Cybersecurity Transformation: Cyber-Resilient IT Project Management Framework
Abstract
1. Introduction
1.1. Organization
1.2. Overview of IT Project Life Cycle
1.3. IT Project Risk Management
1.4. Risk Management, Cybersecurity, Governance, and Project Management Frameworks
1.5. Contributions
1.6. Framework Evaluation Criteria
2. Related Work
3. Cyber-Resilient IT Project Management Framework
3.1. The Generic IT Project Life Cycle
3.1.1. Start the Project
3.1.2. Plan the Project
3.1.3. Execute the Plan
3.1.4. Finish the Project
3.2. The Cybersecurity Risk Management Process: An Overview
- Project Cybersecurity-based Governance: To guide the project and cybersecurity decisions
- Project Threat Modeling (PTM): To evaluate the IT design in terms of threats
- Project Asset Identification and Categorization: To do asset valuation
- Project Risk Assessment: To identify risk and set criticality priorities
- Project Risk Strategy: To decide about the best defense
- Project Security Controls Selection: To select security controls
- Project Risk Monitor: To continuously monitor systems and controls
- Project Risk Response: To act against incidents
- Project Risk Recovery and Evaluation: To restore normal operation and learn lessons
3.3. The Mapping Between IT Project Management and Cybersecurity Risk Management
3.4. The Cybersecurity Risk Management Process: Detailed Steps
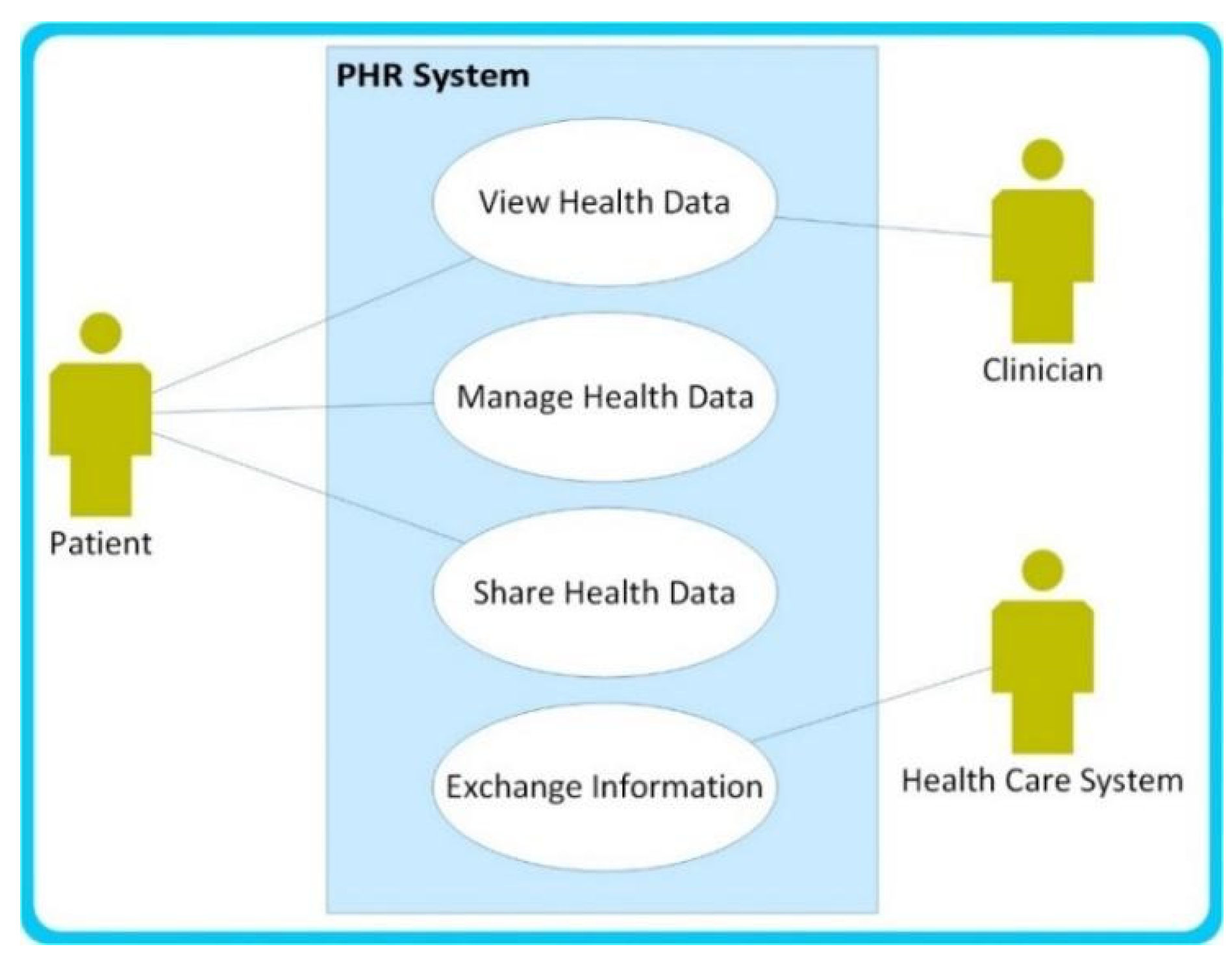
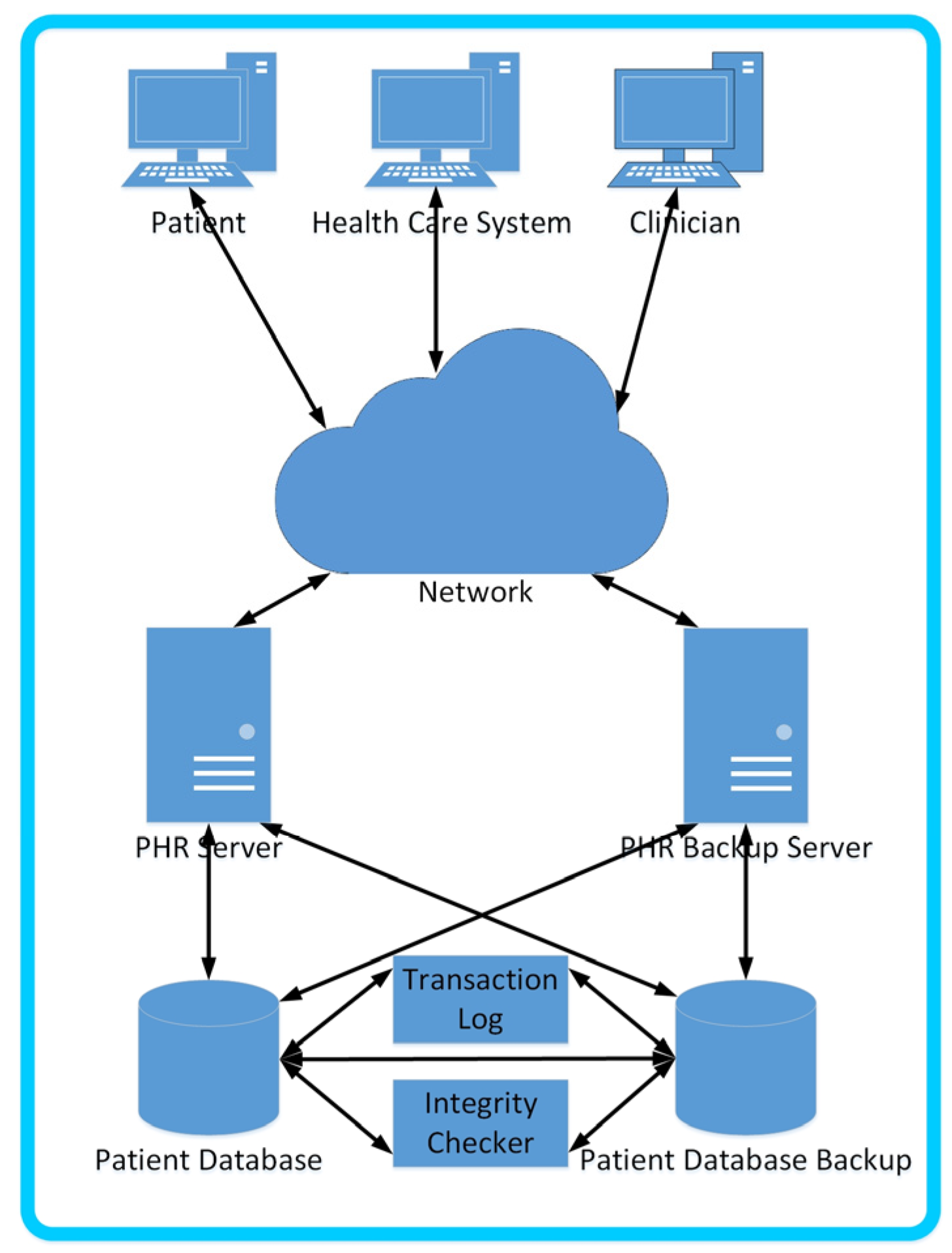
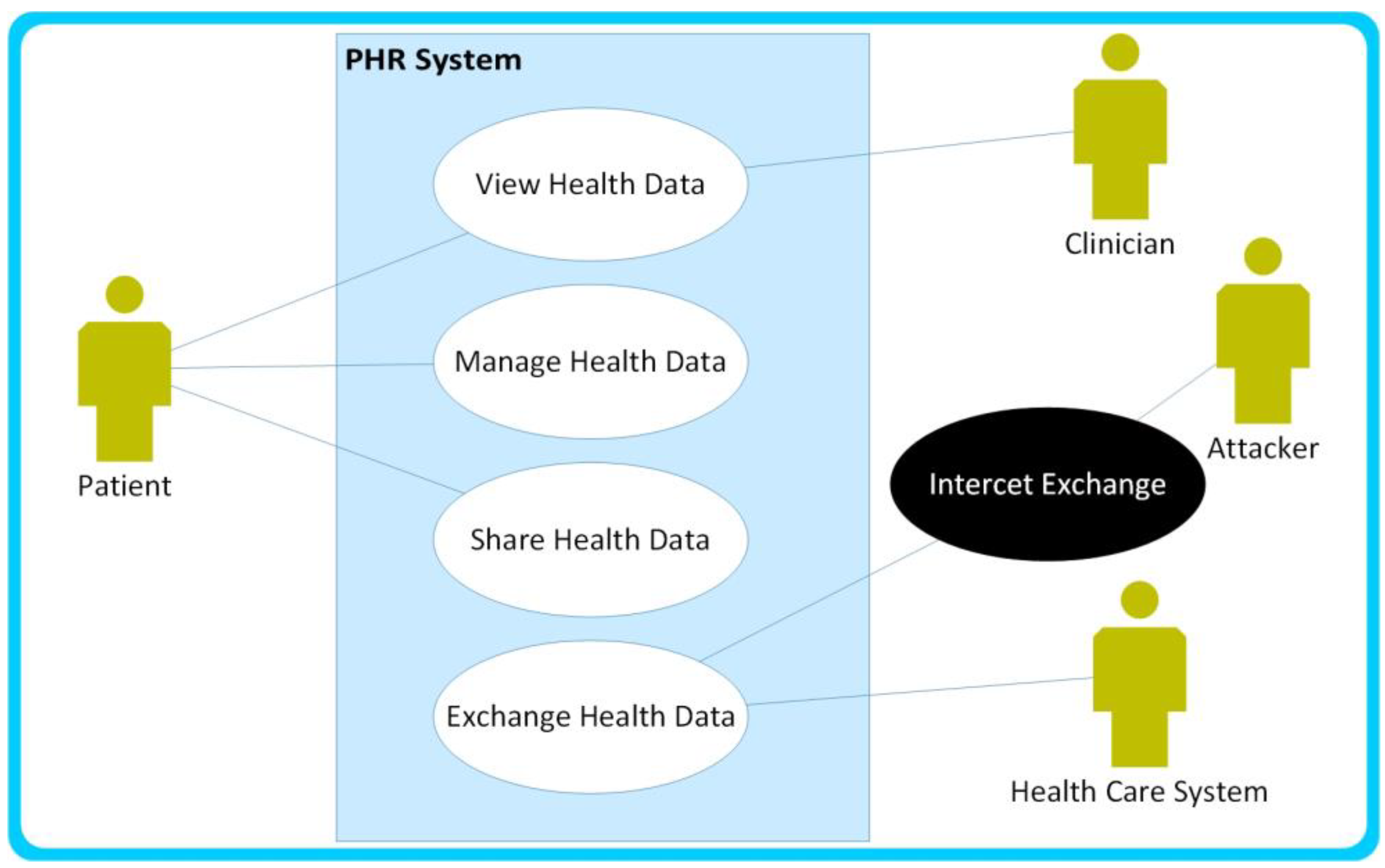
4. Case Study
- To enable patients to access, share, and manage their health data
- To enable clinicians to access the shared patients’ health data
- To enable patients to exchange health information with healthcare systems
- Business Case Document: One main purpose of this document is the analysis of the risks of several alternatives for achieving business value. Therefore, the following steps are added:
- (A)
- Project Threat Modeling
- (B)
- Project Asset Identification and Categorization
- 2.
- Project Charter Document: One main purpose of this document is the identification of the project’s governance structure and the risks. Therefore, the following step is added:
- (C)
- Project Cybersecurity-based Governance
- (A)
- Project Risk Assessment
- (B)
- Project Risk Strategy
- (C)
- Project Cybersecurity-based Governance
- Develop the IT System.Secure systems development of the PHR system includes the following:
- (1)
- Functional requirements specifications, including security functional requirements that describe the features that provide security protection against attacks and failures.
- (2)
- Non-functional requirements specifications, including non-functional security requirements that include the features that provide availability, confidentiality, safety, integrity, resilience, and reliability.
- (1)
- Secure software design that includes the following:
- Design of software architecture that can protect the assets and minimize the effect of the attacks.
- Implement secure system design guidelines that may include the following:
- -
- Defense in depth which avoids a single point of failure through layering or using multiple controls.
- -
- How to respond to and handle failures and what to choose between fail-safe, fail-fail-secure, fail-open, or fail-closed. In the case of the PHR system, the choice is fail-secure to protect the assets.
- -
- Logging user and system events.
- -
- System input validation.
- -
- Use of the need-to-know principle to ensure users or subjects should only have access to the information that they need for their work tasks.
- -
- Use of the least privilege principle to ensure that every user or subject operates using the least set of privileges necessary to perform the work.
- -
- The balance between security, functionality, and usability.
- -
- Authentication and session management.
- (2)
- Use of secure systems coding principles.
- (3)
- Testing the software, including security testing.
- 2.
- Part of execute the project phase is the implementation of project responses. Therefore, the following steps are added:
- (A)
- Project Security Controls Selection
- (B)
- Project Cybersecurity-based Governance
- Deploy IT Product or Service: Deploying an IT product or service focuses on releasing or installing the system that was developed. Releasing the system can take more than one approach such as direct cutover, phased, and parallel each with advantages and disadvantages. For example, the phased approach is less risky, but it may take longer time than the cutover. Whatever approach is taken, cybersecurity must be taken into consideration.
- Manage System Maintenance: Part of finishing the project is managing system maintenance. After a system becomes operational, maintenance management deals with maintaining the system using various processes and methodologies such as configuration management, maintenance release, version control, and security. Monitoring, response, and evaluation will be there even after the system is released. Therefore, the following steps are added:
- (A)
- Project Risk Monitor
- (B)
- Project Risk Response
- (C)
- Project Risk Recovery and Evaluation
- (D)
- Project Cybersecurity-based Governance
5. Discussion
6. Applications of the Framework
6.1. Integration into Existing Organizational Processes
- Risk-Based Approach: From the initiation of the project, CYBITJET emphasizes identifying cybersecurity risks early and continuously addressing them throughout the life cycle. Organizations can use the framework to prioritize risks based on their impact on business objectives.
- Governance and Stakeholder Engagement: The framework encourages strong governance by involving all relevant stakeholders, including project managers, cybersecurity teams, and business executives. This ensures alignment between project goals and the organization’s security objectives, making the adoption of cybersecurity measures a collective responsibility.
6.2. Practical Implementation of the Framework
- Customized Threat Modeling: Based on the organization’s specific industry and project, the framework can be adapted to perform threat modeling early in the project to identify vulnerabilities unique to the organization. For example, in a healthcare project, as shown in our case study, the system architecture and patient data security were assessed using threat modeling tailored to healthcare-specific risks.
- Risk Assessment and Mitigation Strategies: Organizations can adopt the risk assessment and mitigation strategies outlined in the framework. By conducting both qualitative and quantitative risk analyses, the framework helps organizations develop comprehensive responses, whether through risk avoidance, mitigation, or acceptance, tailored to the unique needs of each project.
6.3. Adaptability Across Various IT Project Types
- Small Projects: For projects with limited scope, the framework allows for a simplified application, focusing on critical security aspects such as data protection and access control.
- Complex Projects: For larger projects, such as those involving cloud deployments or cross-organizational systems, the framework’s continuous risk monitoring and governance integration ensure that cybersecurity is an ongoing priority throughout the project’s life cycle.
6.4. Practical Benefits for Organizations
- Enhanced Cybersecurity Posture: The integration of cybersecurity into each phase of project management ensures that security is not an afterthought but an integral part of the project’s development and execution.
- Compliance with Industry Standards: Organizations can ensure compliance with key industry standards, such as ISO/IEC 27001, NIST, and COBIT, as the framework maps directly to these standards, facilitating easier integration and audit preparation.
- Improved Project Success Rate: By addressing cybersecurity risks proactively, organizations reduce the likelihood of project failure due to security breaches or other cybersecurity-related incidents.
6.5. Framework Adaptation for Organizational Needs
- Organizations with High Regulatory Requirements: For industries such as healthcare and finance, where regulatory compliance is critical, the framework provides a structured approach to ensuring that data privacy and security are maintained throughout the project life cycle.
- Agile Development Environments: CYBITJET can also be adapted to agile methodologies, allowing for iterative security assessments and integrations, ensuring that each iteration of the project is reviewed for security risks.
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Admass, W.S.; Munaye, Y.Y.; Diro, A.A. Cyber security: State of the art, challenges and future directions. Cyber Secur. Appl. 2024, 2, 100031. [Google Scholar] [CrossRef]
- Gartner Inc. Gartner Forecasts Worldwide IT Spending to Grow 4.3% in 2023. Available online: https://www.gartner.com/en/newsroom/press-releases/2023-07-19-gartner-forecasts-worldwide-it-spending-to-grow-4-percent-in-2023 (accessed on 20 August 2023).
- Gartner Inc. Gartner Top 10 Strategic Technology Trends for 2023. Available online: https://www.gartner.com/en/articles/gartner-top-10-strategic-technology-trends-for-2023 (accessed on 21 August 2023).
- McManus, J.; Wood-Harper, T. A Study in Project Failure. Available online: https://www.bcs.org/articles-opinion-and-research/a-study-in-project-failure (accessed on 25 July 2023).
- CHAOS Manifesto. Think Big, Act Small. The Standish Group International Inc. Available online: https://www.standishgroup.com/sample_research_files/CM2013.pdf (accessed on 20 July 2023).
- Project Management Institute. The Standard for Project Management and a Guide to the Project Management Body of Knowledge (PMBOK Guide); Project Management Institute Inc.: Newtown Square, PA, USA, 2021. [Google Scholar]
- Al-Janabi, S.; Janicki, R. Data Repair of Density-based Data Cleaning Approach Using Conditional Functional Dependencies. Data Technol. Appl. 2022, 56, 429–446. [Google Scholar] [CrossRef]
- Razmak, J.; Al-Janabi, S.; Kharbat, F.; Bélanger, C. Lean Database: An Interdisciplinary Perspective Combining Lean Thinking and Technology. Int. Arab. J. Inf. Technol. 2021, 18, 25–35. [Google Scholar] [CrossRef] [PubMed]
- Rekatsinas, T.; Chu, X.; Ilyas, I.F.; Re, C. Holoclean: Holistic data repairs with probabilistic inference. VLDB Endow. 2017, 10, 1190–1201. [Google Scholar] [CrossRef]
- InfoSecurity. Cybercrime Costs World Economy over 1% of Global GDP. Available online: https://www.infosecurity-magazine.com/news/cybercrime-costs-1trillion (accessed on 19 August 2023).
- Aboud, S.J.; AL-Fayoumi, M.A.; Al-Fayoumi, M.; Jabbar, H.S. An Efficient RSA Public Key Encryption Scheme; Fifth International Conference on Information Technology: Las Vegas, NV, USA, 2008; pp. 127–130. [Google Scholar]
- Verizon Communications Inc. 2023 Data Breach Investigations Report. Available online: https://www.verizon.com/business/resources/reports/dbir/ (accessed on 20 August 2023).
- Syms, F.; Smith, D. Cybersecurity in Canada: Operations, Investigations, and Protection; Emond Publishing: Toronto, ON, Canada, 2023. [Google Scholar]
- Schwalbe, K. Information Technology Project Management; Cengage Learning Inc.: Boston, MA, USA, 2018. [Google Scholar]
- Sommerville, I. Software Engineering; Pearson Education Limited: New York, NY, USA, 2016. [Google Scholar]
- NIST CSF. Framework for Improving Critical Infrastructure Cybersecurity. Available online: https://www.nist.gov/cyberframework (accessed on 31 August 2023).
- ISACA. COBIT 2019 Framework: Governance and Management Objectives; ISACA: Schaumburg, IL, USA, 2018. [Google Scholar]
- ISO/IEC 27000: 2018; Information Technology-Security Techniques-Information Security Management Systems-Overview and Vocabulary. International Organization for Standardization/International Electrotechnical Commission: Geneva, Switzerland, 2018.
- Project Management Institute. A Guide to the Project Management Body of Knowledge (PMBOK Guide); Project Management Institute Inc.: Newtown Square, PA, USA, 2017. [Google Scholar]
- NIST RMF. Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy. Available online: https://csrc.nist.gov/pubs/sp/800/37/r2/final (accessed on 31 August 2023).
- SDL. Microsoft Security Development Lifecycle (SDL). Available online: https://learn.microsoft.com/en-us/compliance/assurance/assurance-microsoft-security-development-lifecycle (accessed on 3 September 2023).
- NIST SSDF. Secure Software Development Framework (SSDF) Version 1.1: Recommendations for Mitigating the Risk of Software Vulnerabilities. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-218.pdf (accessed on 15 September 2023).
- ISO 31000:2018; Risk Management-Guidelines. International Organization for Standardization: Geneva, Switzerland, 2018.
- Shakatreh, M.; Rumman, A.; Mugableh, I. Reviewing the Framework of Risk Management: Policy and Hedging. Int. J. Prof. Bus. Rev. 2023, 8, 1–20. [Google Scholar] [CrossRef]
- Zwikael, O.; Ahn, M. The Effectiveness of Risk Management: An Analysis of Project Risk Planning Across Industries and Countries. Risk Anal. 2011, 31, 25–37. [Google Scholar] [CrossRef]
- Mishra, B.K.; Rolland, E.; Satpathy, A.; Moore, M. A framework for enterprise risk identification and management: The resource-based view. Manag. Audit. J. 2019, 34, 162–188. [Google Scholar] [CrossRef]
- Oluomachi, E.; Ahmed, A.; Ahmed, W.; Samson, E. Assessing The Effectiveness of Current Cybersecurity Regulations and Policies in the US. Int. J. Sci. Res. Publ. 2024, 14, 78–85. [Google Scholar] [CrossRef]
- Chauhan, M.; Shiaeles, S. An Analysis of Cloud Security Frameworks, Problems, and Proposed Solutions. Network 2023, 3, 422–450. [Google Scholar] [CrossRef]
- Aversano, L.; Grasso, C.; Tortorella, M. A Literature Review of Business/IT Alignment Strategies. Procedia Technol. 2012, 5, 462–474. [Google Scholar] [CrossRef][Green Version]
- Njanka, S.; Sandula, G.; Colomo-Palacios, R. IT-Business Alignment: A Systematic Literature Review. Procedia Comput. Sci. 2021, 181, 333–340. [Google Scholar] [CrossRef]
- Gilbert, A.; Waal, B.; Smit, J. Business and IT Alignment; Answers and Remaining Questions; Pacific Asia Conference on Information Systems: Ho Chi Minh, Vietnam, 2009. [Google Scholar]
- Daud, M.; Rasiah, R.; George, M.; Asirvatham, D.; Thangiah, G. Bridging the Gap between Organisational Practices and Cyber Security Compliance: Can Cooperation Promote Compliance in Organisations? Int. J. Bus. Soc. 2018, 19, 161–180. [Google Scholar]
- Abrahams, T.; Farayola, O.; Amoo, O.; Ayinla, B.; Osasona, F.; Atadoga, A. Continuous improvement in information security: A review of lessons from superannuation cybersecurity uplift programs. Int. J. Sci. Res. Arch. 2024, 11, 1327–1337. [Google Scholar] [CrossRef]
- Chaudhary, S.; Vasileios, G.; Sokratis, K. Developing metrics to assess the effectiveness of cybersecurity awareness program. J. Cybersecur. 2022, 8, tyac006. [Google Scholar] [CrossRef]
- Kure, H.; Islam, S.; Mouratidis, H. An integrated cyber security risk management framework and risk predication for the critical infrastructure protection. Neural Comput. Appl. 2022, 34, 15241–15271. [Google Scholar] [CrossRef]
- Durst, S.; Hinteregger, C.; Zieba, M. The Effect of Environmental Turbulence on Cyber Security Risk Management and Organizational Resilience. Comput. Secur. 2024, 137, 103591. [Google Scholar] [CrossRef]
- Oueslati, H.; Rahman, M.; Othmane, L. Literature Review of the Challenges of Developing Secure Software Using the Agile Approach. In Proceedings of the 2015 10th International Conference on Availability, Reliability and Security, Toulouse, France, 24–28 August 2015; pp. 540–547. [Google Scholar]
- Salin, H.; Lundgren, M. Towards Agile Cybersecurity Risk Management for Autonomous Software Engineering Teams. J. Cybersecur. Priv. 2022, 2, 276–291. [Google Scholar] [CrossRef]
- Lee, I. Cybersecurity: Risk management framework and investment cost analysis. Bus. Horiz. 2021, 64, 659–671. [Google Scholar] [CrossRef]
- Nikolaenko, V.; Sidorov, A. Analysis of 105 IT Project Risks. J. Risk Financ. Manag. 2023, 16, 33. [Google Scholar] [CrossRef]
- Nikolaenko, V.; Sidorov, A. Assessing the Maturity Level of Risk Management in IT Projects. Sustainability 2023, 15, 12752. [Google Scholar] [CrossRef]
- Ganin, A.; Quach, P.; Panwar, M.; Collier, Z.; Keisler, J.; Marchese, D.; Linkov, I. Multicriteria Decision Framework for Cybersecurity Risk Assessment and Management. Risk Anal. 2020, 40, 183–199. [Google Scholar] [CrossRef] [PubMed]
- Bialas, A. Risk Management in Critical Infrastructure—Foundation for Its Sustainable Work. Sustainability 2016, 8, 240. [Google Scholar] [CrossRef]
- Aboud, S.J.; Alnuaimi, M.; Jabbar, H.S. Efficient Password Scheme Without Trusted Server. Int. J. Aviat. Technol. Eng. Manag. (IJATEM) 2011, 1, 52–57. [Google Scholar] [CrossRef]
- Cherdantseva, Y.; Burnap, P.; Blyth, A.; Eden, P.; Jones, K.; Soulsby, H.; Stoddart, K. A review of cyber security risk assessment methods for SCADA systems. Comput. Secur. 2016, 56, 1–27. [Google Scholar] [CrossRef]
- Pitropakis, N.; Panaousis, E.; Giannakoulias, A.; Kalpakis, G.; Rodriguez, R.; Sarigiannidis, P. An Enhanced Cyber Attack Attribution Framework. In Trust, Privacy and Security in Digital Business, Proceedings of the 15th International Conference, TrustBus 2018, Regensburg, Germany, 5–6 September 2018; Springer International Publishing: New York, NY, USA; pp. 213–228.
- Mayer, N.; Aubert, J. A Risk Management Framework for Security and Integrity of Networks and Services. J. Risk Res. 2021, 24, 987–998. [Google Scholar] [CrossRef]
- Kure, H.; Islam, S. Assets Focus Risk Management Framework for Critical Infrastructure Cybersecurity Risk Management. IET Cyber-Phys. Syst. Theory Appl. 2019, 4, 332–340. [Google Scholar] [CrossRef]
- NIST Special Publication 800-39. Managing Information Security Risk: Organization, Mission, and Information System View. Available online: https://csrc.nist.gov/pubs/sp/800/39/final (accessed on 2 September 2023).
- SAMM. Software Assurance Maturity Model. Available online: https://owasp.org/www-project-samm/ (accessed on 15 September 2023).
- STRIDE. Microsoft Threat Modeling Tool Threats—STRIDE Model. Available online: https://learn.microsoft.com/en-us/azure/security/develop/threat-modeling-tool-threats#stride-model (accessed on 14 September 2023).
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection-Information Security Management Systems—Requirements. International Organization for Standardization/International Electrotechnical Commission: Geneva, Switzerland, 2022.



| Framework/Standard | Focus |
|---|---|
| NIST CSF [16] | It is designed for critical infrastructure and commercial organizations. It consists of six functions that could improve existing cybersecurity practices or be used as a starting point for developing cybersecurity risk management. |
| COBIT 2019 [17] | Created for the governance and management of enterprise information and technology. It addresses many IT-related disciplines such as security, governance, and management. It connects IT with business objectives. |
| ISO/IEC 27000:2018 [18] | Describes the requirements for an information security management system and provides a framework to establish, implement, maintain, and continually improve the information security management system and secure assets. |
| PMBOK Guide [19] | Defines components of the project such as project management knowledge areas (e.g., project risk management and project time management), project management processes, project phases, and project life cycle. |
| NIST RMF [20] | It is a risk management process to identify and respond to cybersecurity threats. It consists of six cyclical steps plus a preparatory step. It establishes mandatory security and privacy requirements for federal agencies. |
| Microsoft SDL [21] | Microsoft’s security development lifecycle focuses on the development of secure software to build security in every phase of software development. It consists of seven phases that address the development while addressing the security. |
| NIST SSDF [22] | A secure software development framework describes high-level practices based on established standards, guidance, and secure software development practice documents. |
| ISO 31000 [23] | Set of standards that relate to risk management to help organizations develop risk management strategies that integrate risk management into the activities and functions of the organization. |
| Factor | Evaluation Criterion |
|---|---|
| Risk-based approach | How the proposed framework addresses the cybersecurity-related risks in IT project management |
| Comprehensiveness | How the proposed framework covers various aspects of cybersecurity governance in IT project management |
| Alignment with business objectives | How the proposed framework aligns IT project management with business objectives |
| Integration with industry standards | How the proposed framework integrates easily with recognized standards in IT project management |
| Continuous improvement | Whether the proposed framework supports continuous improvement over time in IT project management |
| Work | Limitations |
|---|---|
| [16,20,50] | They focus on managing security risks, but they lack the effective integration of cybersecurity into the fabric of IT project management. |
| [21,22] | They focus on developing secure codes only without a holistic approach to how to manage IT projects and harmonizing cybersecurity risk management with the IT project management life cycle. |
| [51] | STRIDE focuses on threat modeling. |
| [17,18,23] | There is no clear direct connection between their steps in terms of cybersecurity and IT project management. |
| [19] | Although it acknowledges the significance of project management, it does not focus on the cybersecurity of IT products during the project management life cycle. |
| [35,36,37,38,39] | They do not address IT project management explicitly. |
| [40,41] | Both works do not elaborate in detail on the cybersecurity risks and how to mitigate them. |
| [42,43,45,46,47,48] | They are mainly about cybersecurity or how to protect the infrastructure, but there is a notable gap in the seamless integration of these elements into IT project risk management. |
| Cybersecurity Risk Management Activities | IT Project Phases | Start the Project | Plan the Project | Execute the Plan | Finish the Project |
|---|---|---|---|---|---|
| - Project Cybersecurity-based Governance | - Project Threat Modeling - Project Asset Identification and Categorization | - Business Case - Project Charter | |||
| - Project Risk Assessment - Project Risk Strategy | - Plan Project Risk - Plan Project Scope - Plan Project Schedule - Plan Project Budget - Plan Project Quality - Plan Project Communications - Plan Project Resources | ||||
| - Project Security Controls Selection | - Implement Project Response - Develop Secure IT System - Manage Project Scope - Manage Project Schedule - Manage Project Budget - Manage Project Quality - Manage Project Communications - Manage Project Resources | ||||
| - Project Risk Monitor - Project Risk Response - Project Risk Recovery and Evaluation | - Deploy IT Product or Service - Manage System Maintenance - Close the Project - Evaluate the Project |
| Factors | Evaluation Criteria | Indicators | Examples |
|---|---|---|---|
| Risk-based approach | How the proposed framework addresses the cybersecurity-related risks in IT project management | As demonstrated in the case study, from the early phases of the project, CYBITJET focuses on the identification and prioritization of cybersecurity risks to help organizations allocate and manage resources efficiently, which mitigates the most critical cybersecurity risks first. Furthermore, CYBITJET provides flexibility in managing risks because the order of the steps of the cybersecurity risk management process does not necessarily mean the sequence of implementation. | It is up to the organization to perform the project threat modeling, project asset identification, and categorization or alternate between them as each way has its capabilities. Furthermore, CYBITJET provides capabilities to select risk strategies and controls, secure development, and monitoring that help to prioritize and take actions in IT project development based on the risk level posed to the project or product. |
| Comprehensiveness | How the proposed framework covers various aspects of cybersecurity governance in IT project management | CYBITJET integrates cybersecurity governance and IT project management where risk management is part of IT project management, to ensure that risk management is an integral part of decision-making and governance. The outcomes of the project cybersecurity-based governance step inform, direct, establish, and monitor how the other steps achieve their outcomes. | As shown in the case study, depending on the governance steps, the threat modeling can be performed in the early phases of the project, and/or after the product is deployed in the maintenance phase after the project is closed to respond to the future or unpredicted threats. It provides a structured process that covers all aspects of risk management. |
| Alignment with business objectives | How the proposed framework aligns IT project management with business objectives | CYBITJET is process-oriented, focusing on cybersecurity risk management throughout the IT project management. As shown in the case study, CYBITJET can align with the organization’s strategic goals and objectives. | The PRRS06: Rejection is not selected as a risk response strategy for the PHR system because it is not a valid due care and due diligence response to risk, as per the strategy, goals, mission, and objectives of the organization, that are determined in the project cybersecurity-based governance steps. |
| Integration with industry standards | How the proposed framework integrates easily with recognized standards in IT project management | As demonstrated in the case study, CYBITJET steps can be integrated with different industry standards such as ISO/IEC 27001:2013 and COBIT 2019. | The PSCS01: Preventive controls can be implemented using ISO/IEC 27001:2013: A.9.2.3. This shows its interoperability and compatibility such that any organization that is already adhering to these standards can integrate CYBITJET into their existing cybersecurity programs across different aspects of their operations. |
| Continuous improvement | Whether the proposed framework supports continuous improvement over time in IT project management | CYBITJET promotes continuous improvement that helps organizations evolve cybersecurity capabilities in response to changing business requirements and threats. | As shown in the case study in the monitoring and recovery activity of the cybersecurity risk management process, the product or the result of the generic IT project life cycle would still be monitored and logged even after release and until it is decommissioned. Also, updating the plans based on the lessons learned allows organizations to detect and respond to emerging threats and vulnerabilities in a timely manner. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Janabi, S.; Jabbar, H.; Syms, F. Cybersecurity Transformation: Cyber-Resilient IT Project Management Framework. Digital 2024, 4, 866-897. https://doi.org/10.3390/digital4040043
Al-Janabi S, Jabbar H, Syms F. Cybersecurity Transformation: Cyber-Resilient IT Project Management Framework. Digital. 2024; 4(4):866-897. https://doi.org/10.3390/digital4040043
Chicago/Turabian StyleAl-Janabi, Samir, Haidar Jabbar, and Francis Syms. 2024. "Cybersecurity Transformation: Cyber-Resilient IT Project Management Framework" Digital 4, no. 4: 866-897. https://doi.org/10.3390/digital4040043
APA StyleAl-Janabi, S., Jabbar, H., & Syms, F. (2024). Cybersecurity Transformation: Cyber-Resilient IT Project Management Framework. Digital, 4(4), 866-897. https://doi.org/10.3390/digital4040043





