes it to authenticated devices. This key is used to encrypt broadcast and multicast data, preventing unauthorized access.
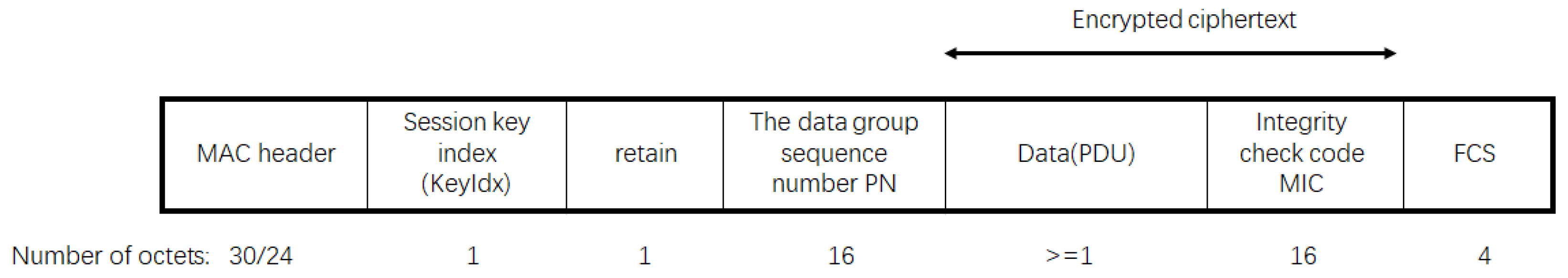
3.2. WAPI Data Packet Structure
3.3. Diversified IoT Device Terminal Access Solutions
3.3.1. Devices with Operating Systems
P12 Certificate Distribution
P10 Certificate Request Process
3.3.2. Devices Without Operating Systems
3.4. Theoretical Analysis of WAPI Protocol Security
3.4.1. Certificate Authentication and Verification
3.4.2. Unicast Key Negotiation
3.4.3. Multicast Key Distribution
3.4.4. Linking Theoretical Analysis to Implementation
4. Testing and Verification
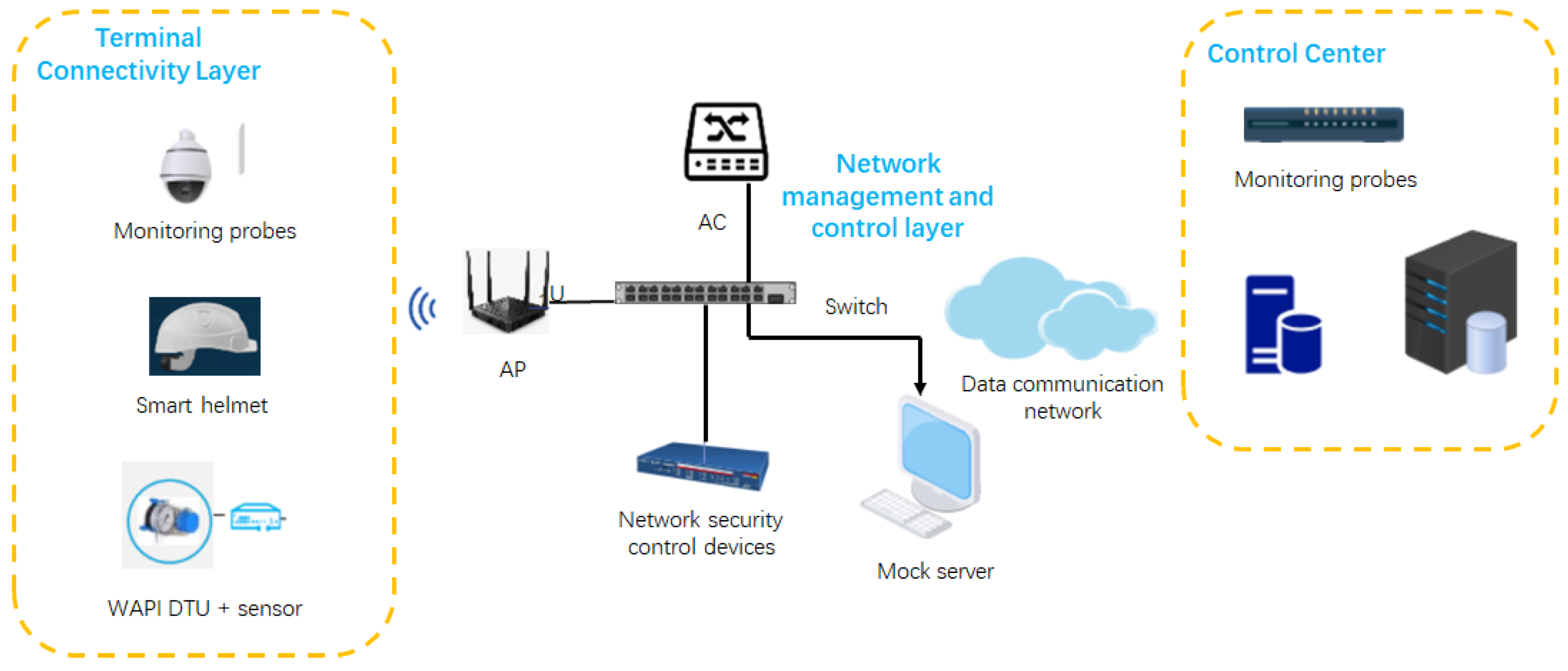
4.1. Testing Environment
4.2. Equipment Configurations
4.2.1. Network Cameras
4.2.2. Smart Helmets
4.2.3. WAPI DTU and Sensor
4.3. Testing Results
4.3.1. Signal Measurement Coverage Test
4.3.2. Throughput Testing Under Multi-Network Interference Conditions
4.3.3. Latency Testing Under Multi-Network Interference Conditions
4.3.4. WAPI Authentication Server Performance
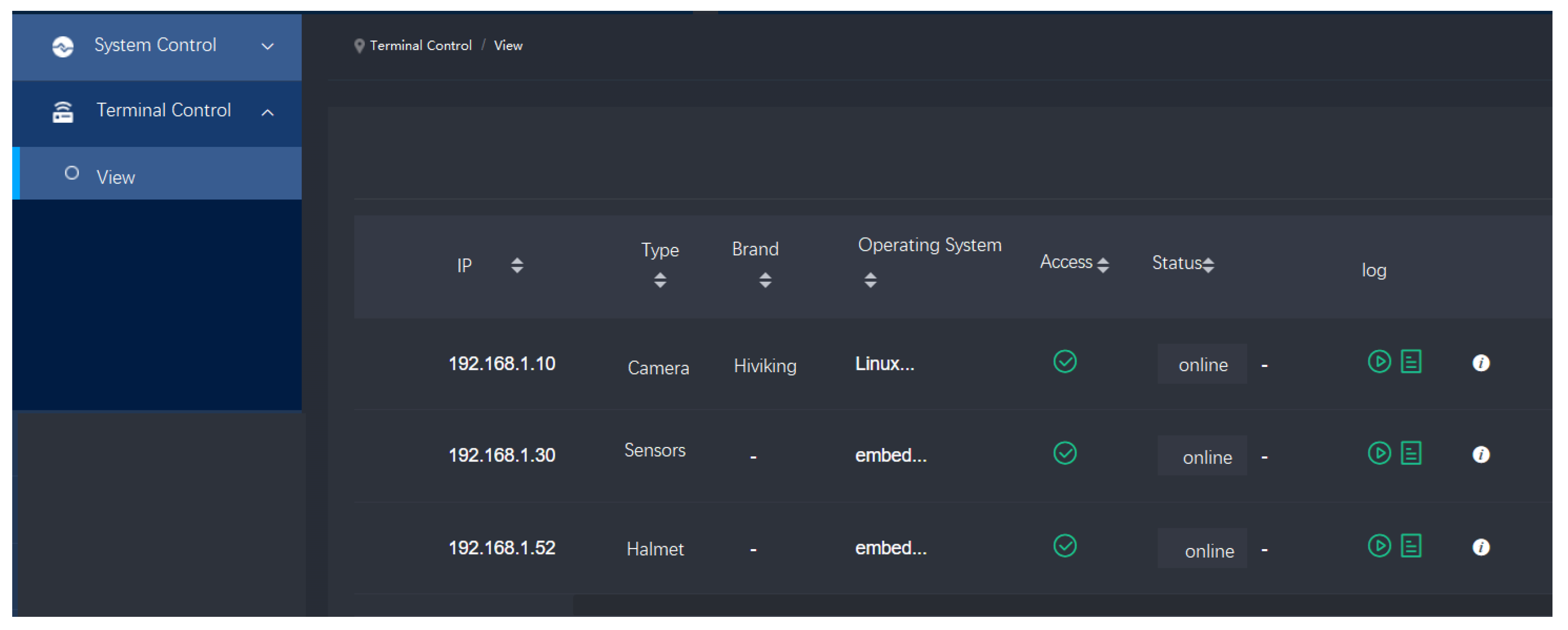
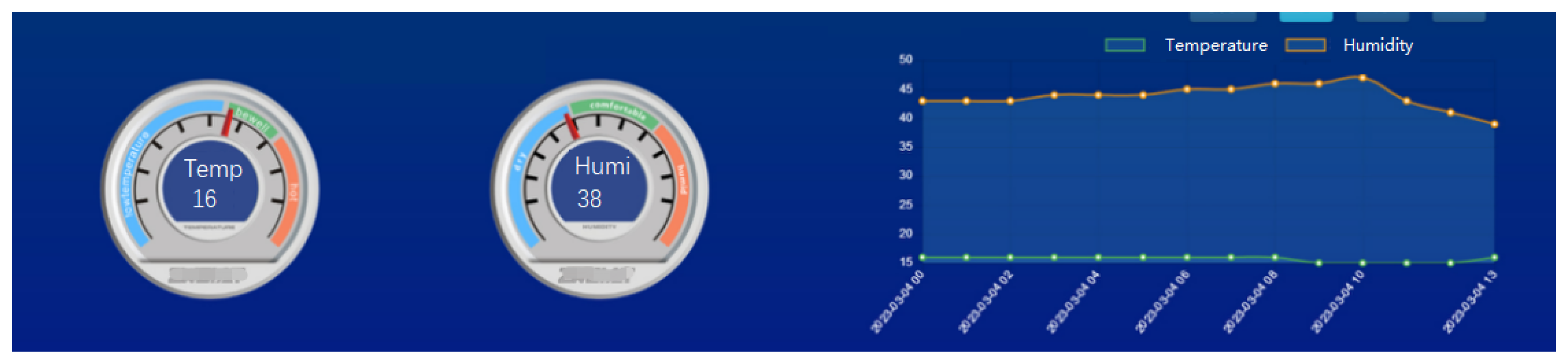
4.4. Visualization Platform for IoT Devices’ Control
4.5. Discussion
4.5.1. Security and Usability of WAPI in Smart Factories
4.5.2. Security Threat Models and WAPI Defense Capabilities
4.5.3. Support and Verification for Diverse Devices
4.5.4. Energy Efficiency Considerations
4.5.5. Intuitive and Cutting-Edge Visualization Platform
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| WAPI | Wireless LAN Authentication and Privacy Infrastructure Protocol |
| MIC | Message Integrity Code |
| STA | Terminal device |
| AP | Access point |
| AS | Authentication Server |
| CPE | Customer-Premises Equipment |
| PKI | Public Key Infrastructure |
| Modbus RTU | Modbus Remote Terminal Unit |
| MITM | Man in the middle |
| DoS | Denial of service |
| DTU | Data Transmission Unit |
References
- Ryalat, M.; ElMoaqet, H.; AlFaouri, M. Design of a smart factory based on cyber-physical systems and Internet of Things towards Industry 4.0. Appl. Sci. 2023, 13, 2156. [Google Scholar] [CrossRef]
- Wang, Y.; Wei, Z.; Bao, H.; Deng, G.; Li, J.; Li, P.; Nie, L.; Fu, H. Intelligent support and command system based on WAPI terminal equipment. J. Phys. Conf. Ser. 2021, 2113, 012054. [Google Scholar] [CrossRef]
- 29167-16:2022; Information Technology—Automatic Identification and Data Capture Techniques—Part 16: Crypto Suite ECDSA-ECDH Security Services for Air Interface Communications. ISO/IEC: Geneva, Switzerland, 2022.
- Mansour, M.; Gamal, A.; Ahmed, A.I.; Said, L.A.; Elbaz, A.; Herencsar, N.; Soltan, A. Internet of Things: A Comprehensive Overview on Protocols, Architectures, Technologies, Simulation Tools, and Future Directions. Energies 2023, 16, 3465. [Google Scholar] [CrossRef]
- Li, K.; Liu, J. A security protocol of RFID communication system based on password authenticated with provable security. Int. J. Auton. Adapt. Commun. Syst. 2021, 14, 64–82. [Google Scholar] [CrossRef]
- Priyanka, E.B.; Maheswari, C.; Thangavel, S. A smart-integrated IoT module for intelligent transportation in oil industry. Int. J. Numer. Model. Electron. Netw. Devices Fields 2021, 34, e2731. [Google Scholar] [CrossRef]
- Fan, C.; Qian, J.; Du, M.; Wang, X.; Xiang, X. Design and Implementation of Security Enhancement Mechanism for Smart Distribution Transformer Combine Terminal Based on WAPI. In Proceedings of the 2023 IEEE International Conferences on Internet of Things (iThings), Green Computing & Communications (GreenCom), Cyber, Physical & Social Computing (CPSCom), Smart Data (SmartData), and Congress on Cybermatics (Cybermatics), Danzhou, China, 17–21 December 2023; pp. 166–171. [Google Scholar]
- Kumar, V.; Pal, O.; Thakur, V.; Kumar, K. SCGKM: A secure and cost-effective group key management scheme for multicast communication in large dynamic groups. Int. J. Inf. Technol. 2022, 14, 781–788. [Google Scholar] [CrossRef]
- Mustafa, R.; Sarkar, N.I.; Mohaghegh, M.; Pervez, S. A Cross-Layer Secure and Energy-Efficient Framework for the Internet of Things: A Comprehensive Survey. Sensors 2024, 24, 7209. [Google Scholar] [CrossRef] [PubMed]
- Li, J.; Wang, R.; Wang, K. Service Function Chaining in Industrial Internet of Things with Edge Intelligence: A Natural Actor-Critic Approach. IEEE Trans. Ind. Inform. 2022, 19, 491–502. [Google Scholar] [CrossRef]
- Noor-A-Rahim, M.; John, J.; Firyaguna, F.; Sherazi, H.H.R.; Kushch, S.; Vijayan, A.; O’Connell, E.; Pesch, D.; O’Flynn, B.; O’Brien, W. Wireless Communications for Smart Manufacturing and Industrial IoT: Existing Technologies, 5G and Beyond. Sensors 2023, 23, 73. [Google Scholar] [CrossRef] [PubMed]
- Seferagić, A.; Famaey, J.; De Poorter, E.; Hoebeke, J. Survey on Wireless Technology Trade-offs for the Industrial Internet of Things. Sensors 2020, 20, 488. [Google Scholar] [CrossRef] [PubMed]
- Xiao, Y.; Fei, Z.; Zheng, K.; Zhang, T.; Qian, B.; Zheng, W. A Survey of Power Grid Operation State Visualization. J. Comput.-Aided Des. Comput. Graph. 2019, 31, 1750–1758. [Google Scholar]
- Yang, Q.; Cai, Y.; Shen, L.; Chen, X.; Lan, L.; Jiang, X. Research on Data Management of Power Grid Enterprises Based on Data Middle Platform. Earth Environ. Sci. 2021, 714, 042012. [Google Scholar] [CrossRef]
- WAPI Test Laboratory, WAPI Alliance (Wireless Network Security Industry Alliance of Zhongguancun). Authentication Server Authentication and Privacy Infrastructure (WAPI) Test Report [TH-AS2001]; WAPI Alliance: Beijing, China, 2024. [Google Scholar]



| Device Name | Quantity | Power Supply | Remarks |
|---|---|---|---|
| WAPI AS | 1 | AC 220 V | Core WAPI AS node |
| WAPI AP | 5 | DC 12 V | WAPI wireless access |
| Secure Gateway | 1 | AC 220 V | Edge protection |
| Hikvision Camera | 8 | DC 12 V | Video surveillance |
| Smart helmets | 10 | Battery/DC | Worker location |
| WAPI sensor | 12 | DC 12 V | Industrial data upload |
| Test Point | WAPI-2.4G (Mbps) | WAPI-5G (Mbps) |
|---|---|---|
| 1 | 25.8 | 219 |
| 2 | 28.9 | 247 |
| 3 | 16.7 | 215 |
| 4 | 27.6 | 230 |
| 5 | 24.7 | 230 |
| 6 | 20.0 | 236 |
| Test Point | WAPI-2.4G (Mbps) | WAPI-5G (Mbps) |
|---|---|---|
| 1 | 16.3 | 174.9 |
| 2 | 18.8 | 206.8 |
| 3 | 18.2 | 154 |
| 4 | 19.5 | 189 |
| 5 | 16.7 | 178 |
| 6 | 20.0 | 192 |
| Test Point | WAPI-2.4G (ms) | WAPI-5G (ms) |
|---|---|---|
| 1 | 3.37 | 3.48 |
| 2 | 3.37 | 3.56 |
| 3 | 3.36 | 3.48 |
| 4 | 3.71 | 3.34 |
| 5 | 3.38 | 3.78 |
| 6 | 3.69 | 3.25 |
| Reference Section | Test Item | Result |
|---|---|---|
| 7.3.3.1 X.509 V3 Certificate Management Test | X.509 v3 Certificate Management Test | passed |
| 7.3.2 WAPI Port Number Test | Certificate Authentication and Key Management | passed |
| 7.3.3.2 X.509 Protocol Process | Certificate Authentication and Key Management | passed |
| 7.3.3.4 MAC Address Binding | MAC Address Binding Function Test | passed |
| 7.3.3.7 Roaming Test | Certificate Authentication (Access Point AS roaming) | passed |
| 7.3.4 WAPI Protocol Integrity | WAPI Subtype field in Auth Request WAPI Version field in Auth Request WAI Type field in Auth Request | passed |
| 6.5.1 Authentication Performance Testing | Certificate authentication performance test | 377/S |
| Feature | WAPI | WPA3 |
|---|---|---|
| Authentication | Certificate-based (PKI) | Password-based (SAE) |
| Encryption algorithm | ECC, SM4, AES | AES-GCMP |
| Regulatory origin | Chinese National Standard | IEEE Standard |
| Offline/local CA support | Supported | Not supported |
| Mutual authentication | Mandatory | Optional |
| Industrial adaptation | Smart grids, power systems | Public Wi-Fi, consumer devices |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, P.; Yang, Y.; Zheng, Y.; Sun, Y. Multiplexed Internet of Things Data Transmission and Visualization Utilizing Wireless LAN Authentication and Privacy Infrastructure Protocol in Smart Factories. Sensors 2025, 25, 3134. https://doi.org/10.3390/s25103134
Zhang P, Yang Y, Zheng Y, Sun Y. Multiplexed Internet of Things Data Transmission and Visualization Utilizing Wireless LAN Authentication and Privacy Infrastructure Protocol in Smart Factories. Sensors. 2025; 25(10):3134. https://doi.org/10.3390/s25103134
Chicago/Turabian StyleZhang, Peng, Yanhong Yang, Yili Zheng, and Yizhen Sun. 2025. "Multiplexed Internet of Things Data Transmission and Visualization Utilizing Wireless LAN Authentication and Privacy Infrastructure Protocol in Smart Factories" Sensors 25, no. 10: 3134. https://doi.org/10.3390/s25103134
APA StyleZhang, P., Yang, Y., Zheng, Y., & Sun, Y. (2025). Multiplexed Internet of Things Data Transmission and Visualization Utilizing Wireless LAN Authentication and Privacy Infrastructure Protocol in Smart Factories. Sensors, 25(10), 3134. https://doi.org/10.3390/s25103134






