Power Consumption Efficiency of Encryption Schemes for RFID
Abstract
:1. Introduction
2. Background and Related Work
2.1. Security Level
- operations to break 7 rounds of 256-bit AES;
- operations to break 8 rounds of 256-bit AES.
- operations to break 7 rounds of 256-bit Salsa20;
- operations to break 8 rounds of 256-bit Salsa20.
2.2. AES and Salsa20 Implementations
2.3. Salsa20 vs. ChaCha8 for RFID Applications
3. Algorithm Descriptions
3.1. The AES Algorithm
- AddroundKey transformation: this is simply the XOR between each bit of the State to each bit of the round key. This is the operation that depends on the cryptography key.
- SubByte transformation: this is a non-linear byte substitution. It has two steps, of which the first one is a multiplicative inverse and the other is an affine transformation.
- ShiftRow transformation: this is a byte-wise operation. The first row of the State is not shifted, but the last three rows of the State are rotated over 1, 2, and 3 bytes, respectively. This operation adds linear diffusion.
- MixColumn transformation adds linear diffusion into the cryptography. Each column of the State is combined using an invertible linear transformation. Each column is treated as a polynomial over GF (Galois field) and it is then multiplied by a fixed polynomial modulo , given by
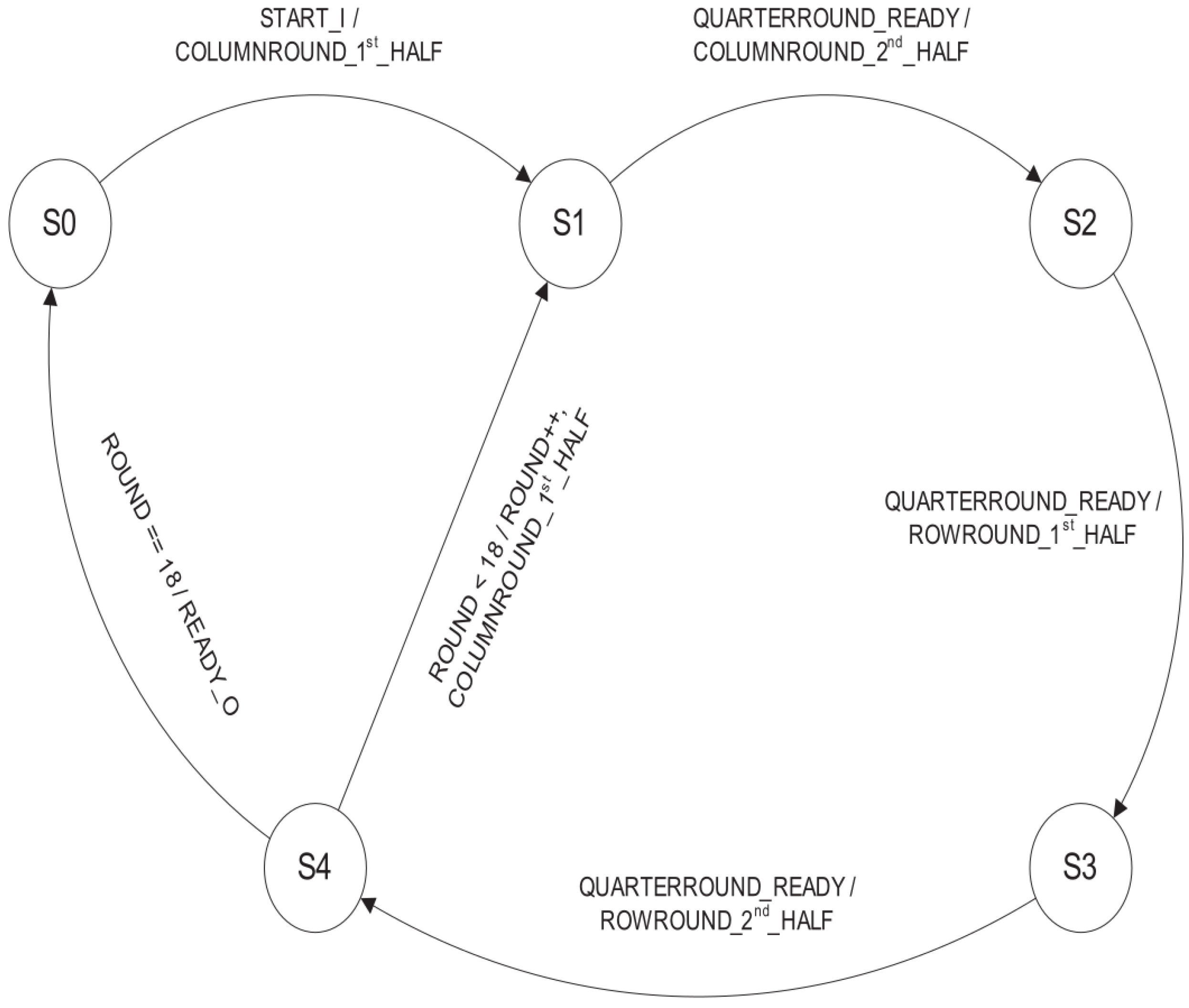
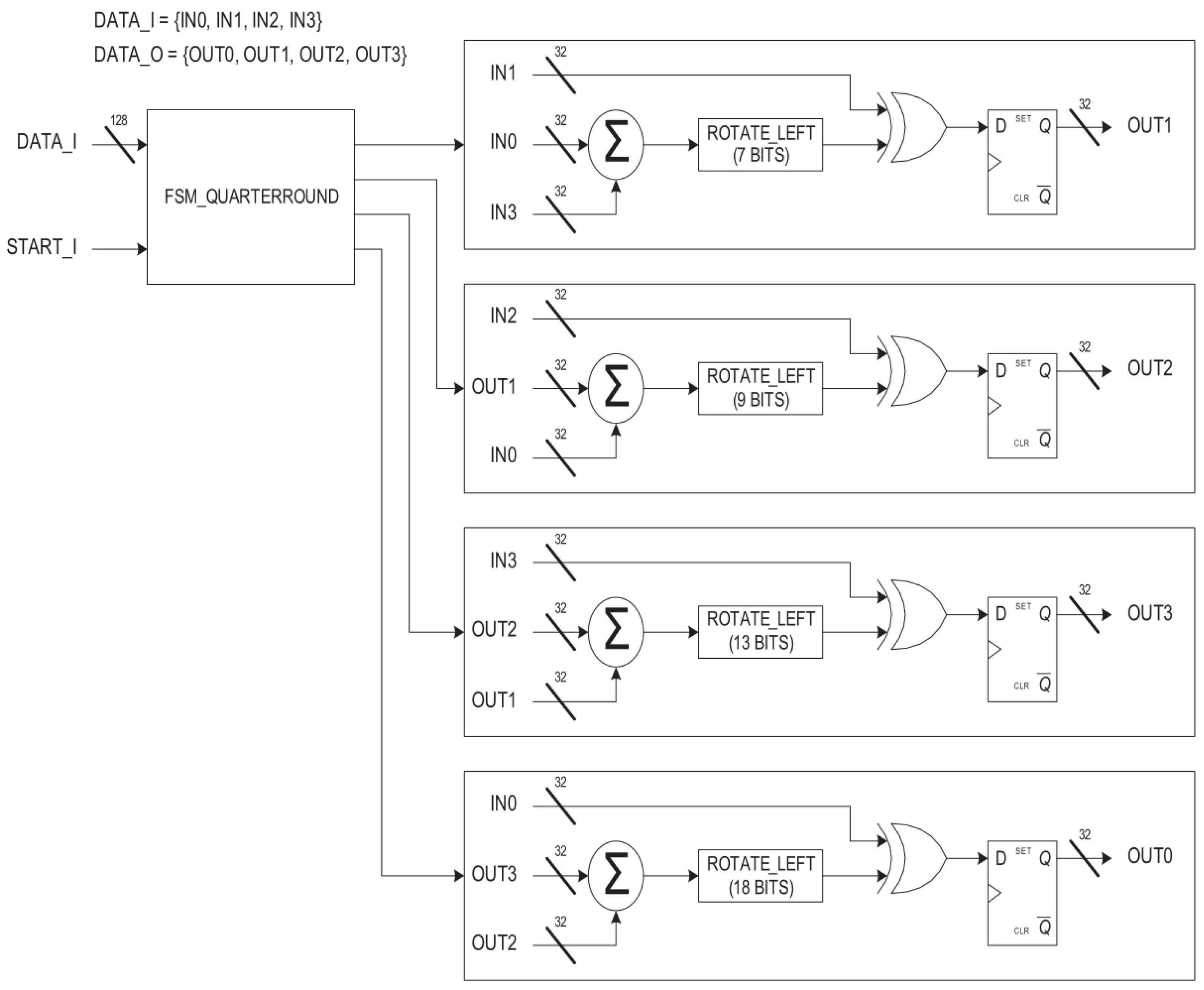
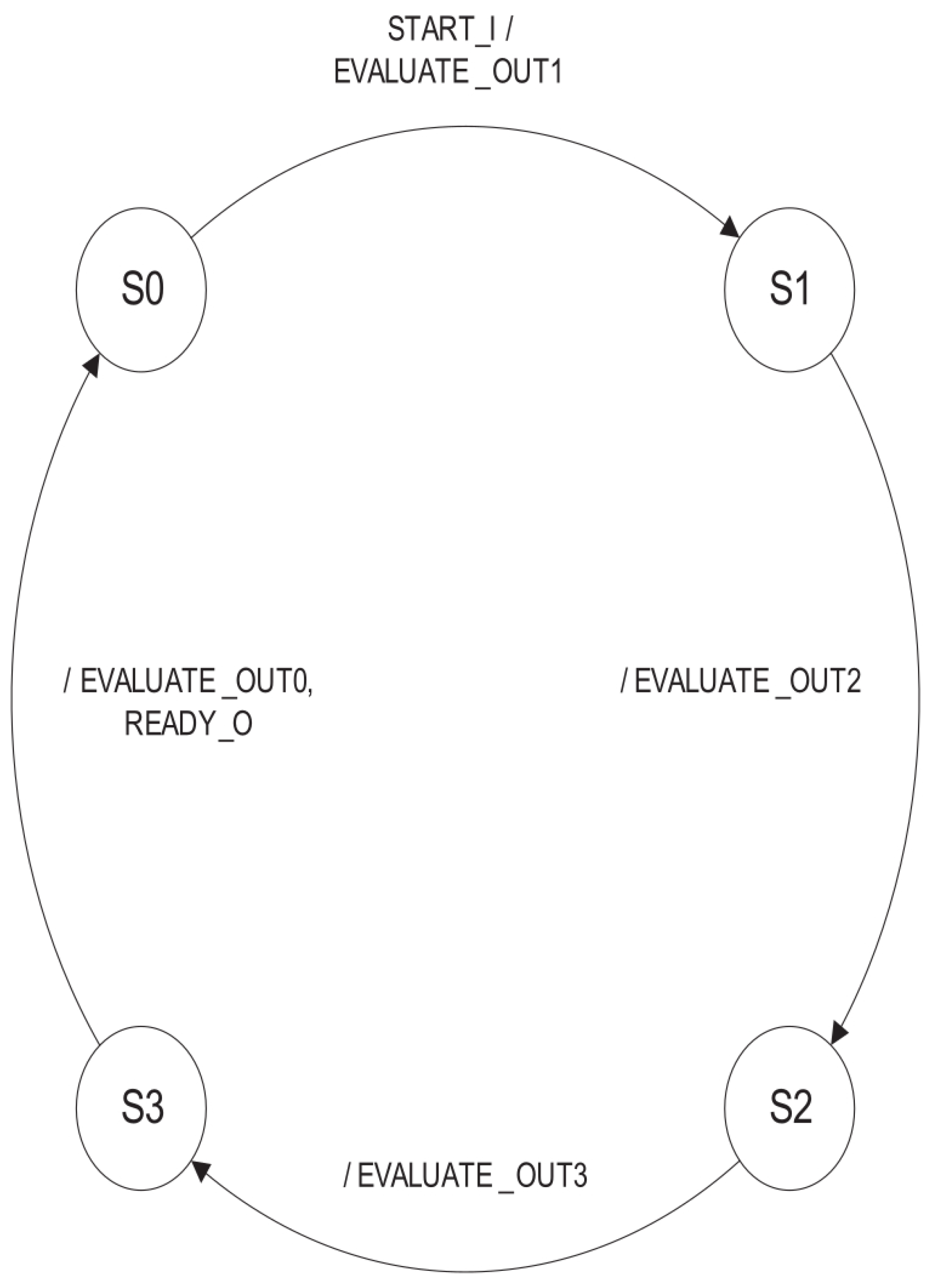
3.2. The Salsa20 Algorithm
4. Algorithm Implementations
4.1. AES Implementation
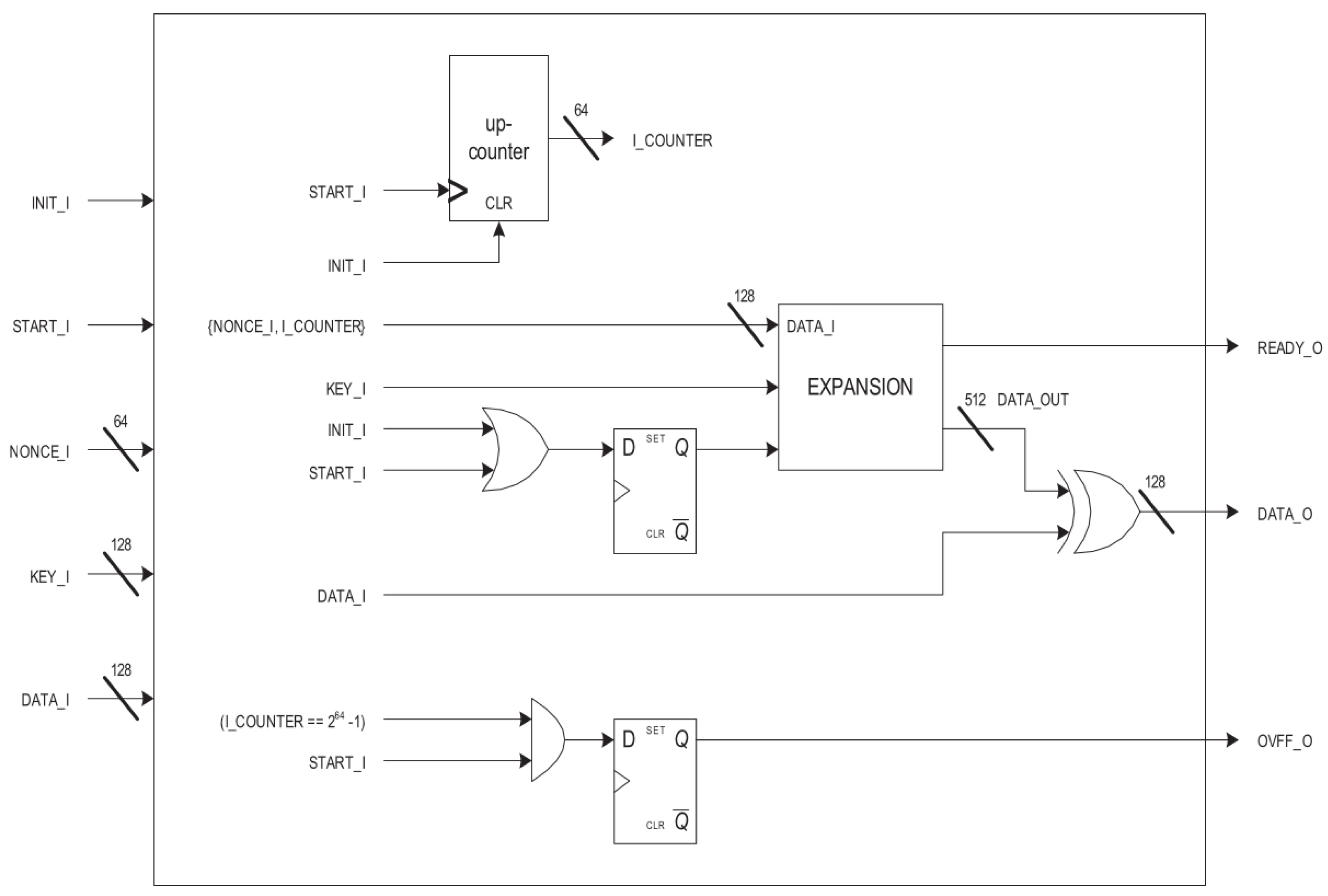
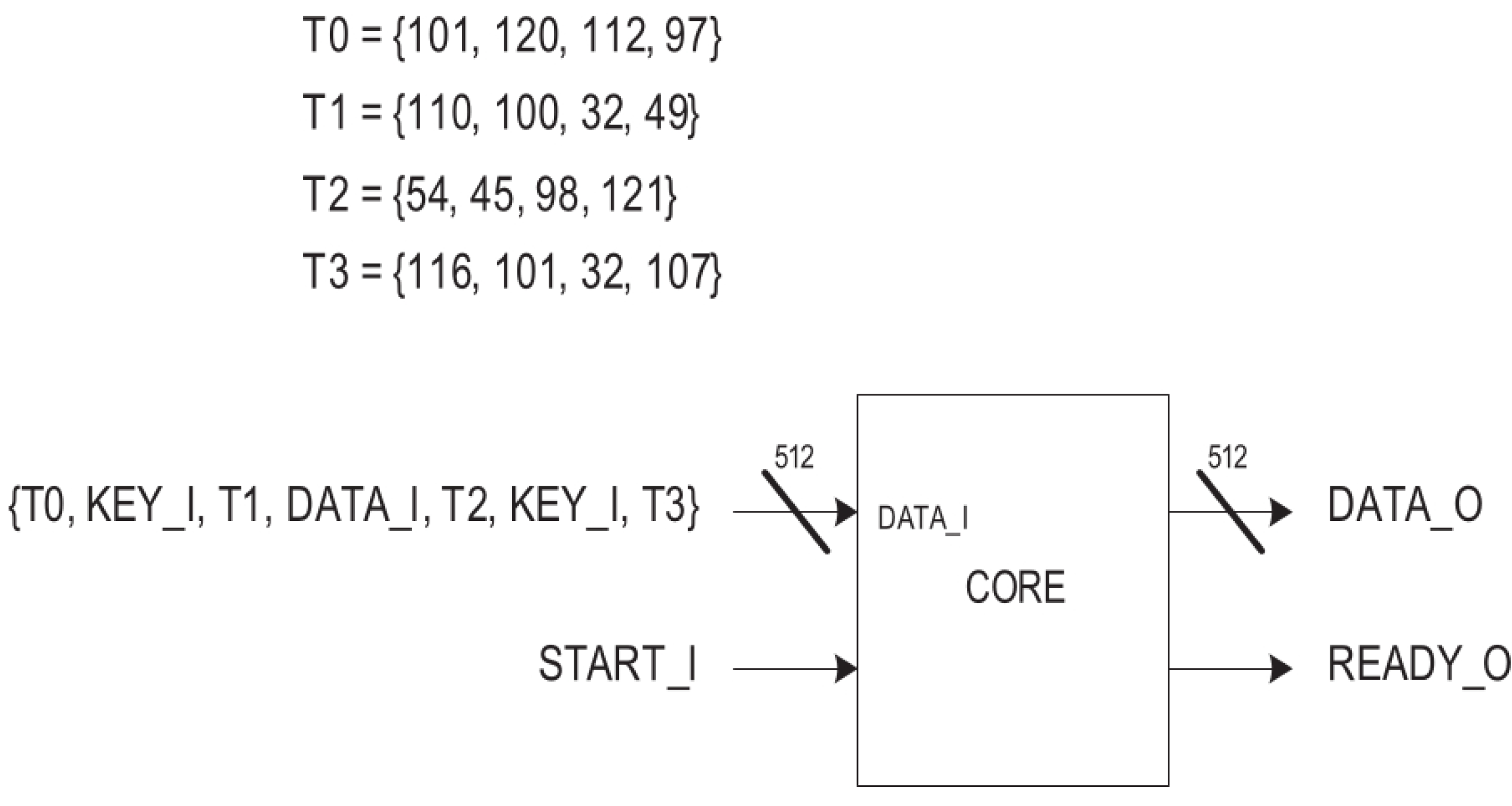
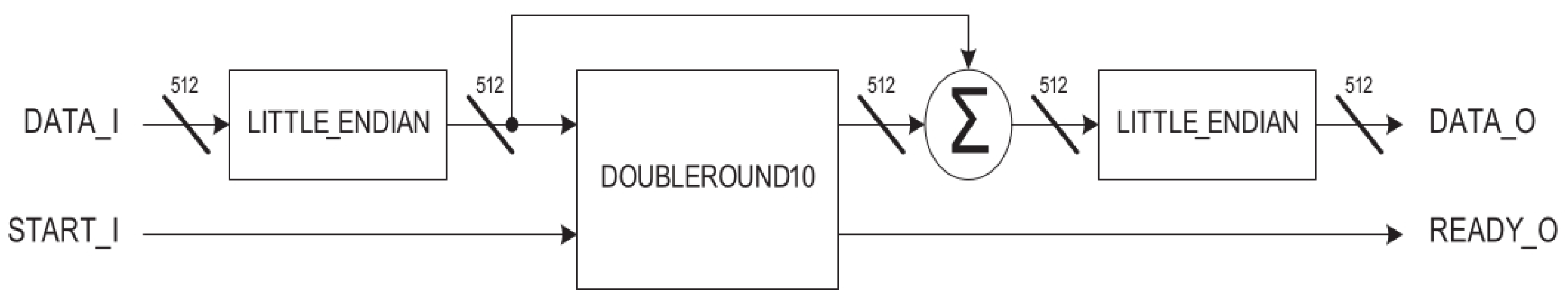
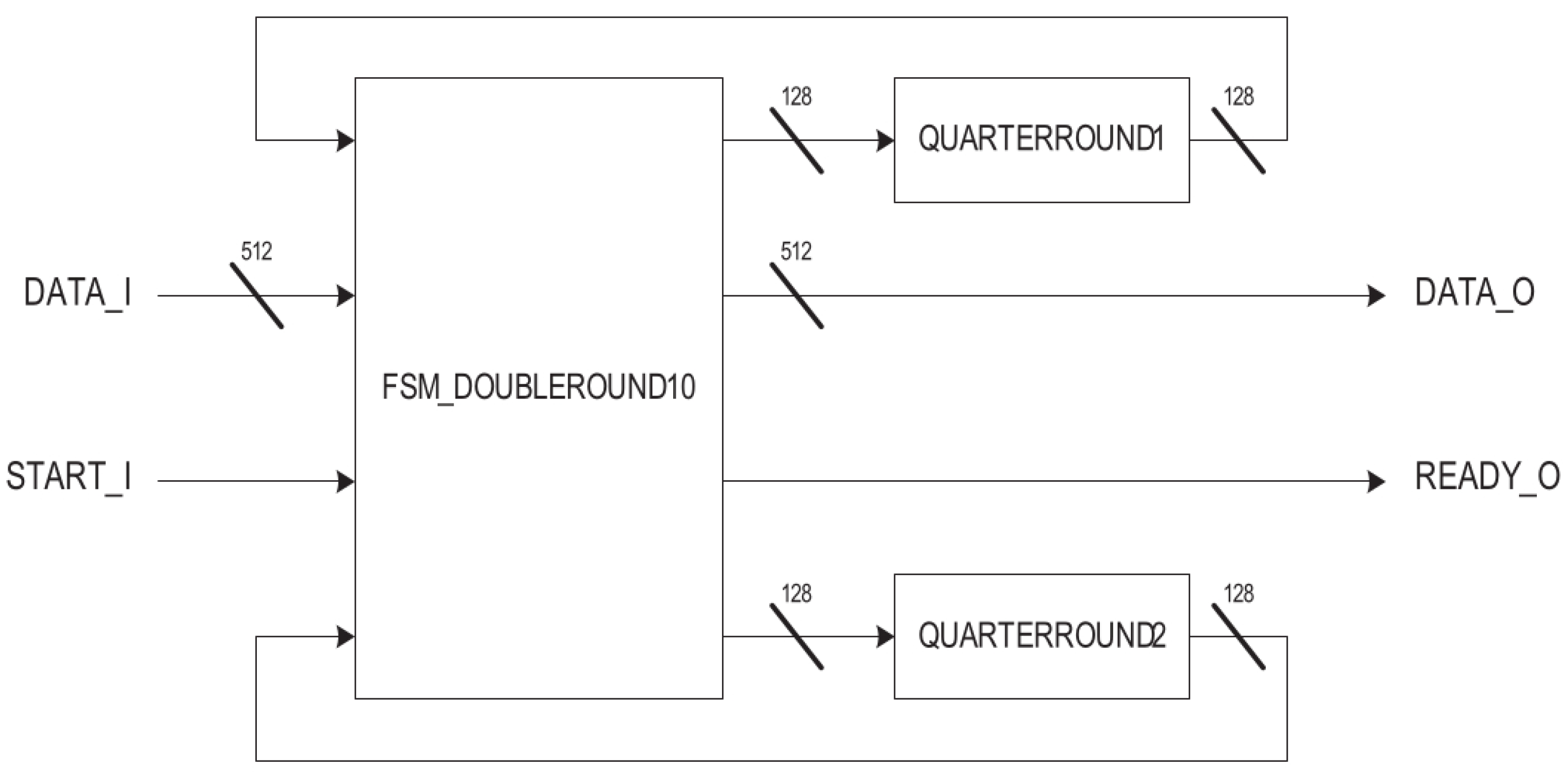
4.2. Salsa20 Implementation
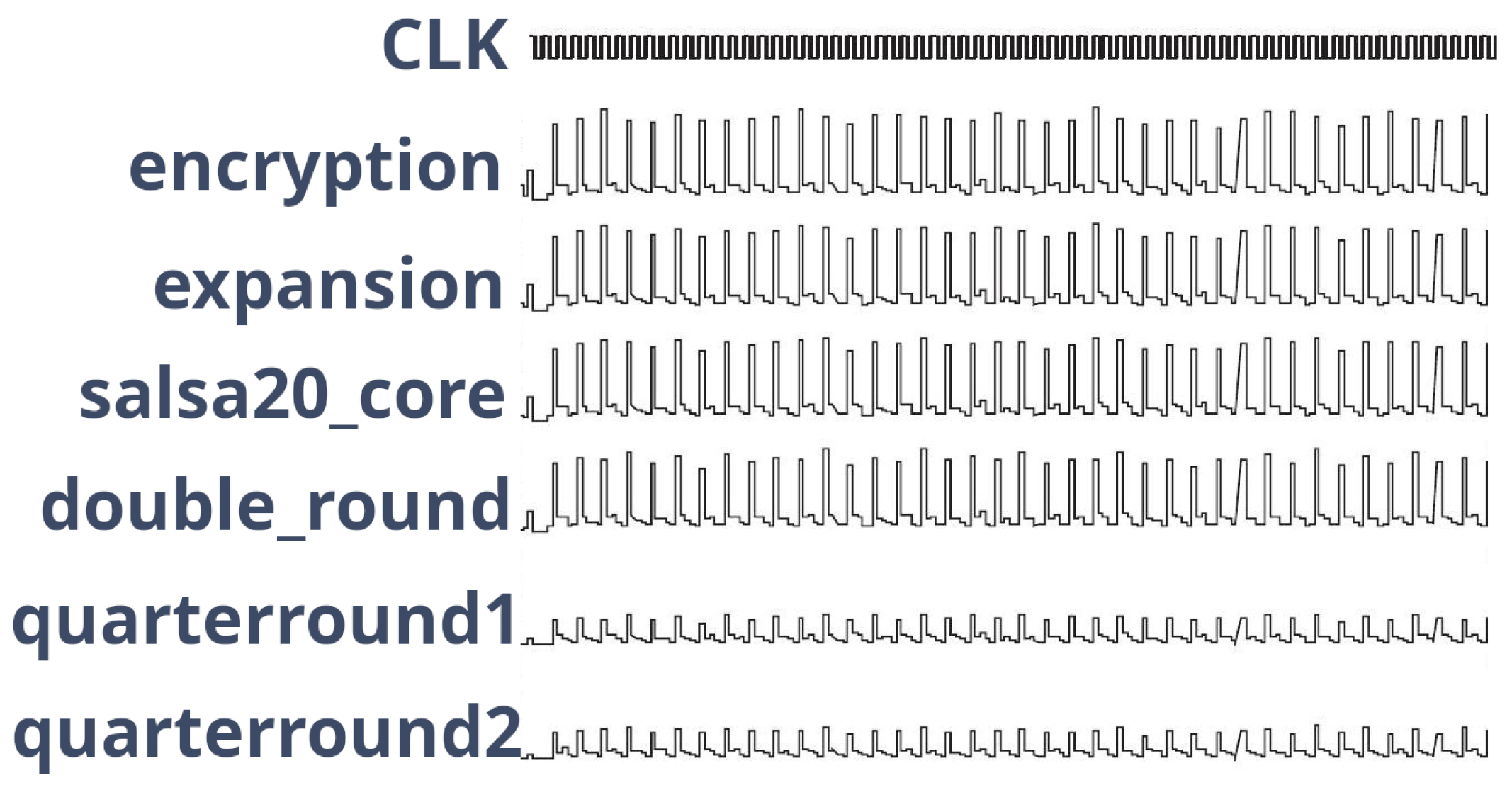
5. Results and Discussion
5.1. AES Design
5.2. Salsa20 Design
5.3. Layout Comparison
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Munoz-Ausecha, C.; Ruiz-Rosero, J.; Ramirez-Gonzalez, G. RFID applications and security review. Computation 2021, 9, 69. [Google Scholar] [CrossRef]
- Casella, G.; Bigliardi, B.; Bottani, E. The evolution of RFID technology in the logistics field: A review. Procedia Comput. Sci. 2022, 200, 1582–1592. [Google Scholar] [CrossRef]
- Costa, F.; Genovesi, S.; Borgese, M.; Michel, A.; Dicandia, F.A.; Manara, G. A review of RFID sensors, the new frontier of internet of things. Sensors 2021, 21, 3138. [Google Scholar] [CrossRef] [PubMed]
- Oren, Y.; Feldhofer, M. A low-resource public-key identification scheme for RFID tags and sensor nodes. In Proceedings of the Second ACM Conference on Wireless Network Security (WiSec ‘09), Zurich, Switzerland, 16–19 March 2009; Association for Computing Machinery: New York, NY, USA, 2009; pp. 59–68. [Google Scholar]
- FIPS-197; Advanced Encryption Standard. National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, November 2001.
- Piret, G.; Quisquater, J.J. A Differential Fault Attack Technique against SPN Structures, with Application to the AES and KHAZAD. In Cryptographic Hardware and Embedded Systems—CHES 2003; Lecture Notes in Computer Science; Walter, C.D., Koç, Ç.K., Paar, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2779. [Google Scholar]
- Mangard, S. A Simple Power-Analysis (SPA) Attack on Implementations of the AES Key Expansion. In Information Security and Cryptology—ICISC 2002; Lecture Notes in Computer Science; Lee, P.J., Lim, C.H., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2587. [Google Scholar]
- Bernstein, D.J. ‘The Salsa20 Family of Stream Ciphers’ eSTREAM, ECRYPT Stream Cipher Project, Report 2005/025. 2005. Available online: http://www.ecrypt.eu.org/stream (accessed on 1 January 2020).
- Fischer, S.; Meier, W.; Berbain, C.; Biasse, J.F.; Robshaw, M.J.B. Non-Randomness in eSTREAM Candidates Salsa20 and TSC-4. In Progress in Cryptology—INDOCRYPT 2006; Lecture Notes in Computer Science; Barua, R., Lange, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4329. [Google Scholar]
- Tsunoo, Y.; Saito, T.; Kubo, H.; Suzaki, T.; Nakashima, H. Differential cryptanalysis of Salsa20/8. Workshop Rec. SASC 2007, 28, 10–22. [Google Scholar]
- Fu, L.; Shen, X.; Zhu, L.; Wang, J. A low-cost UHF RFID tag chip with AES cryptography engine. Secur. Comm. Netw. 2014, 7, 365–375. [Google Scholar] [CrossRef]
- Peris-Lopez, P.; Hernandez-Castro, J.C.; Estevez-Tapiador, J.M.; Ribagorda, A. M2AP: A Minimalist Mutual-Authentication Protocol for Low-Cost RFID Tags. In Ubiquitous Intelligence and Computing. UIC 2006; Lecture Notes in Computer Science; Ma, J., Jin, H., Yang, L.T., Tsai, J.J.P., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4159. [Google Scholar]
- Satoh, A.; Morioka, S.; Takano, K.; Munetoh, S. A Compact Rijndael Hardware Architecture with S-Box Optimization. In Advances in Cryptology—ASIACRYPT 2001; Lecture Notes in Computer Science; Boyd, C., Ed.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2248. [Google Scholar]
- Mangard, S.; Aigner, M.; Dominikus, S. A highly regular and scalable AES hardware architecture. IEEE Trans. Comput. 2003, 52, 483–491. [Google Scholar] [CrossRef]
- Feldhofer, M.; Wolkerstorfer, J.; Rijmen, V. AES implementation on a grain of sand. IEE Proc. Inf. Secur. 2005, 152, 13–20. [Google Scholar] [CrossRef]
- Henzen, L.; Carbognani, F.; Felber, N.; Fichtner, W. VLSI hardware evaluation of the stream ciphers Salsa20 and ChaCha, and the compression function Rumba. In Proceedings of the 2nd International Conference on Signals, Circuits and Systems, Nabeul, Tunisia, 7–9 November 2008; pp. 1–5. [Google Scholar]
- Nikitha, G.; Kathrine, G.; Duthie, C.; Ebenezer, V.; Silas, S. Hybrid Cryptographic Algorithm to Secure Internet of Things. In Proceedings of the 7th International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 17–19 May 2023; pp. 1556–1562. [Google Scholar]
- Bokhari, M.; Afzal, S. Performance of Software and Hardware Oriented Lightweight Stream Cipher in Constraint Environment: A Review. In Proceedings of the 10th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 15–17 March 2023; pp. 1667–1672. [Google Scholar]
- Bernstein, D. ChaCha, a Variant of Salsa20. Workshop Rec. SASC 2008, 8, 3–5. [Google Scholar]
- Pfau, J.; Reuter, M.; Harbaum, T.; Hofmann, K.; Becker, J. A Hardware Perspective on the ChaCha Ciphers: Scalable Chacha8/12/20 Implementations Ranging from 476 Slices to Bitrates of 175 Gbit/s. In Proceedings of the 2019 32nd IEEE International System-on-Chip Conference (SOCC), Singapore, 3–6 September 2019; pp. 294–299. [Google Scholar] [CrossRef]






| Average Power (μW) | Encryption/Decryption (# Cycles) | Block Size (# bits) | Cells (#) | Total Area (μm2) |
|---|---|---|---|---|
| 4.01 | 180 | 128 | 4303 | 217,250 |
| Average Power (μW) |
Encryption/Decryption (# Cycles) |
Block Size (# bits) |
Cells (#) | Total Area (μm2) |
|---|---|---|---|---|
| 2.82 | 202 | 512 | 3468 | 135,150 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gazziro, M.; Carmo, J.P. Power Consumption Efficiency of Encryption Schemes for RFID. Chips 2024, 3, 216-228. https://doi.org/10.3390/chips3030010
Gazziro M, Carmo JP. Power Consumption Efficiency of Encryption Schemes for RFID. Chips. 2024; 3(3):216-228. https://doi.org/10.3390/chips3030010
Chicago/Turabian StyleGazziro, Mario, and João Paulo Carmo. 2024. "Power Consumption Efficiency of Encryption Schemes for RFID" Chips 3, no. 3: 216-228. https://doi.org/10.3390/chips3030010
APA StyleGazziro, M., & Carmo, J. P. (2024). Power Consumption Efficiency of Encryption Schemes for RFID. Chips, 3(3), 216-228. https://doi.org/10.3390/chips3030010







