Encrypted Client Hello Is Coming: A View from Passive Measurements
Abstract
1. Introduction
2. Background and Related Work
3. Dataset and Methodology
- Outgoing DNS: We record all DNS transactions initiated by the campus resolver to answer queries by internal clients. To this end, Tstat has been configured to produce a “DNS log” which records all the DNS transactions observed in the traffic. Indeed, all internal clients are configured to use the internal DNS resolver, which answers the client’s recursive queries by contacting the required authoritative DNS servers. Our setup allows us to observe DNS traffic between the internal resolver and the internet, but we cannot record the individual DNS requests/responses issued by clients. Thus, we can collect the whole set of domains accessed by internal clients, but we cannot link them to the corresponding user. Moreover, some requests might be handled by the DNS server thanks to the cache, without the need for issuing any query to the external authoritative name server. For DNS transactions, Tstat exports the endpoint IP addresses and port numbers as well as the queries and resource records carried within packets. For each one, Tstat reports the domain name, DNS record type (A, AAAA, HTTPS, etc.), and the content of the record. Specifically, in the case of HTTPS records, it records the contained information if present—i.e., ECH keys, the Application-Level Protocol Negotiation (ALPN) preferences, and the possible IPs in both 6 and 4 versions. We use this dataset to study the prevalence of HTTPS DNS queries in client traffic and the extent to which they are successfully resolved. Over the month of February, we collected 879 million DNS queries, resulting in 615 million responses to 105,000 unique domains. We refer to this dataset as DNS-Outgoing.
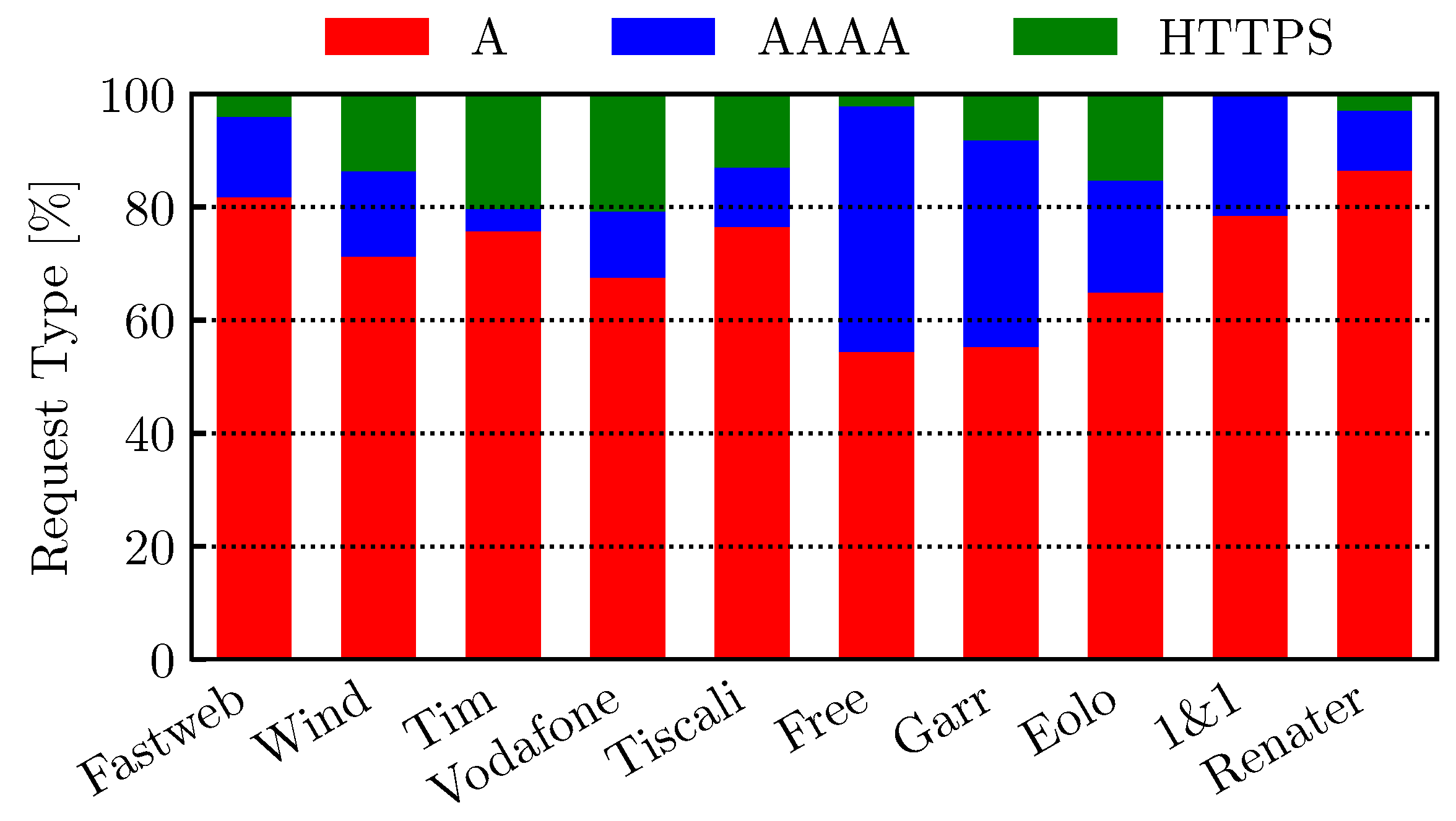
- Incoming DNS: We collect all the DNS transactions initiated by any external node and directed to the internal DNS resolver for the campus. This traffic includes (almost) unique requests issued by ISP/corporate/open resolvers operating on behalf of worldwide users accessing the domains belonging to the campus’s two DNS zones, i.e., the campus websites. We record the same kind of data as for DNS-Outgoing, but we never observe any answer to DNS HTTPS queries, as the internal resolver does not hold any resource record of this type. Over the month of February 2025, we collected 220 million DNS queries and 64 million responses. We use this dataset to study the volume of HTTPS DNS traffic that an authoritative DNS resolver must expect as of 2025 and its adoption across different Internet service providers (ISPs). We refer to this dataset as DNS-Incoming.
- QUIC traffic: We also collect logs related to all QUIC connections by internal clients to external web servers. Indeed, Tstat identifies QUIC traffic thanks to Deep Packet Inspection, matching the QUIC headers contained in the first packets of each UDP flow. For each UDP flow identified as a QUIC connection, it records several metrics, such as size and timing of the first packets and the type of QUIC frames they carry. Moreover, in the case of “Initial” QUIC frames, Tstat decrypts the packet payload using the encryption keys mechanically derived from the packet headers. Thus, it obtains and records various fields of the contained TLS Client Hello message, such as the Server Name Indication (that is, the server’s domain name) and the presence (and size) of an Encrypted Client Hello, which, obviously, we cannot decrypt. Notice that, when a client does not possess a valid ECH configuration, it generates a GREASE ECH extension—a randomized but syntactically correct placeholder—to maintain protocol consistency [20]. These GREASE values do not represent actual Encrypted Client Hello messages but serve to ensure that middleboxes and servers properly ignore unknown extensions. Over February 2025, we collected 106 million QUIC connections to 95,500 unique domain names. We refer to this dataset as QUIC-Outgoing.
Ethical Considerations
4. Results
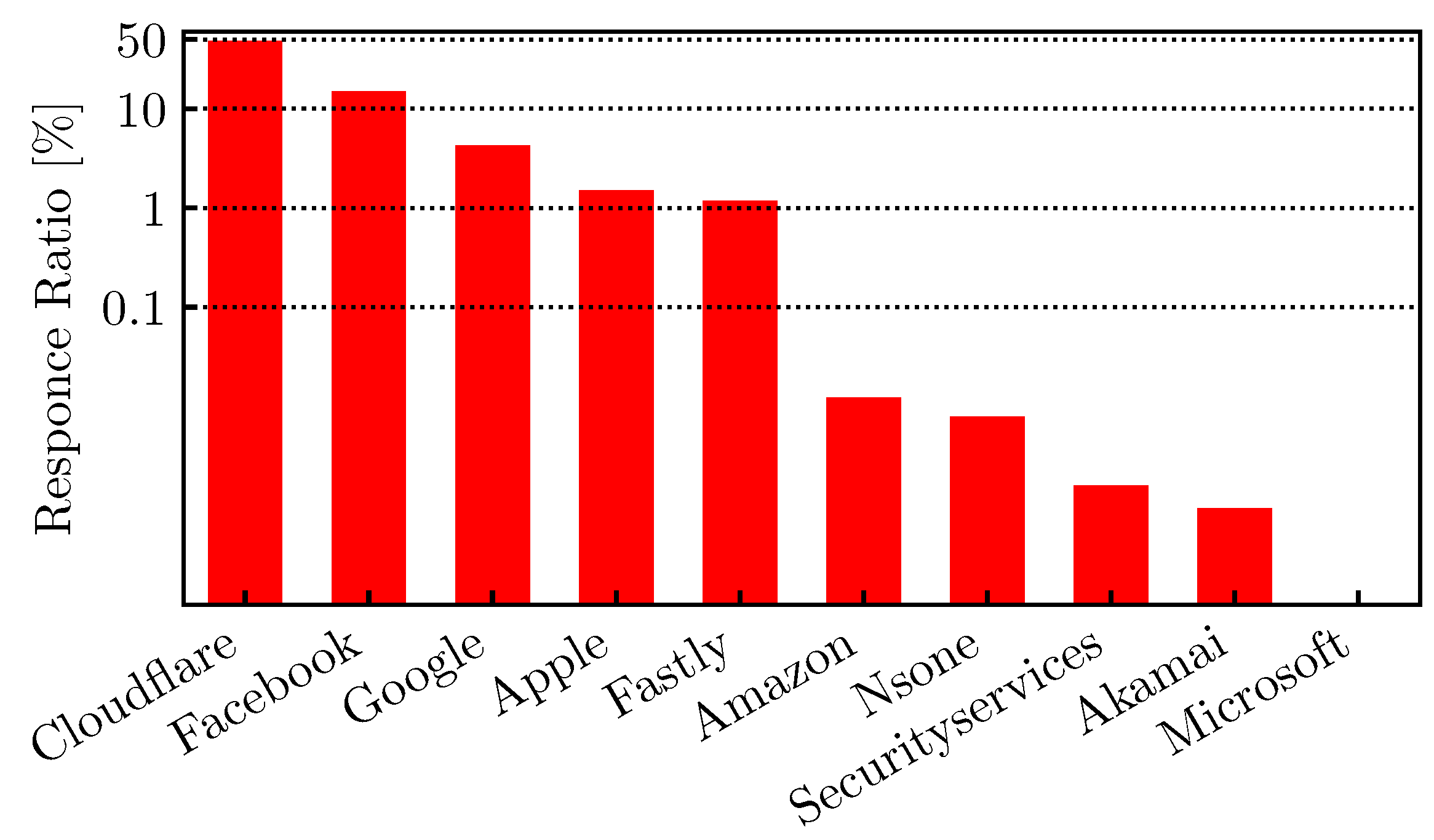
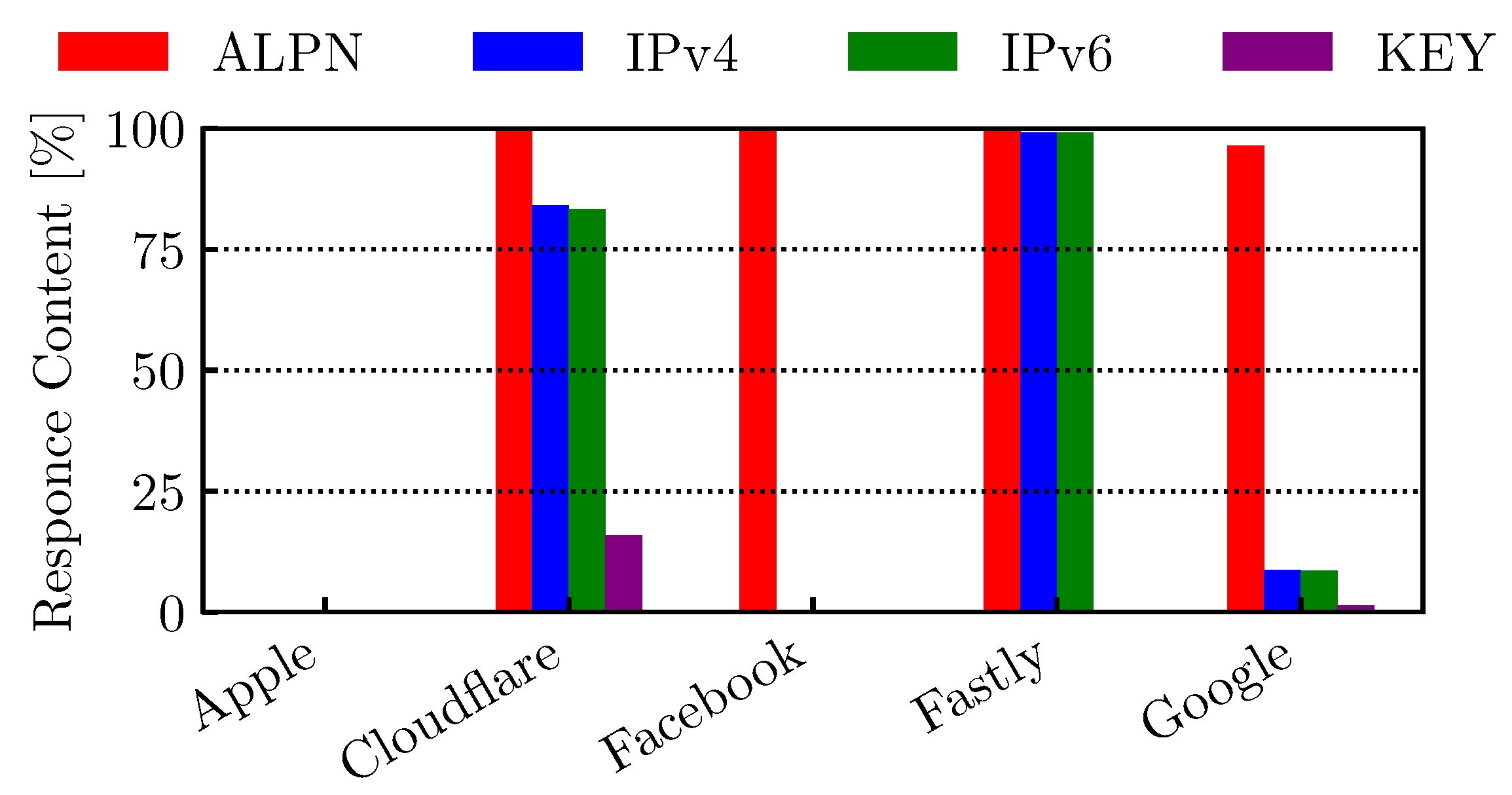
4.1. HTTPS DNS Traffic
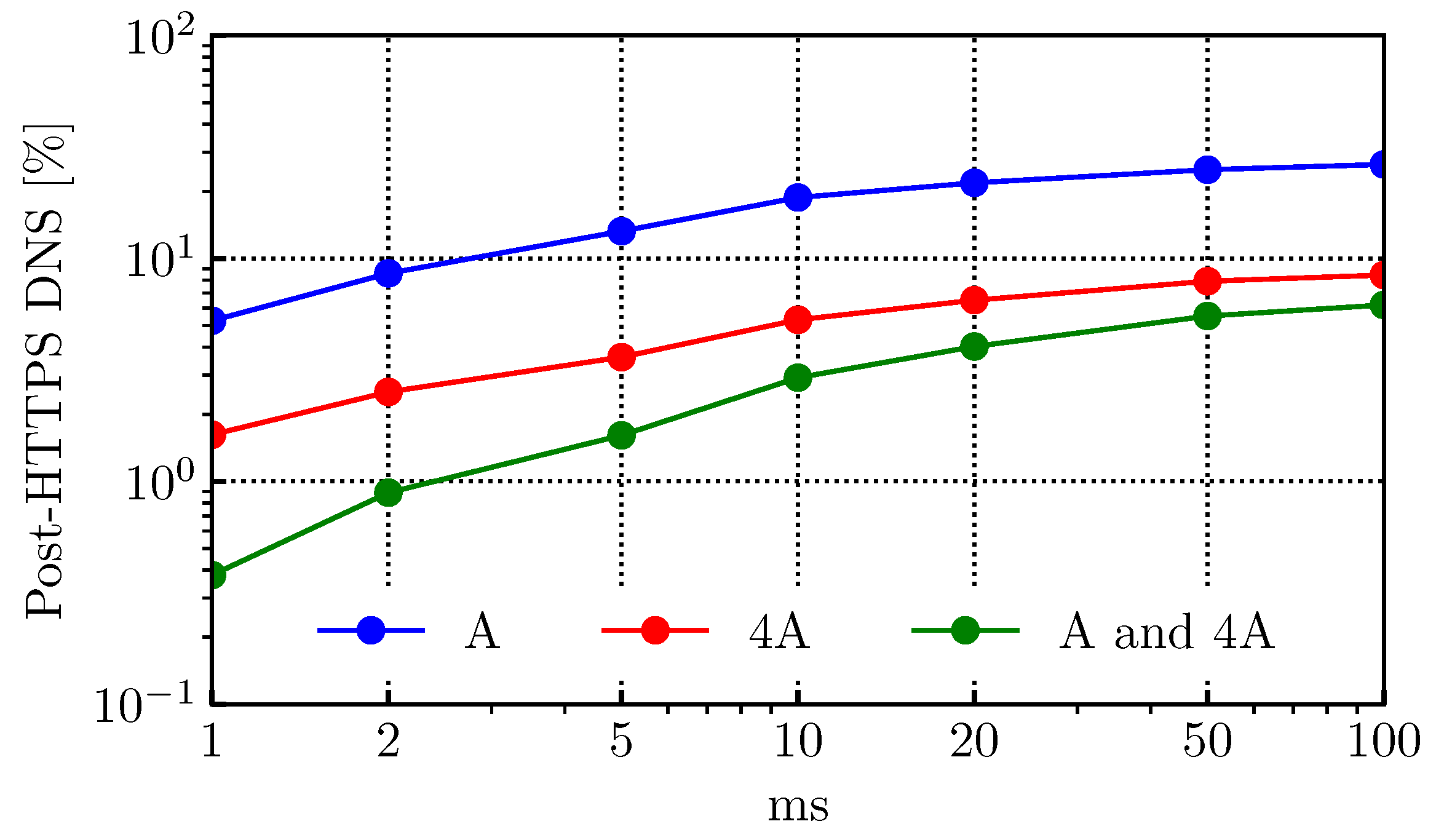
4.2. HTTPS DNS and Query Volume
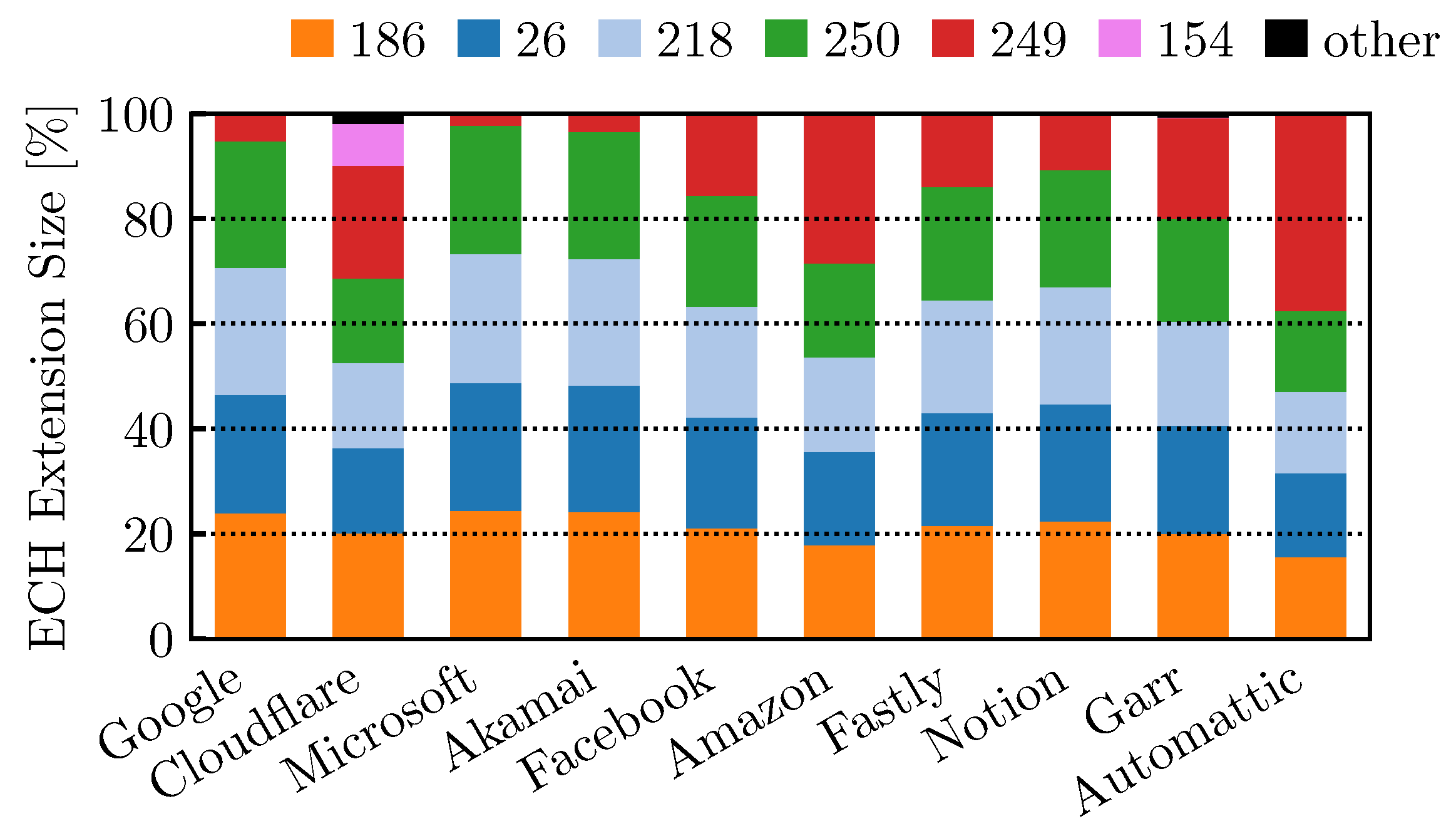
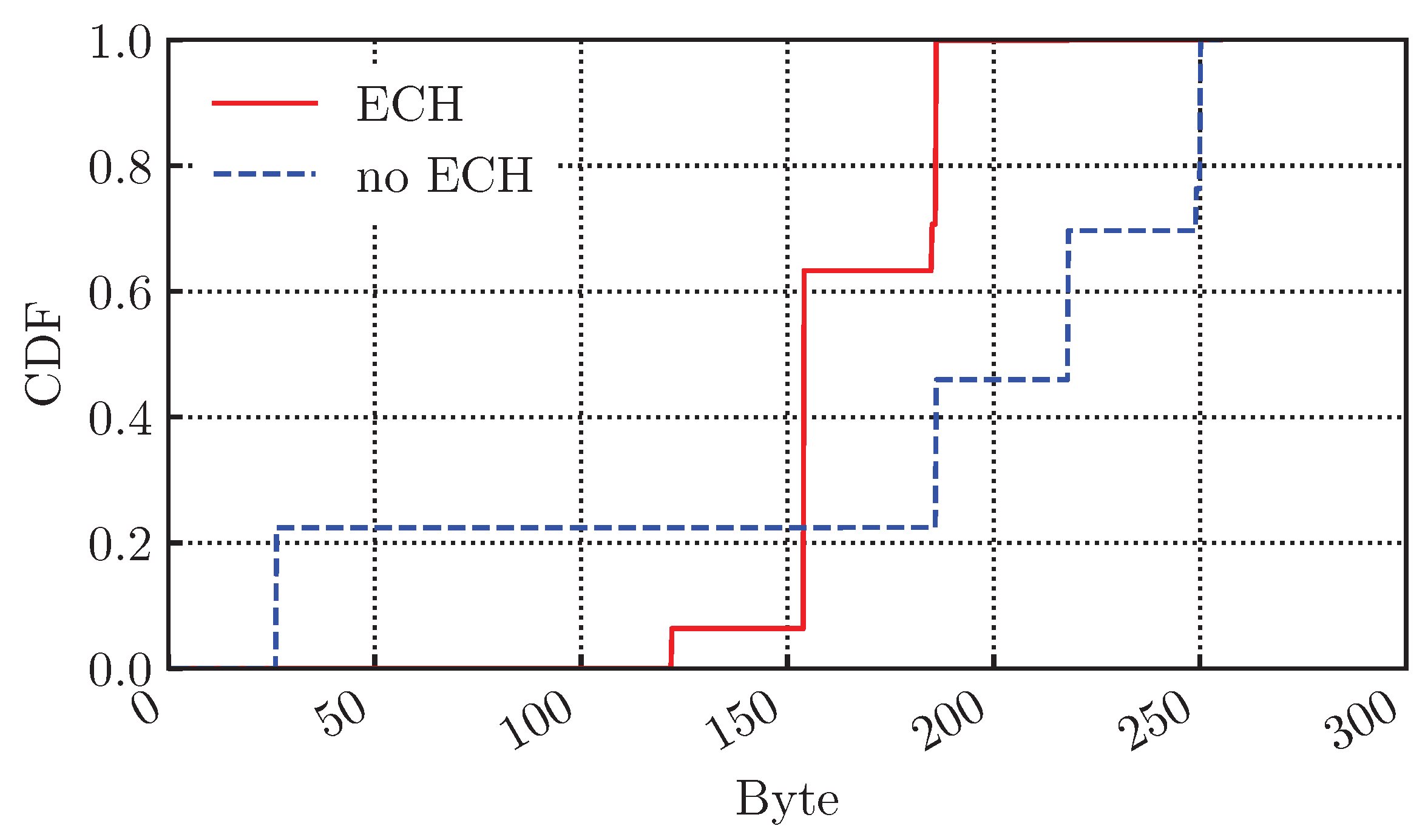
4.3. Encrypted Client Hello in QUIC Flows
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Farrell, S.; Tschofenig, H. Pervasive Monitoring Is an Attack. RFC 7258. 2014. Available online: https://www.rfc-editor.org/rfc/rfc7258.html (accessed on 4 August 2025).
- Naylor, D.; Finamore, A.; Leontiadis, I.; Grunenberger, Y.; Mellia, M.; Munafò, M.; Papagiannaki, K.; Steenkiste, P. The cost of the“ s” in https. In Proceedings of the 10th ACM International on Conference on emerging Networking Experiments and Technologies, Sydney, Australia, 2–5 December 2014; pp. 133–140. [Google Scholar]
- Iyengar, J.; Thomson, M. QUIC: A UDP-Based Multiplexed and Secure Transport. RFC 9000. 2021. Available online: https://www.rfc-editor.org/info/rfc9000 (accessed on 4 August 2025).
- Hu, Z.; Zhu, L.; Heidemann, J.; Mankin, A.; Wessels, D.; Hoffman, P.E. Specification for DNS over Transport Layer Security (TLS). RFC 7858. 2016. Available online: https://www.rfc-editor.org/info/rfc7858 (accessed on 4 August 2025).
- Hoffman, P.E.; McManus, P. DNS Queries over HTTPS (DoH). RFC 8484. 2018. Available online: https://www.rfc-editor.org/info/rfc8484 (accessed on 4 August 2025).
- Casanova, L.F.G.; Lin, P.C. Generalized classification of DNS over HTTPS traffic with deep learning. In Proceedings of the 2021 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference (APSIPA ASC), Tokyo, Japan, 14–17 December 2021; pp. 1903–1907. [Google Scholar]
- Vekshin, D.; Hynek, K.; Cejka, T. Doh insight: Detecting dns over https by machine learning. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Virtual, 25–28 August 2020; pp. 1–8. [Google Scholar]
- Rescorla, E.; Oku, K.; Sullivan, N.; Wood, C.A. TLS Encrypted Client Hello. Internet-Draft draft-ietf-tls-esni-24, Internet Engineering Task Force. Work in Progress. 2025. Available online: https://datatracker.ietf.org/doc/draft-ietf-tls-esni/24/ (accessed on 4 August 2025).
- Schwartz, B.M.; Bishop, M.; Nygren, E. Service Binding and Parameter Specification via the DNS (SVCB and HTTPS Resource Records). RFC 9460. 2023. Available online: https://www.rfc-editor.org/info/rfc9460 (accessed on 4 August 2025).
- Trevisan, M.; Soro, F.; Mellia, M.; Drago, I.; Morla, R. Does domain name encryption increase users’ privacy? ACM SIGCOMM Comput. Commun. Rev. 2020, 50, 16–22. [Google Scholar] [CrossRef]
- Trevisan, M.; Soro, F.; Mellia, M.; Drago, I.; Morla, R. Attacking DoH and ECH: Does Server Name Encryption Protect Users’ Privacy? ACM Trans. Internet Technol. 2023, 23, 19. [Google Scholar] [CrossRef]
- Shamsimukhametov, D.; Kurapov, A.; Liubogoshchev, M.; Khorov, E. Is encrypted clienthello a challenge for traffic classification? IEEE Access 2022, 10, 77883–77897. [Google Scholar] [CrossRef]
- Bhargavan, K.; Cheval, V.; Wood, C. A symbolic analysis of privacy for tls 1.3 with encrypted client hello. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 365–379. [Google Scholar]
- Niere, N.; Lange, F.; Heitmann, N.; Somorovsky, J. Encrypted Client Hello (ECH) in Censorship Circumvention. Free. Open Commun. Internet 2025, 2, 64–73. [Google Scholar]
- Tsiatsikas, Z.; Karopoulos, G.; Kambourakis, G. Measuring the adoption of TLS encrypted client hello extension and its forebear in the wild. In European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2022; pp. 177–190. [Google Scholar]
- Zirngibl, J.; Sattler, P.; Carle, G. A first look at SVCB and HTTPS DNS resource records in the wild. In Proceedings of the 2023 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Delft, The Netherlands, 3–7 July 2023; pp. 470–474. [Google Scholar]
- Dong, H.; Zhang, Y.; Lee, H.; Huque, S.; Sun, Y. Exploring the Ecosystem of DNS HTTPS Resource Records: An End-to-End Perspective. In Proceedings of the 2024 ACM on Internet Measurement Conference, Madrid, Spain, 4–6 November 2024; pp. 423–440. [Google Scholar]
- Trevisan, M.; Finamore, A.; Mellia, M.; Munafo, M.; Rossi, D. Traffic analysis with off-the-shelf hardware: Challenges and lessons learned. IEEE Commun. Mag. 2017, 55, 163–169. [Google Scholar] [CrossRef]
- Trevisan, M. Dpmon: A Differentially-Private Query Engine for Passive Measurements. Preprint. Available online: https://ssrn.com/abstract=4901748 (accessed on 4 August 2025).
- Benjamin, D. Applying Generate Random Extensions And Sustain Extensibility (GREASE) to TLS Extensibility. RFC 8701. 2020. Available online: https://www.rfc-editor.org/info/rfc8701 (accessed on 4 August 2025).
- Fan, J.; Xu, J.; Ammar, M.H. Crypto-pan: Cryptography-based prefix-preserving anonymization. Comput. Netw. 2004, 46, 253–272. [Google Scholar] [CrossRef]

| DNS-Outgoing | DNS-Incoming | |||
|---|---|---|---|---|
| Query | Response | Query | Response | |
| A | 38.67% | 48.28% | 53.34% | 64.04% |
| AAAA | 19.18% | 5.69% | 17.68% | 0.1% |
| HTTPS | 7.89% | 0.89% | 5.48% | 0% |
| NS | 29.7% | 2.76% | 3.03% | 0.7% |
| Other | 4.56% | 42.38% | 20.47% | 35.16% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Merlach, G.; Trevisan, M.; Giordano, D. Encrypted Client Hello Is Coming: A View from Passive Measurements. Network 2025, 5, 29. https://doi.org/10.3390/network5030029
Merlach G, Trevisan M, Giordano D. Encrypted Client Hello Is Coming: A View from Passive Measurements. Network. 2025; 5(3):29. https://doi.org/10.3390/network5030029
Chicago/Turabian StyleMerlach, Gabriele, Martino Trevisan, and Danilo Giordano. 2025. "Encrypted Client Hello Is Coming: A View from Passive Measurements" Network 5, no. 3: 29. https://doi.org/10.3390/network5030029
APA StyleMerlach, G., Trevisan, M., & Giordano, D. (2025). Encrypted Client Hello Is Coming: A View from Passive Measurements. Network, 5(3), 29. https://doi.org/10.3390/network5030029







