Block-CITE: A Blockchain-Based Crowdsourcing Interactive Trust Evaluation
Abstract
1. Introduction
- We propose a Blockchain-based Crowdsourcing Interactive Trust Evaluation (Block-CITE) scheme, which operates in a decentralized way. Unlike previous works, Block-CITE is able to guarantee security by allowing users to take part in the blockchain-based crowdsourcing service without revealing their true identities and storing the hash value of trademark materials and examination results to the blockchain. As such, the ownership of anonymous users for their trademark materials can be guaranteed.
- A concrete scheme is presented in this work, and smart contract are utilized for performing the whole process of the proposed scheme, Block-CITE. As such, the functions of crowdsourcing for trademark examination can be realized without trusting any centralized entity.
- A detailed security analysis of Block-CITE is undertaken in this paper. Specifically, we conduct a simulation on the well-known 51% attack in the blockchain network, and we also provide a theoretical proof of blockchain security. Both the simulation result and the theoretical proof of security show that Block-CITE is secure enough for industrial trademark examination.
2. Related Works
2.1. Centralized Crowdsourcing Solutions
2.2. Distributed Crowdsourcing Solutions
2.3. Blockchain-Based Crowdsourcing Solutions
3. Preliminaries
3.1. Bilinear Pairing
- Equation holds, where and .
- In polynomial time, there exists an efficient algorithm to compute the bilinearty equation.
- , in the case where g is a generator of .
3.2. Blockchain
3.3. Smart Contract
4. Block-CITE: A Blockchain-Based Crowdsourcing Interactive Trust Evaluation Method
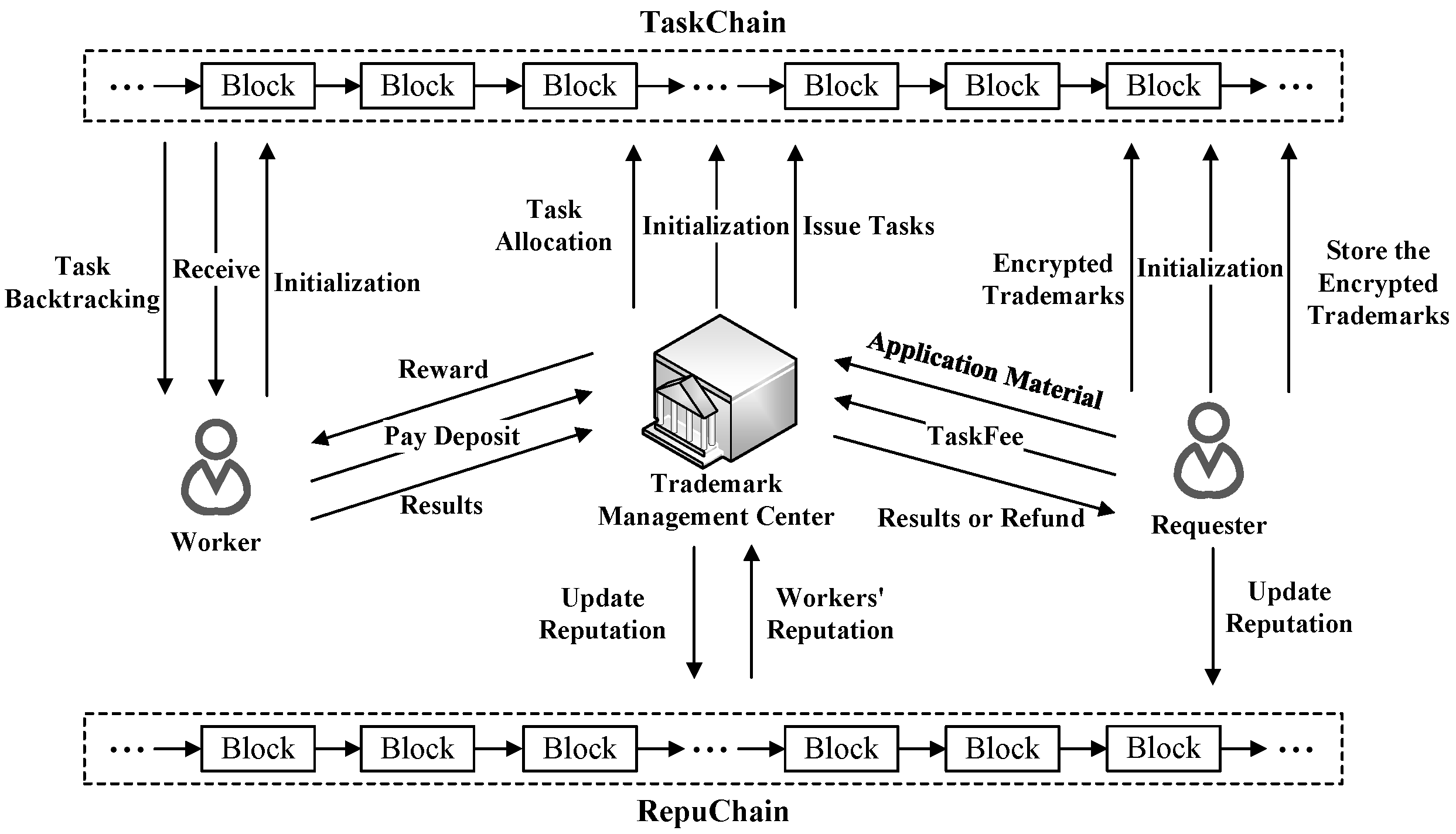
4.1. Overview
4.2. The Protocol of Block-CITE
4.2.1.
4.2.2.
4.2.3.
4.2.4.
4.2.5.
4.2.6.
4.3. Smart Contracts for Block-CITE
4.3.1. Initialization Contract
| Algorithm 1 Initialization. |
Input: random integer k, group generator g, random integer , key generation function , secure hash function Output:
Begin
End |
4.3.2. Requesting Contract
| Algorithm 2 Requesting. |
Input: System parameter , plaintext of trademark material M, public key of TMC Output: Ciphertext of trademark material , the set of digital signature , hash value h Begin
End |
4.3.3. Receiving Contract
| Algorithm 3 Receiving. |
Input: Ciphertext of the trademark material , private key of the TMC , public signature key of the requester , the set of digital signature Output: Transactions information , the set of tasks Begin
End |
4.3.4. Submitting Contract
| Algorithm 4 Submitting. |
Input: Plaintext of the trademark material M, the set of task Output: the set of solution Begin
End |
4.3.5. Reward Paying Contract
| Algorithm 5 Reward Paying. |
Input: The set of task , the set of solution Output: Rewards to worker , compensation to requester Begin
End |
5. Security Analysis
5.1. Setup
5.2. Threat Model
5.2.1. Malicious Requesters
5.2.2. Malicious Workers
5.2.3. Malicious Miners
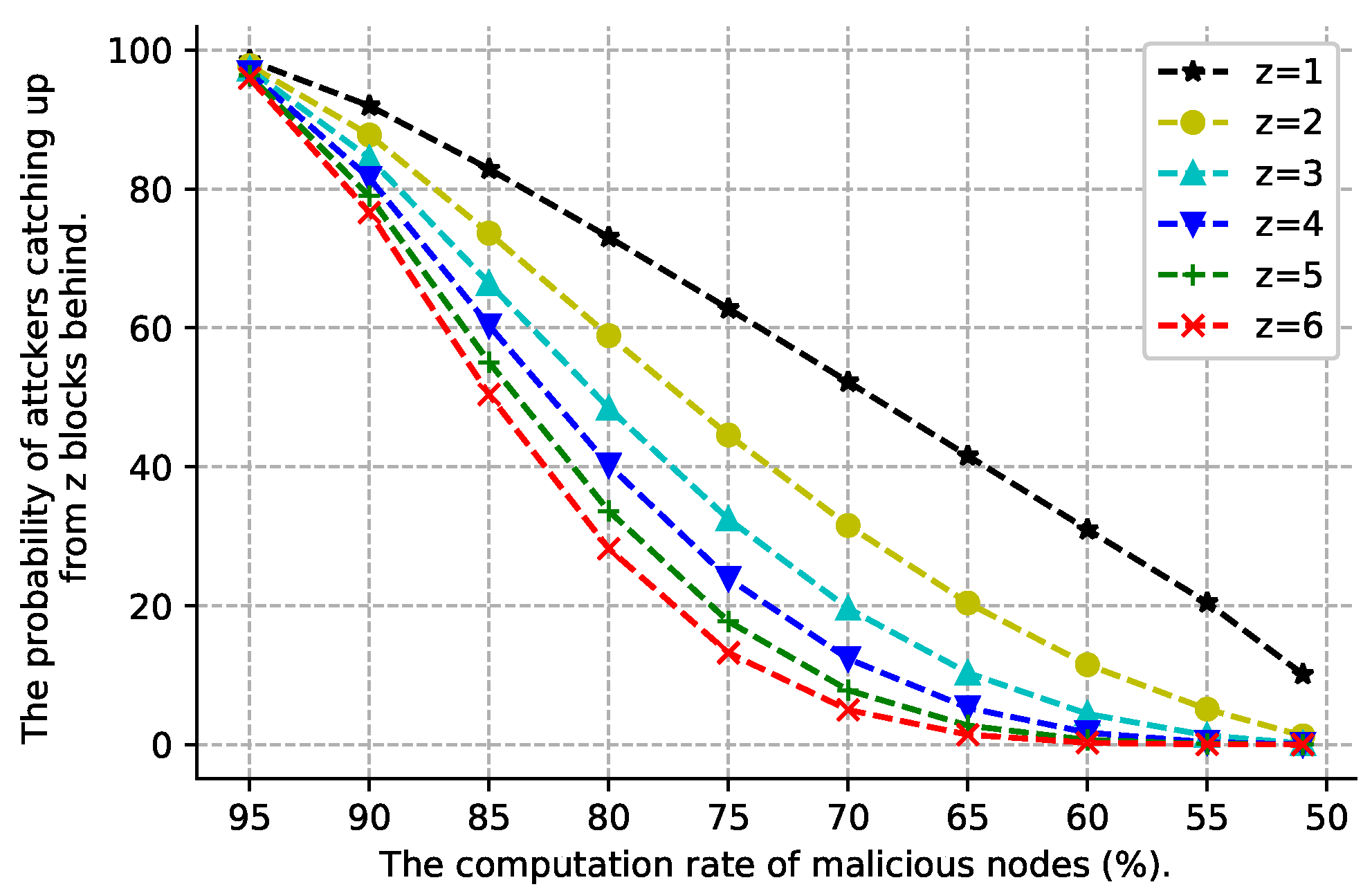
5.3. Blockchain Security
6. Performance Analysis
6.1. Setup
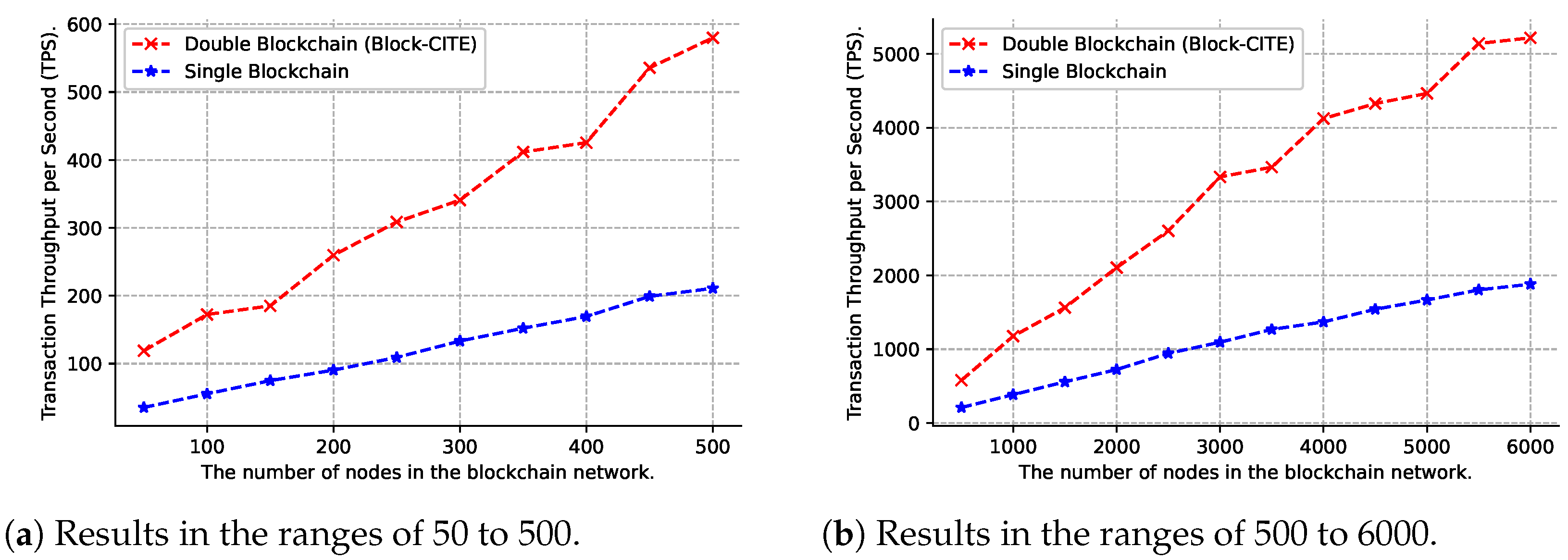
6.2. Transaction Throughput
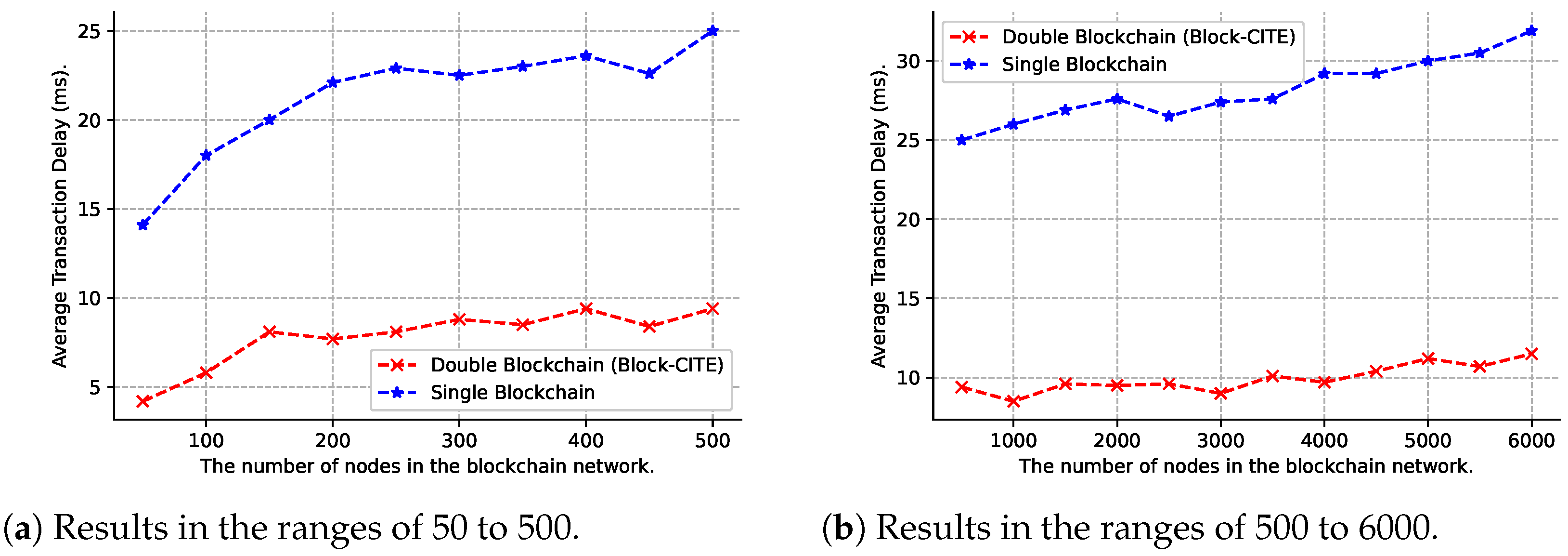
6.3. Transaction Delay
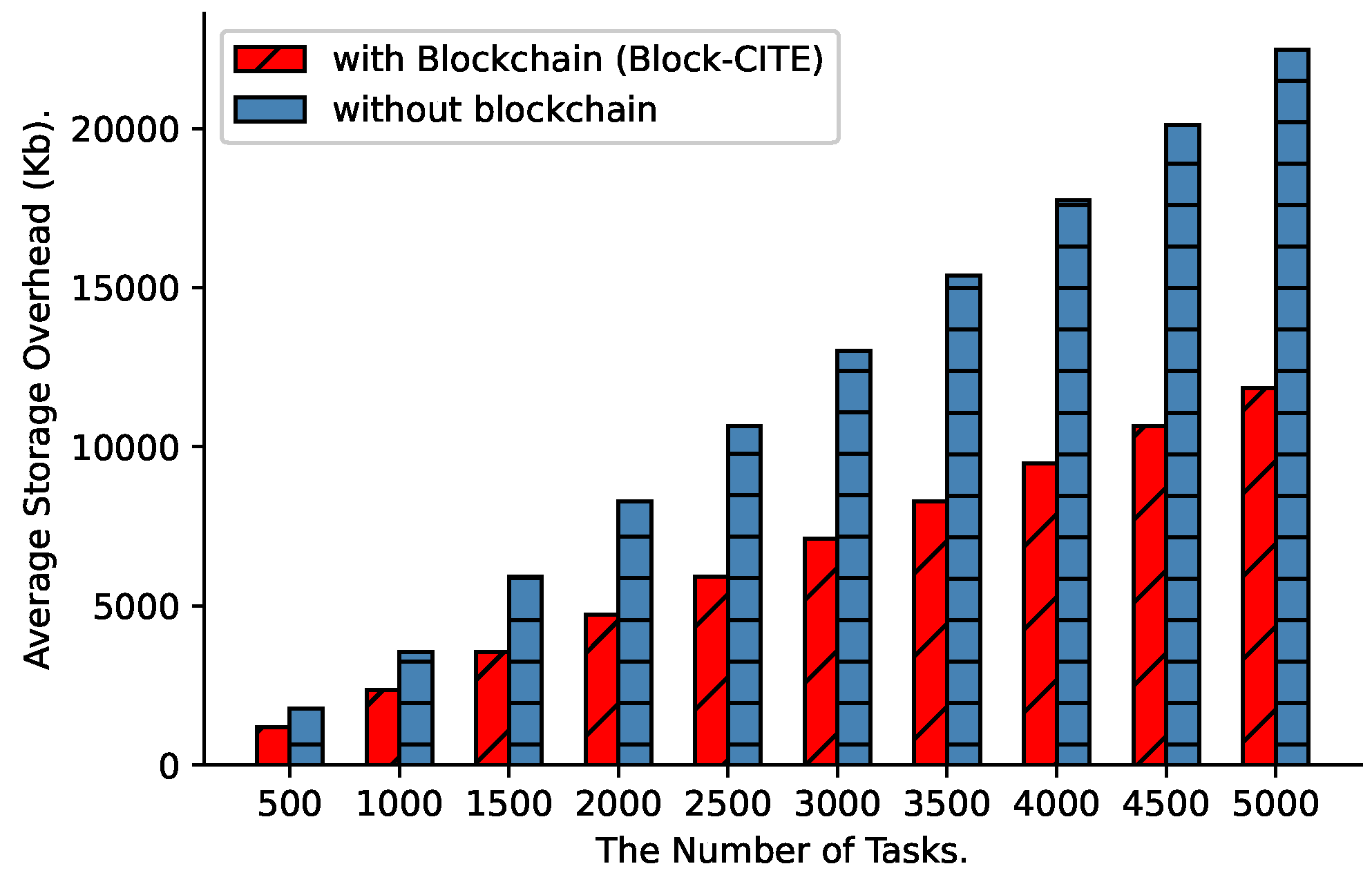
6.4. Storage Overhead
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Fu, X.; Wang, H.; Shi, P. A survey of Blockchain consensus algorithms: Mechanism, design and applications. Sci. China Inf. Sci. 2021, 64, 1–15. [Google Scholar]
- Ma, Y.; Sun, Y.; Lei, Y.; Qin, N.; Lu, J. A survey of blockchain technology on security, privacy, and trust in crowdsourcing services. World Wide Web 2020, 23, 393–419. [Google Scholar] [CrossRef]
- Howe, J. The rise of crowdsourcing. Wired Mag. 2006, 14, 176–183. [Google Scholar]
- Chittilappilly, A.I.; Chen, L.; Amer-Yahia, S. A survey of general-purpose crowdsourcing techniques. IEEE Trans. Knowl. Data Eng. 2016, 28, 2246–2266. [Google Scholar] [CrossRef]
- Kadadha, M.; Singh, S.; Mizouni, R.; Otrok, H. A Context-Aware Blockchain-Based Crowdsourcing Framework: Open Challenges and Opportunities. IEEE Access 2022, 10, 93659–93673. [Google Scholar] [CrossRef]
- Zhang, G.; Yang, Z.; Liu, W. Blockchain-based privacy preserving e-health system for healthcare data in cloud. Comput. Netw. 2022, 203, 108586. [Google Scholar]
- Liao, Z.; Ai, J.; Liu, S.; Zhang, Y.; Liu, S. Blockchain-based mobile crowdsourcing model with task security and task assignment. Expert Syst. Appl. 2023, 211, 118526. [Google Scholar] [CrossRef]
- Shinde, S.M.; Gurrala, V.R. Securing trustworthy evidence for robust forensic cloud-blockchain environment for immigration management with improved ECC encryption. Expert Syst. Appl. 2023, 229, 120478. [Google Scholar] [CrossRef]
- Wan, X.; Teng, Z.; Li, Q.; Deveci, M. Blockchain technology empowers the crowdfunding decision-making of marine ranching. Expert Syst. Appl. 2023, 221, 119685. [Google Scholar] [CrossRef]
- Yang, H.; Yang, Z.; Xiang, S.; Zhao, H.; Ackom, E. A Double-Chain Blockchain With Economic Attributes and Network Constraints of Prosumer Transactions. IEEE Trans. Ind. Inform. 2022, 19, 2351–2362. [Google Scholar] [CrossRef]
- Wang, W.; Wang, L.; Zhang, P.; Xu, S.; Fu, K.; Song, L.; Hu, S. A privacy protection scheme for telemedicine diagnosis based on double blockchain. J. Inf. Secur. Appl. 2021, 61, 102845. [Google Scholar] [CrossRef]
- Ren, W.; Wan, X.; Gan, P. A double-blockchain solution for agricultural sampled data security in Internet of Things network. Future Gener. Comput. Syst. 2021, 117, 453–461. [Google Scholar] [CrossRef]
- Li, Z.; Hao, J.; Liu, J.; Wang, H.; Xian, M. An IoT-applicable access control model under double-layer blockchain. IEEE Trans. Circuits Syst. Ii Express Briefs 2020, 68, 2102–2106. [Google Scholar]
- Huang, X.; Wu, J.; Li, J.; Xia, C. BEADS: Blockchain-Empowered Auction in Decentralized Storage. In Proceedings of the 2021 IEEE International Conference on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), New York City, NY, USA, 30 September–3 October 2021; pp. 368–373. [Google Scholar]
- Peng, S.; Hu, X.; Zhang, J.; Xie, X.; Long, C.; Tian, Z.; Jiang, H. An efficient double-layer blockchain method for vaccine production supervision. IEEE Trans. Nanobiosci. 2020, 19, 579–587. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Van der Schaar, M. Reputation-based incentive protocols in crowdsourcing applications. In Proceedings of the 2012 Proceedings IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 2140–2148. [Google Scholar]
- Ni, J.; Zhang, A.; Lin, X.; Shen, X.S. Security, privacy, and fairness in fog-based vehicular crowdsensing. IEEE Commun. Mag. 2017, 55, 146–152. [Google Scholar] [CrossRef]
- Zhang, X.; Xue, G.; Yu, R.; Yang, D.; Tang, J. Keep your promise: Mechanism design against free-riding and false-reporting in crowdsourcing. IEEE Internet Things J. 2015, 2, 562–572. [Google Scholar]
- Lu, Z.; Wang, Y.; Tong, X.; Mu, C.; Chen, Y.; Li, Y. Data-driven many-objective crowd worker selection for mobile crowdsourcing in industrial IoT. IEEE Trans. Ind. Inform. 2021, 19, 531–540. [Google Scholar] [CrossRef]
- Ma, R.; Feng, T.; Xiong, J.; Li, Q.; Tian, Y. DScPA: A Dynamic Sub-cluster Privacy-preserving Aggregation Scheme for Mobile Crowdsourcing in Industrial IoT. IEEE Internet Things J. 2023, 11, 1880–1892. [Google Scholar] [CrossRef]
- Zhang, S.; Wu, J.; Lu, S. Minimum makespan workload dissemination in DTNs: Making full utilization of computational surplus around. In Proceedings of the Fourteenth ACM International Symposium on Mobile Ad Hoc Networking and Computing, Bangalore, India, 29 July 2–1 August 2013; pp. 293–296. [Google Scholar]
- Yang, P.; Li, Q.; Yan, Y.; Li, X.Y.; Xiong, Y.; Wang, B.; Sun, X. “Friend is treasure”: Exploring and exploiting mobile social contacts for efficient task offloading. IEEE Trans. Veh. Technol. 2015, 65, 5485–5496. [Google Scholar] [CrossRef]
- Cheung, M.H.; Southwell, R.; Hou, F.; Huang, J. Distributed time-sensitive task selection in mobile crowdsensing. In Proceedings of the 16th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Hangzhou, China, 22–25 June 2015; pp. 157–166. [Google Scholar]
- Wang, X.; Tushar, W.; Yuen, C.; Zhang, X. Promoting users’ participation in mobile crowdsourcing: A distributed truthful incentive mechanism (DTIM) approach. IEEE Trans. Veh. Technol. 2020, 69, 5570–5582. [Google Scholar] [CrossRef]
- Li, M.; Wu, J.; Wang, W.; Zhang, J. Toward privacy-preserving task assignment for fully distributed spatial crowdsourcing. IEEE Internet Things J. 2021, 8, 13991–14002. [Google Scholar] [CrossRef]
- Xu, Y.; Xiao, M.; Liu, A.; Wu, J. Edge resource prediction and auction for distributed spatial crowdsourcing with differential privacy. IEEE Internet Things J. 2022, 9, 15554–15569. [Google Scholar] [CrossRef]
- Hasan, F.A.; Ashqar, H.I.; AlSobeh, A.; Darwish, O. Blockchain-Based National Digital Identity Framework–Case of Palestine. In Proceedings of the 2024 International Conference on Intelligent Computing, Communication, Networking and Services (ICCNS), Dubrovnik, Croatia, 24–27 September 2024; pp. 76–83. [Google Scholar]
- AlSobeh, A.M.; Magableh, A.A. BlockASP: A framework for AOP-based model checking blockchain system. IEEE Access 2023, 11, 115062–115075. [Google Scholar] [CrossRef]
- AlSobeh, A. OSM: Leveraging model checking for observing dynamic 1 behaviors in aspect-oriented applications. arXiv 2024, arXiv:2403.01349. [Google Scholar] [CrossRef]
- Harasees, A.; Al-Ahmad, B.; Alsobeh, A.; Abuhussein, A. A secure IoT framework for remote health monitoring using fog computing. In Proceedings of the 2024 International Conference on Intelligent Computing, Communication, Networking and Services (ICCNS), Dubrovnik, Croatia, 24–27 September 2024; pp. 17–24. [Google Scholar]
- Li, M.; Weng, J.; Yang, A.; Lu, W.; Zhang, Y.; Hou, L.; Liu, J.N.; Xiang, Y.; Deng, R.H. CrowdBC: A blockchain-based decentralized framework for crowdsourcing. IEEE Trans. Parallel Distrib. Syst. 2018, 30, 1251–1266. [Google Scholar]
- Zou, J.; Ye, B.; Qu, L.; Wang, Y.; Orgun, M.A.; Li, L. A proof-of-trust consensus protocol for enhancing accountability in crowdsourcing services. IEEE Trans. Serv. Comput. 2018, 12, 429–445. [Google Scholar]
- Yang, M.; Zhu, T.; Liang, K.; Zhou, W.; Deng, R.H. A blockchain-based location privacy-preserving crowdsensing system. Future Gener. Comput. Syst. 2019, 94, 408–418. [Google Scholar]
- Tong, W.; Dong, X.; Shen, Y.; Zhang, Y.; Jiang, X.; Tian, W. CHChain: Secure and parallel crowdsourcing driven by hybrid blockchain. Future Gener. Comput. Syst. 2022, 131, 279–291. [Google Scholar] [CrossRef]
- Fu, S.; Huang, X.; Liu, L.; Luo, Y. BFCRI: A Blockchain-Based Framework for Crowdsourcing With Reputation and Incentive. IEEE Trans. Cloud Comput. 2022, 11, 2158–2174. [Google Scholar] [CrossRef]
- Wang, W.; Wang, Y.; Duan, P.; Liu, T.; Tong, X.; Cai, Z. A triple real-time trajectory privacy protection mechanism based on edge computing and blockchain in mobile crowdsourcing. IEEE Trans. Mob. Comput. 2022, 22, 5625–5642. [Google Scholar] [CrossRef]
- Nakamoto, S.; Bitcoin, A. A peer-to-peer electronic cash system. Bitcoin 2008, 4, 15. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 11 September 2025).
- Szabo, N. Smart contracts: Building blocks for digital markets. EXTROPY J. Transhumanist Thought 1996, 18, 28. [Google Scholar]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Project Yellow Pap. 2014, 151, 1–32. Available online: https://cryptodeep.ru/doc/paper.pdf (accessed on 11 September 2025).
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V.S. Use of elliptic curves in cryptography. In Proceedings of the Conference on the Theory and Application of Cryptographic Techniques, Linz, Austria, 9–11 April 1985; Springer: Berlin/Heidelberg, Germany, 1985; pp. 417–426. [Google Scholar]
- Zhang, J.; Hong, Z.; Qiu, X.; Zhan, Y.; Guo, S.; Chen, W. Skychain: A deep reinforcement learning-empowered dynamic blockchain sharding system. In Proceedings of the 49th International Conference on Parallel Processing, Edmonton, AB, Canada, 17–20 August 2020; pp. 1–11. [Google Scholar]
- Garay, J.; Kiayias, A.; Leonardos, N. The bitcoin backbone protocol: Analysis and applications. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, 26–30 April 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 281–310. [Google Scholar]
- Alharby, M.; Van Moorsel, A. Blocksim: A simulation framework for blockchain systems. ACM Sigmetrics Perform. Eval. Rev. 2019, 46, 135–138. [Google Scholar] [CrossRef]
- Kalodner, H.; Möser, M.; Lee, K.; Goldfeder, S.; Plattner, M.; Chator, A.; Narayanan, A. {BlockSci}: Design and applications of a blockchain analysis platform. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August; 2020; pp. 2721–2738. [Google Scholar]

| Symbol | Meaning |
|---|---|
| n | Total number of nodes in the blockchain network |
| M | Plaintext of the trademark material |
| Ciphertext of the trademark material | |
| ith data block of M | |
| Encrypted data block of | |
| Digital signature of | |
| Set of | |
| Information of a trademark application | |
| ith task of trademark application | |
| Set of | |
| ith requester | |
| ith worker | |
| Solution of the ith task | |
| Set of | |
| Number of tasks finished in time | |
| Number of tasks finished over time | |
| Payment that a task needs to pay | |
| Reputation of the worker scored by the requester | |
| Reputation of the worker scored by the TMC | |
| Head of the block at the current epoch | |
| Random number in the blockhead at the current epoch |
| Symbol | Meaning |
|---|---|
| n | Number of total nodes |
| Percentage of malicious nodes | |
| s | Probability of a miner providing a PoW solution |
| Average time latency to accept the new block for a miner | |
| z | Number of blocks that malicious node lags behind the longest chain |
| c | Computation times in a round |
| T | Current time |
| P | Computation power of honest nodes |
| Q | Computation power of malicious nodes |
| Probability of honest nodes generating a new block | |
| L | Lower bound of the probability that honest nodes generate the new block in a round |
| Number of blocks mined by honest nodes | |
| Number of blocks mined by malicious blocks |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, J.; Jiang, L.; Liang, H.; Peng, T.; Wang, S.; Wei, H. Block-CITE: A Blockchain-Based Crowdsourcing Interactive Trust Evaluation. AI 2025, 6, 245. https://doi.org/10.3390/ai6100245
Li J, Jiang L, Liang H, Peng T, Wang S, Wei H. Block-CITE: A Blockchain-Based Crowdsourcing Interactive Trust Evaluation. AI. 2025; 6(10):245. https://doi.org/10.3390/ai6100245
Chicago/Turabian StyleLi, Jiaxing, Lin Jiang, Haoxian Liang, Tao Peng, Shaowei Wang, and Huanchun Wei. 2025. "Block-CITE: A Blockchain-Based Crowdsourcing Interactive Trust Evaluation" AI 6, no. 10: 245. https://doi.org/10.3390/ai6100245
APA StyleLi, J., Jiang, L., Liang, H., Peng, T., Wang, S., & Wei, H. (2025). Block-CITE: A Blockchain-Based Crowdsourcing Interactive Trust Evaluation. AI, 6(10), 245. https://doi.org/10.3390/ai6100245





