Evaluation of Compliance Rule Languages for Modelling Regulatory Compliance Requirements
Abstract
1. Introduction
2. Research Approach
- The expressiveness in terms of the different scope (i.e., control flow, etc.) and deontic effects and modalities (i.e., obligations) of a compliance requirement as a normative construct.
- The complexity measured by metrics that help untangle the components of formulas (i.e., operands, operators) as well as the elements of graphs (i.e., nodes, edges).
- A systematic literature review and classification of business-process compliance languages.
- A practical application of typical compliance rule languages found in the literature.
- A comparison of the expressiveness and complexity for textual and visual compliance rule languages.
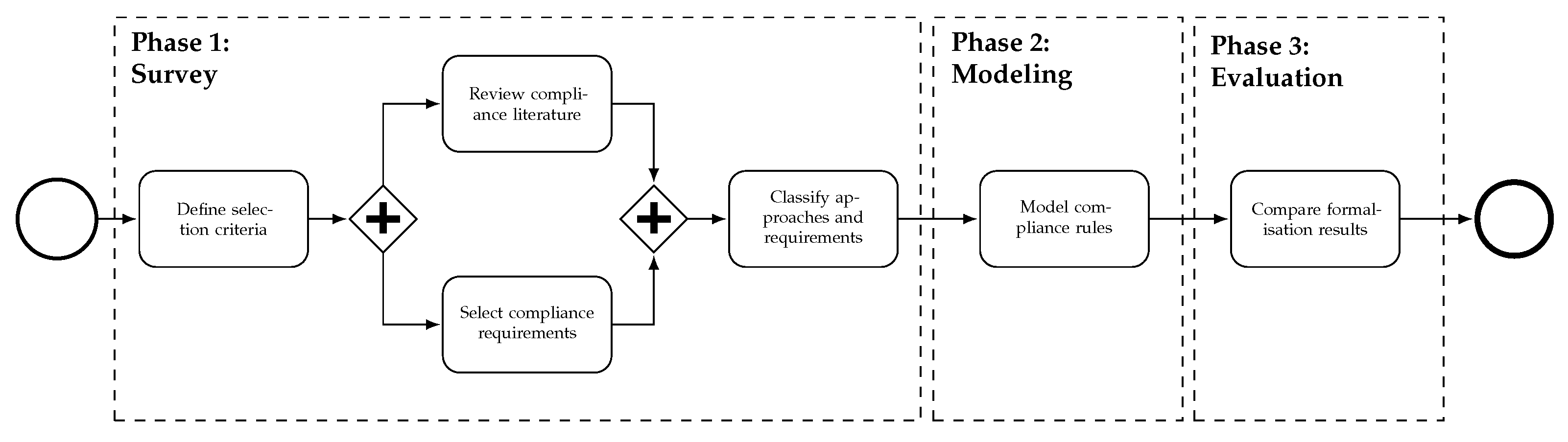
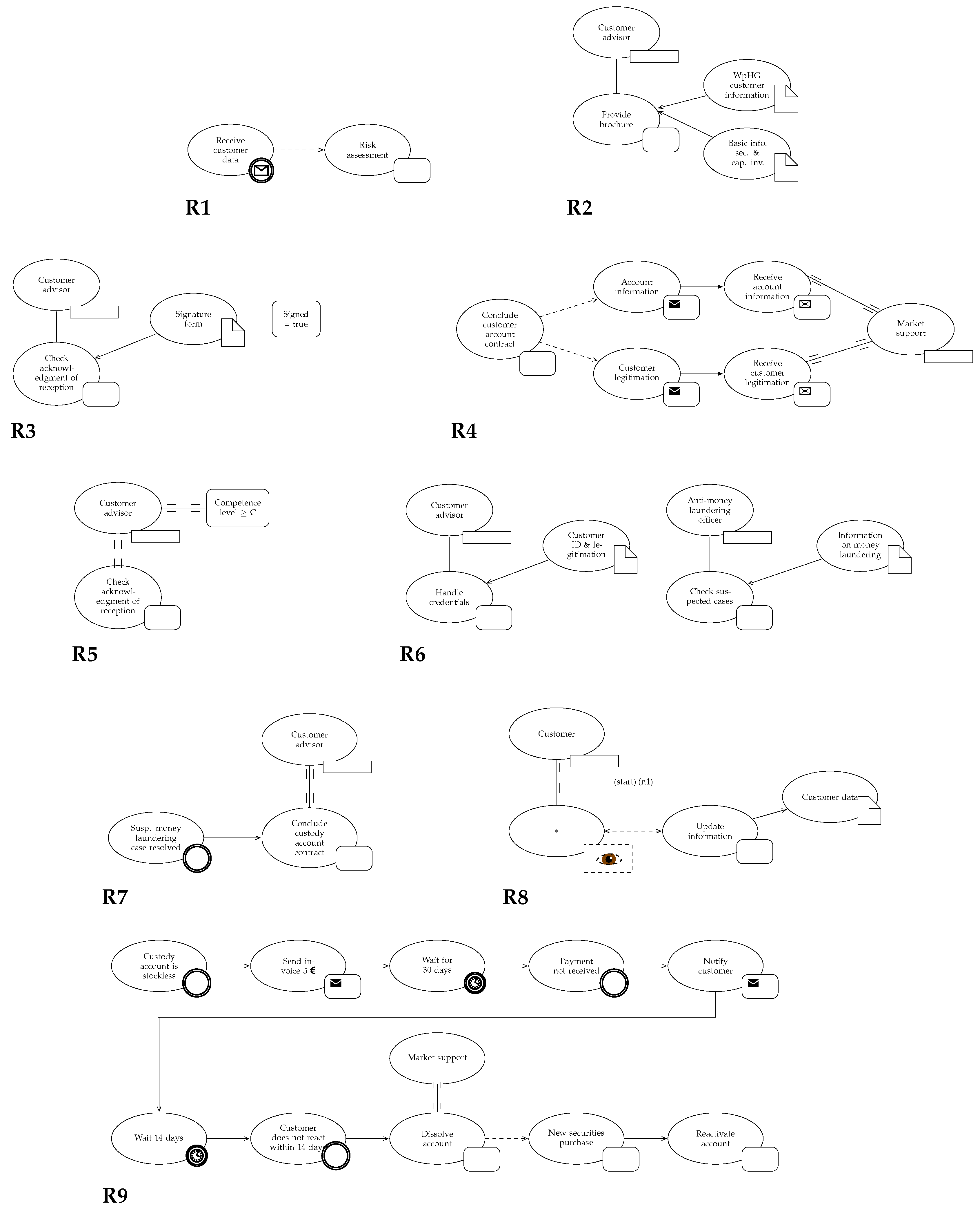
- Phase 1—Survey: We start our survey with the definition of search phrases and criteria to set the goals and boundaries for the following literature review. We focus on approaches that are explicitly described as compliance approaches and refrain from technical-oriented approaches that view compliance as a peripheral aspect and solve rather specific problems. The approach had to be designed for end users of IT tools, which implies the availability of a meta-model or grammar which enables the automated execution of compliance checks (cf. Section 3).The comparison of the approaches is driven by a realistic process from the finance industry which incorporates different types of compliance requirements. The requirements are divided into four process perspectives [28]: control flow, data flow, time and resources. In addition, we include the concept of a compensation to demonstrate how temporary compliance violations can be resolved later.
- Phase 2—Modeling: After selecting and classifying the compliance approaches, we briefly introduce each language used in the respective approaches, before modelling the requirements derived from the given example process. As we distinguish between a high-level language (if applicable) and the underlying formalism, we provide a large number of details for the subsequent evaluation (involve [29] in Section 5.5). Moreover, we juxtapose textual and visual approaches to simplify the direct comparison between similar approaches (cf. Section 5).
- Phase 3—Evaluation: In the last phase, the approaches are compared regarding their expressiveness and complexity. First, the expressiveness is measured by the level of completion with which the requirements introduced in Phase 1 have been modelled in Phase 2. To extend the discussion to the correct interpretation and modelling of each compliance requirement, we characterize the semantics of the formalised rules with regard to a number of modalities (i.e., obligations, permissions and prohibitions) which are based on legal theory [25] (cf. Section 6.1).Second, the complexity is measured by means of metrics which were originally used to analyse the complexity of software (modules). In this context, they serve as a simple but effective instrument to compare the lexical complexity of the different modelling languages.In line with metrics for programming languages, both the variety and the volume of the used language constructs is considered when lexical complexity is determined. To do this, we first discuss the applicability of software metrics, before we apply the Halstead metrics to the rule formalisation developed in Phase 2 (cf. Section 6.2).
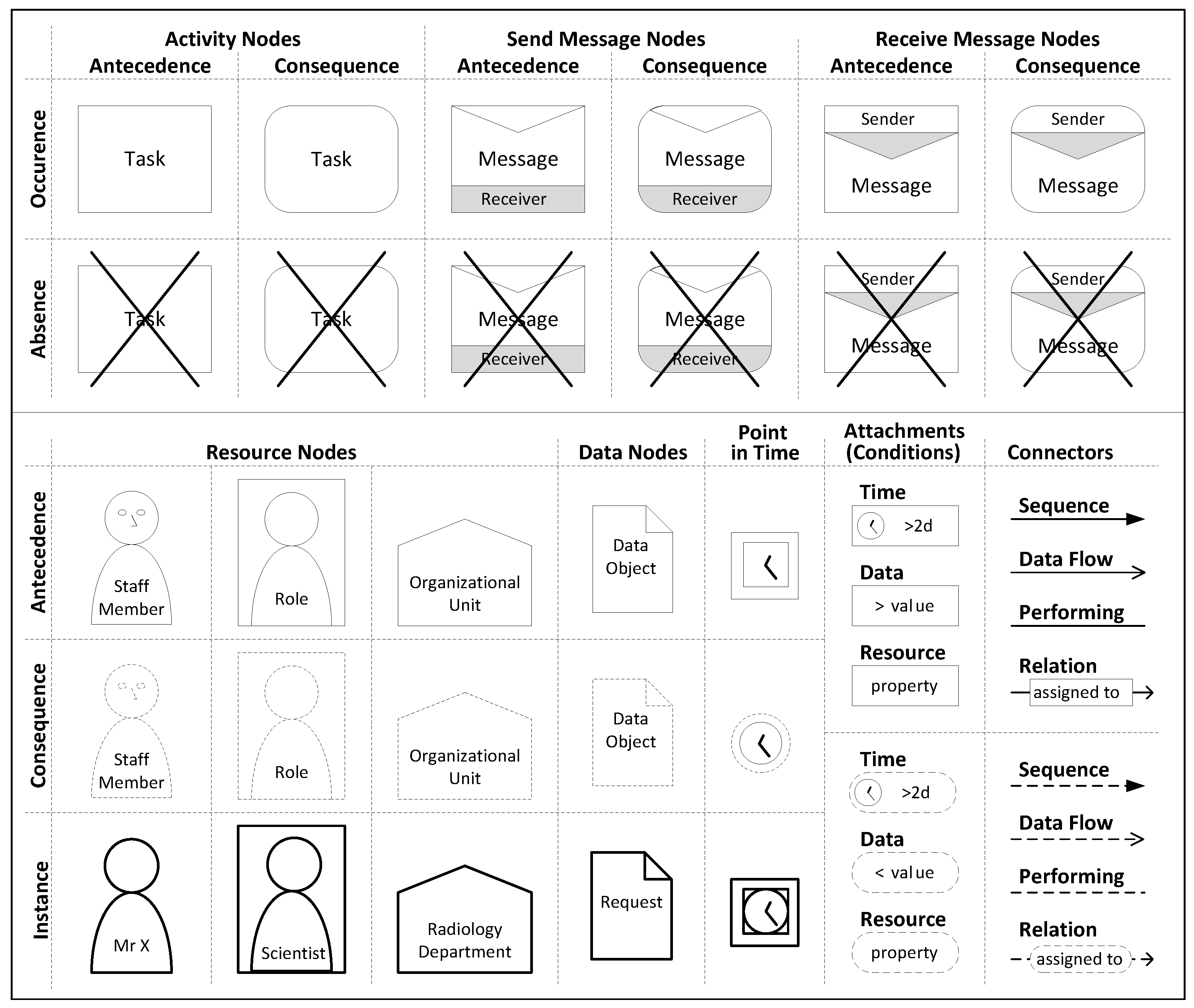
3. Language Selection Process
4. Running Example
4.1. Process Model
4.2. Compliance Requirements
5. Language-Specific Compliance Rule Formalisation
5.1. BPMN-Q
5.2. CRL
5.3. Declare
5.4. eCRG
- The antecedence pattern corresponds to the if part and describes the scope of a compliance rule, i.e., to which situations the rule is applied or when it is triggered.
- The consequence pattern corresponds to the then and else parts and describes how the rule can be satisfied once it is triggered.
5.5. DMQL
- The minimum and maximum path length;
- The minimum and maximum number of overlapping edges and nodes between different paths contained in a query;
- Required, allowed and forbidden nodes and edge types on the path, and
- required, allowed or forbidden patterns on the path.
5.6. PCL
- (i)
- If every propositional letter is a literal (i.e., l), then its negation ¬l is also a literal;
- (ii)
- If X is a deontic operator (i.e., a specific type of an obligation) and l is a literal, then Xl and ¬Xl are deontic literals.
5.7. PENELOPE
6. Evaluation of Compliance Languages Based on the Formalisation Results
6.1. Expressiveness
- Persistence: An important distinction is whether an obligation is terminated or removed. Consider an update of your online banking account. As soon as you have filled out all mandatory text fields, the punctual obligation expires and your session is terminated (non-persistent). We speak of a persistent obligation if the action linked to the obligation is removed, such as the standing order for a credit being terminated when it is completely paid back. Both achievement and maintenance are persistent obligations.
- Achievement: This obligation type refers to a period of time in which the obligation must be met at least once. It can be further distinguished into preemptive and non-preemptive obligations. In general, it is obligatory for a train conductor to identify her/himself by means of a service card.If the conductor presented a service card before conducting the ticket inspection, then the obligation to show the service card requested by the passenger during the ticket inspection has already been fulfilled and is categorised as a preemptive obligation.
- Maintenance: This obligation type refers to a period of time in which the obligation must be continually met. Paying the monthly flat rate is an example of a periodical expenditure, whether it be the apartment rent or the high-speed internet.
- Perdurance: A perdurant obligation persists after being violated. The payment of an invoice for an online purchase is, first of all, a perdurant obligation, but in case the purchase has to be returned to the retailer, this obligation becomes non-perdurant.
6.2. Complexity
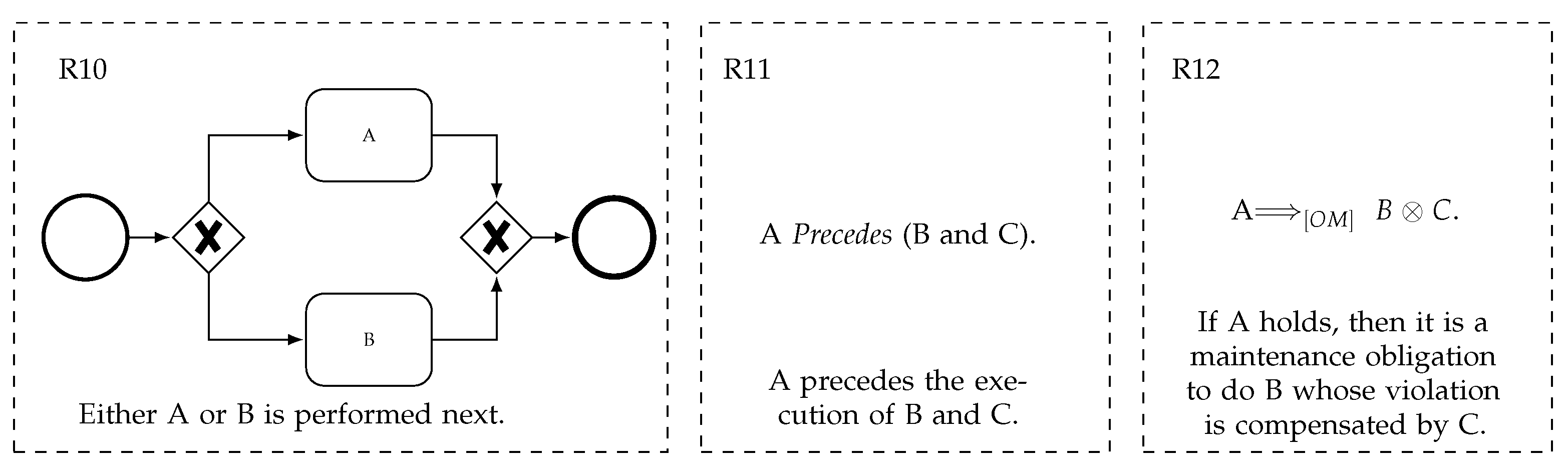
- Example:Figure 10 shows three different compliance rules. The graph is modelled in BPMN 2.0 while the textual rules are specified in CRL and PCL. Activities are simply represented by the letters A, B and C. According to the definition of the metrics, R10 can be expressed by five operators: = {xor-split, xor-join, start event, end event, sequence flow} = 5 and two operands: = {A, B} = 2. After defining the language’s properties, their occurrence can be counted. The operators defined in result in ten, as there are multiple sequence flows, two gateways and two events to consider: = 10; whereas the operators defined in appear only once each, and, hence, result in two: = 2. Similarly, R11 can be decomposed into three operators: = {pattern, and, parentheses} = 3, where the parentheses are counted as a pair; and three operands: = {A, B, C} = 3 resulting in: = 3, respectively = 3. Analogously, R12 can be determined by three different operators: = {deontic modality, ⊗-reparation} = 2, and three operands: = {A, B, C} = 3 resulting in: = 2, respectively = 3.
7. Related Work
8. Discussion
8.1. Summary of Results
8.2. Implications for Research and Practice
8.3. Limitations
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A. Complexity Measures for Evaluated Languages
| ID | ||
|---|---|---|
| R1 | {pattern, sequence flow} | {activity} |
| R2 | {data flow} | {activity, data} |
| R3 | {pattern, sequence flow, data flow} | {activity, data} |
| R4 | {pattern, sequence flow, data flow} | {activity, data} |
| R5 | n.a. | n.a. |
| R6 | n.a. | n.a. |
| R7 | {data flow} | {activity, data} |
| R8 | {pattern, start event, sequence flow} | {activity} |
| R9 | {pattern, sequence flow, data flow} | {activity, data} |
| ID | n | N | V | D | E | ||||
|---|---|---|---|---|---|---|---|---|---|
| R1 | 2 | 1 | 3 | 2 | 2 | 4 | 6.34 | 2.00 | 12.68 |
| R2 | 1 | 2 | 3 | 2 | 3 | 5 | 7.92 | 0.75 | 5.94 |
| R3 | 3 | 2 | 5 | 3 | 3 | 6 | 13.93 | 2.25 | 31.35 |
| R4 | 3 | 2 | 5 | 4 | 4 | 8 | 18.58 | 3.00 | 55.73 |
| R5 | · | · | · | · | · | · | · | · | · |
| R6 | · | · | · | · | · | · | · | · | · |
| R7 | 1 | 2 | 3 | 1 | 2 | 3 | 4.75 | 0.50 | 2.38 |
| R8 | 3 | 1 | 4 | 3 | 1 | 4 | 8.00 | 1.50 | 12.00 |
| R9 | 3 | 2 | 5 | 9 | 9 | 18 | 41.79 | 6.75 | 282.11 |
| ID | ||
|---|---|---|
| R1 | {pattern} | {activity} |
| R2 | {pattern, and, parenthesis} | {activity} |
| R3 | {pattern} | {activity, data} |
| R4 | {pattern, and, parenthesis} | {activity} |
| R5 | {pattern} | {activity, data, resource} |
| R6 | {pattern, and, parenthesis} | {activity} |
| R7 | {pattern} | {activity, data} |
| R8 | {pattern} | {activity} |
| R9 | {pattern, else, parenthesis} | {activity, data} |
| ID | n | N | V | D | E | ||||
|---|---|---|---|---|---|---|---|---|---|
| R1 | 1 | 1 | 2 | 1 | 2 | 3 | 3.00 | 1.00 | 3.00 |
| R2 | 3 | 1 | 4 | 3 | 2 | 5 | 10.00 | 3.00 | 30.00 |
| R3 | 1 | 2 | 3 | 1 | 2 | 3 | 4.75 | 0.50 | 2.38 |
| R4 | 3 | 1 | 4 | 3 | 3 | 6 | 12.00 | 4.50 | 54.00 |
| R5 | 1 | 3 | 4 | 1 | 3 | 4 | 8.00 | 0.50 | 4.00 |
| R6 | 3 | 1 | 4 | 3 | 3 | 6 | 12.00 | 4.50 | 54.00 |
| R7 | 1 | 2 | 3 | 1 | 3 | 4 | 6.34 | 0.75 | 4.75 |
| R8 | 1 | 1 | 2 | 1 | 2 | 3 | 3.00 | 1.00 | 3.00 |
| R9 | 3 | 2 | 5 | 6 | 6 | 12 | 27.86 | 4.50 | 125.38 |
| ID | ||
|---|---|---|
| R1 | {Precendence} | {activity type} |
| R2 | {Existence} | {activity type, multiplicity label} |
| R3 | {Response} | {activity type} |
| R4 | {Response} | {activity type} |
| R5 | n.a. | n.a. |
| R6 | n.a. | n.a. |
| R7 | {Precedence} | {activity type} |
| R8 | {Responded_Existence} | {activity type} |
| R9 | {Branched_Response,Response,Choice} | {activity type, choice label} |
| ID | n | N | V | D | E | ||||
|---|---|---|---|---|---|---|---|---|---|
| R1 | 1 | 1 | 2 | 1 | 2 | 3 | 3.00 | 1.00 | 3.00 |
| R2 | 1 | 2 | 3 | 1 | 2 | 3 | 4.75 | 0.50 | 2.38 |
| R3 | 1 | 1 | 2 | 1 | 2 | 3 | 3.00 | 1.00 | 3.00 |
| R4 | 1 | 1 | 2 | 1 | 2 | 3 | 3.00 | 1.00 | 3.00 |
| R5 | · | · | · | · | · | · | · | · | · |
| R6 | · | · | · | · | · | · | · | · | · |
| R7 | 1 | 1 | 2 | 1 | 2 | 3 | 3.00 | 1.00 | 3.00 |
| R8 | 1 | 1 | 2 | 1 | 2 | 3 | 3.00 | 1.00 | 3.00 |
| R9 | 3 | 2 | 5 | 3 | 6 | 9 | 20.90 | 4.50 | 94.04 |
| ID | ||
|---|---|---|
| R1 | {arc path} | {node event, node task} |
| R2 | {arc non-directed, arc original/opposite direction} | {node lane, node task, node data} |
| R3 | {arc non-directed, arc original/opposite direction, attribute relation} | {node lane, node task, node data, attribute} |
| R4 | {arc path, arc non-directed, arc original/opposite direction} | {node lane, node send, node receive, node task} |
| R5 | {arc non-directed} | {node lane, node task, attribute} |
| R6 | {arc non-directed, arc original/opposite direction} | {node lane, node task, node data} |
| R7 | {arc non-directed, arc original/opposite direction} | {node lane, node task, node event} |
| R8 | {arc non-directed, arc path non-directed, arc original/opposite direction} | {node lane, node various, node task, node data} |
| R9 | {node event, node send, node timer, node, node task} | {node event, node send, node timer, node, node task} |
| ID | n | N | V | D | E | ||||
|---|---|---|---|---|---|---|---|---|---|
| R1 | 1 | 2 | 3 | 1 | 2 | 3 | 4.75 | 0.50 | 2.38 |
| R2 | 2 | 3 | 5 | 3 | 4 | 7 | 16.25 | 1.33 | 21.67 |
| R3 | 3 | 4 | 7 | 3 | 4 | 7 | 19.65 | 1.50 | 29.48 |
| R4 | 3 | 4 | 7 | 6 | 6 | 12 | 33.69 | 2.25 | 75.80 |
| R5 | 1 | 3 | 4 | 2 | 3 | 5 | 10.00 | 0.50 | 5.00 |
| R6 | 2 | 3 | 5 | 4 | 6 | 10 | 23.22 | 2.00 | 46.44 |
| R7 | 2 | 3 | 5 | 2 | 3 | 5 | 11.61 | 1.00 | 11.61 |
| R8 | 3 | 4 | 7 | 3 | 4 | 7 | 19.65 | 1.50 | 29.48 |
| R9 | 3 | 5 | 8 | 10 | 11 | 21 | 63.00 | 3.30 | 207.90 |
| ID | ||
|---|---|---|
| R1 | {operatorType, deontic modalityType} | {(activity)literal} |
| R2 | {operatorType, deontic modalityType, operatorType} | {literal} |
| R3 | {operatorType, deontic modalityType} | {literal, (activity)literal} |
| R4 | {operatorType, deontic modalityType, operatorType} | {literal, (activity)literal} |
| R5 | {operatorType, deontic modalityType, operatorType} | {literal, literal, literal, OR} |
| R6(1) | {operatorType, deontic modalityType, operatorType} | {literal, literal} |
| R6(2) | {operatorType, deontic modalityType, operatorType} | {literal, (resource)literal} |
| R7 | {operatorType, deontic modalityType, operatorType} | {literal, literal} |
| R8 | {operatorType, deontic modalityType, operatorType} | {literal, (resource)literal} |
| R9(1) | {operatorType, deontic modalityType, operatorType} | {literal} |
| R9(2) | {operatorType, deontic modalityType, operatorType} | {literal, (activity)literal} |
| ID | n | N | V | D | E | ||||
|---|---|---|---|---|---|---|---|---|---|
| R1 | 2 | 1 | 3 | 3 | 1 | 4 | 6.34 | 1.00 | 6.34 |
| R2 | 3 | 1 | 4 | 3 | 1 | 4 | 8.00 | 1.50 | 12.00 |
| R3 | 2 | 2 | 4 | 2 | 3 | 5 | 10.00 | 1.50 | 15.00 |
| R4 | 3 | 3 | 6 | 3 | 2 | 5 | 12.92 | 1.00 | 12.92 |
| R5 | 3 | 2 | 5 | 3 | 3 | 6 | 13.93 | 2.25 | 31.35 |
| R6(1) | 3 | 2 | 5 | 3 | 2 | 5 | 11.61 | 1.50 | 17.41 |
| R6(2) | 3 | 2 | 5 | 3 | 2 | 5 | 11.61 | 1.50 | 17.41 |
| R7 | 3 | 2 | 5 | 3 | 2 | 5 | 11.61 | 1.50 | 17.41 |
| R8 | 3 | 2 | 5 | 3 | 2 | 5 | 11.61 | 1.50 | 17.41 |
| R9(1) | 3 | 1 | 4 | 3 | 1 | 4 | 8.00 | 1.50 | 12.00 |
| R9(2) | 3 | 2 | 5 | 3 | 2 | 5 | 11.61 | 1.50 | 17.41 |
| ID | ||
|---|---|---|
| R1 | {event, activity, pattern,logical operator,temporal operator, fluent, agent} | {pattern type, event, fluent, time, AND, LEQ} |
| R2 | {event, pattern, logical operator, temporal operator, fluent, agent} | {pattern type, event, fluent, time, AND, LEQ} |
| R3 | {event, pattern, fluent, agent, temporal operator, logical operator} | {pattern type, resource, fluent, time, AND, LEQ} |
| R4 | {pattern, activity, agent, fluent,temporal operator, logical operator} | {pattern type, AND, LEQ, time, resource} |
| R5 | {pattern, event, agent, temporal operator, logical operator} | {pattern type, fluent, event, advisor, AND, OR, LEQ, time} |
| R6 | n.a. | n.a. |
| R7 | {pattern, event, agent, fluent, temporal operator, logical operator} | {pattern type, activity, advisor, AND, LEQ, time} |
| R8 | n.a. | n.a. |
| R9 | {pattern, agent, fluent, activity, temporal operator,logical operator} | {pattern type, activity, fluent, AND, LEQ, time} |
| ID | n | N | V | D | E | ||||
|---|---|---|---|---|---|---|---|---|---|
| R1 | 7 | 6 | 13 | 10 | 5 | 15 | 55.51 | 2.92 | 161.89 |
| R2 | 6 | 6 | 12 | 9 | 5 | 14 | 50.19 | 2.50 | 125.47 |
| R3 | 6 | 6 | 12 | 10 | 4 | 14 | 50.19 | 2.00 | 100.38 |
| R4 | 6 | 5 | 11 | 79 | 13 | 22 | 76.11 | 7.80 | 593.64 |
| R5 | 5 | 8 | 13 | 8 | 6 | 14 | 51.81 | 1.88 | 97.14 |
| R6 | · | · | · | · | · | · | · | · | · |
| R7 | 6 | 6 | 12 | 9 | 10 | 19 | 68.11 | 5.00 | 340.57 |
| R8 | · | · | · | · | · | · | · | · | · |
| R9 | 6 | 6 | 12 | 12 | 11 | 23 | 82.45 | 5.50 | 453.50 |
| ID | ||
|---|---|---|
| R1 | {activity AO, message CO, sequence flow C} | {organization, message type, activity type} |
| R2 | {activity CO, data flow CO, performing relation CO} | {data, resource, activity type} |
| R3 | {activity AO, activity CO, data object CO, data flow A, data flow C, performing relation C, sequence flow C} | {data, resource, activity type} |
| R4 | {activity AO, message CO, data object C, data flow C, sequence flow C} | {data, organization, message type, activity type} |
| R5 | {activity AO, resource A, condition C, performing relation A, resource relation C} | {resource, condition label, relation label, activity type} |
| R6 | {activity AO, resource relation C} | {resource, relation label, activity type} |
| R7 | {activity AO, activity CO, sequence flow C, performing relation C} | {resource, activity type} |
| R8 | {activity AO, activity CO} | {activity type} |
| R9 | {activity AO, activity CO, message AO, message CA, data object AO, condition AO, condition CO, sequence flow AO, sequence flow CO, data flow AO, dataflow CO, performing relation, xor} | {data, condition label, organization, unit, message type, activity type} |
| ID | n | N | V | D | E | ||||
|---|---|---|---|---|---|---|---|---|---|
| R1 | 3 | 3 | 6 | 3 | 3 | 6 | 15.51 | 1.50 | 23.26 |
| R2 | 3 | 3 | 6 | 4 | 4 | 8 | 20.68 | 2.00 | 41.36 |
| R3 | 7 | 3 | 10 | 8 | 6 | 14 | 46.51 | 7.00 | 325.55 |
| R4 | 5 | 3 | 8 | 9 | 5 | 14 | 42.00 | 4.17 | 175.00 |
| R5 | 5 | 4 | 9 | 5 | 4 | 9 | 28.53 | 2.50 | 71.32 |
| R6 | 2 | 2 | 4 | 4 | 4 | 8 | 16.00 | 2.00 | 32.00 |
| R7 | 4 | 2 | 6 | 4 | 3 | 7 | 18.09 | 3.00 | 54.28 |
| R8 | 2 | 1 | 3 | 2 | 2 | 4 | 6.34 | 2.00 | 12.68 |
| R9 | 14 | 8 | 22 | 28 | 18 | 46 | 205.13 | 15.75 | 3230.86 |
References
- SOX, Sarbanes-Oxley Act of 30 July 2002, 15 USC 7201 Note, Public Law 107-204, 107th Congress, 116 Statistics Act, Section 404; Technical Report. 2002. Available online: https://www.govinfo.gov/app/details/PLAW-107publ204 (accessed on 2 August 2022).
- Leone, A.J. Factors related to internal control disclosure: A discussion of Ashbaugh, Collins, and Kinney (2007) and Doyle, Ge, and McVay (2007). J. Account. Econ. 2007, 44, 224–237. [Google Scholar] [CrossRef]
- COMPAS-Project. D2.1 State-of-the-Art in the Field of Compliance Languages—Compliance-Driven Models, Languages, and Architectures for Services; Report D2.1; Tilburg University: Tilburg, The Netherlands, 2008. [Google Scholar]
- Bartolini, C.; Giurgiu, A.; Lenzini, G.; Robaldo, L. Towards Legal Compliance by Correlating Standards and Laws with a Semi-automated Methodology. In Proceedings of the BNAIC 2016: Artificial Intelligence—28th Benelux Conference on Artificial Intelligence, Amsterdam, The Netherlands, 10–11 November 2016; Bosse, T., Bredeweg, B., Eds.; Revised Selected Papers. Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2016; Volume 765, pp. 47–62. [Google Scholar] [CrossRef]
- Sadiq, S.; Governatori, G.; Namiri, K. Modeling control objectives for business process compliance. In Proceedings of the International Conference on Business Process Management (BPM’07), Brisbane, Australia, 24–28 September 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 149–164. [Google Scholar]
- Reichert, M.; Weber, B. Business Process Compliance. In Enabling Flexibility in Process-Aware Information Systems; Springer: Berlin/Heidelberg, Germany, 2012; pp. 297–320. [Google Scholar]
- Liu, Y.; Muller, S.; Xu, K. A static compliance-checking framework for business process models. IBM Syst. J. 2007, 46, 335–361. [Google Scholar] [CrossRef]
- Häußler, M.; Esser, S.; Borrmann, A. Code compliance checking of railway designs by integrating BIM, BPMN and DMN. Autom. Constr. 2021, 121, 103427. [Google Scholar] [CrossRef]
- Awad, A.; Decker, G.; Weske, M. Efficient Compliance Checking Using BPMN-Q and Temporal Logic. In Proceedings of the International Conference on Business Process Management (BPM’08), Milan, Italy, 2–4 September 2008; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5240, pp. 326–341. [Google Scholar]
- Ghanavati, S.; Amyot, D.; Rifaut, A. Legal Goal-Oriented Requirement Language (Legal GRL) for Modeling Regulations. In Proceedings of the 6th International Workshop on Modeling in Software Engineering (MiSE 2014), Hyderabad, India, 31 May–7 June 2014; Association for Computing Machinery: New York, NY, USA, 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Barnawi, A.; Awad, A.; Elgammal, A.; El Shawi, R.; Almalaise, A.; Sakr, S. Runtime Self-Monitoring Approach of Business Process Compliance in Cloud Environments. Clust. Comput. 2015, 18, 1503–1526. [Google Scholar] [CrossRef]
- Castellanos-Ardila, J.P.; Gallina, B.; Governatori, G. Compliance-aware engineering process plans: The case of space software engineering processes. Artif. Intell. Law 2021, 29, 587–627. [Google Scholar] [CrossRef]
- Ghanavati, S.; Hulstijn, J. Impact of Legal Interpretation on Business Process Compliance. In Proceedings of the 2015 IEEE/ACM 1st International Workshop on TEchnical and LEgal aspects of data pRivacy and SEcurity (TELERISE ’15), Florence, Italy, 18 May 2015; pp. 26–31. [Google Scholar]
- De Masellis, R.; Maggi, F.M.; Montali, M. Monitoring Data-Aware Business Constraints with Finite State Automata. In Proceedings of the 2014 International Conference on Software and System Process (ICSSP 2014), Nanjing, China, 26–28 May 2014; Association for Computing Machinery: New York, NY, USA, 2014; pp. 134–143. [Google Scholar] [CrossRef]
- Corea, C.; Delfmann, P. Detecting Compliance with Business Rules in Ontology-Based Process Modeling. In Proceedings of the Towards Thought Leadership in Digital Transformation: 13. Internationale Tagung Wirtschaftsinformatik, WI 2017, St.Gallen, Switzerland, 12–15 February 2017. [Google Scholar]
- Gong, P.; Knuplesch, D.; Feng, Z.; Jiang, J. bpCMon: A Rule-Based Monitoring Framework for Business Processes Compliance. Int. J. Web Serv. Res. (IJWSR) 2017, 14, 23. [Google Scholar] [CrossRef]
- Loreti, D.; Chesani, F.; Ciampolini, A.; Mello, P. Distributed Compliance Monitoring of Business Processes over MapReduce Architectures. In Proceedings of the ICPE ’17 Companion; Association for Computing Machinery: New York, NY, USA, 2017; pp. 79–84. [Google Scholar] [CrossRef]
- Tosatto, S.C.; Governatori, G. Computational Complexity of Compliance and Conformance: Drawing a Line Between Theory and Practice. J. Appl. Logics—IfCoLog J. Logics Their Appl. 2021, 8, 1023–1064. [Google Scholar]
- Oyekola, O.; Xu, L. Verification and compliance in collaborative processes. In Proceedings of the Working Conference on Virtual Enterprises; Springer: Berlin/Heidelberg, Germany, 2020; pp. 213–223. [Google Scholar]
- Hamdani, R.E.; Mustapha, M.; Amariles, D.R.; Troussel, A.; Meeùs, S.; Krasnashchok, K. A combined rule-based and machine learning approach for automated GDPR compliance checking. In Proceedings of the Eighteenth International Conference on Artificial Intelligence and Law, São Paulo, Brazil, 21–25 June 2021; pp. 40–49. [Google Scholar]
- Cunha, V.H.C.; Caiado, R.G.G.; Corseuil, E.T.; Neves, H.F.; Bacoccoli, L. Automated compliance checking in the context of Industry 4.0: From a systematic review to an empirical fuzzy multi-criteria approach. Soft Comput. 2021, 25, 6055–6074. [Google Scholar]
- Krasnashchok, K.; Mustapha, M.; Al Bassit, A.; Skhiri, S. Towards privacy policy conceptual modeling. In Proceedings of the International Conference on Conceptual Modeling; Springer: Berlin/Heidelberg, Germany, 2020; pp. 429–438. [Google Scholar]
- Becker, J.; Delfmann, P.; Eggert, M.; Schwittay, S. Generalizability and applicability of model-based business process compliance—Checking approaches: A state-of-the-art analysis and research roadmap. Bus. Res. 2012, 5, 221–247. [Google Scholar]
- Fellmann, M.; Zasada, A. State-of-the-Art of Business Process Compliance Approaches: A Survey. In Proceedings of the 22st European Conference on Information Systems, ECIS 2014, Tel Aviv, Israel, 9–11 June 2014. [Google Scholar]
- Hashmi, M.; Governatori, G. Norms modeling constructs of business process compliance management frameworks: A conceptual evaluation. Artif. Intell. Law 2018, 26, 251–305. [Google Scholar] [CrossRef]
- Knuplesch, D.; Reichert, M.; Kumar, A. A framework for visually monitoring business process compliance. Inf. Syst. 2017, 64, 381–409. [Google Scholar] [CrossRef]
- Ly, L.T.; Maggi, F.M.; Montali, M.; Rinderle-Ma, S.; van der Aalst, W.M. Compliance monitoring in business processes: Functionalities, application, and tool-support. Inf. Syst. 2015, 54, 209–234. [Google Scholar] [CrossRef] [PubMed]
- Van Der Aalst, W.M.; Pesic, M. DecSerFlow: Towards a truly declarative service flow language. In Proceedings of the 4th International Workshop on Web Services and Formal Methods (WS-FM’06), Brisbane, Australia, 28–29 September 2007; Springer: Berlin/Heidelberg, Germany, 2006; pp. 1–23. [Google Scholar]
- Garey, M.R.; Johnson, D.S. Computers and intractability: A guide to the theory of npcompleteness (series of books in the mathematical sciences), ed. In Computers and Intractability; Freeman: San Francisco, CA, USA, 1979; Volume 340. [Google Scholar]
- Webster, J.; Watson, R.T. Analyzing the past to prepare for the future: Writing a literature review. MIS Q. 2002, 26, xiii–xxiii. [Google Scholar]
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering–a systematic literature review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar]
- Awad, A.; Weidlich, M.; Weske, M. Visually Specifying Compliance Rules and Explaining their Violations for Business Processes. J. Vis. Lang. Comput. 2011, 22, 30–55. [Google Scholar] [CrossRef]
- Elgammal, A.; Turetken, O.; van den Heuvel, W.J.; Papazoglou, M. Formalizing and appling compliance patterns for business process compliance. Softw. Syst. Model. 2016, 15, 119–146. [Google Scholar]
- Letia, I.A.; Goron, A. Model checking as support for inspecting compliance to rules in flexible processes. J. Vis. Lang. Comput. 2015, 28, 100–121. [Google Scholar] [CrossRef]
- Delfmann, P.; Breuker, D.; Matzner, M.; Becker, J. Supporting Information Systems Analysis Through Conceptual Model Query–The Diagramed Model Query Language (DMQL). Commun. Assoc. Inf. Syst. 2015, 37, 24. [Google Scholar] [CrossRef]
- Knuplesch, D.; Reichert, M. A visual language for modeling multiple perspectives of business process compliance rules. Softw. Syst. Model. 2017, 16, 715–736. [Google Scholar]
- Governatori, G.; Rotolo, A. A Conceptually Rich Model of Business Process Compliance. In Proceedings of the 7th Asia-Pacific Conference on Conceptual Modelling (APCCM’10), Brisbane, Australia, 18–21 January 2010; Volume 110, pp. 3–12. [Google Scholar]
- Ramezani, E.; Fahland, D.; Van Dongen, B.; Van Der Aalst, W. Diagnostic Information in Temporal Compliance Checking; Technical Report; BPM Center: San Pedro, Costa Rica, 2012. [Google Scholar]
- Goedertier, S.; Vanthienen, J. Designing Compliant Business Processes with Obligations and Permissions. In Proceedings of the 4th Business Process Management Workshops: BPM 2006 International Workshops, BPD, BPI, ENEI, GPWW, DPM, semantics4ws, Vienna, Austria, 4–7 September 2006; Eder, J., Dustdar, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 5–14. [Google Scholar] [CrossRef]
- Yu, J.; Manh, T.P.; Han, J.; Jin, Y.; Han, Y.; Wang, J. Pattern Based Property Specification and Verification for Service Composition. In Proceedings of 7th International Conference in Web Information Systems Engineering (WISE’06); Aberer, K., Peng, Z., Rundensteiner, E.A., Zhang, Y., Li, X., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 156–168. [Google Scholar]
- Forster, A.; Engels, G.; Schattkowsky, T.; Van Der Straeten, R. Verification of business process quality constraints based on visual process patterns. In Proceedings of the 1st Joint IEEE/IFIP Symposium on Theoretical Aspects of Software Engineering (TASE’07), Shanghai, China, 6–8 June 2007; pp. 197–208. [Google Scholar]
- Caron, F.; Vanthienen, J.; Baesens, B. Comprehensive rule-based compliance checking and risk management with process mining. Decis. Support Syst. 2013, 54, 1357–1369. [Google Scholar]
- Becker, J.; Delfmann, P.; Dietrich, H.A.; Steinhorst, M.; Eggert, M. Business process compliance checking–applying and evaluating a generic pattern matching approach for conceptual models in the financial sector. Inf. Syst. Front. 2016, 18, 359–405. [Google Scholar]
- Ramezani, E.; Fahland, D.; van der Aalst, W.M. Where did I misbehave? diagnostic information in compliance checking. In Proceedings of the 10th International Conference on Business Process Management (BPM’12), Tallinn, Estonia, 3–6 September 2012; Springer: Berlin/Heidelberg, Germany; pp. 262–278. [Google Scholar]
- Timm, F.; Zasada, A.; Thiede, F. Building a Reference Model for Anti-Money Laundering in the Financial Sector. In Proceedings of the 18th Conference on Learning, Knowledge, Data, Analytics (LWDA’16), Potsdam, Germany, 12 September 2016. [Google Scholar]
- Zasada, A.; Bui, T. More than meets the eye: A Case Study on the Role of IT Affordances in Supporting Compliance. In Proceedings of the 24th Americas Conference on Information Systems (AMCIS’18), New Orleans, LA, USA, 16–18 August 2018. [Google Scholar]
- Bank for International Settlements. A Global Regulatory Framework for More Resilient Banks and Banking Systems; Technical Report; Bank for International Settlements: Basel, Switzerland, 2011. [Google Scholar]
- Awad, A.; Barnawi, A.; Elgammal, A.; Elshawi, R.; Almalaise, A.; Sakr, S. Runtime detection of business process compliance violations: An approach based on anti patterns. In Proceedings of the 30th Annual ACM Symposium on Applied Computing, (SAC ’15), Salamanca, Spain, 13–17 April 2015; pp. 1203–1210. [Google Scholar]
- Dwyer, M.B.; Avrunin, G.S.; Corbett, J.C. Patterns in property specifications for finite-state verification. In Proceedings of the 21st International Conference on Software Engineering (ICSE’99), Los Angeles, CA, USA, 16–22 May 1999; pp. 411–420. [Google Scholar]
- Elgammal, A.; Turetken, O.; van den Heuvel, W.J.; Papazoglou, M. Root-cause analysis of design-time compliance violations on the basis of property patterns. In Proceedings of the International Conference on Service-Oriented Computing (ICSOC’10), Perth, Australia, 13–15 December 2010; pp. 17–31. [Google Scholar]
- Turetken, O.; Elgammal, A.; van den Heuvel, W.J.; Papazoglou, M.P. Enforcing compliance on business processes through the use of patterns. In Proceedings of the 19th European Conference on Information Systems, (ECIS’11), Helsinki, Finland, 9–11 June 2011; p. 5. [Google Scholar]
- Turetken, O.; Elgammal, A.; van den Heuvel, W.J.; Papazoglou, M.P. Capturing compliance requirements: A pattern-based approach. IEEE Softw. 2012, 29, 28–36. [Google Scholar]
- Elgammal, A.; Turetken, O.; Van Den Heuvel, W.J. Using patterns for the analysis and resolution of compliance violations. Int. J. Coop. Inf. Syst. 2012, 21, 31–54. [Google Scholar] [CrossRef]
- Pnueli, A. The temporal logic of programs. In Proceedings of the 18th Annual Symposium on Foundations of Computer Science, Washington, DC, USA, 30 September–31 October 1977; pp. 46–57. [Google Scholar]
- Knuplesch, D.; Reichert, M.; Ly, L.T.; Kumar, A.; Rinderle-Ma, S. Visual modeling of business process compliance rules with the support of multiple perspectives. In Proceedings of the 32nd International Conference on Conceptual Modeling (ER’13), Hong-Kong China, 11–13 November 2013; Lecure Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2013; Volume 8217, pp. 106–120. [Google Scholar]
- Pesic, M.; Schonenberg, H.; van der Aalst, W. DECLARE: Full Support for Loosely-Structured Processes. In Proceedings of the 11th IEEE International Conference on Enterprise Distributed Object Computing (EDOC’07), Annapolis, MD, USA, 15–19 October 2007; p. 287. [Google Scholar]
- Pesic, M. Constraint-Based Workflow Management Systems: Shifting Control to Users. Ph.D. Thesis, Eindhoven University of Technology: Eindhoven, The Netherlands, 2008. [Google Scholar]
- Montali, M.; Maggi, F.M.; Chesani, F.; Mello, P.; Aalst, W.M.P.v.d. Monitoring Business Constraints with the Event Calculus. ACM Trans. Intell. Syst. Technol. 2014, 5, 1–30. [Google Scholar] [CrossRef]
- Ly, L.T.; Rinderle-Ma, S.; Dadam, P. Design and Verification of Instantiable Compliance Rule Graphs in process-aware Information Systems. In Proceedings of the 22nd International Conference on Advanced Information Systems Engineering (CAiSE’10), Hammamet, Tunisia, 7–11 June 2010; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2010; Volume 6051, pp. 9–23. [Google Scholar]
- Ly, L.T. SeaFlows—A Compliance Checking Framework for Supporting the Process Lifecycle. Ph.D. Thesis, University of Ulm, Ulm, Germany, 2013. [Google Scholar]
- Delfmann, P.; Steinhorst, M.; Dietrich, H.A.; Becker, J. The generic model query language GMQL – Conceptual specification, implementation, and runtime evaluation. Inf. Syst. 2015, 47, 129–177. [Google Scholar] [CrossRef]
- Antoniou, G.; Billington, D.; Governatori, G.; Maher, M.J. Representation results for defeasible logic. ACM Trans. Comput. Log. (TOCL’01) 2001, 2, 255–287. [Google Scholar] [CrossRef]
- Antoniou, G.; Billington, D.; Governatori, G.; Maher, M.J. Embedding Defeasible Logic into Logic Programming. Theory Pract. Log. Program. 2006, 6, 703–735. [Google Scholar] [CrossRef]
- Governatori, G.; Rotolo, A. Logic of Violations: A Gentzen System for Reasoning with Contrary-To-Duty Obligation. Australas. J. Log. 2006, 4, 193–215. [Google Scholar] [CrossRef]
- Lam, H.P.; Hashmi, M.; Scofield, B. Enabling Reasoning with LegalRuleML. In Proceedings of the 10th International Symposium on the Web: Research and Applications (RuleML’16), Stony Brook, NY, USA, 6–9 July 2016; Alferes, J.J., Bertossi, L., Governatori, G., Fodor, P., Roman, D., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2016; pp. 241–257. [Google Scholar] [CrossRef]
- Governatori, G. Representing business contracts in RuleML. Int. J. Coop. Inf. Syst. 2005, 14, 181–216. [Google Scholar] [CrossRef]
- Hansen, J.; Pigozzi, G.; van der Torre, L.W.N. Ten Philosophical Problems in Deontic Logic. In Proceedings of the Normative Multi-Agent Systems, 19th European Summer School in Logic, Language and Information (ESSLLI 2007) Trinity College, Dublin, Ireland, 6–17 August 2007. [Google Scholar]
- Alchourrón, C.E. Philosophical Foundations of Deontic Logic and the Logic of Defeasible Conditionals. In Deontic Logic in Computer Science; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 1994; pp. 43–84. [Google Scholar]
- Governatori, G.; Olivieri, F.; Rotolo, A.; Scannapieco, S. Computing Strong and Weak Permissions in Defeasible Logic. J. Philos. Log. 2013, 42, 799–829. [Google Scholar] [CrossRef]
- Stolpe, A. Relevance, Derogation and Permission. In Proceedings of the Deontic Logic in Computer Science; Governatori, G., Sartor, G., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 98–115. [Google Scholar]
- Hashmi, M.; Governatori, G.; Wynn, M.T. Business Process Data Compliance. In Proceedings of the 6th International Symposium on Rules on the Web: Research and Applications (RuleML’12), Montpellier, France, 27–29 August 2012; pp. 32–46. [Google Scholar] [CrossRef]
- Hashmi, M.; Governatori, G.; Wynn, M.T. Normative requirements for regulatory compliance: An abstract formal framework. Inf. Syst. Front. 2016, 18, 429–455. [Google Scholar] [CrossRef]
- Kowalski, R.; Sergot, M. A Logic-Based Calculus of Events. In Foundations of Knowledge Base Management; Schmidt, J., Thanos, C., Eds.; Topics in Information Systems; Springer: Berlin/Heidelberg, Germany, 1989; pp. 23–55. [Google Scholar]
- Miller, R.; Shanahan, M. The Event Calculus in Classical Logic—Alternative Axiomatisations. Electron. Trans. Artif. Intell. 1999, 3, 77–105. [Google Scholar]
- Sadri, F.; Kowalski, R. Variants of the Event Calculus. In Proceedings of the 12th International Conference on Logic Programming; Sterling, L., Ed.; MIT: Cambrdige, MA, USA, 1995. [Google Scholar]
- Hashmi, M.; Governatori, G.; Wynn, M.T. Modeling Obligations with Event-Calculus. In Proceedings of the 8th International Symposium on Rules on the Web: Research and Applications (RuleML’14), Prague, Czech Republic, 18–20 August 2014; pp. 296–310. [Google Scholar]
- Kunen, K. Negation in logic programming. J. Log. Program. 1987, 4, 289–308. [Google Scholar]
- Halstead, M.H. Elements of Software Science. Oper. Program. Syst. Ser. 1977, 7, 26. [Google Scholar]
- Carmo, J.; Jones, A.J. Deontic logic and contrary-to-duties. In Handbook of Philosophical Logic; Springer: Berlin/Heidelberg, Germany, 2002; pp. 265–343. [Google Scholar]
- Jones, A.J.; Sergot, M. On the characterisation of law and computer systems: The normative systems perspective. In Deontic Logic in Computer Science: Normative System Specification; Association of Computing Machine (ACM): New York, NY, USA, 1993; pp. 275–307. [Google Scholar]
- Piqué-Angordans, J.; Posteguillo, S.; Andreu-Besó, J.V. Epistemic and deontic modality: A linguistic indicator of disciplinary variation in academic English. LSP Prof. Commun. (2001–2008) 2002, 2, 49–65. [Google Scholar]
- van der Torre, L.; Tan, Y.H. An update semantics for deontic reasoning. Norms Logics Inf. Syst. 1998, 73–90. [Google Scholar]
- Hilpinen, R. Deontic logic. Blackwell Guide Philos. Log. 2001, 4, 159–182. [Google Scholar]
- Strasser, C.; Antonelli, G.A. Non-Monotonic Logic. In The Stanford Encyclopedia of Philosophy; Edward, N.Z., Ed.; Metaphysics Research Lab, Stanford University: Stanford, CA, USA, 2018. [Google Scholar]
- McCarty, L.T. Defeasible deontic reasoning. Fundam. Informaticae 1994, 21, 125–148. [Google Scholar] [CrossRef]
- Allaire, M.; Governatori, G. On the Equivalence of Defeasible Deontic Logic and Temporal Defeasible Logic. In Proceedings of the 17th International Conference on Principles and Practice of Multi-Agent Systems (PRIMA’14), Gold Coast, QLD, Australia, 1–5 December 2015; Dam, H.K., Pitt, J., Xu, Y., Governatori, G., Ito, T., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2014; pp. 74–90. [Google Scholar]
- Governatori, G.; Hashmi, M. No Time for Compliance. In Proceedings of the 19th IEEE International Enterprise Distributed Object Computing Conference (EDOC’15), Adelaide, Australia, 24–25 September 2015; pp. 9–18. [Google Scholar] [CrossRef]
- Governatori, G.; Rotolo, A. A Gentzen system for reasoning with contrary-to-duty obligations: A preliminary study. In Proceedings of the 6th International Workshop on Deontic Logic in Computer Science (Deon’02), London, UK, 22–24 May 2002; pp. 97–116. [Google Scholar]
- Governatori, G. An Abstract Normative Framework for Business Process Compliance. Inf. Technol. 2013, 55, 231–238. [Google Scholar]
- Governatori, G. The Regorous approach to process compliance. In Proceedings of the 19th IEEE International Enterprise Distributed Object Computing Workshop (EDOCW’15), Adelaide, SA, Australia, 22–25 September 2015; pp. 33–40. [Google Scholar]
- Elgammal, A.; Turetken, O.; van den Heuvel, W.J.; Papazoglou, M. On the Formal Specification of Regulatory Compliance: A Comparative Analysis. In Proceedings of the 8th International Conference on Service-Oriented Computing (ICSOC’10), San Francisco, CA, USA, 7–10 December 2010; pp. 27–38. [Google Scholar]
- Herrestad, H. Norms and Formalisation. In Proceedings of the 3rd International Conference on Artificial Intelligence and Law (ICAIL’91), Oxford, UK, 25–28 June 1991. [Google Scholar]
- Yu, S.; Zhou, S. A survey on metric of software complexity. In Proceedings of the 2nd IEEE International Conference on Information Management and Engineering (ICIME’10), Chengdu, China, 16–18 April 2010; pp. 352–356. [Google Scholar]
- McCabe, T.J. A complexity measure. IEEE Trans. Softw. Eng. 1976, 4, 308–320. [Google Scholar] [CrossRef]
- Henry, S.; Kafura, D. Software structure metrics based on information flow. IEEE Trans. Softw. Eng. 1981, 5, 510–518. [Google Scholar] [CrossRef]
- Albrecht, A.J.; Gaffney, J.E. Software function, source lines of code, and development effort prediction: A software science validation. IEEE Trans. Softw. Eng. 1983, 6, 639–648. [Google Scholar] [CrossRef]
- Mendling, J. Detection and Prediction of Errors in EPC Business Process Models. Ph.D. Thesis, Vienna University of Economics and Business Administrationa, Vienna, Austria, 2007. [Google Scholar]
- Curtis, B.; Sheppard, S.B.; Milliman, P.; Borst, M.; Love, T. Measuring the psychological complexity of software maintenance tasks with the Halstead and McCabe metrics. IEEE Trans. Softw. Eng. 1979, 2, 96–104. [Google Scholar] [CrossRef]
- Shepperd, M.; Ince, D.C. A critique of three metrics. J. Syst. Softw. 1994, 26, 197–210. [Google Scholar] [CrossRef]
- Ferrer, J.; Chicano, F.; Alba, E. Estimating software testing complexity. Inf. Softw. Technol. 2013, 55, 2125–2139. [Google Scholar] [CrossRef]
- Cardoso, J.; Mendling, J.; Neumann, G.; Reijers, H.A. A discourse on complexity of process models. In Proceedings of the 4th International Conference on Business Process Management (BPM’06), Vienna, Austria; Springer: Berlin/Heidelberg, Germany, 2006; pp. 117–128. [Google Scholar]
- Otto, P.N.; Antón, A.I. Addressing legal requirements in requirement engineering. In Proceedings of the 15th IEEE International Requirements Engineering Conference (RE’07), New Delhi, India, 15–19 October 2007; pp. 5–14. [Google Scholar]
- El Kharbili, M. Business Process Regulatory Compliance Management Solution Frameworks: A Comparative Evaluation. In Proceedings of the 8th Asia-Pacific Conference on Conceptual Modelling (APCCM’12); Australian Computer Society, Inc.: Wollongong, NSW, Australia, 2012; Volume 130, pp. 23–32. [Google Scholar]
- Bonatti, P.A.; Shahmehri, N.; Duma, C.; Olmedilla, D.; Nejdl, W.; Baldoni, M.; Baroglio, C.; Martelli, A.; Coraggio, P.; Antoniou, G.; et al. Rule-Based Policy Specification: State of the Art and Future Work, REWERSE Project Report-i2-D1; Report; Universitá di Napoli Fedrecio II: Naples, Italy, August 2004. [Google Scholar]
- Ly, L.T.; Maggi, F.M.; Montali, M.; Rinderle, S.; van der Aalst, W. A Framework for the Systematic Comparison and Evaluation of Compliance Monitoring Approaches. In Proceedings of the 17th IEEE International Enterprise Computing Conference (EDOC’13), Vancouver, BC, Canada, 9–13 September 2013. [Google Scholar]
- Fenech, S.; Pace, G.J.; Okika, J.C.; Ravn, A.P.; Schneider, G. On the Specification of Full Contracts. In Proceedings of the 6th International Workshop on Formal Engineering approaches to Software Components and Architectures (FESCA’09), York, UK, 28 March 2009. [Google Scholar]
- Prisacariu, C.; Schneider, G. A Formal Language for Electronic Contracts. In Proceedings of the 9th International Conference on Formal Methods for Open Object-Based Distributed Systems (IFIP’07), Paphos, Cyprus, 6–8 June 2007; Springer: Berlin/Heidelberg, Germany; pp. 174–189. [Google Scholar]
- John, T.; Kundisch, D.; Szopinski, D. Visual languages for modeling business models: A critical review and future research directions. In Proceedings of the Thirty Eighth International Conference on Information Systems (ICIS), Seoul, Repulic of Korea, 10–13 December 2017. [Google Scholar]
- Cabanillas, C.; Resinas, M.; Ruiz-Cortés, A. On the identification of data-related compliance problems in business processes. In Proceedings of the Jornadas Científico-Técnicas En Servicios Web Y SOA (JSWEB’10), Sevilla, Spain, 20–21 September 2010; Volume 1, pp. 89–102. [Google Scholar]
- Turki, S.; Bjekovic-Obradovic, M. Compliance in e-Government Service Engineering: State-of-the-Art. In Proceedings of the 1st International Conference on Exploring Services Science (IESS’10), Geneva, Switzerland, 17–19 February 2010; Lecture Notes in Business Information Processing. Springer: Berlin/Heidelberg, Germany; pp. 270–275. [Google Scholar]
- Giorgini, P.; Massacci, F.; Zannone, N. Security and Trust Requirements Engineering. In Foundations of Security Analysis and Design III: FOSAD 2004/2005 Tutorial Lectures; Aldini, A., Gorrieri, R., Martinelli, F., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 237–272. [Google Scholar] [CrossRef]
- Ghanavati, S.; Amyot, D.; Peyton, L. Towards a Framework for Tracking Legal Compliance in Healthcare. In Proceedings of the 19th International Conference on Advanced Information Systems Engineering (CAiSE’07), Trondheim, Norway, 11–15 June 2007; Springer: Berlin/Heidelberg, Germany; pp. 218–232. [Google Scholar]
- Ghanavati, S.; Amyot, D.; Peyton, L. A Requirements Management Framework for Privacy Compliance. In Proceedings of the Anais do—Workshop em Engenharia de Requisitos (WER’07), Toronto, ON, Canada, 17–18 May 2007; pp. 149–159. [Google Scholar]
- Amyot, D. Introduction to the User Requirements Notation: Learning by example. Comput. Netw. 2003, 42, 285–301. [Google Scholar] [CrossRef]
- Amyot, D.; He, X.; He, Y.; Cho, D.Y. Generating scenarios from use case map specifications. In Proceedings of the 3rd International Conference on Quality Software (QSIC’03), Dallas, TX, USA, 6–7 November 2003; pp. 108–115. [Google Scholar] [CrossRef]
- Kerrigan, S.; Law, K.H. Logic-based Regulation Compliance-assistance. In Proceedings of the 9th International Conference on Artificial Intelligence and Law (ICAIL’03), Scotland, UK, 24–28 June 2003; pp. 126–135. [Google Scholar] [CrossRef]
- Vardi, M.Y. Branching vs. Linear Time: Final Showdown. In Tools and Algorithms for the Construction and Analysis of Systems; Margaria, T., Yi, W., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2031, pp. 1–22. [Google Scholar] [CrossRef]
- Hashmi, M.; Governatori, G.; Lam, H.P.; Wynn, M.T. Are We Done With Business Process Compliance: State-of-the-Art and Challenges Ahead. Knowl. Inf. Syst. 2018, 57, 79–133. [Google Scholar] [CrossRef]
- Sackmann, S.; Kühnel, S.; Seyffarth, T. Using Business Process Compliance Approaches for Compliance Management with regard to Digitization: Evidence from a Systematic Literature Review. In Proceedings of the 16th International Conference Business Process Management (BPM’18), Sydney, NSW, Australia, 9–14 September 2018. [Google Scholar]
- Ramezani, E.; Fahland, D.; van der Werf, J.M.E.M.; Mattheis, P. Separating Compliance Management and Business Process Management. In Proceedings of the 9th International Workshops (BPM’11), Clermont-Ferrand, France, 29 August 2011; Revised Selected Papers; Part II. pp. 459–464. [Google Scholar] [CrossRef]
- Casanovas, P.; González-Conejero, J.; de Koker, L. Legal Compliance by Design (LCbD) and through Design (LCtD): Preliminary Survey. In Proceedings of the 1st Workshop on Technologies for Regulatory Compliance Co-Located with the 30th International Conference on Legal Knowledge and Information Systems (JURIX’17), Luxembourg, 17 September 2017; pp. 33–49. [Google Scholar]
- Goedertier, S.; Vanthienen, J.; Caron, F. Declarative business process modelling: Principles and modelling languages. Enterp. Inf. Syst. 2015, 9, 161–185. [Google Scholar] [CrossRef]





| Language | Approach | Classification | |||
|---|---|---|---|---|---|
| Graph | Pattern | Query | Logic | ||
| BPMN-Q [32] * | Pattern-based language expressing compliance requirements as BPMN graphs with a formal representation in CTL. | X | X | X | |
| CRL [33] * | Pattern-based language expressing compliance requirements as atomic and composite pattern with a formal representation in LTL and MTL. | X | |||
| Declare [28] * | Framework supporting several declarative languages (i.e., ConDec, ConDec++, DecSerFlow) for modelling graphical constraints with a formal representation in LTL. | X | X | ||
| DCR [34] | Combination of two logics for verifying compliance via model checking. Process and organisational view are expressed as graphs before being translated into description logic. The data view is implemented as hybrid logic. | X | X | X | |
| DMQL [35] * | Query language based on graph theory for matching patterns in conceptual models represented in arbitrary modelling languages. | X | X | X | |
| eCRG [36] * | Visual language for modelling compliance rules with a formal representation in FOL. Specified compliance rules are verified against event logs. | X | |||
| PCL [37] * | Combination of deontic and defeasable logic to capture the intuition of normative requirements. Compliance rules are formally represented as obligations, prohibitions and permissions. | X | |||
| Petri-net Pattern [38] | Repository of frequent compliance patterns formally represented as Petri-nets. Conformance checks are performed on the basis of event logs. | X | X | ||
| PENELOPE [39] * | Declarative language for expressing temporal deontic assignments. Compliance rules are formally represented as obligations and permissions. | X | |||
| PROPOLS [40] | Pattern-based property specification language based on OWL. Specified properties are used to verify compliance in BPEL service composition schemas. | X | X | ||
| PPSL [41] | Pattern-based property specification language based on UML activities. Constraints are modelled as visual patterns with a formal representation in LTL. | X | X | ||
| Rule Pattern [42] | Rule-based process mining approach enclosing patterns formally grounded and divided into static (FOL), dynamic (LTL) and composed pattern. | X | |||
| Control flow | R1: Order |
| R2: Occurence | |
| Data flow | R3: Data value |
| R4: Interaction | |
| Resources | R5: Employee role |
| R6: Segregation of duties | |
| Time | R7: Point in time |
| R8: Period of time (interval) |
| ID | Compliance Requirement |
|---|---|
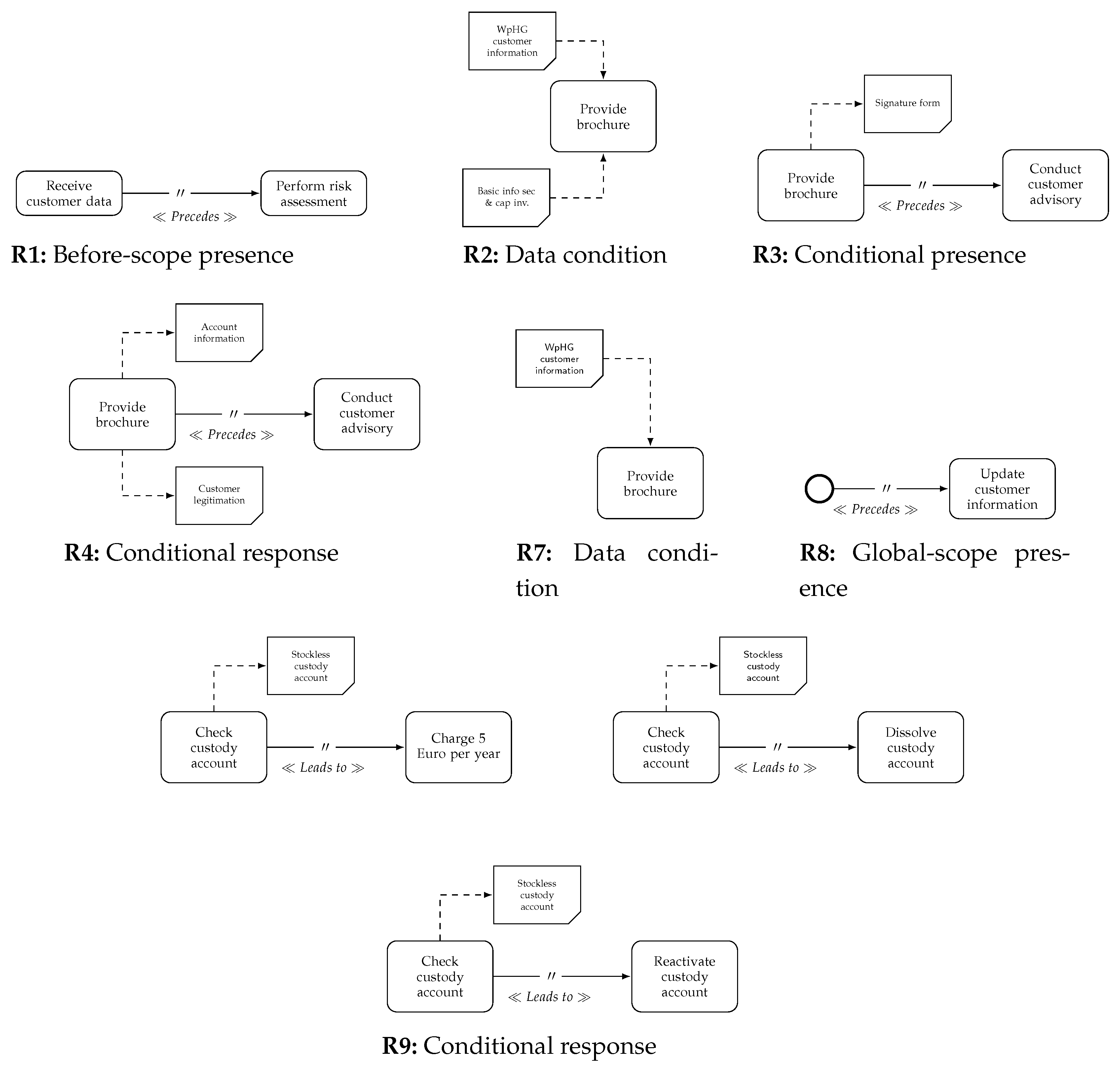
| R1 | The customer data must be received before the individual risk assessment can take place. |
| R2 | The customer advisor must provide the two obligatory brochures WpHG Customer Information and the Basic Information Securities and Capital Investment. |
| R3 | The customer advisor must ensure that the customer acknowledges receipt of the two brochures |
| R4 | After concluding the custody account contract, the customer legitimation and the account documents need to be send to market support. |
| R5 | The investment advice needs to be conducted by a customer advisor with a securities competence of level C or above. |
| R6 | The customer identification and legitimation must be handled by the customer advisor, while suspected cases of money laundering must be checked by an anti-money-laundering officer. |
| R7 | Before concluding a custody-account contract, the customer advisor needs to wait until the suspected case of anti-money laundering is resolved. |
| R8 | The customer information must be updated with every future customer contact. |
| R9 | Stockless custody accounts are charged with a fee of EUR 5 per year. If the fee is not paid, the account is terminated by market support. The account is reactivated by a new securities purchase. |
| Pattern | Type | CTL Mapping |
|---|---|---|
 | Global-scope Presence (Leads To) | AG(start → AF(executed(A))) |
 | Conditional Response (Leads to) | AG((executed(A) ∧ stableDataCondition)→ AF(executed(B))) |
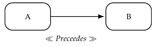 | Before-scope Presence (Precedence) | ¬E[¬executed(A) U ready(B)] |
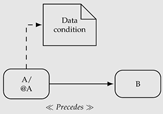 | Conditional Presence (Precedence) | ¬E[¬(executed(A) ∧ stableDataCondition) U ready(B)]b |
| ID | CTL Representation |
|---|---|
| R1 | ¬E[¬executed(Receive customer data) U ready(Perform risk assessment)] |
| R2 | AG(ready(Check new customer) → state(Customer information brochure, provided)) |
| AG(ready(Check new customer) → state(Basic information securities and capital investment brochure, provided)) | |
| R3 | ¬E[¬(executed(Conduct customer advisory) ∧ state(Signature form, signed) U ready(Provide brochures)] |
| R4 | AG((executed(Conclude custody account contract) ∧ state(Documents, received)) → AF(executed(Send account information and legitimation documents))) |
| R5 | R5 cannot be modelled with BPMN-Q semantics. |
| R6 | R6 cannot be modelled with BPMN-Q semantics. |
| R7 | AG(ready(Conclude custody account) → state(Money-laundering case, solved)) |
| R8 | AG(start → AF(executed(Update customer information))) |
| R9 | R9 cannot be modelled with BPMN-Q semantics. |
| Pattern | Type | LTL Mapping |
|---|---|---|
| P Exists | Atomic Pattern | F(P) |
| P LeadsTo Q | Atomic Pattern | G(P → F(Q)) |
| P Precedes Q | Atomic Pattern | ¬Q W P |
| t PerformedBy R | Resource Pattern | G(t → t.Role(R)) |
| SegregatedFrom | Resource Pattern | G(.Role(R) →¬(.Role(R))∧ G(.User(U) →¬(.User(U)) |
| P Frees Q | Atomic Pattern | P R Q |
| P (LeadsTo|DirectlyFollowedBy) (Else|ElseNext) , …, (Else|ElseNext) | Atomic Pattern | G(p → F|X((F|X() |
| F|X())))) |
| ID | Pattern and LTL Representation | |
|---|---|---|
| R1 | ReceiveCustomerData Precedes PerformRiskAssessment | |
| ¬ReceiveCustomerData W(PerformRiskAssessment) | ||
| R2 | (CustomerInformationBrochure And SecuritiesAndCapitalInvestmentBrochure) Exists | |
| F(CustomerInformationBrochure ∧ SecuritiesAndCapitalInvestmentBrochure) | ||
| R3 | NewCustomer.AcknowledgeInformationBrochures=‘Yes’ FreesConductCustomerAdvisory | |
| NewCustomer.AcknowledgeInformationBrochures=‘Yes’ R(ConductCustomerAdvisory) | ||
| R4 | ConcludeCustodyAccountContract LeadsTo (SendAccountDocuments And SendCustomerLegitimation) | |
| G(ConcludeCustodyAccountContract → F(SendAccountDocuments∧ SendCustomerLegitimation)) | ||
| R5 | ConductInvestmentAdvice PerformedBy Role.CustomerAdvisorSecuritiesCompetence ≥ ‘C’ | |
| G(ConductInvestmentAdvice →ConductInvestmentAdvice.Role(‘CustomerAdvisor’∧ SecuritiesCompetence≥ ‘C’)) | ||
| R6 | (ConductCustomerIdentification And ConductCustomerLegitimation) SegregatedFrom CheckSuspectedMoneyLaunderingCase | |
| G((ConductCustomerIndentification.Role(‘CustomerAdvisor’) ∧ConductCustomerLegitimation.Role(‘CustomerAdvisor’)) →¬(CheckSuspectedMoneyLaunderingCase.Role(‘AntiMoneyLaunderingOfficer’)) ∧ G((ConductCustomerIndentification.User(‘U’) ∧ ConductCustomerLegitimation.User(‘U’)) →¬(CheckSuspectedMoneyLaunderingCase.User(‘U’)) | ||
| R7 | MoneyLaunderingCase.Solved=‘Yes’ Frees ConcludeCustodyAccount | |
| MoneyLaunderingCase.Solved=‘Yes’ R(ConcludeCustodyAccount) | ||
| R8 | CustomerContact LeadsTo UpdateCustomerInformation | |
| G(CustomerContact → F(UpdateCustomerInformation)) | ||
| R9 | ((CheckCustodyAccount =‘Stockless’) LeadsTo (CustomerPayFee= 5 ‘Euro’)) Else DissolveCustodyAccount Else ReactivateDissolvedCustodyAccount | |
| G((CheckCustodyAccount =‘Stockless’) → (F(CustomerPayFee= 5 ‘Euro’) ∧ F(CustomerPayFeeNotSuccceed) ∧ (CustomerPayFeeNotSuccceed) → X(DissolveCustodyAccountNotSucceed) ∧ F(DissolveCustodyAccountNotSucceed) ∧ (DissolveCustodyAccountNotSucceed) F(ReactivateDissolvedCustodyAccount)))) | ||
| Visual Constraint | Control Flow Pattern | LTL Mapping |
|---|---|---|
 | (A) | F(A) |
 | (A,B) | F(A)→F(B) |
 | (A,B) | F(A)↔F(B) |
 | (A,B) | F(A)↔F(B) |
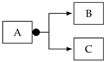 | (A,(B,C)) | G(A→F(B∨C)) |
 | (A,B) | (F B)→ () |
 | (A,B) | ((F A)∧(¬F B))∨((¬F A)∧(F B)) |
| ID | Pattern and LTL Representation |
|---|---|
| R1 | (Receive customer data,Perform risk assessment) |
| (F )→ () | |
| R2 | () |
| F() | |
| R3 | (,Ensure Acknowledgement) |
| F()↔F() | |
| R4 | (,Send Documents) |
| F()↔F() | |
| R5 | R5 cannot be modelled withDeclaresemantics. |
| R6 | R6 cannot be modelled withDeclaresemantics. |
| R7 | (Check Suspected Case,Conclude Contract) |
| (F )→ () | |
| R8 | (,Update Customer Information) |
| F()→F() | |
| R9 | (,(,)) |
| G(→F(∨)) | |
| (,) | |
| (,) | |
| (,Reactivate Account) | |
| F()↔F() |
| R1 | |
|---|---|
| R2 | |
| R3 | |
| R4 | |
| R5 | |
| R6-1 | |
| R6-2 | |
| R7 | |
| R8 | |
| R9-1 | |
| R9-2 | |
| Nodes | Edge Directions |
|---|---|
 | 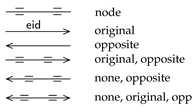 |
| Operator | Intuitive Reading |
|---|---|
| achievement, persistent, preemptive | |
| [OAPP] | |
| achievement, persistent, non-preemptive | |
| [OAPNP] | |
| achievement, non-persistent, preemptive | |
| [OANPP] | |
| achievement, non-persistent, non-preemptive | |
| [OANPNP] | |
| maintenance | |
| [M] | |
| punctual | |
| [P] |
| ID | Compliance Requirements |
|---|---|
| R1 | |
| R2 | |
| R3 | |
| R4 | |
| R5 | |
| R6 | (1) |
| (2) | |
| R7 | (1) |
| Alternatively | |
| (2) | |
| R8 | |
| R9 | (1) |
| (2) | |
| Alternatively | |
| (1) | |
| (2) | |
| (3) | |
| Terms | Meanings |
|---|---|
| Oblig() | agent π must perform the activity α by due date δ |
| Per() | agent π can perform the activity α prior to due date δ |
| CC() | agent π must perform activity by due date after activity is performed prior to the due date |
| ID | Compliance Requirements |
|---|---|
| R1 | |
| R2 | ⟵ |
| R3 | ⟵ |
| R4 | |
| R5 | ⟵ |
| ∧ | |
| R6 | provides a maintenance obligation which cannot be modeled with PENELOPE semantics. |
| R7 | ⟵ |
| R8 | is a maintenance obligation, which cannot be modeled with PENELOPE semantics. |
| R9 | |
| Language | Deontic Modalities | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Punctual | Achievement | Preemptive | Non-preemptive | Maintenance | Perdurant | Permission | Prohibition | Violation | Compensation | |
| BPMN-Q | − | + | − | − | + | − | − | + | + | (+) |
| CRL | (+) | + | − | − | + | − | − | + | + | + |
| Declare | (+) | + | + | + | + | − | − | + | + | (+) |
| DMQL | + | + | + | + | − | − | − | + | (+) | (+) |
| eCRG | + | + | + | + | + | + | (+) | + | + | + |
| PCL | + | + | + | + | + | + | + | + | + | + |
| PENELOPE | − | + | − | − | − | − | + | − | − | − |
| Language | n | N | V | D | E | SD | Min. | Max. |
|---|---|---|---|---|---|---|---|---|
| BPMN-Q | 4.67 | 8.00 | 16.89 | 2.79 | 67.03 | 100.76 | R7 | R9 |
| CRL | 3.44 | 5.11 | 9.66 | 2.25 | 31.17 | 41.49 | R1/R8 | R9 |
| Declare | 2.57 | 3.86 | 5.81 | 1.43 | 15.92 | 34.45 | R2 | R9 |
| DMQL | 5.67 | 8.56 | 22.43 | 1.54 | 47.75 | 64.20 | R1 | R9 |
| eCRG | 8.22 | 12.89 | 44.31 | 4.44 | 440.70 | 1,051.10 | R8 | R9 |
| PCL | 5.67 | 5.89 | 13.03 | 1.81 | 15.76/16.36 * | 6.86/6.73 * | R1 | R5 |
| PENELOPE | 12.14 | 17.29 | 62.05 | 3.94 | 267.51 | 197.73 | R5 | R4 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zasada, A.; Hashmi, M.; Fellmann, M.; Knuplesch, D. Evaluation of Compliance Rule Languages for Modelling Regulatory Compliance Requirements. Software 2023, 2, 71-120. https://doi.org/10.3390/software2010004
Zasada A, Hashmi M, Fellmann M, Knuplesch D. Evaluation of Compliance Rule Languages for Modelling Regulatory Compliance Requirements. Software. 2023; 2(1):71-120. https://doi.org/10.3390/software2010004
Chicago/Turabian StyleZasada, Andrea, Mustafa Hashmi, Michael Fellmann, and David Knuplesch. 2023. "Evaluation of Compliance Rule Languages for Modelling Regulatory Compliance Requirements" Software 2, no. 1: 71-120. https://doi.org/10.3390/software2010004
APA StyleZasada, A., Hashmi, M., Fellmann, M., & Knuplesch, D. (2023). Evaluation of Compliance Rule Languages for Modelling Regulatory Compliance Requirements. Software, 2(1), 71-120. https://doi.org/10.3390/software2010004







