Automatic Symbol Resolution on Embedded Platforms by the Example of Smart TV Device
Abstract
:1. Introduction
1.1. Area of Research
1.2. Preliminary Analysis of Research Gap
2. Related Works
3. Contribution
- Symbol resolution for Samsung firmware based on search of characteristic binary values in previous firmwares (Section 5.2).
- New framework for symbol resolution on a Samsung TV, based on locating string references (Section 5.3).
4. Background
4.1. Firmware Security
- Firmware signing is one of the ways of protecting Smart TV devices before installing corrupted firmwares. This feature is implemented by the software vendor, who signs the firmware image with a private key, kept in secret. A device with such a feature enabled will first validate the firmware before accepting its installation. In case of detection compromised firmware integrity, the device will reject its upgrade or installation. This can be omitted by turning off the feature that checks firmware signing or uploading a rootkit when the firmware is already run by the system [59].
- Firmware encryption—different vendors use different types for firmware encryption. In the case of Samsung’s devices, firmwares can be encrypted using multiple algorithms. There are already available tools for decryption of such firmwares (https://wiki.samygo.tv/index.php?title=Playing_with_Firmware_Images, accessed on 13 April 2021).
- Firmware data mangling is an example of applying the approach “security by obscurity”. In this case, one or more base functions can be generated and blended into the existing code. Such an approach may mean that it will be more difficult or even impossible for the attackers to distinguish the base function’s codes from the codes of the firmware [60].
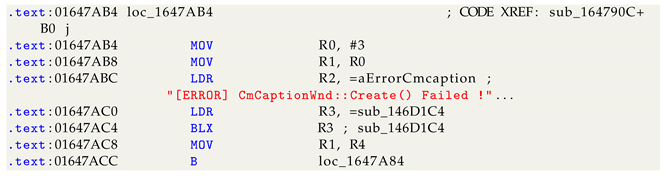
- Removing symbols from firmware is another example of the “security by obscurity” approach. In this case, software vendors remove symbols (Figure 2) from the final version of the firmware [27]. In such case, if one wanted to hack the firmware, they would have to use hardcoded addresses instead of function symbols. This method is not a reliable one, because of possible differences with function’s addresses between different firmwares [27] (Figure 3).
4.2. Symbols Removal
4.3. Netcast Operating System (LG)
4.4. Orsay Operating System (Samsung)
5. Materials and Methods
5.1. Address to Symbol
 |
5.2. Distinctive Functions
 |
 |
 |
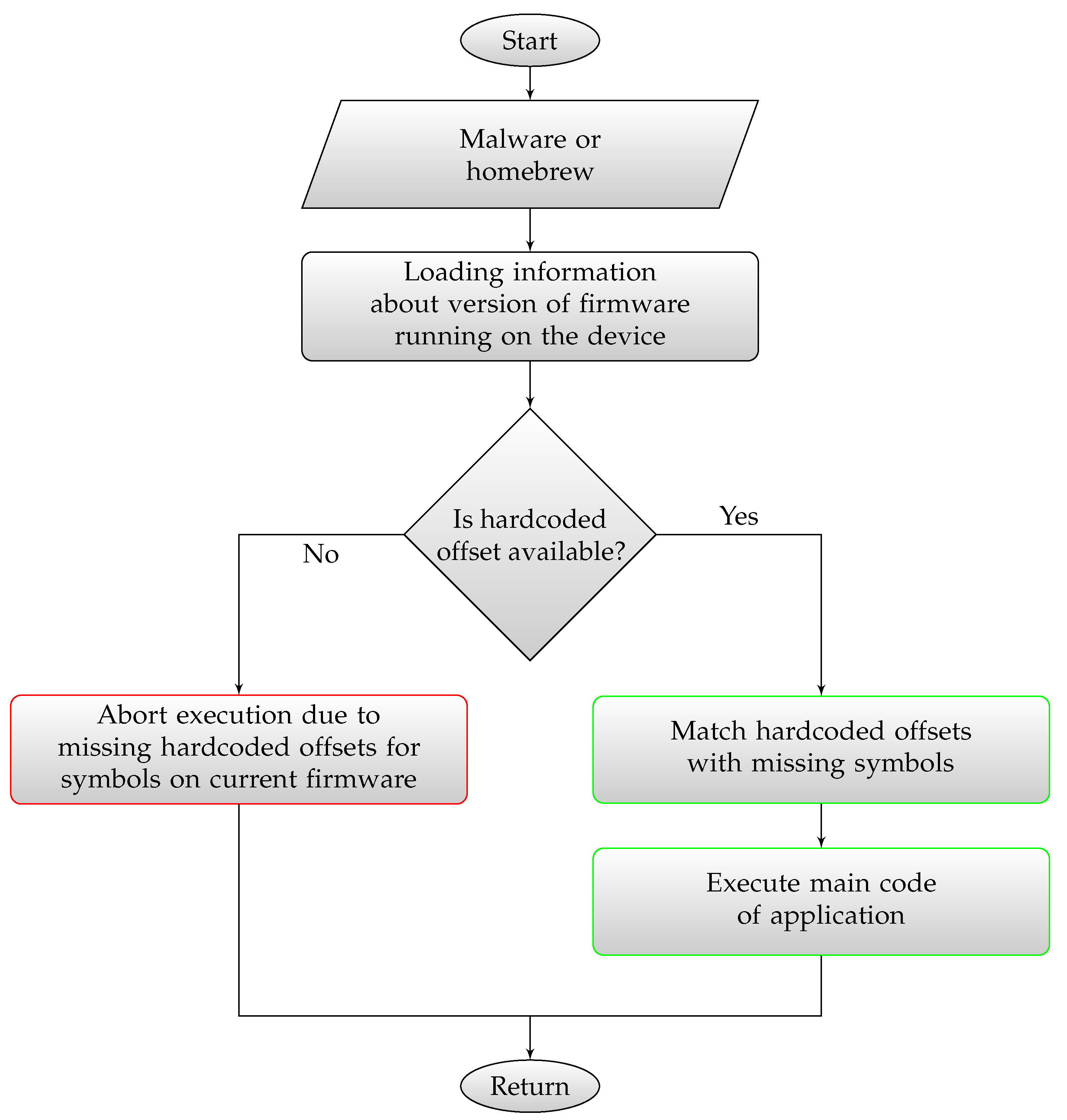
5.3. Framework Description
- find_func_by_string - localizes the function by specific string.
- find_nth_func_by_string - localizes the function which is presented in assembly below or above the function with specific string.
- find_nth_func - localizes the function present below or above specific function.
- find_nth_func_from_export - localizes function which is present in assembly below or above the function with specific exported symbol.
- find_function_start - localizes the function’s entry point.
 |
 |
 |
5.4. Experimental Setup
6. Results
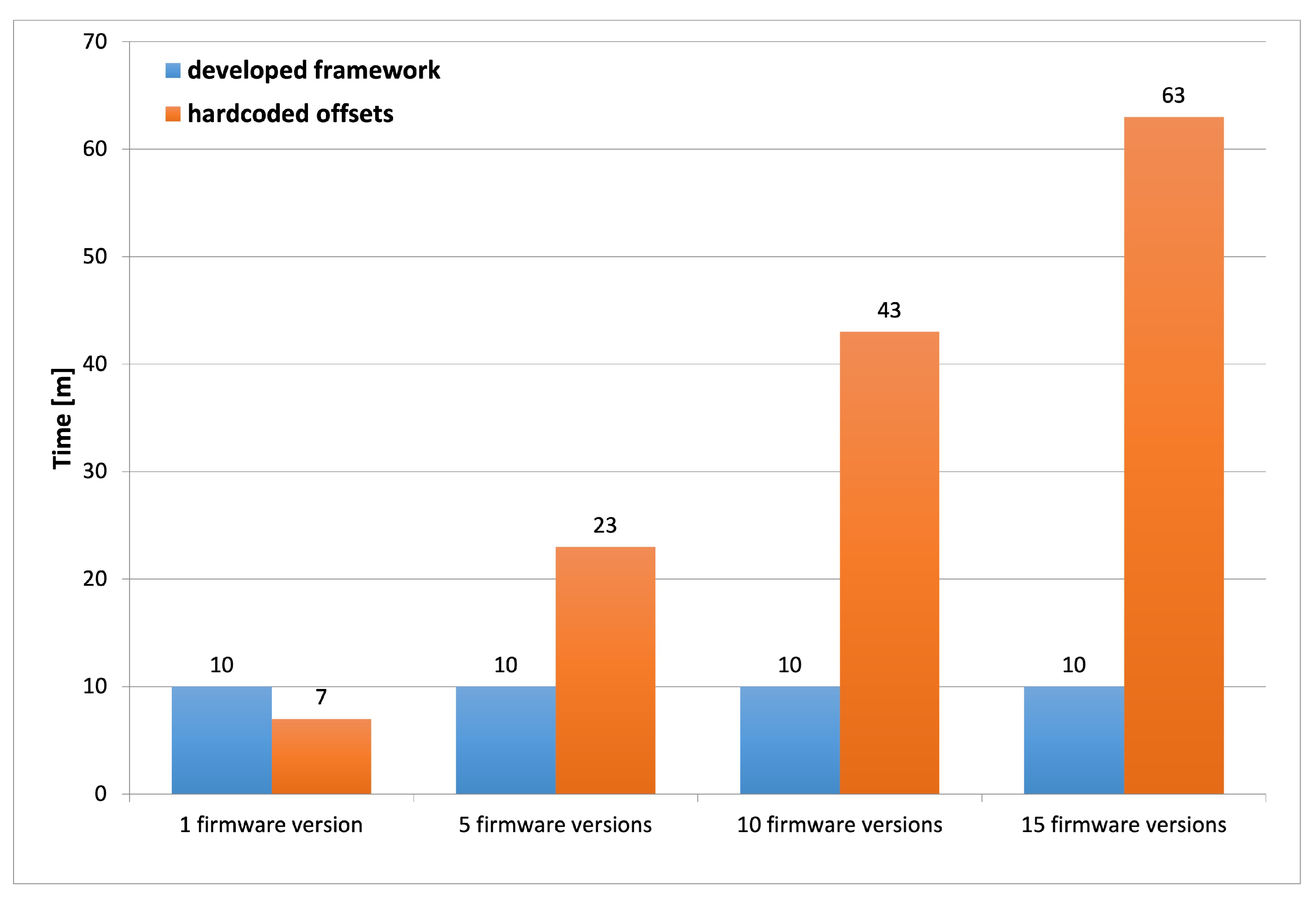
 |
Tests of Developed Framework
7. Legality and Ethics of Conducted Research
8. Discussion
Significance of Further Research in this Field and the Current State of the Industry
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Duch, P.; Jaworski, T. Enriching Computer Science Programming Classes with Arduino Game Development. In Proceedings of the 11th International Conference on Human System Interaction (HSI), Gdansk, Poland, 4–6 July 2018; pp. 148–154. [Google Scholar] [CrossRef]
- Perenc, I.; Jaworski, T.; Duch, P. Teaching programming using dedicated Arduino educational board. Comput. Appl. Eng. Educ. 2019, 27, 943–954. [Google Scholar] [CrossRef]
- Duch, P.; Jaworski, T. Dante—Automated Assessments Tool for Students’ Programming Assignments. In Proceedings of the 11th International Conference on Human System Interaction (HSI), Gdansk, Poland, 4–6 July 2018; pp. 162–168. [Google Scholar] [CrossRef]
- Majchrowicz, M.; Kapusta, P.; Jackowska-Strumiłło, L.; Banasiak, R.; Sankowski, D. Multi-GPU, multi-node algorithms for acceleration of image reconstruction in 3D Electrical Capacitance Tomography in heterogeneous distributed system. Sensors 2020, 20, 391. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Papoutsakis, M.; Fysarakis, K.; Spanoudakis, G.; Ioannidis, S.; Koloutsou, K. Towards a Collection of Security and Privacy Patterns. Appl. Sci. 2021, 11, 1396. [Google Scholar] [CrossRef]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and security: Challenges and solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Lee, J.; Choi, S.; Kim, D.; Choi, Y.; Sun, W. A Novel Hardware Security Architecture for IoT Device: PD-CRP (PUF Database and Challenge–Response Pair) Bloom Filter on Memristor-Based PUF. Appl. Sci. 2020, 10, 6692. [Google Scholar] [CrossRef]
- Pieroni, A.; Scarpato, N.; Felli, L. Blockchain and IoT Convergence—A Systematic Survey on Technologies, Protocols and Security. Appl. Sci. 2020, 10, 6749. [Google Scholar] [CrossRef]
- Horalek, J.; Sobeslav, V. Cybersecurity Analysis of IoT Networks. In International Conference on Computational Collective Intelligence; Springer: Berlin/Heidelberg, Germany, 2019; pp. 488–499. [Google Scholar]
- Shelupanov, A.; Evsyutin, O.; Konev, A.; Kostyuchenko, E.; Kruchinin, D.; Nikiforov, D. Information Security Methods—Modern Research Directions. Symmetry 2019, 11, 150. [Google Scholar] [CrossRef] [Green Version]
- Fujdiak, R.; Mlynek, P.; Mrnustik, P.; Barabas, M.; Blazek, P.; Borcik, F.; Misurec, J. Managing the secure software development. In Proceedings of the 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; pp. 1–4. [Google Scholar]
- Adat, V.; Gupta, B. Security in Internet of Things: Issues, challenges, taxonomy, and architecture. Telecommun. Syst. 2018, 67, 423–441. [Google Scholar] [CrossRef]
- Kang, S.; Kim, S. How to obtain common criteria certification of smart TV for home IoT security and reliability. Symmetry 2017, 9, 233. [Google Scholar] [CrossRef] [Green Version]
- Alam, I.; Khusro, S.; Naeem, M. A review of smart TV: Past, present, and future. In Proceedings of the International Conference on Open Source Systems Technologies (ICOSST), Lahore, Pakistan, 18–20 December 2017; pp. 35–41. [Google Scholar] [CrossRef]
- Goud, N. FBI issues Cyber Attack Warning against Smart TVs. 2020. Available online: https://www.infosecurity-magazine.com/news/fbi-issues-smart-tv-cybersecurity/ (accessed on 13 April 2021).
- Goud, N. Which Phone Protects Your Security the Best? We Asked the Experts. 2017. Available online: https://time.com/4905774/which-phone-is-most-secure/ (accessed on 13 April 2021).
- Grimes, R.A. Macs’ Low Popularity Keeps Them Safer from Hacking and Malware. 2009. Available online: https://www.csoonline.com/article/2629811/macs--low-popularity-keeps-them-safer-from-hacking-and-malware.html (accessed on 13 April 2021).
- Ghiglieri, M.; Volkamer, M.; Renaud, K. Exploring consumers’ attitudes of smart TV related privacy risks. In International Conference on Human Aspects of Information Security, Privacy, and Trust; Springer: Berlin/Heidelberg, Germany, 2017; pp. 656–674. [Google Scholar]
- ECU Concerns over Hacking and Data Privacy. 2020. Available online: https://studyonline.ecu.edu.au/blog/concerns-over-hacking-and-data-privacy (accessed on 13 April 2021).
- Feamster, N. Outsourcing Home Network Security. In ACM SIGCOMM Workshop on Home Networks; HomeNets ’10; ACM: New York, NY, USA, 2010; pp. 37–42. [Google Scholar] [CrossRef] [Green Version]
- Lee, S.; Kim, S. Hacking, Surveilling and Deceiving Victims on Smart TV. Blackhat USA. 2013. Available online: https://docs.huihoo.com/blackhat/usa-2013/US-13-Lee-Hacking-Surveilling-and-Deceiving-Victims-on-Smart-TV-Slides.pdf (accessed on 10 January 2020).
- Arabo, A.; El-Mousa, F. Security framework for smart devices. In Proceedings of the International Conference on Cyber Security, Cyber Warfare and Digital Forensic (CyberSec), Kuala Lumpur, Malaysia, 26–28 June 2012; pp. 82–87. [Google Scholar] [CrossRef]
- Ghiglieri, M.; Tews, E. A privacy protection system for HbbTV in Smart TVs. In Proceedings of the IEEE 11th Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2014; pp. 357–362. [Google Scholar] [CrossRef] [Green Version]
- Landau, S. What Was Samsung Thinking? IEEE Secur. Priv. 2015, 13, 3–4. [Google Scholar] [CrossRef]
- Xin, W.; Suying, Y. The Security File System in Smart TV Operating System. Inf. Secur. Comput. Fraud. 2014, 2, 48–51. [Google Scholar] [CrossRef]
- Altinyurt, E.U. SamyGO. Available online: http://www.samygo.tv:samygo (accessed on 30 September 2018).
- Wikileaks. Samsung’s Countermeasure Fixing Security Holes. Available online: https://wikileaks.org/sony/docs/07/Documents/@Deals/An%20Overview%20of%20Security%20Model%20applied%20on%20Samsung%202010%20TV_BDPs%20-%20Oct%202010.pdf (accessed on 30 September 2018).
- Kolnowski, T. Smart TVs Continue to Resonate with Global Consumers. 2019. Available online: https://digitized.house/smart-tvs-continue-to-resonate-with-global-consumers/ (accessed on 13 April 2021).
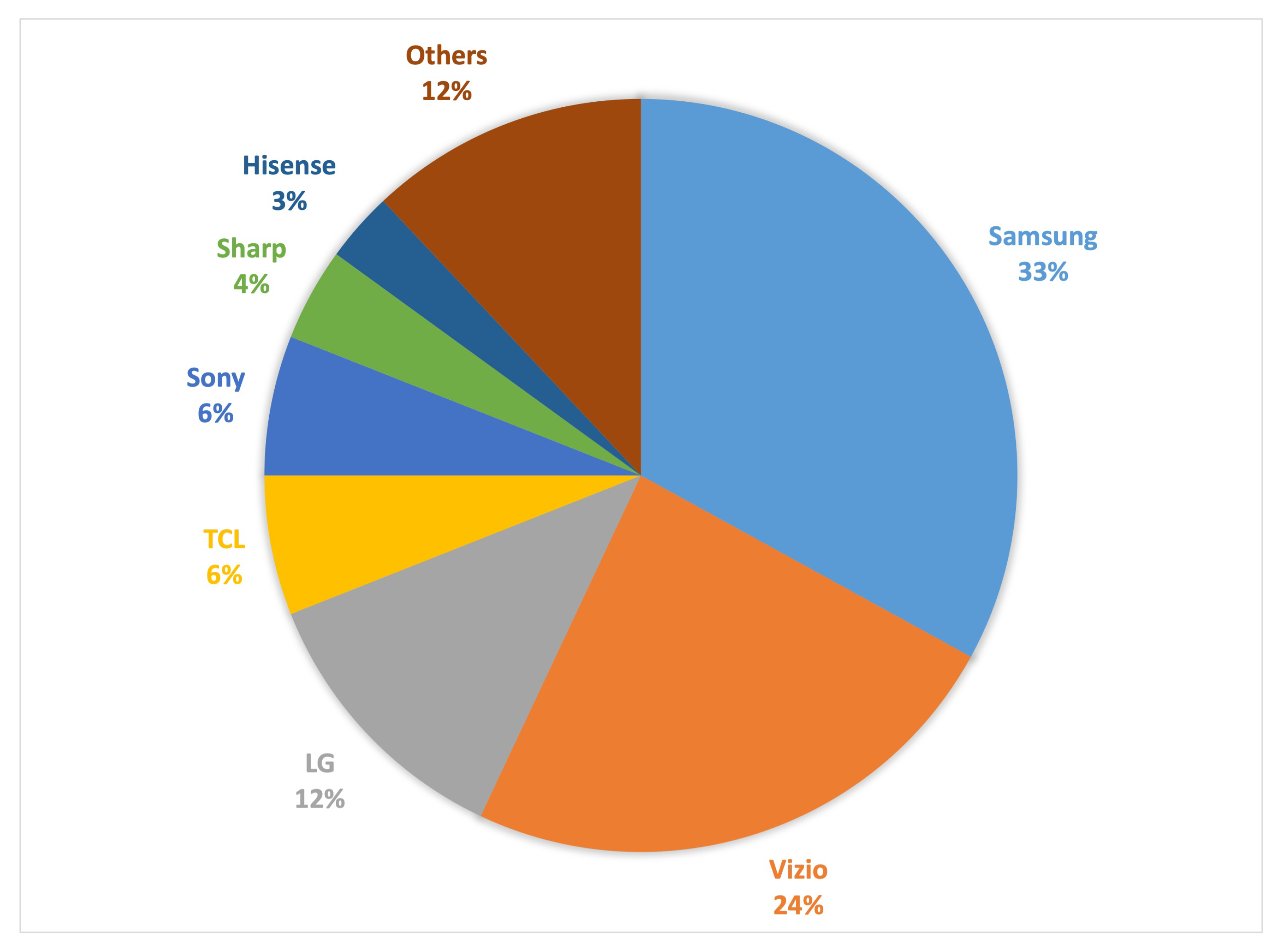
- Department, S.R. Share of Smart TVs by Manufacturer in U.S. Wi-Fi Households from 2017 to 2020. 2021. Available online: https://www.statista.com/statistics/782217/smart-tv-share-by-oem-in-the-us/ (accessed on 13 April 2021).
- Paul Roberts, S.L. Security Holes Opened Back Door to TCL Android Smart TVs. 2021. Available online: https://securityledger.com/2020/11/security-holes-opened-back-door-to-tcl-android-smart-tvs/ (accessed on 13 April 2021).
- Richi Jennings, S.B. Disconnect Your TCL Smart TV from the Internet—NOW. 2021. Available online: https://securityboulevard.com/2020/11/disconnect-your-tcl-smart-tv-from-the-internet-now/ (accessed on 13 April 2021).
- Loi, T.; Fortinet, I. The Sony Smart TV Exploit: An Inside View of Hijacking Your Living Room. 2021. Available online: https://www.fortinet.com/blog/threat-research/sony-smart-tv-exploit-inside-view-hijacking-your-living-room (accessed on 13 April 2021).
- Tara Seals, T. Android-Based Sony Smart-TVs Open to Image Pilfering. 2021. Available online: https://threatpost.com/android-sony-smart-tvs/144133/ (accessed on 13 April 2021).
- Openlgtv. Available online: http://openlgtv.org.ru/wiki/index.php/Wiki_index (accessed on 30 September 2018).
- Kuipers, R.; Starck, E.; Heikkinen, H. Smart TV Hacking: Crash Testing Your Home Entertainment. 2012. Available online: https://www.yumpu.com/en/document/view/33718312/smart-tv-hacking-crash-testing-your-home-codenomicon (accessed on 13 April 2021).
- Majchrowicz, M.; Kapusta, P.; Faustryjak, D.; Jackowska-Strumillo, L. System for remote parental control and management of rooted smart TVs. In Proceedings of the International Interdisciplinary PhD Workshop (IIPhDW), Swinoujscie, Poland, 9–12 May 2018; pp. 357–360. [Google Scholar] [CrossRef]
- Majchrowicz, M.; Kapusta, P.; Jackowska-Strumillo, L. Application of Different Kinds of Interfaces in Modern Devices for Taking Care of People. In Proceedings of the 11th International Conference on Human System Interaction (HSI), Gdansk, Poland, 4–6 July 2018; pp. 207–213. [Google Scholar] [CrossRef]
- Grattafiori, A.; Yavor, J. The outer limits: Hacking the Samsung Smart TV. Blackhat USA. 2013. Available online: https://infocondb.org/con/black-hat/black-hat-usa-2013/the-outer-limits-hacking-the-samsung-smart-tv (accessed on 13 April 2021).
- Majchrowicz, M.; Kapusta, P. Rooting Smart TVs by exploiting design flaws in application framework. In Proceedings of the International Interdisciplinary PhD Workshop 2017; 2017; pp. 8–14. [Google Scholar]
- Smit, L. What Does Your Television Know about You. 2015. Available online: https://www.semanticscholar.org/paper/What-Does-Your-Television-Know-About-You-Smit/cce770c96595ff53ce15a483d0ff9b471f575d8b (accessed on 13 April 2021).
- DoctorBeet. LG Smart TVs Logging USB Filenames and Viewing info to LG Servers. 2013. Available online: http://doctorbeet.blogspot.com/2013/11/lg-smart-tvs-logging-usb-filenames-and.html (accessed on 13 April 2021).
- Crossley, D. Samsung’s Listening TV Is Proof That Tech Has Outpaced Our Rights. 2015. Available online: https://www.theguardian.com/media-network/2015/feb/13/samsungs-listening-tv-tech-rights (accessed on 13 April 2021).
- Gross, G. WikiLeaks’ CIA document dump shows agency can compromise Android TVs. PC World 2017, 24, 08131384. [Google Scholar]
- Welt, N. Weeping Angel: The Latest Surveillance Tool, That Can Turn Your Smart TV into a Bug TV. 2017. Available online: http://mastersofmedia.hum.uva.nl/blog/2017/09/25/weeping-angel-cia-bug-smart-tv/ (accessed on 13 April 2021).
- Munro, K. Is Your Smart TV Listening to You?—Update. 2015. Available online: https://www.pentestpartners.com/security-blog/is-your-samsung-tv-listening-to-you-update/ (accessed on 13 April 2021).
- Oren, Y.; Keromytis, A.D. From the aether to the ethernet—Attacking the internet using broadcast digital television. In Proceedings of the 23rd {USENIX} Security Symposium ({USENIX} Security 14), San Diego, CA, USA, 20–22 August 2014; pp. 353–368. [Google Scholar]
- Bachy, Y.; Basse, F.; Nicomette, V.; Alata, E.; Kaániche, M.; Courrége, J.; Lukjanenko, P. Smart-TV Security Analysis: Practical Experiments. In Proceedings of the 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Rio de Janeiro, Brazil, 22–25 June 2015; pp. 497–504. [Google Scholar] [CrossRef] [Green Version]
- Michéle, B.; Karpow, A. Watch and be watched: Compromising all Smart TV generations. In Proceedings of the IEEE 11th Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2014; pp. 351–356. [Google Scholar] [CrossRef] [Green Version]
- Travis, G. Emulating Usb Dfu to Capture Firmware. 2012. Available online: http://travisgoodspeed.blogspot.com/2012/10/emulating-usb-dfu-to-capture-firmware.html (accessed on 13 April 2021).
- Sidiropoulos, N.; Stefopoulos, P. Smart tv hacking. Res. Proj. 2013, 1, 2012–2013. [Google Scholar]
- Bachy, Y.; Nicomette, V.; Kaâniche, M.; Alata, E. Smart-TV security: Risk analysis and experiments on Smart-TV communication channels. J. Comput. Virol. Hacking Tech. 2019, 15, 61–76. [Google Scholar] [CrossRef] [Green Version]
- Chernyshev, M.; Hannay, P. Security assessment of IoT devices: The case of two smart TVs. In Proceedings of the 13th Australian Digital Forensics Conference, Perth, Western Australia, 30 November–2 December 2015; pp. 85–94. [Google Scholar] [CrossRef]
- Niemietz, M.; Somorovsky, J.; Mainka, C.; Schwenk, J. Not so Smart: On Smart TV Apps. In Proceedings of the 2015 International Workshop on Secure Internet of Things (SIoT), Vienna, Austria, 21–25 September 2015; pp. 72–81. [Google Scholar] [CrossRef]
- Wang, X. Research Of Security Strengthen Tactics Based On Smart Tv Os. J. Investig. Med. 2015, 63, S32. [Google Scholar]
- j00ru. Unexported SSDT Functions Finding Method. 2009. Available online: https://j00ru.vexillium.org/2009/11/unexported-ssdt-functions-finding-method/ (accessed on 13 April 2021).
- Suiche, M. Windows Vista 64bits and Unexported Kernel Symbols. 2007. Available online: https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.174.2486&rep=rep1&type=pdf (accessed on 13 April 2021).
- Leeqwind. From CVE-2017-0263 to Windows Menu Management Component. 2018. Available online: https://xiaodaozhi.com/exploit/117.html (accessed on 13 April 2021).
- Jurczyk, M. One Font Vulnerability to Rule Them All. 2015. Available online: https://j00ru.vexillium.org/talks/recon-one-font-vulnerability-to-rule-them-all/ (accessed on 13 April 2021).
- Leclercq, M. Firmware Authentication and Deciphering for Secure TV Receiver. U.S. Patent 9,177,152, 11 March 2015. [Google Scholar]
- Johnson, H.; Gu, Y.X.; Wiener, M. Securing Accessible Systems Using Dynamic Data Mangling. U.S. Patent 9,698,973, 4 July 2017. [Google Scholar]
- Andriesse, D. Practical Binary Analysis: Build Your Own Linux Tools for Binary Instrumentation, Analysis, and Disassembly; no starch press; 2018; pp. 31–55. [Google Scholar]
- Free Software Foundation. GCC Online Documentation; Free Software Foundation: Boston, MA, USA, 2020. [Google Scholar]
- Wired. U.S. Declares iPhone Jailbreaking Legal, Over Apple’s Objections. 2018. Available online: https://www.wired.com/2010/07/feds-ok-iphone-jailbreaking/ (accessed on 13 April 2021).
- ComputerWeekly. Apple iPhone Jailbreaking Is ’Okay under EU Law’. ComputerWeekly. Available online: https://www.computerweekly.com/news/1280093396/Apple-iPhone-jailbreaking-is-okay-under-EU-law (accessed on 13 April 2021).
- Bishop, M. About Penetration Testing. IEEE Secur. Priv. 2007, 5, 84–87. [Google Scholar] [CrossRef]
- Bertoglio, D.; Zorzo, A. Overview and open issues on penetration test. J. Braz. Comput. Soc. 2017, 23. [Google Scholar] [CrossRef] [Green Version]
- Zhao, J.J.; Zhao, S.Y.; Zhao, S.Y. Opportunities and threats: A security assessment of state e-government websites. Gov. Inf. Q. 2010, 27, 49–56. [Google Scholar] [CrossRef]
- Cavusoglu, H.; Cavusoglu, H.; Raghunathan, S. Efficiency of Vulnerability Disclosure Mechanisms to Disseminate Vulnerability Knowledge. IEEE Trans. Softw. Eng. 2007, 33, 171–185. [Google Scholar] [CrossRef]
- Ding, A.Y.; De Jesus, G.L.; Janssen, M. Ethical Hacking for Boosting IoT Vulnerability Management: A First Look into Bug Bounty Programs and Responsible Disclosure; ICTRS ’19; Association for Computing Machinery: New York, NY, USA, 2019; pp. 49–55. [Google Scholar] [CrossRef] [Green Version]
- Ķinis, U. From Responsible Disclosure Policy (RDP) towards State Regulated Responsible Vulnerability Disclosure Procedure (hereinafter—RVDP): The Latvian approach. Comput. Law Secur. Rev. 2018, 34, 508–522. [Google Scholar] [CrossRef]
- Qualsys. Heap-Based Buffer Overflow in Sudo. Available online: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt (accessed on 16 April 2021).


| Method of Resolving Missings Symbols | Does Method Work across Different Firmware Versions (Including Future Ones) | Does Method Require Changes in Code and Recompilation in Order to Support New Firmwares | Is Method Capable of Recovering All of Missing Symbols |
|---|---|---|---|
| Hardcoding functions offsets | No | Yes | Yes |
| Using relative offset to known symbols | No | Yes | No |
| Finding functions with specific binary values | Yes | No | No |
| Finding functions with specific string references | Yes | No | No |
| Providing symbol files for known fw versions | No | Yes | Yes |
| Developed framework | Yes | No | Yes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Majchrowicz, M.; Duch, P. Automatic Symbol Resolution on Embedded Platforms by the Example of Smart TV Device. Appl. Sci. 2021, 11, 3674. https://doi.org/10.3390/app11083674
Majchrowicz M, Duch P. Automatic Symbol Resolution on Embedded Platforms by the Example of Smart TV Device. Applied Sciences. 2021; 11(8):3674. https://doi.org/10.3390/app11083674
Chicago/Turabian StyleMajchrowicz, Michał, and Piotr Duch. 2021. "Automatic Symbol Resolution on Embedded Platforms by the Example of Smart TV Device" Applied Sciences 11, no. 8: 3674. https://doi.org/10.3390/app11083674






