1. Introduction
Spoofing targeting the Global Navigation Satellite System (GNSS) aims to falsify the Position, Velocity, and Timing (PVT) results of victim receivers by emitting forged GNSS signals. Given the crucial role of GNSS as a PVT source across various domains, particularly in safety-critical applications such as electricity, communications, and autonomous driving, GNSS spoofing constitutes a significant security threat.
In response, anti-spoofing techniques have been extensively investigated over the past decades to detect, identify, and mitigate spoofing signals. These techniques can be broadly categorized into four types [
1]: signal processing techniques, cryptographic techniques, external information techniques, and spatial characteristic techniques. Notably, spatial characteristic techniques focus on analyzing the Direction of Arrival (DoA) of received signals, which are indirectly correlated to GNSS measurements including pseudoranges [
2], carrier phases [
3], Doppler shifts [
4], and signal power [
5], or directly determined using conventional DoA measurement methods such as antenna arrays [
6] and synthetic aperture techniques [
7].
Generally, spatial characteristic techniques are founded on one of two typical hypotheses. Some of these techniques operate under the assumption that spoofing signals originate from a single antenna, referred to as centralized spoofing in this paper, and consequently follow identical propagation paths. Thus, the primary objective of these techniques is to exploit the uniformity of the DoAs. Others presuppose that the spoofer cannot configure the DoAs of its signals to replicate the authentic DoAs recorded in the ephemeris. Consequently, they focus on scrutinizing the inconsistency between the measured DoA set of received signals and the anticipated DoA set suggested by the ephemeris. Both types of techniques can offer effective safeguards when the corresponding hypothesis is satisfied.
However, it is conceivable that spoofing signals could potentially be emitted from various directions, with multiple antennas each transmitting a single signal [
8,
9]. This scenario is termed distributed spoofing. Additionally, with the assistance of unmanned autonomous vehicles, a spoofer could even monitor the DoAs of authentic signals as recorded in the ephemeris data. Intuitively, such distributed GNSS spoofing is likely to undermine the aforementioned spatial characteristic techniques. However, verifying this inference is challenging. To date, to the best of our knowledge, the threat of distributed GNSS spoofing remains a theoretical possibility and has not been corroborated by any of the published literature.
To address the gap in the current research, we first analyze the potential challenges associated with executing distributed spoofing and elucidate several feasible distributed spoofing architectures. Subsequently, to validate and assess the threat of distributed GNSS spoofing, we devise an experimental platform for distributed GNSS spoofing. Finally, we construct a prototype based on the proposed architecture using Field Programmable Gate Array (FPGA) and conduct distributed spoofing experiments. The results confirm the significant threat posed by distributed spoofing yet also reveal its limitations, which may be leveraged to mitigate the risk of distributed spoofing.
2. Overview of Distributed GNSS Spoofing
In comparison to centralized spoofing, distributed spoofing presents a more intricate deployment structure. It not only necessitates the use of multiple spoofing antennas but also imposes a strict requirement that each antenna should transmit only one spoofing signal, or more precisely, only transmitting signals corresponding to one satellite, including both civilian signals and military signals on multiple frequencies. As a counterexample, the multi-antenna spoofing structure introduced in [
10] is distinct from distributed spoofing, as it associates spoofing nodes and victims in one-to-one mapping groups. In each group, the spoofing node emits multiple spoofing signals, akin to centralized spoofing.
2.1. Difficulties of Distributed GNSS Spoofing Implementation
While distributed spoofing may seem like a natural extension of centralized spoofing by deploying multiple spoofing nodes, several disparities exist between the two deployment structures, imposing additional requirements for distributed spoofing and rendering it a challenging task.
2.1.1. Diverse Propagation Paths
A critical disparity arises from the dispersion of propagation paths for each spoofing signal. In centralized spoofing, all signals traverse the same path, experiencing identical propagation delays. Consequently, each pseudorange measurement incurs a concurrent deviation, identified as additional clock bias in the PVT solution, maintaining pseudorange consistency and avoiding triggering the Receiver Autonomous Integrity Monitoring (RAIM) alarm. However, in distributed spoofing, due to different propagation distances and physical device characteristics, each signal experiences entirely distinct propagation delays, leading to discrepant deviations in pseudorange measurements. If not properly compensated, these deviations can result in potential pseudorange inconsistencies, making distributed spoofing readily handled by RAIM detection.
To compensate for propagation delays, two techniques can be utilized: closed-loop compensation and open-loop compensation.
This technique can be implemented if the spoofer has access to the victim’s GNSS receiver. It can be satisfied, for example, in a self-spoofing scenario or by hijacking the victim’s GNSS data through network hijacking. By comparing the time information of transmitted signals from spoofing nodes with received signals from the victim, the delay of each propagation path can be directly estimated.
Implementing closed-loop compensation may be challenging in real-world scenarios. An alternative technique is open-loop compensation. As proposed in [
11], the spoofer can calibrate the base propagation delay of each path and extrapolate the actual propagation delay using the physical distance between each spoofing antenna and the victim antenna. Such distances can be obtained either by ranging equipment like Light Detection and Ranging (LiDAR) units or calculated from positioning results. However, the precision of open-loop compensation depends heavily on ranging or positioning accuracy.
2.1.2. Clock Synchronization
GNSS satellite clocks need to be highly synchronized to guarantee the precision of pseudorange measurements, a scenario mirrored when a spoofer emits spoofing signals. In centralized spoofing, all signals are generated by a unique clock, introducing only an additional clock bias and drift in the PVT solution, without affecting the pseudorange consistency. However, in distributed spoofing, if spoofing nodes are driven by unsynchronized clocks, different clock drifts will result in time-varying deviations in each pseudorange measurement, severely compromising pseudorange consistency. To address this issue, the spoofer should synchronize multiple spoofing clocks using either local data links or GNSS synchronization.
2.1.3. Self-Interference
In certain spoofing scenarios, access to authentic GNSS signals is necessary. Authentic signals can serve various purposes, such as synchronizing spoofing clocks, as discussed in
Section 2.1.2, or generating spoofing signals in a receiver–spoofer structure [
12]. This requirement indicates that a spoofing node has to simultaneously transmit and receive GNSS signals, necessitating careful handling of transmitter–receiver isolation problems. Moreover, to ensure control over the victim, the arrival power of spoofing signals at the victim should exceed that of authentic signals. Considering the inverse square attenuation law, the power advantage of spoofing signals over authentic signals at spoofing nodes will be significantly large, exacerbating the transmitter–receiver isolation problem.
For centralized spoofing, this problem can be partially mitigated with a directive transmitting antenna and physical blockage/isolation between transmitting and receiving antennas. However, replicating this complex structure multiple times in distributed spoofing becomes costly and cumbersome. The spoofer may explore sophisticated signal processing techniques to mitigate self-interference such as Successive Spoofing Cancellation (SSC) [
13].
2.2. Potential Deployment Structure of Distributed GNSS Spoofing
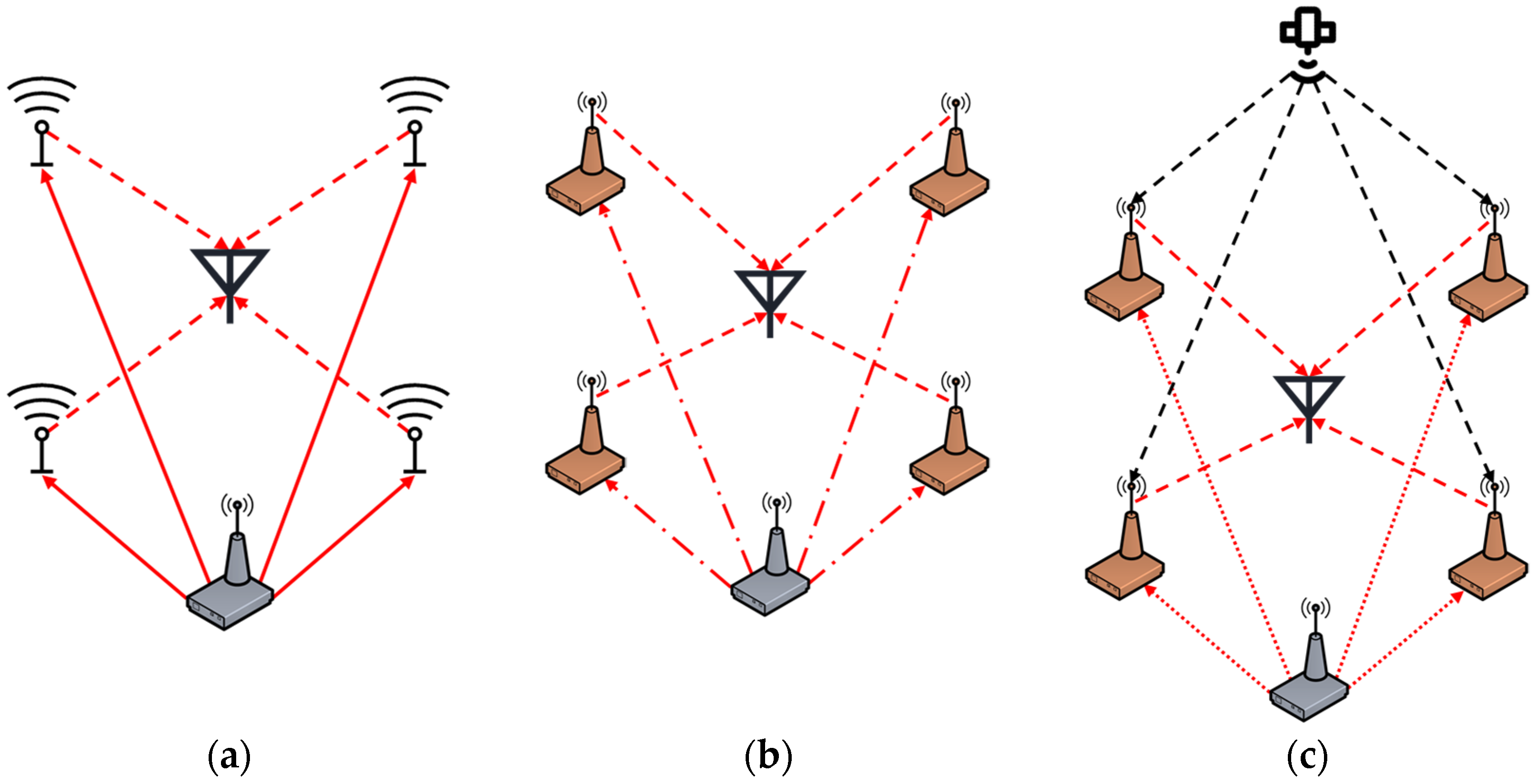
Considering various distributed levels and the aforementioned difficulties, we propose three potential structures feasible for distributed spoofing, as illustrated in
Figure 1, arranged by increasing complexity of realization: allocation mode, transmission mode, and self-generation mode.
In the allocation mode, a central spoofing node (depicted as the gray equipment) generates each spoofing signal and allocates them to multiple spoofing antennas using signal cables (depicted as red solid lines). Each spoofing antenna then transmits spoofing signals toward the victim antenna (depicted as red dashed lines). This mode circumvents the clock synchronization issue, as each spoofing signal is driven by the clock of the central spoofing node. However, the cable connection structure in allocation mode may add complexity to implementation.
To enhance flexibility, in the transmission mode, a central spoofing node generates each spoofing signal and transmits the signal sampling point files to multiple transfer spoofing nodes via wireless communication techniques (depicted as red dash–dot lines) [
14]. The transfer spoofing nodes then reconstruct the spoofing signals and emit them to the victim antenna. Additionally, clock synchronization of the transfer spoofing nodes can be achieved using wireless communication data links as well. However, the continuous operation of the transmission mode heavily relies on the reliability of wireless communication links, and the limited payload imposes restrictions on the data size of spoofing signals, potentially affecting signal quality.
For further flexibility, in the self-generation mode, the central spoofing node acts solely as a central controller. It remotely assigns spoofing tasks to the spoofing nodes (depicted as red dotted lines). Each spoofing node operates independently, receiving authentic GNSS signals (depicted as black dashed lines) to accomplish clock synchronization and spoofing signal generation. Meanwhile, each node transmits spoofing signals to the victim antenna according to the instructions from the central spoofing node. However, each spoofing node must contend with the challenge of self-interference, as previously mentioned.
3. Distributed GNSS Spoofing Experimental Platform
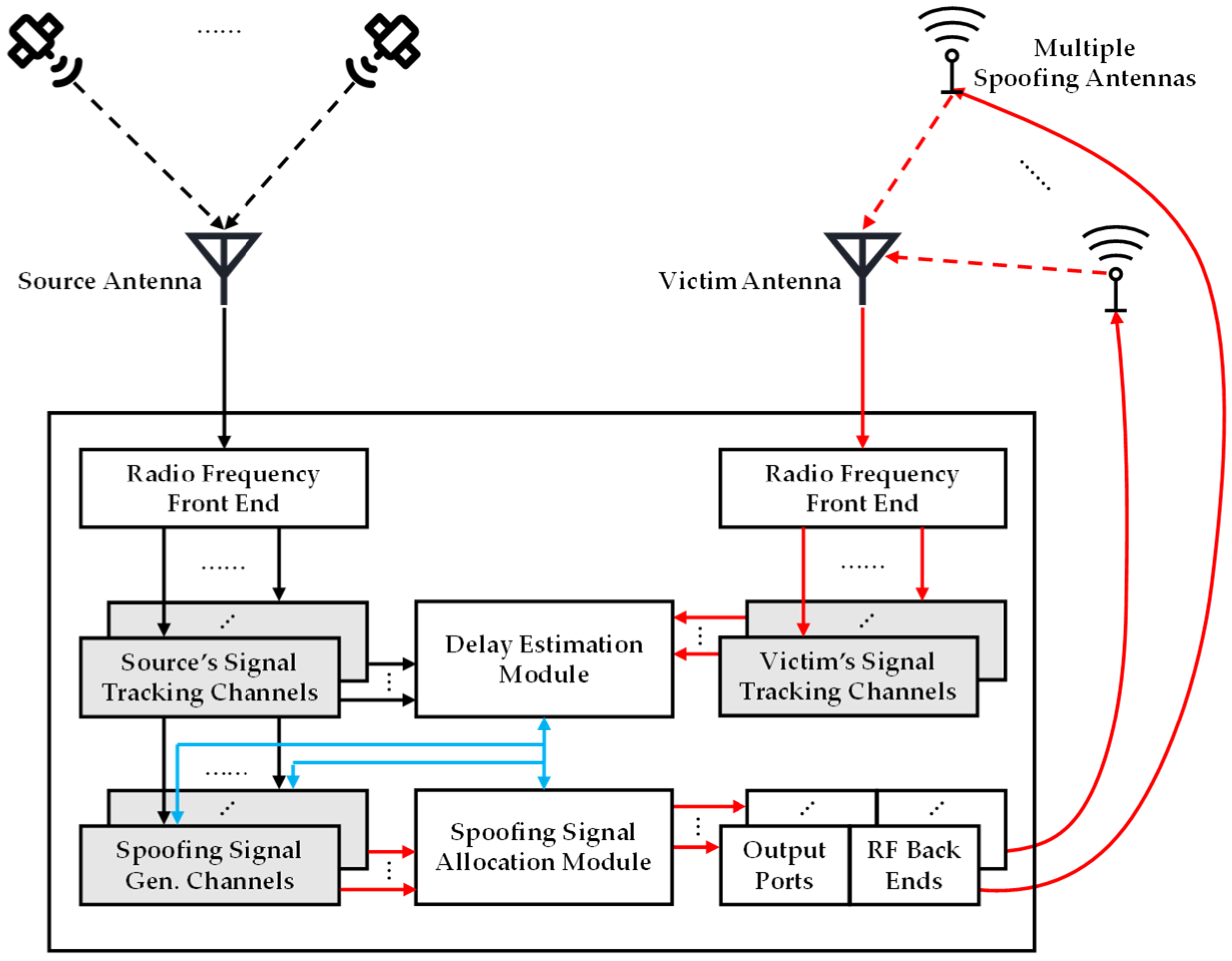
To validate the security threat posed by distributed spoofing, we have developed an experimental platform based on the closed-loop compensation technique and the allocation mode, as depicted in
Figure 2.
The experimental platform employs a receiver–spoofer structure to generate spoofing signals. Authentic signals are resolved by the tracking channels, after undergoing processing through the radio frequency front end, including analog-to-digital converters and downconverters. Using the extracted signal parameters and the desired false PVT solution, the spoofer adjusts the signal parameters and reconstructs multiple spoofing signals. These spoofing signals are then allocated to multiple spoofing antennas, after passing through their respective radio frequency back ends, consisting of digital-to-analog converters and upconverters. Simultaneously, the experimental platform keeps processing signals received by the victim antenna to monitor the effects of distributed spoofing.
Upon completion of the experimental platform setup, it is necessary to estimate the propagation delays corresponding to each propagation path associated with different spoofing antennas. This involves extracting the transmit time of the authentic signal from the source antenna and its corresponding spoofing signal from the victim antenna simultaneously. The average difference between the transmit time pairs can be approximated as the propagation delay of the corresponding propagation path. Subsequently, during the execution of distributed spoofing, each spoofing signal should calibrate the propagation delay when allocated to a specific spoofing antenna by modifying its transmit time.
4. Field Test Results of Distributed GNSS Spoofing
Based on the proposed distributed spoofing experimental platform in
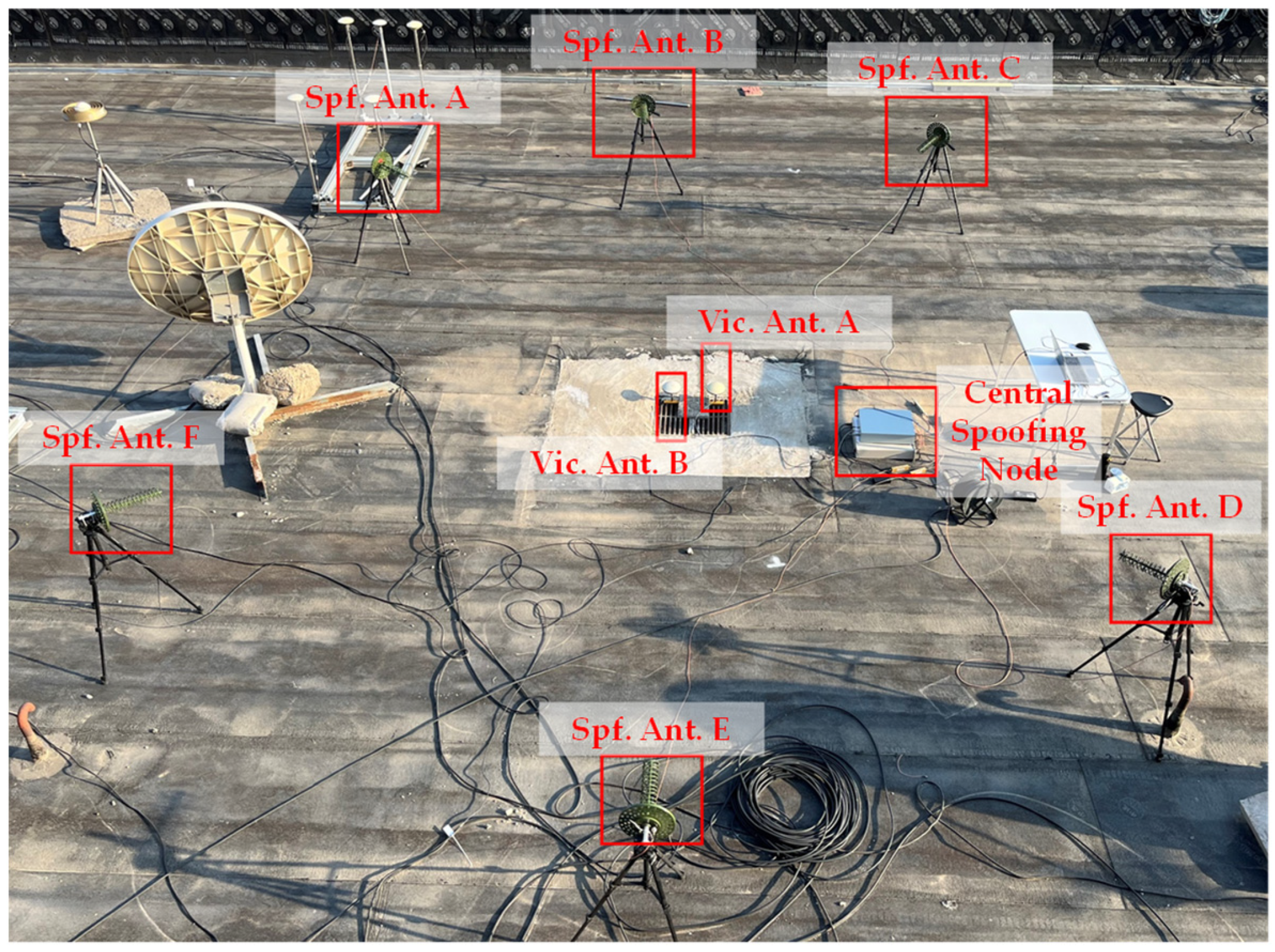
Section 3, we developed a central spoofing node using FPGA, as shown in
Figure 3. This node can generate up to 12 spoofing signals and allocate them to a maximum of 8 spoofing antennas. Utilizing this central node, we established a distributed spoofing experimental setup on the roof of Weiqing Building at Tsinghua University. In this setup, six spoofing antennas are employed to execute distributed spoofing toward the victim’s antenna placed at the center, as depicted in
Figure 4.
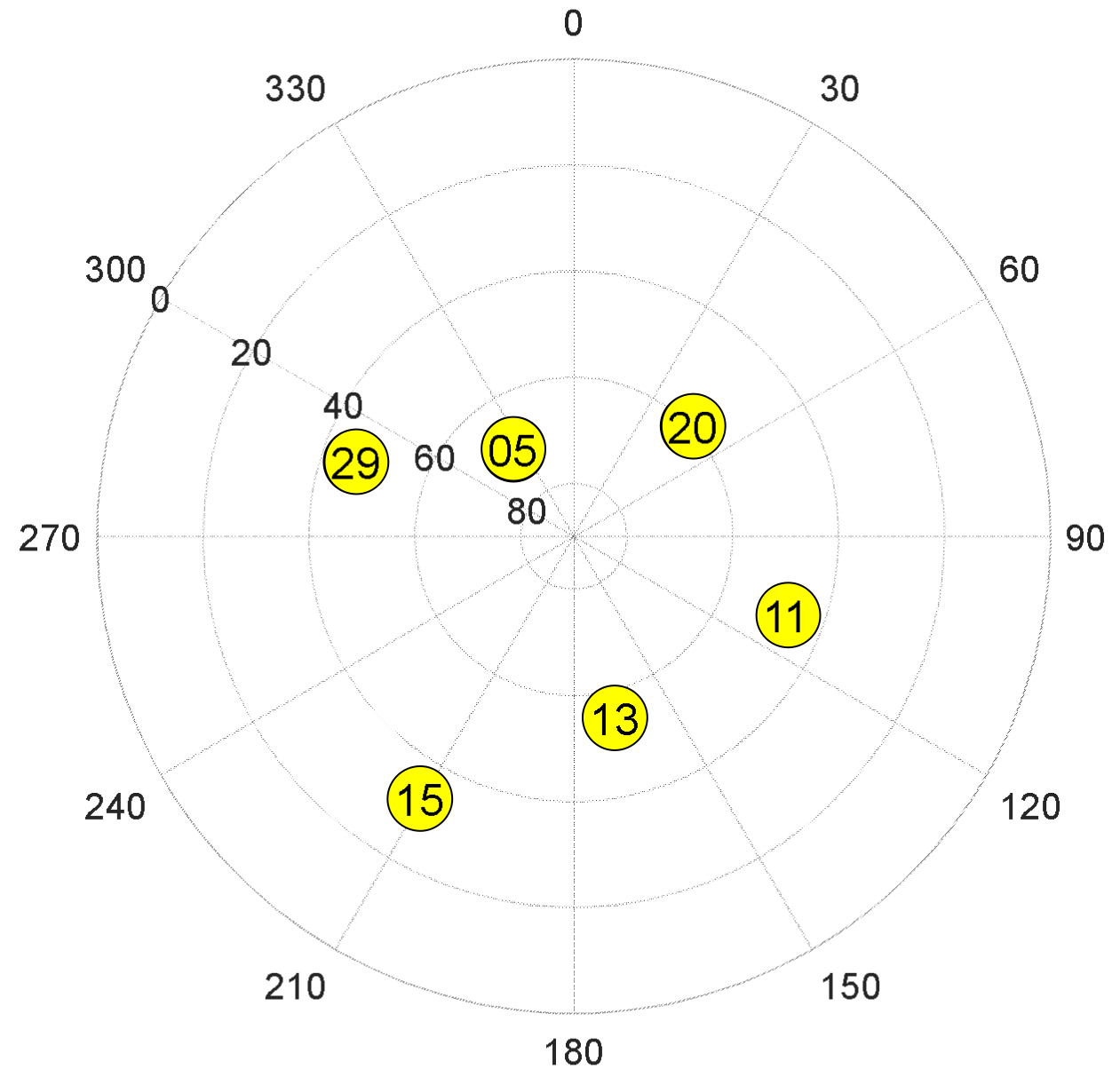
Figure 5 illustrates the Sky plot of the utilized spoofing signals.
To verify the validation of distributed spoofing, we conducted four groups of spoofing experiments, with settings detailed in
Table 1. Group 0 represents authentic signals received from the source antenna, serving as a benchmark. The false PVT set in the other groups is identical to that of Group 0.
Group 1 represents centralized spoofing, where all spoofing signals are transmitted from a single spoofing antenna. Group 2 represents distributed spoofing without propagation delay calibration, while Group 3 represents distributed spoofing with propagation delay calibration. Additionally, Group 4 examines the influence of distributed spoofing on an innocent antenna adjacent to the victim antenna.
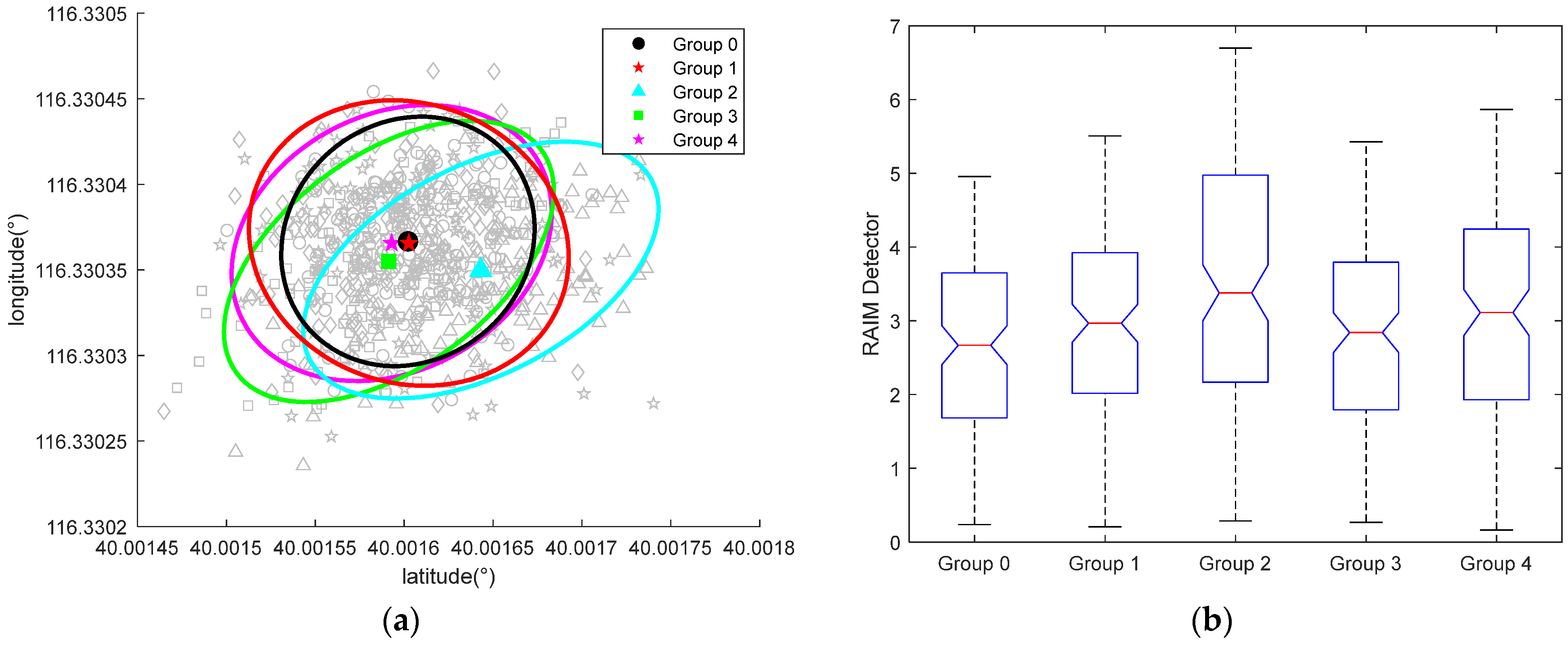
The 95% confidence ellipses of positioning results for each group are presented in
Figure 6a. Compared with the benchmark, the positioning Root-Mean-Square-Error (RMSE) slightly increases in all spoofing groups, indicating a slight degradation in the signal quality of the spoofing signals compared to authentic ones. Nonetheless, the results demonstrate that distributed spoofing effectively manipulates the victim to resolve a false PVT solution. Notably, the positioning results of Group 2 exhibit a clear bias from the desired PVT, highlighting the significant influence of diverse propagation delays on the efficiency of distributed spoofing and emphasizing the importance of propagation delay compensation.
To assess pseudorange consistency, we computed the RAIM detector for each group, as illustrated in
Figure 6b. The relative relationship of RAIM detectors provides valuable insights. An overall lower RAIM detector value for Group 3 compared to Group 2 confirms the effectiveness of propagation delay compensation. Conversely, a higher average RAIM detector for Group 4 compared to Group 3 implies that the accuracy of the propagation delay compensation operation is also a critical factor.
5. Conclusions
This paper presents a concise analysis of distributed spoofing, an intricate deployment structure wherein each spoofing antenna transmits only one spoofing signal. Distributed spoofing can be employed to imitate the DoA set of authentic signals, posing challenges to the efficacy of existing spatial-characteristic-based anti-spoofing algorithms. However, implementing distributed spoofing faces several obstacles, including diverse propagation paths, clock synchronization, and self-interference. Addressing these challenges, this study proposes three potential structures feasible for distributed spoofing implementation. Additionally, to validate the threat of distributed spoofing, this paper proposes a distributed spoofing experimental platform and develops a corresponding prototype. Field test results confirm the feasibility of distributed spoofing and emphasize that correct propagation delay compensation is a significant precondition of distributed spoofing implementation. The conclusions exploit the potential risk of distributed spoofing, partially breaking the current assumptions of the spatial characteristics of spoofing signals, advocating for increased attention to enhancing GNSS security and developing new anti-spoofing techniques.
Author Contributions
Conceptualization, M.Z., H.L. and M.L.; methodology, M.Z. and H.L.; software, M.Z.; validation, M.Z. and H.L.; formal analysis, M.Z. and H.L.; investigation, M.Z.; resources, M.Z.; data curation, M.Z.; writing—original draft preparation, M.Z.; writing—review and editing, M.Z., H.L. and M.L.; visualization, M.Z.; supervision, H.L. and M.L.; project administration, H.L. and M.L.; funding acquisition, H.L. and M.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Changsha’s Major Science and Technology Project, grant number kq2207007.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No data are publicly available.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Zidan, J.; Adegoke, E.I.; Kampert, E.; Birrell, S.A.; Ford, C.R.; Higgins, M.D. GNSS Vulnerabilities and Existing Solutions: A Review of the Literature. IEEE Access 2021, 9, 153960–153976. [Google Scholar] [CrossRef]
- Wen, J.; Li, H.; Lu, M. A Flexible GNSS Spoofer Localization System: Spoofing Discrimination and Localization Method. NAVIGATION J. Inst. Navig. 2022, 69, navi.511. [Google Scholar] [CrossRef]
- Borio, D.; Gioia, C. A Sum-of-Squares Approach to GNSS Spoofing Detection. IEEE Trans. Aerosp. Electron. Syst. 2016, 52, 1756–1768. [Google Scholar] [CrossRef]
- Tu, J.; Zhan, X.; Zhang, X.; Zhang, Z.; Jing, S. Low-complexity GNSS Anti-spoofing Technique Based on Doppler Frequency Difference Monitoring. IET Radar Sonar Amp. Navig. 2018, 12, 1058–1065. [Google Scholar] [CrossRef]
- Wang, F.; Li, H.; Lu, M. GNSS Spoofing Countermeasure with a Single Rotating Antenna. IEEE Access 2017, 5, 8039–8047. [Google Scholar] [CrossRef]
- Appel, M.; Konovaltsev, A.; Meurer, M. Joint Antenna Array Attitude Tracking and Spoofing Detection Based on Phase Difference Measurements. In Proceedings of the 29th International Technical Meeting of the Satellite Division of the Institute of Navigation, ION GNSS 2016, Portland, OR, USA, 12–16 September 2016; Institute of Navigation: Portland, OR, USA, 2016; Volume 5, pp. 3018–3026. [Google Scholar]
- Lan, X.; Wan, L.; Han, G.; Rodrigues, J.J.P.C. A Novel DOA Estimation Algorithm Using Array Rotation Technique. Future Internet 2014, 6, 155–170. [Google Scholar] [CrossRef]
- Merwe, J.R.V.D.; Zubizarreta, X.; Lukcin, I.; Rugamer, A.; Felber, W. Classification of Spoofing Attack Types. In Proceedings of the 2018 European Navigation Conference (ENC), Gothenburg, Sweden, 14–17 May 2018; IEEE: Gothenburg, Sweden, May, 2018; pp. 91–99. [Google Scholar]
- Psiaki, M.L.; Humphreys, T.E. GNSS Spoofing and Detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Pardhasaradhi, B.; Srihari, P.; Aparna, P. Spoofer-to-Target Association in Multi-Spoofer Multi-Target Scenario for Stealthy GPS Spoofing. IEEE Access 2021, 9, 108675–108688. [Google Scholar] [CrossRef]
- Zhong, M.; Zhang, X.; Gao, W.; Lu, M.; Li, H. Prototype Development of a Flexible Covert Spoofer Using Measurement Information from LiDAR and AHRS. In Proceedings of the 35th International Technical Meeting of the Satellite Division of the Institute of Navigation, ION GNSS+ 2022, Denver, CO, USA, 19–23 September 2022; Institute of Navigation: Denver, CO, USA, 2022; Volume 5, pp. 3548–3559. [Google Scholar]
- Humphreys, T.E.; Ledvina, B.M.; Psiaki, M.L.; O’Hanlon, B.W.; Kintner, P.M., Jr. Assessing the Spoofing Threat: Development of a Portable Gps Civilian Spoofer. In Proceedings of the 21st International Technical Meeting of the Satellite Division of the Institute of Navigation, ION GNSS 2008, Savannah, GA, USA, 16–19 September 2008; The Institute of Navigation: Savannah, GA, USA, 2008; Volume 2, pp. 1198–1209. [Google Scholar]
- Broumandan, A.; Jafarnia-Jahromi, A.; Lachapelle, G. Spoofing Detection, Classification and Cancelation (SDCC) Receiver Architecture for a Moving GNSS Receiver. GPS Solut 2015, 19, 475–487. [Google Scholar] [CrossRef]
- Lenhart, M.; Spanghero, M.; Papadimitratos, P. Distributed and Mobile Message Level Relaying/Replaying of GNSS Signals. In Proceedings of the 2022 International Technical Meeting of The Institute of Navigation, ITM 2022, Long Beach, CA, USA, 25–27 January 2022; Institute of Navigation: Long Beach, CA, USA, 2022; Volume 2022, pp. 56–67. [Google Scholar]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).