Intrusion Detection in Internet of Things Systems: A Review on Design Approaches Leveraging Multi-Access Edge Computing, Machine Learning, and Datasets
Abstract
:1. Introduction
1.1. IoT Network Intrusion Detection Systems
1.2. Motivation and Contribution
- We examine some of the leading IoT challenges presented in the recent research trends. Moreover, we analyze the feasibility of emerging technologies such as MEC to design security applications for the IoT.
- We investigate the ML-based NIDS designed for IoT and their implementation strategies.
- We examine the placement strategies used in MEC to develop NIDS for the IoT systems.
- We review various datasets and metrics used to develop NIDS for IoT systems.
- We propose a security framework for the resource-constrained IoT systems by utilizing the modern MEC architecture.
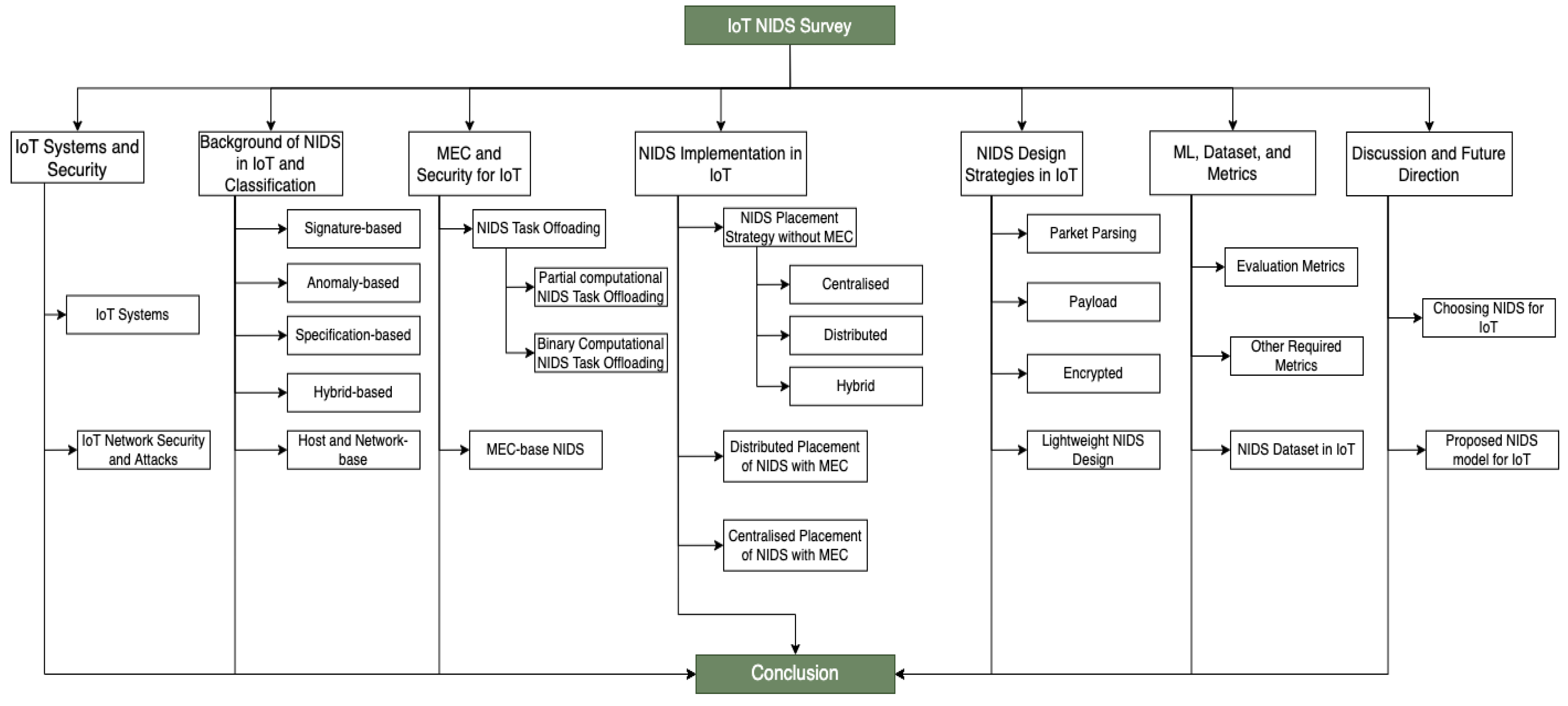
1.3. Paper Outlines
2. IoT System and Security Issues
2.1. IoT System
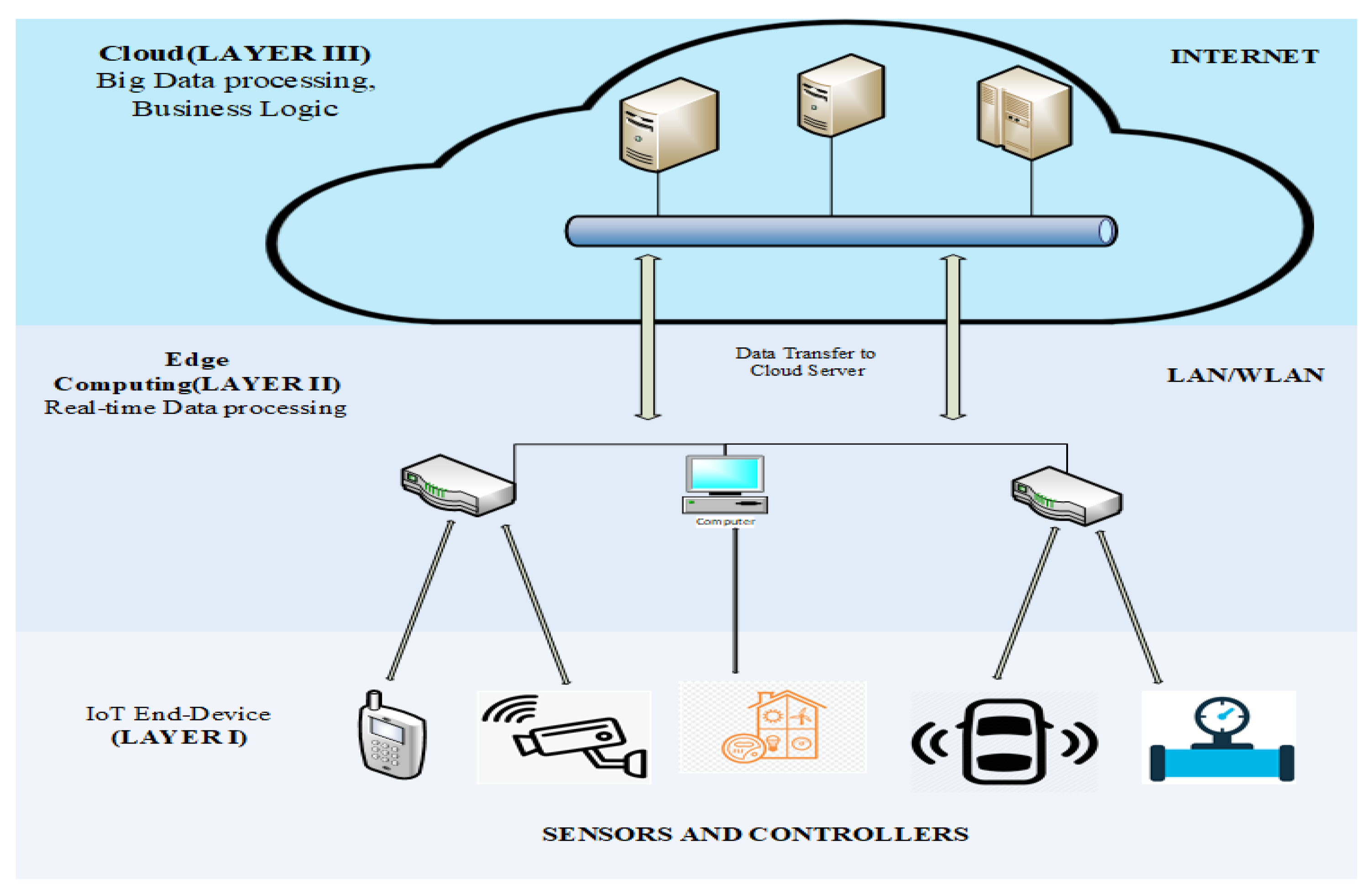
2.2. IoT-MEC Architecture
2.2.1. Sensor Level (IoT End-Device)
2.2.2. MEC/Fog
2.2.3. Cloud
2.3. IoT Network Security and Attacks
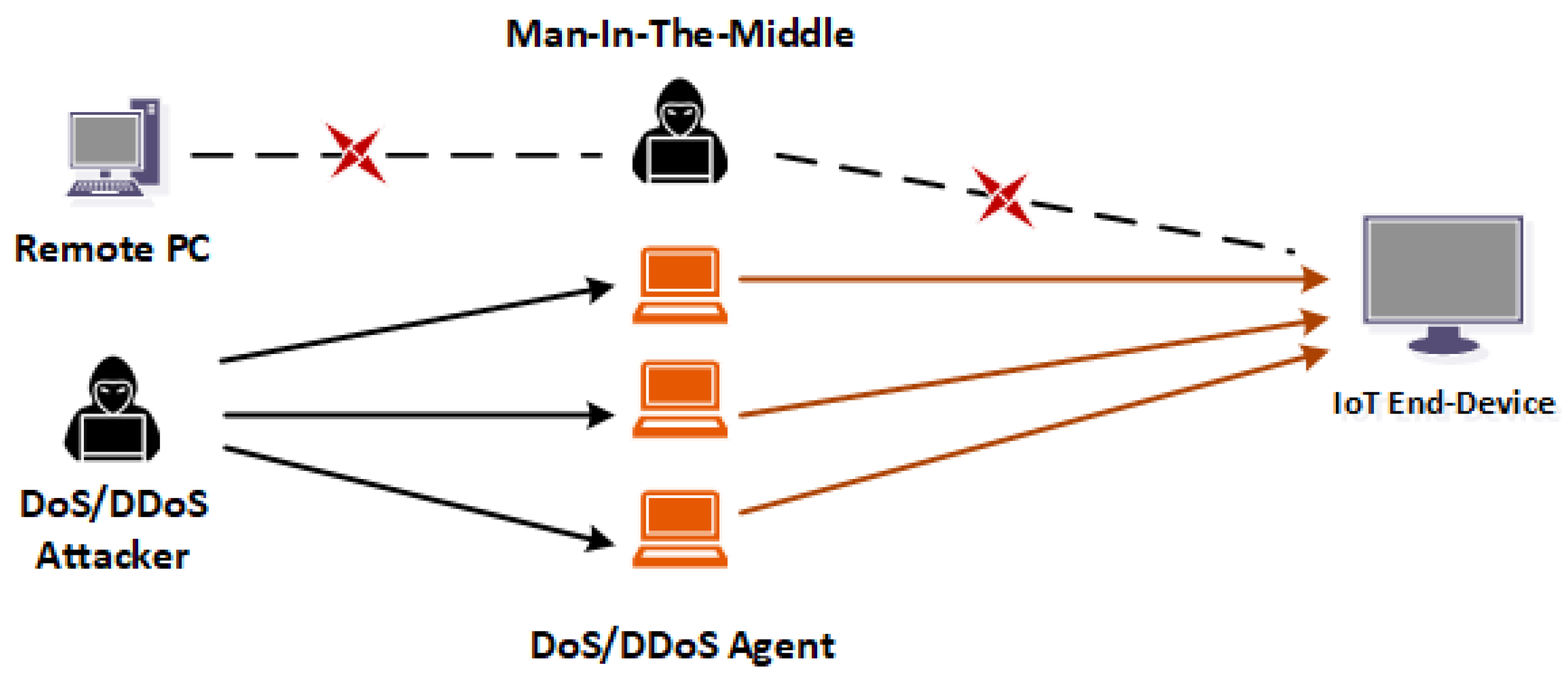
- A distributed denial-of-service (DDoS): The attack is a malicious network attack that can disrupt the regular traffic and the network’s services. DDoS floods the target or surrounding infrastructure with highly intense network traffic [44]. DDoS attacks become successful when attackers apply multiple compromised computing systems as the sources to generate a large amount of network traffic. The targets can be either the IoT system or other networked devices [45,46].
- Privacy leakage: Data protection and privacy should be a priority in IoT system communication. Most IoT system manufacturers and users pay minimal attention to the contents of information stored on their devices and how third-party companies analyze and process such IoT privacy information. IoT systems such as wearable devices that collect user’s information about their location, situation, and health information have contributed immensely to the high rise in the risk of personal privacy leakage [51,52].
- Marai Botnet Attack: Mirai is malware that turns networked devices into remotely controlled bots that cyber-attackers use as part of a botnet in a large-scale network. It primarily targets online consumer devices such as IP cameras and home routers. Attacks such as DoS/DDoS also used Mirai as a prevalent initiator [53,54].
- Sybil Attack: Sybil attacks are found in peer-to-peer networks. A Sybil attack subverts the IoT device’s identity to create many anonymous identities and consume a disproportionate power. It is named after Sybil, the author of the book Sybil, which is a case study of a woman dealing with a dissociative identity disorder. An IoT device in a network that operates multiple identities often undermines the authorized network access in reputation systems [55,56]. Sybil attacks capitalize on this weakness in the IoT system network to initial attacks.
- AI-Based Attacks: AI attacks have been around since 2007 [57,58], and the high threats they pose to the IoT are becoming more prevalent. Hackers now create AI-powered tools that are quicker, simpler to scale, and more efficient than human-centric attacks. This is a significant danger to the IoT ecosystem. While the techniques and features of conventional IoT risks offered by cybercriminals may appear to be the same, the scale, automation, and customisation of AI-powered attacks will make them increasingly difficult to eradicate.
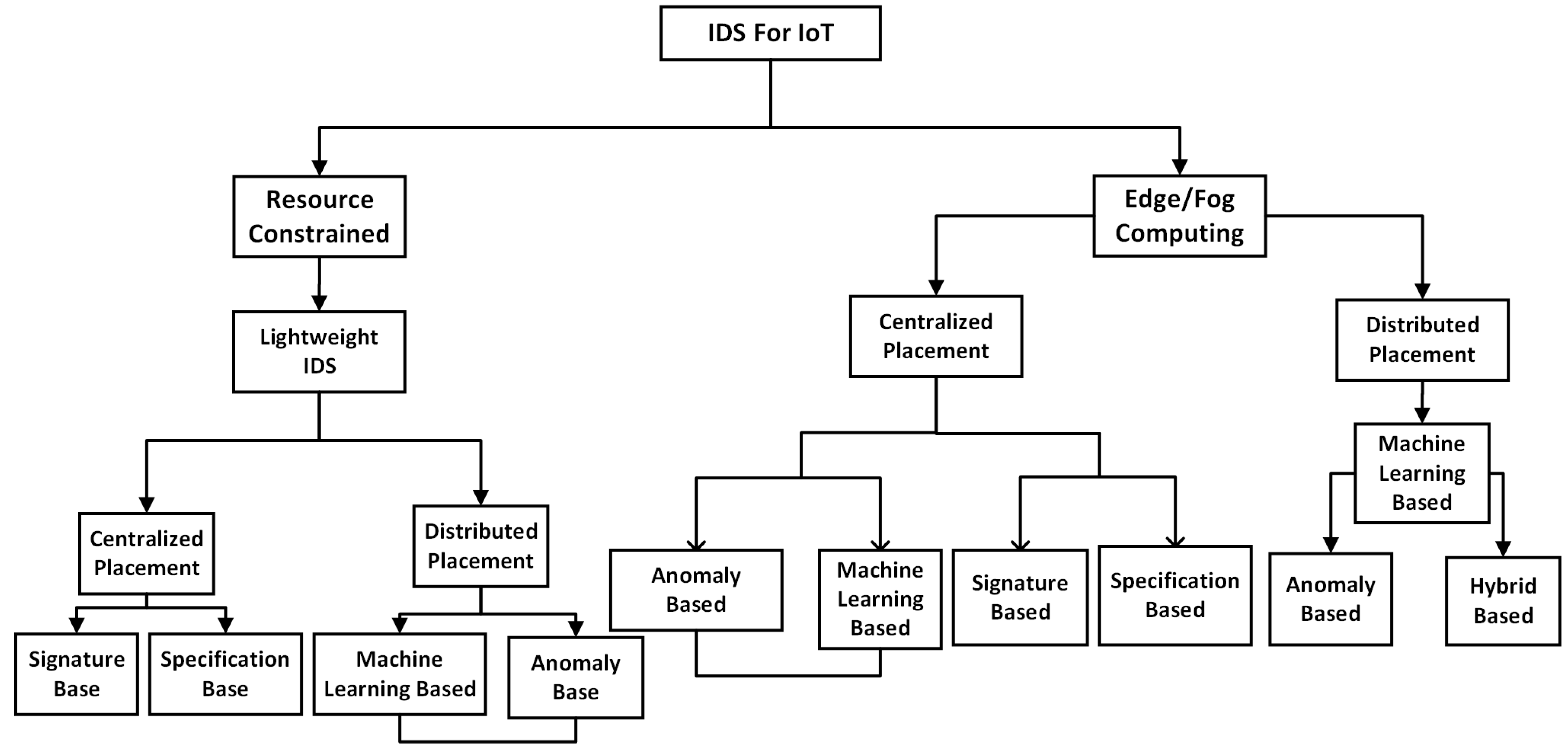
3. Background of NIDS in IoT and Their Classification
3.1. Signature-Based NIDS in IoT Systems
3.2. Anomaly-Based NIDS for IoT Systems
3.3. Specification-Based NIDS for IoT Systems
3.4. Hybrid-Based NIDS for IoT Systems
- Sequence-based: either anomaly or misuse detection is applied first, and a different technique is applied next.
- Parallel-based: multiple detectors are concurrently applied, and the final decision is made based on multiple output sources.
3.5. Host and Network-Based NIDS for IoT Systems
4. Multi-Access Edge Computing as a Resource to Provide Security for IoT
- Providing security context-awareness (the capability of the MEC server to disseminate real-time security information to the IoT device) [103];
- Energy-saving during and after data transfer;
- Improvement of privacy/security in IoT (users are deprived of the total ownership of their data in cloud computing, which results in private data leakage and loss) [104];
- Optimal resource allocation by the MEC for the IoT system [105].
4.1. NIDS Task Offloading in IoT-MEC Environment
4.1.1. Partial Computational NIDS Task Offloading
- First, the sequence of execution functions or routines cannot be discretionarily selected because the outputs of some components of the NIDS model are the inputs of others.
- Second, due to resource constraints and security considerations, some algorithms or routines of the NIDS must be offloaded to the MEC for execution, while others have to be executed locally.
4.1.2. Binary NIDS Task Offloading
4.2. MEC-Based NIDS Design for IoT Systems
5. Mode of NIDS Implementation in IoT Systems
5.1. IoT NIDS Based on Placement Strategies without MEC
- Physical domain: interfaces the sensors to the IoT board.
- Network domain: gives the IoT device the capabilities to transfer data.
- Application domain: gives the user power to interact with the IoT device.
5.1.1. Centralized Placement
5.1.2. Distributed Placement
5.1.3. Hybrid Placement
5.2. Distributed Placement Strategies of NIDS in IoT with MEC
5.3. Centralized NIDS Placement Strategies Based on IoT with MEC
| Reference | Detection Methods | Threats Identified | Placement Strategies |
|---|---|---|---|
| Thanigaivelan et al. [118] | Network fingerprinting | Network Anomalies | Distributed locally in the IoT Devices |
| Ferdowsi and W. Saad [119] | Artificial Neural Network (ANN) | Data Intrusion | Distributed locally in the IoT Devices |
| R. Chen, C. M. Liu, and C. Chen [148] | Artificial Immune-Base (ANN) | Network Intrusion | Distributed locally in the IoT Devices |
| Wang et al. [117] | ZeroR, KNN, SVM, NaiveBayes, Neural Network | Network Intrusion | Distributed with MEC |
| Hosseinpour et al. [141] | Negative selection algorithm | Network Intrusion (DoS/DDoS) | Distributed with cloud, Fog, and MEC |
| D. A. Abeshu and C. Naveen [149] | Stacked Autoencoder Deep Learning | Network Intrusion Attacks | Distributed with MEC |
| A. Abeshu and C. Naveen [150] | Multi-Layer Deep Network | Network Intrusion Attacks | Distributed Locally and Fog |
| Diro Abebe and Chilamkurti Naveen [151] | LSTM Deep Learning | Network Intrusion Attacks | Distributed Locally and Fog |
| A. S. Sohal et al. [152] | Markov Model and Virtual Honeypot Device | Network Intrusion Attacks | Distributed with Fog to MEC |
| J. Stolfo et al. [153] | Offensive Decoy technology | Cloud Data attacks | Distributed with cloud and Fog |
| B. K. Sudqi et al. [154] | Multilayer Perceptron (MLP) | Network Intrusion Attacks | Centralized on Fog |
| Sheikhan Mansour and Bostani Hamid [140] | MapReduce approach | anomaly-based and misuse-based attacks | Distributed locally on IoT |
| Gajewski M et al. [142] | Co-responsible distributed NIDS | Network Intrusion Attacks | Distributed between IoT and ISP’s Server |
| Xingshuo et al. [155] | Sample extreme learning Machine | Network Intrusion Attacks | Distributed between IoT, MEC, and Fog |
6. NIDS Design Strategies for IoT Systems
6.1. Packet Parsing-Based NIDS Design for IoT
- Packets consist of communication contents and can effectively be employed to detect U2L and R2L attacks.
- Packets contain TCP/IP data content and timestamps that precisely provide the NIDS information about attack sources.
- Packets analysis promote real-time data processing without content caching within the IoTs’ network.
6.2. Payload Analysis-Based NIDS Design for IoT
6.3. Encrypted Traffic Analysis-Based NIDS Design for IoT
6.4. Lightweight NIDS Design in IoT Systems
- Applying new protocols to decrease the number of computational operations required by a traditional NIDS;
- Utilizing optimization techniques to design a security system such that the scalar multiplication, addition, and doubling are reduced.
- Offloading of all or parts of the computationally intensive algorithms to a proximal device (MEC platform) in the same network that has more resources than the IoT device;
- Using modern algorithms that require less computational resources instead of the use of classical, alternative methods;
- Utilizing data feature dimensionality reduction. Different algorithms such as sparse auto-encoder, the Ranker method, principal component analysis (PCA), etc., are used by researchers to reduce the dimension of the dataset to lightweight ML-based NIDS for IoT devices.
7. Machine Learning, Dataset, and Metrics for IoT Systems NIDS
7.1. Evaluation Metrics for NIDS in IoT
- Compare two or more NIDS on a similar scale.
- Evaluate the required performances.
- Determine the best configuration of the NIDS.
7.1.1. Performance and Evaluation Metrics Used in ML-Based NIDS for IoT Systems
7.1.2. Other Required Metrics
7.2. Datasets Used in IoT Systems NIDS Design
| Dataset Description | Telemetry | Attack Types | Year Created |
|---|---|---|---|
| NSL-KDD [217] | General Purpose | 2009 | |
| UNB-ISCX 2012 [199] | General Purpose | DoS, DDoS, Brute Force, XSS, SQL Injection, Infiltration, Portscan, and Botnet | 2012 |
| [203,204] | General Purpose | Analysis, Backdoor, DoS, Exploit, Fizzers, Generic, Reconnaissance, Shellcode, and Worm | 2015 |
| CICIDS2017 [200] | General Purpose | DoS, DDoS, Brute Force, XSS, SQL Injection, Infiltration, Portscan, and Botnet | 2017 |
| AWS(CSE-CIC-IDS2018) [201] | General Purpose | DoS, DDoS, Brute Force, XSS, SQL Injection, Infiltration, Portscan, and Botnet | 2018 |
| IoT Network Intrusion Dataset [205] | IoT | Benign, mitm-arpspoofing, DoS-synflooding, scan-hostport, scan-portos, mirai-udpflooding, mirai-ackflooding, mirai-httpflooding, mirai-hostbruteforce | 2019 |
| IoTID20 Dataset [206] | IoT | DoS/DDoS attacks | 2020 |
| TON_IoT Dataset [207] | IoT, IIoT, MEC, Fog | DoS, DDoS and ransomware | 2019 |
| OPCUA dataset [208] | IoT | DoS, Eavesdropping, Man-in-the-middle, Impersonation, Spoofing attacks | 2020 |
| IOT DOS AND DDOS ATTACK DATASET [209,210,211,218] | IoT | DoS and DDoS attacks | 2021 |
| IOT HEALTHCARE SECURITY DATASET [219] | IoT, SDN, IIoT | Normal and IoT attack traffic | 2021 |
| Mqtt-iot-ids2020 DATASET [213] | IoI, IIoT | Normal operation, aggressive scan, UDP scan, Sparta SSH brute-force, and MQTT brute-force attack. | 2020 |
| Edge-IIoTset DATASET [214] | IoT, IIoT, MEC | DoS/DDoS attacks, Information gathering, Man in the middle attacks, Injection attacks, and Malware attacks | 2022 |
| NSS MIRAI DATASET [220] | IoT | Mirai type botnet attack | 2020 |
| WUSTL-IIOT-2021 [221] | IoT | Command Injection, DoS, Reconnaissance, Backdoor | 2021 |
| IOT-BDA BOTNET ANALYSIS DATASET [216] | IoT | Port scanning, exploitation, C2 communications and DDoS | 2021 |
| THE BOT-IOT DATASET [222] | IoT | DDoS, DoS, OS and Service Scan, Keylogging and Data exfiltration attacks | 2019 |
| X-IIoTID dataset [215] | IoT, IIoT | Brute force attack, dictionary attack, and the malicious insider, reverse shell and Man-in-the-Middle | 2021 |
8. Discussion and Future Trends
8.1. Choosing NIDS for IoT Systems
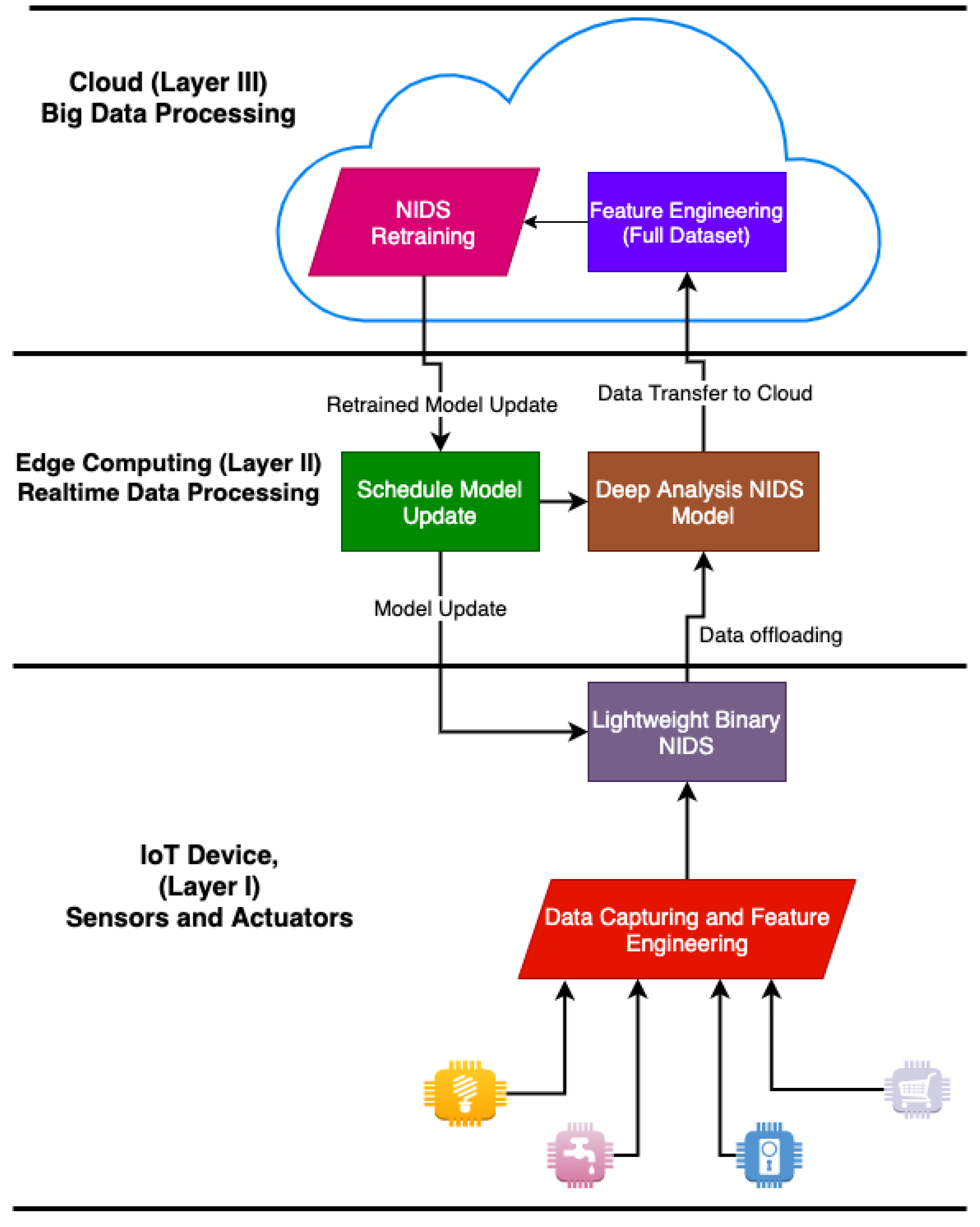
8.2. Proposed NIDS Model for IoT Systems
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Li, H.; Ota, K.; Dong, M. Learning IoT in edge: Deep learning for the Internet of Things with edge computing. IEEE Netw. 2018, 32, 96–101. [Google Scholar] [CrossRef] [Green Version]
- Stoyanova, M.; Nikoloudakis, Y.; Panagiotakis, S.; Pallis, E.; Markakis, E.K. A survey on the internet of things (IoT) forensics: Challenges, approaches, and open issues. IEEE Commun. Surv. Tutor. 2020, 22, 1191–1221. [Google Scholar] [CrossRef]
- Yastrebova, A.; Kirichek, R.; Koucheryavy, Y.; Borodin, A.; Koucheryavy, A. Future networks 2030: Architecture & requirements. In Proceedings of the 2018 10th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT), Moscow, Russia, 5–9 November 2018; pp. 1–8. [Google Scholar]
- Jurcut, A.; Niculcea, T.; Ranaweera, P.; Le-Khac, N.A. Security considerations for Internet of Things: A survey. SN Comput. Sci. 2020, 1, 1–19. [Google Scholar] [CrossRef]
- Shi, W.; Dustdar, S. The promise of edge computing. Computer 2016, 49, 78–81. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.D.; Liyanage, M. Survey on multi-access edge computing security and privacy. IEEE Commun. Surv. Tutor. 2021, 23, 1078–1124. [Google Scholar] [CrossRef]
- Pacheco, J.; Hariri, S. IoT security framework for smart cyber infrastructures. In Proceedings of the 2016 IEEE 1st International Workshops on Foundations and Applications of Self* Systems (FAS* W), Augsburg, Germany, 12–16 September 2016; pp. 242–247. [Google Scholar]
- Borhani, M.; Liyanage, M.; Sodhro, A.H.; Kumar, P.; Jurcut, A.D.; Gurtov, A. Secure and resilient communications in the industrial internet. In Guide to Disaster-Resilient Communication Networks; Springer: Berlin/Heidelberg, Germany, 2020; pp. 219–242. [Google Scholar]
- Butun, I.; Morgera, S.D.; Sankar, R. A survey of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2013, 16, 266–282. [Google Scholar] [CrossRef]
- Alrajeh, N.A.; Khan, S.; Shams, B. Intrusion detection systems in wireless sensor networks: A review. Distrib. Sens. Netw. 2013, 9, 167575. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef] [Green Version]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Sain, M.; Kang, Y.J.; Lee, H.J. Survey on security in Internet of Things: State of the art and challenges. In Proceedings of the 2017 19th International conference on advanced communication technology (ICACT), Pyeongchang, Korea, 19–22 February 2017; pp. 699–704. [Google Scholar]
- Benabdessalem, R.; Hamdi, M.; Kim, T.H. A survey on security models, techniques, and tools for the internet of things. In Proceedings of the 2014 7th International Conference on Advanced Software Engineering and Its Applications, Hainan Island, China, 20–23 December 2014; pp. 44–48. [Google Scholar]
- Jurcut, A.D.; Ranaweera, P.; Xu, L. Introduction to IoT security. In IoT Security: Advances in Authentication; John Wiley & Sons: Hoboken, NJ, USA, 2020; pp. 27–64. [Google Scholar] [CrossRef]
- Pawar, P.; Trivedi, A. Device-to-device communication based IoT system: Benefits and challenges. IETE Tech. Rev. 2019, 36, 362–374. [Google Scholar] [CrossRef]
- Ashouri, M.; Lorig, F.; Davidsson, P.; Spalazzese, R. Edge computing simulators for iot system design: An analysis of qualities and metrics. Future Internet 2019, 11, 235. [Google Scholar] [CrossRef] [Green Version]
- Mahbub, M.; Gazi, M.S.A.; Provar, S.A.A.; Islam, M.S. Multi-Access Edge Computing-Aware Internet of Things: MEC-IoT. In Proceedings of the 2020 Emerging Technology in Computing, Communication and Electronics (ETCCE), London, UK, 19–20 August 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Xu, L.; Jurcut, A.D.; Ahmadi, H. Emerging Challenges and Requirements for internet of things in 5G. In 5G Enabled Internet Things; CRC Press: Boca Raton, FL, USA, 2019; pp. 29–48. [Google Scholar]
- Said, O.; Tolba, A. Accurate performance prediction of IoT communication systems for smart cities: An efficient deep learning based solution. Sustain. Cities Soc. 2021, 69, 102830. [Google Scholar] [CrossRef]
- Catarinucci, L.; De Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stefanizzi, M.L.; Tarricone, L. An IoT-aware architecture for smart healthcare systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Almotiri, S.H.; Khan, M.A.; Alghamdi, M.A. Mobile health (m-health) system in the context of IoT. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Vienna, Austria, 22–24 August 2016; pp. 39–42. [Google Scholar]
- Khoi, N.M.; Saguna, S.; Mitra, K.; Ahlund, C. Irehmo: An efficient iot-based remote health monitoring system for smart regions. In Proceedings of the 2015 17th International Conference on E-health Networking, Application and Services (HealthCom), Boston, MA, USA, 14–17 October 2015; pp. 563–568. [Google Scholar]
- Coelho, C.; Coelho, D.; Wolf, M. An IoT smart home architecture for long-term care of people with special needs. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 626–627. [Google Scholar]
- Wang, S.; Hou, Y.; Gao, F.; Ji, X. A novel IoT access architecture for vehicle monitoring system. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016; pp. 639–642. [Google Scholar]
- Wang, S.; Hou, Y.; Gao, F.; Ma, S. A novel clock synchronization architecture for IoT access system. In Proceedings of the 2016 2nd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 14–17 October 2016; pp. 1456–1459. [Google Scholar]
- Shang, W.; Yu, Y.; Droms, R.; Zhang, L. Challenges in IoT Networking via TCP/IP Architecture; Technical Report; NDN-0038; NDN Project; Named Data Networking. 2016. Available online: https://named-data.net/wp-content/uploads/2016/02/ndn-0038-1-challenges-iot.pdf (accessed on 17 March 2022).
- Alkhabbas, F.; Spalazzese, R.; Davidsson, P. Architecting emergent configurations in the internet of things. In Proceedings of the 2017 IEEE International Conference on Software Architecture (ICSA), Gothenburg, Sweden, 3–7 April 2017; pp. 221–224. [Google Scholar]
- Park, S.; Crespi, N.; Park, H.; Kim, S.H. IoT routing architecture with autonomous systems of things. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 442–445. [Google Scholar]
- Amadeo, M.; Campolo, C.; Iera, A.; Molinaro, A. Named data networking for IoT: An architectural perspective. In Proceedings of the 2014 European Conference on Networks and Communications (EuCNC), Bologna, Italy, 23–26 June 2014; pp. 1–5. [Google Scholar]
- Ikram, M.A.; Alshehri, M.D.; Hussain, F.K. Architecture of an IoT-based system for football supervision (IoT Football). In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 69–74. [Google Scholar]
- Lyu, X.; Tian, H.; Jiang, L.; Vinel, A.; Maharjan, S.; Gjessing, S.; Zhang, Y. Selective offloading in mobile edge computing for the green Internet of Things. IEEE Netw. 2018, 32, 54–60. [Google Scholar] [CrossRef]
- Ali, B.; Gregory, M.A.; Li, S. Multi-access edge computing architecture, data security and privacy: A review. IEEE Access 2021, 9, 18706–18721. [Google Scholar] [CrossRef]
- Khan, B.U.I.; Olanrewaju, R.F.; Anwar, F.; Mir, R.N.; Najeeb, A.R. A critical insight into the effectiveness of research methods evolved to secure IoT ecosystem. Int. J. Inf. Comput. Secur. 2019, 11, 332–354. [Google Scholar] [CrossRef]
- Wang, H.; Zhang, Z.; Taleb, T. Special issue on security and privacy of IoT. World Wide Web 2018, 21, 1–6. [Google Scholar] [CrossRef] [Green Version]
- Pongle, P.; Chavan, G. A survey: Attacks on RPL and 6LoWPAN in IoT. In Proceedings of the 2015 International conference on pervasive computing (ICPC), Pune, India, 8–10 January 2015; pp. 1–6. [Google Scholar]
- Hasan, M.; Mohan, S. Protecting actuators in safety-critical IoT systems from control spoofing attacks. In Proceedings of the 2nd International ACM Workshop on Security and Privacy for the Internet-of-Things, Xi’an, China, 30 May 2019; pp. 8–14. [Google Scholar]
- Javed, A.; Malik, K.M.; Irtaza, A.; Malik, H. Towards protecting cyber-physical and IoT systems from single-and multi-order voice spoofing attacks. Appl. Acoust. 2021, 183, 108283. [Google Scholar] [CrossRef]
- Aldabbas, H.; Amin, R. A novel mechanism to handle address spoofing attacks in SDN based IoT. Clust. Comput. 2021, 24, 3011–3026. [Google Scholar] [CrossRef]
- Varalakshmi, I.; Thenmozhi, M.; Sasi, R. Detection of Distributed Denial of Service Attack in an Internet of Things Environment-A Review. In Proceedings of the 2021 International Conference on System, Computation, Automation and Networking (ICSCAN), Iasi, Romania, 20–23 October 2021; pp. 1–6. [Google Scholar]
- Ferrag, M.A.; Shu, L.; Djallel, H.; Choo, K.K.R. Deep learning-based intrusion detection for distributed denial of service attack in Agriculture 4.0. Electronics 2021, 10, 1257. [Google Scholar] [CrossRef]
- Gupta, B.; Chaudhary, P.; Chang, X.; Nedjah, N. Smart defense against distributed Denial of service attack in IoT networks using supervised learning classifiers. Comput. Electr. Eng. 2022, 98, 107726. [Google Scholar] [CrossRef]
- Alyas, M.; Noor, M.I.; Hassan, H. DDOS Attack Detection Strategies in Cloud A Comparative Stud. VFAST Trans. Softw. Eng. 2017, 12, 35–42. [Google Scholar] [CrossRef] [Green Version]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Yan, Q.; Huang, W.; Luo, X.; Gong, Q.; Yu, F.R. A multi-level DDoS mitigation framework for the industrial internet of things. IEEE Commun. Mag. 2018, 56, 30–36. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Elwekeil, M.; Wang, T.; Zhang, S. A deep autoencoder trust model for mitigating jamming attack in IoT assisted by cognitive radio. IEEE Syst. J. 2021. [Google Scholar] [CrossRef]
- Kerrakchou, I.; Chadli, S.; Kharbach, A.; Saber, M. Simulation and Analysis of Jamming Attack in IoT Networks. In Proceedings of the International Conference on Digital Technologies and Applications, Moscow, Russia, 30–31 March 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 323–333. [Google Scholar]
- Salem, O.; Alsubhi, K.; Shaafi, A.; Gheryani, M.; Mehaoua, A.; Boutaba, R. Man-in-the-Middle Attack Mitigation in Internet of Medical Things. IEEE Trans. Ind. Inform. 2021, 18, 2053–2062. [Google Scholar] [CrossRef]
- Pospisil, O.; Fujdiak, R.; Mikhaylov, K.; Ruotsalainen, H.; Misurec, J. Testbed for LoRaWAN Security: Design and Validation through Man-in-the-Middle Attacks Study. Appl. Sci. 2021, 11, 7642. [Google Scholar] [CrossRef]
- Liu, J.; Sun, W. Smart attacks against intelligent wearables in people-centric internet of things. IEEE Commun. Mag. 2016, 54, 44–49. [Google Scholar] [CrossRef]
- Ziegeldorf, J.H.; Morchon, O.G.; Wehrle, K. Privacy in the Internet of Things: Threats and challenges. Secur. Commun. Netw. 2014, 7, 2728–2742. [Google Scholar] [CrossRef]
- Kambourakis, G.; Kolias, C.; Stavrou, A. The mirai botnet and the iot zombie armies. In Proceedings of the MILCOM 2017—2017 IEEE Military Communications Conference (MILCOM), Baltimore, MD, USA, 23–25 October 2017; pp. 267–272. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Shabtai, A.; Breitenbacher, D.; Elovici, Y. N-baiot—Network-based detection of iot botnet attacks using deep autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef] [Green Version]
- Rajan, A.; Jithish, J.; Sankaran, S. Sybil attack in IOT: Modelling and defenses. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Chennai, India, 3–5 August 2017; pp. 2323–2327. [Google Scholar]
- Evangelista, D.; Mezghani, F.; Nogueira, M.; Santos, A. Evaluation of Sybil attack detection approaches in the Internet of Things content dissemination. In Proceedings of the 2016 Wireless Days (WD), Toulouse, France, 23–25 March 2016; pp. 1–6. [Google Scholar]
- Li, J.; Zhao, Z.; Li, R.; Zhang, H. Ai-based two-stage intrusion detection for software defined iot networks. IEEE Internet Things J. 2018, 6, 2093–2102. [Google Scholar] [CrossRef] [Green Version]
- Falco, G.; Viswanathan, A.; Caldera, C.; Shrobe, H. A master attack methodology for an AI-based automated attack planner for smart cities. IEEE Access 2018, 6, 48360–48373. [Google Scholar] [CrossRef]
- Schneier, B. Security Risks of Embedded Systems—Schneier on Security. 2014. Available online: https://www.schneier.com/blog/archives/2014/01/security_risks_9.html (accessed on 13 May 2021).
- Vaca, F.D. An Ensemble Learning Based Multi-level Network Intrusion Detection System for Wi-Fi Dominant Networks. Ph.D. Thesis, Purdue University Graduate School, Lafayette, IN, USA, 2019. [Google Scholar]
- Abduvaliyev, A.; Pathan, A.S.K.; Zhou, J.; Roman, R.; Wong, W.C. On the vital areas of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2013, 15, 1223–1237. [Google Scholar] [CrossRef]
- Ioulianou, P.; Vasilakis, V.; Moscholios, I.; Logothetis, M. A Signature-based Intrusion Detection System for the Internet of Things. Inf. Commun. Technol. Form 2018, in press. [Google Scholar]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the 2013 IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar]
- Olsson, J. 6LoWPAN demystified. Tex. Instrum. 2014, 13, 1–13. [Google Scholar]
- Boujrad, M.; Lazaar, S.; Hassine, M. Performance Assessment of Open Source IDS for improving IoT Architecture Security implemented on WBANs. In Proceedings of the 3rd International Conference on Networking, Information Systems & Security, Msida, Malta, 15–17 December 2020; pp. 1–4. [Google Scholar]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Dubouilh, P.L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. Threat analysis of IoT networks using artificial neural network intrusion detection system. In Proceedings of the Networks, Computers and Communications (ISNCC), Marrakech, Morocco, 16–18 May 2016; pp. 1–6. [Google Scholar]
- Hanif, S.; Ilyas, T.; Zeeshan, M. Intrusion detection in IoT using artificial neural networks on UNSW-15 dataset. In Proceedings of the 2019 IEEE 16th International Conference on Smart Cities: Improving Quality of Life Using ICT & IoT and AI (HONET-ICT), Charlotte, NC, USA, 6–9 October 2019; pp. 152–156. [Google Scholar]
- Qureshi, A.U.H.; Larijani, H.; Ahmad, J.; Mtetwa, N. A heuristic intrusion detection system for Internet-of-Things (IoT). In Proceedings of the Intelligent Computing, Proceedings of the Computing Conference, London, UK, 16–17 July 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 86–98. [Google Scholar]
- Almogren, A.S. Intrusion detection in Edge-of-Things computing. J. Parallel Distrib. Comput. 2020, 137, 259–265. [Google Scholar] [CrossRef]
- Tharewal, S.; Ashfaque, M.W.; Banu, S.S.; Uma, P.; Hassen, S.M.; Shabaz, M. Intrusion detection system for industrial Internet of Things based on deep reinforcement learning. Wirel. Commun. Mob. Comput. 2022, 2022, 9023719. [Google Scholar] [CrossRef]
- Caminero, G.; Lopez-Martin, M.; Carro, B. Adversarial environment reinforcement learning algorithm for intrusion detection. Comput. Netw. 2019, 159, 96–109. [Google Scholar] [CrossRef]
- Mothukuri, V.; Khare, P.; Parizi, R.M.; Pouriyeh, S.; Dehghantanha, A.; Srivastava, G. Federated learning-based anomaly detection for IoT security attacks. IEEE Internet Things J. 2021, 9, 2545–2554. [Google Scholar] [CrossRef]
- Mehta, D.; Mady, A.E.d.; Boubekeur, M. Anomaly-Based Intrusion Detection System for Embedded Devices on Internet. In Proceedings of the Tenth International Conference on Advances in Circuits, Electronics and Micro-electronics, Venice, Italy, 16–20 September 2018. [Google Scholar]
- Canedo, J.; Skjellum, A. Using machine learning to secure IoT systems. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust, PST, Auckland, New Zealand, 12–14 December 2016; pp. 219–222. [Google Scholar] [CrossRef]
- Wu, Y.; Dai, H.N.; Tang, H. Graph neural networks for anomaly detection in industrial internet of things. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Pacheco, J.; Benitez, V.H.; Felix-Herran, L.C.; Satam, P. Artificial neural networks-based intrusion detection system for internet of things fog nodes. IEEE Access 2020, 8, 73907–73918. [Google Scholar] [CrossRef]
- Alladi, T.; Agrawal, A.; Gera, B.; Chamola, V.; Sikdar, B.; Guizani, M. Deep neural networks for securing IoT enabled vehicular ad-hoc networks. In Proceedings of the ICC 2021-IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Eskandari, M.; Janjua, Z.H.; Vecchio, M.; Antonelli, F. Passban IDS: An intelligent anomaly-based intrusion detection system for IoT edge devices. IEEE Internet Things J. 2020, 7, 6882–6897. [Google Scholar] [CrossRef]
- Alsoufi, M.A.; Razak, S.; Siraj, M.M.; Nafea, I.; Ghaleb, F.A.; Saeed, F.; Nasser, M. Anomaly-based intrusion detection systems in iot using deep learning: A systematic literature review. Appl. Sci. 2021, 11, 8383. [Google Scholar] [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R. Design of anomaly-based intrusion detection system using fog computing for IoT network. Autom. Control Comput. Sci. 2021, 55, 137–147. [Google Scholar] [CrossRef]
- Heartfield, R.; Loukas, G.; Bezemskij, A.; Panaousis, E. Self-configurable cyber-physical intrusion detection for smart homes using reinforcement learning. IEEE Trans. Inf. Forensics Secur. 2020, 16, 1720–1735. [Google Scholar] [CrossRef]
- Ma, X.; Shi, W. Aesmote: Adversarial reinforcement learning with smote for anomaly detection. IEEE Trans. Netw. Sci. Eng. 2020, 8, 943–956. [Google Scholar] [CrossRef]
- Mitchell, R.; Chen, I.R. A survey of intrusion detection techniques for cyber-physical systems. ACM Comput. Surv. (CSUR) 2014, 46, 55. [Google Scholar] [CrossRef] [Green Version]
- Le, A.; Loo, J.; Chai, K.K.; Aiash, M. A specification-based IDS for detecting attacks on RPL-based network topology. Information 2016, 7, 25. [Google Scholar] [CrossRef] [Green Version]
- Althubaity, A.; Ammar, R.; Han, S. Detecting Rules-related Attacks in RPL-based Resource-Constrained Wireless Networks. In Proceedings of the 2020 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), Louisville, KY, USA, 9–11 December 2020; pp. 1–8. [Google Scholar]
- Kareem, M.A.; Tayeb, S. ML-based NIDS to secure RPL from routing attacks. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Virtual, 27–30 January 2021; pp. 1000–1006. [Google Scholar]
- Sharma, V.; You, I.; Yim, K.; Chen, R.; Cho, J.H. BRIoT: Behavior rule specification-based misbehavior detection for IoT-embedded cyber-physical systems. IEEE Access 2019, 7, 118556–118580. [Google Scholar] [CrossRef]
- Yun, K.; Astillo, P.V.; Lee, S.; Kim, J.; Kim, B.; You, I. Behavior-Rule Specification-based IDS for Safety-Related Embedded Devices in Smart Home. In Proceedings of the 2021 World Automation Congress (WAC), Virtual, 1–5 August 2021; pp. 65–70. [Google Scholar]
- Ning, H.; Liu, H. Cyber-physical-social based security architecture for future internet of things. Adv. Internet Things 2012, 2, 1. [Google Scholar] [CrossRef] [Green Version]
- Cervantes, C.; Poplade, D.; Nogueira, M.; Santos, A. Detection of sinkhole attacks for supporting secure routing on 6LoWPAN for Internet of Things. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 606–611. [Google Scholar]
- Krimmling, J.; Peter, S. Integration and evaluation of intrusion detection for CoAP in smart city applications. In Proceedings of the Communications and Network Security (CNS), San Francisco, CA, USA, 29–31 October 2014; pp. 73–78. [Google Scholar]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Privacy-preserved task offloading in mobile blockchain with deep reinforcement learning. IEEE Trans. Netw. Serv. Manag. 2020, 17, 2536–2549. [Google Scholar] [CrossRef]
- Wu, H.; Wolter, K.; Jiao, P.; Deng, Y.; Zhao, Y.; Xu, M. EEDTO: An energy-efficient dynamic task offloading algorithm for blockchain-enabled IoT-edge-cloud orchestrated computing. IEEE Internet Things J. 2020, 8, 2163–2176. [Google Scholar] [CrossRef]
- Gassais, R.; Ezzati-Jivan, N.; Fernandez, J.M.; Aloise, D.; Dagenais, M.R. Multi-level host-based intrusion detection system for Internet of things. J. Cloud Comput. 2020, 9, 1–16. [Google Scholar] [CrossRef]
- Wang, X.; Lu, X. A host-based anomaly detection framework using XGBoost and LSTM for IoT devices. Wirel. Commun. Mob. Comput. 2020, 2020, 8838571. [Google Scholar] [CrossRef]
- Kfouri, G.d.O.; Gonçalves, D.G.; Dutra, B.V.; de Alencastro, J.F.; de Caldas Filho, F.L.; e Martins, L.M.; Praciano, B.J.; de Oliveira Albuquerque, R.; de Sousa, R.T., Jr. Design of a distributed HIDS for IoT backbone components. Ann. Comput. Sci. Inf. Syst. 2019, 81–88. [Google Scholar] [CrossRef] [Green Version]
- Smys, S.; Basar, A.; Wang, H. Hybrid intrusion detection system for internet of things (IoT). J. ISMAC 2020, 2, 190–199. [Google Scholar] [CrossRef]
- Blakley, J. Open Edge Computing Initiative. 2021. Available online: https://www.openedgecomputing.org/ (accessed on 5 January 2022).
- ETSI, M. Mobile edge computing (mec): Framework and reference architecture. ETSI DGS MEC 2016, 3, 1–18. [Google Scholar]
- Ai, Y.; Peng, M.; Zhang, K. Edge computing technologies for Internet of Things: A primer. Digit. Commun. Netw. 2018, 4, 77–86. [Google Scholar] [CrossRef]
- Gyamfi, E.; Jurcut, A. Novel Online Network Intrusion Detection System for Industrial IoT based on OI-SVDD and AS-ELM. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Corcoran, P.; Datta, S.K. Mobile-edge computing and the Internet of Things for consumers: Extending cloud computing and services to the edge of the network. IEEE Consum. Electron. Mag. 2016, 5, 73–74. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context aware computing for the internet of things: A survey. IEEE Commun. Surv. Tutor. 2013, 16, 414–454. [Google Scholar] [CrossRef] [Green Version]
- Suo, H.; Liu, Z.; Wan, J.; Zhou, K. Security and privacy in mobile cloud computing. In Proceedings of the 2013 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013; pp. 655–659. [Google Scholar]
- Li, B.; Wu, W.; Zhao, W.; Zhang, H. Security enhancement with a hybrid cooperative noma scheme for mec system. IEEE Trans. Veh. Technol. 2021, 70, 2635–2648. [Google Scholar] [CrossRef]
- Li, L.; Ota, K.; Dong, M. DeepNFV: A lightweight framework for intelligent edge network functions virtualization. IEEE Netw. 2018, 33, 136–141. [Google Scholar] [CrossRef]
- Mastorakis, S.; Mtibaa, A.; Lee, J.; Misra, S. Icedge: When edge computing meets information-centric networking. IEEE Internet Things J. 2020, 7, 4203–4217. [Google Scholar] [CrossRef]
- Kaur, K.; Garg, S.; Aujla, G.S.; Kumar, N.; Rodrigues, J.J.; Guizani, M. Edge computing in the industrial internet of things environment: Software-defined-networks-based edge-cloud interplay. IEEE Commun. Mag. 2018, 56, 44–51. [Google Scholar] [CrossRef]
- He, Y.; Yu, F.R.; Zhao, N.; Leung, V.C.; Yin, H. Software-defined networks with mobile edge computing and caching for smart cities: A big data deep reinforcement learning approach. IEEE Commun. Mag. 2017, 55, 31–37. [Google Scholar] [CrossRef]
- Baktir, A.C.; Ozgovde, A.; Ersoy, C. How can edge computing benefit from software-defined networking: A survey, use cases, and future directions. IEEE Commun. Surv. Tutor. 2017, 19, 2359–2391. [Google Scholar] [CrossRef]
- Wang, Q.; Hu, H.; Sun, H.; Hu, R.Q. Secure and energy-efficient offloading and resource allocation in a NOMA-based MEC network. In Proceedings of the 2020 IEEE/ACM Symposium on Edge Computing (SEC), San Jose, CA, USA, 12–14 November 2020; pp. 420–424. [Google Scholar]
- Ahmad, I.; Lembo, S.; Rodriguez, F.; Mehnert, S.; Vehkaperä, M. Security of Micro MEC in 6G: A Brief Overview. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022; pp. 332–337. [Google Scholar]
- Ansere, J.A.; Han, G.; Wang, H.; Choi, C.; Wu, C. A Reliable Energy Efficient Dynamic Spectrum Sensing for Cognitive Radio IoT Networks. IEEE Internet Things J. 2019, 6, 6748–6759. [Google Scholar] [CrossRef]
- Liao, R.F.; Wen, H.; Wu, J.; Pan, F.; Xu, A.; Song, H.; Xie, F.; Jiang, Y.; Cao, M. Security enhancement for mobile edge computing through physical layer authentication. IEEE Access 2019, 7, 116390–116401. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.D.; Liyanage, M. Realizing multi-access edge computing feasibility: Security perspective. In Proceedings of the 2019 IEEE Conference on Standards for Communications and Networking (CSCN), Paris, France, 29–31 October 2019; pp. 1–7. [Google Scholar]
- Aazam, M.; Zeadally, S.; Harras, K.A. Offloading in fog computing for IoT: Review, enabling technologies, and research opportunities. Future Gener. Comput. Syst. 2018, 87, 278–289. [Google Scholar] [CrossRef]
- Wang, Y.; Meng, W.; Li, W.; Liu, Z.; Liu, Y.; Xue, H. Adaptive machine learning-based alarm reduction via edge computing for distributed intrusion detection systems. Concurr. Comput. Pract. Exp. 2019, 31, e5101. [Google Scholar] [CrossRef]
- Thanigaivelan, N.K.; Nigussie, E.; Kanth, R.K.; Virtanen, S.; Isoaho, J. Distributed internal anomaly detection system for Internet-of-Things. In Proceedings of the Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 319–320. [Google Scholar]
- Ferdowsi, A.; Saad, W. Generative adversarial networks for distributed intrusion detection in the internet of things. arXiv 2019, arXiv:1906.00567. [Google Scholar]
- Singh, J.; Bello, Y.; Hussein, A.R.; Erbad, A.; Mohamed, A. Hierarchical security paradigm for iot multiaccess edge computing. IEEE Internet Things J. 2020, 8, 5794–5805. [Google Scholar] [CrossRef]
- Yang, L.; Zhang, H.; Li, M.; Guo, J.; Ji, H. Mobile edge computing empowered energy efficient task offloading in 5 G. IEEE Trans. Veh. Technol. 2018, 67, 6398–6409. [Google Scholar] [CrossRef]
- Abeysekara, P.; Dong, H.; Qin, A.K. Machine learning-driven trust prediction for mec-based iot services. In Proceedings of the 2019 IEEE International Conference on Web Services (ICWS), Milan, Italy, 8–13 July 2019; pp. 188–192. [Google Scholar]
- Alladi, T.; Kohli, V.; Chamola, V.; Yu, F.R.; Guizani, M. Artificial intelligence (AI)-empowered intrusion detection architecture for the internet of vehicles. IEEE Wirel. Commun. 2021, 28, 144–149. [Google Scholar] [CrossRef]
- Dinh, T.Q.; Tang, J.; La, Q.D.; Quek, T.Q. Offloading in mobile edge computing: Task allocation and computational frequency scaling. IEEE Trans. Commun. 2017, 65, 3571–3584. [Google Scholar]
- Chen, X.; Zhang, H.; Wu, C.; Mao, S.; Ji, Y.; Bennis, M. Optimized computation offloading performance in virtual edge computing systems via deep reinforcement learning. IEEE Internet Things J. 2018, 6, 4005–4018. [Google Scholar] [CrossRef] [Green Version]
- Iqbal, M.A.; Bayoumi, M. Secure End-to-End key establishment protocol for resource-constrained healthcare sensors in the context of IoT. In Proceedings of the 2016 International Conference on High Performance Computing & Simulation (HPCS), Pasadena, CA, USA, 3–6 April 2016; pp. 523–530. [Google Scholar]
- Ranaweera, P.; Jurcut, A.; Liyanage, M. MEC-enabled 5G use cases: A survey on security vulnerabilities and countermeasures. ACM Comput. Surv. (CSUR) 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Xu, Y.; Zhang, T.; Yang, D.; Liu, Y.; Tao, M. Joint resource and trajectory optimization for security in UAV-assisted MEC systems. IEEE Trans. Commun. 2020, 69, 573–588. [Google Scholar] [CrossRef]
- Ranaweera, P.; Imrith, V.N.; Liyanag, M.; Jurcut, A.D. Security as a service platform leveraging multi-access edge computing infrastructure provisions. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Sha, K.; Errabelly, R.; Wei, W.; Yang, T.A.; Wang, Z. Edgesec: Design of an edge layer security service to enhance iot security. In Proceedings of the 2017 IEEE 1st International Conference on Fog and Edge Computing (ICFEC), Madrid, Spain, 14–15 May 2017; pp. 81–88. [Google Scholar]
- Singh, A.; Auluck, N.; Rana, O.; Jones, A.; Nepal, S. RT-SANE: Real time security aware scheduling on the network edge. In Proceedings of the10th International Conference on Utility and Cloud Computing, Austin, TX, USA, 5–8 December 2017; pp. 131–140. [Google Scholar]
- Kamma, P.K.; Palla, C.R.; Nelakuditi, U.R.; Yarrabothu, R.S. Design and implementation of 6LoWPAN border router. In Proceedings of the Wireless and Optical Communications Networks (WOCN), Mumbai, India, 24–26 February 2016; pp. 1–5. [Google Scholar]
- Wallgren, L.; Raza, S.; Voigt, T. Routing Attacks and Countermeasures in the RPL-based Internet of Things. Int. J. Distrib. Sens. Netw. 2013, 9, 794326. [Google Scholar] [CrossRef]
- Pongle, P.; Chavan, G. Real time intrusion and wormhole attack detection in internet of things. Int. J. Comput. Appl. 2015, 121, 1–9. [Google Scholar] [CrossRef]
- Gyamfi, E.; Jurcut, A. A Robust Security Task Offloading in Industrial IoT-Enabled Distributed Multi-Access Edge Computing. Front. Signal Proc. 2022, 2, 788943. [Google Scholar] [CrossRef]
- Gyamfi, E.; Ansere, J.A.; Kamal, M.; Tariq, M.; Jurcut, A. An Adaptive Network Security System for IoT-Enabled Maritime Transportation. In Proceedings of the EEE Transactions on Intelligent Transportation Systems, Macau, China, 8–12 October 2022. [Google Scholar]
- Abraham, A.; Thomas, J. Distributed intrusion detection systems: A computational intelligence approach. In Applications of Information Systems to Homeland Security and Defense; IGI Global: Hershey, PA, USA, 2006; pp. 107–137. [Google Scholar]
- Giang, N.K.; Blackstock, M.; Lea, R.; Leung, V.C. Developing iot applications in the fog: A distributed dataflow approach. In Proceedings of the 2015 5th International Conference on the Internet of Things (IOT), Seoul, Korea, 26–28 October 2015; pp. 155–162. [Google Scholar]
- Halinen, A.; Törnroos, J.Å.; Elo, M. Network process analysis: An event-based approach to study business network dynamics. Ind. Mark. Manag. 2013, 42, 1213–1222. [Google Scholar] [CrossRef]
- Sheikhan, M.; Bostani, H. A hybrid intrusion detection architecture for internet of things. In Proceedings of the 2016 8th International Symposium on Telecommunications (IST), Tehran, Iran, 27–28 September 2016; pp. 601–606. [Google Scholar]
- Hosseinpour, F.; Vahdani Amoli, P.; Plosila, J.; Hämäläinen, T.; Tenhunen, H. An intrusion detection system for fog computing and IoT based logistic systems using a smart data approach. Int. J. Digit. Content Technol. Its Appl. 2016, 10, 1–14. [Google Scholar]
- Gajewski, M.; Batalla, J.M.; Mastorakis, G.; Mavromoustakis, C.X. A distributed IDS architecture model for Smart Home systems. Clust. Comput. 2019, 22, 1739–1749. [Google Scholar] [CrossRef] [Green Version]
- Khan, Z.A.; Herrmann, P. A trust based distributed intrusion detection mechanism for internet of things. In Proceedings of the 2017 IEEE 31st International Conference on Advanced Information Networking and Applications (AINA), Taipei, Taiwan, 27–29 March 2017; pp. 1169–1176. [Google Scholar]
- Zhou, C.V.; Leckie, C.; Karunasekera, S. A survey of coordinated attacks and collaborative intrusion detection. Comput. Secur. 2010, 29, 124–140. [Google Scholar] [CrossRef]
- Arshad, J.; Azad, M.A.; Abdellatif, M.M.; Rehman, M.H.U.; Salah, K. COLIDE: A collaborative intrusion detection framework for Internet of Things. IET Netw. 2018, 8, 3–14. [Google Scholar] [CrossRef] [Green Version]
- Cho, E.J.; Kim, J.H.; Hong, C.S. Attack model and detection scheme for botnet on 6LoWPAN. In Proceedings of the Asia-Pacific Network Operations and Management Symposium, Jeju Island, Korea, 23–25 September 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 515–518. [Google Scholar]
- Jun, C.; Chi, C. Design of complex event-processing IDS in internet of things. In Proceedings of the 2014 Sixth International Conference on Measuring Technology and Mechatronics Automation, Zhangjiajie, China, 10–11 January 2014; pp. 226–229. [Google Scholar]
- Chen, R.; Liu, C.M.; Chen, C. An artificial immune-based distributed intrusion detection model for the internet of things. Advanced materials research. Trans. Tech. Publ. 2012, 366, 165–168. [Google Scholar]
- Abeshu, A.; Chilamkurti, N. Deep learning: The frontier for distributed attack detection in fog-to-things computing. IEEE Commun. Mag. 2018, 56, 169–175. [Google Scholar] [CrossRef]
- Diro, A.A.; Naveen, C. Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener. Comput. Syst. 2018, 82, 761–768. [Google Scholar] [CrossRef]
- Diro, A.; Chilamkurti, N. Leveraging LSTM networks for attack detection in fog-to-things communications. IEEE Commun. Mag. 2018, 56, 124–130. [Google Scholar] [CrossRef]
- Sohal, A.S.; Sandhu, R.; Sood, S.K.; Chang, V. A cybersecurity framework to identify malicious edge device in fog computing and cloud-of-things environments. Comput. Secur. 2018, 74, 340–354. [Google Scholar] [CrossRef]
- Stolfo, S.J.; Salem, M.B.; Keromytis, A.D. Fog computing: Mitigating insider data theft attacks in the cloud. In Proceedings of the 2012 IEEE symposium on security and privacy workshops, Francisco, CA, USA, 24–25 May 2012; pp. 125–128. [Google Scholar]
- Sudqi Khater, B.; Abdul Wahab, A.; Idris, M.; Abdulla Hussain, M.; Ahmed Ibrahim, A. A Lightweight Perceptron-Based Intrusion Detection System for Fog Computing. Appl. Sci. 2019, 9, 178. [Google Scholar] [CrossRef] [Green Version]
- An, X.; Zhou, X.; Lü, X.; Lin, F.; Yang, L. Sample selected extreme learning machine based intrusion detection in fog computing and MEC. Wirel. Commun. Mob. Comput. 2018, 2018. [Google Scholar] [CrossRef] [Green Version]
- Kovanen, T.; David, G.; Hämäläinen, T. Survey: Intrusion detection systems in encrypted traffic. In Internet of Things, Smart Spaces, and Next Generation Networks and Systems; Springer: Berlin/Heidelberg, Germany, 2016; pp. 281–293. [Google Scholar]
- Yin, X.C.; Liu, Z.G.; Nkenyereye, L.; Ndibanje, B. Toward an applied cyber security solution in IoT-based smart grids: An intrusion detection system approach. Sensors 2019, 19, 4952. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Qiu, H.; Dong, T.; Zhang, T.; Lu, J.; Memmi, G.; Qiu, M. Adversarial attacks against network intrusion detection in iot systems. IEEE Internet Things J. 2020, 8, 10327–10335. [Google Scholar] [CrossRef]
- Husnain, M.; Hayat, K.; Cambiaso, E.; Fayyaz, U.U.; Mongelli, M.; Akram, H.; Ghazanfar Abbas, S.; Shah, G.A. Preventing MQTT Vulnerabilities Using IoT-Enabled Intrusion Detection System. Sensors 2022, 22, 567. [Google Scholar] [CrossRef]
- Jiang, X.; Qiu, T.; Zhou, X.; Zhang, B.; Sun, X.; Chi, J. A Text Similarity-based Protocol Parsing Scheme for Industrial Internet of Things. In Proceedings of the 2021 IEEE 24th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Dalian, China, 5–7 May 2021; pp. 781–787. [Google Scholar]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network intrusion detection for IoT security based on learning techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Khan, M.A.; Karim, M.; Kim, Y. A scalable and hybrid intrusion detection system based on the convolutional-LSTM network. Symmetry 2019, 11, 583. [Google Scholar] [CrossRef] [Green Version]
- Liu, H.; Lang, B.; Liu, M.; Yan, H. CNN and RNN based payload classification methods for attack detection. Knowl. Based Syst. 2019, 163, 332–341. [Google Scholar] [CrossRef]
- Vieira, L.; Santos, L.; Gonçalves, R.; Rabadão, C. Identifying attack signatures for the internet of things: An IP flow based approach. In Proceedings of the 2019 14th Iberian Conference on Information Systems and Technologies (CISTI), Coimbra, Portugal, 19–22 June 2019; pp. 1–7. [Google Scholar]
- Pontes, C.F.; de Souza, M.M.; Gondim, J.J.; Bishop, M.; Marotta, M.A. A new method for flow-based network intrusion detection using the inverse Potts model. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1125–1136. [Google Scholar] [CrossRef]
- Tiburski, R.T.; Moratelli, C.R.; Johann, S.F.; Neves, M.V.; de Matos, E.; Amaral, L.A.; Hessel, F. Lightweight security architecture based on embedded virtualization and trust mechanisms for IoT edge devices. IEEE Commun. Mag. 2019, 57, 67–73. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Senouci, S.M.; Al-Bahri, M. A lightweight anomaly detection technique for low-resource IoT devices: A game-theoretic methodology. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 23–27 May 2016; pp. 1–6. [Google Scholar]
- MALEH, Y.; Ezzati, A. Lightweight Intrusion Detection Scheme for Wireless Sensor Networks. IAENG Int. J. Comput. Sci. 2015, 42, 1–8. [Google Scholar]
- Zhao, S.; Li, W.; Zia, T.; Zomaya, A.Y. A dimension reduction model and classifier for anomaly-based intrusion detection in internet of things. In Proceedings of the 2017 IEEE 15th Intl Conf on Dependable, Autonomic and Secure Computing, 15th Intl Conf on Pervasive Intelligence and Computing, 3rd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Orlando, FL, USA, 6–10 November 2017; pp. 836–843. [Google Scholar]
- Liu, H.; Lang, B. Machine Learning and Deep Learning Methods for Intrusion Detection Systems: A Survey. Appl. Sci. 2019, 9, 4396. [Google Scholar] [CrossRef] [Green Version]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Mikolajczyk, K.; Leibe, B.; Schiele, B. Multiple object class detection with a generative model. In Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition, San Diego, CA, USA, 20–25 June 2006; Volume 1, pp. 26–33. [Google Scholar]
- Lin, R.S.; Ross, D.A.; Lim, J.; Yang, M.H. Adaptive discriminative generative model and its applications. In Advances in Neural Information Processing Systems; 2005; pp. 801–808. Available online: https://proceedings.neurips.cc/paper/2004/file/f12f2b34a0c3174269c19e21c07dee68-Paper.pdf (accessed on 18 November 2021).
- HaddadPajouh, H.; Dehghantanha, A.; Khayami, R.; Choo, K.K.R. A deep Recurrent Neural Network based approach for Internet of Things malware threat hunting. Future Gener. Comput. Syst. 2018, 85, 88–96. [Google Scholar] [CrossRef]
- Saeed, A.; Ahmadinia, A.; Javed, A.; Larijani, H. Intelligent intrusion detection in low-power IoTs. ACM Trans. Internet Technol. (TOIT) 2016, 16, 27. [Google Scholar] [CrossRef]
- Azmoodeh, A.; Dehghantanha, A.; Choo, K.K.R. Robust malware detection for internet of (battlefield) things devices using deep eigenspace learning. IEEE Trans. Sustain. Comput. 2018, 4, 88–95. [Google Scholar] [CrossRef]
- Erfani, S.M.; Rajasegarar, S.; Karunasekera, S.; Leckie, C. High-dimensional and large-scale anomaly detection using a linear one-class SVM with deep learning. Pattern Recognit. 2016, 58, 121–134. [Google Scholar] [CrossRef]
- Razzak, I.; Zafar, K.; Imran, M.; Xu, G. Randomized nonlinear one-class support vector machines with bounded loss function to detect of outliers for large scale IoT data. Future Gener. Comput. Syst. 2020, 112, 715–723. [Google Scholar] [CrossRef]
- La, Q.D.; Quek, T.Q.; Lee, J.; Jin, S.; Zhu, H. Deceptive attack and defense game in honeypot-enabled networks for the internet of things. IEEE Internet Things J. 2016, 3, 1025–1035. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Burnap, P. Pulse: An adaptive intrusion detection for the internet of things. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT, London, UK, 28–29 March 2018. [Google Scholar]
- Arrington, B.; Barnett, L.; Rufus, R.; Esterline, A. Behavioral modeling intrusion detection system (bmids) using internet of things (iot) behavior-based anomaly detection via immunity-inspired algorithms. In Proceedings of the 2016 25th International Conference on Computer Communication and Networks (ICCCN), Waikoloa, HI, USA, 1–4 August 2016; pp. 1–6. [Google Scholar]
- Pajouh, H.H.; Javidan, R.; Khayami, R.; Ali, D.; Choo, K.K.R. A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks. IEEE Trans. Emerg. Top. Comput. 2016, 7, 314–323. [Google Scholar] [CrossRef]
- Ghosh, P.; Mitra, R. Proposed GA-BFSS and logistic regression based intrusion detection system. In Proceedings of the 2015 Third International Conference on Computer, Communication, Control and Information Technology (C3IT), Hooghly, India, 7–8 February 2015; pp. 1–6. [Google Scholar]
- Prokofiev, A.O.; Smirnova, Y.S.; Surov, V.A. A method to detect Internet of Things botnets. In Proceedings of the 2018 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Moscow, Russia, 29 January–1 February 2018; pp. 105–108. [Google Scholar]
- Azad, C.; Mehta, A.K.; Jha, V.K. Evolutionary Decision Tree-Based Intrusion Detection System. In Proceedings of the Third International Conference on Microelectronics, Computing and Communication Systems; Springer: Berlin/Heidelberg, Germany, 2019; pp. 271–282. [Google Scholar]
- Kumar, V.; Das, A.K.; Sinha, D. UIDS: A unified intrusion detection system for IoT environment. Evol. Intell. 2021, 14, 47–59. [Google Scholar] [CrossRef]
- Amarasinghe, K.; Manic, M. Improving user trust on deep neural networks based intrusion detection systems. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 3262–3268. [Google Scholar]
- Blanco, R.; Cilla, J.J.; Malagón, P.; Penas, I.; Moya, J.M. Tuning cnn input layout for ids with genetic algorithms. In Proceedings of the International Conference on Hybrid Artificial Intelligence Systems, Oviedo, Spain, 20–22 June 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 197–209. [Google Scholar]
- Mayhew, M.; Atighetchi, M.; Adler, A.; Greenstadt, R. Use of machine learning in big data analytics for insider threat detection. In Proceedings of the MILCOM 2015-2015 IEEE Military Communications Conference, Tampa, FL, USA, 26–28 October 2015; pp. 915–922. [Google Scholar]
- Li, W.; Yi, P.; Wu, Y.; Pan, L.; Li, J. A new intrusion detection system based on KNN classification algorithm in wireless sensor network. J. Electr. Comput. Eng. 2014, 2014, 240217. [Google Scholar] [CrossRef]
- Singh, R.R.; Gupta, N.; Kumar, S. To reduce the false alarm in intrusion detection system using self organizing map. Int. J. Soft Comput. Eng. (IJSCE) 2011, 2231, 2307. [Google Scholar]
- Cárdenas, A.A.; Baras, J.S.; Seamon, K. A framework for the evaluation of intrusion detection systems. In Proceedings of the 2006 IEEE Symposium on Security and Privacy (S&P’06), Oakland, CA, USA, 21–24 May 2006; p. 15. [Google Scholar]
- Gu, G.; Fogla, P.; Dagon, D.; Lee, W.; Skorić, B. Measuring intrusion detection capability: An information-theoretic approach. In Proceedings of the 2006 ACM Symposium on Information, computer and communications security, Taipei, Taiwan, 21–24 March 2006; pp. 90–101. [Google Scholar]
- Fink, G.A.; Chappell, B.; Turner, T.; O’Donoghue, K. A metrics-based approach to intrusion detection system evaluation for distributed real-time systems. In Proceedings of the 16th International Parallel and Distributed Processing Symposium, Ft. Lauderdale, FL, USA, 15–19 April 2001; p. 8. [Google Scholar]
- Kim, J.; Kim, J.; Thu, H.L.T.; Kim, H. Long short term memory recurrent neural network classifier for intrusion detection. In Proceedings of the 2016 International Conference on Platform Technology and Service (PlatCon), Jeju, Korea, 15–17 February 2016; pp. 1–5. [Google Scholar]
- Ansere, J.A.; Han, G.; Bonsu, K.A.; Peng, Y. Energy Efficient Joint Power Allocation and User Selection Algorithm for Data Transmission in Internet of Things Networks. IEEE Internet Things J. 2020, 7, 8736–8747. [Google Scholar] [CrossRef]
- Ansere, J.A.; Han, G.; Liu, L.; Peng, Y.; Kamal, M. Optimal Resource Allocation in Energy Efficient Internet of Things Networks with Imperfect CSI. IEEE Internet Things J. 2020, 7, 5401–5411. [Google Scholar] [CrossRef]
- Tsai, C.F.; Lin, C.Y. A triangle area based nearest neighbors approach to intrusion detection. Pattern Recognit. 2010, 43, 222–229. [Google Scholar] [CrossRef]
- IDS 2012 Datasets Research Canadian Institute for Cybersecurity UNB. Available online: https://www.unb.ca/cic/datasets/ids.html (accessed on 22 April 2020).
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. In Proceedings of the International Conference on Information Systems Security and Privacy, Funchal, Madeira, 22–24 January 2018; pp. 108–116. Available online: https://www.scitepress.org/Papers/2018/66398/66398.pdf (accessed on 17 October 2021).
- IDS 2018 Datasets Research Canadian Institute for Cybersecurity UNB. Available online: https://www.unb.ca/cic/datasets/ids-2018.html (accessed on 22 April 2020).
- Ullah, I.; Mahmoud, Q.H. A two-level hybrid model for anomalous activity detection in IoT networks. In Proceedings of the 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–6. [Google Scholar]
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar]
- Moustafa, N.; Slay, J. The evaluation of Network Anomaly Detection Systems: Statistical analysis of the UNSW-NB15 data set and the comparison with the KDD99 data set. Inf. Secur. J. Glob. Perspect. 2016, 25, 18–31. [Google Scholar] [CrossRef]
- Kang, H.; Ahn, D.H.; Lee, G.M.; Yoo, J.; Park, K.H.; Kim, H.K. IoT Network Intrusion Dataset. IEEE Dataport. 2019. Available online: https://ieee-dataport.org/ieee-dataport-dataset-upload-contest-entries (accessed on 10 January 2022).
- Ullah, I.; Mahmoud, Q.H. A scheme for generating a dataset for anomalous activity detection in iot networks. In Proceedings of the Canadian Conference on Artificial Intelligence, Ottawa, ON, Canada, 13–15 May 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 508–520. [Google Scholar]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT telemetry dataset: A new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Pinto, R.; Gonçalves, G.; Tovar, E.; Delsing, J. Attack detection in cyber-physical production systems using the deterministic dendritic cell algorithm. In Proceedings of the 2020 25th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Vienna, Austria, 8–11 September 2020; Volume 1, pp. 1552–1559. [Google Scholar]
- Sousa, B.; Cruz, T.; Arieiro, M.; Pereira, V. An ELEGANT dataset with Denial of Service and Man in The Middle attacks. arXiv 2021, arXiv:2103.09380. [Google Scholar]
- Sambangi, S.; Gondi, L.; Aljawarneh, S.; Annaluri, S.R. SDN DDOS Attack Image Dataset. 2021. Available online: https://ieee-dataport.org/documents/sdn-ddos-attack-image-dataset (accessed on 10 January 2022).
- Hussain, F.; Abbas, S.G.; Husnain, M.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. IoT DoS and DDoS attack detection using ResNet. In Proceedings of the 2020 IEEE 23rd International Multitopic Conference (INMIC), Bahawalpur, Pakistan, 5–7 November 2020; pp. 1–6. [Google Scholar]
- LEE, Y. Development of Industrial IoT System for Anomaly Detection in Smart Factory. 2020. Available online: https://ieee-dataport.org/documents/development-industrial-iot-system-anomaly-detection-smart-factory (accessed on 10 January 2022).
- Hindy, H.; Tachtatzis, C.; Atkinson, R.; Bayne, E.; Bellekens, X. Mqtt-iot-ids2020: Mqtt Internet of Things Intrusion Detection Dataset. IEEE Dataport. 2020. Available online: https://ieee-dataport.org/open-access/mqtt-iot-ids2020-mqtt-internet-things-intrusion-detection-dataset (accessed on 11 January 2022).
- Ferrag, M.A.; Friha, O.; Hamouda, D.; Maglaras, L.; Janicke, H. Edge-IIoTset: A New Comprehensive Realistic Cyber Security Dataset of IoT and IIoT Applications for Centralized and Federated Learning. IEEE Access 2022, 40281–40306. [Google Scholar] [CrossRef]
- Al-Hawawreh, M.; Sitnikova, E.; Aboutorab, N. X-IIoTID: A connectivity-and device-agnostic intrusion dataset for industrial Internet of Things. IEEE Internet Things J. 2021, 9, 3962–3977. [Google Scholar] [CrossRef]
- Trajanovski, T.; Zhang, N. IoT-BDA Botnet Analysis Dataset. IEEE Internet Things J. 2021, 9. [Google Scholar] [CrossRef]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Milano, Italy, 7–10 September 2009; pp. 1–6. [Google Scholar]
- Hussain, F.; Abbas, S.G.; Husnain, M.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. IoT DoS and DDoS Attack Dataset. 2021. Available online: https://ieee-dataport.org/documents/iot-dos-and-ddos-attack-dataset (accessed on 11 January 2022). [CrossRef]
- Hussain, F.; Abbas, S.G.; Shah, G.A.; Pires, I.M.; Fayyaz, U.U.; Shahzad, F.; Garcia, N.M.; Zdravevski, E. A Framework for Malicious Traffic Detection in IoT Healthcare Environment. Sensors 2021, 21, 3025. [Google Scholar] [CrossRef]
- Kalupahana Liyanage, K.S.; Divakaran, D.M.; Singh, R.P.; Gurusamy, M. NSS Mirai Dataset. 2020. Available online: https://ieee-dataport.org/documents/nss-mirai-dataset (accessed on 10 January 2022).
- Zolanvari, M. WUSTL-IIOT-2021. 2021. Available online: https://ieee-dataport.org/documents/wustl-iiot-2021, (accessed on 10 January 2022).
- Moustafa, N. The Bot-IoT Dataset. 2019. Available online: https://ieee-dataport.org/documents/bot-iot-dataset (accessed on 11 January 2022).
| Acronym | Short Definition |
|---|---|
| IoT | Internet of Things |
| NIDS | Network Intrusion Detection System |
| ML | Machine Learning |
| NIDS | Intrusion Detection System |
| MEMS | Micro-electromechanical System |
| OT | Operational Technology |
| VHD | Virtual Honeypot Device |
| IEEE | Electrical and Electronics Engineers |
| 6LoWPAN | IPv6 Low-Power Wireless Personal Area Network |
| LPWAN | Low Power Wide Area Network |
| DoS | Denial-of-Service |
| DDoS | Distributed Denial-of-Service |
| MITM | Man-In-The-Middle |
| WSN | Wireless Sensor Network |
| RPL | Routing Protocol for Low Power and Lossy Network |
| NFV | Network Functions Virtualisation |
| ICN | Information-Centric Network |
| SDN | Software-Defined Network |
| MEC | Mobile Edge Computing |
| VM | Virtual Machine |
| RL | Reinforcement Learning |
| LA | Learning Automata |
| MLP | Multilayer Perceptron |
| R2L | Remote-to-Local |
| U2R | User-to-Route |
| CNN | Convolutional Neural Network |
| DIDS | Distributed Denial of Service |
| LSTM | Long Short-Term Memory |
| RNN | Recurrent Neural Network |
| AIS | Artificial Immune System |
| PCA | Principal Component Analysis |
| QoS | Quality of Service |
| Source | Attacks | Mode of Attack Initiation |
|---|---|---|
| [38,39,40] | Spoofing | Impersonation |
| [41,42,43] | Denial of Service (DoS) | Network Flooding |
| [44,45,46] | Distributed Denial-of-Service (DDoS) | Network Flooding |
| [47,48] | Jamming | Fake Signaling |
| [49,50] | Man-In-the-Middle | Eavesdropping Packets |
| [51,52] | Privacy Leakage | Attack Authentication Storage |
| [53,54] | Marai Botnet Attack | Malware Implant on Devices |
| [55,56] | Sybil Attack | Creates Anonymous Identities |
| [57,58] | AI-Based Attacks | Creates AI-powered Tools |
| Host-Based NIDS | Network-Based IDS | |
|---|---|---|
| Data Source | System call logs | Captured network traffic |
| Placement Strategy | Locally on the hosted device or machine | Specific IoT devices on the same subnet |
| Detection Rate | Low, difficult to detect new attacks | High, can detect new attacks in real time |
| Threats Trace-ability | Based on system calls | Trace intrusion based on network addresses and timestamps |
| Limitations | Cannot analyse network attacks, rules created can be obsolete, depends on the operating system (OS) | Monitor only network traffic within a specific subnet |
| Reference | ML Methods | Precision | Recall | Accuracy |
|---|---|---|---|---|
| Mayhew et al. [189] | Behavior-Based Access Control | 99.1% | - | - |
| Haddadpajouh et al. [174] | RNN, LSTM | - | - | 98.18% |
| Saeed et al [175] | RNN | - | - | 97.23% |
| Azmoodeh et. al. [176] | Deep Eigenspace learning | 98.59% | 98.37% | 99.68% |
| Erfani et al [177] | One-Class SVM | - | - | - |
| La et al. [179] | Bayesian Game Theory | - | - | - |
| Arrington et al. [181] | Behavioral Modeling | - | - | - |
| Li et al. [190] | KNN | 98.5% | - | - |
| Pajouh et al. [182] | Naïve Bayes | 84.86% | - | - |
| Ghosh and Mitra. [183] | Logistic Regression | - | - | 93.26% |
| Prokofiev et al. [184] | Logistic Regression | 94.0% | 98.0% | 97.30% |
| Singh and Neetesh [191] | Self-Organizing Map | 64% | - | - |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gyamfi, E.; Jurcut, A. Intrusion Detection in Internet of Things Systems: A Review on Design Approaches Leveraging Multi-Access Edge Computing, Machine Learning, and Datasets. Sensors 2022, 22, 3744. https://doi.org/10.3390/s22103744
Gyamfi E, Jurcut A. Intrusion Detection in Internet of Things Systems: A Review on Design Approaches Leveraging Multi-Access Edge Computing, Machine Learning, and Datasets. Sensors. 2022; 22(10):3744. https://doi.org/10.3390/s22103744
Chicago/Turabian StyleGyamfi, Eric, and Anca Jurcut. 2022. "Intrusion Detection in Internet of Things Systems: A Review on Design Approaches Leveraging Multi-Access Edge Computing, Machine Learning, and Datasets" Sensors 22, no. 10: 3744. https://doi.org/10.3390/s22103744
APA StyleGyamfi, E., & Jurcut, A. (2022). Intrusion Detection in Internet of Things Systems: A Review on Design Approaches Leveraging Multi-Access Edge Computing, Machine Learning, and Datasets. Sensors, 22(10), 3744. https://doi.org/10.3390/s22103744







