Game-Theoretical Approaches for Service Provisioning in Network Virtualization: Survey, Taxonomies and Open Challenges
Abstract
:1. Introduction
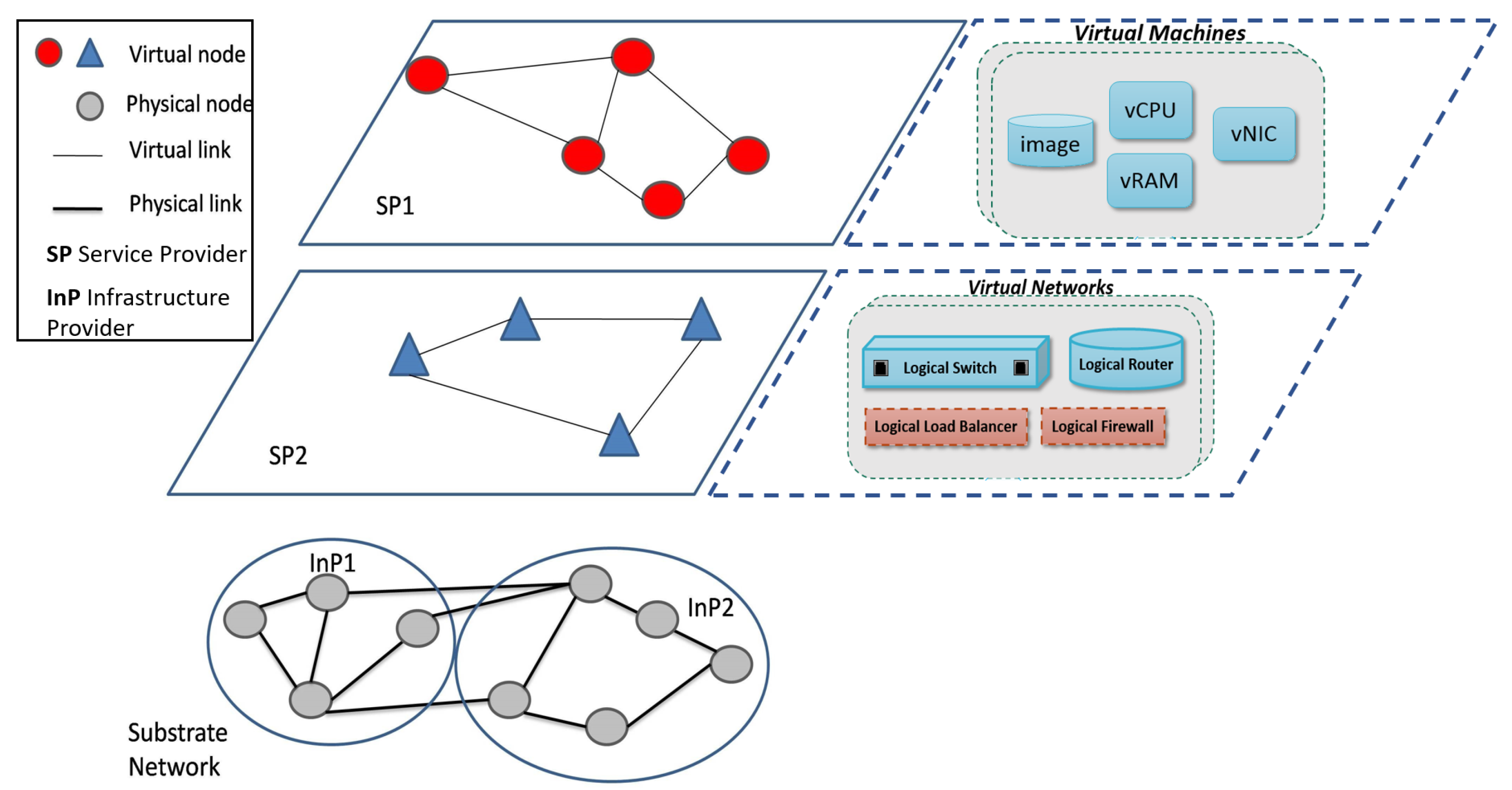
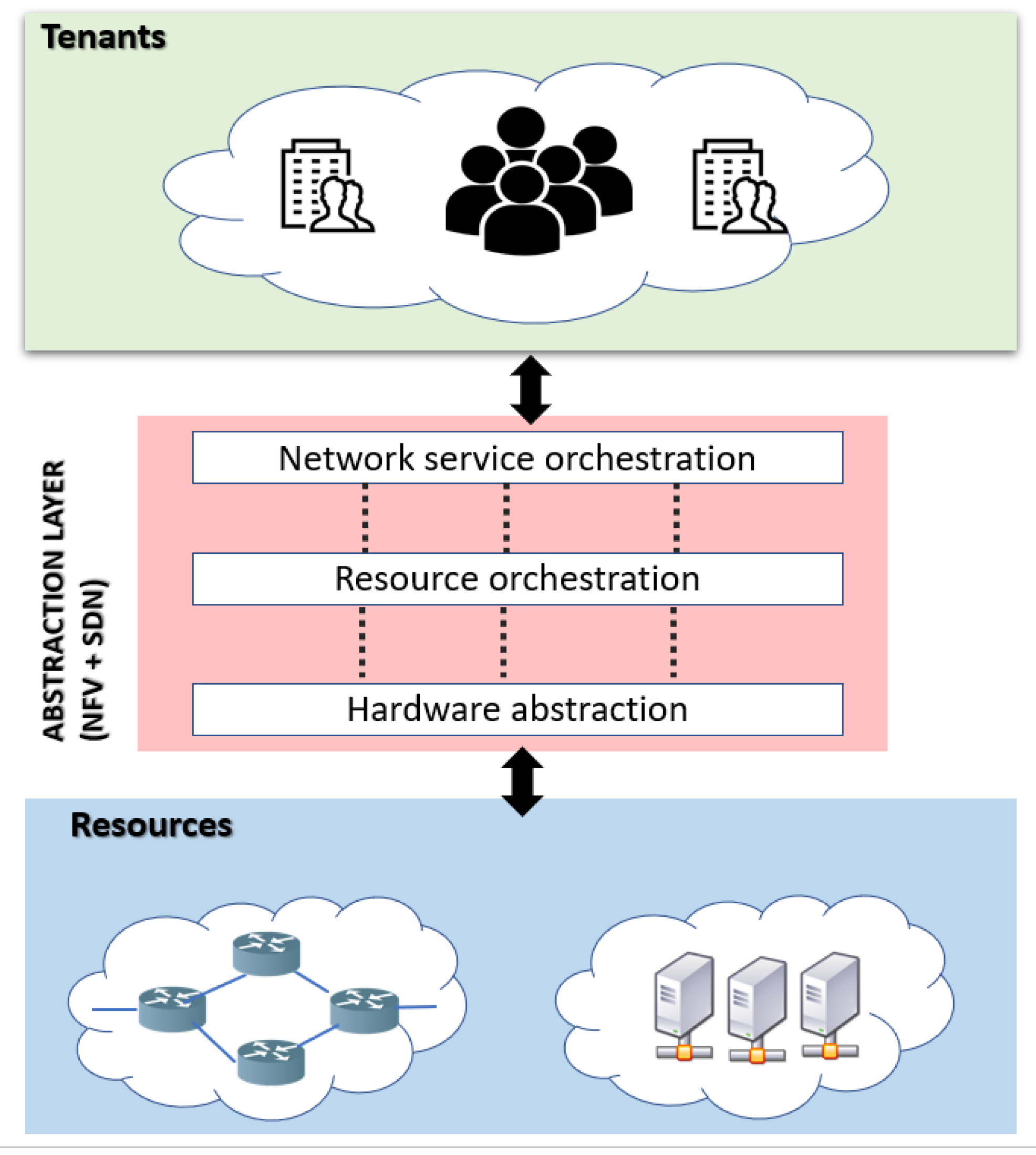
2. Network Virtualization
2.1. NV Typical Architecture
2.2. NV Enabling Technologies
- Software Defined Networking [7]: The traditional hardware-based networks cannot meet the computing and storage needs for the user’s service requests in an unstable and a changing environment. SDN provides a better fit in such situations by including simplified and enhanced network control, flexible and efficient network management, and improved network service performance. Moreover, the SDN separates the control plane from the data plane through a well-defined programming interface, such that the centralized controller can have a complete view of the entire network as shown in Figure 2. Thus, SDN ensures a new virtualization level through open protocols, such as OpenFlow (OF) protocols, and standardized interface between the control plane and the data plane.
- NFV: The NFV paradigm aim is to decouple network functions from dedicated physical equipment by using virtualization technology, and runs the virtual network functions (VNFs) in the general purpose physical or virtual network appliances. To conclude, the main difference between the SDN and NFV architectures is the overall focus network management responsibilities, and the standards controlling the architectural and functional deployment.
- SDN-enabled NFV architecture: Several recent approaches [8,9,10] were aimed at integrating the SDN into NFV architecture to enhance the network performance by combining the benefits of the two paradigms described by Figure 3. This revolutionary architecture concept is dedicated to adapt the increasing on-demanding services for the next-generation mobile networks such as the 5G [11] technologies and other applications, by providing more flexibility and more scalability.
3. An Overview of Game Theory
3.1. Concept and Characteristics
3.2. The Nash Equilibrium
3.3. Mixed Strategies
3.4. Pareto Efficiency
4. Taxonomy: Classification of GT Approaches in Network Virtualization
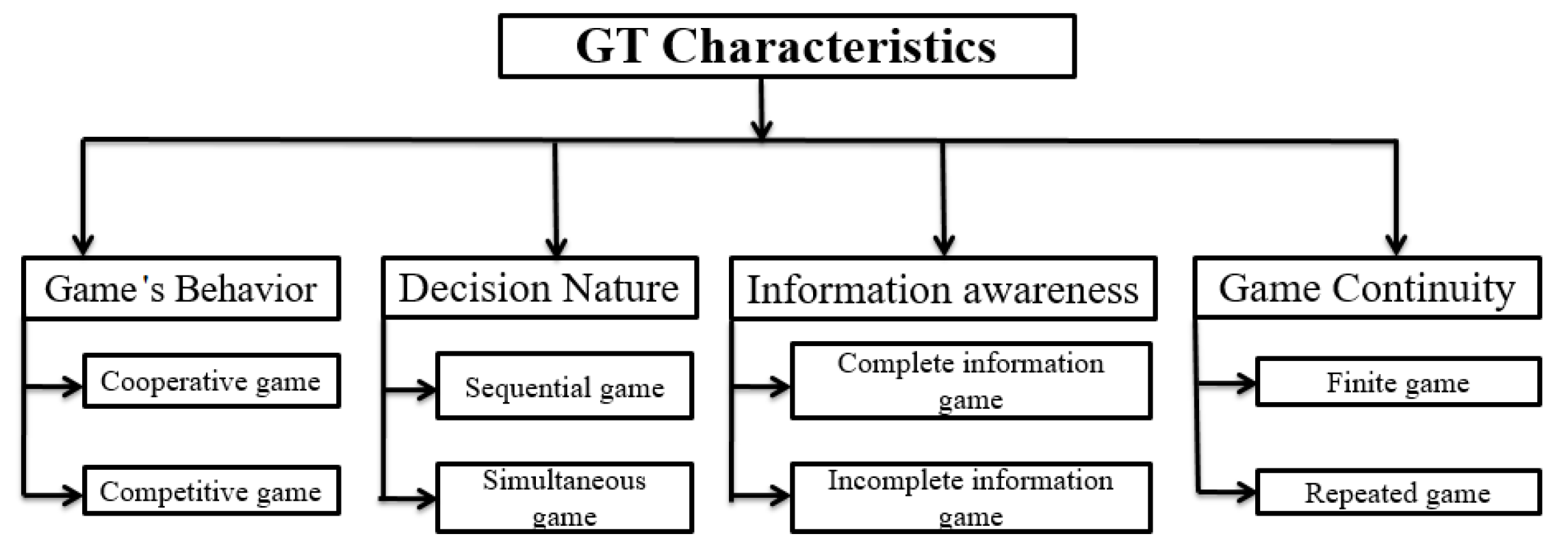
4.1. Game Theory Characteristics
4.1.1. Player’s Behavior
- Non-cooperative games: Each player takes the best strategy to maximize their winning comparing with the strategies of other players. Each player takes their decision and reason selfishly and individually without cooperating with other agents. In [40], a non-cooperative congestion game mechanism has been proposed to solve the service chain composition problem in NFV. Thus, the service chain configuration is converted to a mathematical game model for the seeking of Nash equilibrium.
- Cooperative games: The players cooperate by exchanging information to maximize the collective gain that does not necessarily favor a player’s victory at the expense of others. We can also talk about groups of players who can form coalitions and groups and choose a panel of strategies to increase the typical gain. Jose et al. [41] investigated a new security mechanism based on a cooperative game for resilient cyber-physical systems. Several cooperative and virtualized agents decide on a set of orchestrated management decisions to enable resilient system operation in the presence of a malicious agent or severe security threat.
4.1.2. Decision Nature
- Simultaneous games: Each player chooses at the beginning of the game his strategy, once and for all, without having information about what the other players will play. Otherwise, each participant makes the decision at the same time without exchanging information with other agents. In [42], a new simultaneous game model was proposed to optimize the network slicing placement problem for many NFV network slice use cases.
- Sequential games: The game’s exact sequence is specified from the beginning of the game. Each agent considers the set of actions available when it is its turn to play. According to the strategy taken previously by the opponent, the player takes the best strategy to win the game. Typically, a simultaneous game is represented in normal form as in the previous example, while a sequential game is naturally represented in the form of a tree. Laszlo et al. [43] proposed a new sequential pricing game of NFV infrastructure providers. The interaction between the infrastructure providers and the customers was formulated as a trade-off problem to be optimized in terms of price and resource allocation.
4.1.3. Information Awareness
- Complete information games: In the simplest case where players have the full information about the game (such as check games and ladies game), they know the entire game until the current stage. It is a sequential game where the players have an overview of the opponent’s game and possible strategies—for example, chess games. Therefore, the player’s current action influences the next action of the other adversaries. The authors, in [44], proposed a new complete information game-theoretical model in order to ensure the relatively resources allocation among tenants in 5G systems. To this end, a bankruptcy game based on new allocation rules was formulated to meet tenants’ needs by respecting the resource’s fair distribution.
- Incomplete information games: When the player has incomplete and limited knowledge about the opponents’ game and strategies, we talk about the game with incomplete information (for example, dominoes and poker). It is a game where a part of the game is hidden, and the player has only a portion of the information about other players. Decision-making is more critical and crucial than a perfect information game. In [45], a novel incomplete information game-based model was proposed for the cloud resource allocation. An auction game model was formulated to optimize the resource allocation between multiple infrastructure providers and the service providers. A Bayesian Nash equilibrium solution is reached to improve the network performance.
4.1.4. Game Continuity
- Finite games: This game is characterized by consistent and well-known boundaries and rules. During the game, the players focus on maximizing their utility functions because the purpose of the game is winning. Shu-Ting et al. [46] introduced a new finite game-based model to provide an optimized and efficient solution to the service chain composition problem in the network function virtualization paradigm. The service chain composition is converted to the seeking of the Nash equilibrium under the formulated game model.
- Infinite games: The game is repeated where the boundaries and the rules are dynamic and infinite. Thus, the players do not have any knowledge about the beginning or end of the game. The player’s purpose is to continue playing and to sometimes bring more players into the game. However, the infinite games are the less investigated concept in the NFV paradigm compared with the finite game modeling. No research paper solved the optimization problems in the NFV through the infinite game.
4.2. Game Goals
- 1
- Maximize bandwidth allocation: The importance of this objective becomes apparent with data-intensive applications. Real-time video services systems are the best examples [47].
- 2
- Maximizing power allocation: Applications that consider this objective are those with very limited energy capacity. The sensor network represents a good use case [48].
- 3
- Fairly allocate the physical resource: One of the most addressed goals for cellular applications such as LTE networks [49] is to efficiently manage the physical resources by sharing them fairly among mobile devices and user applications. Network slicing is a good example.
- 4
- Ensure load balancing: Nowadays, load balancing is becoming a necessity for many emerging applications that are very resource-intensive and require a balanced allocation in cloud computing environments [50].
- 5
- Reduce congestion: the object is to ensure secure and reliable communications with the congestion problem. The need for congestion control depends on the type of applications. For example, in the vehicular ad hoc network, this issue is crucial because a congested network can have a negative impact on the reaction time of the safety equipment and thus make driving less safe [51].
- 6
- Improving Fault Tolerance: Fault tolerance is an indispensable goal for many applications such as wireless sensor networks (WSNs). WSNs are characterized by limited sensor hardware resources, resulting in power depletion, non-rechargeable batteries, and physical failures. Improving fault tolerance [52,53] by maintaining network connectivity and coverage in the presence of faulty sensors is a challenge for WSNs.
- 7
- Security: Nowadays, and with the increasing number of attackers and cybercrimes, security is increasingly becoming a key challenge for any applications or environments where new threats and vulnerabilities are raided to target network features [54].
4.2.1. Goal 1: Maximize the Bandwidth Allocation
- Resource negotiation game: During the game, the SP starts by reclaiming the resource from the InP; then, it chooses to lease the resource from InP or to leave and to look for another one depending on the required QoS. Thus, the InP can admit or reject the request based on the resource sufficiency. The SP has a contract with an InP, so any direction to another InP can apply a penalty cost. When the two players are satisfied, the resource is allocated to the SP. However, if both players are dissatisfied, SP can lease the resource from another InP without any charged monetary penalty. Then, in case of only InP being satisfied, the SP must pay a penalty. The last case occurs when the SP is the only satisfied player; consequently, it is redirected to another InP without any charge. The players aim at maximizing their gains by reaching the Nash equilibrium.
- Node and link allocation games: two game models are proposed to fairly allocate the node and link resources for the SPs. The authors consider the SPs as a competitive player with selfish behaviors which aim at maximizing their utility function by consuming the maximum of the resources. The optimal solution for all players is achieved by the Nash equilibrium for each game.
4.2.2. Goal 2: Maximize the Power Allocation
4.2.3. Goal 3: Fairly Allocate the Physical Resource
4.2.4. Goal 4: Ensure the Load Balancing
4.2.5. Goal 5: To Reduce the Congestion
4.2.6. Goal 6: To Enhance the Fault Tolerance
4.2.7. Goal 7: To Ensure Security
4.3. Players during the Game
- The real players are nominated to present physical entities such as the service provider and the cloud provider. The game schemes based on those players try fundamentally to allocate enough resources to the lessees and to maximize the revenues of the lessors.
- The virtual players are designed to model virtual entities such as the virtual network, the task, and virtual machines. Thus, the interaction between the virtual players can address the virtual resource allocation by proactively preventing the network congestion and to prevent the future allocation to support the sharing of the resources between multi-tenants.
4.3.1. Virtual Network (VN)
4.3.2. Service/Cloud Provider
4.3.3. Virtual Operator
4.3.4. Virtual Machine
4.3.5. Task
5. Discussion and Future Research Directions
5.1. Cooperative Environment
5.2. Security and Resiliency
5.3. Traffic Management
5.4. Pricing
5.5. Resource and Service Management
5.6. Scalability
5.7. Decentralized Networks
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Pan, J.; Paul, S.; Jain, R. A Survey of the Research on Future Internet Architectures. IEEE Commun. Mag. 2011, 49, 26–36. [Google Scholar] [CrossRef]
- Han, B.; Gopalakrishnan, V.; Ji, L.; Lee, S. Network function virtualization: Challenges and opportunities for innovations. IEEE Commun. Mag. 2015, 53, 90–97. [Google Scholar] [CrossRef]
- Jain, R.; Paul, S. Network Virtualization and Software Defined Networking for Cloud Computing: A Survey. IEEE Commun. Mag. 2010, 51, 24–31. [Google Scholar] [CrossRef]
- Chowdhury, N.M.K.; Boutaba, R. A survey of network virtualization. Comput. Netw. 2010, 54, 862–876. [Google Scholar] [CrossRef]
- Turner, J.; Taylor, D. Diversifying the Internet. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM ’05), St. Louis, MO, USA, 28 November–2 December 2005; Volume 2. [Google Scholar]
- Feamster, N.; Gao, L.; Rexford, J. How to Lease the Internet in your Spare Time? SIGCOMM Comp. Commun. Revi. 2007, 37, 61–64. [Google Scholar] [CrossRef]
- Yang, L.; Ng, B.; Seah, W.K.; Groves, L.; Singh, D. A survey on network forwarding in Software-Defined Networking. J. Netw. Comput. Appl. 2021, 176, 102947. [Google Scholar] [CrossRef]
- Tipantuña, C.; Hesselbach, X. NFV/SDN Enabled Architecture for Efficient Adaptive Management of Renewable and Non-Renewable Energy. IEEE Open J. Commun. Soc. 2020, 1, 357–380. [Google Scholar] [CrossRef]
- Saha, D.; Shojaee, M.; Baddeley, M.; Haque, I. An Energy-Aware SDN/NFV Architecture for the Internet of Things. IFIP Netw. Conf. (Netw.) 2020, 1, 604–608. [Google Scholar]
- Bonfim, M.S.; Dias, K.L.; Fernandes, S.F.L. Integrated NFV/SDN Architectures: A Systematic Literature Review. ACM Comput. Surv. 2019, 51, 1–39. [Google Scholar] [CrossRef]
- Kim, Y.H.; Gil, J.M.; Kim, D. A location-aware network virtualization and reconfiguration for 5G core network based on SDN and NFV. Int. J. Commun. Syst. 2021, 34, e4160. [Google Scholar] [CrossRef]
- Sohrabi, M.K.; Azgomi, H. A Survey on the Combined Use of Optimization Methods and Game Theory. Arch. Comput. Methods Eng. 2020, 27, 59–80. [Google Scholar] [CrossRef]
- Riahi, S.; Riahi, A. Game theory for resource sharing in large distributed systems. Int. J. Electr. Comput. Eng. (IJECE) 2019, 9, 1249–1257. [Google Scholar] [CrossRef]
- Halpern, J.Y. Computer Science and Game Theory: A Brief Survey. arXiv 2007, arXiv:cs/0703148. [Google Scholar]
- Wismans, L.J.; Brands, T.; Van Berkum, E.C.; Bliemer, M.C. Pruning and ranking the Pareto optimal set, application for the dynamic multi-objective network design problem. J. Adv. Transp. 2014, 48, 588–607. [Google Scholar] [CrossRef]
- Moeini, A.; Foumani, M.; Jenab, K. Utilisation of pruned Pareto-optimal solutions in the multi objective optimisation: An application to system redundancy allocation problems. Int. J. Appl. Decis. Sci. 2013, 6, 50–65. [Google Scholar] [CrossRef]
- Wang, C.; Yuan, Y. Game based dynamical bandwidth allocation model for virtual networks. In Proceedings of the 2009 First International Conference on Information Science and Engineering, Nanjing, China, 26–28 December 2009. [Google Scholar]
- Zhou, Y.; Li, Y.; Sun, G.; Jin, D.; Su, L.; Zeng, L. Game Theory Based Bandwidth Allocation Scheme for Network Virtualization. In Proceedings of the 2010 IEEE Global Telecommunications Conference GLOBECOM 2010, Miami, FL, USA, 6–10 December 2010. [Google Scholar]
- Seddiki, M.S.; Frikha, M.; Song, Y.Q. A non-cooperative game-theoretic framework for resource allocation in network virtualization. Telecommun. Syst. 2016, 61, 209–219. [Google Scholar] [CrossRef]
- Wang, C.R.; Liu, K.; Wang, C. Game Based Virtual Bandwidth Allocation for Virtual Networks in Data Centers. Procedia Eng. 2011, 23, 780–785. [Google Scholar] [CrossRef] [Green Version]
- Fangwen, F.; Kozat, U.C. Wireless network virtualization as a sequential auction game. In Proceedings of the 2010 Proceedings IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010. [Google Scholar]
- Guo, J.; Liu, F.; Lui, J.C.; Jin, H. Fair Network Bandwidth Allocation in IaaS Datacenters via a Cooperative Game Approach. IEEE/ACM Trans. Netw. 2016, 24, 873–886. [Google Scholar] [CrossRef]
- Wei, J.; Yang, K.; Zhang, G.; Hu, Z. Pricing-based Power Allocation in Wireless Network Virtualization: A Game Approach. In Proceedings of the 2015 International Wireless Communications and Mobile Computing Conference (IWCMC), Dubrovnik, Croatia, 24–28 August 2015. [Google Scholar]
- Fan, B.; Tian, H.; Liu, B. Game Theory Based Power Allocation in LTE Air Interface Virtualization. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015. [Google Scholar]
- Yuan, Y.; Wang, C.R.; Wang, C. A Game Based Approach for Sharing the Data Center Network. Int. Symp. Neural Netw. 2012, 7367, 641–649. [Google Scholar]
- Teng, F.; Magoules, F. Resource pricing and equilibrium allocation policy in cloud computing. In Proceedings of the 2010 10th IEEE International Conference on Computer and Information Technology, Bradford, UK, 29 June–1 July 2010. [Google Scholar]
- Iyer, G.N.; Veeravalli, B. On the Resource Allocation and Pricing Strategies in Compute Clouds Using Bargaining Approaches. In Proceedings of the 2011 17th IEEE International Conference on Networks, Singapore, 14–16 December 2011. [Google Scholar]
- Wei, W.; Fan, X.; Song, H.; Fan, X.; Yang, J. Imperfect Information Dynamic Stackelberg Game Based Resource Allocation Using Hidden Markov for Cloud Computing. IEEE Trans. Serv. Comput. 2018, 11, 78–89. [Google Scholar] [CrossRef]
- Liu, B.; Tian, H. A Bankruptcy Game-Based Resource Allocation Approach among Virtual Mobile Operators. IEEE Commun. Lett. 2013, 17, 1420–1423. [Google Scholar]
- Subrata, R.; Zomaya, A.Y.; Landfeldt, B. Game-Theoretic Approach for Load Balancing in Computational Grids. IEEE Trans. Parallel Distrib. Syst. 2008, 19, 66–76. [Google Scholar] [CrossRef]
- Khan, M.A.; Foix-Cablé, V.; Yalin, L.; Despotovic, Z. Autonomic Load Balancing In The Future Disintegrated And Virtualized Netwoks. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Istanbul, Turkey, 6–9 April 2014. [Google Scholar]
- Ardagna, D.; Panicucci, B.; Passacantando, M. A Game Theoretic Formulation of the Service Provisioning Problem in Cloud Systems. In Proceedings of the 20th International Conference on World Wide Web; ACM: New York, NY, USA, 2011. [Google Scholar]
- Niyato, D.; Vasilakos, A.V.; Kun, Z. Resource and Revenue Sharing with Coalition Formation of Cloud Providers: Game Theoretic Approach. In Proceedings of the 2011 11th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, Newport Beach, CA, USA, 23–26 May 2011. [Google Scholar]
- Ye, D.; Chen, J. Non-cooperative games on multidimensional resource allocation. Future Gener. Comput. Syst. 2013, 29, 1345–1352. [Google Scholar] [CrossRef]
- Elias, J.; Martignon, F.; Paris, S.; Wang, J. Efficient Orchestration Mechanisms for Congestion Mitigation in NFV: Models and Algorithms. IEEE Trans. Serv. Comput. 2017, 10, 534–546. [Google Scholar] [CrossRef] [Green Version]
- Pham, C.; Tran, N.H.; Hong, C.S. Virtual Network Function Scheduling: A Matching Game Approach. IEEE Commun. Lett. 2017, 22, 69–72. [Google Scholar] [CrossRef]
- Wei, G.; Vasilakos, A.V.; Xiong, N. Scheduling Parallel Cloud Computing Services: An Evolutional Game. In Proceedings of the 2009 First International Conference on Information Science and Engineering, Nanjing, China, 26–28 December 2009. [Google Scholar]
- Soualah, O.; Fajjari, I.; Aitsaadi, N.; Mellouk, A. A Reliable Virtual Network Embedding Algorithm based on Game Theory within Cloud’s backbone. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014. [Google Scholar]
- Chowdhary, A.; Pisharody, S.; Alshamrani, A.; Huang, D. Dynamic Game based Security framework in SDN-enabled Cloud Networking Environments. In Proceedings of the ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization; ACM: New York, NY, USA, 2017; pp. 53–58. [Google Scholar]
- Le, S.; Wu, Y.; Toyoda, M. A congestion game framework for service chain composition in NFV with function benefit. Inf. Sci. 2020, 514, 512–522. [Google Scholar] [CrossRef]
- Moura, J.; Hutchison, D. Resilient Cyber-Physical Systems: Using NFV Orchestration. arXiv 2020, arXiv:2003.12401. [Google Scholar]
- Esteves, J.J.A.; Boubendir, A.; Guillemin, F.; Sens, P. Optimized Network Slicing Proof-of-Concept with Interactive Gaming Use Case. In Proceedings of the 2020 23rd Conference on Innovation in Clouds, Internet and Networks and Workshops (ICIN), Paris, France, 24–27 February 2020. [Google Scholar]
- Toka, L.; Zubor, M.; Korosi, A.; Darzanos, G.; Rottenstreich, O.; Sonkoly, B. Pricing games of NFV infrastructure providers. Telecommun. Syst. 2020, 76, 219–232. [Google Scholar] [CrossRef]
- Fossati, F.; Hoteit, S.; Moretti, S.; Secci, S. Fair Resource Allocation in Systems With Complete Information Sharing. IEEE/ACM Trans. Netw. 2018, 26, 2801–2814. [Google Scholar] [CrossRef]
- Li, Q.; Huang, C.; Bao, H.; Fu, B.; Jia, X. A Game-based Combinatorial Double Auction Model for Cloud Resource Allocation. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019. [Google Scholar]
- Le, S.T.; Wu, Y.; Sun, X.M. A Game Theoretic Approach for Service Chain Composition in Network Function Virtualization Network. In Proceedings of the 2019 Chinese Control Conference (CCC), Guangzhou, China, 27–30 July 2019. [Google Scholar]
- Wang, C.; Zhang, S.; Chen, Y.; Qian, Z.; Wu, J.; Xiao, M. Joint Configuration Adaptation and Bandwidth Allocation for Edge-based Real-time Video Analytics. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020. [Google Scholar]
- Hammood, D.A.; Alkhayyat, A.; Rahim, H.A.; Ahmad, R.B. Minimum Power Allocation Cooperative Communication based on Health-Care WBAN. Photonic Netw. Commun. 2020, 40, 194–208. [Google Scholar] [CrossRef]
- Alfoudi, A.S.D.; Newaz, S.S.; Otebolaku, A.; Lee, G.M.; Pereira, R. An Efficient Resource Management Mechanism for Network Slicing in a LTE Network. IEEE Access 2019, 7, 89441–89457. [Google Scholar] [CrossRef]
- Mishra, S.K.; Sahoo, B.; Parida, P.P. Load balancing in cloud computing: A big picture. J. King Saud Univ. Comput. Inf. Sci. 2020, 32, 149–158. [Google Scholar] [CrossRef]
- Singh, J.; Singh, K. Congestion Control in Vehicular Ad Hoc Network: A Review. Next Gener. Netw. 2017, 489–496. [Google Scholar] [CrossRef]
- Idoudi, H.; Bennaceur, J. Fault Tolerant Placement Strategy for WSN. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016. [Google Scholar]
- Shankar, A.; Sivakumar, N.R.; Sivaram, M.; Ambikapathy, A.; Nguyen, T.K.; Dhasarathan, V. Increasing fault tolerance ability and network lifetime with clustered pollination in wireless sensor networks. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 2285–2298. [Google Scholar] [CrossRef]
- Berdik, D.; Otoum, S.; Schmidt, N.; Porter, D.; Jararweh, Y. A Survey on Blockchain for Information Systems Management and Security. Inf. Process. Manag. 2021, 58, 102397. [Google Scholar] [CrossRef]
- Rath, K.P. A direct proof of the existence of pure strategy equilibria in games with a continuum of players. Econ. Theory 1992, 2, 427–433. [Google Scholar] [CrossRef]
- Ghomi, E.J.; Rahmani, A.M.; Qader, N.N. Load-balancing algorithms in cloud computing: A survey. J. Netw. Comput. Appl. 2017, 88, 50–71. [Google Scholar] [CrossRef]
- D’Oro, S.; Galluccio, L.; Palazzo, S.; Schembra, G. Exploiting Congestion Games to Achieve Distributed Service Chaining in NFV Networks. IEEE J. Sel. Areas Commun. 2017, 35, 407–420. [Google Scholar] [CrossRef]
- Yan, Q.; Yu, F.R.; Gong, Q.; Li, J. Software-Defined Networking (SDN) and Distributed Denial of Service (DDoS) Attacks in Cloud Computing Environments: A Survey, Some Research Issues, and Challenges. IEEE Commun. Surv. Tutor. 2016, 18, 602–622. [Google Scholar] [CrossRef]
- Fischer, A.; Botero, J.F.; Beck, M.T.; De Meer, H.; Hesselbach, X. Virtual Network Embedding: A Survey. IEEE Trans. Netw. Serv. Manag. 2013, 15, 1888–1906. [Google Scholar] [CrossRef]
- Duan, Q.; Yan, Y.; Vasilakos, A.V. A Survey on Service-Oriented Network Virtualization Toward Convergence of Networking and Cloud Computing. IEEE Trans. Netw. Serv. Manag. 2012, 9, 373–392. [Google Scholar] [CrossRef]
- Sultan, N. Cloud computing for education: A new dawn? Int. J. Inf. Manag. 2010, 20, 109–116. [Google Scholar] [CrossRef]
- Clippel, G. Membership separability: A new axiomatization of the Shapley value. Games Econ. Behav. 2018, 108, 125–129. [Google Scholar] [CrossRef]
- Wang, T.; Liu, F.; Guo, J.; Xu, H. Dynamic SDN controller assignment in data center networks: Stable matching with transfers. In Proceedings of the IEEE INFOCOM 2016—The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar]
- Niazi, R.A.; Faheem, Y. A Bayesian Game-Theoretic Intrusion Detection System for Hypervisor-Based Software Defined Networks in Smart Grids. IEEE Access 2019, 7, 88656–88672. [Google Scholar] [CrossRef]
- Yang, S.; Li, F.; Trajanovski, S.; Yahyapour, R.; Fu, X. Recent Advances of Resource Allocation in Network Function Virtualization. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 295–314. [Google Scholar] [CrossRef]
- Hohlfeld, O.; Kempf, J.; Reisslein, M.; Schmid, S.; Shah, N. Guest editorial scalability issues and solutions for software defined networks. IEEE J. Sel. Areas Commun. 2018, 36, 2592–2602. [Google Scholar] [CrossRef]
- Hu, T.; Guo, Z.; Yi, P.; Baker, T.; Lan, J. Multi-controller based software-defined networking: Asurvey. IEEE Access 2018, 6, 15980–15996. [Google Scholar] [CrossRef]
- Gao, J.; Tembine, H. Empathy and Berge equilibria in the Forwarding Dilemma in Relay-Enabled Networks. In Proceedings of the 2017 International Conference on Wireless Networks and Mobile Communications (WINCOM), Rabat, Morocco, 1–4 November 2017. [Google Scholar]
- Aslam, S.; Alam, F.; Hasan, S.F.; Rashid, M. Decentralized Interference Mitigation Technique for D2D Networks Using Game Theory Optimization. In Proceedings of the 29th International Telecommunication Networks and Applications Conference (ITNAC), Auckland, New Zealand, 27–29 November 2019. [Google Scholar]



| Approaches | Game’s Behaviour | Decision Nature | Information Awareness | Game Continuity | |||||
|---|---|---|---|---|---|---|---|---|---|
| Cooperative | Non-Cooperative | Sequential | Simultaneous | Complete Information | Incomplete Information | Finite | Repeated | ||
| Wang et al. [17] | ✓ | ✓ | ✓ | ✓ | |||||
| Zhou et al. [18] | ✓ | ✓ | ✓ | ✓ | |||||
| Seddiki et al. [19] | ✓ | ✓ | ✓ | ✓ | |||||
| Wang et al. [20] | ✓ | ✓ | ✓ | ✓ | |||||
| Fangwen et al. [21] | ✓ | ✓ | ✓ | ✓ | |||||
| Guo et al. [22] | ✓ | ✓ | ✓ | ✓ | |||||
| Wei et al. [23] | ✓ | ✓ | ✓ | ✓ | |||||
| Fan et al. [24] | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| Yuan et al. [25] | ✓ | ✓ | ✓ | ✓ | |||||
| Teng et al. [26] | ✓ | ✓ | ✓ | ✓ | |||||
| Iyer et al. [27] | ✓ | ✓ | ✓ | ✓ | |||||
| Wei et al. [28] | ✓ | ✓ | ✓ | ✓ | |||||
| Liu et al. [29] | ✓ | ✓ | ✓ | ✓ | |||||
| Subrata et al. [30] | ✓ | ✓ | ✓ | ✓ | |||||
| Khan et al. [31] | ✓ | ✓ | ✓ | ✓ | |||||
| Ardagna et al. [32] | ✓ | ✓ | ✓ | ✓ | |||||
| Niyato et al. [33] | ✓ | ✓ | ✓ | ✓ | |||||
| Ye et al. [34] | ✓ | ✓ | ✓ | ✓ | |||||
| Elias et al. [35] | ✓ | ✓ | ✓ | ✓ | |||||
| Pham et al. [36] | ✓ | ✓ | ✓ | ✓ | |||||
| Wei et al. [37] | ✓ | ✓ | ✓ | ✓ | |||||
| Soualah et al. [38] | ✓ | ✓ | ✓ | ✓ | |||||
| Chowdhary et al. [39] | ✓ | ✓ | ✓ | ✓ | |||||
| P2 Cooperates | P2 Defects | |
|---|---|---|
| P1 cooperates | , | , |
| P1 defects | , | , |
| (a) GT solutions comparison in terms of players | |
| Players | Approaches |
| Virtual Networks | Wang et al. [17] |
| Wang et al. [20] | |
| Yuan et al. [25] | |
| Service Providers | Zhou et al. [18] |
| Seddiki et al. [19] | |
| Fangwen et al. [21] | |
| Wei et al. [28] | |
| Khan et al. [31] | |
| Virtual operators | Wei et al. [23] |
| Fan et al. [24] | |
| Teng et al. [26] | |
| Liu et al. [29] | |
| Elias et al. [35] | |
| Virtual machine | Guo et al. [22] |
| Ye et al. [34] | |
| Task | Guo et al. [22] |
| Subrata et al. [30] | |
| Wei et al. [28] | |
| Iyer et al. [27] | |
| Others | Ardagna et al. [32] |
| Niyato et al. [33] | |
| Pham et al. [36] | |
| Soualah et al. [38] | |
| Chowdhary et al. [39] | |
| Salvatore D’Oro et al. [57] | |
| (b) GT solutions comparison in terms of goals | |
| Goals | Approaches |
| Maximize the bandwidth allocation | Wang et al. [17] |
| Zhou et al. [18] | |
| Seddiki et al. [19] | |
| Yuan et al. [25] | |
| Cui-rong Wang et al. [20] | |
| Maximize the power allocation | Fangwen et al. [21] |
| Wei et al. [23] | |
| Fan et al. [24] | |
| Fairly allocate the resources | Teng et al. [26] |
| Iyer et al. [27] | |
| Guo et al. [22] | |
| Wei et al. [28] | |
| Ardagna et al. [32] | |
| Niyato et al. [33] | |
| Liu et al. [29] | |
| Wei et al. [37] | |
| Ensure the load balancing | Subrata et al. [30] |
| Khan et al. [31] | |
| Ye et al. [34] | |
| Reduce the congestion | Elias et al. [35] |
| Salvatore D’Oro et al. [57] | |
| Pham et al. [36] | |
| Soualah et al. [38] | |
| Enhance the fault tolerance | Ardagna et al. [32] |
| Ensure security | Chowdhary et al. [39] |
| Benefits | Limitations |
|---|---|
| Low complexity | Abrupt failure |
| Efficient resource management | Security issues |
| Economical | Bottlenecks problem and latency |
| Easy control and Quick updates | Single point of failure |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bennaceur, J.; Ahmadi, H.; Souhi, S. Game-Theoretical Approaches for Service Provisioning in Network Virtualization: Survey, Taxonomies and Open Challenges. Telecom 2021, 2, 232-254. https://doi.org/10.3390/telecom2030016
Bennaceur J, Ahmadi H, Souhi S. Game-Theoretical Approaches for Service Provisioning in Network Virtualization: Survey, Taxonomies and Open Challenges. Telecom. 2021; 2(3):232-254. https://doi.org/10.3390/telecom2030016
Chicago/Turabian StyleBennaceur, Jihen, Hanen Ahmadi, and Sami Souhi. 2021. "Game-Theoretical Approaches for Service Provisioning in Network Virtualization: Survey, Taxonomies and Open Challenges" Telecom 2, no. 3: 232-254. https://doi.org/10.3390/telecom2030016
APA StyleBennaceur, J., Ahmadi, H., & Souhi, S. (2021). Game-Theoretical Approaches for Service Provisioning in Network Virtualization: Survey, Taxonomies and Open Challenges. Telecom, 2(3), 232-254. https://doi.org/10.3390/telecom2030016







