Large Geographical Area Aerial Surveillance Systems Data Network Infrastructure Managed by Artificial Intelligence and Certified over Blockchain: A Review
Abstract
:1. Introduction
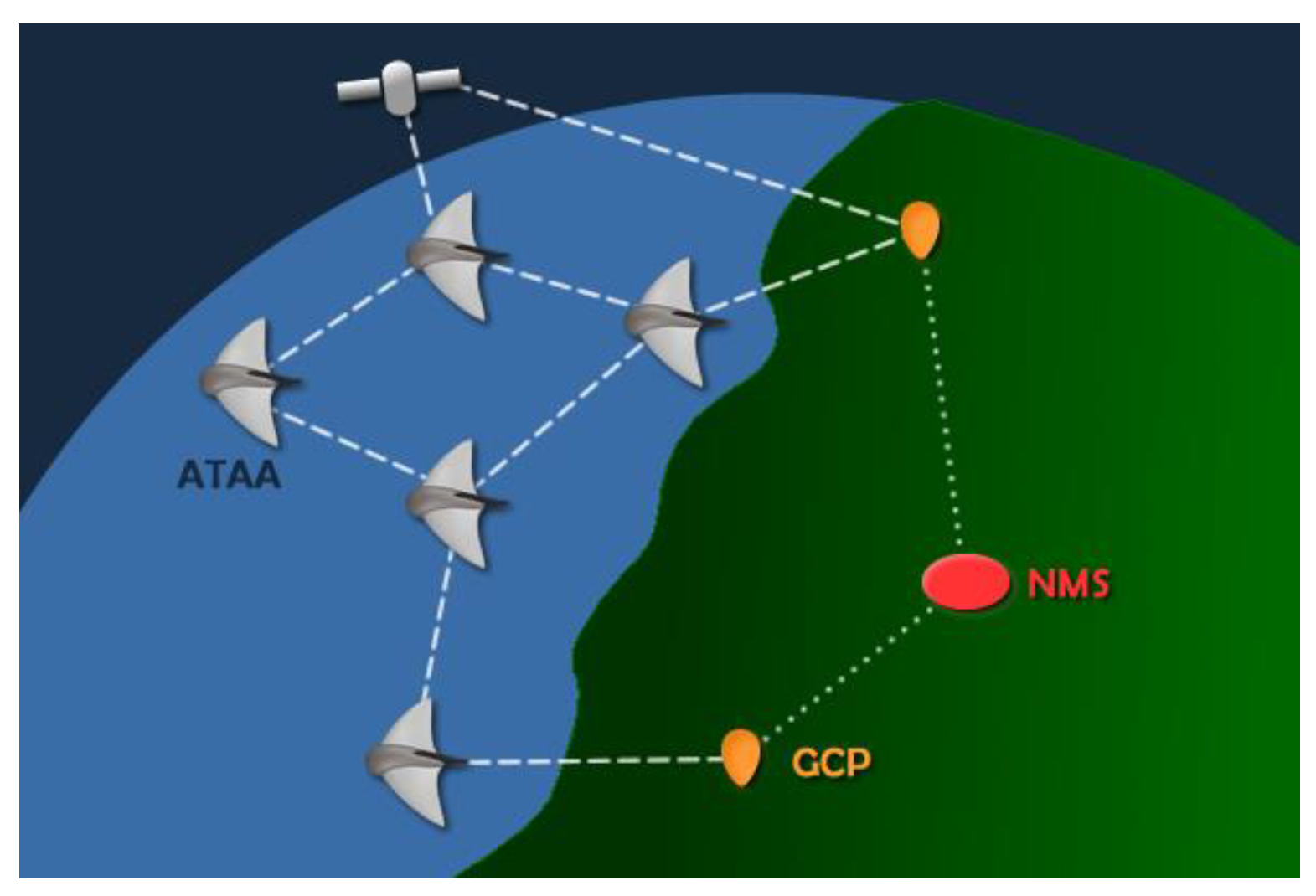
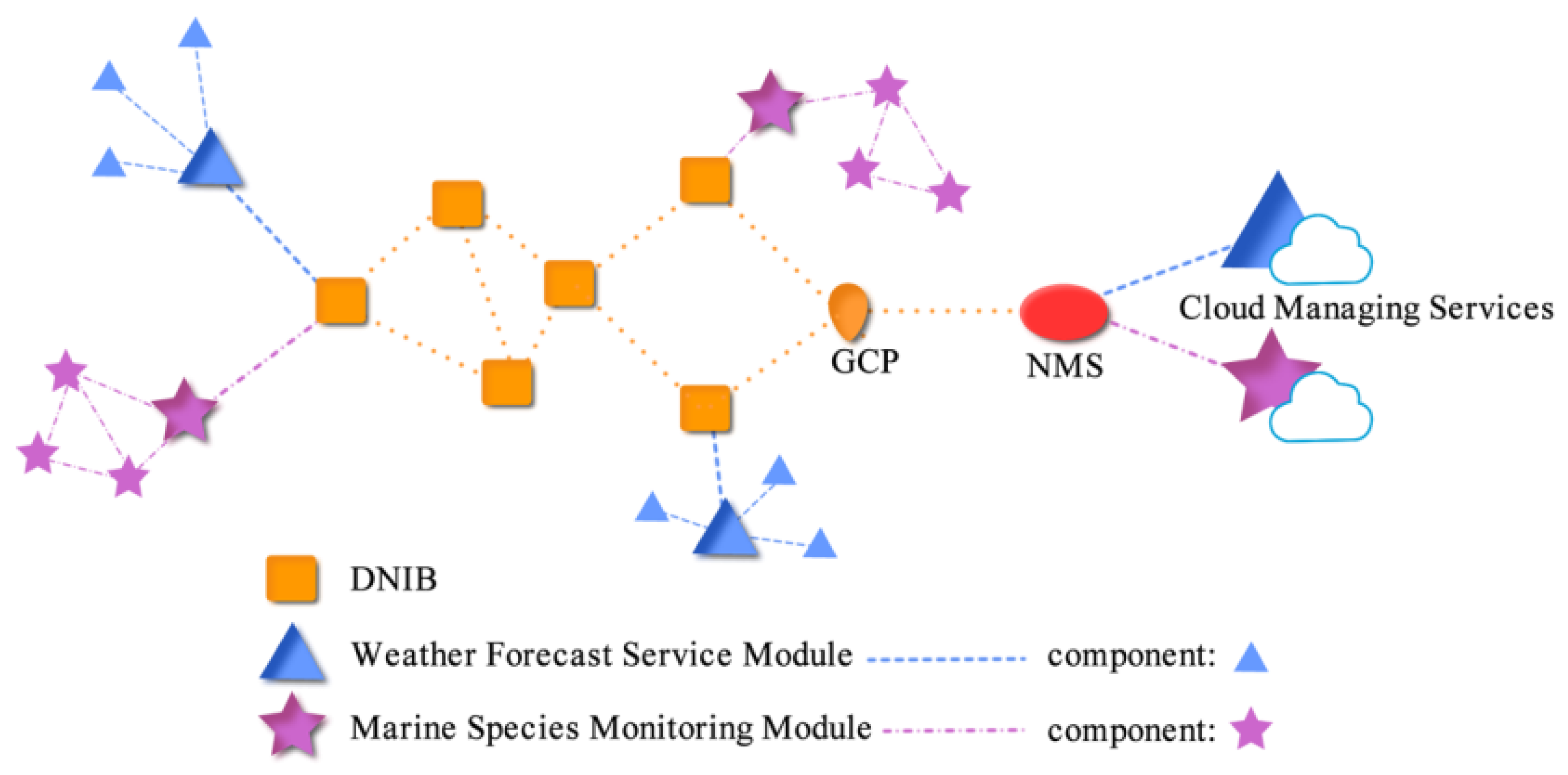
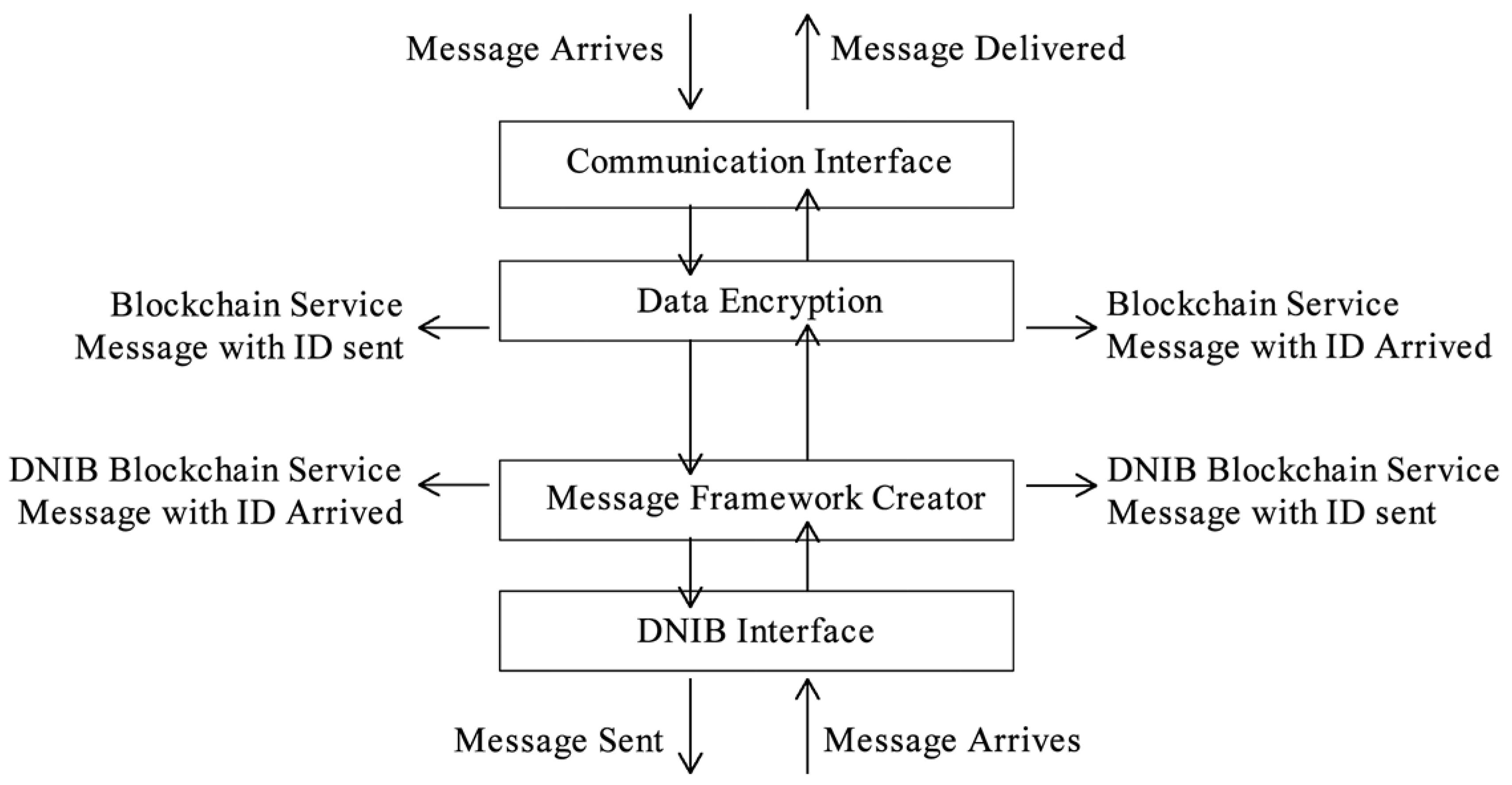
2. Data Network Infrastructure for HSS
- Service type agnostic;
- Hardware and software agnostic;
- Support for several HSS at the same time;
- Security and independence of HSS services;
- Separate operability from maintenance/operation and HSS services;
- Automation of maintenance and operation tasks;
- Simplicity of components and services implementation, maintenance, and substitution;
- Separation of concerns on services and components;
- Visibility and transparency over maintenance/operation to assure the HSS services security.
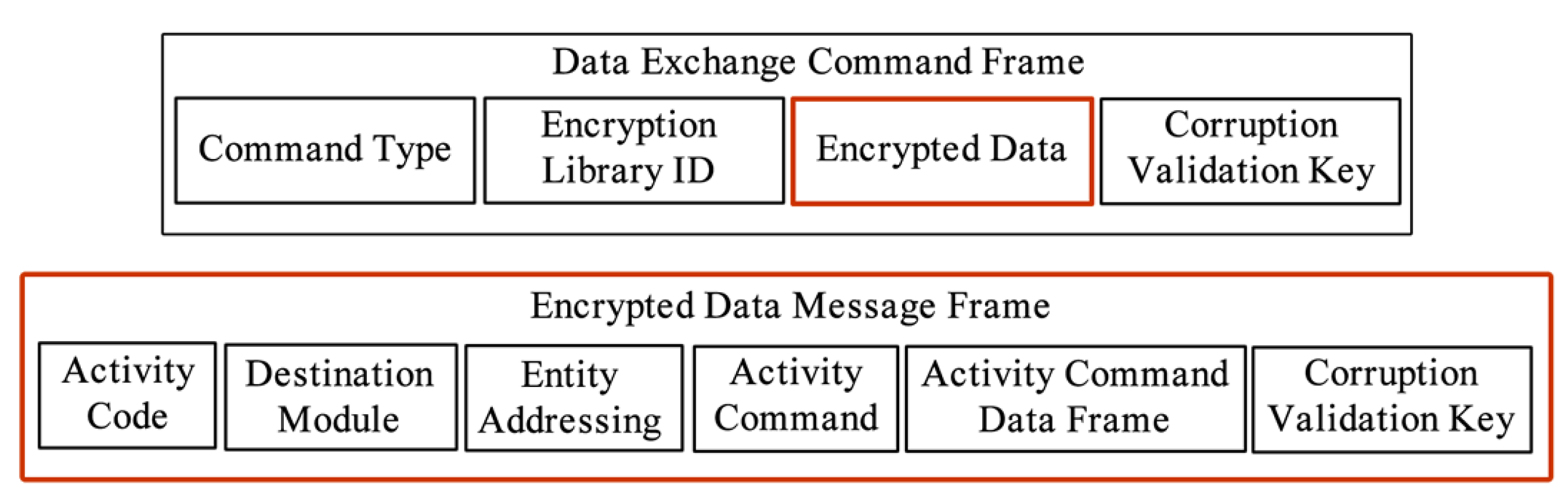
DNIHSS Communication Components
- Independence of software solution implementation: the blocks can be implemented with different technology and software solutions;
- Increased security of the architecture by simplification of concerns: the reduction of responsibilities of each block confines the impact of the action of hackers in case of a compromised module. Usages of different technology solutions in the individual blocks increase the difficulty of hacking activity;
- Responsibility division: the assignment of well-defined responsibilities to the blocks allows a simplified substitution of them by other ones with different technology and implementation solutions. The well-defined responsibility facilitates the security and activity supervision, detecting malicious activity faster;
- Redundancy existence: the blocks can be implemented alongside other blocks with the same responsibilities to add in redundancy and performance.
3. Edge Artificial Intelligence
- TensorFlow [51,52,53,54,55,56,57,58] is an open-source tool developed by Google’s AI department that is perfectly suited for complex numerical computations of high volumes and used in a vast number of fields. It has been used by several tech giants such as Google, SAP, Intel, NVIDIA, AMD, and others. It uses the programing languages C++ and Python;
- Microsoft Cognitive Toolkit [59] is an open-source tool suitable for a variety of AI applications. It allows the distributed training and supports C++, C#, Java, and Python programming languages;
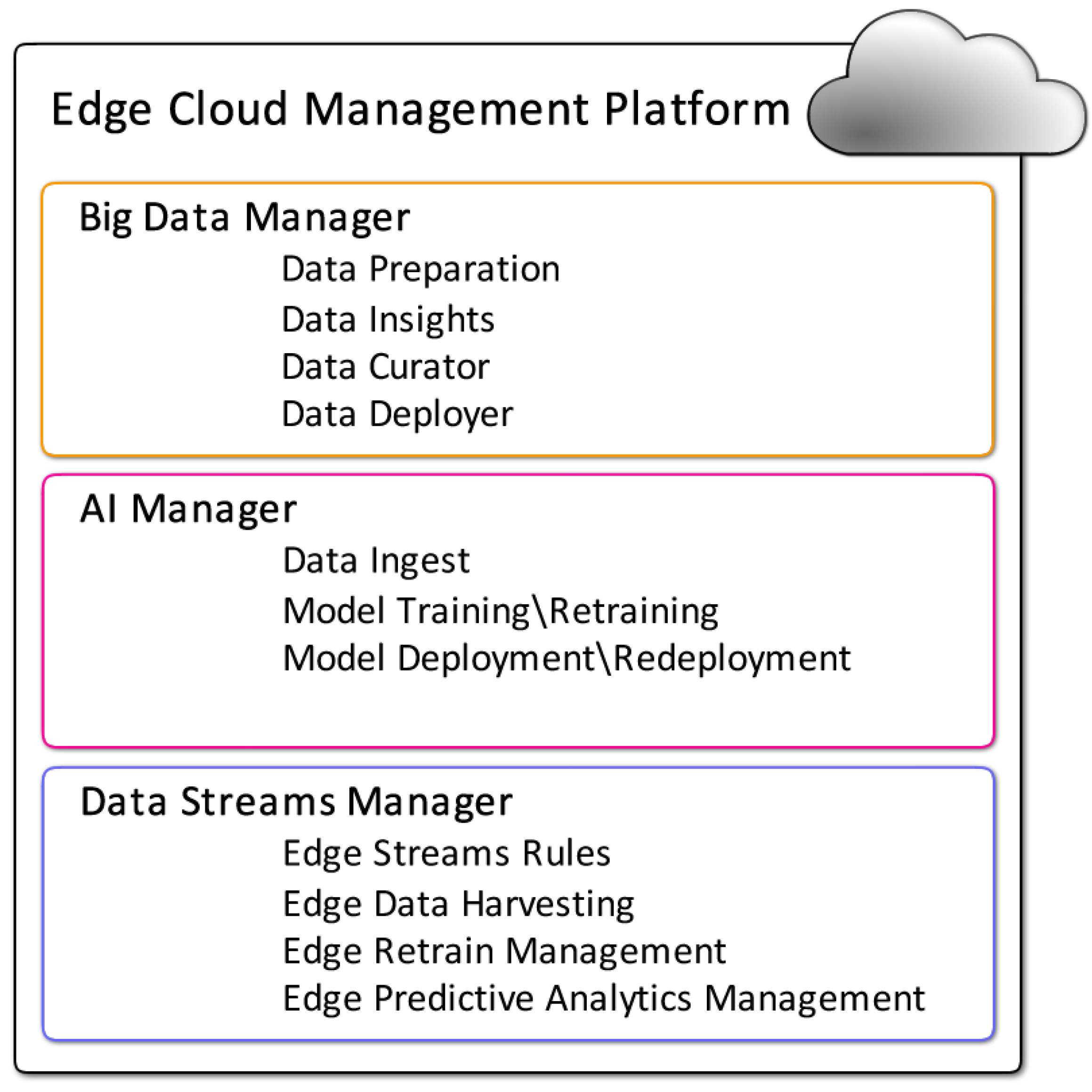
3.1. Edge AI Proposed Infrastructure
- Big Data Manager—for data preparation, analysis, storage, and distribution;
- AI Manager—for data collection and preparation, model training, and model deployment;
- Data Streams Manager—for Edge AI data streams management, from rules definition to data manipulation.
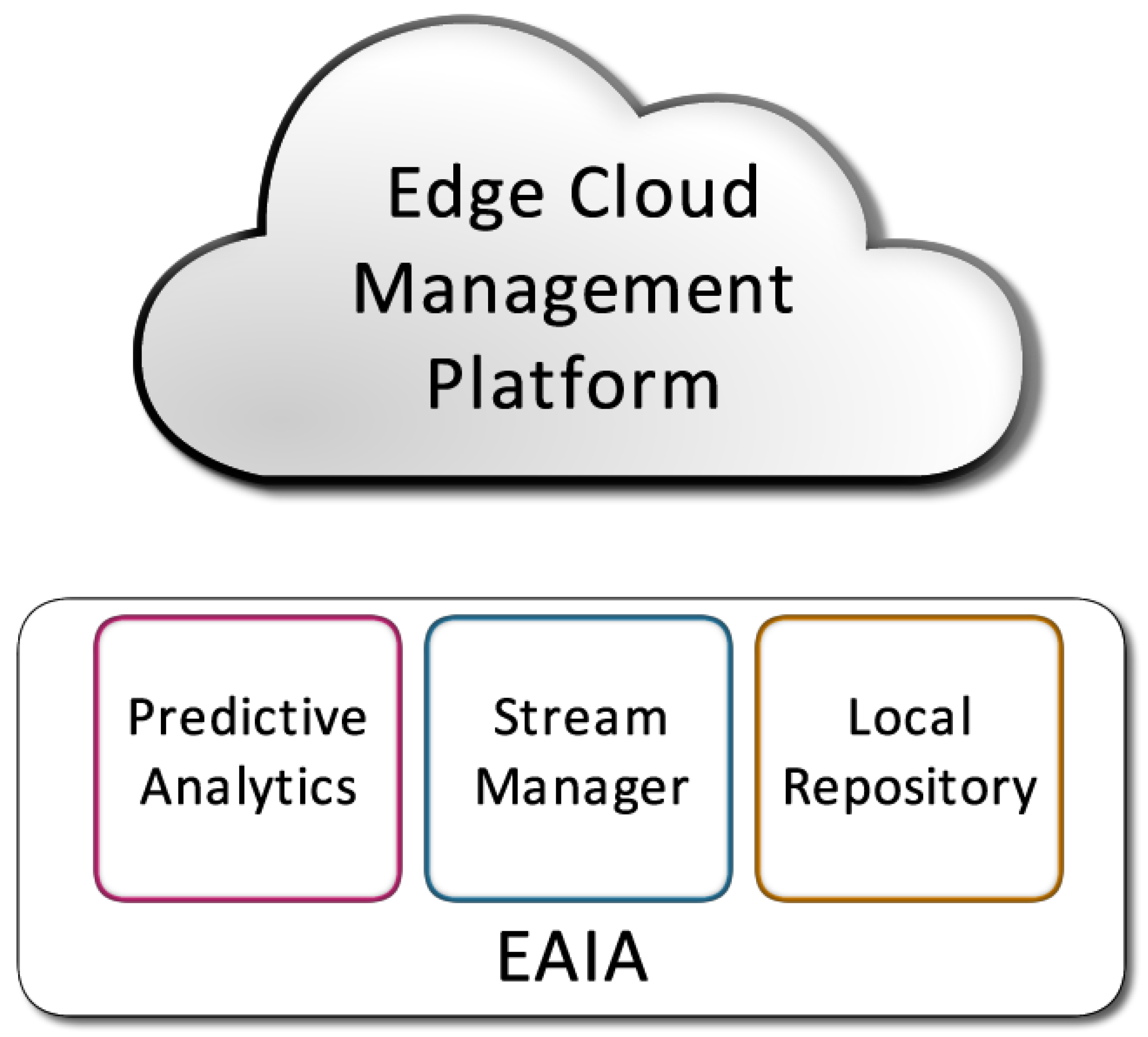
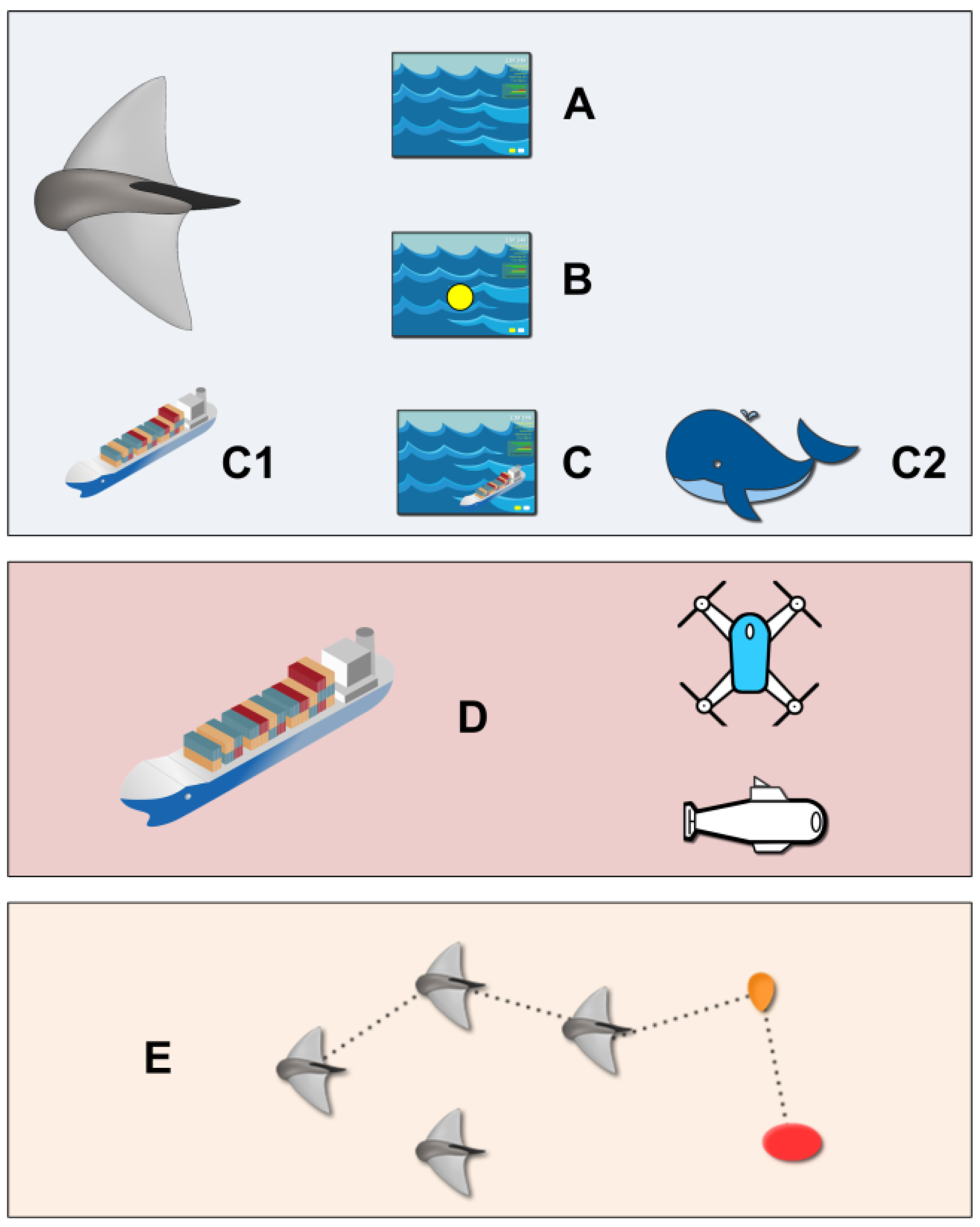
3.2. Edge AI Services Operation Example
4. Conclusions
5. Patents
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Nomenclature
| AI | Artificial Intelligence |
| ATAA | Autonomous Tethered Aerostat Airships |
| DNIB | Data Network Infrastructure Blocks |
| DNIBI | Connected to the DNIB by a Block Interface |
| EAIA | Edge AI Agents |
| DNIHSS | Data Network Infrastructure for Heterogeneous Smart Services |
| GCP | Ground Connection Points |
| GDP | Gross Domestic Product |
| HSS | Heterogeneous Smart Solutions |
| IoT | Edge AI, Blockchain and Internet of Things |
| NMS | Network Managing Services |
| PI | Permanent Installation |
| TI | Temporary Installation |
| TPU | Tensor Processing Unit |
| VPN | Virtual Private Networks |
| VPU | Vision Processing Unit |
References
- Annex 11. Air Traffic Services: Air Traffic Control Service, Flight Information Service, Alerting Service, 13th ed.; International Civil Aviation Organization (ICAO): Ontario, ON, Canada, 2001. [Google Scholar]
- Wahl, T.; Høye, G.K.; Lyngvi, A.; Narheim, B.T. New possible roles of small satellites in maritime surveillance. Acta Astronaut. 2005, 59, 273–277. [Google Scholar] [CrossRef] [Green Version]
- Maini, A.K.; Agrawal, V. Satellite Technology Principles and Applications, 2nd ed.; John Wiley & Sons: West Sussex, UK, 2011. [Google Scholar]
- Cunha, J.; Batista, N.C.; Cardeira, C.; Melicio, R. Wireless networks for traffic light control on urban and aerotropolis roads. J. Sens. Actuator Netw. 2020, 9, 26. [Google Scholar] [CrossRef]
- Buyurgan, N.; Lehlou, N. A terrain risk assessment method for military surveillance applications for mobile assets. Comput. Ind. Eng. 2015, 88, 88–99. [Google Scholar] [CrossRef]
- Babanne, V.; Mahajan, N.S.; Sharma, R.L.; Gargate, P.P. Machine learning based smart surveillance system. In Proceedings of the IEEE 3rd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), Palladam, India, 12–14 December 2019; pp. 84–86. [Google Scholar]
- Hossain, M.A.; Rahman, S.M.M. Towards privacy preserving multimedia surveillance system: A secure privacy vault design. In Proceedings of the IEEE International Symposium on Biometrics and Security Technologies, Chengdu, China, 2–5 July 2013; pp. 280–285. [Google Scholar]
- Asghar, M.N.; Kanwal, N.; Lee, B.; Fleury, M.; Herbst, M.; Qiao, Y. Visual surveillance within the EU general data protection regulation: A technology perspective. IEEE Access 2019, 7, 111709–111726. [Google Scholar] [CrossRef]
- Almoghathawi, Y.; Barker, K. Component importance measures for interdependent infrastructure network resilience. Comput. Ind. Eng. 2019, 133, 153–164. [Google Scholar] [CrossRef]
- Carter, W.A.; Crumpler, W.D. Smart Money on Chinese Advances in AI. Center for Strategic and International Studies. Available online: https://www.csis.org/analysis/smart-money-chinese-advance-ai (accessed on 1 October 2021).
- European Commission. White Paper on Artificial Intelligence: A European Approach to Excellence and Trust. 2020. Available online: https://ec.europa.eu/info/publications/white-paper-artificial-intelligence-european-approach-excellence-and-trust_en (accessed on 1 October 2021).
- Huawei. Huawei Launches the Atlas Intelligent Computing Platform to Fuel an AI Future with Supreme Compute Power. 2018. Available online: https://www.huawei.com/en/press-events/news/2018/10/atlas-intelligent-computing-platform (accessed on 1 October 2021).
- Huawei. Huawei Releases AI Strategy and Full-Stack, All-Scenario AI Portfolio. 2018. Available online: https://www.huawei.com/en/press-events/news/2018/10/huawei-hc-2018-eric-xu-ai (accessed on 1 October 2021).
- Anand, S.R.; Gerard, V. Sizing the Prize: PwC’s Global Artificial Intelligence Study: Exploiting the AI Revolution. PwC Global. Available online: https://www.pwc.com/gx/en/issues/analytics/assets/pwc-ai-analysis-sizing-the-prize-report.pdf (accessed on 1 October 2021).
- Zhang, D.; Mishra, S.; Brynjolfsson, E.; Etchemendy, J.; Ganguli, D.; Grosz, B.; Lyons, T.; Manyika, J.; Niebles, J.C.; Sellitto, M.; et al. The AI Index 2021 Annual Report; AI Index Steering Committee, Human-Centered AI Institute, Stanford University: Stanford, CA, USA, 2021. [Google Scholar]
- Bürer, M.J.; Lapparent, M.; Pallotta, V.; Capezzali, M.; Carpita, M. Use cases for Blockchain in the energy industry opportunities of emerging business models and related risks. Comput. Ind. Eng. 2019, 137, 1–9. [Google Scholar] [CrossRef] [Green Version]
- Li, M.; Shen, L.; Huang, G.Q. Blockchain-enabled workflow operating system for logistics resources sharing in e-commerce logistics real estate service. Comput. Ind. Eng. 2019, 135, 950–969. [Google Scholar] [CrossRef]
- Grilo, A.; Zutshi, A. Preface for special issue on Blockchain and tokenization for industry and services. Comput. Ind. Eng. 2020, 146, 106575. [Google Scholar] [CrossRef]
- Biswas, B.; Gupta, R. Analysis of barriers to implement Blockchain in industry and service sectors. Comput. Ind. Eng. 2019, 136, 225–241. [Google Scholar] [CrossRef]
- Helo, P.; Hao, Y. Blockchains in operations and supply chains: A model and reference implementation. Comput. Ind. Eng. 2019, 136, 242–251. [Google Scholar] [CrossRef]
- Adhikari, S.; Davis, C. Application of Blockchain within Aviation Cybersecurity Framework. Available online: https://doi.org/10.2514/6.2020-2931 (accessed on 1 October 2021).
- Alladi, T.; Chamola, V.; Sahu, N.; Guizani, M. Applications of Blockchain in unmanned aerial vehicles: A review. Veh. Commun. 2020, 23, 100249. [Google Scholar] [CrossRef]
- Dave, D.; Parikh, S.; Patel, R.; Doshi, N. A survey on Blockchain technology and its proposed solutions. Procedia Comput. Sci. 2019, 160, 740–745. [Google Scholar] [CrossRef]
- Bonomo, I.S.; Barbosa, I.R.; Monteiro, L.; Bassetto, C.; Barreto, A.B.; Borges, V.R.P.; Weigang, L. Development of SWIM registry for air traffic management with the Blockchain support. In Proceedings of the 21st IEEE International Conference on Intelligent Transportation Systems, Maui, HI, USA, 4–7 November 2018; pp. 3544–3549. [Google Scholar]
- Mandolla, C.; Petruzzelli, A.M.; Percoco, G.; Urbinati, A. Building a digital twin for additive manufacturing through the exploitation of Blockchain: A case analysis of the aircraft industry. Comput. Ind. 2019, 109, 134–152. [Google Scholar] [CrossRef]
- Liu, X.L.; Wang, W.M.; Guo, H.; Barenji, A.V.; Li, Z.; Huang, G.Q. Industrial Blockchain based framework for product lifecycle management in industry 4.0. Robot. Comput.-Integr. Manuf. 2020, 63, 101897. [Google Scholar] [CrossRef]
- Dalal, D.; Yong, S.; Lewis, A. The Future is Here: Project Ubin: SGD on Distributed Ledger. Deloitte. Available online: https://www2.deloitte.com/content/dam/Deloitte/sg/Documents/financial-services/sg-fsi-project-ubin-report.pdf (accessed on 1 October 2021).
- Batista, N.C.; Melicio, R.; Mendes, V.M.F. Services enabler architecture for smart grid and smart living services providers under industry 4.0. Energy Build. 2017, 141, 16–27. [Google Scholar] [CrossRef] [Green Version]
- Schaeffer, E. Industry X.0: Realizing Digital Value in Industrial Sectors, 1st ed.; Kogan Page: London, UK, 2017; pp. 154–196. [Google Scholar]
- Abood, D.; Quilligan, A.; Narsalay, R. Industry X.0 Combine and Conquer: Unlocking the Power of Digital. Accenture. Available online: https://www.accenture.com/_acnmedia/Accenture/Conversion-Assets/DotCom/Documents/Global/PDF/Dualpub_26/Accenture-Industry-XO-whitepaper.pdf (accessed on 1 October 2021).
- Gomes, I.L.R.; Melicio, R.; Mendes, V.M.F.; Gordo, P.; Pardal, T.C.D. Aerostat powered by PV cells: Hot-spot effect. In Proceedings of the 8th IEEE International Conference on Renewable Energy Research and Applications, Brasov, Romania, 3–6 November 2019; pp. 477–482. [Google Scholar]
- Samson, J.; Katebi, R. Multivariable control of a lighter than air system. In Proceedings of the IEEE 2014 UKACC International Conference on Control, Loughborough, UK, 9–11 July 2014; pp. 256–261. [Google Scholar]
- Lawrence, D.A.; Balsley, B.B. High-resolution atmospheric sensing of multiple atmospheric variables using the datahawk small airborne measurement system. J. Atmos. Ocean. Technol. 2013, 30, 2352–2366. [Google Scholar] [CrossRef]
- Marcadé, E. SAP Leonardo Machine Learning Machine Learning Deep in Enterprise Applications. SAP Leonardo Live. Available online: http://assets.dm.ux.sap.com/de-leonardolive/pdfs/51419_sap_is2_3.pdf (accessed on 1 October 2021).
- Longo, F.; Nicoletti, L.; Padovano, A.; d’Atri, G.; Forte, M. Blockchain-enabled supply chain: An experimental study. Comput. Ind. Eng. 2019, 136, 57–69. [Google Scholar] [CrossRef]
- Hasan, H.; AlHadhrami, E.; AlDhaheri, A.; Salah, K.; Jayaraman, R. Smart contract-based approach for efficient shipment management. Comput. Ind. Eng. 2019, 136, 149–159. [Google Scholar] [CrossRef]
- Kim, S.-K. Blockchain governance game. Comput. Ind. Eng. 2019, 136, 373–380. [Google Scholar] [CrossRef] [Green Version]
- Barry, B.; Brick, C.; Connor, F.; Donohoe, D.; Moloney, D.; Richmond, R.; O’Riordan, M.; Toma, V. Always-on vision processing unit for mobile applications. IEEE Micro 2015, 35, 56–66. [Google Scholar] [CrossRef]
- Rivas-Gomez, S.; Pena, A.J.; Moloney, D.; Laure, E.; Markidis, S. Exploring the vision processing unit as co-processor for inference. In Proceedings of the IEEE International Parallel and Distributed Processing Symposium Workshops, Vancouver, BC, Canada, 21–25 May 2018; pp. 589–598. [Google Scholar]
- Sengupta, J.; Kubendran, R.; Neftci, E.; Andreou, A. High-speed, real-time, spike-based object tracking and path prediction on google edge TPU. In Proceedings of the IEEE 2nd International Conference on Artificial Intelligence Circuits and Systems, Genova, Italy, 31 August–2 September 2020; pp. 134–135. [Google Scholar]
- Huawei. Developers Open API SDK Tools Developer-Huawei Cloud. 2020. Available online: https://developer.huaweicloud.com/en-us/ (accessed on 1 October 2021).
- Huawei. HIC AI Infrastructure Ecosystem | Cloud Solution—Huawei Enterprise Global. 2020. Available online: https://e.huawei.com/sg/solutions/hic/solution/atlas (accessed on 1 October 2021).
- Huawei. Atlas 200 AI Accelerator Module. 2020. Available online: https://e.huawei.com/en/products/cloud-computing-dc/servers/g-series/atlas-200-ai (accessed on 1 October 2021).
- Huawei. Atlas 300 AI Accelerator Card. 2020. Available online: https://e.huawei.com/en/products/cloud-computing-dc/servers/g-series/atlas-300-ai (accessed on 1 October 2021).
- Huawei. Atlas 800 Deep Learning System. 2020. Available online: https://e.huawei.com/en/products/cloud-computing-dc/servers/g-series/atlas-800-ai (accessed on 1 October 2021).
- Huawei. Atlas G2500 Smart Video Analytics Server. 2020. Available online: https://e.huawei.com/en/products/cloud-computing-dc/servers/g-series/g2500 (accessed on 1 October 2021).
- SparkFun. SparkFun Edge Development Board-Apollo3 Blue. SparkFun Electronics. Available online: https://www.sparkfun.com/products/15170 (accessed on 1 October 2021).
- Qualcomm. Dragon Board 820c Development Board—Qualcomm Developer Network. Qualcomm Technologies, Inc. 2020. Available online: https://developer.qualcomm.com/hardware/dragonboard-820c (accessed on 1 October 2021).
- Pester, A.; Schrittesser, M. Object detection with Raspberry Pi3 and movidius neural network stick. In Proceedings of the 5th Experiment International Conference, Funchal, Portugal, 12–14 June 2019; pp. 326–330. [Google Scholar]
- OrangePi. Orange Pi AI Stick 2801: Orangepi. Shenzhen Xunlong Software CO. 2020. Available online: http://www.orangepi.org/Orange%20Pi%20AI%20Stick%202801/ (accessed on 1 October 2021).
- Chen, H. Spam message filtering recognition system based on tensorflow. In Proceedings of the 3rd International Conference on Mechanical, Control and Computer Engineering, Huhhot, China, 14–16 September 2018; pp. 564–567. [Google Scholar]
- Demirović, D.; Skejić, E.; Šerifović–Trbalić, A. Performance of some image processing algorithms in tensorflow. In Proceedings of the 25th IEEE International Conference on Systems, Signals and Image Processing, Maribor, Slovenia, 20–22 June 2018; pp. 1–4. [Google Scholar]
- Ertam, F.; Aydın, G. Data classification with deep learning using tensorflow. In Proceedings of the 2017 International Conference on Computer Science and Engineering (UBMK), Antalya, Turkey, 5–8 October 2017; pp. 755–758. [Google Scholar]
- Huizhong, W.; Linhan, Q.; Keke, H. A tensorflow based feature learning method application in fault detecting of tract motor. In Proceedings of the IEEE 2018 Chinese Control and Decision Conference, Shenyang, China, 9–11 June 2018; pp. 3248–3252. [Google Scholar]
- Ju, Y.; Wang, X.; Chen, X. Research on OMR recognition based on convolutional neural network tensorflow platform. In Proceedings of the IEEE 11th International Conference on Measuring Technology and Mechatronics Automation, Qiqihar, China, 28–29 April 2019; pp. 688–691. [Google Scholar]
- Nandan, N.; Thippeswamy, K. A tensorflow based robotic arm. In Proceedings of the 2018 International Conference on Electrical, Electronics, Communication, Computer, and Optimization Techniques, Msyuru, India, 14–15 December 2018; pp. 326–330. [Google Scholar]
- Phadnis, R.; Mishra, J.; Bendale, S. Objects talk—object detection and pattern tracking using tensorflow. In Proceedings of the IEEE 2nd International Conference on Inventive Communication and Computational Technologies, Coimbatore, India, 20–21 April 2018; pp. 1216–1219. [Google Scholar]
- Zeng, Z.; Gong, Q.; Zhang, J. CNN model design of gesture recognition based on tensorflow framework. In Proceedings of the IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference, Chengdu, China, 15–17 March 2019; pp. 1062–1067. [Google Scholar]
- Banerjee, D.S.; Hamidouche, K.; Panda, D.K. Re-designing CNTK deep learning framework on modern GPU enabled clusters. In Proceedings of the IEEE International Conference on Cloud Computing Technology and Science, Luxembourg, 12–15 December 2016; pp. 144–151. [Google Scholar]
- Adie, H.T.R.; Pradana, I.A.; Pranowo, P. Parallel computing accelerated image inpainting using GPU CUDA, theano, and tensorflow. In Proceedings of the 10th International Conference on Information Technology and Electrical Engineering, Kuta, Indonesia, 24–26 July 2018; pp. 621–625. [Google Scholar]
- Boufenar, C.; Batouche, M. Investigation on deep learning for off-line handwritten arabic character recognition using theano research platform. In Proceedings of the IEEE Intelligent Systems and Computer Vision, Fez, Morocco, 17–19 April 2017; pp. 1–6. [Google Scholar]
- Soni, A.; Singh, A.P. Automatic motorcyclist helmet rule violation detection using tensorflow & keras in openCV. In Proceedings of the IEEE International Students’ Conference on Electrical, Electronics and Computer Science, Bhopal, India, 22–23 February 2020; pp. 1–5. [Google Scholar]
- Tseng, C.; Lee, S. Design of digital differentiator using supervised learning on keras framework. In Proceedings of the IEEE 8th Global Conference on Consumer Electronics, Osaka, Japan, 15–18 October 2019; pp. 162–163. [Google Scholar]
- Vani, A.K.; Raajan, R.N.; Winmalar, D.H.; Sudharsan, R. Using the keras model for accurate and rapid gender identification through detection of facial features. In Proceedings of the IEEE 4th International Conference on Computing Methodologies and Communication, Erode, India, 11–13 March 2020; pp. 572–574. [Google Scholar]
- Komar, M.; Yakobchuk, P.; Golovko, V.; Dorosh, V.; Sachenko, A. Deep neural network for image recognition based on the Caffe framework. In Proceedings of the 2018 IEEE Second International Conference on Data Stream Mining & Processing, Lviv, Ukraine, 21–25 August 2018; pp. 102–106. [Google Scholar]
- Satyavolu, S.; Bagubali, A. Implementation of tensorflow and Caffe frameworks: In view of application. In Proceedings of the IEEE International Conference on Vision Towards Emerging Trends in Communication and Networking, Vellore, India, 30–31 March 2019; pp. 1–4. [Google Scholar]
- Shams, S.; Platania, R.; Lee, K.; Park, S. Evaluation of deep learning frameworks over different HPC architectures. In Proceedings of the IEEE 37th International Conference on Distributed Computing Systems, Atlanta, GA, USA, 5–8 June 2017; pp. 1389–1396. [Google Scholar]
- Wang, L.; Zhao, Y.; Li, X. An automatic conversion tool for caffe neural network configuration oriented to openCL-based FPGA platforms. In Proceedings of the IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference, Chengdu, China, 15–17 March 2019; pp. 195–198. [Google Scholar]
- Manu, K. Introducing Machine Learning with SAP Leonardo. SAP Press. 2018. Available online: https://docero.tips/doc/introducing-machine-learning-with-sap-leonardo-2018-kjdwezq7eg (accessed on 1 October 2021).
- Chen, L.; Li, R.; Liu, Y.; Zhang, R.; Woodbridge, D.M. Machine learning-based product recommendation using Apache Spark. In Proceedings of the IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation, San Francisco, CA, USA, 4–8 August 2017; pp. 1–6. [Google Scholar]
- Kaplunovich, A.; Yesha, Y. Cloud big data decision support system for machine learning on AWS: Analytics of analytics. In Proceedings of the 2017 IEEE International Conference on Big Data, Boston, MA, USA, 11–14 December 2017; pp. 3508–3516. [Google Scholar]
- Ramesh, R. Predictive analytics for banking user data using AWS machine learning cloud service. In Proceedings of the IEEE 2nd International Conference on Inventive Communication and Computational Technologies, Chennai, India, 20–21 April 2018; pp. 210–215. [Google Scholar]
- Vaibhav, S.L.; Rao, K.S.; Kumar, V.; Vijayananda, J. A comparative study of feature selection methods for classification of chest x-ray image as normal or abnormal inside AWS ECS cluster. In Proceedings of the IEEE International Conference on Cloud Computing in Emerging Markets, Bangalore, India, 23–24 November 2018; pp. 7–13. [Google Scholar]
- Tajane, K.; Dave, S.; Jahagirdar, P.; Ghadge, A.; Musale, A. AI based chat-bot using azure cognitive services. In Proceedings of the IEEE 4th International Conference on Computing Communication Control and Automation, Pune, India, 16–18 August 2018; pp. 1–4. [Google Scholar]
- Verma, A.; Malla, D.; Choudhary, A.K.; Arora, V. A detailed study of azure platform & its cognitive services. In Proceedings of the IEEE International Conference on Machine Learning, Big Data, Cloud and Parallel Computing, Faridabad, India, 14–16 February 2019; pp. 129–134. [Google Scholar]




Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Batista, N.; Melicio, R.; Santos, L.F. Large Geographical Area Aerial Surveillance Systems Data Network Infrastructure Managed by Artificial Intelligence and Certified over Blockchain: A Review. Network 2021, 1, 335-353. https://doi.org/10.3390/network1030019
Batista N, Melicio R, Santos LF. Large Geographical Area Aerial Surveillance Systems Data Network Infrastructure Managed by Artificial Intelligence and Certified over Blockchain: A Review. Network. 2021; 1(3):335-353. https://doi.org/10.3390/network1030019
Chicago/Turabian StyleBatista, Nelson, Rui Melicio, and Luis Filipe Santos. 2021. "Large Geographical Area Aerial Surveillance Systems Data Network Infrastructure Managed by Artificial Intelligence and Certified over Blockchain: A Review" Network 1, no. 3: 335-353. https://doi.org/10.3390/network1030019
APA StyleBatista, N., Melicio, R., & Santos, L. F. (2021). Large Geographical Area Aerial Surveillance Systems Data Network Infrastructure Managed by Artificial Intelligence and Certified over Blockchain: A Review. Network, 1(3), 335-353. https://doi.org/10.3390/network1030019







