ZigBee Cyberattacks Simulation †
Abstract
1. Introduction
2. Related Works
3. Cyberattacks on ZigBee Networks
- Sniffing—malicious traffic interception enables attackers to collect sensitive information. By employing brute force and dictionary attacks, they can decrypt network traffic, leading to various security threats. Additionally, by executing a man-in-the-middle attack, they can manipulate network traffic [20].
- BotNet—network of compromised devices, referred to as bots, that are utilized to perform malicious actions. These devices are controlled by an attacker who employs various methods to infect additional devices, thereby expanding the BotNet. Such attacks can facilitate other cyberattacks due to their large scale and distributed nature [21,22].
- Distributed Denial of Service (DDoS)—DDoS attacks targeting IoT devices involve a large number of compromised devices that generate a substantial volume of traffic, overwhelming the communication infrastructure. Such an attack can disrupt the normal functioning of IoT devices [23].
- Brute Force—refers to the systematic testing of numerous passwords, logins, or encryption keys to gain unauthorized access. This method relies on the attacker attempting a wide array of combinations until the correct access credentials are discovered [24].
- Dictionary—involves attempting to use a set of potential combinations of passwords or keys to discover the actual one. Upon a successful attack, the attacker can gain unauthorized access to the network [25].
- Man-in-the-Middle—the covert capturing of data exchanged between two devices enables an attacker to manipulate the traffic before forwarding it to the intended recipient [26].
- Replay—the interception and retransmission of legitimate data transmissions by an attacker can mislead the recipient into performing unauthorized actions. An attacker executing this type of attack may induce unauthorized changes, such as unlocking smart locks and controlling smart home systems [27].
4. Cyberattack Simulation Module
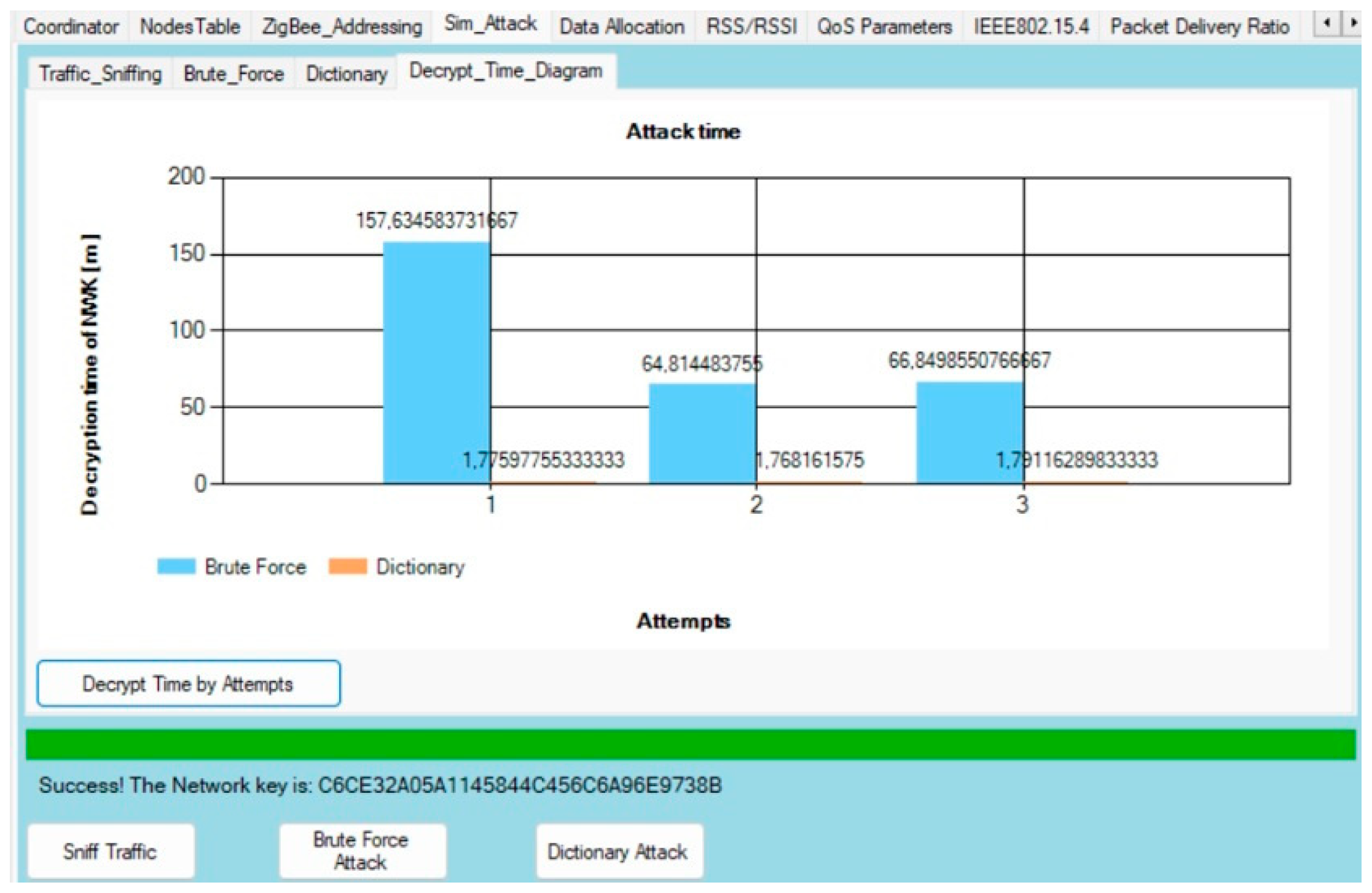
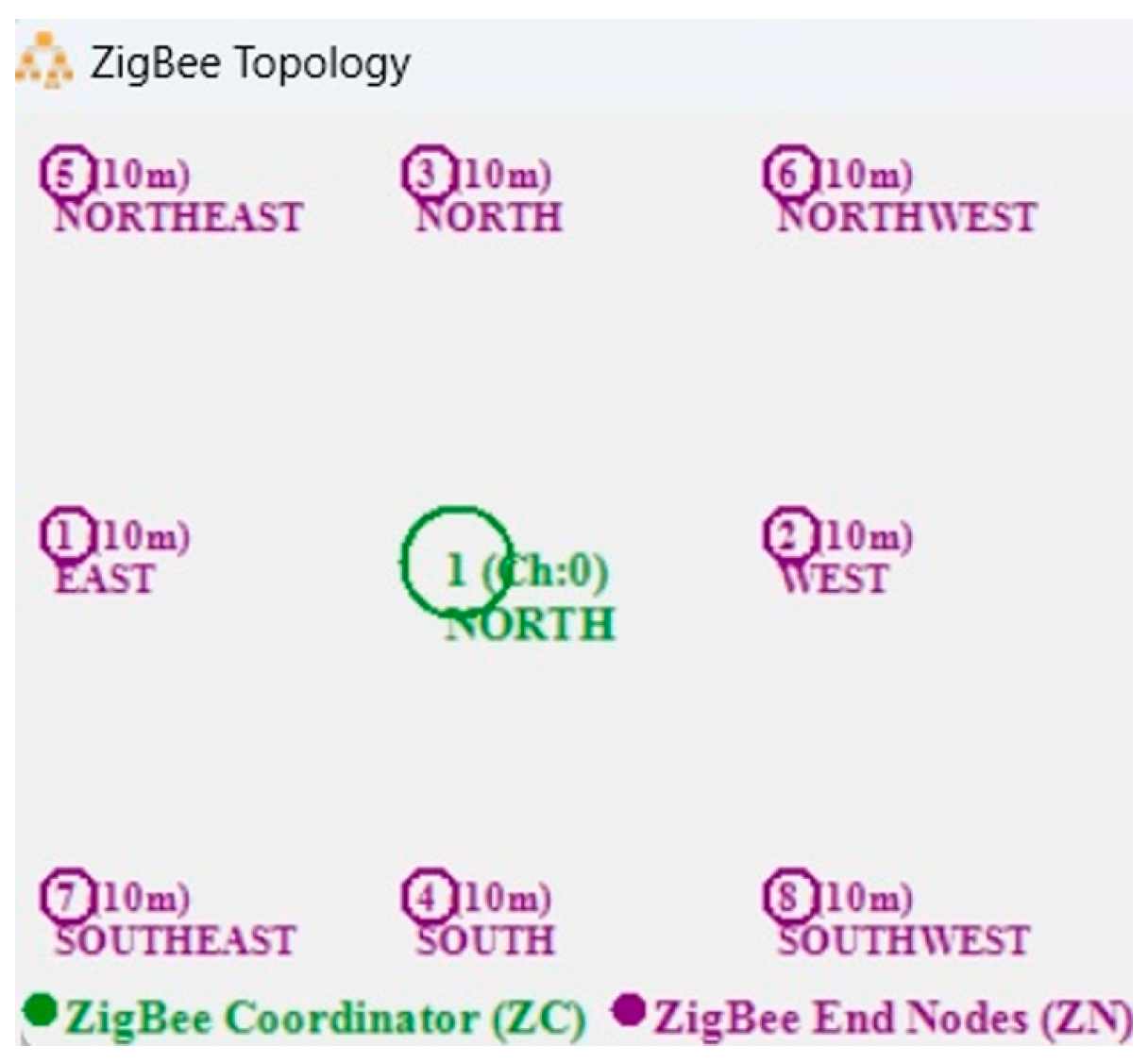
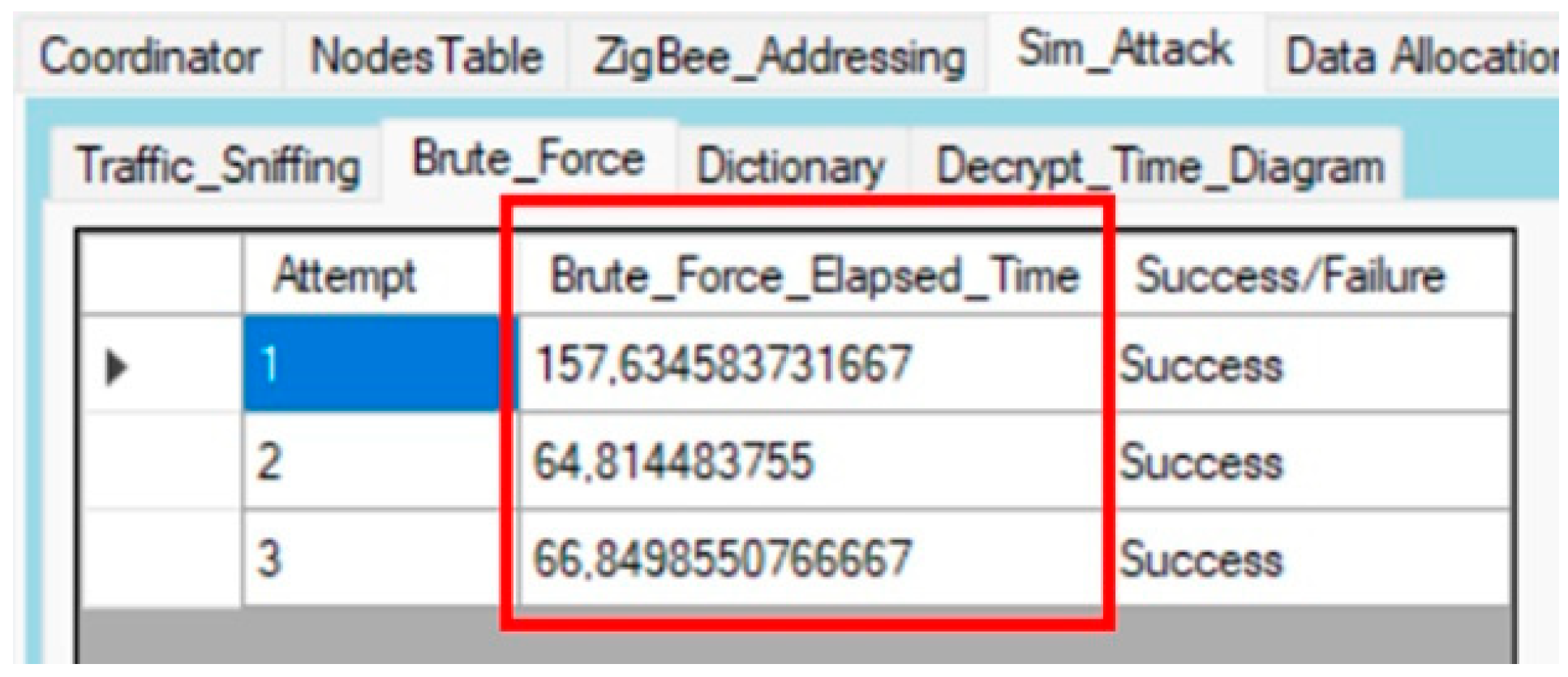
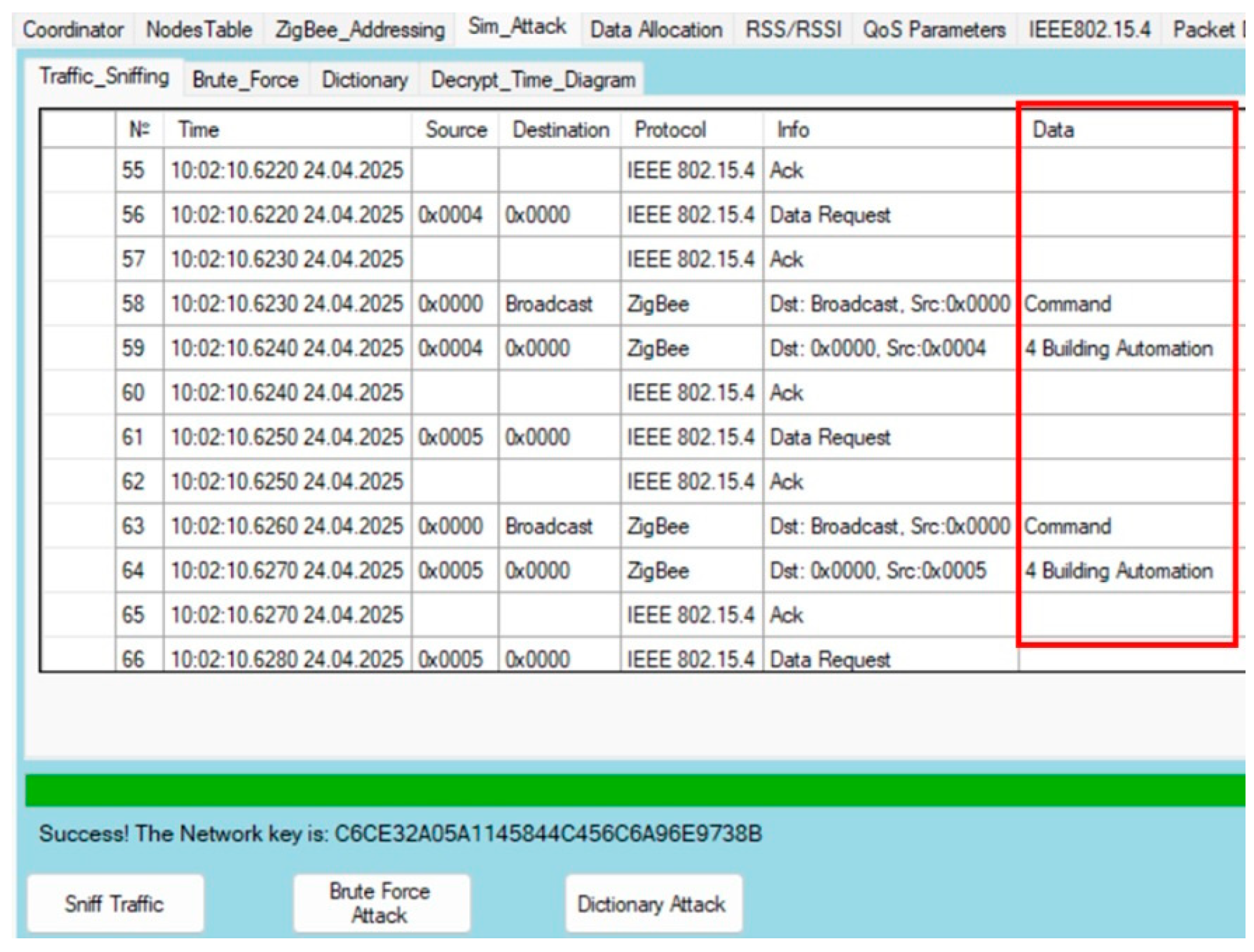
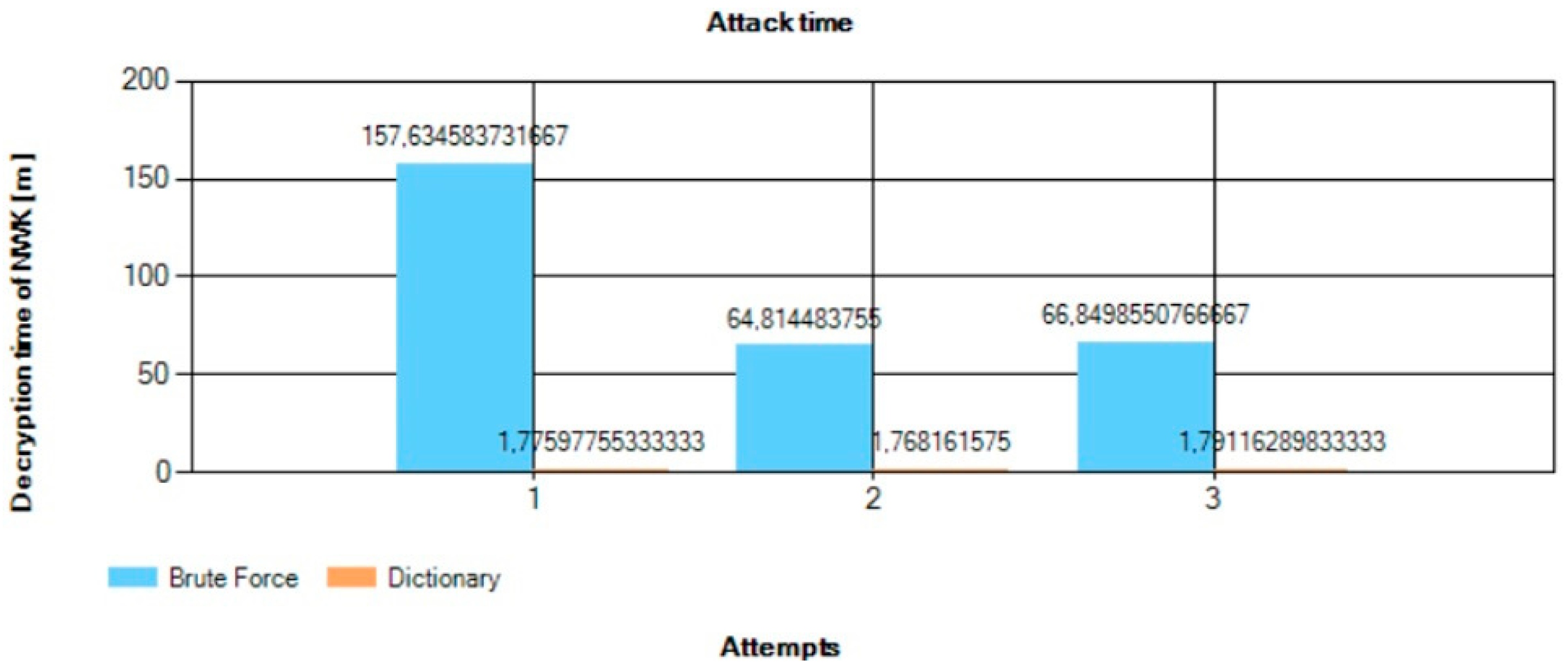
5. Experimental Research and Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Auhl, Z.; Moraliyage, H.; Chilamkurti, N.; Alahakoon, D. RACER: A Lightweight Distributed Consensus Algorithm for the IoT with Peer-Assisted Latency-Aware Traffic Optimisation. Technologies 2025, 13, 151. [Google Scholar] [CrossRef]
- Stoyanov, I.S.; Iliev, T.B.; Mihaylov, G.Y.; Evstatiev, B.I.; Sokolov, S.A. Analysis of the Cybersecurity Threats in Smart Grid University of Telecommunications and Post, Sofia, Bulgaria. In Proceedings of the International Symposium for Design and Technology in Electronic Packaging (SIITME), Iasi, Romania, 25–28 October 2018. [Google Scholar] [CrossRef]
- Li, J.; Wang, S.; Xu, Z.; Xi, W.; Wang, S.; Gong, W. EchScatter: Enriching Codeword Translation for High-Throughput Ambient ZigBee Backscatter. ACM Trans. Sens. Netw. 2025, 21, 1–21. [Google Scholar] [CrossRef]
- Network Simulator Projects. Network Simulator 2 (NS2). Available online: https://networksimulator2.com (accessed on 25 July 2024).
- Sandeep; Vasaya, N.; Smera, C.; Kirubanand, V.B.; Balamurugan, E. Simulation model of ZigBee network to analyze routing protocols for the sustainable Healthcare environment. NeuroQuantology 2022, 20, 1471–1479. [Google Scholar]
- Ns3 Projects. Ns 3 Simulations, Zigbee Simulation. Available online: https://ns3simulation.com/zigbee-simulation/ (accessed on 25 July 2024).
- Fang, X.; Zheng, L.; Fang, X.; Chen, W.; Fang, K.; Yin, L.; Zhu, H. Pioneering advanced security solutions for reinforcement learning-based adaptive key rotation in Zigbee networks. Sci. Rep. 2024, 14, 13931. [Google Scholar] [CrossRef]
- Cheimaras, V.; Peladarinos, N.; Monios, N.; Daousis, S.; Papagiakoumos, S.; Papageorgas, P.; Piromalis, D. Emergency Communication System Based on Wireless LPWAN and SD-WAN Technologies: A Hybrid Approach. Signals 2023, 4, 315–336. [Google Scholar] [CrossRef]
- Zhi, H.; He, Y.; Tian, Z.; Xin, P. Wireless Mesh System Design for Photovoltaic Power Station Based on LoRa. In Proceedings of the 2023 International Conference on Frontiers of Artificial Intelligence and Machine Learning, Beijing, China, 14–16 April 2023; pp. 70–74. [Google Scholar]
- Chowdhury, M.; Ray, B.; Chowdhury, S.; Rajasegarar, S. A novel insider attack and machine learning based detection for the internet of things. ACM Trans. Internet Things 2021, 2, 1–23. [Google Scholar] [CrossRef]
- Adday, G.; Subramaniam, S.; Zukarnain, Z.; Samian, N. Investigating and Analyzing Simulation Tools of Wireless Sensor Networks: A Comprehensive Survey. IEEE Access 2024, 12, 22938–22977. [Google Scholar] [CrossRef]
- Mbarek, B.; Soula, M.; Pitner, T.; Meddeb, A. An Effective Replica Node Detection Scheme in Internet of Things Networks. In Proceedings of the 2023 International Wireless Communications and Mobile Computing, Marrakesh, Morocco, 19–23 June 2023; pp. 608–613. [Google Scholar] [CrossRef]
- TinyOS. Available online: https://github.com/tinyos (accessed on 4 September 2024).
- Yigit, Y.; Dagdeviren, O.; Challenger, M. Self-Stabilizing Capacitated Vertex Cover Algorithms for Internet-of-Things-Enabled Wireless Sensor Networks. Sensors 2022, 22, 3774. [Google Scholar] [CrossRef] [PubMed]
- Chen, G.; Dong, W.; Qiu, F.; Guan, G.; Gao, Y.; Zeng, S. Scalable and interactive simulation for IoT applications with TinySim. IEEE Internet Things J. 2023, 10, 20984–20999. [Google Scholar] [CrossRef]
- Pellenz, M.E.; Lachowski, R.; Jamhour, E.; Brante, G.; Moritz, G.L.; Souza, R.D. In-network data aggregation for information-centric WSNs using unsupervised machine learning techniques. In Proceedings of the 2021 IEEE Symposium on Computers and Communications (ISCC), Athens, Greece, 5–8 September 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Zhou, T.; Yang, C.; Chen, H.; Han, Y.; Bao, W.; Cheng, Q. Performance research on ZigBee wireless sensor network self-organizing network for 220 kV four-circuit transmission lines on the same tower. Sustain. Energy Technol. Assess. 2022, 53, 102302. [Google Scholar] [CrossRef]
- Almutairi, R.; Bergami, G.; Morgan, G. Advancements and Challenges in IoT Simulators: A Comprehensive Review. Sensors 2024, 24, 1511. [Google Scholar] [CrossRef]
- Kebande, V.R.; Awad, A.I. Industrial internet of things ecosystems security and digital forensics: Achievements, open challenges, and future directions. ACM Comput. Surv. 2024, 56, 1–37. [Google Scholar] [CrossRef]
- Jin, H.; Jeon, G.; Choi, H.W.A.; Jeon, S.; Seo, J.T. A threat modeling framework for IoT-Based botnet attacks. Heliyon 2024, 10, e39192. [Google Scholar] [CrossRef]
- Lefoane, M.; Ghafir, I.; Kabir, S.; Awan, I.U. Internet of Things botnets: A survey on Artificial Intelligence based detection techniques. J. Netw. Comput. Appl. 2025, 236, 104110. [Google Scholar] [CrossRef]
- Kornyo, O.; Asante, M.; Opoku, R.; Owusu-Agyemang, K.; Partey, B.T.; Baah, E.K.; Boadu, N. Botnet attacks classification in AMI networks with recursive feature elimination (RFE) and machine learning algorithms. Comput. Secur. 2023, 135, 103456. [Google Scholar] [CrossRef]
- Kumari, P.; Jain, A.K. A comprehensive study of DDoS attacks over IoT network and their countermeasures. Comput. Secur. 2023, 127, 103096. [Google Scholar] [CrossRef]
- Pourrahmani, H.; Yavarinasab, A.; Monazzah, A.M.H. A review of the security vulnerabilities and countermeasures in the Internet of Things solutions: A bright future for the Blockchain. Internet Things 2023, 23, 100888. [Google Scholar] [CrossRef]
- Bala, B.; Behal, S. AI techniques for IoT-based DDoS attack detection: Taxonomies, comprehensive review and research challenges. Comput. Sci. Rev. 2024, 52, 100631. [Google Scholar] [CrossRef]
- Upadhyay, D.; Ghosh, S.; Ohno, H.; Zaman, M.; Sampalli, S. Securing industrial control systems: Developing a SCADA/IoT test bench and evaluating lightweight cipher performance on hardware simulator. Int. J. Crit. Infrastruct. Prot. 2024, 47, 100705. [Google Scholar] [CrossRef]
- Wang, Z.; Sun, C. LICAPA: Lightweight collective attestation for physical attacks detection in highly dynamic networks. Pervasive Mob. Comput. 2024, 99, 101903. [Google Scholar] [CrossRef]
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23, 5941. [Google Scholar] [CrossRef] [PubMed]
- Yordanova, M.; Haka, A.; Aleksieva, V.; Valchanov, H. Enhanced Simulation Tool for ZigBee Security. In Proceedings of the 2024 5th International Conference on Communications, Information, Electronic and Energy Systems (CIEES), Veliko Tarnovo, Bulgaria, 20–22 November 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Connectivity Standards Alliance. Zigbee Specification, Revision 23, 15 March 2023. Available online: https://csa-iot.org/all-solutions/zigbee/ (accessed on 24 April 2025).





Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Haka, M.; Haka, A.; Aleksieva, V.; Valchanov, H. ZigBee Cyberattacks Simulation. Eng. Proc. 2025, 104, 46. https://doi.org/10.3390/engproc2025104046
Haka M, Haka A, Aleksieva V, Valchanov H. ZigBee Cyberattacks Simulation. Engineering Proceedings. 2025; 104(1):46. https://doi.org/10.3390/engproc2025104046
Chicago/Turabian StyleHaka, Marieta, Aydan Haka, Veneta Aleksieva, and Hristo Valchanov. 2025. "ZigBee Cyberattacks Simulation" Engineering Proceedings 104, no. 1: 46. https://doi.org/10.3390/engproc2025104046
APA StyleHaka, M., Haka, A., Aleksieva, V., & Valchanov, H. (2025). ZigBee Cyberattacks Simulation. Engineering Proceedings, 104(1), 46. https://doi.org/10.3390/engproc2025104046





