Double-Layered Authentication Door-Lock System Utilizing Hybrid RFID-PIN Technology for Enhanced Security †
Abstract
1. Introduction
- Manual door-locks employ keys that are often difficult to insert/remove from the lock;
- Manual doors sometimes have misaligned door latches;
- Automated, battery-operated doors face failures due to power discharge;
- Some automated door-locks either become stuck or cease to function in scenarios of system glitches;
- Electronic doors can be breached by unauthorized personnel;
- Conventional automated doors employ GSM, resulting in a lack of cost effectiveness;
- Locks based solely on passwords do not provide adequate security.
2. The Literature Survey
2.1. Applications of RFID
2.1.1. Digital Applications
2.1.2. RFID Tags
2.1.3. Wearable Applications
2.1.4. Other Applications
2.2. RFID-Based Lock Systems
2.3. Pin/Password-Based Lock Systems
3. The Proposed Technology
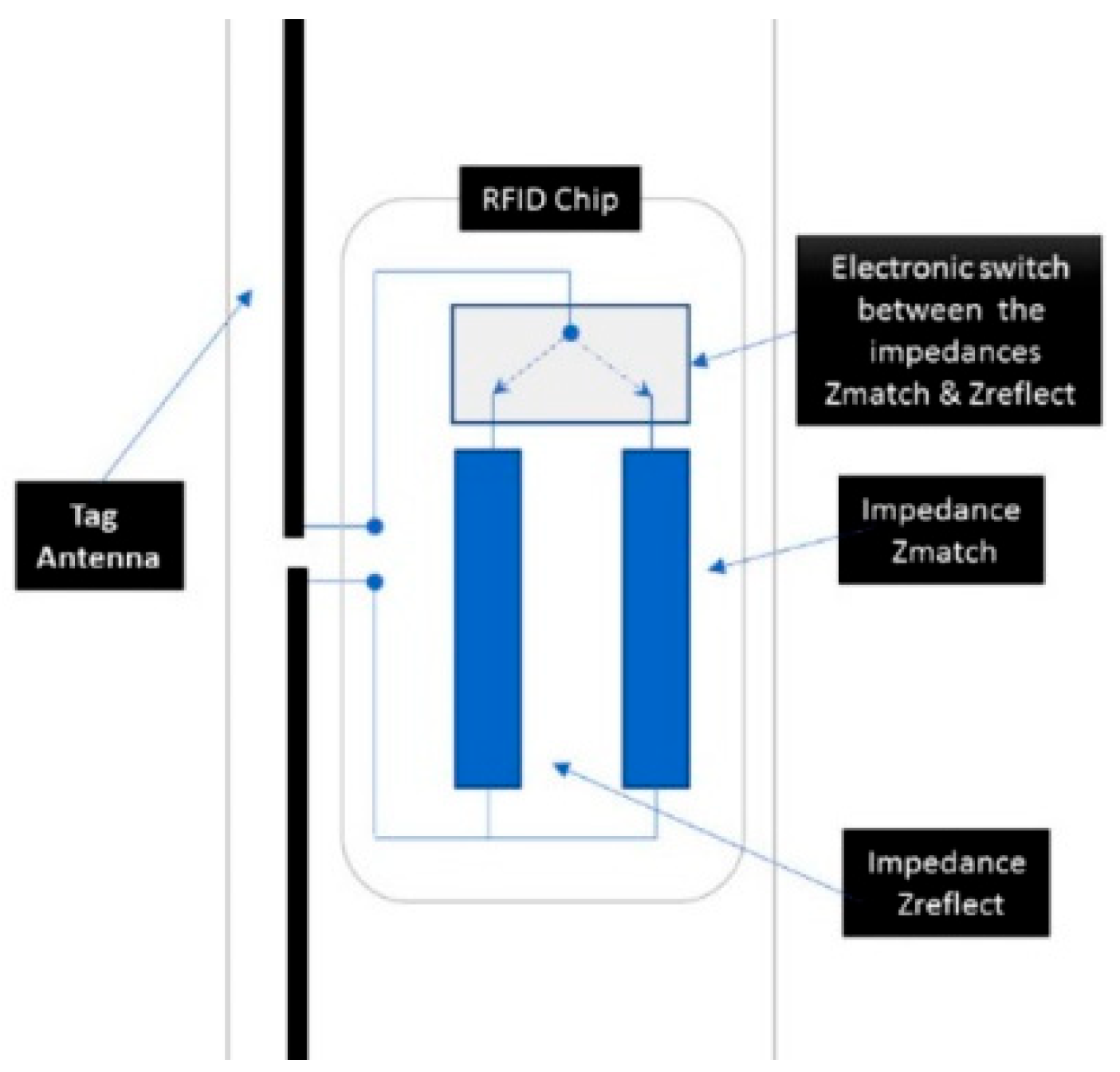
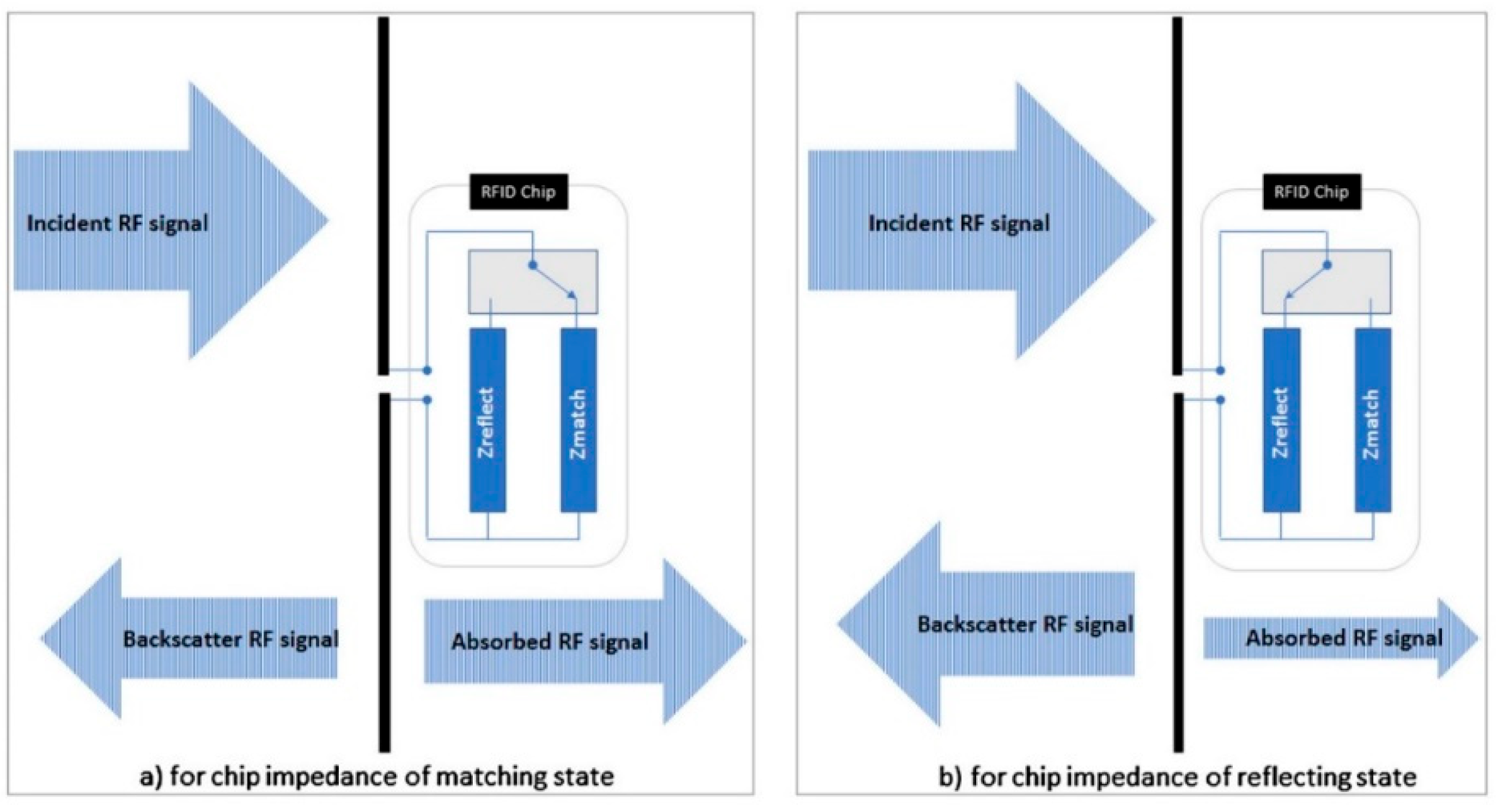
3.1. RFID Technology
3.2. RFID Interfacing with the SPI Bus Protocol
3.3. The Hybrid Security System: RFID- and Keypad-Based
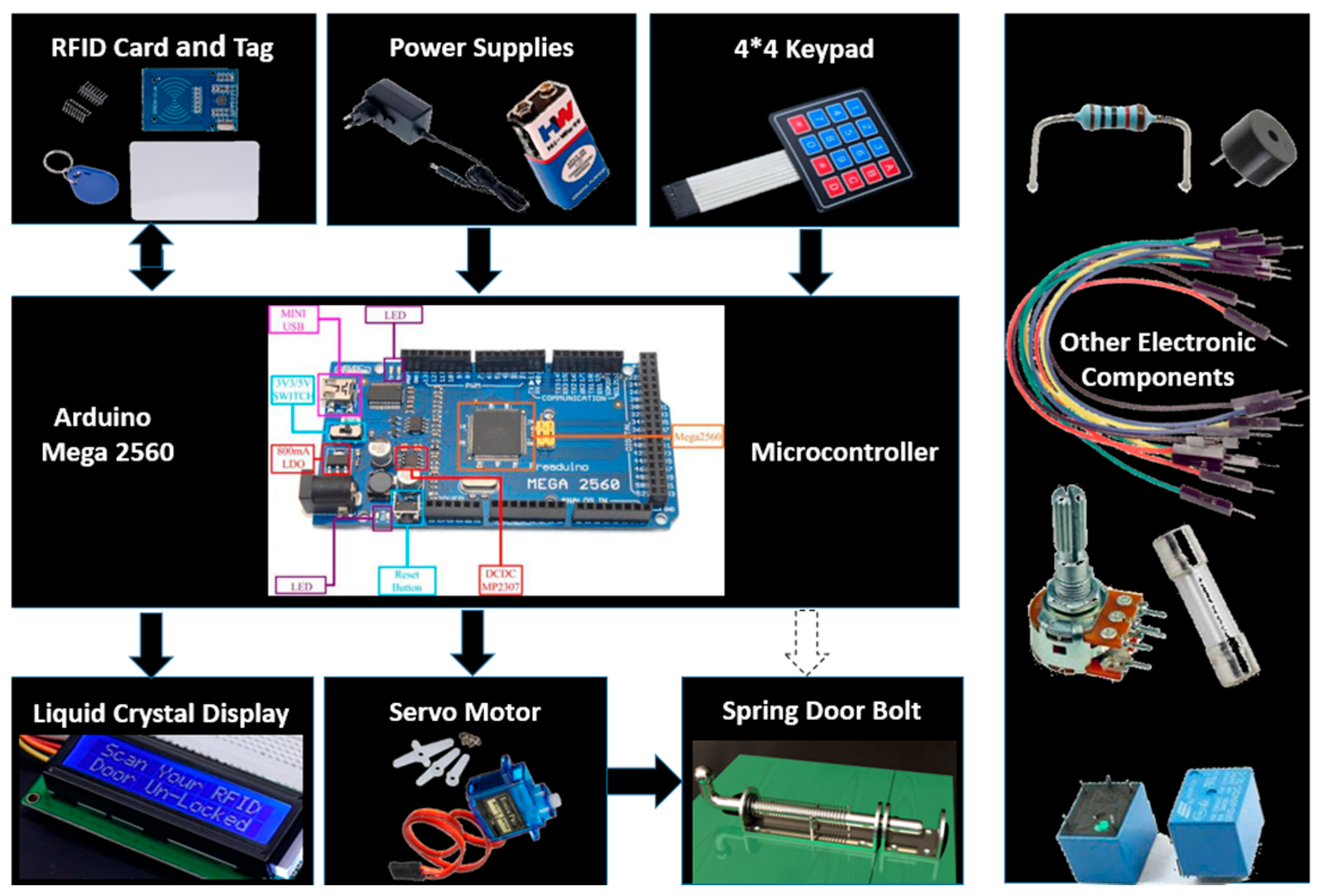
3.3.1. Components of the System
- The RFID Reader: This device reads the RFID tags or cards that authorized personnel possess. Each RFID tag contains a unique identifier, and when presented to the reader, it communicates this identifier to the system.
- The PIN Keypad: The PIN keypad allows authorized individuals to input their personal identification number. The PIN adds an additional layer of security to the system.
- The Control Unit: The control unit is the brain of the system. It processes inputs from the RFID reader and the PIN keypad, validates them and then decides whether to grant access or not.
- The Lock Mechanism: The lock mechanism controls physical access to the location. It is electronically controlled by the control unit, which triggers the lock to open or remain closed based on the authentication outcome.
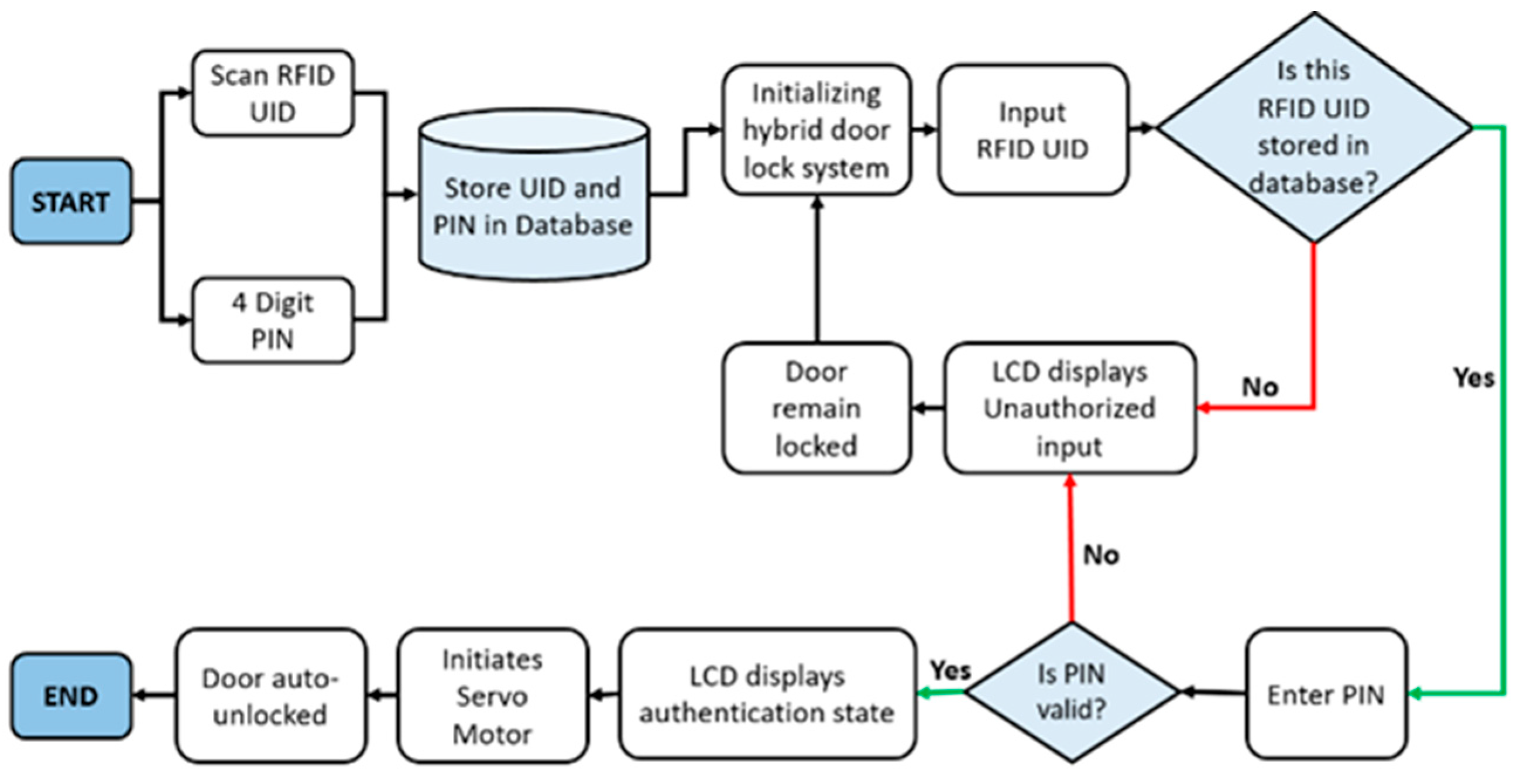
3.3.2. The Authentication Process
- Initial Request: An individual approaches the door and initiates the authentication process.
- RFID Authentication: The individual puts forth their solution of using an RFID card or tag with the RFID reader. The reader communicates the PIN to the control unit.
- PIN Authentication: After successful RFID authentication, the system prompts the individual to enter their PIN on the keypad.
- Dual Authentication: The control unit compares the RFID identifier with the authorized database and checks whether the entered PIN matches the authorized individual’s PIN.
- Access Decision: If both the RFID and PIN authentications are successful and match the authorized records, the control unit triggers the lock to open. If either authentication fails or both authentications fail, the lock remains secured, and access is denied.
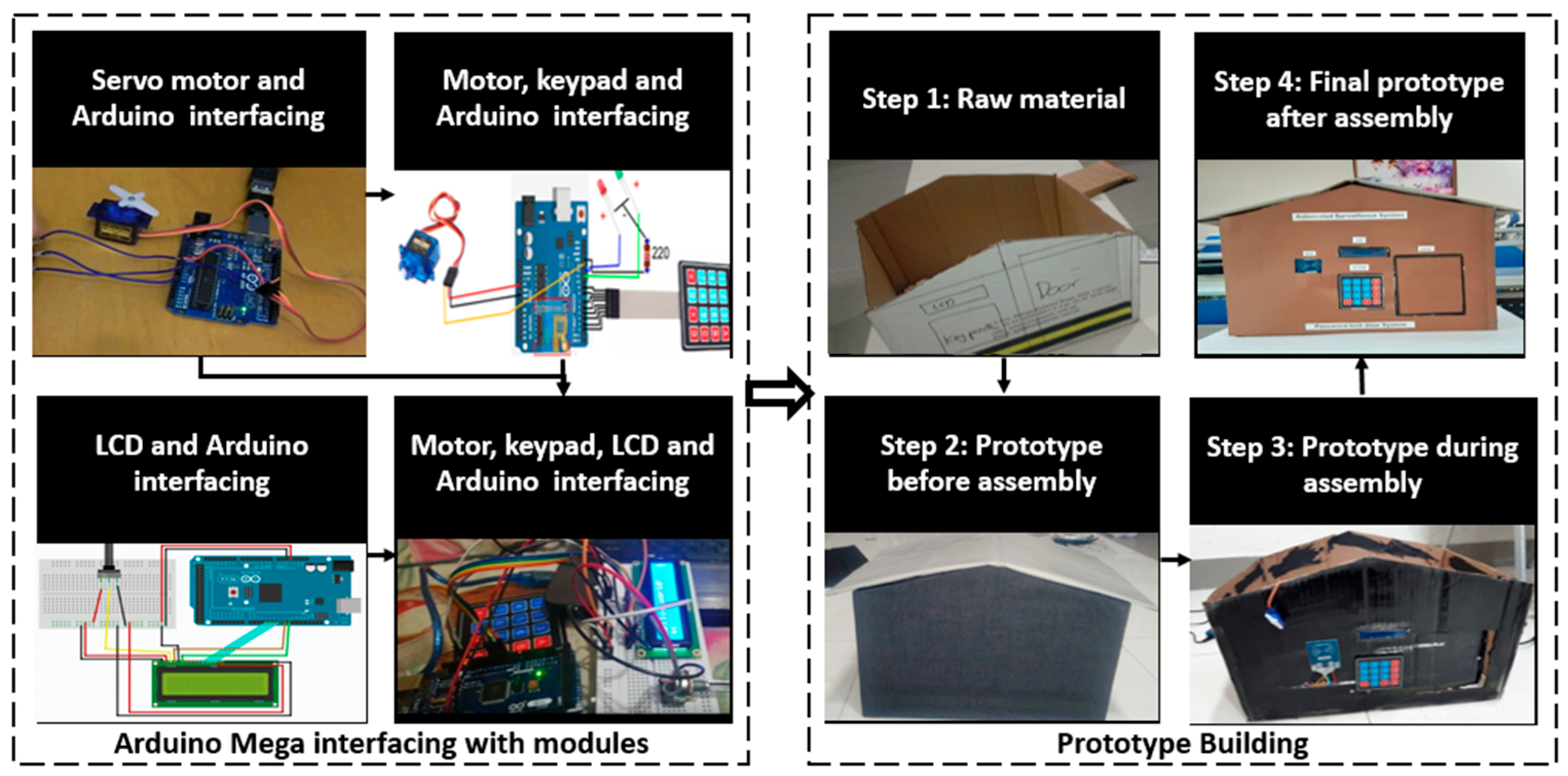
3.4. A Description of the Hardware and Electrical Components
4. Results
5. Conclusions and Discussion
- Multi-Layered Security: Combining RFID and PIN authentication creates a multi-layered defence against potential breaches, particularly for highly sensitive locations.
- Mitigating Credential Theft: By adding a PIN component, credential theft can be prevented, as an unauthorized person cannot enter without the corresponding PIN.
- The Human Factor: People can forget to lock doors, lose their access cards or even share them unintentionally. A hybrid system minimizes these risks by requiring a PIN only known to authorized individuals.
- Protection against Lost Cards: The hybrid system adds an extra layer of protection because even if a card is lost, the PIN is still required to gain entry to sensitive areas.
- Accountability and Audit Trail: The system provides a clearer audit trail of the access to the sensitive area, crucial for security investigations and compliance purposes.
- Compliance Requirements: The hybrid system can help meet compliance standards for sectors (like government and healthcare) subject to strict security regulation.
- Deterrence: The complexity of the system (since gaining unauthorized access requires both an RFID card and a PIN) reduces the likelihood of attempted breaches.
- Dynamic Access Control: A hybrid system allows for more sophisticated access control configurations in case the privileges are to be dynamically modified.
- Emergencies and Threat Scenarios: The RFID-PIN system facilitates swift changes to the access permissions in case of emergencies.
- Technology Advancements: It can adapt to emerging threats by integrating novel authentication technologies.
- Centralized Management: The system allows administrators to control/monitor access permissions effectively.
- Employee Training: The system enforces security practices better by requiring employees to input unique PINs.
6. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| RFID | Radio Frequency Identification |
| OTP | One-Time Password |
| UID | Unique Identification Number |
| LCD | Liquid Crystal Display |
| IoT | Internet of Things |
| SCM | Supply Chain Management |
| AES | Advanced Encryption Standard |
| SHA | Secure Hash Algorithm |
| SMS | Short Message Service |
| GSM | Global System for Mobile Communications |
| IC | Integrated Circuit |
| HLPSL | High-Level Protocol Specification Language |
| ECC | Elliptic Curve Cryptography |
| UHF | Ultra-High-Frequency |
| LF | Low-Frequency |
| HF | High-Frequency |
| SHF | Super High-Frequency |
| RBAC | Role-Based Access Control |
| SSB | Smart Shopping Booth |
| VM | Vending Machine |
| WAPDA | Water and Power Development Authority (Power Supply in Pakistan) |
| NoSQL | Not Only SQL (Non-Relational Database) |
| SCL | Serial Clock Line (Part of the SPI Protocol) |
| MISO | Master-In Slave-Out |
| MOSI | Master-Out Slave-In |
| SS | Slave Select |
| HDLS | Hybrid Door-Lock System |
References
- Divya, R.S.; Mathew, M. Survey on various door-lock access control mechanisms. In Proceedings of the 2017 International Conference on Circuit, Power and Computing Technologies (ICCPCT), Kollam, India, 20–21 April 2017. [Google Scholar]
- Haibi, J.A.; Yassini, K.E.; Oufaska, K. Suitcase traceability system via RFID and NoSQL database. In Proceedings of the SCA’18: 3rd International Conference on Smart City Applications, Tetouan, Morocco, 10–11 October 2018; pp. 1–6. [Google Scholar]
- Gabsi, S.; Kortli, Y.; Beroulle, V.; Kieffer, Y.; Alasiry, A.; Hamdi, B. Novel ECC-based RFID mutual authentication protocol for emerging IoT applications. IEEE Access 2021, 9, 130895–130913. [Google Scholar] [CrossRef]
- Khan, M.U.A.; Raad, R.; Foroughi, J.; Raheel, M.S.; Houshyar, S. An octagonal-shaped conductive HC12 and LIBERATOR-40 thread embroidered chipless RFID for general IoT applications. Sens. Actuators A Phys. 2021, 318, 112485. [Google Scholar] [CrossRef]
- Agarwal, A.; Mehandiratta, E.; Sanket, R.; Samkaria, R.; Gupta, T.; Singh, R.; Gehlot, A. Smart door-lock system for elderly, handicapped people living alone. Int. J. Smart Home 2016, 10, 155–162. [Google Scholar] [CrossRef]
- Haibi, A.; Oufaska, K.; El Yassini, K.; Boulmalf, M.; Bouya, M. Systematic mapping study on RFID technology. IEEE Access 2022, 10, 6363–6379. [Google Scholar] [CrossRef]
- Rouchdi, Y.; Haibi, A.; El Yassini, K.; Boulmalf, M.; Oufaska, K. A New RFID Middleware and BagTrac Application. In Proceedings of the International Conference on Advanced Intelligent Systems for Sustainable Development (AI2SD’2018), Tangier, Morocco, 12–14 July 2018; pp. 869–884. [Google Scholar]
- Haibi, A.; Oufaska, K.; El Yassini, K. Tracking Luggage System in Aerial Transport via RFID Technology. In Proceedings of the Third International Conference on Smart City Applications, Oujda, Morocco, 10–11 October 2018; pp. 289–299. [Google Scholar] [CrossRef]
- Kisic, M.; Dakic, B.; Damnjanovic, M.; Blaz, N.; Zivanov, L. Design and simulation of 13.56 MHz RFID tag in ink-jet printing technology. In Proceedings of the 36th International Spring Seminar on Electronics Technology, Alba Iulia, Romania, 8–12 May 2013. [Google Scholar]
- Good, T.; Benaissa, M. A low-frequency RFID to challenge security and privacy concerns. In Proceedings of the 2009 IEEE 6th International Conference on Mobile Adhoc and Sensor Systems, Macau, China, 12–15 October 2009. [Google Scholar]
- Haibi, A.; Bouazza, H.; Bouya, M.; El Yassini, K.; Oufaska, K.; Boulmalf, M.; Lazaro, A.; Hadjoudja, A. A new compact metal mountable dualband UHF RFID tag antenna with an adapted middleware for transport and SCM fields. Int. J. Commun. Antenna Propag. 2021, 11, 106–117. [Google Scholar]
- Turner, M.; Naber, J. The design of a bi-directional, RFID-based ASIC for interfacing with SPI bus peripherals. In Proceedings of the 2010 53rd IEEE International Midwest Symposium on Circuits and Systems, Seattle, WA, USA, 1–4 August 2010. [Google Scholar]
- Lee, C.; Ho, G.; Choy, K.L.; Pang, G. A RFID-based recursive process mining system for quality assurance in the garment industry. Int. J. Prod. Res. 2014, 52, 4216–4233. [Google Scholar] [CrossRef]
- Wang, X. Tennis robot design via Internet of Things and deep learning. IEEE Access 2021, 9, 127460–127470. [Google Scholar] [CrossRef]
- Herrojo, C.; Paredes, F.; Mata-Contreras, J.; Martín, F. Chipless-RFID: A review and recent developments. Sensors 2019, 19, 3385. [Google Scholar] [CrossRef] [PubMed]
- Ramzan, A.; Rehman, S.; Perwaiz, A. RFID technology: Beyond cash-based methods in vending machine. In Proceedings of the 2017 2nd International Conference on Control and Robotics Engineering (ICCRE), Bangkok, Thailand, 1–3 April 2017. [Google Scholar]
- Lodhi, E.; Fenghua, Z.; Lodhi, Z.; Saleem, Q.; Xiong, G.; Wang, F. Design and Implementation of RFID based Smart Shopping Booth. In Proceedings of the 2019 6th International Conference on Information Science and Control Engineering (ICISCE), Shanghai, China, 20–22 December 2019. [Google Scholar]
- Ahtsham, M.; Yan, H.Y.; Ali, U. IoT based door-lock surveillance system using cryptographic algorithms. In Proceedings of the 2019 IEEE 16th International Conference on Networking, Sensing and Control (ICNSC), Banff, AB, Canada, 9–11 May 2019. [Google Scholar]
- Orji, E.Z.; Nduanya, U.I.; Oleka, C.V. Microcontroller Based Digital Door-lock Security System Using Keypad. Int. J. Latest Technol. Eng. Manag. Appl. Sci. 2019, 8, 92–97. [Google Scholar]
- Prabhakar, A.; Oza, S.; Shrivastava, N.; Srivastava, P.; Wadhwa, G. Password Based Door-lock System. Int. Res. J. Eng. Technol. 2019, 6, 1154–1157. [Google Scholar]
- Baikerikar, J.; Kavathekar, V.; Ghavate, N.; Sawant, R.; Madan, K. Smart door-locking mechanism. In Proceedings of the 2021 4th Biennial International Conference on Nascent Technologies in Engineering (ICNTE), Navi, Mumbai, India, 15–16 January 2021; pp. 1–4. [Google Scholar]
- Makandar, A.; Biradar, M.R.; Talawar, M.S. Digital door-lock security system using Arduino UNO. Int. Res. J. Modern. Eng. Technol. Sci. 2021, 3, 647–652. [Google Scholar]
- Nikitin, P. Leon Theremin (Lev Termen). IEEE Antennas Propag. Mag. 2012, 54, 252–257. [Google Scholar] [CrossRef]
- Stockman, H. Communication by Means of Reflected Power. Proc. IRE 1948, 36, 1196–1204. [Google Scholar] [CrossRef]
- Duroc, Y.; Tedjini, S. RFID: A key technology for Humanity. C. R. Phys. 2018, 19, 64–71. [Google Scholar] [CrossRef]
| Category | Available Worldwide | Selected in Hybrid Door-Lock System |
|---|---|---|
| Model | Variety of Models | MFRC522 |
| Type | Passive/Active | Passive |
| Battery | Battery-less/Battery Operated | Battery-less |
| Host Interface | I2C/SPI | SPI |
| Tag Reader Strength | High/Very Low | Very Low |
| Bytes in UID | 4/7 Bytes | 4 Bytes |
| Frequency Range | LF (kHz), HF and UHF (MHz), SHF (GHz) | HF (MHz) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ramzan, A.; Farhan, W.; Malahat, I.; Afzal, N. Double-Layered Authentication Door-Lock System Utilizing Hybrid RFID-PIN Technology for Enhanced Security. Mater. Proc. 2025, 23, 19. https://doi.org/10.3390/materproc2025023019
Ramzan A, Farhan W, Malahat I, Afzal N. Double-Layered Authentication Door-Lock System Utilizing Hybrid RFID-PIN Technology for Enhanced Security. Materials Proceedings. 2025; 23(1):19. https://doi.org/10.3390/materproc2025023019
Chicago/Turabian StyleRamzan, Aneeqa, Warda Farhan, Itba Malahat, and Namra Afzal. 2025. "Double-Layered Authentication Door-Lock System Utilizing Hybrid RFID-PIN Technology for Enhanced Security" Materials Proceedings 23, no. 1: 19. https://doi.org/10.3390/materproc2025023019
APA StyleRamzan, A., Farhan, W., Malahat, I., & Afzal, N. (2025). Double-Layered Authentication Door-Lock System Utilizing Hybrid RFID-PIN Technology for Enhanced Security. Materials Proceedings, 23(1), 19. https://doi.org/10.3390/materproc2025023019




