Toward Automatic Monitoring for Anomaly Detection in Open-Pit Phosphate Mines Using Artificial Vision: A Case Study of the Screening Unit
Abstract
:1. Introduction
2. Malfunctions of the Phosphate Production Chain in the Benguerir Mining Site
- Project losses: there are losses of phosphate in places that have been abandoned and not mined; they involve the abandonment of phosphate levels whose mining generates very high ratios and is, therefore, economically unfeasible.
- On-site losses: there are losses linked to different operational stages, from the kinematic chain that extracts the various phosphate layers to the final loading of the product.
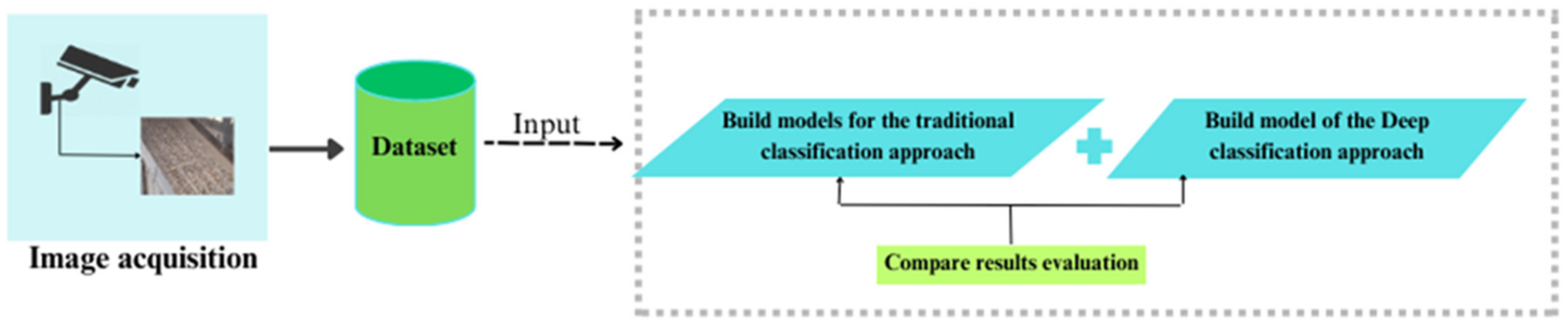
3. Materials and Methods
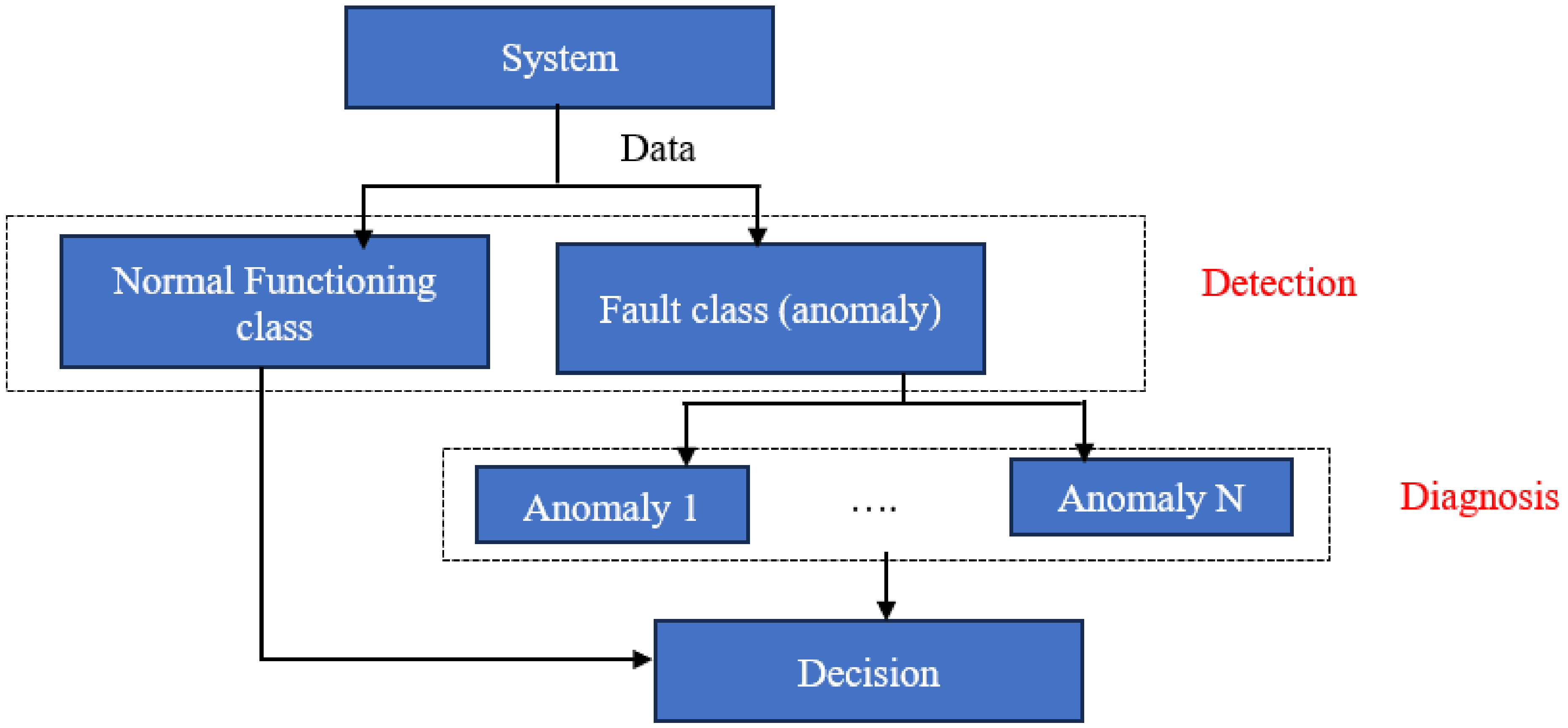
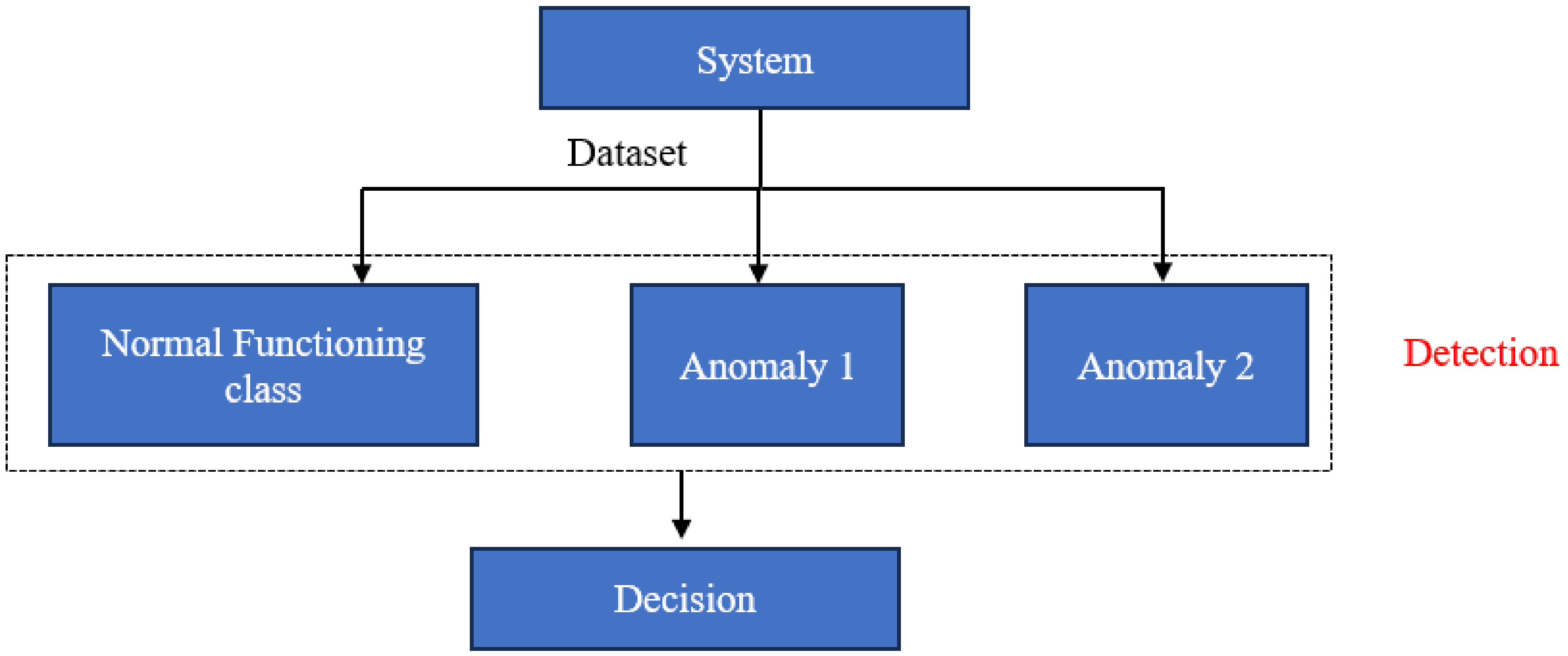
3.1. Method
- Anomaly 1: High sterilization rate.
- Anomaly 2: The passage of phosphate material to screen rejection (phosphate loss).
| Algorithm | Principle | Application |
|---|---|---|
| HOG: Histogram of Oriented Gradient | HOG is a feature descriptor proposed by Navneet Dalal and Bill Triggs in 2005 [30] and used in computer vision for object detection. The basic principle of this descriptor is the use of the intensity distribution of the gradient or the direction of the contours. |  |
| SIFT: Scale Invariant Feature Transform | SIFT is a feature extractor proposed by researcher David Lowe in [31]. The general idea of this algorithm is to extract characteristic points, called “features points”, on an image in such a way that these points are invariant to several transformations, including rotation, illumination, and, especially, invariant to scale. | 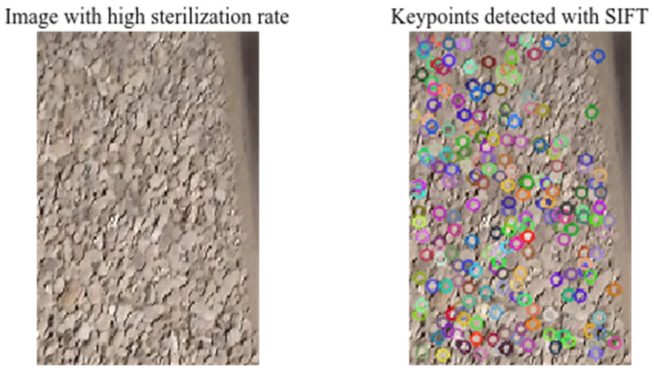 |
| LBP: Local Binary Pattern | This descriptor was first mentioned in 1993 to measure an image’s local contrast but was popularised three years later by Ojala et al. to analyze textures [32]; it is also used to detect and track moving objects in an image sequence. The general principle is to compare a pixel’s luminance level with its neighbors’ levels. | 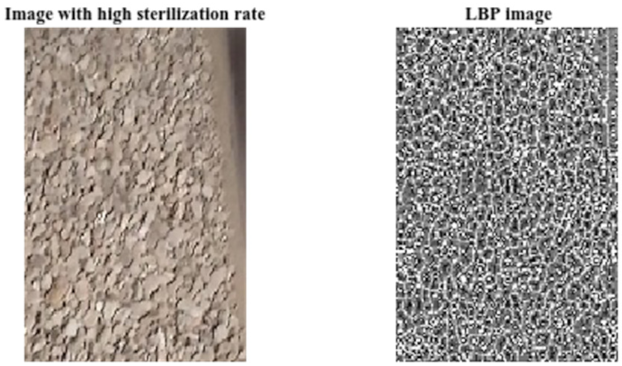 |
3.2. Datasets Preparation and System Configuration
3.3. Evaluation Metrics
- “TP of Ci” is all Ci instances that are classified as Ci.
- “TN of Ci” is all non-Ci instances not classified as Ci.
- “FP of Ci” is all non-Ci instances that are classified as Ci.
- “FN of Ci” is all Ci instances not classified as Ci.
4. Implementation and Results
4.1. Implementation
4.1.1. Machine-Learning Approach
4.1.2. Deep-Learning Approach
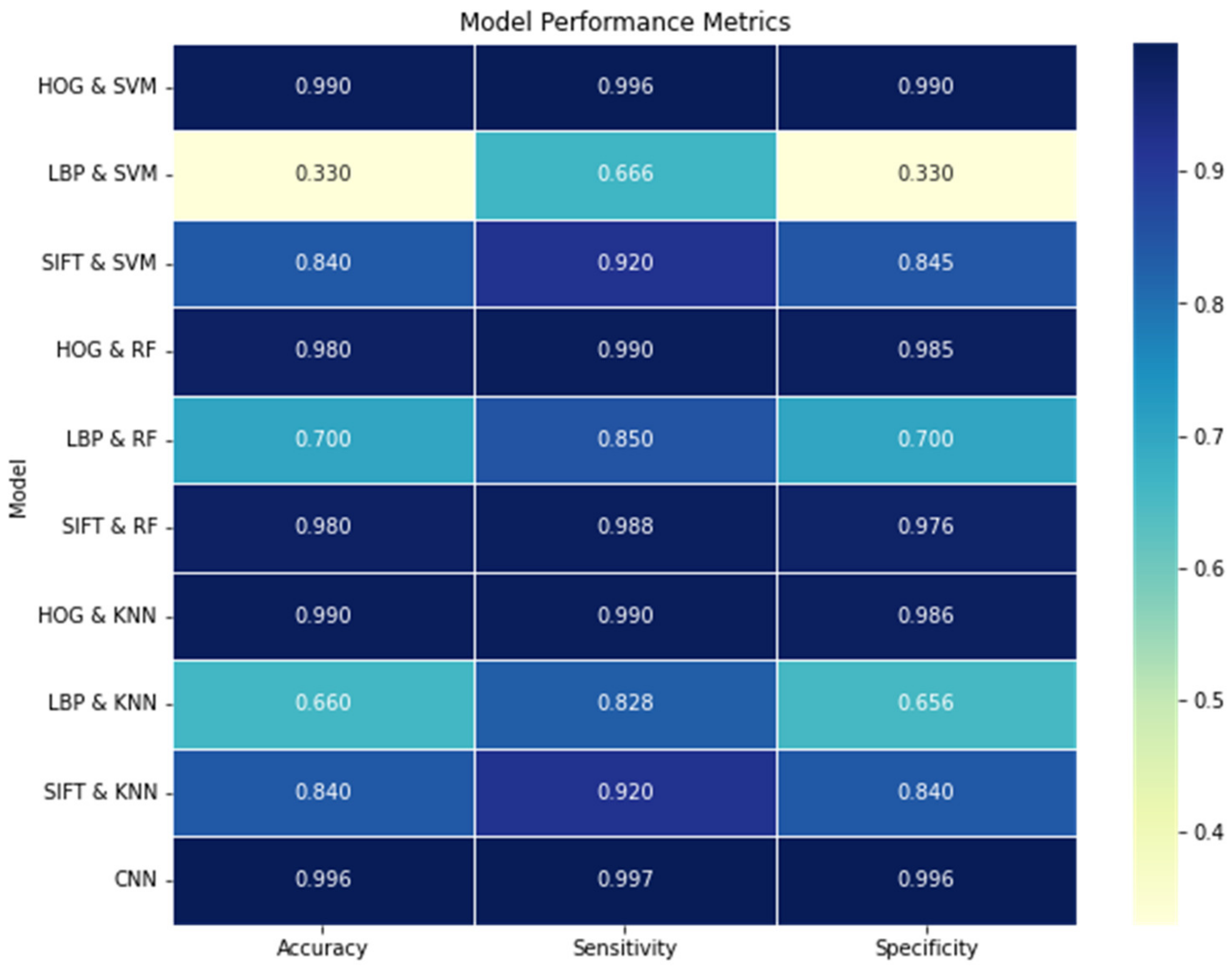
4.2. Results
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kelly, T.; Matos, G.R.; Buckingham, D.A.; DiFrancesco, C.A.; Porter, K.E.; Berry, C.; Crane, M.; Goonan, T.; Sznopek, J. Historical Statistics for Mineral and Material Commodities in the United States; Data Series; U.S. Geological Survey: Reston, VA, USA, 2005; Volume 140. [Google Scholar]
- Steen, I. Phosphorus Availability in the 21st Century: Management of a Non-Renewable Resource. Phosphorus Potassium 1998, 217, 25–31. [Google Scholar]
- Cordell, D.; Drangert, J.-O.; White, S. The story of phosphorus: Global food security and food for thought. Glob. Environ. Chang. 2009, 19, 292–305. [Google Scholar] [CrossRef]
- Van Vuuren, D.P.; Bouwman, A.F.; Beusen, A.H.W. Phosphorus demand for the 1970–2100 period: A scenario analysis of resource depletion. Glob. Environ. Chang. 2010, 20, 428–439. [Google Scholar] [CrossRef]
- Stewart, W.M.; Dibb, D.W.; Johnston, A.E.; Smyth, T.J. The Contribution of Commercial Fertilizer Nutrients to Food Production. Agron. J. 2005, 97, 1–6. [Google Scholar] [CrossRef]
- Gouaillier, V.; Fleurant, A.-E. La Vidéosurveillance Intelligente: Promesses et Défis; CRIM: Montreal, QC, Canada, 2009; Volume 104. [Google Scholar]
- David Jenkins, M.; Buggy, T.; Morison, G. An imaging system for visual inspection and structural condition monitoring of railway tunnels. In Proceedings of the 2017 IEEE Workshop on Environmental, Energy, and Structural Monitoring Systems (EESMS), Milan, Italy, 24–25 July 2017; pp. 1–6. [Google Scholar]
- Marino, F.; Distante, A.; Mazzeo, P.L.; Stella, E. A Real-Time Visual Inspection System for Railway Maintenance: Automatic Hexagonal-Headed Bolts Detection. IEEE Trans. Syst. Man Cybern. Part C 2007, 37, 418–428. [Google Scholar] [CrossRef]
- Park, S.; Choi, Y. Applications of Unmanned Aerial Vehicles in Mining from Exploration to Reclamation: A Review. Minerals 2020, 10, 663. [Google Scholar] [CrossRef]
- Dey, P.; Chaulya, S.K.; Kumar, S. Hybrid CNN-LSTM and IoT-based coal mine hazards monitoring and prediction system. Process Saf. Environ. Prot. 2021, 152, 249–263. [Google Scholar] [CrossRef]
- Wang, C.; Chang, L.; Zhao, L.; Niu, R. Automatic Identification and Dynamic Monitoring of Open-Pit Mines Based on Improved Mask R-CNN and Transfer Learning. Remote Sens. 2020, 12, 3474. [Google Scholar] [CrossRef]
- El Hiouile, L.; Errami, A.; Azami, N.; Majdoul, R.; Deshayes, L. Evaluation of Classical Descriptors coupled to Support Vector Machine Classifier for Phosphate ore Screening monitoring. In Proceedings of the 13th International Conference on Intelligent Systems: Theories and Applications, Rabat, Morocco, 23–24 September 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 1–7. [Google Scholar]
- El Hiouile, L.; Errami, A.; Azami, N.; Majdoul, R. Deep Neural Network Descriptor for Anomaly Detection in the Screening Unit of an Open Pit Phosphate Mine. In International Symposium on Ubiquitous Networking; Elbiaze, H., Sabir, E., Falcone, F., Sadik, M., Lasaulce, S., Ben Othman, J., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 239–251. [Google Scholar]
- Laaniber, N.; El Krouni, M. Rapport du Projet de fin d Études—PDF Téléchargement Gratuit. Available online: https://docplayer.fr/82250671-Rapport-du-projet-de-fin-d-etudes.html (accessed on 20 May 2023).
- Tidriri, K. Decision Fusion Dedicated to the Monitoring of Complex Systems. Ph.D. Thesis, Université d’Angers, Angers, France, 2018. [Google Scholar]
- Tidriri, K.; Chatti, N.; Verron, S.; Tiplica, T. Bridging data-driven and model-based approaches for process fault diagnosis and health monitoring: A review of researches and future challenges. Annu. Rev. Control. 2016, 42, 63–81. [Google Scholar] [CrossRef]
- Weimer, D.; Scholz-Reiter, B.; Shpitalni, M. Design of deep convolutional neural network architectures for automated feature extraction in industrial inspection. CIRP Ann. 2016, 65, 417–420. [Google Scholar] [CrossRef]
- Staar, B.; Lütjen, M.; Freitag, M. Anomaly detection with convolutional neural networks for industrial surface inspection. Procedia CIRP 2019, 79, 484–489. [Google Scholar] [CrossRef]
- Haselmann, M.; Gruber, D.P.; Tabatabai, P. Anomaly Detection Using Deep Learning based Image Completion. arXiv 2018, arXiv:1811.06861. [Google Scholar]
- Ricco, R. SVM—Support Vector Machine. Available online: https://eric.univ-lyon2.fr/ricco/cours/slides/svm.pdf (accessed on 1 October 2023).
- Pal, M. Random forest classifier for remote sensing classification. Int. J. Remote Sens. 2005, 26, 217–222. [Google Scholar] [CrossRef]
- Cunningham, P.; Delany, S. k-Nearest neighbour classifiers. arXiv 2007, arXiv:2004.04523. [Google Scholar]
- Khan, S.; Rahmani, H.; Shah, S.A.A.; Bennamoun, M. A Guide to Convolutional Neural Networks for Computer Vision. In Lectures on Computer Vision; Springer: Cham, Switzerland, 2018; Volume 8, pp. 1–207. [Google Scholar] [CrossRef]
- Seemanthini, K.; Manjunath, S.S. Human Detection and Tracking using HOG for Action Recognition. Procedia Comput. Sci. 2018, 132, 1317–1326. [Google Scholar] [CrossRef]
- Patel, H.A.; Rajput, R.D. Smart Surveillance System Using Histogram of Oriented Gradients (HOG) Algorithm and Haar Cascade Algorithm. In Proceedings of the 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018; pp. 1–4. [Google Scholar]
- Vashistha, P.; Bhatnagar, C.; Khan, M.A. An architecture to identify violence in video surveillance system using ViF and LBP. In Proceedings of the 2018 4th International Conference on Recent Advances in Information Technology (RAIT), Dhanbad, India, 15–17 March 2018; pp. 1–6. [Google Scholar]
- Bilik, S.; Horak, K. SIFT and SURF based feature extraction for the anomaly detection 2022. arXiv 2022. [Google Scholar] [CrossRef]
- Amraee, S.; Vafaei, A.; Jamshidi, K.; Adibi, P. Abnormal event detection in crowded scenes using one-class SVM. SIViP 2018, 12, 1115–1123. [Google Scholar] [CrossRef]
- Decor, G.; Bah, M.D.; Foucher, P.; Charbonnier, P.; Heitz, F. Defect Detection in Tunnel Images using Random Forests and Deep Learning. In Proceedings of the 10th International Conference on Pattern Recognition Systems, Tours, France, 8–10 July 2019. [Google Scholar]
- Dalal, N.; Triggs, B. Histograms of Oriented Gradients for Human Detection. In Proceedings of the 2005 IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR’05), San Diego, CA, USA, 20–25 June 2005; IEEE: San Diego, CA, USA, 2005; Volume 1, pp. 886–893. [Google Scholar]
- Lowe, D.G. Distinctive Image Features from Scale-Invariant Keypoints. Int. J. Comput. Vis. 2004, 60, 91–110. [Google Scholar] [CrossRef]
- Ojala, T.; Pietikäinen, M.; Harwood, D. A Comparative Study of Texture Measures with Classification Based on Featured Distributions. Pattern Recognit. 1996, 29, 51–59. [Google Scholar] [CrossRef]
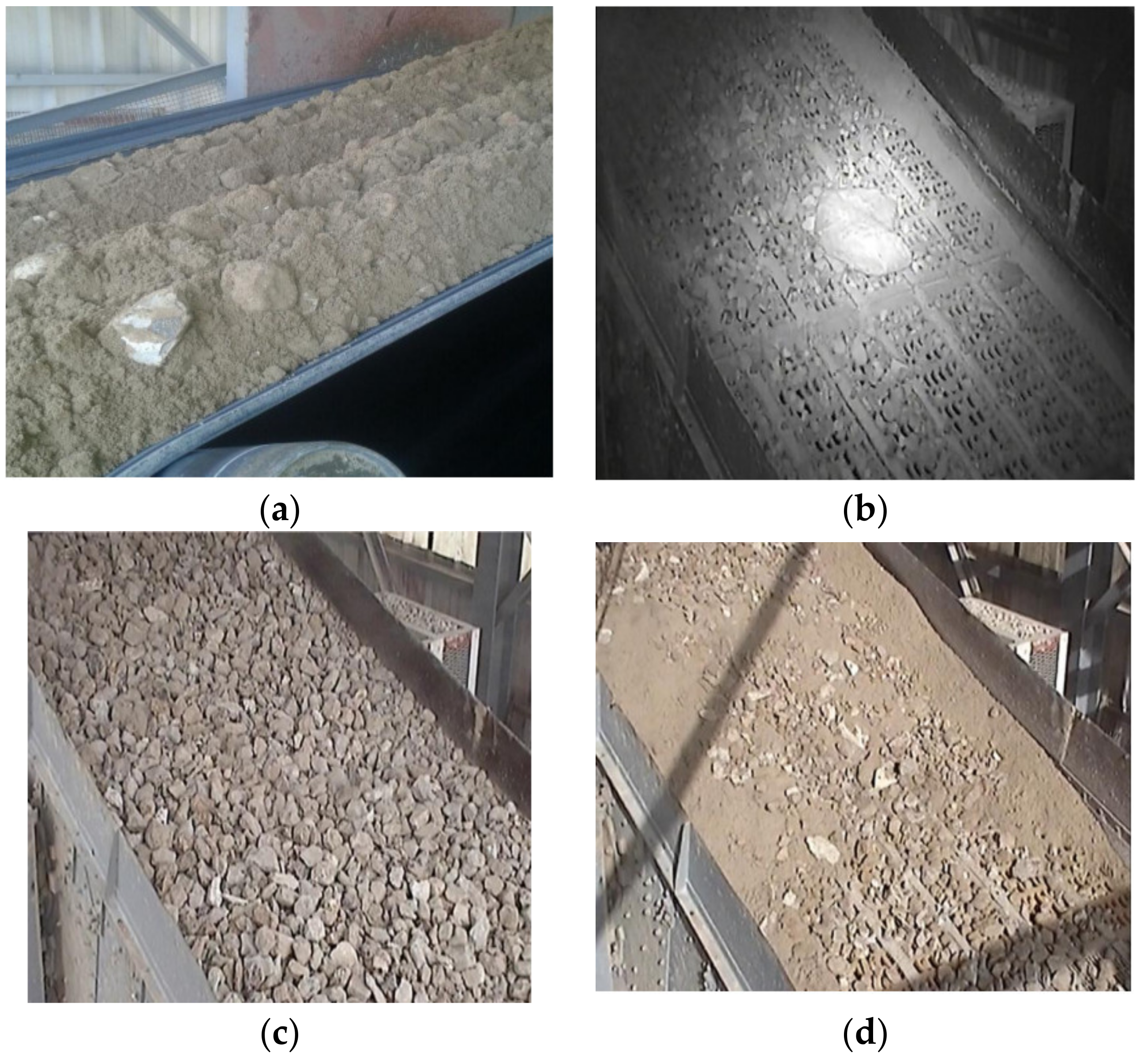


| Class | Train | Test |
|---|---|---|
| Phosphate less | 399 | 266 |
| High-sterilization rate | 400 | 267 |
| Good functioning | 401 | 267 |
| Total | 1200 | 800 |
| Input: Image (180, 120, 1) |
|---|
| Normalization |
| Conv4-64 |
| Maxpol-2 |
| Dropout (0.1) |
| Conv4-64 |
| Maxpool-2 |
| Dropout (0.3) |
| Flatten |
| Fc-256 |
| Dropout (0.5) |
| Fc-64 |
| Normalization |
| SoftMax |
| Model | HOG & SVM | LBP & SVM | SIFT & SVM | HOG & RF | LBP & RF | SIFT & RF | HOG & KNN | LBP & KNN | SIFT & KNN | CNN |
|---|---|---|---|---|---|---|---|---|---|---|
| Train Accuracy | 0.99 | 0.42 | 0.84 | 0.97 | 0.93 | 0.94 | 0.99 | 0.76 | 0.81 | 1 |
| Model | Time to Process an Image (s) |
|---|---|
| HOG and SVM | 0.025 |
| HOG and RF | 0.013 |
| HOG and KNN | 0.013 |
| SIFT and SVM | 0.004 |
| SIFT and RF | 0.0005 |
| SIFT and KNN | 0.0007 |
| CNN | 0.0008 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
El Hiouile, L.; Errami, A.; Azami, N. Toward Automatic Monitoring for Anomaly Detection in Open-Pit Phosphate Mines Using Artificial Vision: A Case Study of the Screening Unit. Mining 2023, 3, 645-658. https://doi.org/10.3390/mining3040035
El Hiouile L, Errami A, Azami N. Toward Automatic Monitoring for Anomaly Detection in Open-Pit Phosphate Mines Using Artificial Vision: A Case Study of the Screening Unit. Mining. 2023; 3(4):645-658. https://doi.org/10.3390/mining3040035
Chicago/Turabian StyleEl Hiouile, Laila, Ahmed Errami, and Nawfel Azami. 2023. "Toward Automatic Monitoring for Anomaly Detection in Open-Pit Phosphate Mines Using Artificial Vision: A Case Study of the Screening Unit" Mining 3, no. 4: 645-658. https://doi.org/10.3390/mining3040035
APA StyleEl Hiouile, L., Errami, A., & Azami, N. (2023). Toward Automatic Monitoring for Anomaly Detection in Open-Pit Phosphate Mines Using Artificial Vision: A Case Study of the Screening Unit. Mining, 3(4), 645-658. https://doi.org/10.3390/mining3040035






