Chaotic Discrete Fractional-Order Food Chain Model and Hybrid Image Encryption Scheme Application
Abstract
1. Introduction
2. Preliminaries
3. Discrete-Time Fractional-Order Food Chain Model
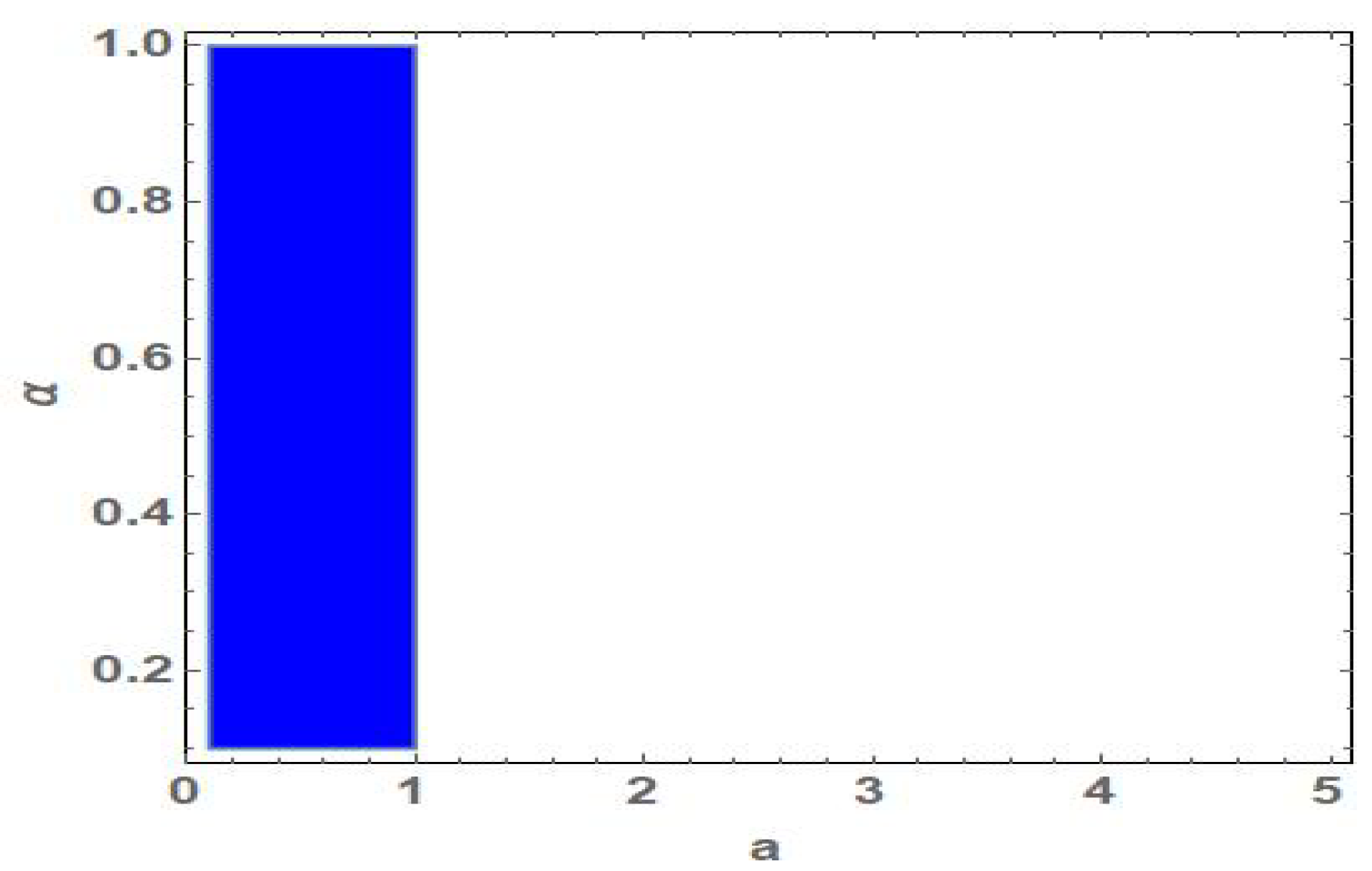
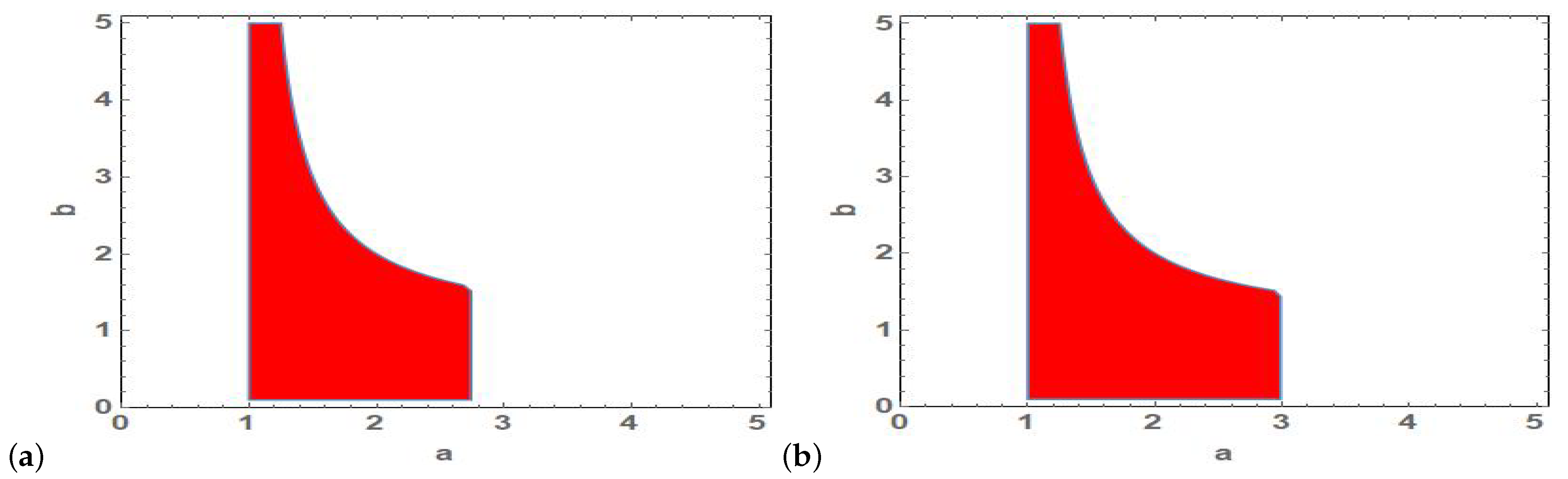
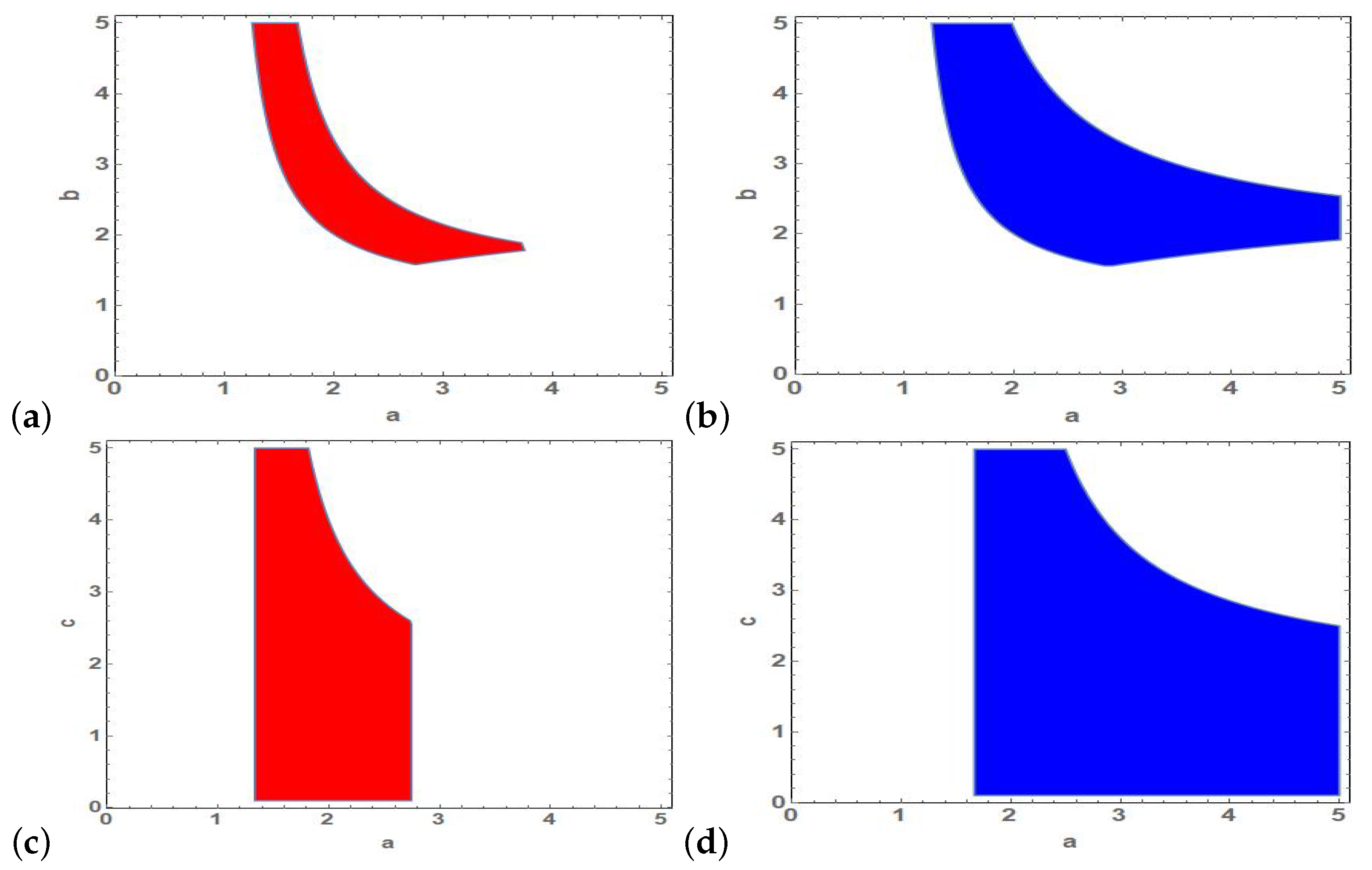
3.1. Stability of Fixed Points
3.1.1. Stability Analysis of
3.1.2. Stability Analysis of
3.1.3. Stability Analysis of
3.1.4. Stability Analysis of
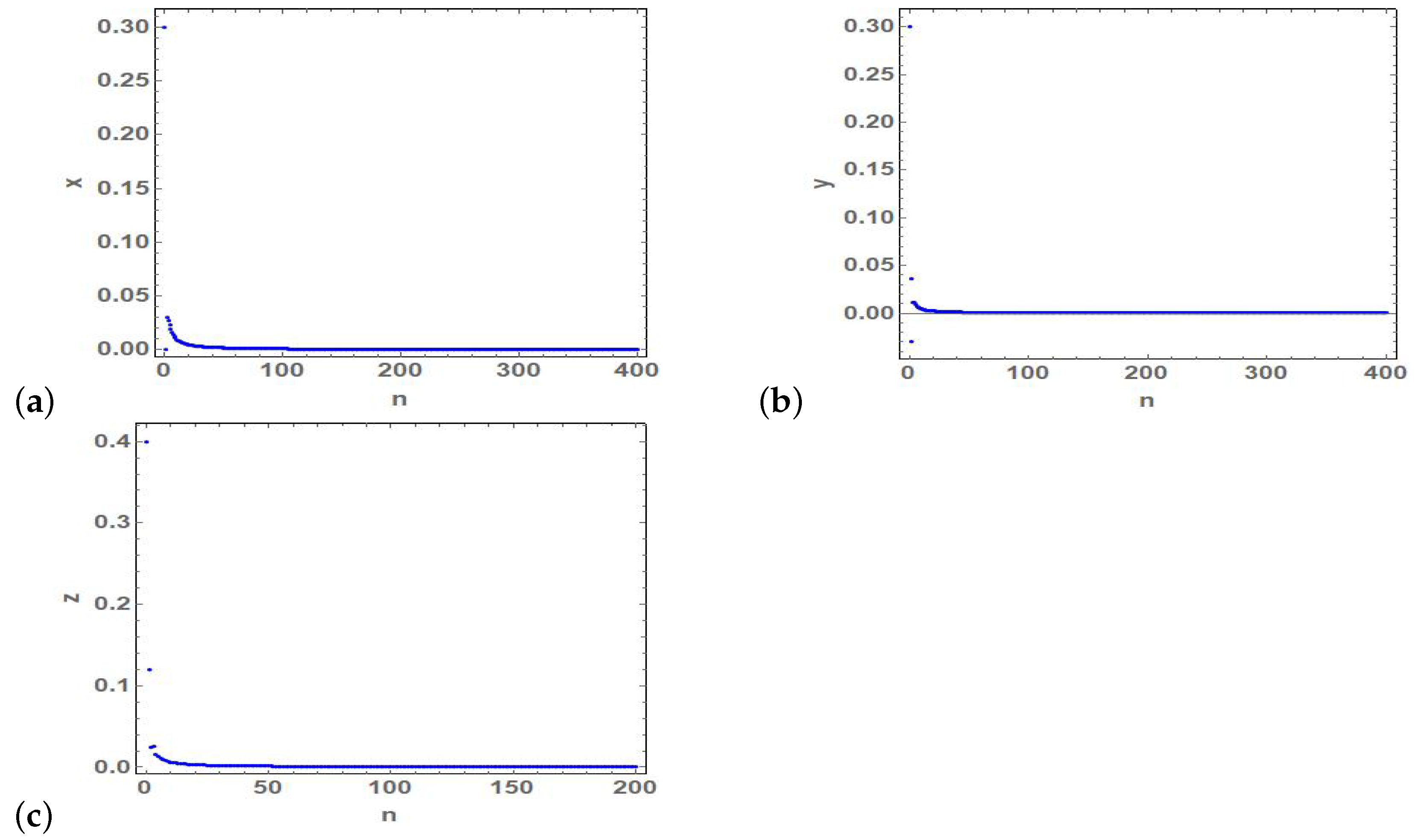
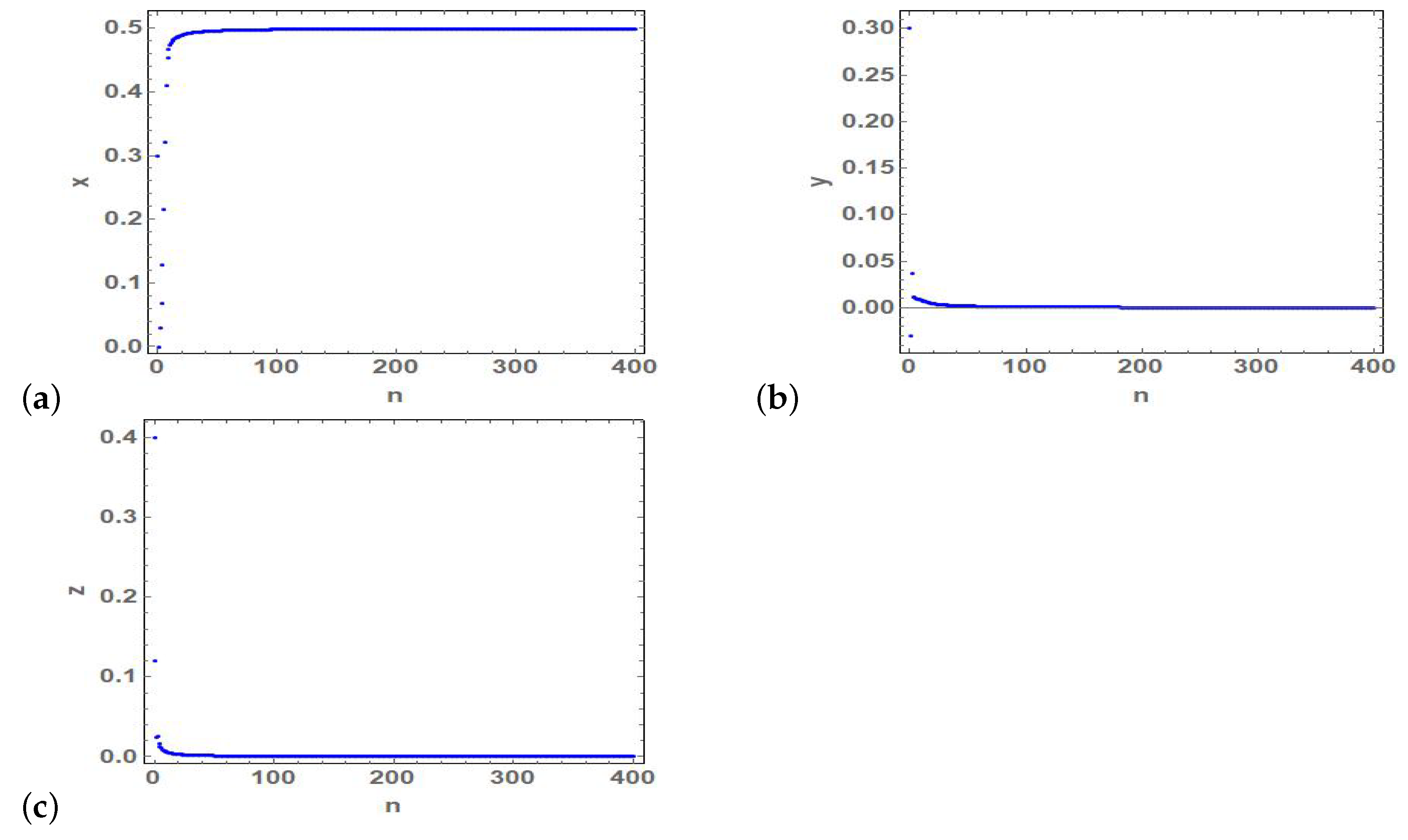
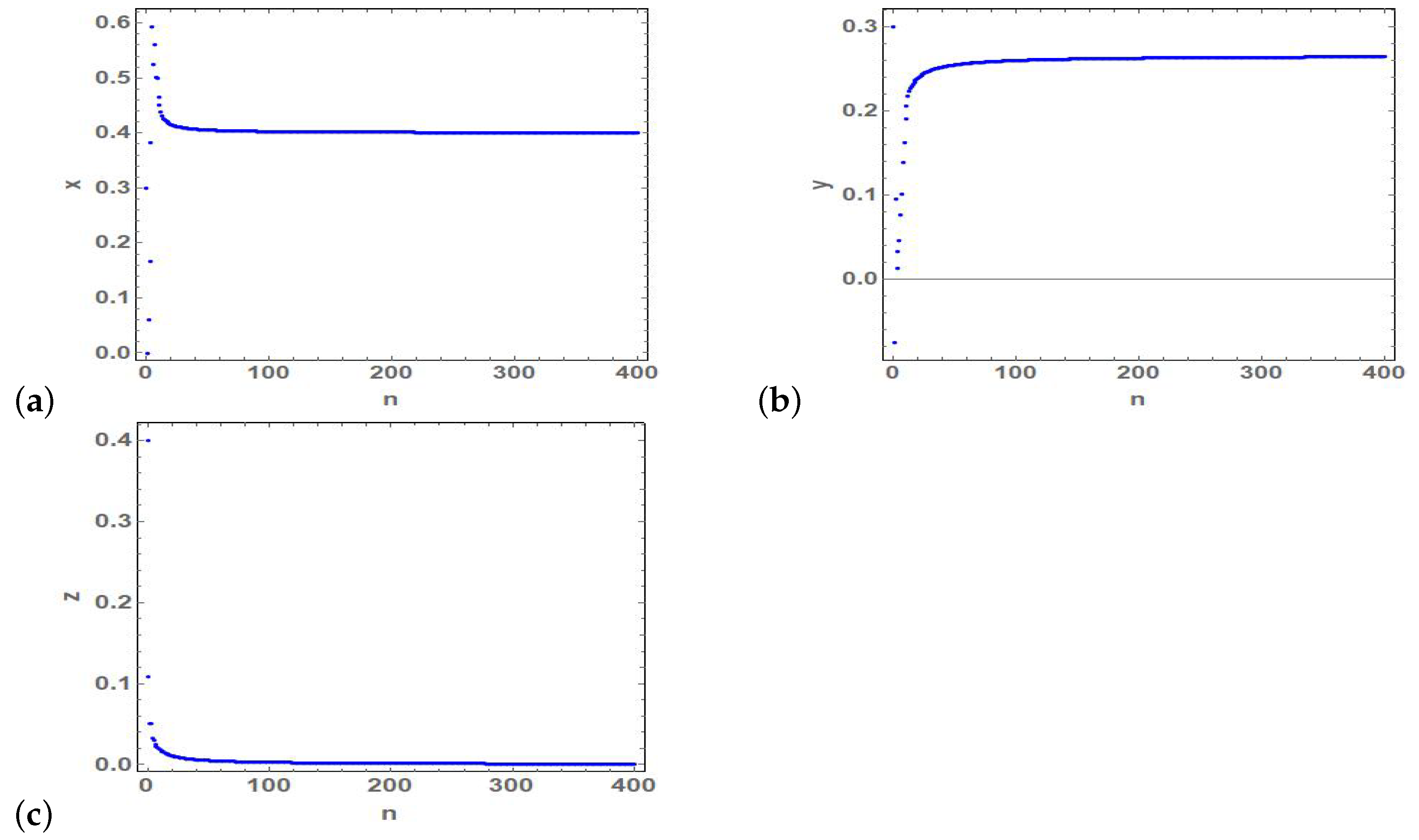
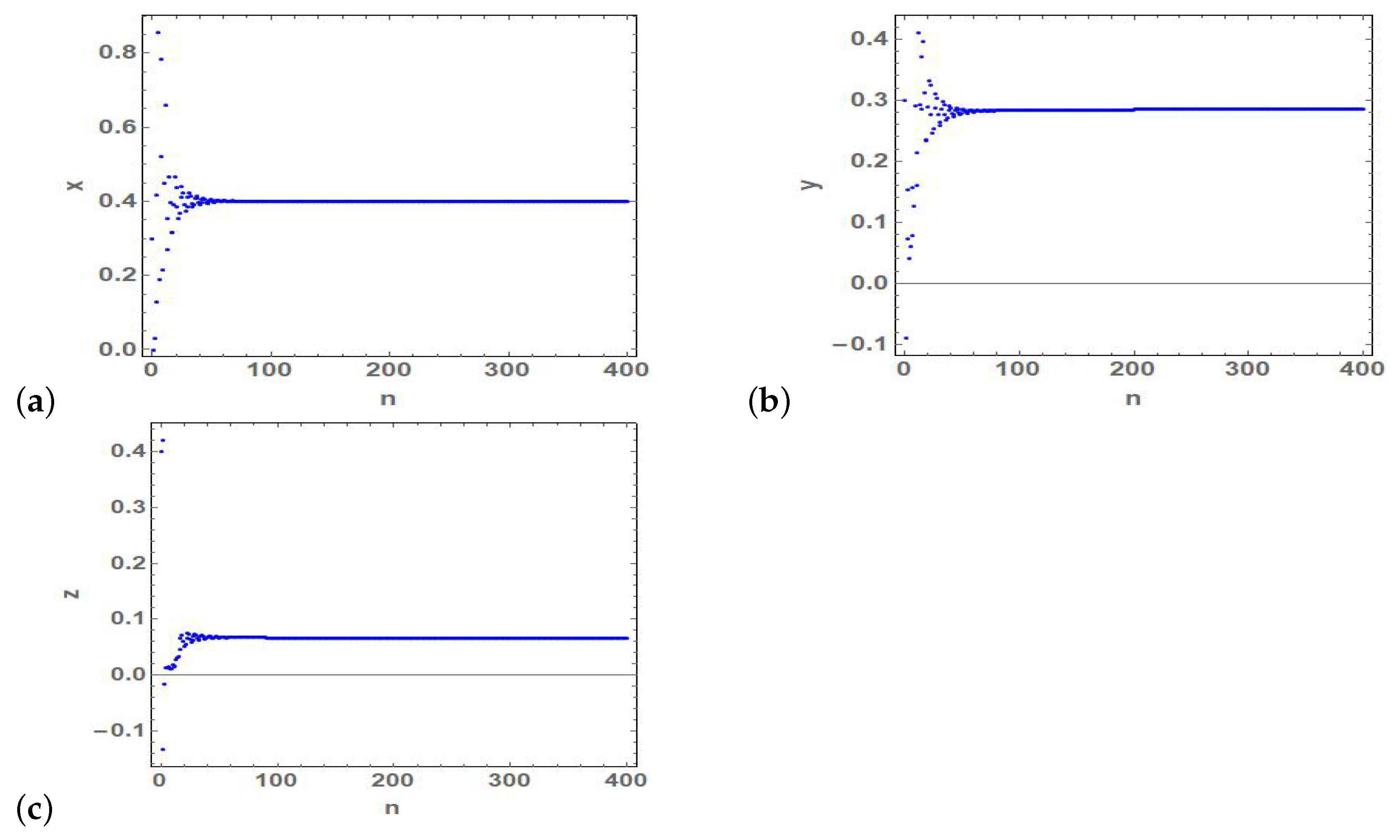
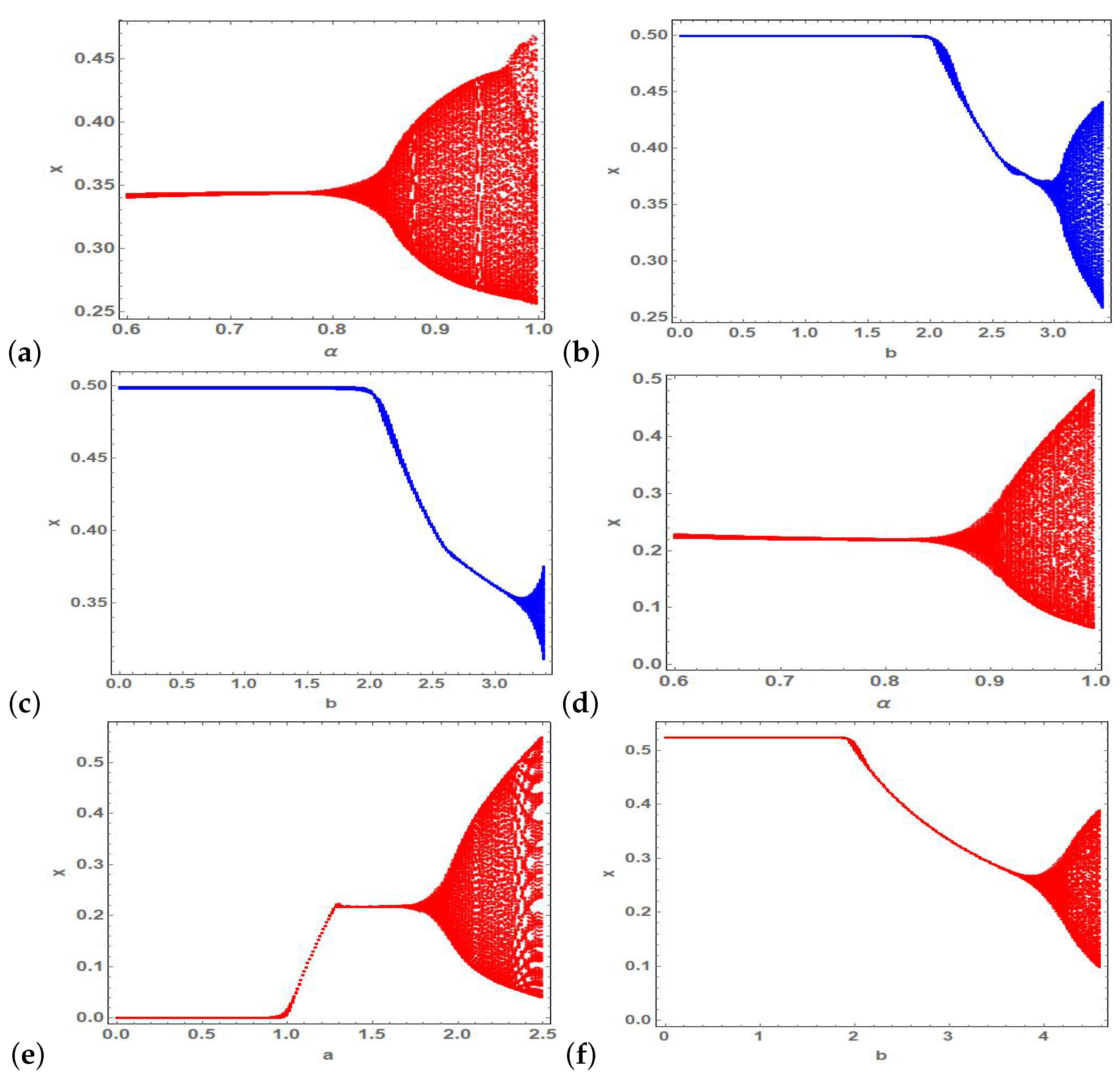
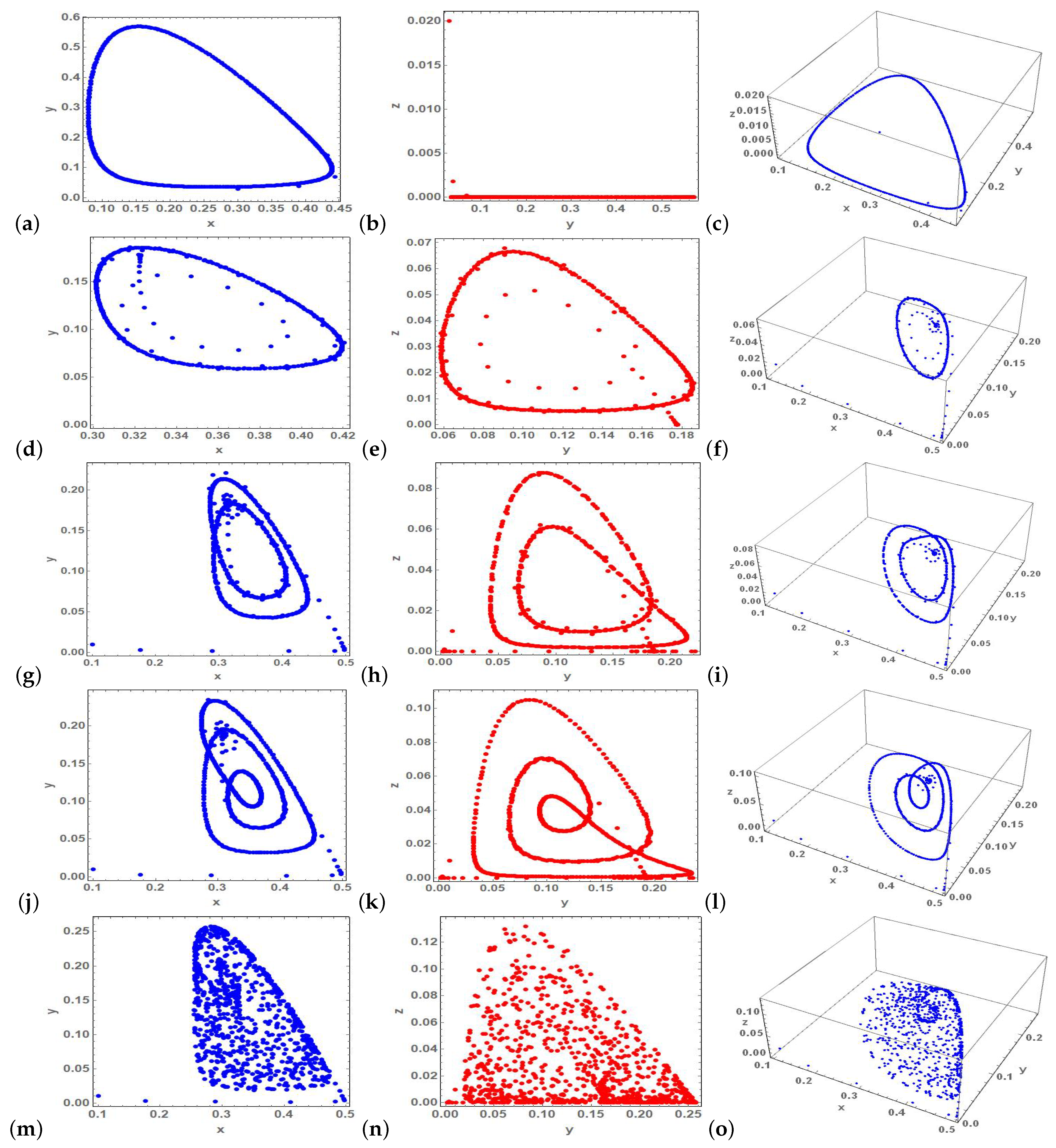
4. Numerical Simulations
5. Hybrid Image Encryption Scheme
6. Security Analysis of the Proposed Scheme
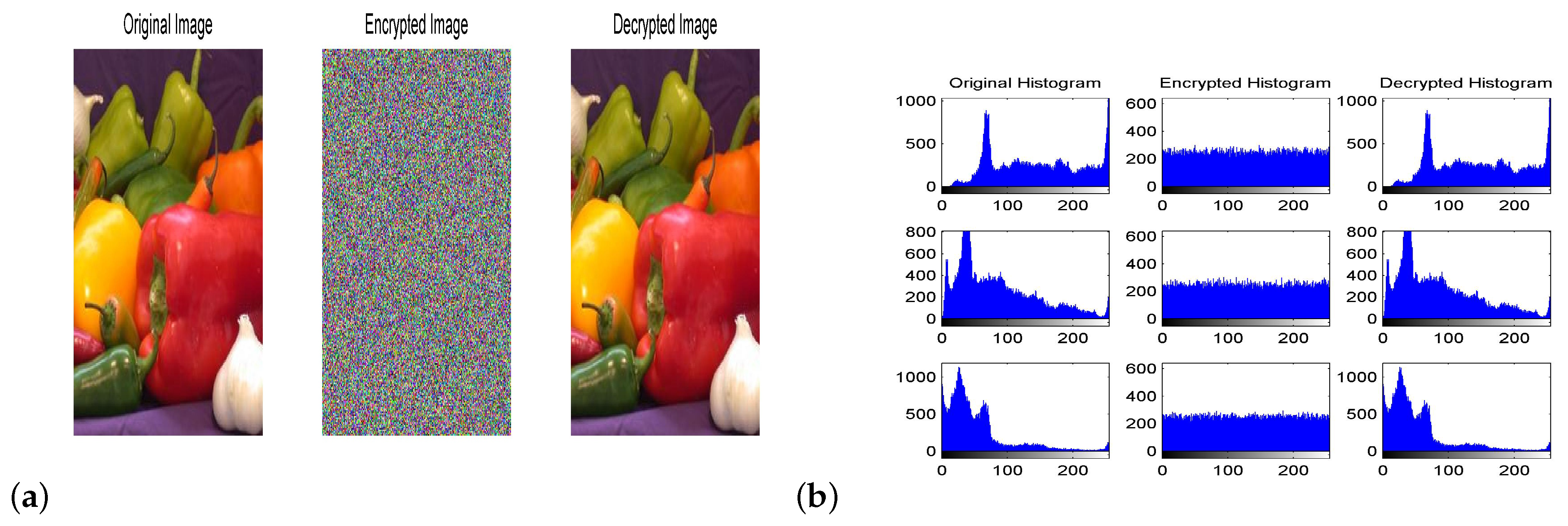
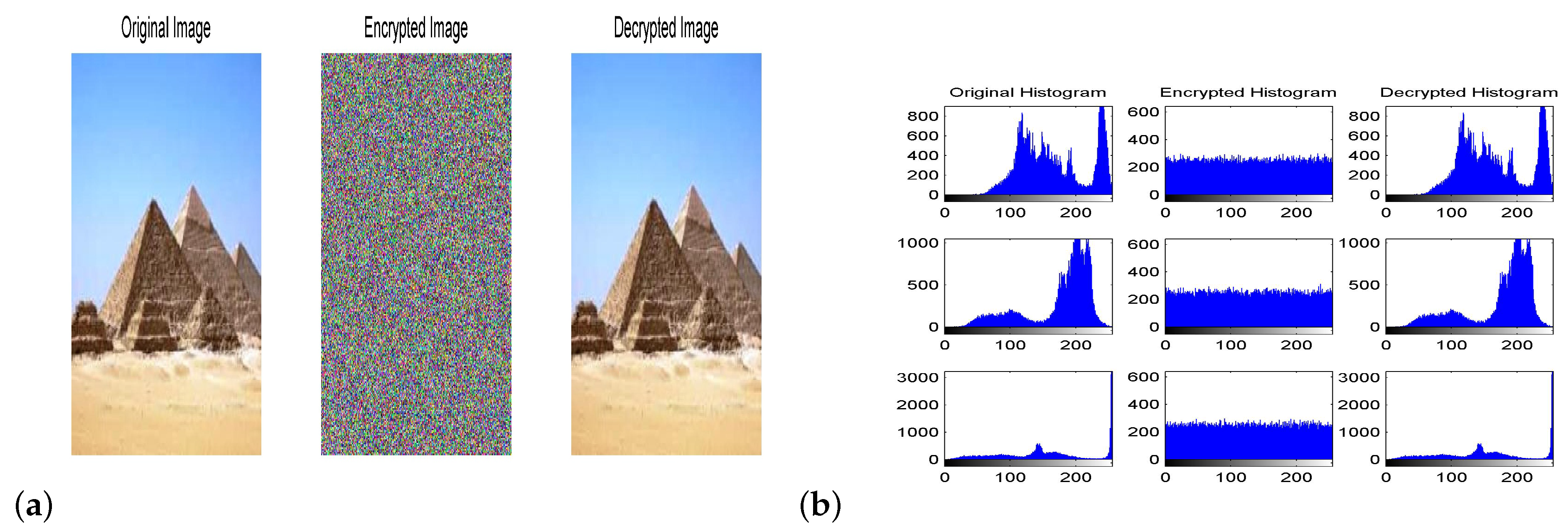
6.1. Numerical Simulations
6.2. Keyspace Analysis
6.3. Analysis of Key Sensitivity
6.4. Analysis of Information Entropy
6.5. Differential Attacks Analysis
6.6. Resistance against Other Attacks
7. Discussion and Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Hilfer, R. Applications of Fractional Calculus in Physics; World Scientific: Singapore, 2000. [Google Scholar]
- Podlubny, I. Fractional Differential Equations: An Introduction to Fractional Derivatives; Elsevier: Amsterdam, The Netherlands, 1998. [Google Scholar]
- Baleanu, D.; Güvenç, Z.B.; Machado, J.T. (Eds.) New Trends in Nanotechnology and Fractional Calculus Applications; Springer: New York, NY, USA, 2010. [Google Scholar]
- Freeborn, T.J. A survey of fractional-order circuit models for biology and biomedicine. IEEE J. Emerg. Sel. Top. Circuits Syst. 2013, 3, 416–424. [Google Scholar] [CrossRef]
- Chen, W.C. Nonlinear dynamics and chaos in a fractional-order financial system. Chaos Solitons Fractals 2008, 36, 1305–1314. [Google Scholar] [CrossRef]
- Tarasova, V.V.; Tarasov, V.E. Elasticity for economic processes with memory: Fractional differential calculus approach. Fractional Differential Calc. 2016, 6, 219–232. [Google Scholar] [CrossRef]
- Magin, R.L. Fractional calculus models of complex dynamics in biological tissues. Comput. Math. Appl. 2010, 59, 1586–1593. [Google Scholar] [CrossRef]
- Hartley, T.T.; Lorenzo, C.F.; Qammer, H.K. Chaos in a fractional order Chua’s system. IEEE Trans. Circuits Syst. Fundam. Appl. 1995, 42, 485–490. [Google Scholar] [CrossRef]
- Yu, Y.; Li, H.X.; Wang, S.; Yu, J. Dynamic analysis of a fractional-order Lorenz chaotic system. Chaos Solitons Fractals 2009, 42, 1181–1189. [Google Scholar] [CrossRef]
- He, S.; Sun, K.; Wang, H. Complexity analysis and DSP implementation of the fractional-order Lorenz hyperchaotic system. Entropy 2015, 17, 8299–8311. [Google Scholar] [CrossRef]
- Sun, K.; Wang, X.; Sprott, J.C. Bifurcations and chaos in fractional-order simplified Lorenz system. Int. J. Bifurc. Chaos 2010, 20, 1209–1219. [Google Scholar] [CrossRef]
- Li, C.; Chen, G. Chaos in the fractional order Chen system and its control. Chaos Solitons Fractals 2004, 22, 549–554. [Google Scholar] [CrossRef]
- Wang, J.; Xiong, X.; Zhang, Y. Extending synchronization scheme to chaotic fractional-order Chen systems. Phys. Stat. Mech. Appl. 2006, 370, 279–285. [Google Scholar] [CrossRef]
- Liu, W.; Chen, Z. Dynamical behaviour of fractional-order atmosphere-soil-land plant carbon cycle system. AIMS Math. 2020, 5, 1532. [Google Scholar] [CrossRef]
- Li, Z.; Liu, L.; Dehghan, S.; Chen, Y.; Xue, D. A review and evaluation of numerical tools for fractional calculus and fractional order controls. Int. J. Control 2017, 90, 1165–1181. [Google Scholar] [CrossRef]
- Wang, Z.; Wang, Z.; Wu, B. September. Control and synchronization of fractional order complex valued chaotic Chen systems. J. Phys. Conf. Ser. 2018, 1074, 012101. [Google Scholar] [CrossRef]
- Song, C.; Fei, S.; Cao, J.; Huang, C. Robust synchronization of fractional-order uncertain chaotic systems based on output feedback sliding mode control. Mathematics 2019, 7, 599. [Google Scholar] [CrossRef]
- Li, G.; Zhang, X.; Yang, H. Numerical Analysis, Circuit Simulation, and Control Synchronization of Fractional-Order Unified Chaotic System. Mathematics 2019, 7, 1077. [Google Scholar] [CrossRef]
- Alizadeh, S.; Baleanu, D.; Rezapour, S. Analyzing transient response of the parallel RCL circuit by using the Caputo—Fabrizio fractional derivative. Adv. Differ. Equ. 2020, 2020, 55. [Google Scholar] [CrossRef]
- Wu, G.C.; Deng, Z.G.; Baleanu, D.; Zeng, D.Q. New variable-order fractional chaotic systems for fast image encryption. Chaos Interdiscip. J. Nonlinear Sci. 2019, 29, 083103. [Google Scholar] [CrossRef]
- Tsirimokou, G.; Psychalinos, C.; Elwakil, A. Design of CMOS Analog Integrated Fractional-Order Circuits: Applications in Medicine and Biology; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Zhang, Y.; Liu, X.; Belic, M.R.; Zhong, W.; Zhang, Y.; Xiao, M. Propagation dynamics of a light beam in a fractional Schrodinger equation. Phys. Rev. Lett. 2015, 115, 180403. [Google Scholar] [CrossRef]
- Zhang, Y.; de Araujo, C.B.; Eyler, E.E. Higher-order correlation on polarization beats in Markovian stochastic fields. Phys. Rev. A 2001, 63, 043802. [Google Scholar] [CrossRef]
- Zhang, Y.; Gan, C.; Song, J.; Yu, X.; Ma, R.; Ge, H.; Li, C.; Lu, K. Coherent laser control in attosecond sum-frequency polarization beats using twin noisy driving fields. Phys. Rev. A 2005, 71, 023802. [Google Scholar] [CrossRef]
- Wu, G.C.; Baleanu, D. Discrete fractional logistic map and its chaos. Nonlinear Dyn. 2014, 75, 283–287. [Google Scholar] [CrossRef]
- Edelman, M.; Tarasov, V.E. Fractional standard map. Phys. Lett. A 2009, 374, 279–285. [Google Scholar] [CrossRef]
- Khennaoui, A.A.; Ouannas, A.; Bendoukha, S.; Wang, X.; Pham, V.T. On chaos in the fractional-order discrete-time unified system and its control synchronization. Entropy 2018, 20, 530. [Google Scholar] [CrossRef] [PubMed]
- Liu, Y. Chaotic synchronization between linearly coupled discrete fractional Hénon maps. Indian J. Phys. 2016, 90, 313–317. [Google Scholar] [CrossRef]
- Shukla, M.K.; Sharma, B.B. Investigation of chaos in fractional order generalized hyperchaotic Henon map. AEU Int. J. Electron. Commun. 2017, 78, 265–273. [Google Scholar] [CrossRef]
- Ji, Y.; Lai, L.; Zhong, S.; Zhang, L. Bifurcation and chaos of a new discrete fractional-order logistic map. Commun. Nonlinear Sci. Numer. Simul. 2018, 57, 352–358. [Google Scholar] [CrossRef]
- Fridrich, J. Image encryption based on chaotic maps. In Proceedings of the 1997 IEEE International Conference on Systems, Man, and Cybernetics. Computational Cybernetics and Simulation, Orlando, FL, USA, 12–15 October 1997; Volume 2, pp. 1105–1110. [Google Scholar]
- Lian, S.; Sun, J.; Wang, Z. Security analysis of a chaos-based image encryption algorithm. Phys. Stat. Mech. Appl. 2005, 351, 645–661. [Google Scholar] [CrossRef]
- Wang, X.; Liu, L. Cryptanalysis of a parallel sub-image encryption method with high-dimensional chaos. Nonlinear Dyn. 2013, 73, 795–800. [Google Scholar] [CrossRef]
- Tong, X.J. The novel bilateral–Diffusion image encryption algorithm with dynamical compound chaos. J. Syst. Softw. 2012, 85, 850–858. [Google Scholar] [CrossRef]
- Seyedzadeh, S.M.; Mirzakuchaki, S. A fast color image encryption algorithm based on coupled two-dimensional piecewise chaotic map. Signal Process. 2012, 92, 1202–1215. [Google Scholar] [CrossRef]
- Machado, J.A. Discrete-time fractional-order controllers. Fract. Calc. Appl. Anal. 2001, 4, 47–66. [Google Scholar]
- Wu, G.C.; Baleanu, D. Chaos synchronization of the discrete fractional logistic map. Signal Process. 2014, 102, 96–99. [Google Scholar] [CrossRef]
- Wu, G.C.; Baleanu, D.; Zeng, S.D. Discrete chaos in fractional sine and standard maps. Phys. Lett. A 2014, 378, 484–487. [Google Scholar] [CrossRef]
- Hu, T. Discrete chaos in fractional Hénon map. Appl. Math. 2014, 5, 2243–2248. [Google Scholar] [CrossRef]
- Abdeljawad, T. Different type kernel h- fractional differences and their fractional h- sums. Chaos Solitons Fractals 2018, 116, 146–156. [Google Scholar] [CrossRef]
- Khennaoui, A.A.; Ouannas, A.; Bendoukha, S.; Grassi, G.; Lozi, R.P.; Pham, V.T. On fractional—Order discrete—Time systems: Chaos, stabilization and synchronization. Chaos Solitons Fractals 2019, 119, 150–162. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, D. Double optical image encryption using discrete Chirikov standard map and chaos-based fractional random transform. Opt. Lasers Eng. 2013, 51, 472–480. [Google Scholar] [CrossRef]
- Diab, H. An efficient chaotic image cryptosystem based on simultaneous permutation and diffusion operations. IEEE Access 2018, 6, 42227–42244. [Google Scholar] [CrossRef]
- Annaby, M.H.; Rushdi, M.A.; Nehary, E.A. Color image encryption using random transforms, phase retrieval, chaotic maps, and diffusion. Opt. Lasers Eng. 2018, 103, 9–23. [Google Scholar] [CrossRef]
- Qumsieh, R.; Farajallah, M.; Hamamreh, R. Joint block and stream cipher based on a modified skew tent map. Multimed. Tools Appl. 2019, 78, 33527–33547. [Google Scholar] [CrossRef]
- Wang, H.; Xiao, D.; Chen, X.; Huang, H. Cryptanalysis and enhancements of image encryption using combination of the 1D chaotic map. Signal Process. 2018, 144, 444–452. [Google Scholar] [CrossRef]
- Abdeljawad, T.; Banerjee, S.; Wu, G.C. Discrete tempered fractional calculus for new chaotic systems with short memory and image encryption. Optik 2019, 218, 163698. [Google Scholar] [CrossRef]
- Ridha, M.J. Image Scramble based on Discrete Cosine Transform and Henon Map. Iraqi J. Inf. Technol. 2019, 9, 96–107. [Google Scholar] [CrossRef]
- Deshpande, A.; Daftardar-Gejji, V. Chaos in discrete fractional difference equations. Pramana 2016, 87, 49. [Google Scholar] [CrossRef]
- Tarasova, V.V.; Tarasov, V.E. Exact discretization of an economic accelerator and multiplier with memory. Fractal Fract. 2017, 1, 6. [Google Scholar] [CrossRef]
- Girejko, E.; Pawl uszewicz, E.; Wyrwas, M. The Z-transform method for sequential fractional difference operators. In Theoretical Developments and Applications of Non-Integer Order Systems; Springer: Cham, Switzerland, 2016; pp. 57–67. [Google Scholar]
- Danca, M.F.; Feckan, M. Chaos suppression in a Gompertz-like discrete system of fractional order. arXiv 2019, arXiv:1908.11195. [Google Scholar] [CrossRef]
- Brandibur, O.; Kaslik, E.; Mozyrska, D.; Wyrwas, M. Stability of Systems of Fractional-Order Difference Equations and Applications to a Rulkov-Type Neuronal Model. In New Trends in Nonlinear Dynamics; Springer: Cham, Switzerland, 2020; pp. 305–314. [Google Scholar]
- Jouini, L.; Ouannas, A.; Khennaoui, A.A.; Wang, X.; Grassi, G.; Pham, V.T. The fractional form of a new three-dimensional generalized Hénon map. Adv. Differ. Equ. 2019, 2019, 122. [Google Scholar] [CrossRef]
- Xin, B.; Peng, W.; Kwon, Y. A fractional-order difference Cournot duopoly game with long memory. arXiv 2019, arXiv:1903.04305. [Google Scholar]
- Volterra, V. Variazioni e fluttuazioni del numero di individui in specie animali conviventi. Mem. Acad. Lincei. 1926, 2, 31–113. [Google Scholar]
- Lotka, A.J. Elements of Physical Biology; Williams and Wilkins: Baltimore, MD, USA, 1925. [Google Scholar]
- Kot, M. Elements of Mathematical Ecology; Cambridge University Press: Cambridge, MA, USA, 2001. [Google Scholar]
- Alsedà, L.; Vidiella, B.; Solé, R.; Lázaro, J.T.; Sardanyés, J. Dynamics in a time-discrete food-chain model with strong pressure on preys. Commun. Nonlinear Sci. Numer. Simul. 2020, 84, 105187. [Google Scholar] [CrossRef]
- ElGamal, T. A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 1985, 31, 469–472. [Google Scholar] [CrossRef]
- Dăscălescu, A.C.; Boriga, R. A novel pseudo-random bit generator based on a new couple of chaotic systems. Ann. Ovidius Univ. Econ. Sci. Ser. 2011, 11, 553–558. [Google Scholar]
- Norouzi, B.; Mirzakuchaki, S. A fast color image encryption algorithm based on hyper-chaotic systems. Nonlinear Dyn. 2014, 78, 995–1015. [Google Scholar] [CrossRef]
- Hu, T.; Liu, Y.; Gong, L.H.; Ouyang, C.J. An image encryption scheme combining chaos with cycle operation for DNA sequences. Nonlinear Dyn. 2017, 87, 51–66. [Google Scholar] [CrossRef]
- Luo, Y.; Du, M.; Liu, J. A symmetrical image encryption scheme in wavelet and time domain. Commun. Nonlinear Sci. Numer. Simul. 2015, 20, 447–460. [Google Scholar] [CrossRef]
- Wu, Y.; Noonan, J.P.; Agaian, S. NPCR and UACI randomness tests for image encryption. Cyber J. Multidisciplinary J. Sci. Technol. 2011, 2, 31–38. [Google Scholar]
- Zhang, Y.-Q.; Wang, X.-Y. A symmetric image encryption algorithm based on mixed linear-nonlinear coupled map lattice. Inf. Sci. 2014, 273, 329–351. [Google Scholar] [CrossRef]
- Pareek, N.K.; Patidar, V.; Sud, K.K. Cryptography using multiple one- dimensional chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 2005, 10, 715–723. [Google Scholar] [CrossRef]
- Ye, G.; Pan, C.; Huang, X.; Mei, Q. An efficient pixel-level chaotic image encryption algorithm. Nonlinear Dyn. 2018, 94, 745–756. [Google Scholar] [CrossRef]
- Wang, X.Y.; Teng, L.; Qin, X. Anovel colour image encryption algorithm based on chaos. Signal Process 2012, 92, 1101–1108. [Google Scholar] [CrossRef]
- Singh, K.M.; Singh, L.D.; Tuithung, T. Cryptanalysis of multimedia encryption using elliptic curve Cryptography. Optik 2018, 168, 370–375. [Google Scholar]
- Shanks, D. Class number, a theory of factorization, and genera. In Proceedings of the Symposia in Pure Mathematics; Number Theory Institute, State Univ. New York: Stony Brook, NY, USA, 1969; Volume XX, pp. 415–440. [Google Scholar]
- Pollard, J.M. Monte Carlo methods for index computation (mod p). Math. Comput. 1978, 32, 918–924. [Google Scholar]





| Image | |||
|---|---|---|---|
| Original King Tut | |||
| Encrypted King Tut | 289 | 293 | 278 |
| Original baboon | |||
| Encrypted baboon | 252 | 248 | 228 |
| Original pepper | |||
| Encrypted pepper | 267 | 309 | 215 |
| Original pyramids | |||
| Encrypted pyramids | 298 | 209 | 269 |
| Image | Key Value | Mismatch (%) | Average Difference (%) |
|---|---|---|---|
| King Tut | |||
| King Tut | |||
| King Tut | |||
| Baboon | |||
| Baboon | |||
| Baboon | |||
| Pepper | |||
| Pepper | |||
| Pepper | |||
| Pyramids | |||
| Pyramids | |||
| Pyramids |
| Image | Information Entropy (R) | (G) | (B) |
|---|---|---|---|
| King Tut | 7.9975 | 7.9973 | 7.9977 |
| Baboon | 7.9968 | 7.9966 | 7.9978 |
| Pepper | 7.9967 | 7.9976 | 7.9967 |
| Egyptian pyramids | 7.9972 | 7.9974 | 7.9975 |
| Image | NPCR (R, G, B) % | UACI (R, G, B) % |
|---|---|---|
| King Tut | 99.6268, 99.6402, 99.6361 | 33.531, 33.531, 33.533 |
| Baboon | 99.6332, 99.6329, 99.6241 | 33.537, 33.536, 33.536 |
| Pepper | 99.6112, 99.6351, 99.6293 | 33.528, 33.506, 33.511 |
| Egyptian pyramids | 99.6339, 99.6383, 99.6154 | 33.471, 33.483, 33.485 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Askar, S.; Al-khedhairi, A.; Elsonbaty, A.; Elsadany, A. Chaotic Discrete Fractional-Order Food Chain Model and Hybrid Image Encryption Scheme Application. Symmetry 2021, 13, 161. https://doi.org/10.3390/sym13020161
Askar S, Al-khedhairi A, Elsonbaty A, Elsadany A. Chaotic Discrete Fractional-Order Food Chain Model and Hybrid Image Encryption Scheme Application. Symmetry. 2021; 13(2):161. https://doi.org/10.3390/sym13020161
Chicago/Turabian StyleAskar, Sameh, Abdulrahman Al-khedhairi, Amr Elsonbaty, and Abdelalim Elsadany. 2021. "Chaotic Discrete Fractional-Order Food Chain Model and Hybrid Image Encryption Scheme Application" Symmetry 13, no. 2: 161. https://doi.org/10.3390/sym13020161
APA StyleAskar, S., Al-khedhairi, A., Elsonbaty, A., & Elsadany, A. (2021). Chaotic Discrete Fractional-Order Food Chain Model and Hybrid Image Encryption Scheme Application. Symmetry, 13(2), 161. https://doi.org/10.3390/sym13020161






