A Conditional Generative Adversarial Network Based Approach for Network Slicing in Heterogeneous Vehicular Networks
Abstract
1. Introduction
- When considering the advantages of SDN and NFV concepts and the notion of network slicing, how can we design an architecture that provides reliable information to create HetVNET slices?
- augment the data used in creating network slices in HetVNET; and
- additionally, propose a centralized SDN based architecture with the aim of enhancing flexibility and adaptability of the HetVNET.
2. Related Work
3. Methodology
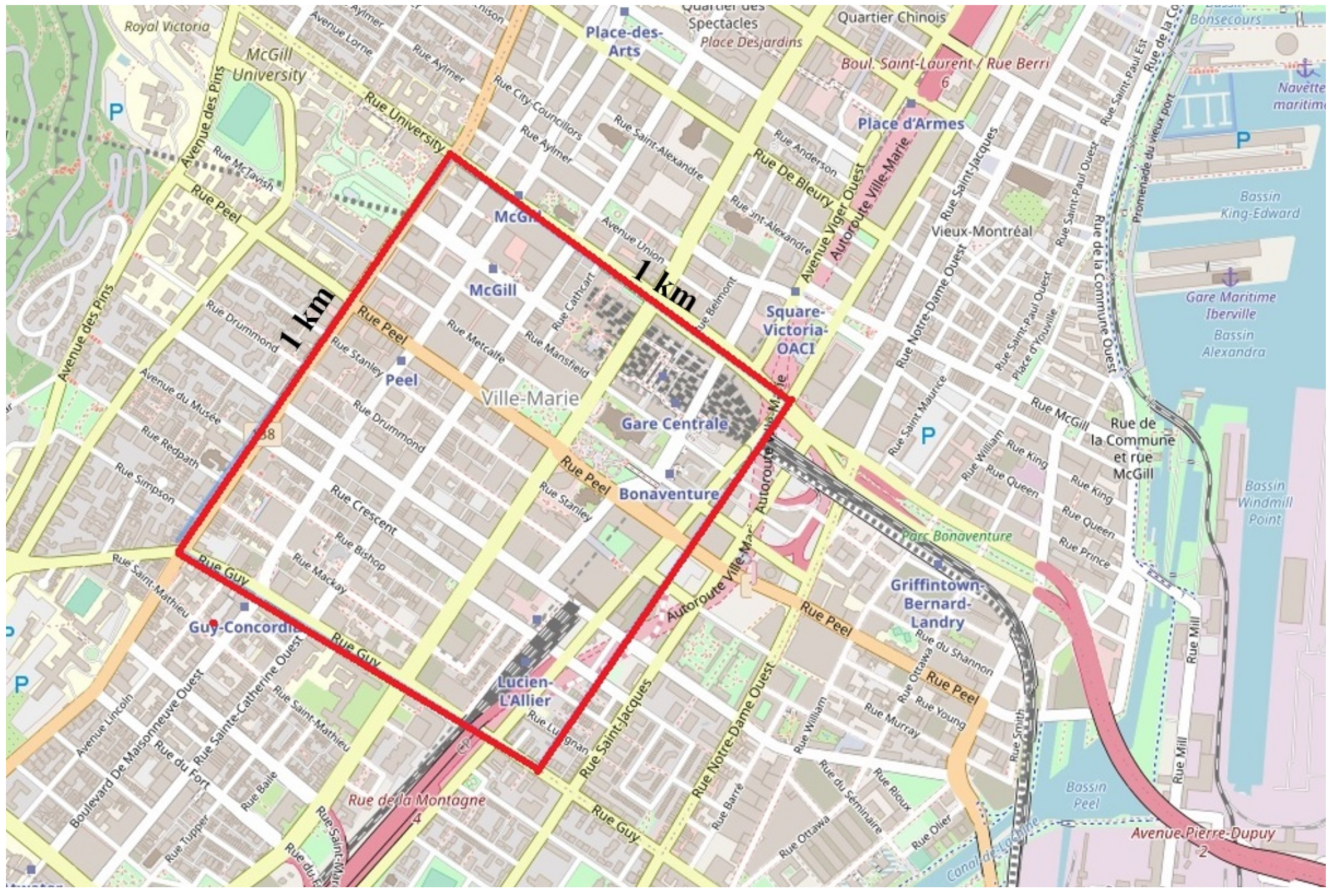
3.1. Generating Dataset Using Simulation Scenarios
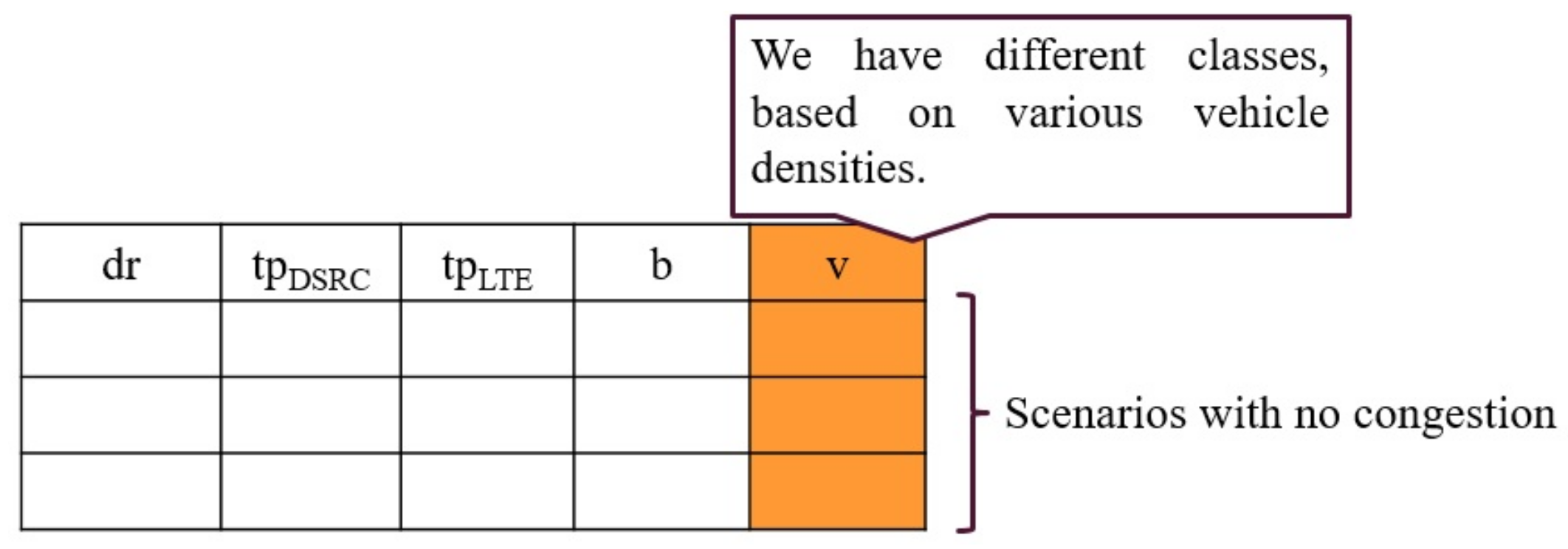
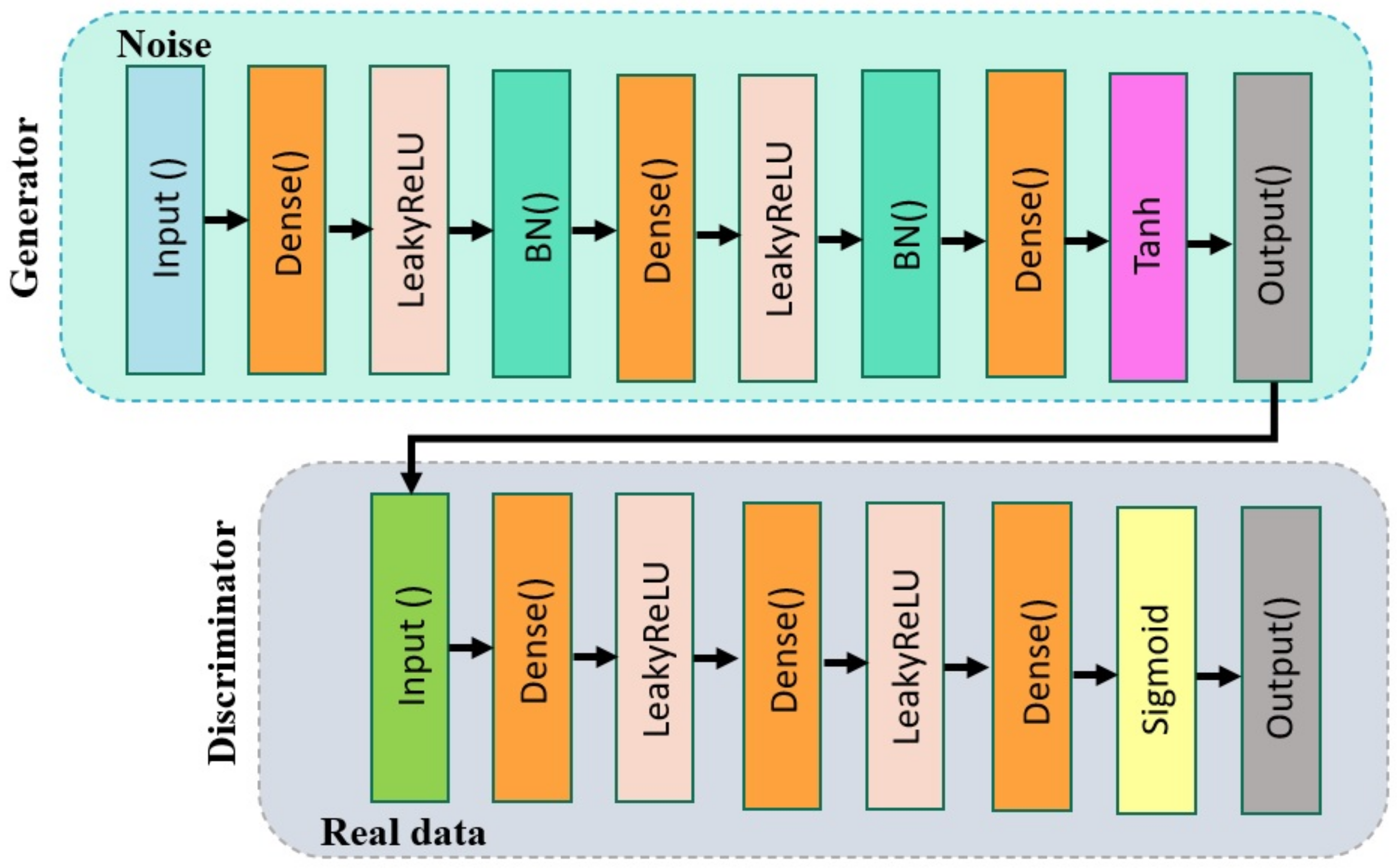
3.2. Proposing CGAN Model for HetVNET
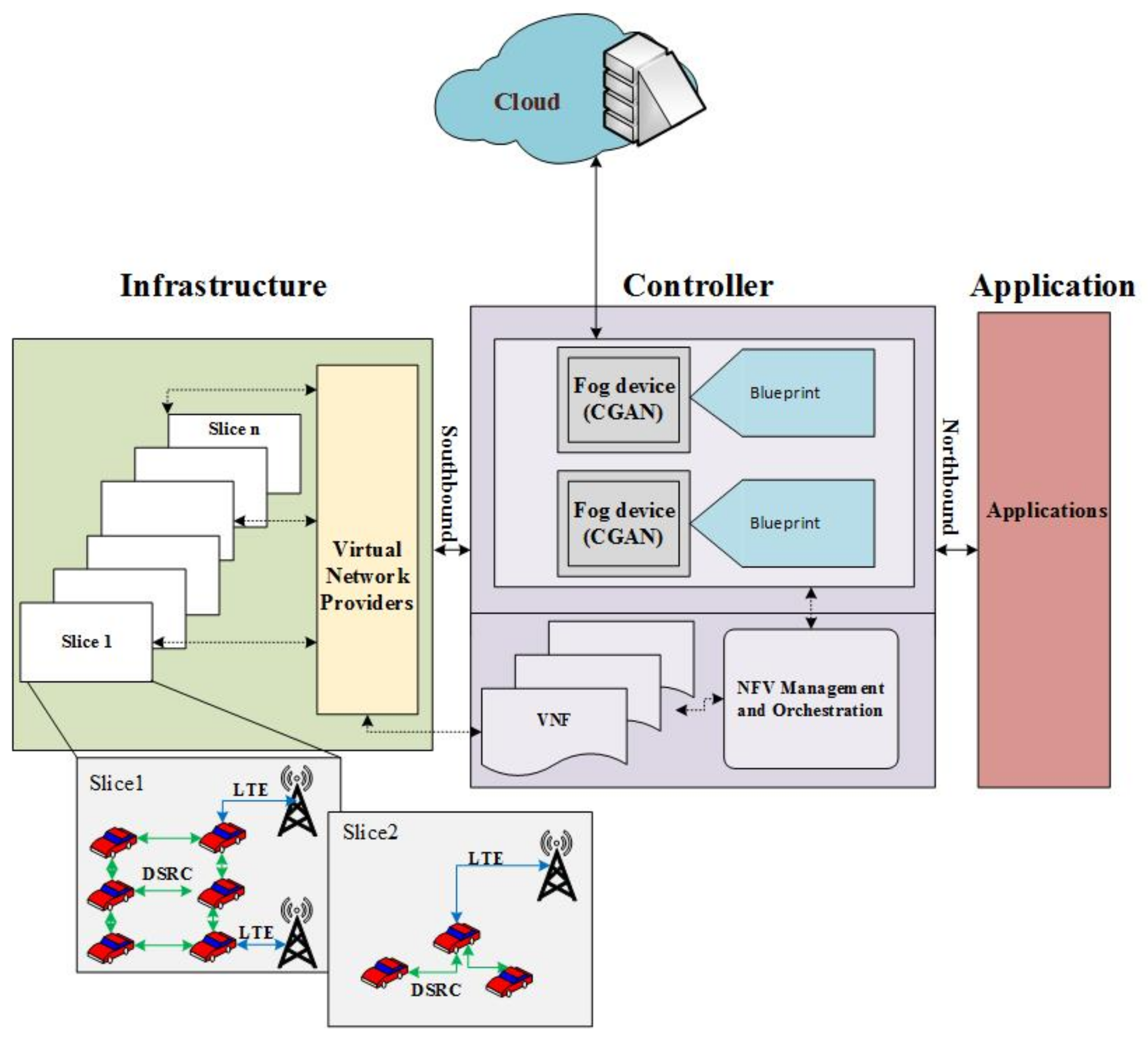
3.3. A Hybrid CGAN-SDN Architecture
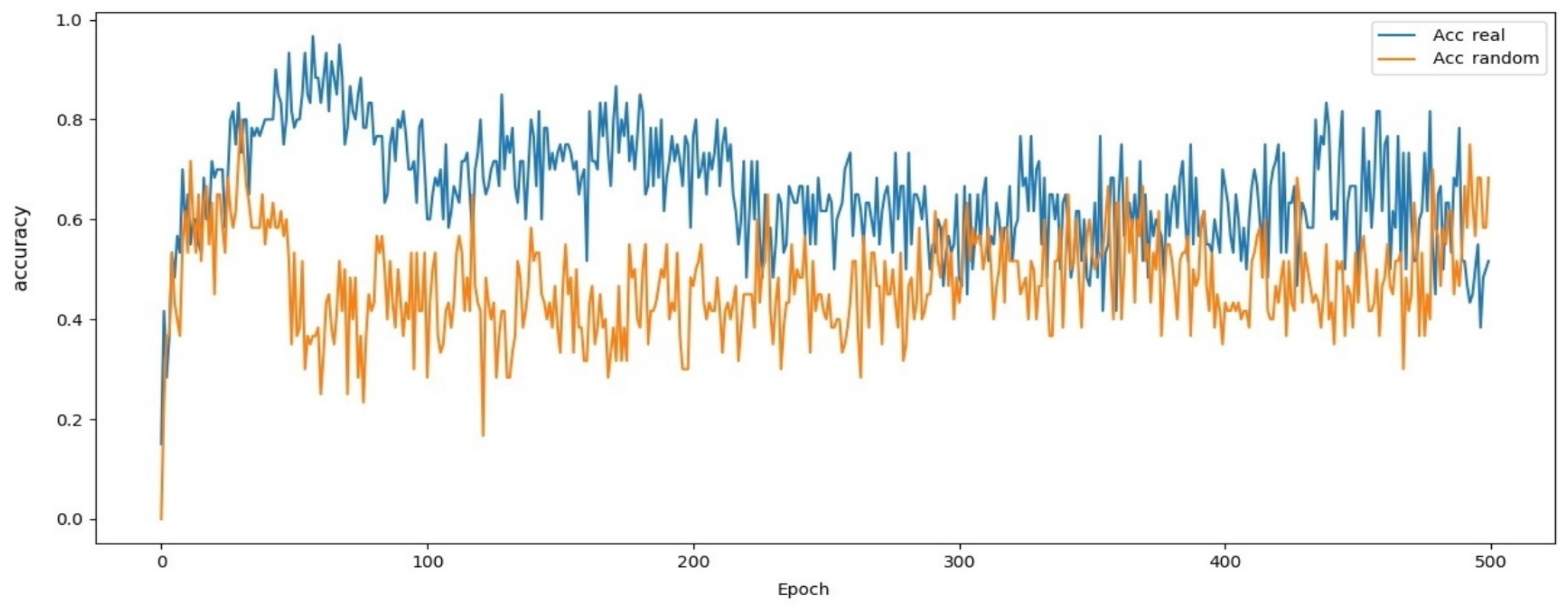
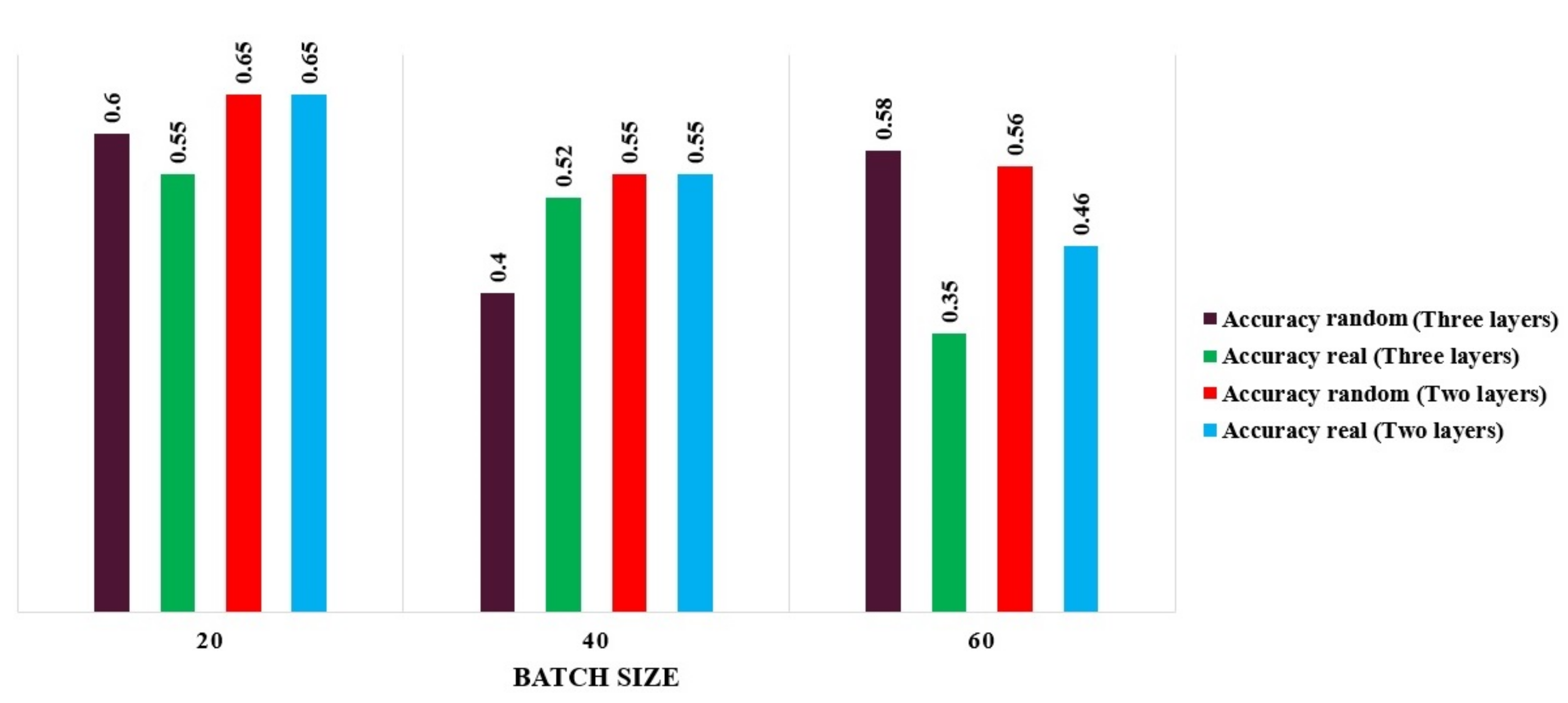
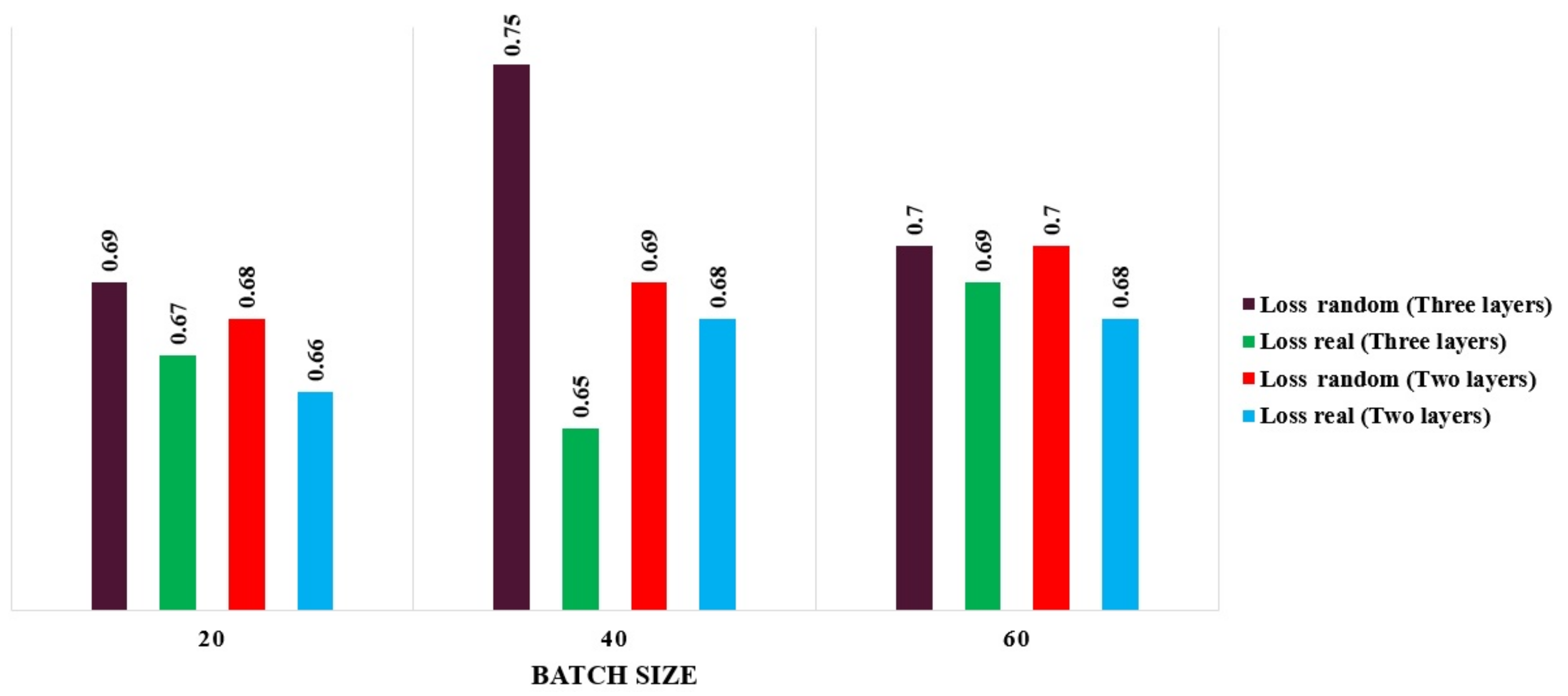
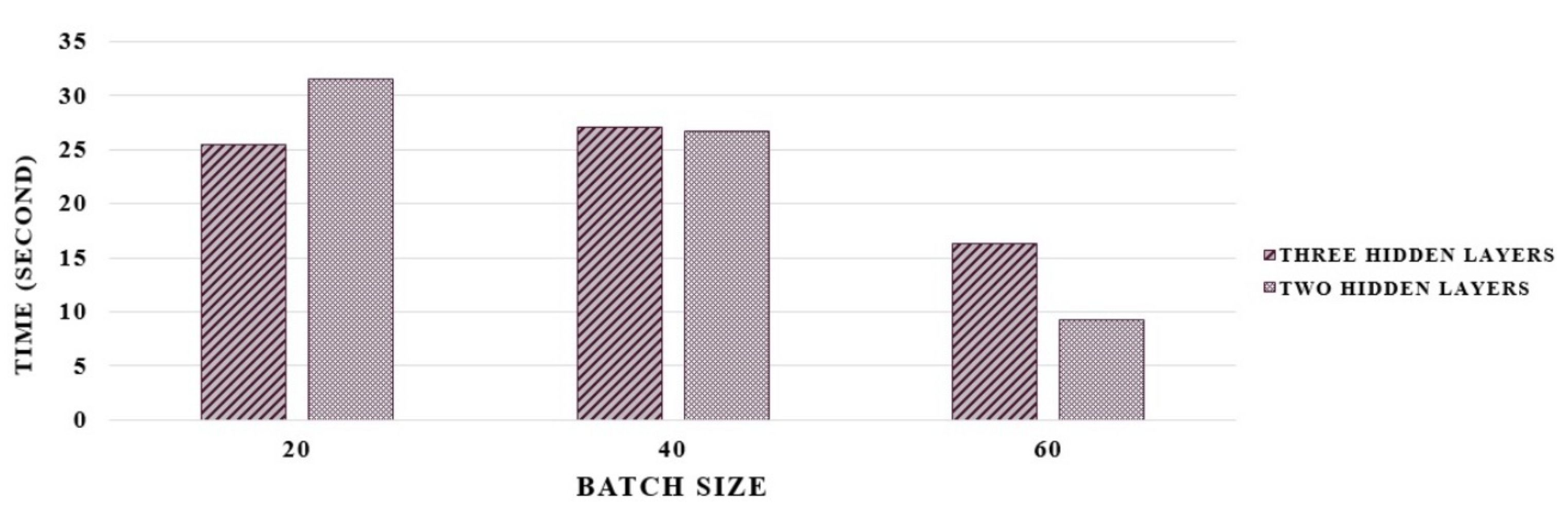
4. The Proposed CGAN Model Performance Evaluation
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Duan, Q.; Ansari, N.; Toy, M. Software-defined network virtualization: An architectural framework for integrating SDN and NFV for service provisioning in future networks. IEEE Netw. 2016, 30, 10–16. [Google Scholar] [CrossRef]
- Herrera, J.G.; Botero, J.F. Resource allocation in NFV: A comprehensive survey. IEEE Trans. Netw. Serv. Manag. 2016, 13, 518–532. [Google Scholar] [CrossRef]
- Gomes, R.L.; Bittencourt, L.F.; Madeira, E.R.M.; Cerqueira, E.C.; Gerla, M. Software-defined management of edge as a service networks. IEEE Trans. Netw. Serv. Manag. 2016, 13, 226–239. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, N.; Chu, X.; Long, K.; Aghvami, A.-H.; Leung, V.C. Network slicing based 5g and future mobile networks: Mobility, resource management, and challenges. IEEE Commun. Mag. 2017, 55, 138–145. [Google Scholar] [CrossRef]
- Zhou, X.; Li, R.; Chen, T.; Zhang, H. Network slicing as a service: Enabling enterprises’ own software-defined cellular networks. IEEE Commun. Mag. 2016, 54, 146–153. [Google Scholar] [CrossRef]
- Rost, P.; Mannweiler, C.; Michalopoulos, D.S.; Sartori, C.; Sciancalepore, V.; Sastry, N.; Holland, O.; Tayade, S.; Han, B.; Bega, D.; et al. Network slicing to enable scalability and flexibility in 5G mobile networks. IEEE Commun. Mag. 2017, 55, 72–79. [Google Scholar] [CrossRef]
- Foukas, X.; Patounas, G.; Elmokashfi, A.; Marina, M.K. Network slicing in 5G: Survey and challenges. IEEE Commun. Mag. 2017, 55, 94–100. [Google Scholar] [CrossRef]
- Falahatraftar, F.; Pierre, S.; Chamberland, S. A Multiple Linear Regression Model for Predicting Congestion in Heterogeneous Vehicular Networks. In Proceedings of the 2020 16th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Thessaloniki, Greece, 12–14 October 2020; pp. 93–98. [Google Scholar]
- Soto, I.; Amador, O.; Urueña, M.; Calderon, M. Strengths and weaknesses of the ETSI adaptive DCC algorithm: A proposal for improvement. IEEE Commun. Lett. 2019, 23, 802–805. [Google Scholar] [CrossRef]
- Amador, O.; Soto, I.; Calderon, M.; Urueña, M. Experimental Evaluation of the ETSI DCC Adaptive Approach and Related Algorithms. IEEE Access 2020, 8, 49798–49811. [Google Scholar] [CrossRef]
- Lyamin, N.; Vinel, A.; Smely, D.; Bellalta, B. ETSI DCC: Decentralized Congestion Control in C-ITS. IEEE Commun. Mag. 2018, 56, 112–118. [Google Scholar] [CrossRef]
- Shen, X.; Gao, J.; Wu, W.; Lyu, K.; Li, M.; Zhuang, W.; Li, X.; Rao, J. AI-assisted network-slicing based next-generation wireless networks. IEEE Open J. Veh. Technol. 2020, 1, 45–66. [Google Scholar] [CrossRef]
- Jiacheng, C.; Haibo, Z.; Ning, Z.; Peng, Y.; Lin, G.; Sherman, S.X. Software defined internet of vehicles: Architecture, challenges and solutions. J. Commun. Inf. Netw. 2016, 1, 14–26. [Google Scholar] [CrossRef]
- Davy, S.; Famaey, J.; Serrat, J.; Gorricho, J.L.; Miron, A.; Dramitinos, M.; Neves, P.M.; Latre, S.; Goshen, E. Challenges to support edge-as-a-service. IEEE Commun. Mag. 2014, 52, 132–139. [Google Scholar] [CrossRef][Green Version]
- Tayyaba, S.K.; Khattak, H.A.; Almogren, A.; Shah, M.A.; Din, I.U.; Alkhalifa, I.; Guizani, M. 5G Vehicular Network Resource Management for Improving Radio Access Through Machine Learning. IEEE Access 2020, 8, 6792–6800. [Google Scholar]
- Campolo, C.; Molinaro, A.; Iera, A.; Fontes, R.R.; Rothenberg, C.E. Towards 5G network slicing for the V2X ecosystem. In Proceedings of the 2018 4th IEEE Conference on Network Softwarization and Workshops (NetSoft), Montreal, QC, Canada, 25–29 June 2018; pp. 400–405. [Google Scholar]
- Cui, Y.; Zheng, H.; Wang, H.; Wu, D. An Intelligent Coordinator Design for Network Slicing in Service-Oriented Vehicular Networks. In Proceedings of the GLOBECOM 2020–2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Khan, H.; Samarakoon, S.; Bennis, M. Enhancing video streaming in vehicular networks via resource slicing. IEEE Trans. Veh. Technol. 2020, 69, 3513–3522. [Google Scholar] [CrossRef]
- Mei, J.; Wang, X.; Zheng, K. Intelligent Network Slicing for V2X Services Toward 5G. IEEE Netw. 2019, 33, 196–204. [Google Scholar] [CrossRef]
- Chen, Y.; Wang, Y.; Liu, M.; Zhang, J.; Jiao, L. Network Slicing Enabled Resource Management for Service-Oriented Ultra-Reliable and Low-Latency Vehicular Networks. IEEE Trans. Veh. Technol. 2020, 69, 7847–7862. [Google Scholar] [CrossRef]
- Khan, H.; Luoto, P.; Bennis, M.; Latva-aho, M. On the Application of Network Slicing for 5G-V2X. In Proceedings of the 24th European Wireless Conference, Catania, Italy, 2–4 May 2018; pp. 1–6. [Google Scholar]
- Sanchez-Iborra, R.; Santa, J.; Gallego-Madrid, J.; Covaci, S.; Skarmeta, A. Empowering the Internet of vehicles with multi-RAT 5G network slicing. Sensors 2019, 19, 3107. [Google Scholar] [CrossRef]
- Wu, H.W.Y.; Min, G.; Xu, J.; Tang, P. Data-driven dynamic resource scheduling for network slicing: A deep reinforcement learning approach. Inf. Sci. 2019, 498, 106–116. [Google Scholar]
- Koo, J.; Mendiratta, V.B.; Rahman, M.R.; Walid, A. Deep reinforcement learning for network slicing with heterogeneous resource requirements and time varying traffic dynamics. In Proceedings of the 2019 15th International Conference on Network and Service Management (CNSM), Halifax, NS, Canada, 21–25 October 2019; pp. 1–5. [Google Scholar]
- Cui, Y.; Huang, X.; Wu, D.; Zheng, H. Machine Learning based Resource Allocation Strategy for Network Slicing in Vehicular Networks. In Proceedings of the 2020 IEEE/CIC International Conference on Communications in China (ICCC), Chongqing, China, 9–11 August 2020; pp. 454–459. [Google Scholar]
- Xiong, K.; Leng, S.; Hu, J.; Chen, X.; Yang, K. Smart network slicing for vehicular fog-RANs. IEEE Trans. Veh. Technol. 2019, 68, 3075–3085. [Google Scholar] [CrossRef]
- Khan, H.; Luoto, P.; Samarakoon, S.; Bennis, M.; Latva-Aho, M. Network slicing for vehicular communication. Trans. Emerg. Telecommun. Technol. 2019, e3652. [Google Scholar] [CrossRef]
- Zemouri, S.; Djahel, S.; Murphy, J. An altruistic prediction-based congestion control for strict beaconing requirements in urban VANETs. IEEE Trans. Syst. Man Cybern. Syst. 2018, 49, 2582–2597. [Google Scholar] [CrossRef]
- Zhang, F.; Du, Y.; Liu, W.; Li, P. Model predictive power control for cooperative vehicle safety system. IEEE Access 2018, 6, 4797–4810. [Google Scholar] [CrossRef]
- Joseph, M.; Liu, X.; Jaekel, A. An adaptive power level control algorithm for DSRC congestion control. In Proceedings of the 8th ACM Symposium on Design and Analysis of Intelligent Vehicular Networks and Applications, Montreal, QC, Canada, 25 October 2018; pp. 57–62. [Google Scholar]
- Shah, S.A.A.; Ahmed, E.; Rodrigues, J.; Ali, I.; Noor, R.M. Shapely value perspective on adapting transmit power for periodic vehicular communications. IEEE Trans. Intell. Transp. Syst. 2018, 19, 977–986. [Google Scholar] [CrossRef]
- Sharma, S.; Chahal, M.; Harit, S. Transmission Rate-based Congestion Control in Vehicular Ad Hoc Networks. In Proceedings of the 2019 Amity International Conference on Artificial Intelligence (AICAI), Dubai, United Arab Emirates, 4–6 February 2019; pp. 303–307. [Google Scholar]
- Cho, B.M.; Jang, M.S.; Park, K.J. Channel-Aware Congestion Control in Vehicular Cyber-Physical Systems. IEEE Access 2020, 8, 73193–73203. [Google Scholar] [CrossRef]
- OpenStreetMap Contributors. 2017. Available online: https://planet.osm.org; https://www.openstreetmap.org (accessed on 15 March 2021).
- Lopez, P.A.; Behrisch, M.; Bieker-Walz, L.; Erdmann, J.; Flötteröd, Y.P.; Hilbrich, R.; Lücken, L.; Rummel, J.; Wagner, P.; Wiessner, P. Microscopic traffic simulation using sumo. In Proceedings of the 2018 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 2575–2582. [Google Scholar]
- Hagenauer, F.; Dressler, F.; Sommer, C. Poster: A simulator for heterogeneous vehicular networks. In Proceedings of the 2014 IEEE Vehicular Networking Conference (VNC), Paderborn, Germany, 3–5 December 2014; pp. 185–186. [Google Scholar]
- Ignaciuk, P.; Bartoszewicz, A. Data Transfer Concepts and Congestion. In Congestion Control in Data Transmission Networks: Sliding Mode and Other Designs; Springer: London, UK, 2012; pp. 2–12. [Google Scholar]
- Mirza, M.; Osindero, S. Conditional generative adversarial nets. arXiv 2014, arXiv:1411.1784. [Google Scholar]
- Ǵeron, A. Data Transfer Concepts and Congestion. In Hands-On Machine Learning with Scikit-Learn, Keras, and TensorFlow: Concepts, Tools, and Techniques to Build Intelligent Systems, 2nd ed.; O’Reilly Media: Sebastopol, CA, USA, 2019; pp. 279–598. [Google Scholar]
- Alliance, N. Description of Network Slicing Concept; NGMN 5G P; Next Generation Mobile Networks Ltd.: Frankfurt, Germany; Hesse, Germany, 2016; Volume 1. [Google Scholar]

| Parameter | IEEE 802.11 p | LTE |
|---|---|---|
| Number of Base Station | 1 | |
| Number of Resource Blocks | 25, 50, 100 | |
| Bandwidth | 10 MHz | 5 MHz, 10 MHz, 20 MHz |
| Transmission power | 30 dBm (Maximally) | 43 dBm, 46 dBm |
| Transmission data rate | 6–27 Mbps | |
| Modulation techniques | QPSK, 16-QAM, 64-QAM | |
| Simulation time | 1000 s | |
| Simulation runs | 500 | |
| Number of vehicles | 50, 100, 150, 200 | |
| Simulation area | 1000 m × 1000 m | |
| Number of lanes | 4 (two in each direction) | |
| Maximum speed | 40 km/h | |
| Propagation model | Nakagami | |
| Size of message | 400 Bytes | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Falahatraftar, F.; Pierre, S.; Chamberland, S. A Conditional Generative Adversarial Network Based Approach for Network Slicing in Heterogeneous Vehicular Networks. Telecom 2021, 2, 141-154. https://doi.org/10.3390/telecom2010009
Falahatraftar F, Pierre S, Chamberland S. A Conditional Generative Adversarial Network Based Approach for Network Slicing in Heterogeneous Vehicular Networks. Telecom. 2021; 2(1):141-154. https://doi.org/10.3390/telecom2010009
Chicago/Turabian StyleFalahatraftar, Farnoush, Samuel Pierre, and Steven Chamberland. 2021. "A Conditional Generative Adversarial Network Based Approach for Network Slicing in Heterogeneous Vehicular Networks" Telecom 2, no. 1: 141-154. https://doi.org/10.3390/telecom2010009
APA StyleFalahatraftar, F., Pierre, S., & Chamberland, S. (2021). A Conditional Generative Adversarial Network Based Approach for Network Slicing in Heterogeneous Vehicular Networks. Telecom, 2(1), 141-154. https://doi.org/10.3390/telecom2010009






