Firmware Attestation in IoT Swarms Using Relational Graph Neural Networks and Static Random Access Memory
Abstract
1. Introduction
2. Related Work
2.1. Single-Node IoT Attestation Techniques
2.1.1. Software-Based RA Techniques
2.1.2. Hardware-Based RA Techniques
2.1.3. Hybrid-Based RA Techniques
2.2. Swarm IoT Attestation Techniques
2.3. Advantages of RGNN
3. Background
3.1. IoT Swarms
3.2. Remote Attestation
3.3. SRAM in Attestation
3.4. Graph Neural Networks and Relational Graph Neural Networks
4. Methodology
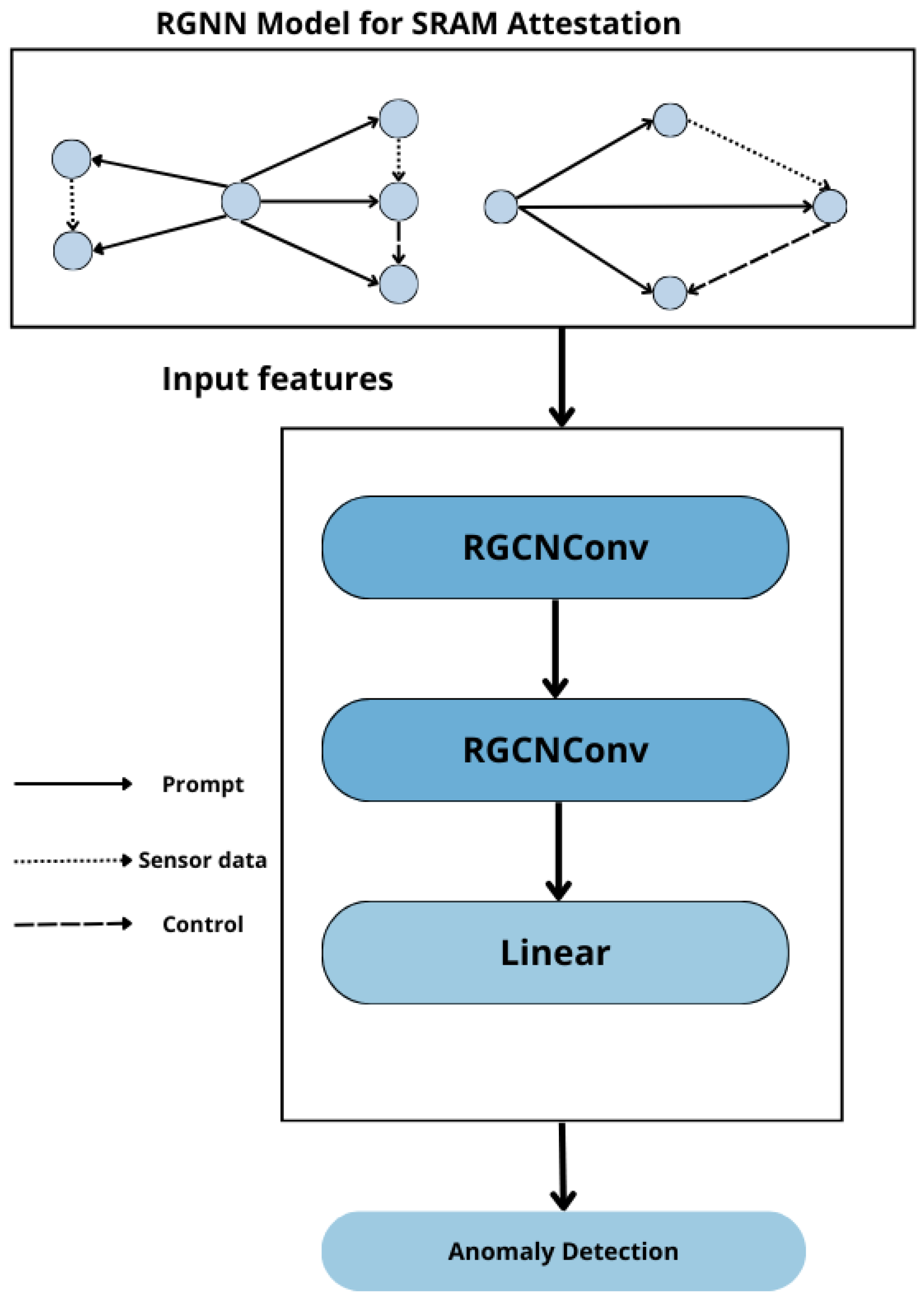
4.1. RGNN Model Architecture
| Listing 1. Compact RGNN model for IoT firmware anomaly detection. |
| class RGNNModel(nn.Module): def __init__(self, in_dim, hid_dim, n_rel, drop=0.1): super().__init__() self.conv1 = gnn.RGCNConv(in_dim, 2 * hid_dim, num_relations=n_rel) self.conv2 = gnn.RGCNConv(2 * hid_dim, hid_dim, num_relations=n_rel) self.lin = nn.Linear(hid_dim, in_dim) self.drop = drop def forward(self, x, edge_idx, edge_type): x = F.relu(self.conv1(x, edge_idx, edge_type)) x = F.dropout(x, p=self.drop, training=self.training) x = F.relu(self.conv2(x, edge_idx, edge_type)) return self.lin(x) |
4.2. Dataset Used
- Node features: SRAM vectors , normalized to and padded to 2048 bytes per node.
- Node roles and graph structure:
- –
- –
- Swarm-2: Table 3 shows N0 (Control) broadcasting to N1–N5, N1 and N4 (Sense) generating data for N2 and N5, N2 (Process) sending signals to N3 (Control), and N5 (Process and Control) processing and controlling LEDs. Table 5 details 8 edges: N0 to N1–N5 (Prompts, type 0), N1 to N2 and N4 to N5 (Sensor Data, type 1), and N2 to N3 (Processed Signal, type 2). Edge indices .
- Scenarios: Swarm-1 includes benign (D1, D2, P1, P2) and anomalous (AN0–AN3, AN12, AN23, AN13, AN123, AN0123) cases; e.g., AN0 alters N0’s broadcast (195 bytes vs. 191). Swarm-2 has benign (D1–D4) and anomalous (AN0–AN5) cases; e.g., AN4 stops N4’s data transmission to N5 (372 bytes vs. 430).
- Labels: 0 (benign) or 1 (anomalous); e.g., AN1 flags N1.
4.3. Anomaly Detection
4.4. System Integration
- 1.
- Collection: Secure SRAM trace gathering.
- 2.
- Input: Node features and graph structure.
- 3.
- Inference: RGNN computes similarities.
- 4.
- Output: Flags anomalies and propagation.
5. Experiments and Results
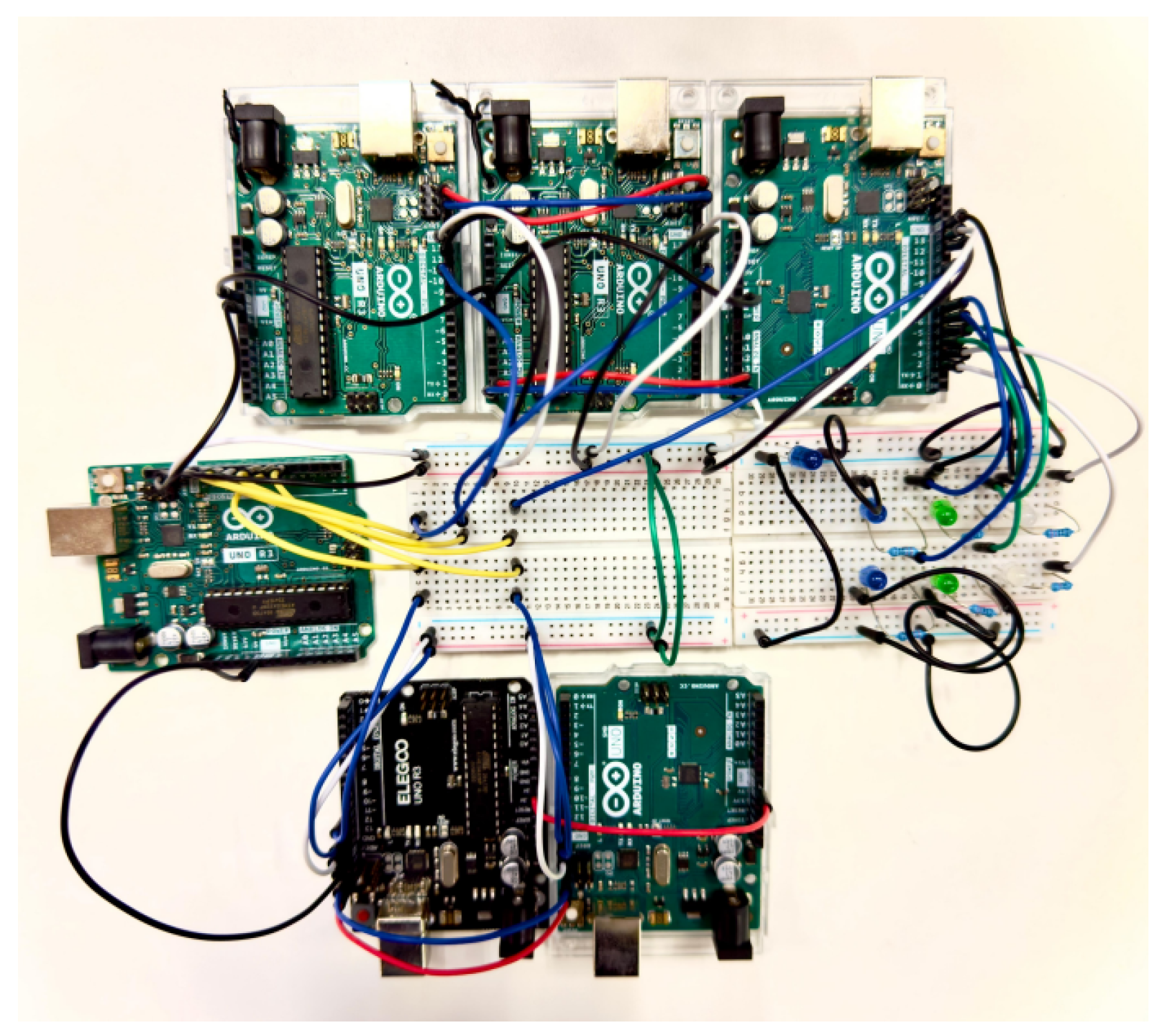
5.1. Experimental Setup
5.2. Evaluation Metrics
- Overall accuracy: Average per-node accuracy across all scenarios and nodes.
- Robustness tests: Performance under Gaussian noise (), 10% dropped responses, and trace replay attacks.
5.3. Results
6. Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| IOT | Internet of Things |
| RGNN | Relational Graph Neural Network |
| GNN | Graph Neural Network |
| SRAM | Static Random-Access Memory |
| RA | Remote Attestation |
References
- Mazhar, T.; Talpur, D.B.; Shloul, T.A.; Ghadi, Y.Y.; Haq, I.; Ullah, I.; Ouahada, K.; Hamam, H. Analysis of IoT Security Challenges and Its Solutions Using Artificial Intelligence. Brain Sci. 2023, 13, 683. [Google Scholar] [CrossRef] [PubMed]
- Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A. Internet of Things: Security and Solutions Survey. Sensors 2022, 22, 7433. [Google Scholar] [CrossRef] [PubMed]
- Lee, J. Collective Attestation for Manageable IoT Environments. Appl. Sci. 2018, 8, 2652. [Google Scholar] [CrossRef]
- Bakhshi, T.; Ghita, B.; Kuzminykh, I. A Review of IoT Firmware Vulnerabilities and Auditing Techniques. Sensors 2024, 24, 708. [Google Scholar] [CrossRef] [PubMed]
- Malhotra, P.; Singh, Y.; Anand, P.; Bangotra, D.K.; Singh, P.K.; Hong, W.-C. Internet of Things: Evolution, Concerns and Security Challenges. Sensors 2021, 21, 1809. [Google Scholar] [CrossRef] [PubMed]
- Kuang, B.; Fu, A.; Susilo, W.; Yu, S.; Gao, Y. A Survey of Remote Attestation in Internet of Things: Attacks, Countermeasures, and Prospects. Comput. Secur. 2022, 112, 102498. [Google Scholar] [CrossRef]
- Kohli, V.; Kohli, B.; Aman, M.N.; Sikdar, B. Swarm-Net: Firmware Attestation in IoT Swarms Using Graph Neural Networks and Volatile Memory. IEEE Internet Things J. 2025, 12, 8338–8352. [Google Scholar] [CrossRef]
- Seshadri, A.; Perrig, A.; van Doorn, L.; Khosla, P. SWATT: SoftWare-Based Attestation for Embedded Devices. In Proceedings of the IEEE Symposium on Security and Privacy, 2004, Berkeley, CA, USA, 12 May 2004; pp. 272–282. [Google Scholar] [CrossRef]
- Seshadri, A.; Luk, M.; Perrig, A.; van Doorn, L.; Khosla, P. SCUBA: Secure Code Update by Attestation in Sensor Networks. In Proceedings of the 5th ACM Workshop on Wireless Security (WiSe ’06), Los Angeles, CA, USA, 29 September 2006; Association for Computing Machinery: New York, NY, USA, 2006; pp. 85–94. [Google Scholar] [CrossRef]
- Seshadri, A.; Luk, M.; Perrig, A. SAKE: Software Attestation for Key Establishment in Sensor Networks. In Distributed Computing in Sensor Systems; Nikoletseas, S.E., Chlebus, B.S., Johnson, D.B., Krishnamachari, B., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 372–385. [Google Scholar] [CrossRef]
- Chen, B.; Dong, X.; Bai, G.; Jauhar, S.; Cheng, Y. Secure and Efficient Software-Based Attestation for Industrial Control Devices with ARM Processors. In Proceedings of the 33rd Annual Computer Security Applications Conference (ACSAC ’17), Orlando, FL, USA, 4–8 December 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 425–436. [Google Scholar] [CrossRef]
- Cao, J.; Zhu, T.; Ma, R.; Guo, Z.; Zhang, Y.; Li, H. A Software-Based Remote Attestation Scheme for Internet of Things Devices. IEEE Trans. Dependable Secur. Comput. 2023, 20, 1422–1434. [Google Scholar] [CrossRef]
- Surminski, S.; Niesler, C.; Linsner, S.; Davi, L.; Reuter, C. SCAtt-Man: Side-Channel-Based Remote Attestation for Embedded Devices That Users Understand. In Proceedings of the Thirteenth ACM Conference on Data and Application Security and Privacy (CODASPY ’23), Charlotte, NC, USA, 24–26 April 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 225–236. [Google Scholar] [CrossRef]
- Laeuchli, J.; Trujillo-Rasua, R. Software-Based Remote Memory Attestation Using Quantum Entanglement. Quantum Inf. Process. 2024, 23, 208. [Google Scholar] [CrossRef]
- Tan, H.; Hu, W.; Jha, S. A TPM-Enabled Remote Attestation Protocol (TRAP) in Wireless Sensor Networks. In Proceedings of the 6th ACM Workshop on Performance Monitoring and Measurement of Heterogeneous Wireless and Wired Networks (PM2HW2N ’11), Miami, FL, USA, 31 October 2011; Association for Computing Machinery: New York, NY, USA, 2011; pp. 9–16. [Google Scholar] [CrossRef]
- Khan, M.A.; Aman, M.N.; Sikdar, B. Soteria: A Quantum-Based Device Attestation Technique for Internet of Things. IEEE Internet Things J. 2024, 11, 15320–15333. [Google Scholar] [CrossRef]
- ElDefrawy, K.E.; Francillon, A.; Perito, D.; Tsudik, G. SMART: Secure and Minimal Architecture for (Establishing a Dynamic) Root of Trust. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 5–8 February 2012; pp. 1–15. [Google Scholar]
- Koeberl, P.; Schulz, S.; Sadeghi, A.-R.; Varadharajan, V. TrustLite: A Security Architecture for Tiny Embedded Devices. In Proceedings of the Ninth European Conference on Computer Systems (EuroSys ’14), Amsterdam, The Netherlands, 14–16 April 2014; Association for Computing Machinery: New York, NY, USA, 2014; pp. 1–14. [Google Scholar] [CrossRef]
- Brasser, F.; El Mahjoub, B.; Sadeghi, A.-R.; Wachsmann, C.; Koeberl, P. TyTAN: Tiny Trust Anchor for Tiny Devices. In Proceedings of the 52nd Annual Design Automation Conference (DAC ’15), San Francisco, CA, USA, 7–11 June 2015; Association for Computing Machinery: New York, NY, USA, 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Asokan, N.; Brasser, F.; Ibrahim, A.; Sadeghi, A.-R.; Schunter, M.; Tsudik, G.; Wachsmann, C. SEDA: Scalable Embedded Device Attestation. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security (CCS ’15), Denver, CO, USA, 12–16 October 2015; Association for Computing Machinery: New York, NY, USA, 2015; pp. 964–975. [Google Scholar] [CrossRef]
- Gugueoth, V.; Safavat, S.; Shetty, S. Security of Internet of Things (IoT) Using Federated Learning and Deep Learning—Recent Advancements, Issues and Prospects. ICT Express 2023, 9, 941–960. [Google Scholar] [CrossRef]
- Abera, T.; Asokan, N.; Davi, L.; Ekberg, J.-E.; Nyman, T.; Paverd, A.; Sadeghi, A.-R.; Tsudik, G. C-FLAT: Control-Flow Attestation for Embedded Systems Software. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security (CCS ’16), Vienna, Austria, 24–28 October 2016; for Computing Machinery: New York, NY, USA, 2016; pp. 743–754. [Google Scholar] [CrossRef]
- Ammar, M.; Washha, M.; Crispo, B. WISE: Lightweight Intelligent Swarm Attestation Scheme for IoT (The Verifier’s Perspective). In Proceedings of the 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Limassol, Cyprus, 15–17 October 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Kuang, B.; Fu, A.; Gao, Y.; Zhang, Y.; Zhou, J.; Deng, R.H. FeSA: Automatic Federated Swarm Attestation on Dynamic Large-Scale IoT Devices. IEEE Trans. Dependable Secur. Comput. 2023, 20, 2954–2969. [Google Scholar] [CrossRef]
- Prakash, V.; Odedina, O.; Kumar, A.; Garg, L.; Bawa, S. A Secure Framework for the Internet of Things Anomalies Using Machine Learning. Discov. Internet Things 2024, 4, 33. [Google Scholar] [CrossRef]
- Chilese, M.; Mitev, R.; Orenbach, M.; Thorburn, R.; Atamli, A.; Sadeghi, A.-R. One for All and All for One: GNN-Based Control-Flow Attestation for Embedded Devices. In Proceedings of the 2024 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2024; pp. 3346–3364. [Google Scholar] [CrossRef]
- Kohli, V.; Kohli, B.; Aman, M.N.; Sikdar, B. IoT Swarm SRAM Dataset for Firmware Attestation. IEEE Dataport 2024. [Google Scholar] [CrossRef]
- Kipf, T.N.; Welling, M. Semi-Supervised Classification with Graph Convolutional Networks. arXiv 2017, arXiv:1609.02907. [Google Scholar] [CrossRef]
- Schlichtkrull, M.; Kipf, T.N.; Bloem, P.; van den Berg, R.; Titov, I.; Welling, M. Modeling Relational Data with Graph Convolutional Networks. In The Semantic Web; Gangemi, A., Navigli, R., Vidal, M.-E., Hitzler, P., Troncy, R., Hollink, L., Tordai, A., Alam, M., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 593–607. [Google Scholar] [CrossRef]


| Technique | Type | Approach | Feature | Firmware Copies Propagated | Anomaly Detection | Scalability | Accuracy (%) |
|---|---|---|---|---|---|---|---|
| SWATT [8] | Software | Crypto | Flash | Yes | No | Low | 90 |
| SCUBA [9] | Software | Crypto | Network | Yes | No | Low | 85 |
| TPM-based [15] | Hardware | Crypto | Flash | Yes | No | Medium | 95 |
| QPUF [16] | Hardware | Crypto | Quantum | No | No | Low | 98 |
| SMART [17] | Hybrid | Crypto | Flash | Yes | No | Medium | 92 |
| WISE [23] | Swarm | Crypto + ML | Flash | No | Partial | High | 62 |
| FeSA [24] | Swarm | FL | Property | No | Partial | High | 87 |
| SAFE-IoT [25] | Swarm | ML | Network | No | Partial | Medium | 90 |
| Swarm-Net [7] | Swarm | GNN | SRAM | No | Yes | High | 99.96 |
| RGNN (Ours) | Swarm | RGNN | SRAM | No | Yes | High | 99.94 (Swarm-1) 100 (Swarm-2) |
| Node | Type | Normal Firmware Functions | d | Anomalous Firmware Functions | d |
|---|---|---|---|---|---|
| N0 | Control | Broadcasts one byte to all nodes | 191 | Generates three random integers; broadcasts one byte to all nodes | 195 |
| N1 | Sense | Generates six floating point numbers in unique ranges; sends data to N2 | 450 | Generates data in an extended range; sends data to N2 | 438 |
| N2 | Process | Processes received data into a six-byte signal; sends Processed Signal to N3 | 516 | Generates a random six-byte signal; sends control signal to N3 | 414 |
| N3 | Control | Control six LEDs using the processed signal | 406 | Control six LEDs at random | 386 |
| Node | Type | Normal Firmware Functions | d | Anomalous Firmware Functions | d |
|---|---|---|---|---|---|
| N0 | Control | Broadcasts one byte to all nodes | 195 | Generates two random integers; broadcasts one byte to all nodes | 199 |
| N1 | Sense | Generates four floating point numbers in unique ranges; sends data to N2 | 438 | Generates data in an extended range; sends data to N2 | 430 |
| N2 | Process | Processes received data into a four-byte signal; sends Processed Signal to N3 | 490 | Generates a random four-byte signal; sends control signal to N3 | 414 |
| N3 | Control | Controls four LEDs using the Processed Signal | 394 | Controls four LEDs at random | 386 |
| N4 | Sense | Generates three floating point numbers in unique ranges; sends data to N5 | 430 | Generates data normally; does not send data to N5 | 372 |
| N5 | Process and Control | Processes received data into a three-byte signal; controls three LEDs using the Processed Signal | 446 | Processes received data normally; controls three unauthorized LEDs | 452 |
| Source Node | Destination Node | Edge Type | Description |
|---|---|---|---|
| N0 | N1 | Prompt (0) | Broadcasts a control byte to initiate N1’s sensing of six floating-point numbers. |
| N0 | N2 | Prompt (0) | Broadcasts a control byte to initiate N2’s processing of Sensor Data. |
| N0 | N3 | Prompt (0) | Broadcasts a control byte to initiate N3’s control of six LEDs. |
| N1 | N2 | Sensor Data (1) | Sends six floating-point numbers to N2 for processing into a six-byte signal. |
| N2 | N3 | Processed Signal (2) | Sends a six-byte processed signal to N3 for controlling six LEDs. |
| Source Node | Destination Node | Edge Type | Description |
|---|---|---|---|
| N0 | N1 | Prompt (0) | Broadcasts a control byte to initiate N1’s sensing of four floating-point numbers. |
| N0 | N2 | Prompt (0) | Broadcasts a control byte to initiate N2’s processing of Sensor Data. |
| N0 | N3 | Prompt (0) | Broadcasts a control byte to initiate N3’s control of four LEDs. |
| N0 | N4 | Prompt (0) | Broadcasts a control byte to initiate N4’s sensing of three floating-point numbers. |
| N0 | N5 | Prompt (0) | Broadcasts a control byte to initiate N5’s processing and control of three LEDs. |
| N1 | N2 | Sensor Data (1) | Sends four floating-point numbers to N2 for processing into a four-byte signal. |
| N2 | N3 | Processed Signal (2) | Sends a four-byte processed signal to N3 for controlling four LEDs. |
| N4 | N5 | Sensor Data (1) | Sends three floating-point numbers to N5 for processing into a three-byte signal. |
| Scenario No. | Scenario | Primary Anomaly | Secondary Anomaly | Swarm Label (N0–N3) |
|---|---|---|---|---|
| 1–2 | D1–2 | – | – | 0-0-0-0 |
| 3–4 | P1–2 | – | – | 0-0-0-0 |
| 5 | AN0 | N0 | – | 1-0-0-0 |
| 6 | AN1 | N1 | N2, N3 | 0-1-1-1 |
| 7 | AN2 | N2 | N3 | 0-0-1-1 |
| 8 | AN3 | N3 | – | 0-0-0-1 |
| 9 | AN12 | N1, N2 | N3 | 0-1-1-1 |
| 10 | AN23 | N2, N3 | – | 0-0-1-1 |
| 11 | AN13 | N1, N3 | N2 | 0-1-1-1 |
| 12 | AN123 | N1–N3 | N2, N3 | 0-1-1-1 |
| 13 | AN0123 | N0–N3 | N2, N3 | 1-1-1-1 |
| Scenario No. | Scenario | Primary Anomaly | Secondary Anomaly | Swarm Label (N0–N5) |
|---|---|---|---|---|
| 1–4 | D1–4 | – | – | 0-0-0-0-0-0 |
| 5 | AN0 | N0 | – | 1-0-0-0-0-0 |
| 6 | AN1 | N1 | N2, N3 | 0-1-1-1-0-0 |
| 7 | AN2 | N2 | N3 | 0-0-1-1-0-0 |
| 8 | AN3 | N3 | – | 0-0-0-1-0-0 |
| 9 | AN4 | N4 | N5 | 0-0-0-0-1-1 |
| 10 | AN5 | N5 | – | 0-0-0-0-0-1 |
| Attribute | Swarm-1 | Swarm-2 | ||||
|---|---|---|---|---|---|---|
| RGNN | fastRGNN | RGAT | RGNN | fastRGNN | RGAT | |
| Total Parameters | 600,160 | 600,160 | 472,736 | 600,160 | 600,160 | 472,736 |
| Conv1 Type | RGCNConv | FastRGCNConv | RGATConv | RGCNConv | FastRGCNConv | RGATConv |
| Latent Dim | 32 | 32 | 32 | 32 | 32 | 32 |
| Dropout | 0.1 | 0.1 | 0.1 | 0.1 | 0.1 | 0.1 |
| Learning Rate | ||||||
| Noise Level | 0.4 | 0.4 | 0.4 | 0.4 | 0.4 | 0.4 |
| Metric | Swarm-1 | Swarm-2 | ||||
|---|---|---|---|---|---|---|
| RGNN (%) | fastRGNN (%) | RGAT (%) | RGNN (%) | fastRGNN (%) | RGAT (%) | |
| Overall Accuracy (OA) | 99.94 | 99.93 | 97.31 | 100.0 | 100.0 | 97.97 |
| Anomaly Recall (AR) | 99.89 | 99.91 | 99.91 | 99.99 | 99.99 | 99.68 |
| Detection Rate (All) | 99.97 | 99.94 | 96.16 | 100.0 | 100.0 | 96.83 |
| Detection Rate (Propagated) | 99.97 | 99.93 | 96.83 | 100.0 | 100.0 | 94.65 |
| Final Loss | 0.0005 | 0.0006 | 0.0031 | 0.0012 | 0.0015 | 0.0035 |
| Avg. Epoch Time (s) | 0.0445 | 0.0806 | 0.1371 | 0.1134 | 5.4953 | 0.4909 |
| Scenario No. | Scenario | RGNN (%) | fastRGNN (%) | RGAT (%) | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| N0 | N1 | N2 | N3 | N0 | N1 | N2 | N3 | N0 | N1 | N2 | N3 | ||
| 1 | D1 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| 2 | D2 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| 3 | P1 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.75 | 100 | 100 | 100 |
| 4 | P2 | 100 | 98.75 | 99.50 | 100 | 100 | 99.00 | 99.50 | 100 | 100 | 99.25 | 99.50 | 100 |
| 5 | AN0 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 93.75 | 44.50 |
| 6 | AN1 | 100 | 100 | 99.75 | 99.50 | 100 | 100 | 99.75 | 98.75 | 100 | 100 | 94.75 | 98.75 |
| 7 | AN2 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.50 | 100 | 100 | 69.50 |
| 8 | AN3 | 100 | 100 | 99.75 | 100 | 100 | 99.75 | 99.75 | 100 | 100 | 100 | 99.75 | 100 |
| 9 | AN12 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 66.50 |
| 10 | AN23 | 100 | 99.75 | 100 | 100 | 100 | 100 | 100 | 100 | 99.75 | 100 | 100 | 100 |
| 11 | AN13 | 100 | 100 | 100 | 100 | 100 | 100 | 99.75 | 100 | 100 | 100 | 95.00 | 100 |
| 12 | AN123 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| 13 | AN0123 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 |
| Scenario No. | Scenario | RGNN (%) | fastRGNN (%) | RGAT (%) | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| N0 | N1 | N2 | N3 | N4 | N5 | N0 | N1 | N2 | N3 | N4 | N5 | N0 | N1 | N2 | N3 | N4 | N5 | ||
| 1 | D1 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.89 | 99.33 | 99.44 | 99.22 | 99.89 | 99.33 |
| 2 | D2 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.44 | 99.67 | 99.67 | 99.78 | 99.56 |
| 3 | D3 | 100 | 99.89 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.89 | 99.00 | 99.67 | 100 | 100 | 99.89 |
| 4 | D4 | 100 | 99.89 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.89 | 99.44 | 99.89 | 100 | 99.78 | 99.67 |
| 5 | AN0 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 87.89 | 98.78 | 100 | 100 |
| 6 | AN1 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.75 | 98.75 | 100 | 100 | 100 | 100 | 13.33 | 100 | 99.75 | 99.44 |
| 7 | AN2 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.50 | 100 | 100 | 93.78 | 100 | 99.44 |
| 8 | AN3 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.75 | 99.75 | 100 | 100 | 100 | 100 | 100 | 99.75 | 100 | 99.89 | 100 |
| 9 | AN4 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 66.50 | 100 | 100 |
| 10 | AN5 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 99.75 | 100 | 100 | 100 | 100 | 100 |
| Model | Swarm-1 | Swarm-2 | ||||||
|---|---|---|---|---|---|---|---|---|
| OA (%) | AR (%) | DR (All Anomalous) (%) | DR (Propagated Anomalous) (%) | OA (%) | AR (%) | DR (All Anomalous) (%) | DR (Propagated Anomalous) (%) | |
| SAGEConv | 99.82 | 99.89 | 99.79 | 99.71 | 99.96 | 99.99 | 99.95 | 99.90 |
| EdgeConv | 99.80 | 99.89 | 99.76 | 99.67 | 99.96 | 100.00 | 99.93 | 99.88 |
| GATConv | 93.31 | 99.91 | 90.37 | 85.59 | 94.96 | 99.98 | 91.62 | 85.44 |
| GIN | 97.58 | 99.89 | 96.56 | 95.20 | 94.54 | 99.97 | 90.91 | 86.38 |
| RGNN | 99.94 | 99.89 | 99.97 | 99.97 | 100.00 | 99.99 | 100.00 | 100.00 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rouagubi, A.; El Youssofi, C.; Chougdali, K. Firmware Attestation in IoT Swarms Using Relational Graph Neural Networks and Static Random Access Memory. AI 2025, 6, 161. https://doi.org/10.3390/ai6070161
Rouagubi A, El Youssofi C, Chougdali K. Firmware Attestation in IoT Swarms Using Relational Graph Neural Networks and Static Random Access Memory. AI. 2025; 6(7):161. https://doi.org/10.3390/ai6070161
Chicago/Turabian StyleRouagubi, Abdelkabir, Chaymae El Youssofi, and Khalid Chougdali. 2025. "Firmware Attestation in IoT Swarms Using Relational Graph Neural Networks and Static Random Access Memory" AI 6, no. 7: 161. https://doi.org/10.3390/ai6070161
APA StyleRouagubi, A., El Youssofi, C., & Chougdali, K. (2025). Firmware Attestation in IoT Swarms Using Relational Graph Neural Networks and Static Random Access Memory. AI, 6(7), 161. https://doi.org/10.3390/ai6070161






