A Service Recommendation Model in Cloud Environment Based on Trusted Graph-Based Collaborative Filtering Recommender System
Abstract
1. Introduction
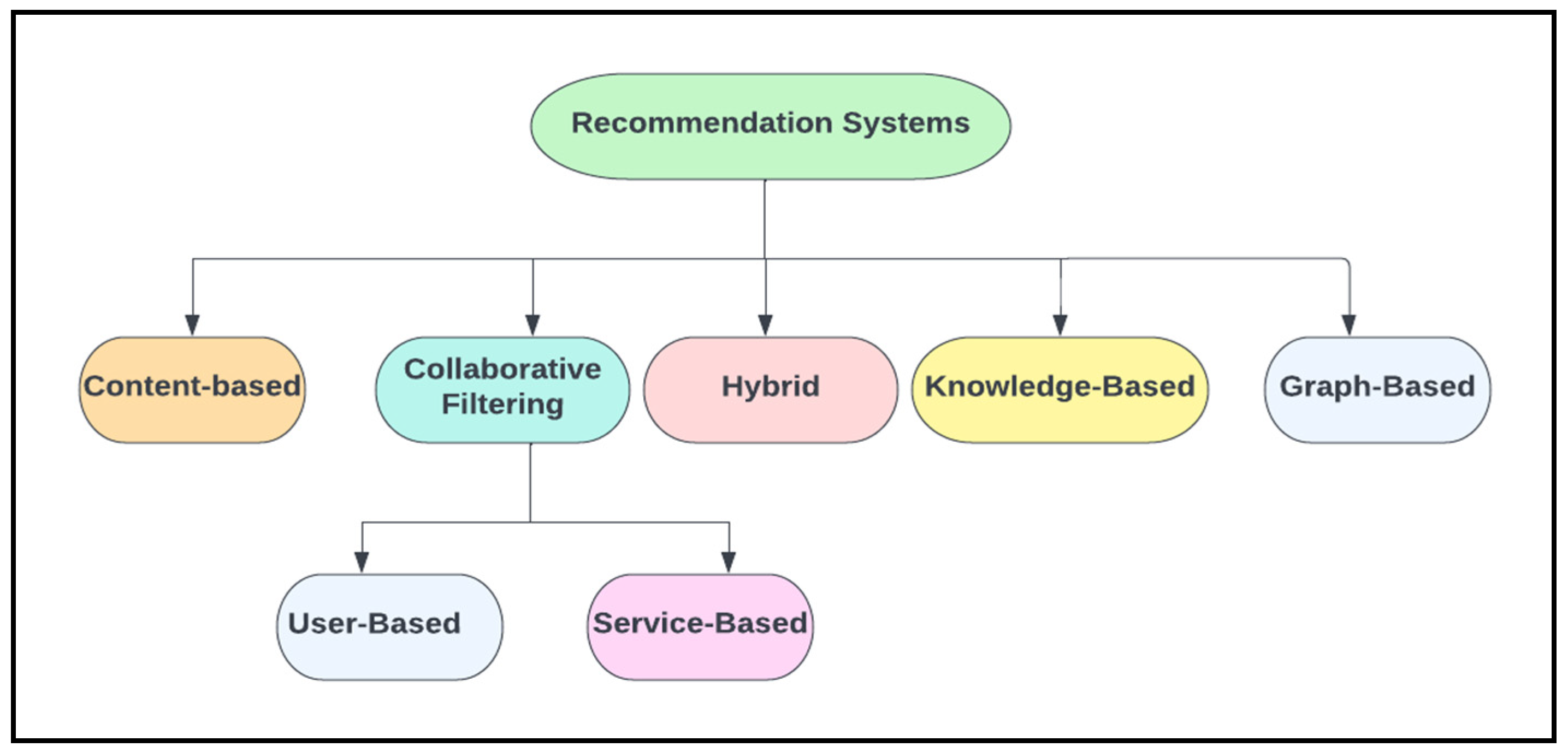
- Content-Based Filtering—Analyzes user preferences to recommend items similar to those previously selected.
- Collaborative Filtering—Identifies users with similar behavior patterns and recommends items based on shared interests.
- Hybrid Models—Combines content-based and collaborative filtering techniques to enhance accuracy and address individual limitations.
- Knowledge-Based Recommendation Systems (RS)—Relies on domain-specific knowledge and explicit user requirements.
- Graph-Based RS—Represents users and services as nodes in a graph, where edges denote interactions or recommendations; a random walk through the graph helps identify the most relevant service.
1.1. Cloud Security
1.1.1. Hard Security Mechanism—Cryptography and Access Control
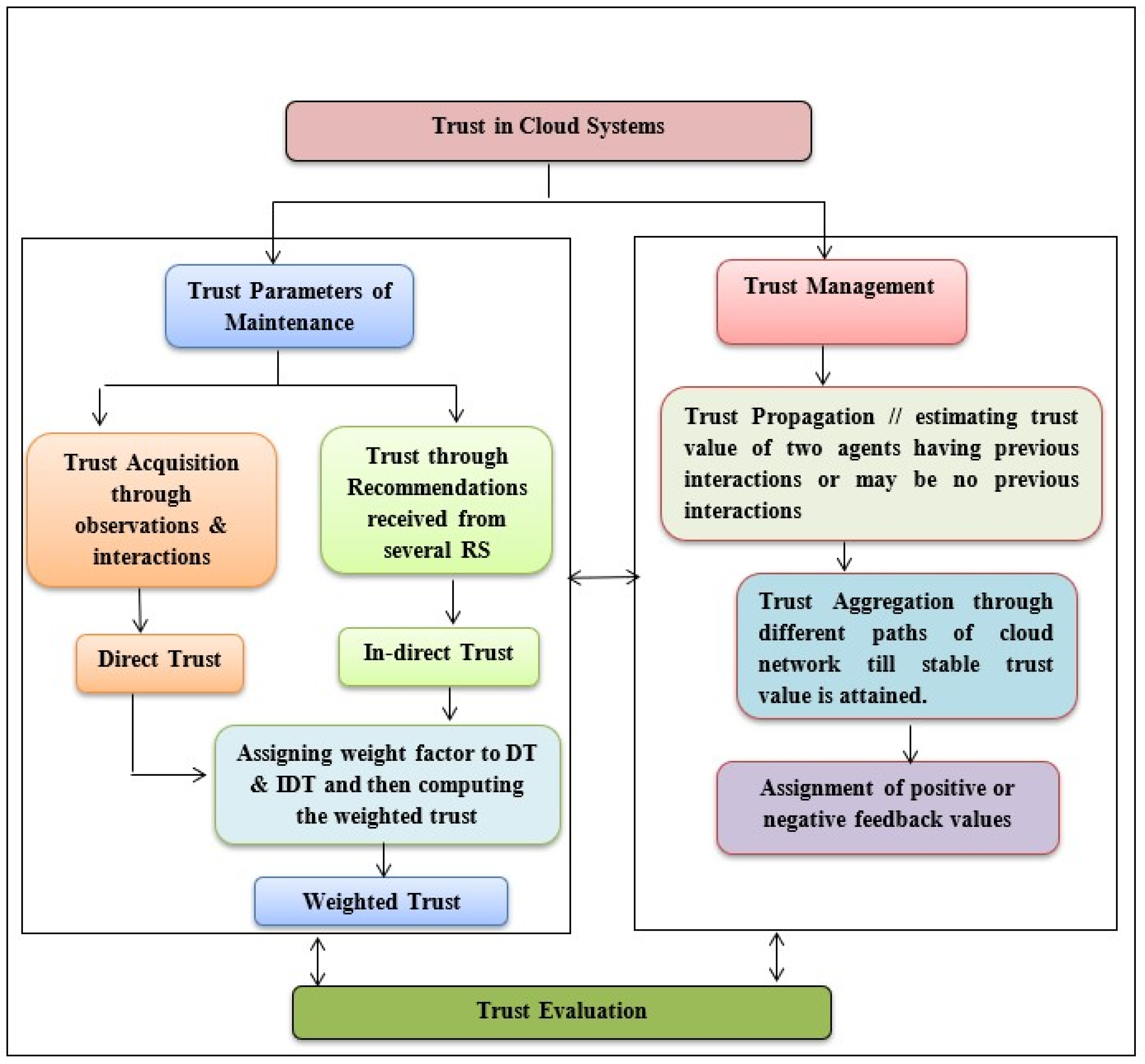
1.1.2. Soft Security Mechanism—Trust
- Direct Trust (DIT): Based on a user’s personal transaction history with the service provider.
- Indirect Trust (IDT): Derived from feedback or recommendations by neighboring nodes.
- Weighted Trust (WT): Combines direct and indirect trust using assigned weight factors to deliver a comprehensive trust score.
1.1.3. Trusted Recommendations
1.2. Novelty and Contributions
- Refinement of Trust Values through recommendation-based security analysis to detect and isolate malicious entities.
- Compute Shortest Distance between the service users using cosine similarity, based on the angular proximity of users in a distributed environment.
- Inference of Trust and construction of a Trusted User Network Set (TUNS) to enable propagation of trust.
- Similarity Index (SI) computation between the SUs on the basis of the evaluated distance between them.
- Weighted Trust computation, by assigning weights with the evaluated parameters SI and Overall Aggregate Trust (OAT) values.
- Prediction of Trusted Ratings for cloud services by utilizing the SI values of users within the TUNS and the OAT, followed by updates to the service-user matrix (SUM).
2. Literature Review
3. Identified Research Gaps and Motivation
- RG1: Lack of robust security evaluation frameworks capable of validating TMS based on user feedback, leading to an increased vulnerability to illicit access and network-level concerns such as Sybil, collusion, and DoS attacks.
- RG2: Absence of effective trust-aware recommendation models that can address core challenges such as data sparsity and cold-start problems, thereby compromising the accuracy of service predictions.
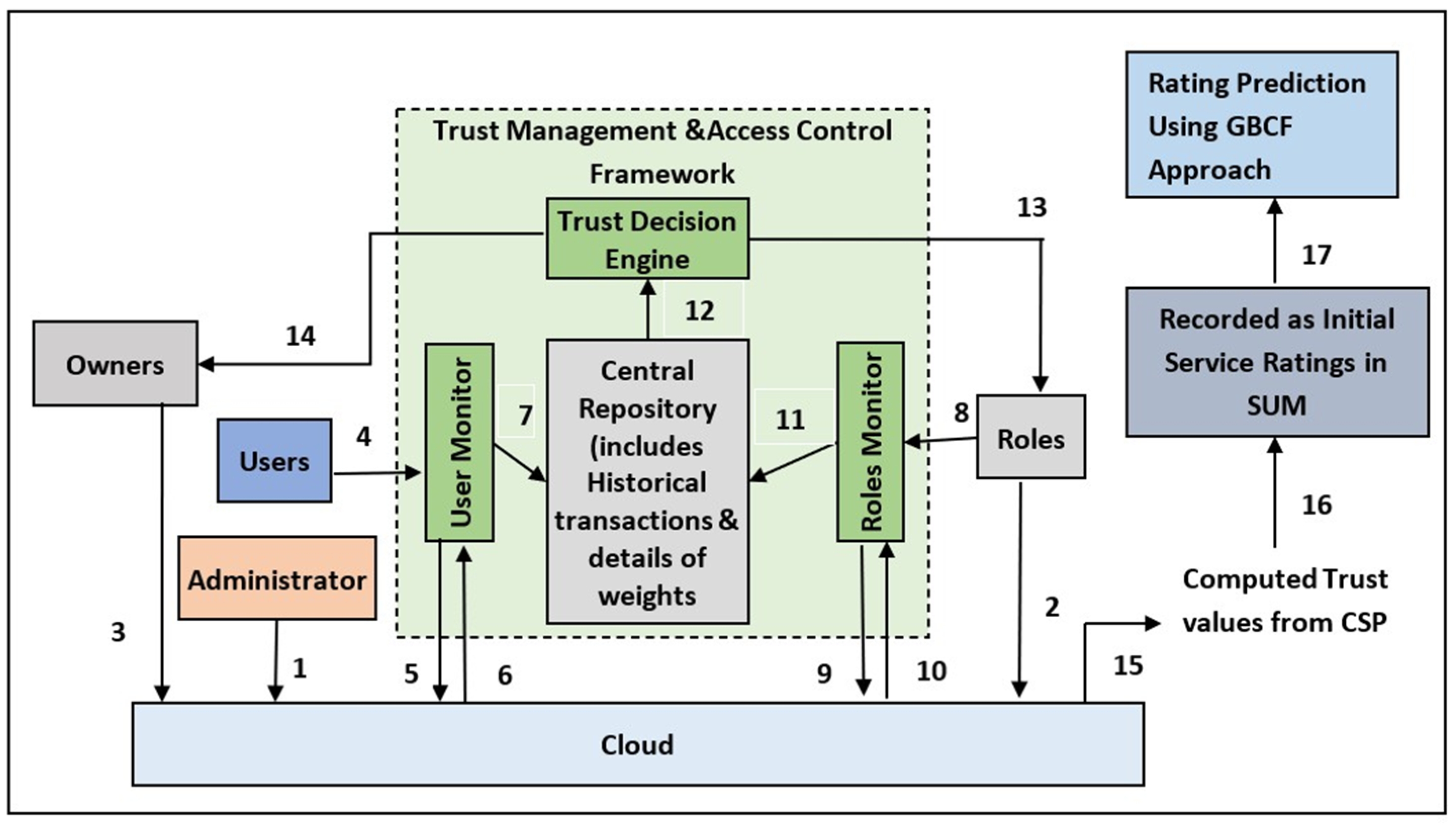
4. Proposed Work—TGBCF
4.1. Working of the TGBCF Model
- Role information via Channel 2;
- System parameters via Channel 1;
- Role updates via Channel 9.
4.2. Algorithmic Simulation of TGBCF
| Algorithm 1 Trusted User Network Construction |
| Input: SUM and AI between service users. Output: Trust user network set TUNS; 1. Initialize 2. for (any two users and in the SUM) If (AI of < TH) then ∈ TUNS of 3. Add user (, TUNS) 4. end if 5. end for 6. Return TUNS |
| Algorithm 2 TGBCF |
| Input: SUM, , SI, OAT Output: Predicted Rating 1. for each unpredicted rating (new service request) in the SUM by user in the a. If (majority ratings for service s trust threshold) go to step 2 b. else the request is denied. 2. Calculate SI and OAT between users using Equations (7) and (8). 3. End if. 4. End for. 5. Predict Rating prediction for a service s using Equation (9) 6. Output Predicted Rating. |
Computational Complexity Analysis of TGBCF
4.3. Comprehensive Analysis for Data Quality and Reliability
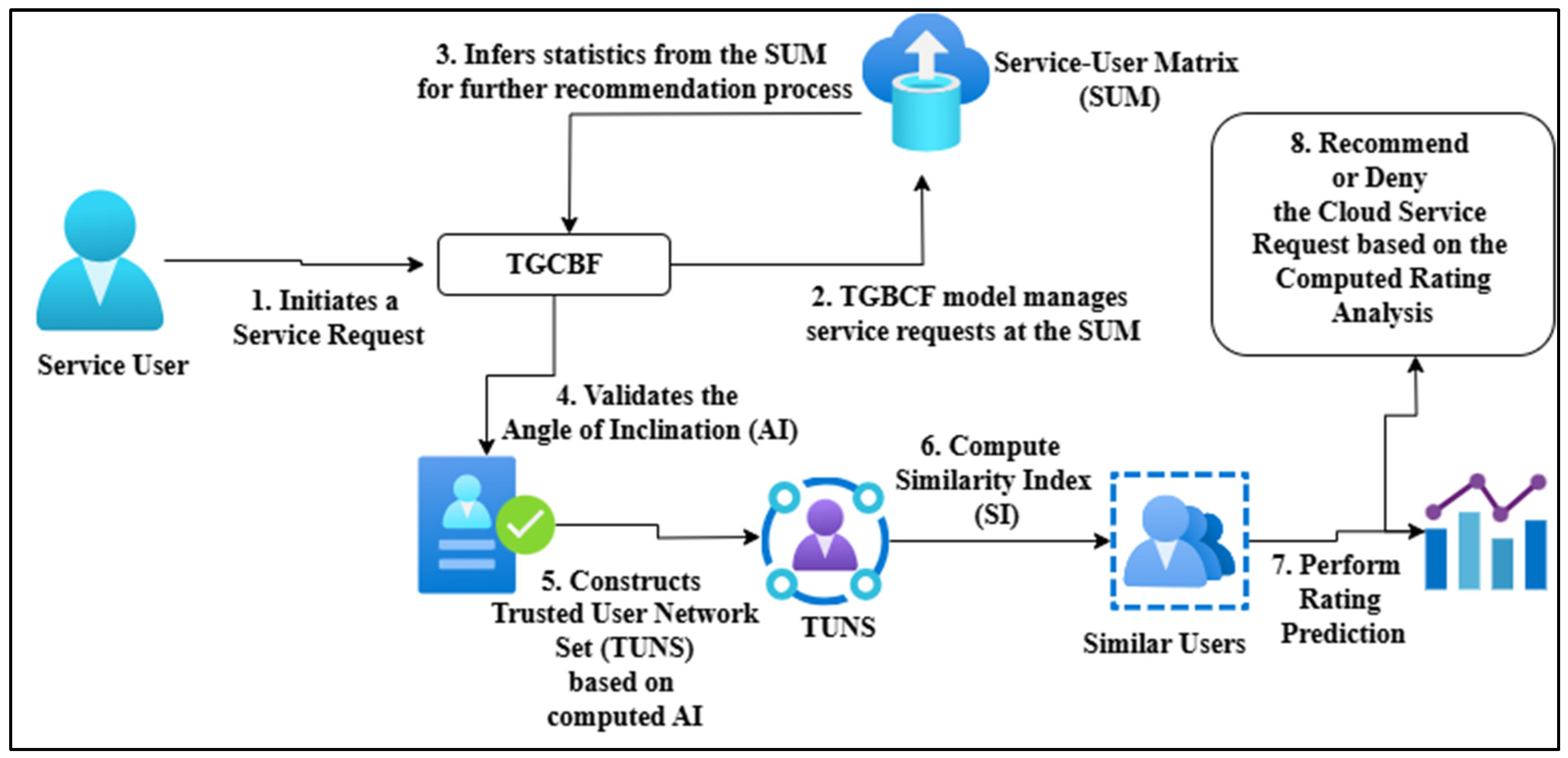
Step-by-Step Working of the TGBCF
- (i)
- User initiates a request for service . However, since only two ratings are available for this service in the user request-service database matrix from users and , only these two service ratings are considered for further computation.
- (ii)
- Evaluate the similarity index by identifying the angle at which user is inclined with other service users. The angle is computed using Equation (6) as follows:
- a.
- //since user is itself computing the distance.
- b.
- c.
- Likewise, all the other angles of inclination of with respect to ,,,, and are computed and the following values are obtained:
- :
- :
- :
- :
- :
5. Simulation Setup
5.1. Setup for Trust Value Computation
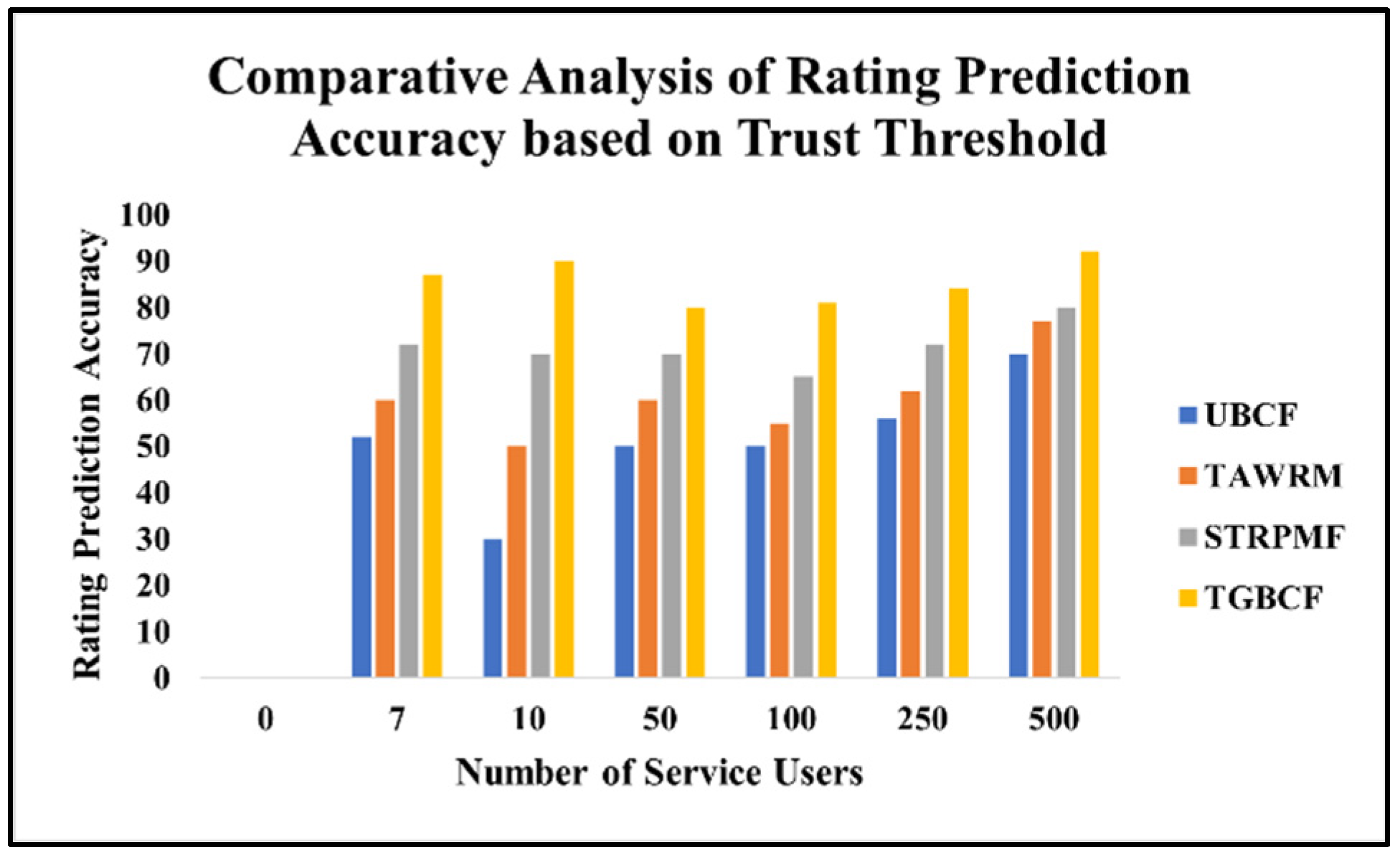
5.2. Setup for Rating Prediction Using Trust
5.3. Comparative Analysis
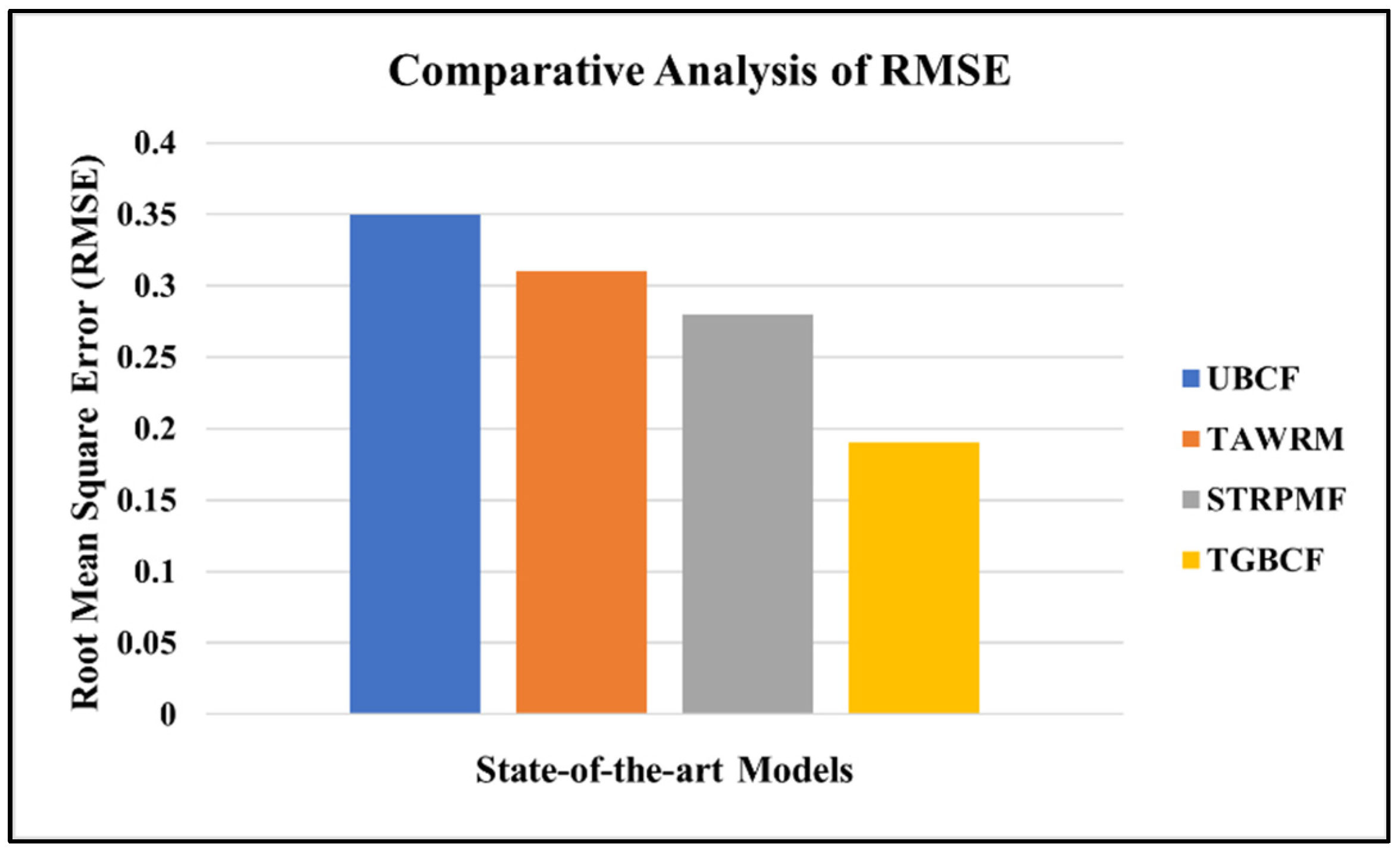
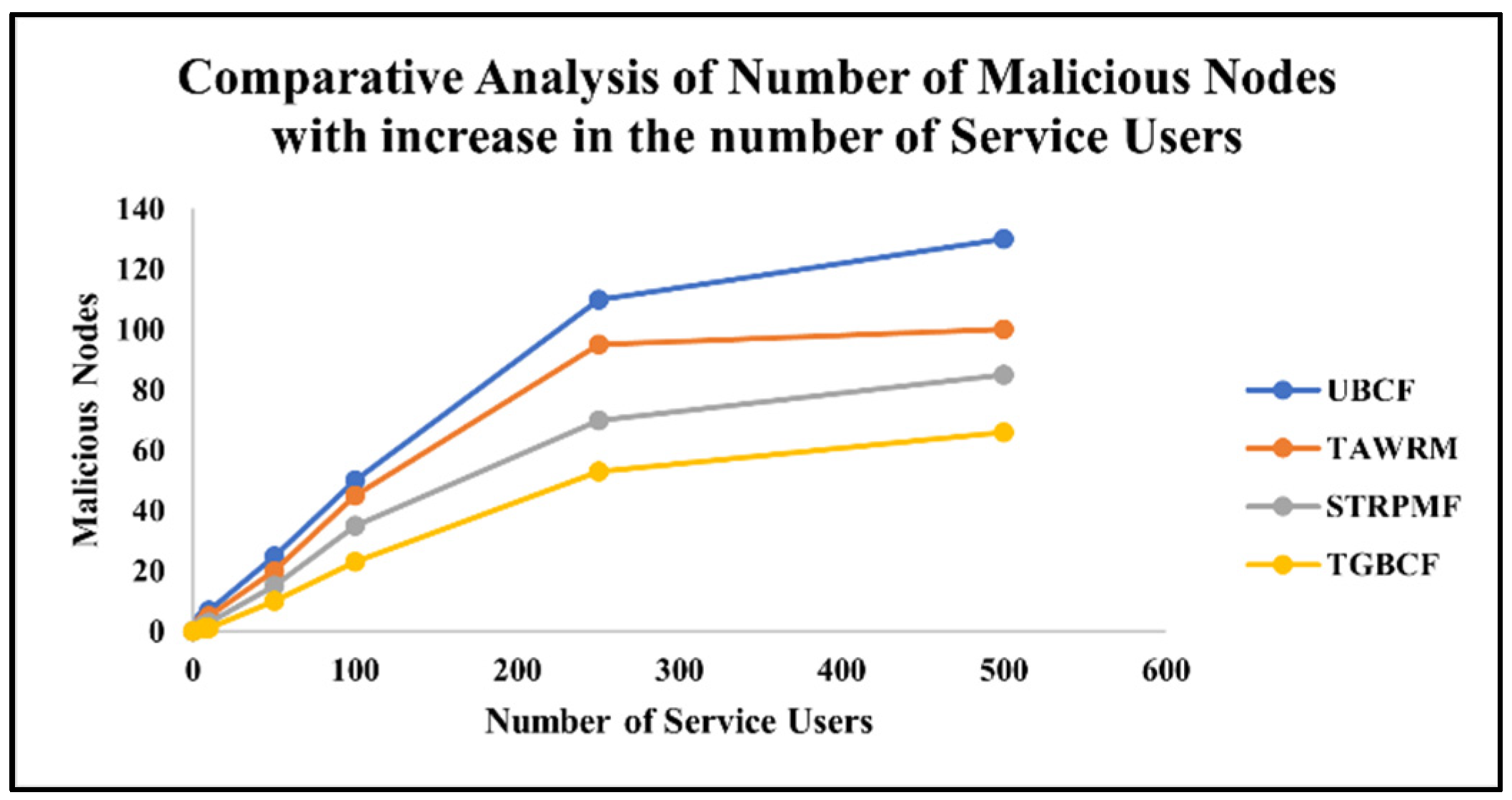
5.4. Evaluation Metrics
5.5. Simulation Results
5.6. Real-World Applicability and Computational Efficiency
- Scalability and Efficiency: The model has been tested on a simulated network of 500 nodes representing service users, providers, and roles. Results show that the trust computation is performed in a time-efficient manner due to the lightweight graph-based structure. This validates that TGBCF can scale to medium-to large-scale cloud environments.
- Trustworthiness Assessment: TGBCF incorporates both direct and indirect trust metrics derived from user interactions and neighborhood feedback, and then computes a weighted trust score. This mirrors real-world scenarios where users interact with multiple services and rely on both personal experience and community insights. The model dynamically adapts to new trust relationships as the system evolves.
- Malicious Node Detection: By setting an unbiased trust threshold (0.6), the system effectively filters out malicious or unreliable nodes, a frequent concern in decentralized cloud ecosystems. This feature makes TGBCF particularly suited for open, multi-tenant cloud platforms where user trust is critical.
- Platform-Agnostic Implementation: The model has been implemented using Python 3.9 with Jupyter Notebook for simulation and Laravel with MySQL for backend deployment. This dual implementation supports its adaptability to both AI-based simulation environments and real-time cloud-based applications, thereby ensuring its cross-platform viability.
- Low Computational Overhead: Trust calculations use simple yet effective operations like feedback weighting, avoiding complex optimization or deep learning routines. This ensures the model can run even on moderate hardware (Intel i5, 8 GB RAM), which is typical in edge or client-side cloud nodes.
- Accuracy and Reliability: The model achieves competitive prediction accuracy using MAE and RMSE when compared with benchmark schemes (e.g., TAWRM, STRPMF, UBCF), reinforcing its practical utility in service rating prediction and user satisfaction enhancement.
6. Formal Analysis
- PROTOCOL Trustworthy Recommendation and malicious_node_identificationInitial conditionSimilarity Index: SI, Trusted User Network Set: TUNSInferred Trust: INT, Overall Aggregate Trust: OAT,SIG SI (user: ui, uj, TUNS, INT)Step 1: If ui, uj TUNSCompute SI, else discard the service request from the user_id//a user not belonging to TUNS is considered malicious.Step 2: Ensure non-negative values for similarity index and Inferred trustTrustNonNegative {all SI: SimilarityIndex | SI.value ≥ 0all INT: InferredTrust | INT.value ≥ 0}Step 3: Compute OAT (ui, uj, weight: w, SI, INT, cloud_service_request, threshold)If (OAT ≤ threshold), the service node isMaliciousassign (isMalicious) = 1, and revoke the cloud service requestelse Predict Rating value for the requested service}Step 4: Predict Service Rating (rating value: OAT, threshold)If (predicted rating for service && OAT threshold), give access to user for the cloud service else deny the service request.
7. Conclusions
8. Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| ACL | Access Control List |
| AI | Angle of Inclination |
| DIT | Direct Trust |
| DoS | Denial-of-Service |
| IDT | Indirect Trust |
| INT | Inferred Trust |
| MAE | Mean Absolute Error |
| NPR | Total Number of Predicted Ratings |
| OAT | Overall Aggregate Trust |
| PR | Predicted Rating |
| RS | Recommender Systems |
| RBAC | Role-based Access Control |
| RMSE | Root Mean Square Error |
| SI | Similarity Index |
| SP | Service Provider |
| SS | Service Set |
| SU | Service User |
| SUM | Service-User Matrix |
| TH | Threshold |
| TMS | Trust Management System |
| TRBAC | Trust-Oriented Role-based Access Control |
| TUNS | Trusted User Network Set |
| US | User Set |
| WT | Weighted Trust |
References
- Park, D.H.; Kim, H.K.; Choi, I.Y.; Kim, J.K. A Literature Review and Classification of Recommender Systems Research. Expert Syst. Appl. 2012, 39, 10059–10072. [Google Scholar] [CrossRef]
- Liu, J.; Dolan, P.; Pedersen, E.R. Personalized News Recommendation Based on Click Behavior. In Proceedings of the 15th International Conference on Intelligent User Interfaces, Hong Kong, China, 7–10 February 2010; pp. 31–40. [Google Scholar]
- Adomavicius, G.; Tuzhilin, A. Toward the Next Generation of Recommender Systems: A Survey of the State-of-the-Art and Possible Extensions. IEEE Trans. Knowl. Data Eng. 2005, 17, 734–749. [Google Scholar] [CrossRef]
- Anthal, J.; Sharma, B.; Manhas, J. Optimization-Enabled Deep Learning for Sentiment Rating Prediction Using Review Data. Serv. Oriented Comput. Appl. 2023, 17, 39–58. [Google Scholar] [CrossRef]
- Li, B.; Ye, C.; Yu, X.; Zhou, H.; Huang, C. QoS Prediction Based on Temporal Information and Request Context. Serv. Oriented Comput. Appl. 2021, 15, 231–244. [Google Scholar] [CrossRef]
- Junejo, A.K.; Jokhio, I.A.; Jan, T. A Multi-Dimensional and Multi-Factor Trust Computation Framework for Cloud Services. Electronics 2022, 11, 1932. [Google Scholar] [CrossRef]
- Lei, C.; Dai, H.; Yu, Z.; Li, R. A Service Recommendation Algorithm with the Transfer Learning-Based Matrix Factorization to Improve Cloud Security. Inf. Sci. 2020, 513, 98–111. [Google Scholar] [CrossRef]
- Mohammadi, V.; Rahmani, A.M.; Darwesh, A.M.; Sahafi, A. Trust-Based Recommendation Systems in Internet of Things: A Systematic Literature Review. Hum.-Cent. Comput. Inf. Sci. 2019, 9, 21. [Google Scholar] [CrossRef]
- Asiri, S.; Miri, A. An IoT Trust and Reputation Model Based on Recommender Systems. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 561–568. [Google Scholar]
- Saxena, U.R.; Alam, T. Role-Based Access Using Partial Homomorphic Encryption for Securing Cloud Data. Int. J. Syst. Assur. Eng. Manag. 2023, 14, 950–966. [Google Scholar] [CrossRef]
- Saxena, U.R.; Alam, T. Role Based Access Control Using Identity and Broadcast-Based Encryption for Securing Cloud Data. J. Comput. Virol. Hack. Tech. 2022, 18, 171–182. [Google Scholar] [CrossRef]
- Saxena, U.R.; Alam, T. Provisioning Trust-Oriented Role-Based Access Control for Maintaining Data Integrity in Cloud. Int. J. Syst. Assur. Eng. Manag. 2023, 14, 2559–2578. [Google Scholar] [CrossRef]
- Saxena, U.R.; Kadel, R. RACHEIM: Reinforced Reliable Computing in Cloud by Ensuring Restricted Access Control. Network 2025, 5, 19. [Google Scholar] [CrossRef]
- Everett, C. Cloud Computing–A Question of Trust. Comput. Fraud Secur. 2009, 2009, 5–7. [Google Scholar] [CrossRef]
- Garrison, G.; Kim, S.; Wakefield, R.L. Success Factors for Deploying Cloud Computing. Commun. ACM 2012, 55, 62–68. [Google Scholar] [CrossRef]
- Ghosh, A.; Arce, I. Guest Editors’ Introduction: In Cloud Computing We Trust—But Should We? IEEE Secur. Priv. 2010, 8, 14–16. [Google Scholar] [CrossRef]
- Habib, S.M.; Hauke, S.; Ries, S.; Mühlhäuser, M. Trust as a Facilitator in Cloud Computing: A Survey. J. Cloud Comput. 2012, 1, 19. [Google Scholar] [CrossRef]
- Khan, K.M.; Malluhi, Q. Establishing Trust in Cloud Computing. IT Prof. 2010, 12, 20–27. [Google Scholar] [CrossRef]
- Al-Na’amneh, Q.; Aljawarneh, M.; Hazaymih, R.; Alzboon, L.; Laila, D.A.; Albawaneh, S. Trust Evaluation Enhancing Security in the Cloud Market Based on Trust Framework Using Metric Parameter Selection. In Utilizing AI in Network and Mobile Security for Threat Detection and Prevention; IGI Global Scientific Publishing: Hershey, PA, USA, 2025; pp. 233–254. [Google Scholar]
- Park, J.S.; Spetka, E.; Rasheed, H.; Ratazzi, P.; Han, K.J. Near-Real-Time Cloud Auditing for Rapid Response. In Proceedings of the 2012 26th International Conference on Advanced Information Networking and Applications Workshops, Fukuoka, Japan, 26–29 March 2012; pp. 1252–1257. [Google Scholar]
- Pearson, S. Toward Accountability in the Cloud. IEEE Internet Comput. 2011, 15, 64–69. [Google Scholar] [CrossRef]
- Takabi, H.; Joshi, J.B.; Ahn, G.J. Security and Privacy Challenges in Cloud Computing Environments. IEEE Secur. Priv. 2010, 8, 24–31. [Google Scholar] [CrossRef]
- Sharma, N.A.; Ali, A.S.; Kabir, M.A. A Review of Sentiment Analysis: Tasks, Applications, and Deep Learning Techniques. Int. J. Data Sci. Anal. 2025, 19, 351–388. [Google Scholar] [CrossRef]
- Jawabreh, E.; Taweel, A. QoS-Based Web Service Selection Using Time-Aware Collaborative Filtering: A Literature Review. Computing 2024, 106, 2033–2058. [Google Scholar] [CrossRef]
- Mostafa, A.M.; Ezz, M.; Elbashir, M.K.; Alruily, M.; Hamouda, E.; Alsarhani, M.; Said, W. Strengthening Cloud Security: An Innovative Multi-Factor Multi-Layer Authentication Framework for Cloud User Authentication. Appl. Sci. 2023, 13, 10871. [Google Scholar] [CrossRef]
- Jin, Y.; Yang, Z.; Liu, J.; Xu, X. Anomaly Detection and Early Warning Mechanism for Intelligent Monitoring Systems in Multi-Cloud Environments Based on LLM. arXiv 2025, arXiv:2506.07407. [Google Scholar]
- Sebestyen, H.; Popescu, D.E.; Zmaranda, R.D. A Literature Review on Security in the Internet of Things: Identifying and Analysing Critical Categories. Computers 2025, 14, 61. [Google Scholar] [CrossRef]
- Kim, Z.; Bauman, K. When Recommendations Know You Too Well: Explanation Types, Privacy Concerns, and Eye-tracking Evidence in Personalized Systems. In Proceedings of the Thirty-First Americas Conference on Information Systems, Montréal, QC, Canada, 14–16 August 2025. [Google Scholar]
- Abawajy, J. Establishing Trust in Hybrid Cloud Computing Environments. In Proceedings of the 2011 IEEE 10th International Conference on Trust, Security and Privacy in Computing and Communications, Changsha, China, 16–18 November 2011; pp. 118–125. [Google Scholar]
- Dimitrakos, T.; Moona, R.; Patel, D.; McKnight, D. Trust Model for Optimized Cloud Services. In Proceedings of the 6th International Conference on Trust Management (TM), Surat, India, 21–25 May 2012; pp. 97–112. [Google Scholar]
- Hwang, K.; Kulkareni, S.; Hu, Y. Cloud Security with Virtualized Defense and Reputation-Based Trust Management. In Proceedings of the 2009 Eighth IEEE International Conference on Dependable, Autonomic and Secure Computing, Chengdu, China, 12–14 December 2009; pp. 717–722. [Google Scholar]
- Zhou, L.; Varadharajan, V.; Hitchens, M. Achieving Secure Role-Based Access Control on Encrypted Data in Cloud Storage. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1947–1960. [Google Scholar] [CrossRef]
- Ghafoorian, M.; Abbasinezhad-Mood, D.; Shakeri, H. A Thorough Trust and Reputation Based RBAC Model for Secure Data Storage in the Cloud. IEEE Trans. Parallel Distrib. Syst. 2018, 30, 778–788. [Google Scholar] [CrossRef]
- Blaze, M.; Feigenbaum, J.; Lacy, J. Decentralized Trust Management. In Proceedings of the 1996 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 6–8 May 1996; pp. 164–173. [Google Scholar]
- Li, N.; Mitchell, J.C.; Winsborough, W.H. Design of a Role-Based Trust-Management Framework. In Proceedings of the 2002 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 12–15 May 2002; pp. 114–130. [Google Scholar]
- Yao, W.T.M. Fidelis: A Policy-Driven Trust Management Framework. In Proceedings of the International Conference on Trust Management, Heraklion, Greece, 28–30 May 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 301–317. [Google Scholar]
- Sandhu, R.; Zhang, X. Peer-to-Peer Access Control Architecture Using Trusted Computing Technology. In Proceedings of the Tenth ACM Symposium on Access Control Models and Technologies, Stockholm, Sweden, 1–3 June 2005; pp. 147–158. [Google Scholar]
- Juels, A.; Kaliski, B.S. PORs: Proofs of Retrievability for Large Files. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 29 October–2 November 2007; pp. 584–597. [Google Scholar]
- Ateniese, G.; Burns, R.; Curtmola, R.; Herring, J.; Kissner, L.; Peterson, Z.; Song, D. Provable Data Possession at Untrusted Stores. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 29 October–2 November 2007; pp. 598–609. [Google Scholar]
- Sandhu, R.; Bhamidipati, V.; Munawer, Q. The ARBAC97 Model for Role-Based Administration of Roles. ACM Trans. Inf. Syst. Secur. 1999, 2, 105–135. [Google Scholar] [CrossRef]
- Sandhu, R.; Munawer, Q. The ARBAC99 Model for Administration of Roles. In Proceedings of the 15th Annual Computer Security Applications Conference (ACSAC’99), Phoenix, AZ, USA, 6–10 December 1999; pp. 229–238. [Google Scholar]
- Oh, S.; Sandhu, R. A Model for Role Administration Using Organization Structure. In Proceedings of the Seventh ACM Symposium on Access Control Models and Technologies, Monterey, CA, USA, 3–4 June 2002; pp. 155–162. [Google Scholar]
- Oh, S.; Sandhu, R.; Zhang, X. An Effective Role Administration Model Using Organization Structure. ACM Trans. Inf. Syst. Secur. 2006, 9, 113–137. [Google Scholar] [CrossRef]
- Crampton, J. Administrative Scope and Role Hierarchy Operations. In Proceedings of the Seventh ACM Symposium on Access Control Models and Technologies, Monterey, CA, USA, 3–4 June 2002; pp. 145–154. [Google Scholar]
- Akl, S.G.; Taylor, P.D. Cryptographic Solution to a Problem of Access Control in a Hierarchy. ACM Trans. Comput. Syst. 1983, 1, 239–248. [Google Scholar] [CrossRef]
- Miklau, G.; Suciu, D. Controlling Access to Published Data Using Cryptography. In Proceedings of the 2003 VLDB Conference, Berlin, Germany, 9–12 September 2003; pp. 898–909. [Google Scholar]
- Tavakolifard, M.; Almeroth, K.C. Social Computing: An Intersection of Recommender Systems, Trust/Reputation Systems, and Social Networks. IEEE Netw. 2012, 26, 53–58. [Google Scholar] [CrossRef]
- Jøsang, A.; Ismail, R.; Boyd, C. A Survey of Trust and Reputation Systems for Online Service Provision. Decis. Support Syst. 2007, 43, 618–644. [Google Scholar] [CrossRef]
- Hassen, H.R.; Bouabdallah, A.; Bettahar, H.; Challal, Y. Key Management for Content Access Control in a Hierarchy. Comput. Netw. 2007, 51, 3197–3219. [Google Scholar] [CrossRef]
- Atallah, M.J.; Blanton, M.; Fazio, N.; Frikken, K.B. Dynamic and Efficient Key Management for Access Hierarchies. ACM Trans. Inf. Syst. Secur. 2009, 12, 18. [Google Scholar] [CrossRef]
- Gentry, C.; Silverberg, A. Hierarchical ID-Based Cryptography. In Advances in Cryptology—ASIACRYPT 2002, Queenstown, New Zealand, 1–5 December 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 548–566. [Google Scholar]
- Boneh, D.; Boyen, X.; Goh, E.J. Hierarchical Identity Based Encryption with Constant Size Ciphertext. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 22–26 May 2005; pp. 440–456. [Google Scholar]
- Sotomayor, B.; Montero, R.S.; Llorente, I.M.; Foster, I. Virtual Infrastructure Management in Private and Hybrid Clouds. IEEE Internet Comput. 2009, 13, 14–22. [Google Scholar] [CrossRef]
- Nurmi, D.; Wolski, R.; Grzegorczyk, C.; Obertelli, G.; Soman, S.; Youseff, L.; Zagorodnov, D. The Eucalyptus Open-Source Cloud-Computing System. In Proceedings of the 2009 9th IEEE/ACM International Symposium on Cluster Computing and the Grid, Shanghai, China, 18–21 May 2009; pp. 124–131. [Google Scholar]
- Hussein, M.K.; Mousa, M.H.; Alqarni, M.A. A Placement Architecture for a Container as a Service (CaaS) in a Cloud Environment. J. Cloud Comput. 2019, 8, 7. [Google Scholar] [CrossRef]
- Rady, M.; Abdelkader, T.; Ismail, R. Integrity and Confidentiality in Cloud Outsourced Data. Ain Shams Eng. J. 2019, 10, 275–285. [Google Scholar] [CrossRef]
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.H.; Konwinski, A.; Zaharia, M. Above the Clouds: A Berkeley View of Cloud Computing; University of California: Berkeley, CA, USA, 2009; unpublished technical report. [Google Scholar]
- Doshi, R.; Kute, V. A Review Paper on Security Concerns in Cloud Computing and Proposed Security Models. In Proceedings of the 2020 International Conference on Emerging Trends in Information Technology and Engineering (ic-ETITE), Vellore, India, 24–25 February 2020; pp. 1–4. [Google Scholar]
- Li, X.; Du, J. Adaptive and Attribute-Based Trust Model for Service-Level Agreement Guarantee in Cloud Computing. IET Inf. Secur. 2013, 7, 39–50. [Google Scholar] [CrossRef]
- Lin, G.; Wang, D.; Bie, Y.; Lei, M. MTBAC: A Mutual Trust Based Access Control Model in Cloud Computing. China Commun. 2014, 11, 154–162. [Google Scholar] [CrossRef]
- Hakim, A.R.; Ramli, K.; Gunawan, T.S.; Windarta, S. A Novel Digital Forensic Framework for Data Breach Investigation. IEEE Access 2023, 11, 42644–42659. [Google Scholar] [CrossRef]
- Uikey, C.; Bhilare, D.S. TrustRBAC: Trust Role Based Access Control Model in Multi-Domain Cloud Environments. In Proceedings of the 2017 International Conference on Information, Communication, Instrumentation and Control (ICICIC), Indore, India, 17–19 August 2017; pp. 1–7. [Google Scholar]
- Zhou, L.; Varadharajan, V.; Hitchens, M. Trust Enhanced Cryptographic Role-Based Access Control for Secure Cloud Data Storage. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2381–2395. [Google Scholar] [CrossRef]
- Zhang, P.; Kong, Y.; Zhou, M. A Domain Partition-Based Trust Model for Unreliable Clouds. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2167–2178. [Google Scholar] [CrossRef]
- Noor, T.H.; Sheng, Q.Z.; Yao, L.; Dustdar, S.; Ngu, A.H. CloudArmor: Supporting Reputation-Based Trust Management for Cloud Services. IEEE Trans. Parallel Distrib. Syst. 2015, 27, 367–380. [Google Scholar] [CrossRef]
- Mahajan, S.; Mahajan, S.; Jadhav, S.; Kolate, S. Trust Management in E-Commerce Websites. Int. Res. J. Eng. Technol. (IRJET) 2017, 4, 2934–2936. [Google Scholar]
- Zarghami, A.; Fazeli, S.; Dokoohaki, N.; Matskin, M. Social Trust-Aware Recommendation System: A t-Index Approach. In Proceedings of the 2009 IEEE/WIC/ACM International Joint Conference on Web Intelligence and Intelligent Agent Technology, Milan, Italy, 15–18 September 2009; Volume 3, pp. 85–90. [Google Scholar]
- Kim, K. A New Similarity Measure to Increase Coverage of Rating Predictions for Collaborative Filtering. Appl. Intell. 2023, 53, 28804–28818. [Google Scholar] [CrossRef]
- Lebib, F.Z.; Djebrit, I.; Mahmoudi, K. Matrix Factorization for Cloud Service Recommendation Based on Social Trust. In Proceedings of the International Conference on Computing Systems and Applications, Algiers, Algeria, 16–18 April 2024; Springer: Cham, Switzerland, 2024; pp. 406–415. [Google Scholar]
- Zhou, L.; Varadharajan, V.; Hitchens, M. Enforcing Role-Based Access Control for Secure Data Storage in the Cloud. Comput. J. 2011, 54, 1675–1687. [Google Scholar] [CrossRef]
- Alshammari, S.T.; Albeshri, A.; Alsubhi, K. Integrating a High-Reliability Multicriteria Trust Evaluation Model with Task Role-Based Access Control for Cloud Services. Symmetry 2021, 13, 492. [Google Scholar] [CrossRef]
- Jøsang, A.; Ismail, R. The Beta Reputation System. In Proceedings of the 15th Bled Electronic Commerce Conference, Bled, Slovenia, 17–19 June 2002; Volume 5, pp. 2502–2511. [Google Scholar]
- Chang, W.; Xu, F.; Dou, J. A Trust and Unauthorized Operation Based RBAC (TUORBAC) Model. In Proceedings of the 2012 International Conference on Control Engineering and Communication Technology, Shenyang, China, 7–9 December 2012; pp. 811–814. [Google Scholar]
- Li, Y.; Liu, J.; Ren, J.; Chang, Y. A Novel Implicit Trust Recommendation Approach for Rating Prediction. IEEE Access 2020, 8, 98305–98315. [Google Scholar] [CrossRef]
- Elmacioglu, E.; Lee, D. On Six Degrees of Separation in DBLP-DB and More. ACM SIGMOD Rec. 2005, 34, 33–40. [Google Scholar] [CrossRef]
- Moradi, P.; Ahmadian, S. A Reliability-Based Recommendation Method to Improve Trust-Aware Recommender Systems. Expert Syst. Appl. 2015, 42, 7386–7398. [Google Scholar] [CrossRef]
- Zhang, P.; Zhou, M.; Kong, Y. A Double-Blind Anonymous Evaluation-Based Trust Model in Cloud Computing Environments. IEEE Trans. Syst. Man Cybern. Syst. 2019, 51, 1805–1816. [Google Scholar] [CrossRef]
- Zhang, F.G. Preventing Recommendation Attack in Trust-Based Recommender Systems. J. Comput. Sci. Technol. 2011, 26, 823–828. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Analysis of Key-Exchange Protocols and Their Use for Building Secure Channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 453–474. [Google Scholar]


| Work | Contribution | Methodology | Identified Gaps |
|---|---|---|---|
| [29,30,31] | Introduced reputation as aggregated feedback for evaluating SPs in cloud environments. | Reputation scores derived from SU feedback and historical interactions. | Lacks dynamic trust updates and handling of feedback manipulation. |
| [32] | Integrated trust thresholds in access control to revoke low-trust entities. | Trust-based revocation list integrated with ACL. | May result in false positives; limited adaptability to dynamic trust. |
| [33] | Suggested TRRBAC model enhancing security compared to RBAC. | Combined trust and reputation feedback; penalty mechanism for negative behavior. | High computational cost; accuracy issues with scaling. |
| [34,35,36,37,38,39] | Explored trust-policy integration for secure cloud environments. | Defined policies integrated with trust values. | Limited by static trust assumptions; challenges with real-time adaptability. |
| [40,41,42,43] | Reviewed RS types used in trust construction (CBF, CF, Hybrid, etc.). | Survey of recommendation techniques across domains. | Cold-start and data sparsity remain unresolved. |
| [44,45,46] | Analyzed sparsity and cold-start in recommendation systems. | Identified key performance challenges. | No robust solution for dynamic user behavior or attack resistance. |
| [47] | Used stored ratings to compute trust values. | Cumulative trust modeling. | Subjective trust evaluation; lacks context sensitivity. |
| [49,50,51,52] | Addressed reliability issues in feedback-based ratings. | Analyzed effects of biased/inaccurate ratings. | Vulnerable to fabricated feedback and manipulation. |
| [53,54,55,56,57,58] | Surveyed trust models for secure cloud access. | Comparative study of multiple trust frameworks. | Lacks adaptive revocation/reassignment mechanisms. |
| [59] | Developed “Cloud-Trust” for adaptive SP selection. | Dynamic trust assessment based on service behavior. | Scalability and malicious behavior detection limited. |
| [60] | Introduced MTBAC considering mutual trust of users and nodes. | Mutual behavioral trust model. | Struggles with scalability and sophisticated attack types. |
| [61,62,63] | Incorporated trust into RBAC for refined access control. | Probabilistic trust scoring in RBAC structures. | Vulnerable to collusion, Sybil, and on/off attacks. |
| [64] | Improved malicious node detection and reduced trust computation cost. | Optimized trust algorithm for performance. | May trade off security accuracy for performance. |
| [65,66] | Discussed Sybil and collusion attacks in cloud platforms. | Attack modeling based on real-world platforms. | Absence of dynamic countermeasures. |
| [67] | Proposed Social Trust-Aware RS using t-index. | Contextual and social behavior modeling. | Ignores evolving trust and access control sensitivity. |
| [68] | Improved UBCF similarity with user contribution levels. | Contribution-based similarity in CF. | Static computation; lacks adaptability to behavior changes. |
| [69] | Trust-aware matrix factorization using social signals. | Matrix factorization incorporating social trust. | Assumes static trust; does not address access control. |
| [70] | Mapped trust to roles in RBAC for cloud data access. | Dynamic trust mapping in RBAC. | Limited flexibility in evolving behavior contexts. |
| [71] | High-reliability multicriteria trust with task-based RBAC. | Balanced trust evaluation (feedback, context, history). | Complexity in multidimensional trust balancing. |
| [72,73] | Identified role of trust-based RS in anomaly and attack detection. | Integration of RS with security analytics. | Need for unified, real-time trust model for detection and prevention. |
| Service User Matrix | ||||||
|---|---|---|---|---|---|---|
| 0.52 | 0.75 | ?? | ||||
| 0.76 | 0.63 | |||||
| 0.69 | ||||||
| 0.73 | 0.72 | 0.79 | ||||
| 0.61 | 0.77 | |||||
| 0.69 | 0.75 | |||||
| 0.53 |
| Users | Angle of Inclination of Other Users with | Distance (D) | Inferred Trust |
|---|---|---|---|
| 0 | 1 | ||
| 1 | 1 | ||
| 2 | 0.5 | ||
| 3 | 0.33 | ||
| 4 | 0.25 |
| Service User Matrix | ||||||
|---|---|---|---|---|---|---|
| 0.52 | 0.75 | 0.60 | ||||
| 0.76 | 0.63 | |||||
| 0.69 | ||||||
| 0.73 | 0.72 | 0.79 | ||||
| 0.61 | 0.77 | |||||
| 0.69 | 0.75 | |||||
| 0.53 |
| Feature | TGBCF (Proposed) | TAWRM | UBCF | STRPMF |
|---|---|---|---|---|
| Trust Modeling | Explicit trust computation using role-based user grouping and rating patterns | Direct and indirect trust via trust paths and networks | No trust modeling; purely rating-based | Implicit trust integrated through social regularization |
| User Similarity | Group-based collaborative filtering with role context | Based on trust network structure | Similarity based on co-rated items | Latent user similarity via PMF with social links |
| Role Awareness | Yes, roles are weighted and influence predictions | No explicit role differentiation | No consideration of user roles | Roles not modeled; only social links considered |
| Rating Prediction Technique | Graph-based Collaborative Filtering + Trust Deviation Weighting | Matrix decomposition on trust-ranked items | Weighted average of Top-N similar users | PMF with trust regularization |
| Handling of Sparsity | Reduces sparsity via grouping and inferred trust | May fail on sparse trust paths | High sensitivity to sparsity | Mitigated through latent factor modeling |
| Access Control Integration | Integrated trust threshold for access decisions | Not supported | Not supported | Not supported |
| Main Limitations | Requires accurate role definition and dynamic threshold tuning | Confined to narrow trust trajectories | Ignores trust and role context | Subjective nature of social trust; lacks fine-grained control |
| Strength | Context-aware, trust-sensitive, and role-integrated prediction | Exploits networked trust structures | Simple and easy to implement | Learns user/item factors with trust influence |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saxena, U.R.; Khatri, Y.; Kadel, R.; Shailendra, S. A Service Recommendation Model in Cloud Environment Based on Trusted Graph-Based Collaborative Filtering Recommender System. Network 2025, 5, 30. https://doi.org/10.3390/network5030030
Saxena UR, Khatri Y, Kadel R, Shailendra S. A Service Recommendation Model in Cloud Environment Based on Trusted Graph-Based Collaborative Filtering Recommender System. Network. 2025; 5(3):30. https://doi.org/10.3390/network5030030
Chicago/Turabian StyleSaxena, Urvashi Rahul, Yogita Khatri, Rajan Kadel, and Samar Shailendra. 2025. "A Service Recommendation Model in Cloud Environment Based on Trusted Graph-Based Collaborative Filtering Recommender System" Network 5, no. 3: 30. https://doi.org/10.3390/network5030030
APA StyleSaxena, U. R., Khatri, Y., Kadel, R., & Shailendra, S. (2025). A Service Recommendation Model in Cloud Environment Based on Trusted Graph-Based Collaborative Filtering Recommender System. Network, 5(3), 30. https://doi.org/10.3390/network5030030









