Blockchain-Assisted Self-Sovereign Identities on Education: A Survey
Abstract
1. Introduction
- We present a detailed review of blockchain-assisted self-sovereign identity (Ba-SSI) in education, developing a structured taxonomy that categorizes and evaluates existing approaches, their unique innovations, and their relevance to academic identity management systems.
- We identify and analyze critical risks and challenges in current academic identity management systems, such as data privacy concerns, scalability issues, and barriers to user acceptance, while exploring how Ba-SSI can address these challenges and its inherent limitations.
- We investigate how blockchain and SSI can resolve long-standing problems in identity management, including data breaches, lack of transparency, and operational inefficiencies, while acknowledging that Ba-SSI is not a one-size-fits-all solution.
- We highlight pressing concerns that warrant further exploration, such as scalability, privacy-preserving techniques, and user adoption, offering a roadmap for future research in this area.
2. Background
2.1. Digital Identity in Principle
2.2. Identity Management Model
2.3. Self-Sovereign Identity Management Model
2.3.1. SSI Attributes
Decentralized Identifiers (DIDs)
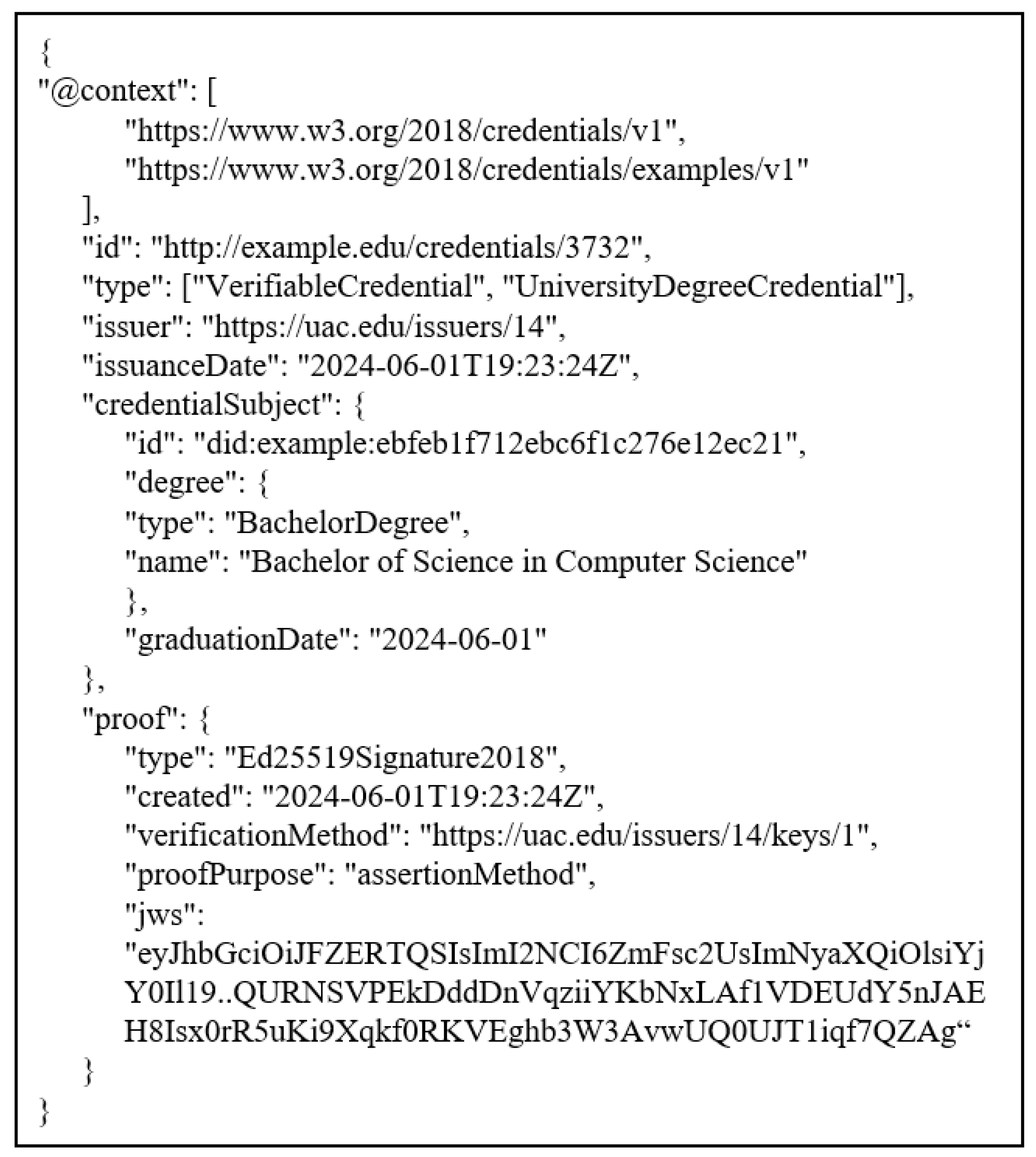
Verifiable Credentials (VCs)
Cryptographic Key Management
Decentralized Storage
Blockchain Technology
2.3.2. Cryptographic Techniques in Formalizing Self-Sovereign Identity
Multi-Party Computation (MPC)
- InitializationAssume there are n parties: . Each party holds a private input, denoted as .
- Input SharingEach party splits its input into shares. For example, with input might create shares . The shares are distributed among all parties such that no single party can reconstruct the original input. This can be done using any technique, such as SSS.
- Computation PhaseThe parties perform computations using their shares. The function f is executed on the shares rather than the original inputs. This computation can be done using secure function evaluation techniques, ensuring that intermediate results do not reveal information about the inputs.
- Output SharingAfter the computation, the parties combine their shares to reconstruct the output. The outputs are denoted as . The outputs are derived from the computation of the private inputs, ensuring that each participant received results without exposing their individual inputs.
Shamir’s Secret Sharing Scheme (SSS)
- Secret initializationLet us assume the secret to be shared is a private key or a sensitive piece of identity data.
- Polynomial creationThe secret S is encoded as the constant term of a polynomial of degree . For a threshold k, the polynomial could be = S + + + …+ where , ,…, are random coefficients.
- Generating sharesCompute n shares by evaluating the polynomial at n distinct points. Each share is a pair (, ).
Attribute-Based Encryption (ABE)
Zero-Knowledge Proofs (ZKPs)
3. Current Education Systems Landscape
3.1. The Importance of Education Recognition Verification
3.2. Characteristics of Current Education System
3.3. Challenges in Traditional Education Credential Issuance and Verification
- I.
- Governance and Adoption
3.3.1. Bureaucratic Process and Control
3.3.2. Inconsistent Standards
3.3.3. Fraud and Counterfeiting
- II.
- Technical and Infrastructure
3.3.4. Lack of Interoperability
3.3.5. Technological Barriers
3.3.6. Legacy Systems and Infrastructures
- III.
- Data and Privacy
3.3.7. Data Fragmentation
3.3.8. Privacy and Security Concerns
3.3.9. Time-Consuming Processes
3.3.10. High Administration Costs
4. Ba-SSI Enhancing Security and Data Sovereignty in Education Management System
4.1. Decentralised Identifiers (DIDs) in Education
4.1.1. Verifiable Credentials
4.1.2. Trusted Peer-to-Peer Relationships
4.2. Secure Storage of Student Data
4.2.1. Create Backup and Redundancy
4.2.2. Protect Data Privacy and Security
4.2.3. Enhance Storage Scalability
4.3. Energy Consumption and Cost Implications of Blockchain
4.3.1. Infrastructure Costs
4.3.2. Transaction Fees
4.3.3. Cost–Benefit Analysis
4.4. Blockchain-Assisted SSI Systems
4.5. Balancing Privacy Protection and Data-Sharing Transparency
5. Ba-SSI Deployment Challenges and Risk
5.1. Cyberthreats Impact
5.2. Scalability Issues
5.3. Privacy Risks
5.4. Data Retention Risks
5.5. Interoperability Issues
5.6. Governance and Compliance Issues
5.7. Staff Malfeasance
5.8. Technical Complexities Risks
5.9. Ethical Considerations Beyond Technical Safeguards
6. Future Work
6.1. Establish of Supervision
6.2. Establish of Standardization
6.3. Integration with Other Technologies
6.4. Enhance User Experience and Adoption
6.5. Improve Interoperability
6.6. Fostering Governance and Regulatory Alignment
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Liu, H.; Li, K.; Chen, Y.; Luo, X.R. Is personally identifiable information really more valuable? Evidence from consumers’ willingness-to-accept valuation of their privacy information. Decis. Support Syst. 2023, 173, 114010. [Google Scholar] [CrossRef]
- Ulven, J.B.; Wangen, G. A systematic review of cybersecurity risks in higher education. Future Internet 2021, 13, 39. [Google Scholar] [CrossRef]
- Sudrastawa, I.P.A.; Ayanto, K.Y.E. Sensitive Personal Data Publication on Higher Education Information System Websites in Indonesia. In Proceedings of the 2019 2nd International Conference of Computer and Informatics Engineering (IC2IE), Banyuwangi, Indonesia, 10–11 September 2019; pp. 93–98. [Google Scholar]
- Liu, S.; Ba, L. Blockchain technology and its application prospect in higher education. In Proceedings of the 13th International Conference on Education Technology and Computers, Wuhan, China, 22–25 October 2021; pp. 237–242. [Google Scholar]
- Shrestha, A.; Graham, D.M.; Dumaru, P.; Paudel, R.; Searle, K.A.; Al-Ameen, M.N. Understanding the Behavior, Challenges, and Privacy Risks in Digital Technology Use by Nursing Professionals. Proc. ACM-Hum.-Comput. Interact. 2022, 6, 1–22. [Google Scholar] [CrossRef]
- Cheesman, M. Self-sovereignty for refugees? The contested horizons of digital identity. Geopolitics 2022, 27, 134–159. [Google Scholar] [CrossRef]
- Ishmaev, G. Sovereignty, privacy, and ethics in blockchain-based identity management systems. Ethics Inf. Technol. 2021, 23, 239–252. [Google Scholar] [CrossRef] [PubMed]
- Gai, K.; Wang, S.; Zhao, H.; She, Y.; Zhang, Z.; Zhu, L. Blockchain-Based Multisignature Lock for UAC in Metaverse. IEEE Trans. Comput. Soc. Syst. 2023, 10, 2201–2213. [Google Scholar] [CrossRef]
- Alzahrani, S.; Daim, T.; Choo, K.K.R. Assessment of the blockchain technology adoption for the management of the electronic health record systems. IEEE Trans. Eng. Manag. 2022, 70, 2846–2863. [Google Scholar] [CrossRef]
- Gai, K.; She, Y.; Zhu, L.; Choo, K.K.R.; Wan, Z. A blockchain-based access control scheme for zero trust cross-organizational data sharing. ACM Trans. Internet Technol. 2023, 23, 1–25. [Google Scholar] [CrossRef]
- Gai, K.; Zhang, Y.; Qiu, M.; Thuraisingham, B. Blockchain-enabled service optimizations in supply chain digital twin. IEEE Trans. Serv. Comput. 2022, 16, 1673–1685. [Google Scholar] [CrossRef]
- Truong, V.T.; Le, L.B.; Niyato, D. Blockchain meets metaverse and digital asset management: A comprehensive survey. IEEE Access 2023, 11, 26258–26288. [Google Scholar] [CrossRef]
- Schlatt, V.; Sedlmeir, J.; Feulner, S.; Urbach, N. Designing a framework for digital KYC processes built on blockchain-based self-sovereign identity. Inf. Manag. 2022, 59, 103553. [Google Scholar] [CrossRef]
- Adamyk, B.; Benson, V.; Adamyk, O.; Liashenko, O. Risk Management in DeFi: Analyses of the Innovative Tools and Platforms for Tracking DeFi Transactions. J. Risk Financ. Manag. 2025, 18, 38. [Google Scholar] [CrossRef]
- Tan, E.; Mahula, S.; Crompvoets, J. Blockchain governance in the public sector: A conceptual framework for public management. Gov. Inf. Q. 2022, 39, 101625. [Google Scholar] [CrossRef]
- Das, D.; Banerjee, S.; Chatterjee, P.; Ghosh, U.; Biswas, U. Blockchain for intelligent transportation systems: Applications, challenges, and opportunities. IEEE Internet Things J. 2023, 10, 18961–18970. [Google Scholar] [CrossRef]
- Trequattrini, R.; Palmaccio, M.; Turco, M.; Manzari, A. The contribution of blockchain technologies to anti-corruption practices: A systematic literature review. Bus. Strategy Environ. 2022, 33, 4–18. [Google Scholar] [CrossRef]
- Amith, K.; Sanjay, H.; Mahadevan, A.; Harshita, K.; Eshwar, D.; Shastry, K.A. Performance driven Hyperledger Fabric-based blockchain framework for mass e-voting in India. Int. J. Inf. Comput. Secur. 2023, 21, 109–134. [Google Scholar] [CrossRef]
- Alamri, B.; Crowley, K.; Richardson, I. Blockchain-based identity management systems in health IoT: A systematic review. IEEE Access 2022, 10, 59612–59629. [Google Scholar] [CrossRef]
- Kapadiya, K.; Patel, U.; Gupta, R.; Alshehri, M.D.; Tanwar, S.; Sharma, G.; Bokoro, P.N. Blockchain and AI-Empowered Healthcare Insurance Fraud Detection: An Analysis, Architecture, and Future Prospects. IEEE Access 2022, 10, 79606–79627. [Google Scholar] [CrossRef]
- Kiania, K.; Jameii, S.M.; Rahmani, A.M. Blockchain-based privacy and security preserving in electronic health: A systematic review. Multimed. Tools Appl. 2023, 82, 28493–28519. [Google Scholar] [CrossRef] [PubMed]
- ITU-T FG DLT. Distributed Ledger Technology Terms and Definitions. Tech. Specif. FG DLT D1.1 2019. Available online: https://www.itu.int/en/ITU-T/focusgroups/dlt/Documents/d11.pdf (accessed on 11 December 2024).
- Queiruga-Dios, A.; Pérez, J.J.B.; Encinas, L.H. Self-Sovereign Identity in University Context. In Proceedings of the 2022 31st Conference of Open Innovations Association (FRUCT), Helsinki, Finland, 27–29 April 2022; pp. 259–264. [Google Scholar]
- Shuaib, M.; Hassan, N.H.; Usman, S.; Alam, S.; Bhatia, S.; Mashat, A.; Kumar, A.; Kumar, M. Self-sovereign identity solution for blockchain-based land registry system: A comparison. Mob. Inf. Syst. 2022, 2022, 8930472. [Google Scholar] [CrossRef]
- Große-Bölting, G.; Gerstenberger, D.; Gildehaus, L.; Mühling, A.; Schulte, C. Identity in higher computer education research: A systematic literature review. ACM Trans. Comput. Educ. 2023, 23, 1–35. [Google Scholar] [CrossRef]
- Satybaldy, A.; Ferdous, M.S.; Nowostawski, M. A taxonomy of challenges for self-sovereign identity systems. IEEE Access 2024, 12, 16151–16177. [Google Scholar] [CrossRef]
- Ye, T.; Luo, M.; Yang, Y.; Choo, K.K.R.; He, D. A Survey on Redactable Blockchain: Challenges and Opportunities. IEEE Trans. Netw. Sci. Eng. 2023, 10, 1669–1683. [Google Scholar] [CrossRef]
- Olivia, W.; Owen, S.; Anu, M.; James, M.; Jacqques, B.; Deepa, M.; Jacques, B.; Michael, M. Digital Identification: A Key to Inclusive Growth. 2019. McKinsey Global Institute. Available online: https://www.mckinsey.com/capabilities/mckinsey-digital/our-insights/digital-identification-a-key-to-inclusive-growth (accessed on 16 October 2024).
- Zhou, L.; Diro, A.; Saini, A.; Kaisar, S.; Hiep, P.C. Leveraging zero knowledge proofs for blockchain-based identity sharing: A survey of advancements, challenges and opportunities. J. Inf. Secur. Appl. 2024, 80, 103678. [Google Scholar] [CrossRef]
- Alizadeh, M.; Andersson, K.; Schelén, O. Comparative analysis of decentralized identity approaches. IEEE Access 2022, 10, 92273–92283. [Google Scholar] [CrossRef]
- Guo, Y.; Liang, H.; Zhu, L.; Gai, K. Zk-SNARKs-Based Anonymous Payment Channel in Blockchain. Blockchains 2024, 2, 20–39. [Google Scholar] [CrossRef]
- Yildiz, H.; Ritter, C.; Nguyen, L.T.; Frech, B.; Martinez, M.M.; Küpper, A. Connecting self-sovereign identity with federated and user-centric identities via saml integration. In Proceedings of the 2021 IEEE Symposium on Computers and Communications (ISCC), Athens, Greece, 5–8 September 2021; pp. 1–7. [Google Scholar]
- Mahnamfar, A.; Bicakci, K.; Uzunay, Y. ROSTAM: A passwordless web single sign-on solution mitigating server breaches and integrating credential manager and federated identity systems. Comput. Secur. 2024, 139, 103739. [Google Scholar] [CrossRef]
- Glöckler, J.; Sedlmeir, J.; Frank, M.; Fridgen, G. A systematic review of identity and access management requirements in enterprises and potential contributions of self-sovereign identity. Bus. Inf. Syst. Eng. 2024, 66, 421–440. [Google Scholar] [CrossRef]
- Sousa, P.R.; Resende, J.S.; Martins, R.; Antunes, L. The case for blockchain in IoT identity management. J. Enterp. Inf. Manag. 2022, 35, 1477–1505. [Google Scholar] [CrossRef]
- Van Delft, B.; Oostdijk, M. A security analysis of OpenID. In Proceedings of the IFIP Working Conference on Policies and Research in Identity Management, Oslo, Norway, 18–19 November 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 73–84. [Google Scholar]
- Recordon, D.; Reed, D. OpenID 2.0: A platform for user-centric identity management. In Proceedings of the Second ACM workshop on Digital Identity Management, Alexandria, VA, USA, 3 November 2006; ACM: New York, NY, USA, 2006; pp. 11–16. [Google Scholar]
- Sucasas, V.; Mantas, G.; Radwan, A.; Rodriguez, J. An OAuth2-based protocol with strong user privacy preservation for smart city mobile e-Health apps. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Johnson, A.D.; Alom, I.; Xiao, Y. Rethinking Single Sign-On: A Reliable and Privacy-Preserving Alternative with Verifiable Credentials. In Proceedings of the 10th ACM Workshop on Moving Target Defense, Copenhagen, Denmark, 26 November 2023; ACM: New York, NY, USA, 2023; pp. 25–28. [Google Scholar]
- Wilson, Y.; Hingnikar, A. Solving Identity Management in Modern Applications: Demystifying OAuth 2.0, OpenID Connect, and SAML 2.0; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Lyastani, S.G.; Schilling, M.; Neumayr, M.; Backes, M.; Bugiel, S. Is FIDO2 the kingslayer of user authentication? A comparative usability study of FIDO2 passwordless authentication. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 268–285. [Google Scholar]
- Mahdad, A.T.; Jubur, M.; Saxena, N. Breaching Security Keys without Root: FIDO2 Deception Attacks via Overlays exploiting Limited Display Authenticators. In Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, UT, USA, 14–18 October 2024; pp. 1686–1700. [Google Scholar]
- Kumar, A.; Saha, R.; Conti, M.; Kumar, G.; Buchanan, W.J.; Kim, T.H. A comprehensive survey of authentication methods in Internet-of-Things and its conjunctions. J. Netw. Comput. Appl. 2022, 204, 103414. [Google Scholar] [CrossRef]
- Bendiab, G.; Shiaeles, S.; Boucherkha, S.; Ghita, B. FCMDT: A novel fuzzy cognitive maps dynamic trust model for cloud federated identity management. Comput. Secur. 2019, 86, 270–290. [Google Scholar] [CrossRef]
- Golla, M.; Ho, G.; Lohmus, M.; Pulluri, M.; Redmiles, E.M. Driving 2FA Adoption at Scale: Optimizing Two-Factor Authentication Notification Design Patterns. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Virtual Event, 11–13 August 2021; pp. 109–126. [Google Scholar]
- Lewis, K.D. Web single sign-on authentication using SAML. arXiv 2009, arXiv:0909.2368. [Google Scholar]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-preserving energy trading using consortium blockchain in smart grid. IEEE Trans. Ind. Inform. 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Grüner, A.; Mühle, A.; Meinel, C. An integration architecture to enable service providers for self-sovereign identity. In Proceedings of the 2019 IEEE 18th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 26–28 September 2019; pp. 1–5. [Google Scholar]
- Moreno, R.T.; García-Rodríguez, J.; Bernabé, J.B.; Skarmeta, A. A Trusted Approach for Decentralised and Privacy-Preserving Identity Management. IEEE Access 2021, 9, 105788–105804. [Google Scholar] [CrossRef]
- Schardong, F.; Custódio, R. Self-Sovereign Identity: A Systematic Review, Mapping and Taxonomy. Sensors 2022, 22, 5641. [Google Scholar] [CrossRef]
- Zeydan, E.; Blanco, L.; Mangues-Bafalluy, J.; Arslan, S.S.; Turk, Y.; Yadav, A.K.; Liyanage, M. Blockchain-based self-sovereign identity: Taking control of identity in federated learning. IEEE Open J. Commun. Soc. 2024, 5, 5764–5781. [Google Scholar] [CrossRef]
- Sporny, M.; Longley, D.; Sabadello, M.; Reed, D.; Steele, O.; Allen, A. Decentralized Identifiers (DIDs) v1.0: Core Architecture, Data Model, and Representations. 2022. Available online: https://www.w3.org/TR/did-1.0/ (accessed on 16 May 2023).
- Xie, T.; Zhang, Y.; Gai, K.; Xu, L. Cross-chain-based decentralized identity for mortgage loans. In Proceedings of the Knowledge Science, Engineering and Management: 14th International Conference, KSEM 2021, Tokyo, Japan, 14–16 August 2021; Proceedings, Part III 14. Springer: Berlin/Heidelberg, Germany, 2021; pp. 619–633. [Google Scholar]
- Sober, M.; Scaffino, G.; Schulte, S. Cross-blockchain communication using Oracles with an off-chain aggregation mechanism based on zk-SNARKs. Distrib. Ledger Technol. Res. Pract. 2024, 3, 1–24. [Google Scholar] [CrossRef]
- Lin, C.; Luo, M.; Huang, X.; Choo, K.K.R.; He, D. An efficient privacy-preserving credit score system based on noninteractive zero-knowledge proof. IEEE Syst. J. 2021, 16, 1592–1601. [Google Scholar] [CrossRef]
- Athalye, A.; Kaashoek, M.F.; Zeldovich, N. Verifying hardware security modules with Information-Preserving refinement. In Proceedings of the 16th USENIX Symposium on Operating Systems Design and Implementation (OSDI 22), Carlsbad, CA, USA, 11–13 July 2022; pp. 503–519. [Google Scholar]
- Tessaro, S.; Zhu, C. Threshold and multi-signature schemes from linear hash functions. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Cham, Switzerland, 2023; pp. 628–658. [Google Scholar]
- Daniel, E.; Tschorsch, F. IPFS and friends: A qualitative comparison of next generation peer-to-peer data networks. IEEE Commun. Surv. Tutor. 2022, 24, 31–52. [Google Scholar] [CrossRef]
- Zhang, Y.; Gai, K.; Xiao, J.; Zhu, L.; Choo, K.K.R. Blockchain-empowered efficient data sharing in Internet of Things settings. IEEE J. Sel. Areas Commun. 2022, 40, 3422–3436. [Google Scholar] [CrossRef]
- Gai, K.; Guo, J.; Zhu, L.; Yu, S. Blockchain Meets Cloud Computing: A Survey. IEEE Commun. Surv. Tutor. 2020, 22, 2009–2030. [Google Scholar] [CrossRef]
- Merkle, R.C. A digital signature based on a conventional encryption function. In Conference on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1987; pp. 369–378. [Google Scholar]
- Xiao, J.; Chang, J.; Lin, L.; Li, B.; Dai, X.; Xiong, Z.; Choo, K.K.R.; Gai, K.; Jin, H. Cloak: Hiding Retrieval Information in Blockchain Systems via Distributed Query Requests. IEEE Trans. Serv. Comput. 2024, 17, 3213–3226. [Google Scholar] [CrossRef]
- Gai, K.; Hu, Z.; Zhu, L.; Wang, R.; Zhang, Z. Blockchain meets DAG: A BlockDAG consensus mechanism. In Proceedings of the Algorithms and Architectures for Parallel Processing: 20th International Conference, ICA3PP 2020, New York City, NY, USA, 2–4 October 2020; Proceedings, Part III 20. Springer: Berlin/Heidelberg, Germany, 2020; pp. 110–125. [Google Scholar]
- Malakhov, I.; Marin, A.; Rossi, S. Analysis of the confirmation time in proof-of-work blockchains. Future Gener. Comput. Syst. 2023, 147, 275–291. [Google Scholar] [CrossRef]
- Li, A.; Wei, X.; He, Z. Robust proof of stake: A new consensus protocol for sustainable blockchain systems. Sustainability 2020, 12, 2824. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. In Proceedings of the 3rd Symposium on Operting Systems Design and Implementation, OSDI ’99, New Orleans, LA, USA, 22–25 February 1999; Volume 99, pp. 173–186. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance and proactive recovery. ACM Trans. Comput. Syst. (TOCS) 2002, 20, 398–461. [Google Scholar] [CrossRef]
- Rajasekaran, A.S.; Azees, M.; Al-Turjman, F. A comprehensive survey on blockchain technology. Sustain. Energy Technol. Assess. 2022, 52, 102039. [Google Scholar] [CrossRef]
- Zhou, X.; Xu, Z.; Wang, C.; Gao, M. PPMLAC: High performance chipset architecture for secure multi-party computation. In Proceedings of the 49th Annual International Symposium on Computer Architecture, New York, NY, USA, 18–22 June 2022; pp. 87–101. [Google Scholar]
- Escudero, D.; Goyal, V.; Polychroniadou, A.; Song, Y. Turbopack: Honest majority MPC with constant online communication. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 951–964. [Google Scholar]
- Brakerski, Z.; Yuen, H. Quantum garbled circuits. In Proceedings of the 54th Annual ACM SIGACT Symposium on Theory of Computing, Rome, Italy, 20–24 June 2022; pp. 804–817. [Google Scholar]
- Zhang, J.; Cheng, X.; Yang, L.; Hu, J.; Liu, X.; Chen, K. Sok: Fully homomorphic encryption accelerators. ACM Comput. Surv. 2024, 56, 1–32. [Google Scholar] [CrossRef]
- Abram, D.; Roy, L.; Scholl, P. Succinct homomorphic secret sharing. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zurich, Switzerland, 26–30 May 2024; Springer: Cham, Switzerland, 2024; pp. 301–330. [Google Scholar]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Abbaszadeh, K.; Pappas, C.; Katz, J.; Papadopoulos, D. Zero-knowledge proofs of training for deep neural networks. In Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, UT, USA, 14–18 October 2024; pp. 4316–4330. [Google Scholar]
- Pedersen, T.P. Non-interactive and information-theoretic secure verifiable secret sharing. In Proceedings of the Annual International Cryptology Conference, Barbara, CA, USA, 11–15 August 1991; Springer: Berlin/Heidelberg, Germany, 1991; pp. 129–140. [Google Scholar]
- Schnorr, C.P. Efficient signature generation by smart cards. J. Cryptol. 1991, 4, 161–174. [Google Scholar] [CrossRef]
- Canetti, R.; Chen, Y.; Holmgren, J.; Lombardi, A.; Rothblum, G.N.; Rothblum, R.D.; Wichs, D. Fiat-Shamir: From practice to theory. In Proceedings of the 51st Annual ACM SIGACT Symposium on Theory of Computing, Phoenix, AZ, USA, 23–26 June 2019; ACM: New York, NY, USA, 2019; pp. 1082–1090. [Google Scholar]
- Bünz, B.; Bootle, J.; Boneh, D.; Poelstra, A.; Wuille, P.; Maxwell, G. Bulletproofs: Short proofs for confidential transactions and more. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 315–334. [Google Scholar]
- Ben-Sasson, E.; Chiesa, A.; Genkin, D.; Tromer, E.; Virza, M. SNARKs for C: Verifying program executions succinctly and in zero knowledge. In Proceedings of the Advances in Cryptology–CRYPTO 2013: 33rd Annual Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2013; Proceedings, Part II. Springer: Berlin/Heidelberg, Germany, 2013; pp. 90–108. [Google Scholar]
- Wei, L.; Wu, J.; Long, C. Facilitating Development of Higher Education Informatization Using Blockchain Technology. In Proceedings of the The 2022 4th International Conference on Blockchain Technology, ICBCT’22, New York, NY, USA, 25–27 March 2022; pp. 131–136. [Google Scholar] [CrossRef]
- Guillén-Gámez, F.D.; Cabero-Almenara, J.; Llorente-Cejudo, C.; Palacios-Rodríguez, A. Differential analysis of the years of experience of higher education teachers, their digital competence and use of digital resources: Comparative research methods. Technol. Knowl. Learn. 2022, 27, 1193–1213. [Google Scholar] [CrossRef]
- Chen, X.; Zou, D.; Cheng, G.; Xie, H.; Jong, M. Blockchain in smart education: Contributors, collaborations, applications and research topics. Educ. Inf. Technol. 2023, 28, 4597–4627. [Google Scholar] [CrossRef]
- Khaldi, A.; Bouzidi, R.; Nader, F. Gamification of e-learning in higher education: A systematic literature review. Smart Learn. Environ. 2023, 10, 10. [Google Scholar] [CrossRef]
- El Koshiry, A.; Eliwa, E.; Abd El-Hafeez, T.; Shams, M.Y. Unlocking the power of blockchain in education: An overview of innovations and outcomes. Blockchain Res. Appl. 2023, 4, 100165. [Google Scholar] [CrossRef]
- Rawas, S. ChatGPT: Empowering lifelong learning in the digital age of higher education. Educ. Inf. Technol. 2024, 29, 6895–6908. [Google Scholar] [CrossRef]
- Ezell, A. Degree Mills: The Billion-Dollar Industry That Has Sold Over a Million Fake Diplomas; Prometheus Books: Buffalo, NY, USA, 2012. [Google Scholar]
- Marklein, M.B. Credentials Fraud Now a Global Threat for Universities. 2016. Available online: https://www.universityworldnews.com/post.php?story=20160603175611493 (accessed on 16 September 2024).
- Haque, M.M.; Adnan, M.N.; Kabir, M.A.; Ahmmad Rashid, M.R.; Mohammad Yasin, A.S.; Pervez, M.S. An innovative approach of verification mechanism for both electronic and printed documents. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 623–627. [Google Scholar] [CrossRef]
- Eaton, S.E.; Carmichael, J.J. Fake degrees and credential fraud, contract cheating, and paper mills: Overview and historical perspectives. In Fake Degrees and Fraudulent Credentials in Higher Education; Springer: Berlin/Heidelberg, Germany, 2023; pp. 1–22. [Google Scholar]
- Ahmed, M.R.; Islam, A.M.; Shatabda, S.; Islam, S. Blockchain-Based Identity Management System and Self-Sovereign Identity Ecosystem: A Comprehensive Survey. IEEE Access 2022, 10, 113436–113481. [Google Scholar] [CrossRef]
- Sozon, M.; Alkharabsheh, O.H.M.; Fong, P.W.; Chuan, S.B. Cheating and plagiarism in higher education institutions (HEIs): A literature review. F1000Research 2024, 13, 788. [Google Scholar] [CrossRef]
- Padillah, R. Ghostwriting: A reflection of academic dishonesty in the artificial intelligence era. J. Public Health 2024, 46, e193–e194. [Google Scholar] [CrossRef] [PubMed]
- Dempere, J.; Modugu, K.; Hesham, A.; Ramasamy, L.K. The impact of ChatGPT on higher education. Front. Educ. 2023, 8, 1206936. [Google Scholar] [CrossRef]
- Hammi, B.; Zeadally, S.; Adja, Y.C.E.; Del Giudice, M.; Nebhen, J. Blockchain-based solution for detecting and preventing fake check scams. IEEE Trans. Eng. Manag. 2021, 69, 3710–3725. [Google Scholar] [CrossRef]
- Rustemi, A.; Dalipi, F.; Atanasovski, V.; Risteski, A. A systematic literature review on blockchain-based systems for academic certificate verification. IEEE Access 2023, 11, 64679–64696. [Google Scholar] [CrossRef]
- Tan, E.; Lerouge, E.; Du Caju, J.; Du Seuil, D. Verification of education credentials on European Blockchain Services Infrastructure (EBSI): Action research in a cross-border use case between Belgium and Italy. Big Data Cogn. Comput. 2023, 7, 79. [Google Scholar] [CrossRef]
- Čučko, Š.; Turkanović, M. Decentralized and self-sovereign identity: Systematic mapping study. IEEE Access 2021, 9, 139009–139027. [Google Scholar] [CrossRef]
- Alsobhi, H.A.; Alakhtar, R.A.; Ubaid, A.; Hussain, O.K.; Hussain, F.K. Blockchain-based micro-credentialing system in higher education institutions: Systematic literature review. Knowl.-Based Syst. 2023, 265, 110238. [Google Scholar] [CrossRef]
- Jayabalan, J.; Jeyanthi, N. Scalable blockchain model using off-chain IPFS storage for healthcare data security and privacy. J. Parallel Distrib. Comput. 2022, 164, 152–167. [Google Scholar] [CrossRef]
- Nadeem, N.; Hayat, M.F.; Qureshi, M.A.; Majid, M.; Nadeem, M.; Janjua, J. Hybrid Blockchain-based Academic Credential Verification System (B-ACVS). Multimed. Tools Appl. 2023, 82, 43991–44019. [Google Scholar] [CrossRef]
- Sporny, M.; Zundel, B.; Noble, G.; Burnett, D.; Longley, D. Verifiable Credentials Data Model 1.0. W3C Recommendation, W3C. 2019. Available online: https://www.w3.org/TR/2019/REC-vc-data-model-20191119/ (accessed on 11 October 2024).
- Sporny, M.; Zundel, B.; Hartog, K.D.; Noble, G.; Longley, D.; Burnett, D. Verifiable Credentials Data Model v1.1. W3C Recommendation, W3C. 2022. Available online: https://www.w3.org/TR/2022/REC-vc-data-model-20220303/ (accessed on 11 October 2024).
- Burnett, D.; Longley, D.; Noble, G.; Sporny, M.; Zundel, B.; Hartog, K.D. Verifiable Credentials Data Model v1.1. W3C Recommendation, W3C. 2021. Available online: https://www.w3.org/TR/2021/REC-vc-data-model-20211109/ (accessed on 11 October 2024).
- Al-Tawara, F.; Qasaimeh, M.; Jarad, D.; Al-Qassas, R.S. Utilizing the Blockchain Technology for Higher Education in the Era of Pandemics: A Systematic Review. In Proceedings of the 2023 14th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 21–23 November 2023; pp. 1–6. [Google Scholar]
- Yin, W. Zero-knowledge proof intelligent recommendation system to protect students’ data privacy in the digital age. Appl. Artif. Intell. 2023, 37, 2222495. [Google Scholar] [CrossRef]
- Li, H.; Han, D. EduRSS: A blockchain-based educational records secure storage and sharing scheme. IEEE Access 2019, 7, 179273–179289. [Google Scholar] [CrossRef]
- Sunny, F.A.; Hajek, P.; Munk, M.; Abedin, M.Z.; Satu, M.S.; Efat, M.I.A.; Islam, M.J. A systematic review of blockchain applications. IEEE Access 2022, 10, 59155–59177. [Google Scholar] [CrossRef]
- Bai, Y.; Lei, H.; Li, S.; Gao, H.; Li, J.; Li, L. Decentralized and self-sovereign identity in the era of blockchain: A survey. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22–25 August 2022; pp. 500–507. [Google Scholar]
- Naik, N.; Jenkins, P. uPort open-source identity management system: An assessment of self-sovereign identity and user-centric data platform built on blockchain. In Proceedings of the 2020 IEEE International Symposium on Systems Engineering (ISSE), Vienna, Austria, 12 October–12 November 2020; pp. 1–7. [Google Scholar]
- Tobin, A.; Reed, D. The inevitable Rise of Self-Sovereign Identity. Sovrin Found. 2016, 29, 18. [Google Scholar]
- Dunphy, P.; Petitcolas, F.A. A first look at identity management schemes on the blockchain. IEEE Secur. Priv. 2018, 16, 20–29. [Google Scholar] [CrossRef]
- Weigl, L.; Barbereau, T.; Fridgen, G. The construction of self-sovereign identity: Extending the interpretive flexibility of technology towards institutions. Gov. Inf. Q. 2023, 40, 101873. [Google Scholar] [CrossRef]
- Dąbrowski, M.; Pacyna, P. Blockchain-based identity discovery between heterogenous identity management systems. In Proceedings of the 2022 6th International Conference on Cryptography, Security and Privacy (CSP), Tianjin, China, 14–16 January 2022; pp. 131–137. [Google Scholar]
- Preukschat, A.; Reed, D. Self-Sovereign Identity; Manning Publications: Shelter Island, NY, USA, 2021. [Google Scholar]
- Takemiya, M.; Vanieiev, B. Sora identity: Secure, digital identity on the blockchain. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (Compsac), Tokyo, Japan, 23–27 July 2018; Volume 2, pp. 582–587. [Google Scholar]
- Kassen, M. Understanding decentralized civic engagement: Focus on peer-to-peer and blockchain-driven perspectives on e-participation. Technol. Soc. 2021, 66, 101650. [Google Scholar] [CrossRef]
- Ali, M.; Nelson, J.; Shea, R.; Freedman, M.J. Blockstack: A global naming and storage system secured by blockchains. In Proceedings of the 2016 USENIX Annual Technical Conference (USENIX ATC 16), Denver, CO, USA, 22–24 June 2016; pp. 181–194. [Google Scholar]
- Otte, P.; de Vos, M.; Pouwelse, J. TrustChain: A Sybil-resistant scalable blockchain. Future Gener. Comput. Syst. 2020, 107, 770–780. [Google Scholar] [CrossRef]
- Sguanci, C.; Spatafora, R.; Vergani, A.M. Layer 2 blockchain scaling: A survey. arXiv 2021, arXiv:2107.10881. [Google Scholar]
- Dewangan, N.K.; Chandrakar, P.; Kumari, S.; Rodrigues, J.J. Enhanced privacy-preserving in student certificate management in blockchain and interplanetary file system. Multimed. Tools Appl. 2023, 82, 12595–12614. [Google Scholar] [CrossRef]
- Wu, T.; Wang, W.; Zhang, C.; Zhang, W.; Zhu, L.; Gai, K.; Wang, H. Blockchain-based anonymous data sharing with accountability for Internet of Things. IEEE Internet Things J. 2022, 10, 5461–5475. [Google Scholar] [CrossRef]
- Cheng, W.; Ming, J.; Guilley, S.; Danger, J.L. Statistical higher-order correlation attacks against code-based masking. IEEE Trans. Comput. 2024, 73, 2364–2377. [Google Scholar] [CrossRef]
- Zhang, J.; Zha, C.; Zhang, Q.; Ma, S. A Denial-of-Service Attack Based on Selfish Mining and Sybil Attack in Blockchain Systems. IEEE Access 2024, 12, 170309–170320. [Google Scholar] [CrossRef]






| Area | Decentralized | Transparency | Security | Interoperability | Immunity | Integrity | Accountability | Privacy | Self-Governing | |
|---|---|---|---|---|---|---|---|---|---|---|
| [12] | Look into managing digital assets in the metaverse. | ☑ | ☑ | ☑ | ☑ | ☑ | ||||
| [13,14] | Leverage KYC to regulate and govern customers’ verification activities to reduce risk due to money laundering. | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | |
| [15] | Deploying blockchain-based identity management in the South Korean public sector. | ☑ | ☑ | ☑ | ☑ | ☑ | ||||
| [16] | Deploy SSI for public transportation, especially in ticketing issuance for travelling in Europe. | ☑ | ☑ | ☑ | ☑ | ☑ | ||||
| [17] | Using blockchain to fight against corruption in nurturing the business, management, and financial domains. | ☑ | ☑ | ☑ | ☑ | |||||
| [18] | Supply-chain management, voting, and government procurement. | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | |
| [19] | Looking into the potential of decentralized technology in healthcare to give patients control over their identity and health records while finding the balance of privacy and portability. | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | |
| [20,21] | Leverage on artificial intelligence to combat healthcare insurance fraud. | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | |||
| Our work | Survey into applying blockchain and with digital identities into modernizing and innovating education information systems based on the challenges encountered. Aims to fill in the gap of missing surveys that approached the feasibility and potential benefits of a blockchain-assisted SSI system in education governance | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ | ☑ |
| Abbreviation | Full Forms |
|---|---|
| SSI | Self-Sovereign Identity |
| PII | Personal Identifiable Information |
| ITU | International Telecommunication Union |
| ID | Identity |
| IdM | Identity Management Model |
| SSO | Single Sign-On |
| SAML | Security Assertion Markup Language |
| AAA | Authentication, Authorization, and Auditing |
| DID | Decentralized Identifiers |
| VC | Verifiable Credentials |
| ZKPs | Zero-Knowledge Proofs |
| HSMs | Hardware Security Modules |
| IPFS | InterPlanetary File System |
| PoS | Proof of Stake |
| PBFT | Practical Byzantine Fault Tolerance |
| NFTs | Non-Fungible Tokens |
| MPC | Multi-Party Computation |
| SSS | Shamir’s Secret Sharing |
| ABE | Attribute-based Encryption |
| zk-SNARK | Zero-Knowledge Succinct Non-Interactive Argument of Knowledge |
| IoT | Internet of Things |
| Type | Impact |
|---|---|
| Forgery of documents | Paper-based documents can be forged or altered, fake diplomas, transcripts, and certificates can be created with relative ease; advanced technology, difficult for institutions and employers to distinguish between genuine and fraudulent credentials [88]. |
| Misrepresentation of Information | Misrepresent someone’s academic achievements by altering grades, claiming unearned degrees, or providing false information about their educational background, which may lead to unqualified individuals obtaining positions or opportunities they are not entitled to [90]. |
| Credential mills/diploma mills/bogus qualifications | Some unregulated, unrecognised or unlicensed institutions, known as credential mills, produce and sell counterfeit degrees and certificates. They exploit the weaknesses in traditional verification systems, flooding the market with fake credentials and undermining the integrity of legitimate educational qualifications [91,92]. |
| Plagiarism | Presenting someone else’s work, ideas, or words as one’s own without proper attribution [93], direct copying and pasting without citation, paraphrasing, or submitting someone’s work as original. |
| Ghostwriting | Practice of hiring someone to assist in writing a book, scripts, research papers, or publications without giving credit to the actual writer, but rather submitting the work as one’s own [94], encompasses the use of AI models like OpenAI’s ChatGPT and Baidu’s Ernie. |
| Project | Open Source | Blockchain Type | Storage | Future Enhancements | Security Features | Fit for Academic Domain |
|---|---|---|---|---|---|---|
| Sovrin [112] | Yes | Public Permissioned (Hyperledger Indy) | Distributed ledger, on/off-chain storage (e.g., encrypted cloud storage) | Integration with other decentralised networks, enhance privacy features | Decentralised identity ledger, zero-knowledge proofs, strong cryptography | Excellent: Strong focus on privacy and verifiable credentials, suitable for academic certificates and transcripts |
| uPort [111] | Yes | Public (Ethereum) | On-chain for identifiers, off-chain for data (IPFS, encrypted cloud storage) | Enhanced interoperability, scalability solutions | Decentralised identifiers (DIDs), verifiable credentials, smart contracts | Good: Ethereum’s smart contracts can manage academic credentials, but scalability may be an issue |
| EverID [92] | No, proprietary | Private, proprietary | Off-chain (secure cloud storage) | Expansion into financial services and healthcare | Biometric verification, secure document storage, multi-factor authentication | Moderate: Focus is more on financial services and healthcare |
| LifeID [92] | Yes | Public (Ethereum) | On-chain for identifiers, off-chain for data (IPFS, encrypted cloud storage) | Improved privacy protocols, wider adoption | Decentralised identifiers (DIDs), verifiable credentials, smart contracts | Good: Ethereum-based solution with strong security, suitable for academic credentials |
| Sora [117] | Yes | Public (Polkadot) | On-chain for identifiers, off-chain for data (IPFS, encrypted cloud storage) | Integration with Polkadot ecosystem, more DeFi applications | Decentralised identifiers (DIDs), verifiable credentials, cross-chain identity | Good: Decentralised IDs and verifiable credentials suitable for academic records |
| SelfKey [92] | Yes | Public (Ethereum) | On-chain for identifiers, off-chain for data (IPFS, encrypted cloud storage) | Cross-chain interoperability enhanced KYC solutions | Decentralised identifiers (DIDs), verifiable credentials, hardware wallet integration | Good: Ethereum-based solution with strong identity verification features suitable for academic use |
| ShoCard [110,113] | No, proprietary | Public (Ethereum) | Off-chain (encrypted cloud storage) | Expansion into more industries, enhanced biometric authentication | Biometric verification, secure document storage, multi-factor authentication | Moderate: Primarily focused on financial services and enterprise use cases |
| WeIdentity [110] | No, proprietary | Public (Consortium, FISCO-BCOS) | On-/off-chain (consortium-managed storage) | Greater integration within the consortium blockchain, enhanced privacy, and security features | Decentralised identifiers (DIDs), verifiable credentials, consortium blockchain security | Good: Consortium blockchain offers strong security and privacy, suitable for academic records |
| Microsoft DID [110] | No, partially | Multi-chain ledger (Azure Cloud) | Off-chain | Driven by Microsoft’s roadmap | Advanced cryptographic protocols | Moderate: Strong integration but non-interoperability |
| IDchainz [92] | Yes | Proprietary | On-chain | Community-driven enhancements | Decentralised and cryptographic methods | Excellent: Customizable, flexible, and user-controlled |
| Civic [118] | No, partially | Ethereum | Off-chain with on-chain verification | Driven by Civic’s roadmap | Identity theft protection, biometrics | Moderate: Partially open source nature limits flexibility to expand |
| Blockstack [119] | Yes | Bitcoin or stacks blockchain (Ethereum) | Off-chain with on-chain verification | Community-driven integrates Web 3.0 | Strong encryption decentralised IDs | Good: Strong privacy and data sovereignty features |
| Principle | Impacts |
|---|---|
| Existence | Users have a digital presence of their identities without depending on third parties |
| Control | Users have ultimate control over their identity and data, including the ability to manage personal information |
| Access | Users can access their data and gain benefits from the solutions |
| Transparency | Systems are open, allowing users to understand how their data are managed and used |
| Persistence | Identities are long lasting and not tied to any single provider. Data must be resilient to changes in technology or service providers |
| Portability | Identities can be easily transferred across different platforms and systems |
| Interoperability | Systems can work together seamlessly, allowing identities to be widely available and recognized across different platforms |
| Consent | Users give explicit permission and have the right to grant or revoke it for data sharing and transactions. It is handled with ethics and trust in digital identity systems |
| Minimization | Only necessary data are collected, stored and shared, reducing exposure and protecting the data, which aligns closely with the applicable privacy and international or regional data-protection standards |
| Protection | Data are secured against unauthorized access and breaches |
| Product | Existence | Control | Access | Transparency | Persistence | Portability | Interoperability | Consent | Minimization | Protection |
|---|---|---|---|---|---|---|---|---|---|---|
| Sovrin | H | H | H | M | H | H | H | H | H | H |
| uPort | H | H | H | H | H | H | H | H | H | H |
| EverID | H | H | H | M | M | M | M | H | H | M |
| LifeID | H | H | H | M | H | M | M | H | H | H |
| Sora | M | M | M | M | M | M | M | M | M | M |
| SelfKey | H | H | H | M | H | H | H | H | H | H |
| Shocard | H | H | H | M | M | M | M | M | H | M |
| WeIdentity | H | H | H | M | M | M | M | H | H | M |
| Microsoft DID | H | H | H | M | H | H | H | H | H | H |
| IDchainz | H | H | H | M | H | H | H | H | H | H |
| Civic | H | H | H | M | H | M | M | H | H | M |
| Blockstack | H | H | H | H | H | H | H | H | H | H |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chan, W.; Gai, K.; Yu, J.; Zhu, L. Blockchain-Assisted Self-Sovereign Identities on Education: A Survey. Blockchains 2025, 3, 3. https://doi.org/10.3390/blockchains3010003
Chan W, Gai K, Yu J, Zhu L. Blockchain-Assisted Self-Sovereign Identities on Education: A Survey. Blockchains. 2025; 3(1):3. https://doi.org/10.3390/blockchains3010003
Chicago/Turabian StyleChan, Weilin, Keke Gai, Jing Yu, and Liehuang Zhu. 2025. "Blockchain-Assisted Self-Sovereign Identities on Education: A Survey" Blockchains 3, no. 1: 3. https://doi.org/10.3390/blockchains3010003
APA StyleChan, W., Gai, K., Yu, J., & Zhu, L. (2025). Blockchain-Assisted Self-Sovereign Identities on Education: A Survey. Blockchains, 3(1), 3. https://doi.org/10.3390/blockchains3010003








