Dependable Wireless System with Shortened Code Using Distance Information between Integrated Terminals
Abstract
1. Introduction
2. Related Works
3. Dependable Wireless System
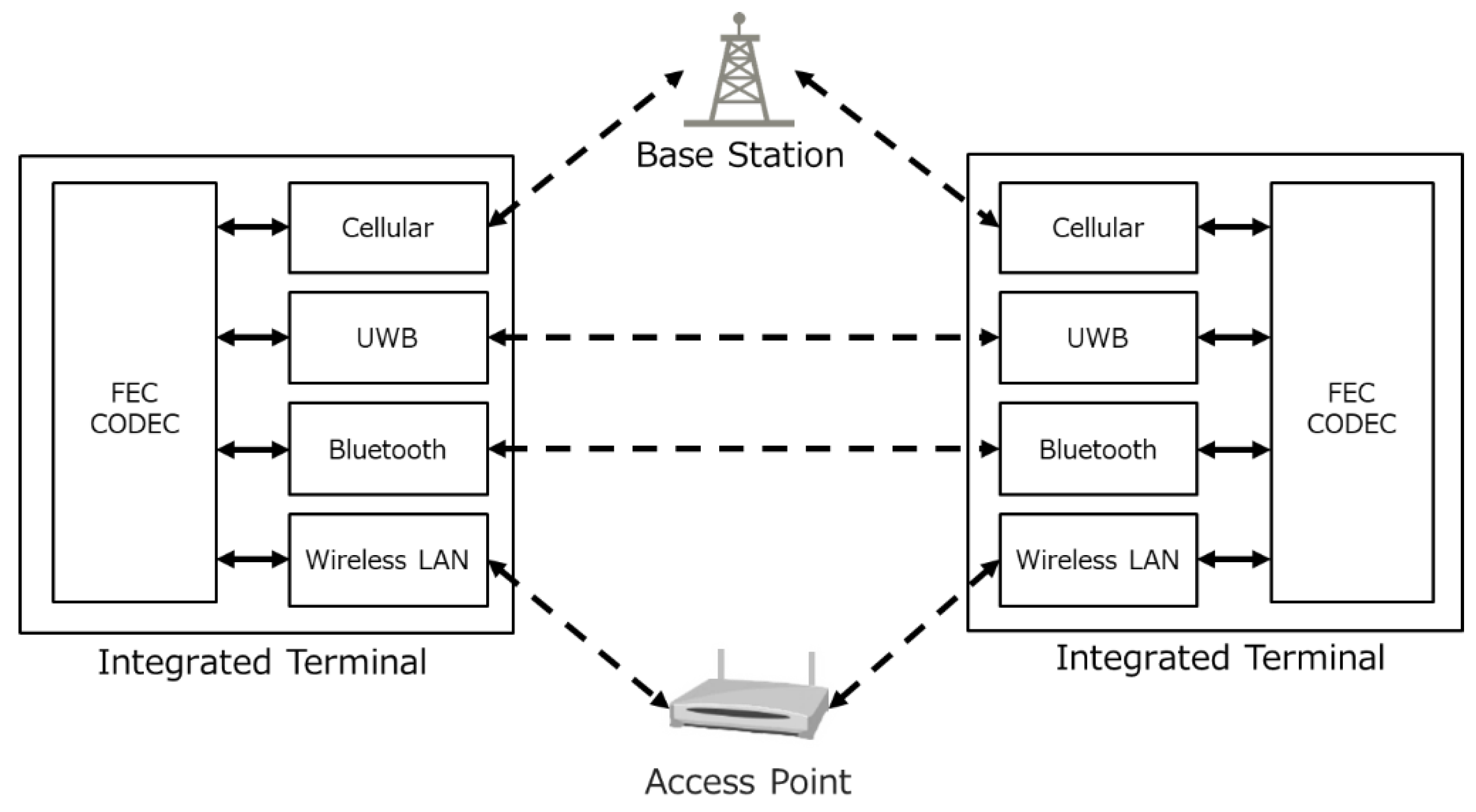
3.1. System Configuration
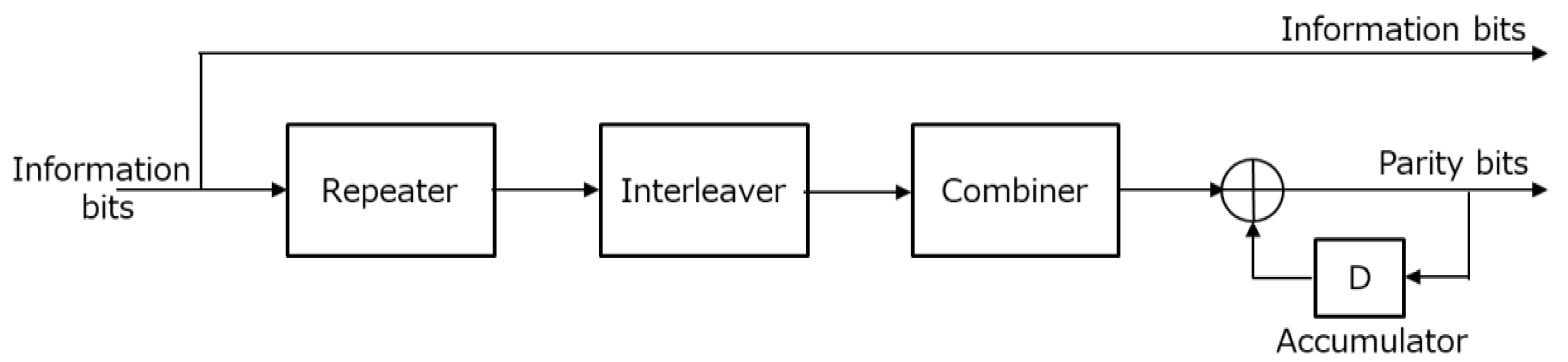
3.2. Shortened Code
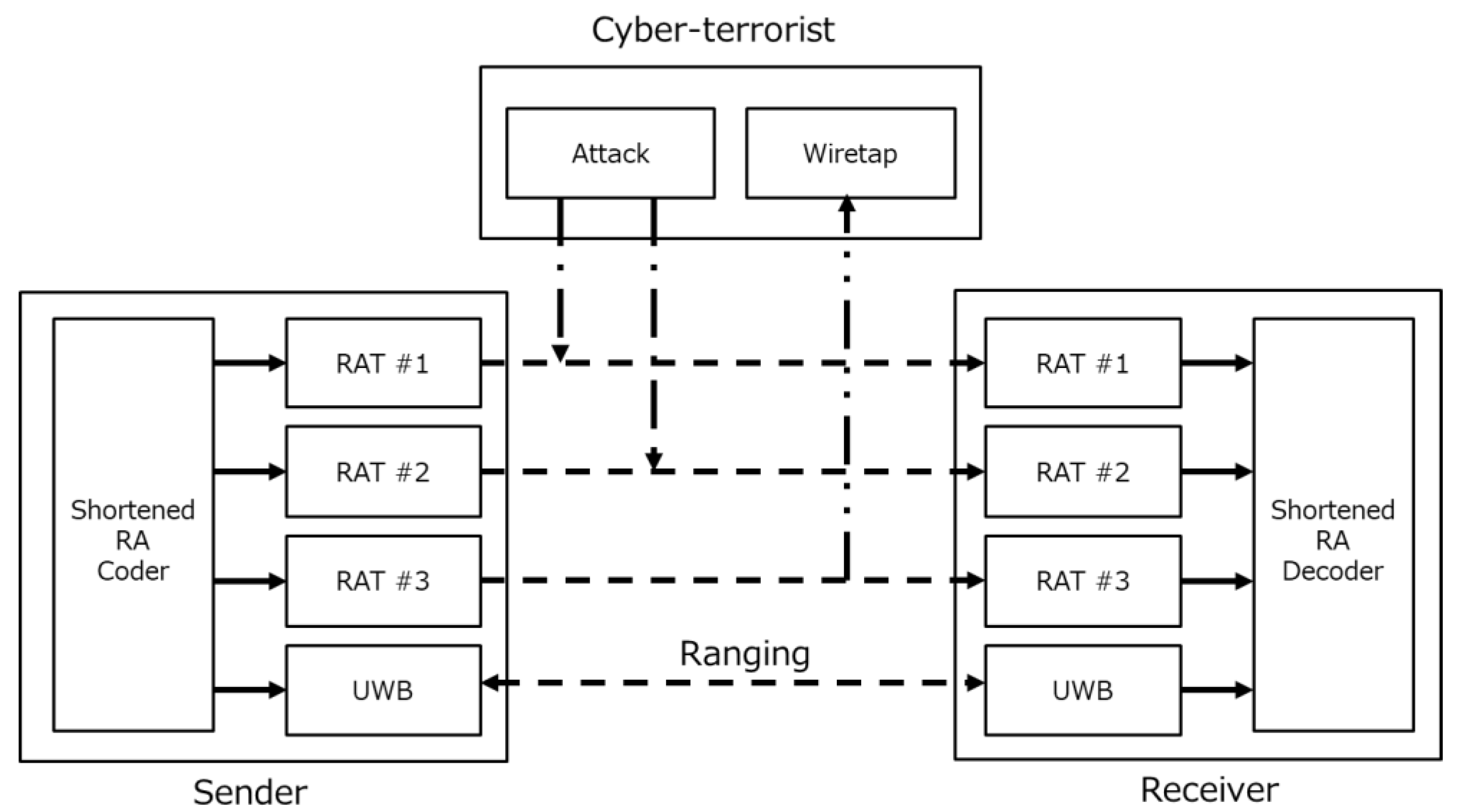
3.3. Sharing Method of Shortened Information
4. Performance Evaluation and Discussion
4.1. Secrecy Capacity
4.2. Simulation Conditions
4.3. Performance of Shortened RA Code
4.4. Performance of UWB Ranging
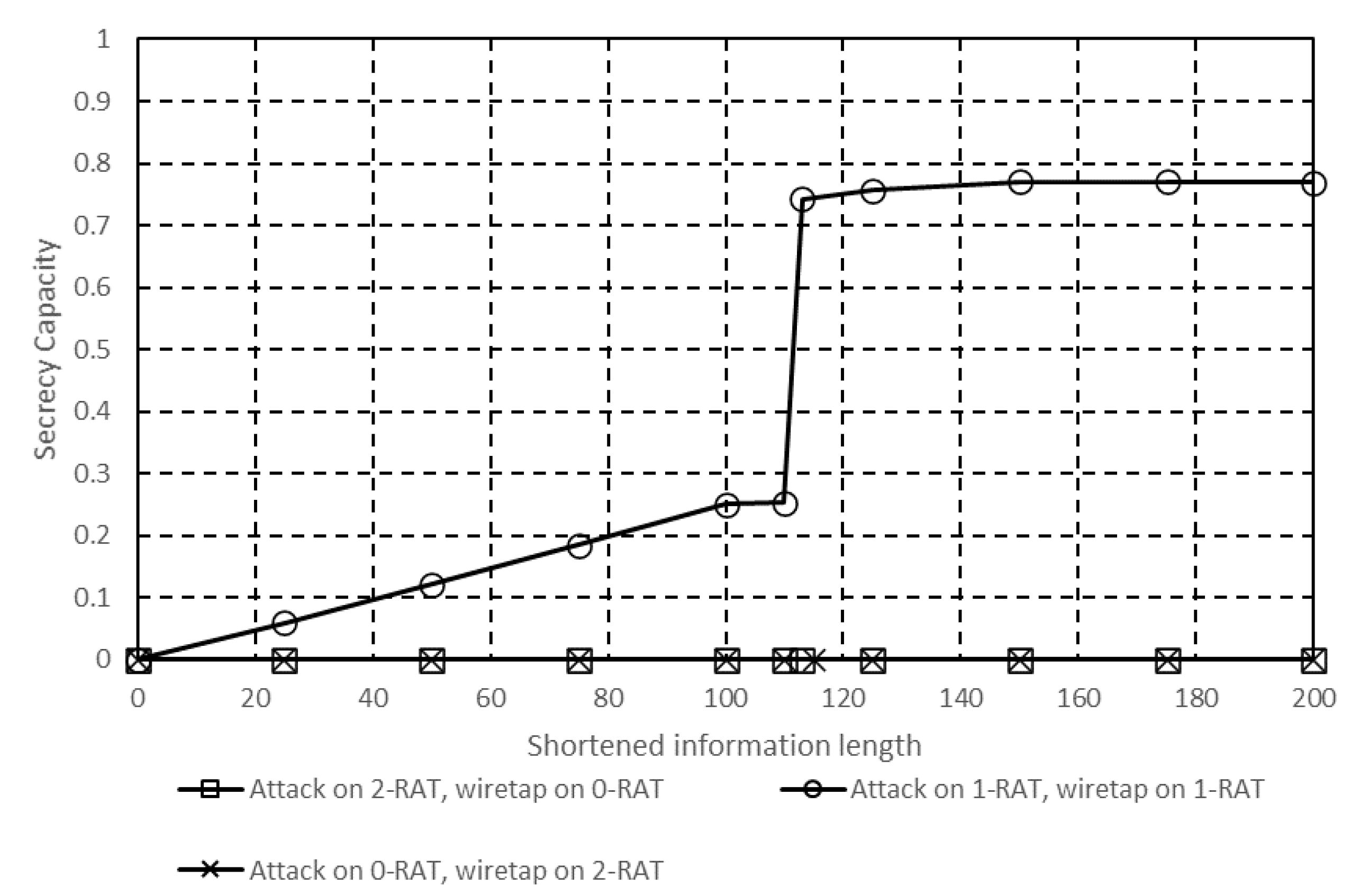
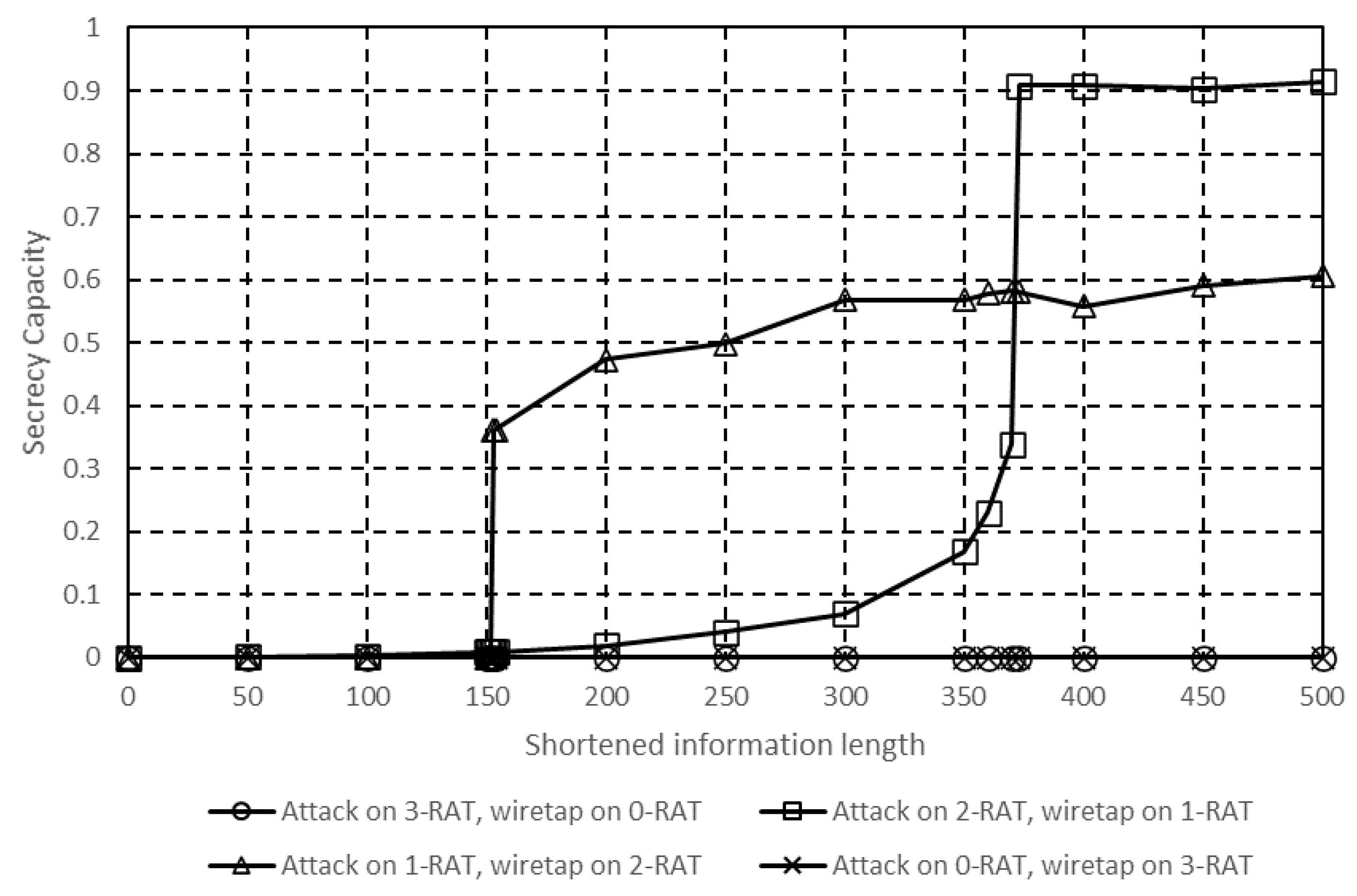
4.5. Performance Using Two RATs for Communication
4.6. Performance Using Three RATs for Communication
5. Conclusions
- Though the shortened information length is the parameter which decides the wiretapping resistance and attack resistance, it is necessary to investigate optimization of the shortened information length and quantization technique, because it is also related to error resistance of distance information.
- It is necessary to examine the effect of the shortened information predicted by the cyberterrorist and the countermeasures and to analyze the performance limit and drawback.
- The evaluation assumes that RAT communication is completely lost due to the attack, but it is necessary to evaluate the actual attack pattern and the impact of attack resistance on each RAT.
- It is necessary to analyze performance degradation due to measured distance error or accuracy.
- It is necessary to examine the application to other codes, because large gain can be obtained by using powerful codes.
- Evaluation of dependability properties based on heuristic strategies such as “what-if analysis” and “robustness checking” are described in [2].
- Finally, an evaluation using a real system is necessary.
Author Contributions
Funding
Conflicts of Interest
References
- Piri, E.; Ruuska, P.; Kanstrén, T.; Mäkelä, J.; Korva, J.; Hekkala, A.; Pouttu, A.; Liina, O.; Latva-aho, M.; Vierimaa, K.; et al. 5GTN: A Test Network for 5G Application Development and Testing. In Proceedings of the European Conference on Networks and Communications (EuCNC), Athens, Greece, 27–30 June 2016. [Google Scholar]
- Testa, A.; Cinque, M.; Coronato, A.; Pietro, G.D.; Augusto, J.C. Heuristic strategies for assessing wireless sensor network resiliency: An event-based formal approach. J. Heuristics 2015, 21, 145–175. [Google Scholar] [CrossRef]
- Avizienis, A.; Laprie, J.-C.; Randell, B.; Landwehr, C. Basic concepts and taxonomy of dependable and secure computing. IEEE Trans. Dependable Secur. Comput. 2004, 1, 11–33. [Google Scholar] [CrossRef]
- Jesus, T.C.; Portugal, P.; Vasques, F.; Costa, D.G. Automated methodology for dependability evaluation of wireless visual sensor networks. Sensors 2018, 18, 2629. [Google Scholar] [CrossRef] [PubMed]
- Jesus, T.C.; Portugal, P.; Costa, D.G.; Vasques, F. A comprehensive dependability model for QoM-Aware industrial WSN when performing visual area coverage in occluded scenarios. Sensors 2020, 20, 6542. [Google Scholar] [CrossRef]
- Diffie, W.; Hellmanuthor, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Vandenwauver, M.; Govaerts, R.; Vandewalle, J. Overview of Authentication Protocols. In Proceedings of the IEEE 31st Annual 1997 International Carnahan Conference on Security Technology, Canberra, ACT, Australia, 15–17 October 1997. [Google Scholar]
- Goldwasser, J.L. Shortened and punctured codes and the MacWilliams identities. Linear Algebra Appl. 1997, 253, 1–13. [Google Scholar] [CrossRef][Green Version]
- Kreer, J. A question of terminology. IRE Trans. Inf. Theory 1957, 3, 208. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Perlman, R. An overview of PKI trust models. IEEE Netw. 1999, 13, 38–43. [Google Scholar] [CrossRef]
- Pavithran, D.; Shaalan, K. Towards Creating Public Key Authentication for IoT blockchain. In Proceedings of the 2019 Sixth HCT Information Technology Trends (ITT), Ras Al Khaimah, UAE, 20–21 November 2019. [Google Scholar]
- Li, Y.; Yu, Y.; Lou, C.; Guizani, N.; Wang, L. Decentralized public key infrastructures atop blockchain. IEEE Netw. 2020, 34, 133–139. [Google Scholar] [CrossRef]
- Hershey, J.E.; Hassan, A.A.; Yarlagadda, R. Unconventional cryptographic keying variable management. IEEE Trans. Commun. 1995, 43, 3–6. [Google Scholar] [CrossRef]
- Wu, X.; Wang, P.; Wang, K.; Xu, Y. Biometric cryptographic key generation based on city block distance. In Proceedings of the 2009 Workshop on Applications of Computer Vision (WACV), Snowbird, UT, USA, 7–8 December 2009. [Google Scholar]
- Yang, T.; Kong, L.; Xin, W.; Hu, J.; Chen, Z. Resisting Relay Attacks on Vehicular Passive Keyless Entry and Start Systems. In Proceedings of the 2012 9th International Conference on Fuzzy Systems and Knowledge Discovery, Chongqing, China, 29–31 May 2012. [Google Scholar]
- Yamasaki, S.; Matsushima, T. A security enhancement technique for wireless communications using secret sharing and physical layer secrecy transmission. IEICE Trans. Inf. Syst. 2016, E99-D, 830–838. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Lin, C.; Harn, L. Unconditionally Secure Multi-Secret Sharing Scheme. In Proceedings of the 2012 IEEE International Conference on Computer Science and Automation Engineering (CSAE), Zhangjiajie, China, 25–27 May 2012. [Google Scholar]
- Gong, X.; Hu, P.; Shum, K.W.; Sung, C.W. A zigzag-decodable ramp secret sharing scheme. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1906–1916. [Google Scholar] [CrossRef]
- Eriguchi, R.; Kunihiro, N. Strongly secure ramp secret sharing schemes from any linear secret sharing schemes. In Proceedings of the 2019 IEEE Information Theory Workshop (ITW), Visby, Sweden, 25–28 August 2019. [Google Scholar]
- Li, X.; Ratazzi, E.P. MIMO Transmissions with Information-Theoretic Secrecy for Secret-Key Agreement in Wireless Networks. In Proceedings of the MILCOM 2005—2005 IEEE Military Communications Conference, Atlantic City, NJ, USA, 17–20 October 2005. [Google Scholar]
- Rao, J.; Vrzic, S. Packet Duplication for URLLC in 5G Dual Connectivity Architecture. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018. [Google Scholar]
- Wan, Y.; Wang, Q.; Duan, S.; Zhang, X. RAFH: Reliable Aware Frequency Hopping Method for Industrial Wireless Sensor Networks. In Proceedings of the 2009 5th International Conference on Wireless Communications, Networking and Mobile Computing, Beijing, China, 24–26 September 2009. [Google Scholar]
- Mohammadmoradi, H.; Heydariaan, M.; Gnawali, O. SRAC: Simultaneous Ranging and Communication in UWB Networks. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini Island, Greece, 29–31 May 2019. [Google Scholar]
- Divsalar, D.; Jin, H.; McEliece, R.J. Coding Theorems for “Turbo-Like” Codes. In Proceedings of the 36th Annual Allerton Conference on Communication Control and Computing, Champaign, IL, USA, 23–25 September 1998. [Google Scholar]
- Vázquez-Araújo, F.J.; González-López, M.; Castedo, L.; Frias, J.G. Capacity approaching low-rate LDGM codes. IEEE Trans. Commun. 2011, 59, 352–356. [Google Scholar] [CrossRef]
- Gallager, R. Low-density parity-check codes. IRE Trans. Inf. Theory 1962, 8, 21–28. [Google Scholar] [CrossRef]
- Jiménez, A.R.; Seco, F. Comparing Decawave and Bespoon UWB Location Systems: Indoor/Outdoor Performance Analysis. In Proceedings of the 2016 International Conference on Indoor Positioning and Indoor Navigation (IPIN), Alcala de Henares, Spain, 4–7 October 2016. [Google Scholar]
- Domuta, I.; Palade, T.P.; Puschita, E.; Pastrav, A. Localization in 802. 15.4z Standard. In Proceedings of the 2020 International Workshop on Antenna Technology (iWAT), Bucharest, Romania, 25–28 February 2020. [Google Scholar]
- Barros, J.; Rodrigues, M.R.D. Secrecy Capacity of Wireless Channels. In Proceedings of the 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, 9–14 July 2006. [Google Scholar]
- Leung-Yan-Cheong, S.; Hellman, M. The Gaussian wire-tap channel. IEEE Trans. Inf. Theory 1978, 24, 451–456. [Google Scholar] [CrossRef]








| Term/Symbol | Definition |
|---|---|
| Shortened information | Information to be removed after encoding |
| Unencoded bits | Bit sequence containing the shortened information and information |
| Column weight | Number of 1’s in column of information bits of the parity check matrix |
| Row weight | Number of 1’s in row of information bits of the parity check matrix |
| Unencoded bit length | |
| Codeword length | |
| Shortened information length | |
| Number of bits that can be decoded by decoder of (, ) code | |
| Number of bits that can be decoded by decoder of (, ) shortened code without the shortened information | |
| Efficiency of (, ) code | |
| Efficiency of (, ) shortened code when decoder uses the shortened information | |
| Efficiency of (, ) shortened code when decoder does not use the shortened information | |
| Column weight | |
| Row weight |
| Term/Symbol | Definition |
|---|---|
| Sender | Terminal sending information to the receiver |
| Receiver | Terminal receiving information from the sender |
| Cyberterrorist | Terminal that can be wiretapped and attacked simultaneously |
| Channel capacity of the receiver under attack | |
| Channel capacity due to wiretapping by the cyberterrorist | |
| Secrecy capacity | |
| Random sequence sent by the sender | |
| Received sequence by the receiver under attack | |
| Wiretapped sequence by the cyberterrorist | |
| Errors not corrected by decoder | |
| Entropy of | |
| Entropy of | |
| Entropy of | |
| Probability of | |
| Probability of | |
| Probability of | |
| Mutual information between and | |
| Mutual information between and | |
| Probability of different bits of and | |
| Probability of different bits of and |
| Parameter | Detail |
|---|---|
| Unencoded bit length () | 600 |
| Codeword length () | 1200 |
| Shortened information length () | 0~500 |
| Column weight () | 3 |
| Decoding algorithm | LogMAP |
| Maximum number of repetitions | 100 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amezawa, Y.; Kohno, R. Dependable Wireless System with Shortened Code Using Distance Information between Integrated Terminals. Telecom 2020, 1, 266-282. https://doi.org/10.3390/telecom1030018
Amezawa Y, Kohno R. Dependable Wireless System with Shortened Code Using Distance Information between Integrated Terminals. Telecom. 2020; 1(3):266-282. https://doi.org/10.3390/telecom1030018
Chicago/Turabian StyleAmezawa, Yasuharu, and Ryuji Kohno. 2020. "Dependable Wireless System with Shortened Code Using Distance Information between Integrated Terminals" Telecom 1, no. 3: 266-282. https://doi.org/10.3390/telecom1030018
APA StyleAmezawa, Y., & Kohno, R. (2020). Dependable Wireless System with Shortened Code Using Distance Information between Integrated Terminals. Telecom, 1(3), 266-282. https://doi.org/10.3390/telecom1030018





