Automated Over-the-Top Service Copyright Distribution Management System Using the Open Digital Rights Language
Abstract
1. Introduction
2. Background
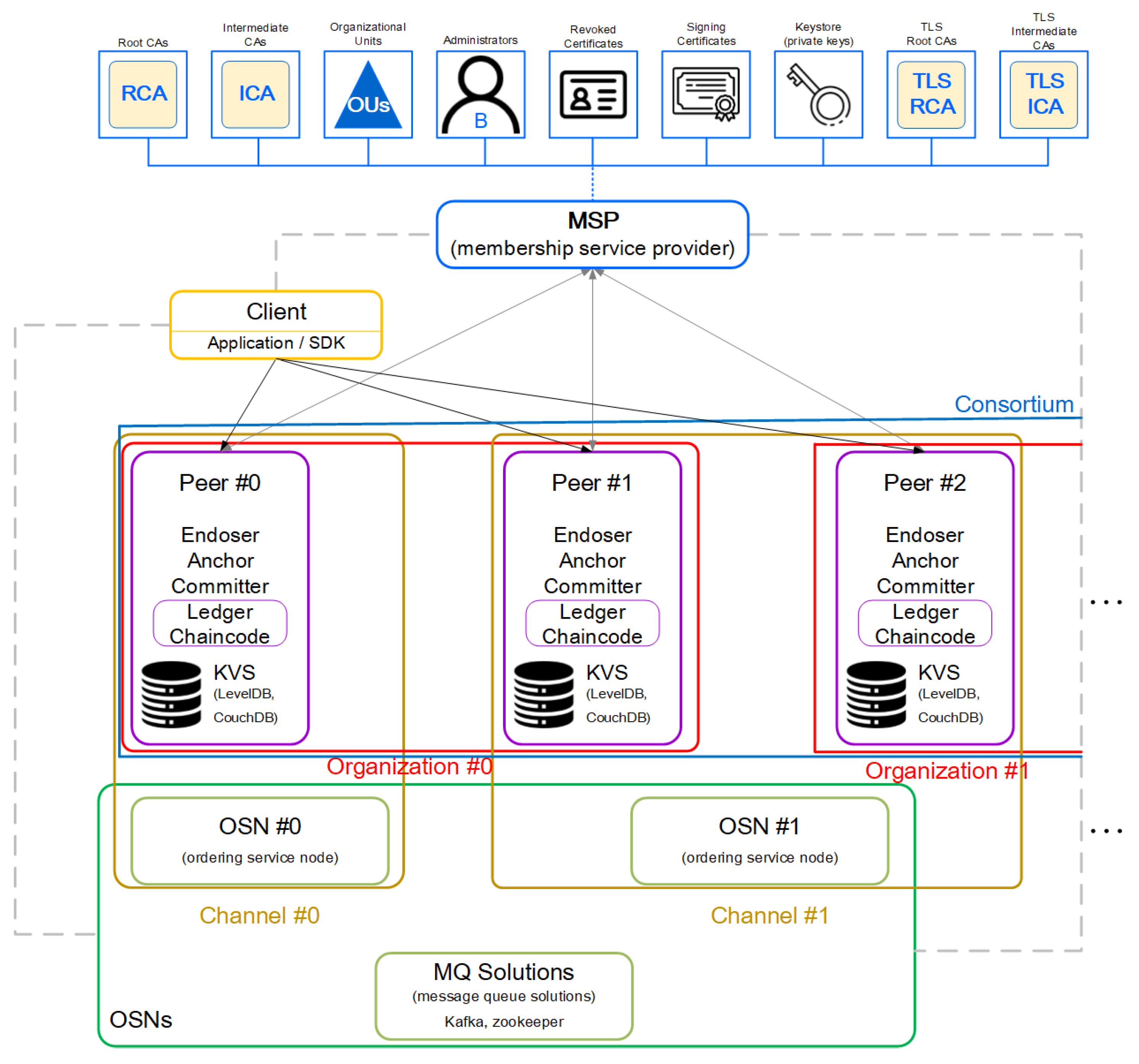
2.1. Hyperledger Fabric
- The client forwards the signed transaction proposal to the predefined Endorser.
- The Endorser checks whether the signature of the transaction proposal received from the client is valid, and if valid, executes the chaincode based on the parameters of the transaction proposal and delivers the transaction results (including Read set and Write set) to the client.
- The client checks whether the signature value of the returned transaction result matches the Endorser’s signature value.
- If the reliability of the transaction result returned through Process 3 is guaranteed, it is delivered to the ordering service node.
- As the ordering service node receives already verified transaction results from the client, it organizes them by channel and time to create a transaction block per channel.
- Transaction blocks per channel generated by the ordering service node are broadcast to all peer nodes on the Blockchain network.
- All peer nodes verify the validity by checking the contents of the R/W set, such as guarantee policy and ledger state changes, based on the received transaction block, and if verification is successful, they commit it to the world state.
2.2. Smart Contract
2.3. ODRL
 |
3. Preliminaries
- (1)
- Lack of privacy protection measures for sensitive data related to digital content copyright (e.g., information on copyright holders, sales proceeds, etc.).
- (2)
- Absence of smart contract signing approach that considers multiple stakeholders.
- (3)
- Lack of a fair and transparent mechanism for the settlement and distribution of digital content royalties.
- (4)
- Absence of a method to verify users’ rights to access digital content.
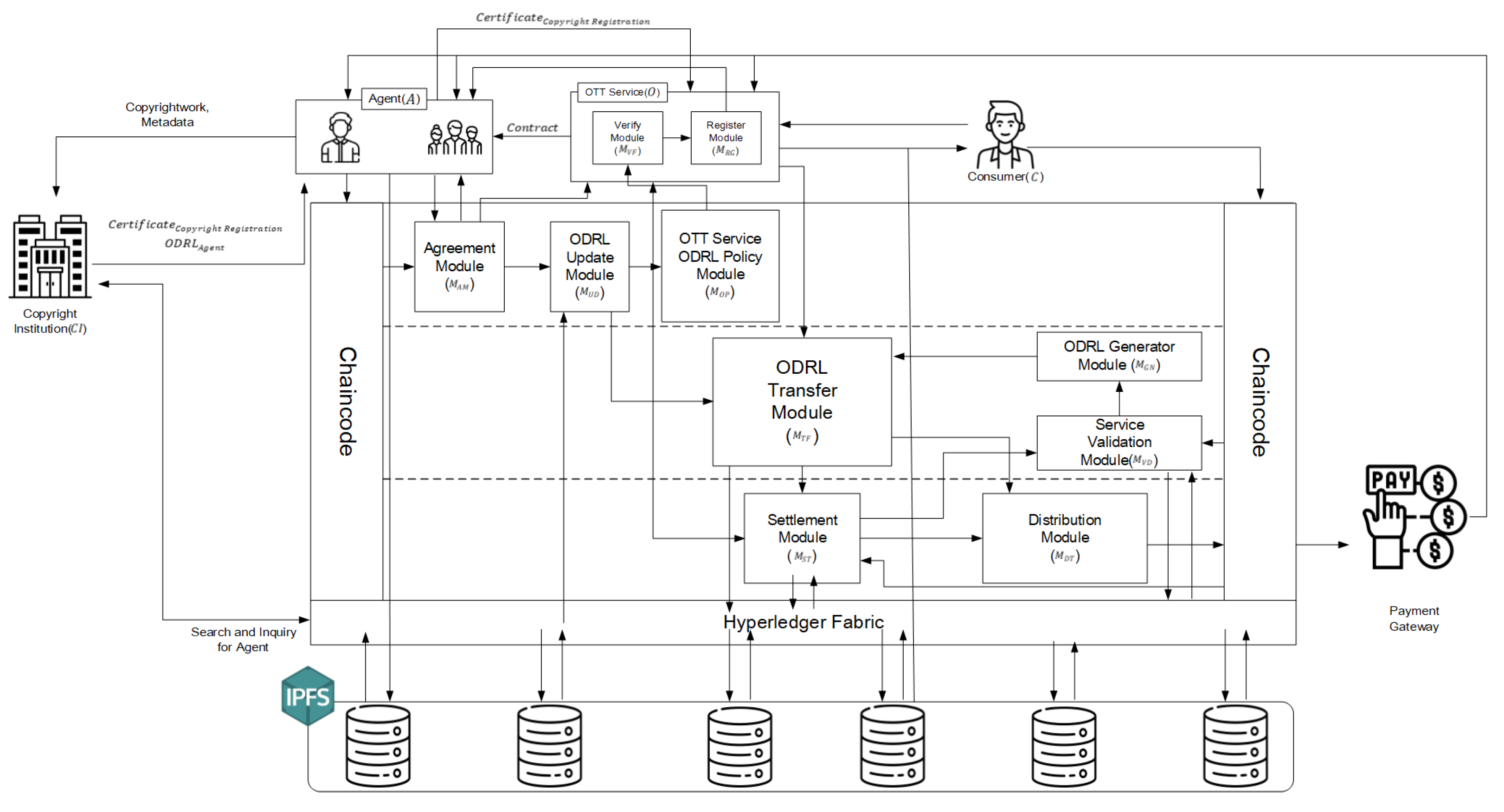
4. Proposed System
- (1)
- The proposed system employs zero-knowledge proofs to safeguard sensitive information in digital content transactions, effectively preventing privacy infringements.
- (2)
- The proposed system ensures the distribution of digital content is based on the signatures of all joint copyright holders, taking into account multiple joint copyright holders.
- (3)
- The proposed system automatically verifies the usage rights of consumers as stated in the ODRL and provides digital content accordingly.
- (4)
- The proposed system automatically extracts information related to copyright royalties distribution from the ODRL and performs settlement and distribution of copyright royalties, considering the joint copyright holders.
- (1)
- It is assumed that when A creates , A submit metadata, which includes information about among copyright holders, to in each country.
- (2)
- Assuming that has received from the process outlined in Assumption (1), it is assumed that they have verified this . Once verification is complete, they are presumed to have issued and based on the received Metadata to A.
- (1)
- Register Phase: Through a with O, A registers their on the InterPlanetary File System (IPFS).
- (2)
- Usage Phase: wishing to access on O pay a . This establishes ’ to use the , resulting in the being specifically provided to these in alignment with their established .
- (3)
- Settlement/Distribution Phase: A transparent and fair settlement and distribution of are performed based on the paid by numerous .
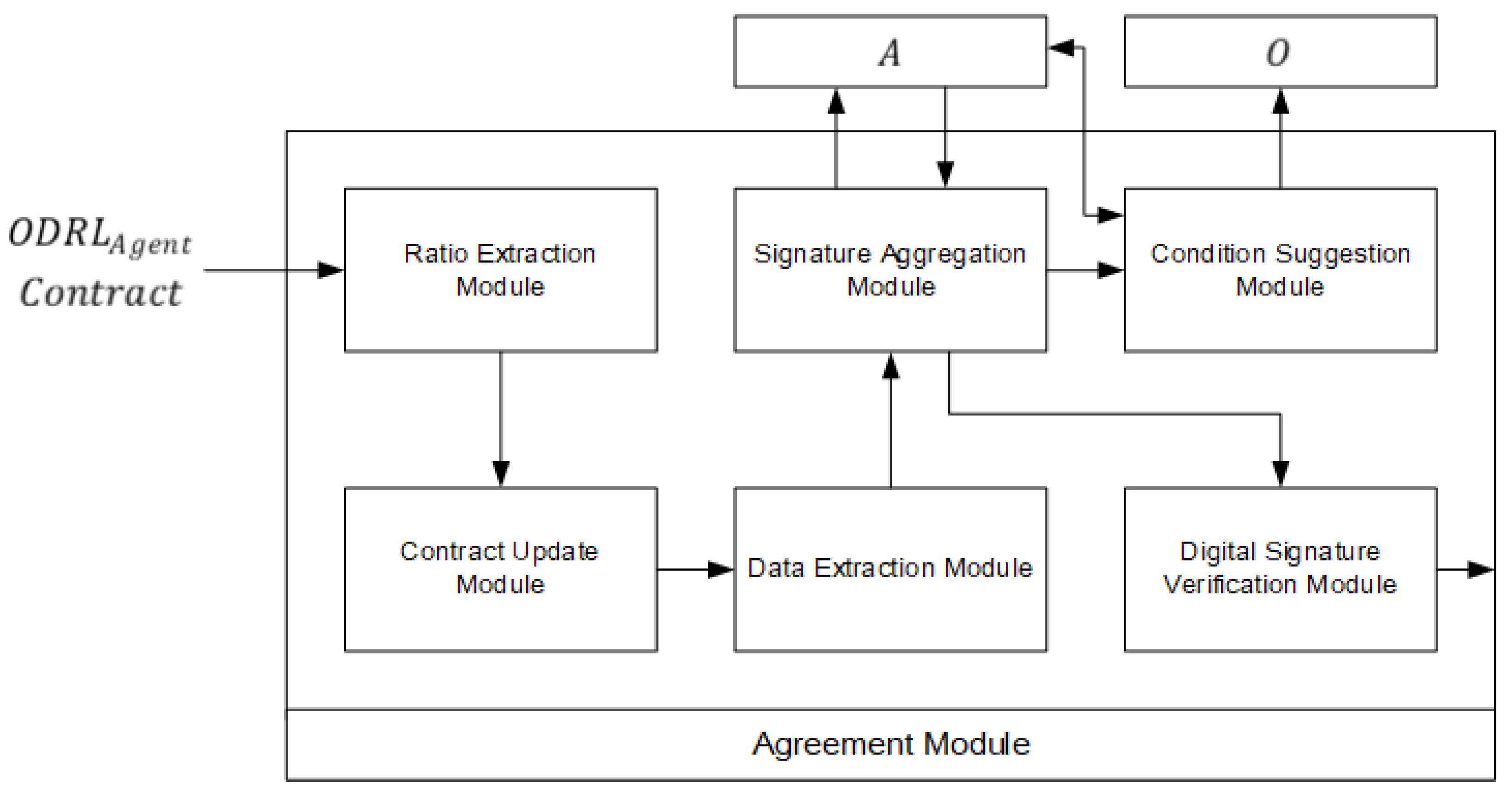
4.1. Register Phase
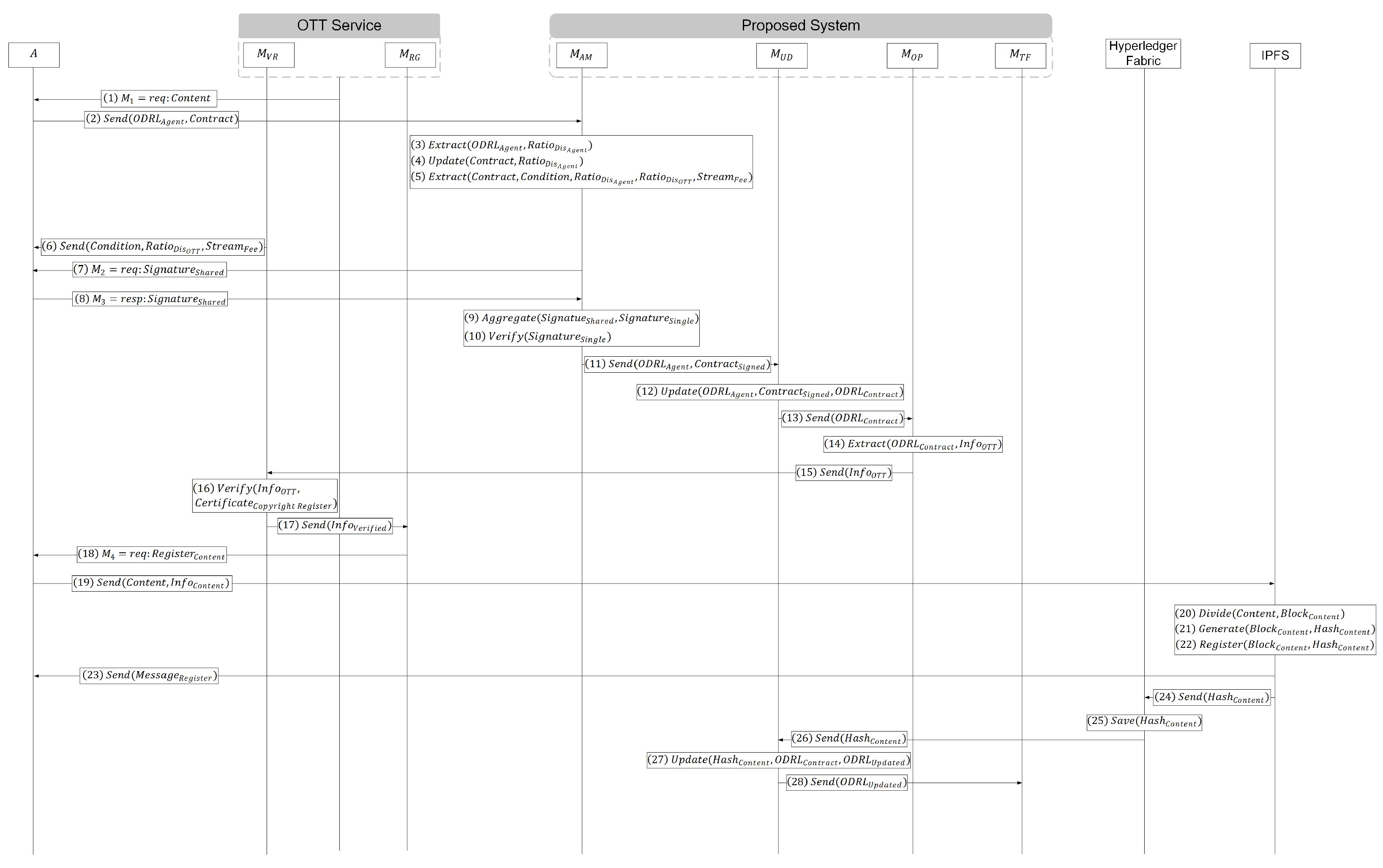
- (1)
- O delivers a to A who owns the copyright for the to be registered in its service.
- (2)
- A delivers the issued from to along with the delivered .
- (3)
- , upon receiving the , extracts from its contents, applicable when A is composed of multiple copyright holders.
- (4)
- proceeds to update the by incorporating the obtained in Step (3).
- (5)
- Following this, extracts the , , , and from the updated as per Step (4).
- (6)
- sends the extracted , , , and to A as derived in Step (5).
- (7)
- requests a from A.
- (8)
- Copyright holders within A, in agreement with the information extracted in Step (5), proceed to sign, thereby sending back a as a response.
- (9)
- aggregates the received in Step (8). Once all copyright holders have signed, a single signature value is derived.
- (10)
- then verifies the validity of the generated in Step (9).
- (11)
- Upon verifying the in Step (10) and confirming the consensus of all copyright holders on the terms, sends the and the to . Additionally, A forwards the , received from , to O’s .
- (12)
- creates the by adding and updating the received in Step (11) to the .
- (13)
- then sends the to .
- (14)
- extracts from the , which is used to verify in O.
- (15)
- sends the extracted to O’s .
- (16)
- compares the information in the received from A in Step (11) with the received from in Step (15).
- (17)
- of O, through Step (16), verifies the match of information and then sends to .
- (18)
- Upon receiving from , which confirms the validation of the in Step (17), requests from A.
- (19)
- A, upon receiving a request for from within O, sends the and to IPFS.
- (20)
- IPFS divides the received from A into smaller fragments to create .
- (21)
- A unique is generated for the created .
- (22)
- IPFS registers the created in Step (20) and the generated in Step (21) within the IPFS network, thereby forming a distributed file system.
- (23)
- IPFS sends a to A, indicating the completion of the registration.
- (24)
- IPFS sends the to Hyperledger Fabric.
- (25)
- Hyperledger Fabric stores the received through process (24) in its ledger.
- (26)
- Hyperledger Fabric then sends the stored to .
- (27)
- adds the received in Step (26) to the , creating an .
- (28)
- forwards the , created in Step (27), to .
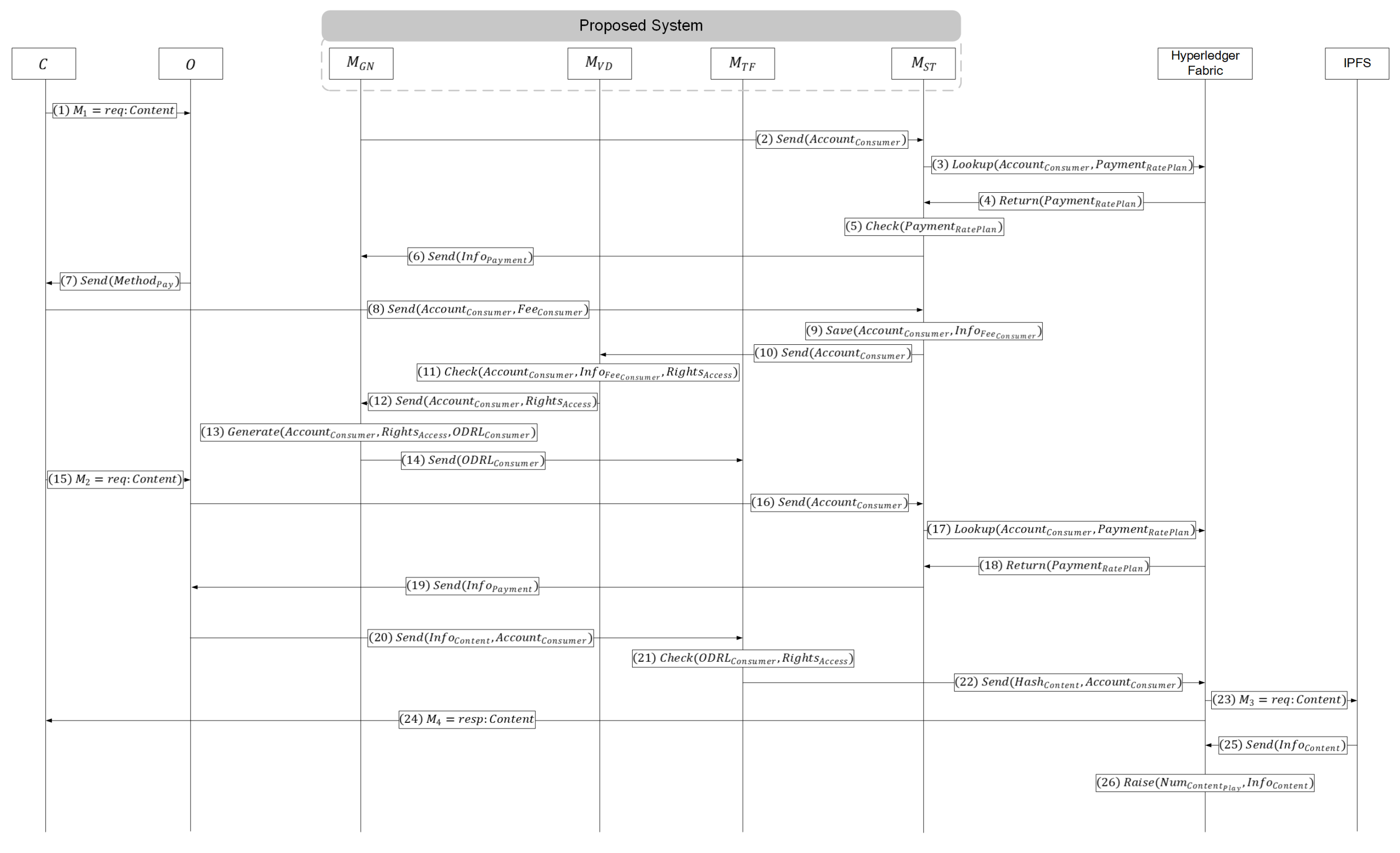
4.2. Usage Phase
- (1)
- C requests playback of the they wish to use through O that owns the .
- (2)
- O sends the of C who requested the playback to .
- (3)
- queries the based on the in Hyperledger Fabric.
- (4)
- Hyperledger Fabric returns the corresponding to the to .
- (5)
- checks the received in Step (4).
- (6)
- , based on the checked in Step (5), verifies that C has not made a payment and sends to O.
- (7)
- O, upon confirming that C has not made the required for using O, provides C with limited playback of along with .
- (8)
- C sends , corresponding to their desired rate plan, to , along with their .
- (9)
- stores in the .
- (10)
- then sends the updated to as per Step (9).
- (11)
- determines the specific rate plan corresponding to the payment made, as indicated by the in the received , and confirms the associated .
- (12)
- Following this, sends the , along with the confirmedfrom Step (11), to .
- (13)
- creates based on the and .
- (14)
- then sends the to .
- (15)
- who have gained for the registered on O re-request the playback of their selected from O.
- (16)
- O sends the details to .
- (17)
- retrieves the from Hyperledger Fabric, using theinformation as a reference.
- (18)
- Hyperledger Fabric provides with the associated with the .
- (19)
- then sends the of C, who has requested playback, to O.
- (20)
- After verifying that C who requested playback has completed the payment, O sends both the and the requested by C to .
- (21)
- checks C’s based on the received from during Step (14).
- (22)
- Once confirms that the specific C has gained for the , it sends the and details to Hyperledger Fabric.
- (23)
- Hyperledger Fabric, upon receiving the , instructs IPFS to send the , which matches the , to C associated with .
- (24)
- Following this request, IPFS delivers the specified to C.
- (25)
- After providing the , IPFS sends the , detailing the delivered, back to Hyperledger Fabric.
- (26)
- Hyperledger Fabric then increments the count by one, based on the it received.
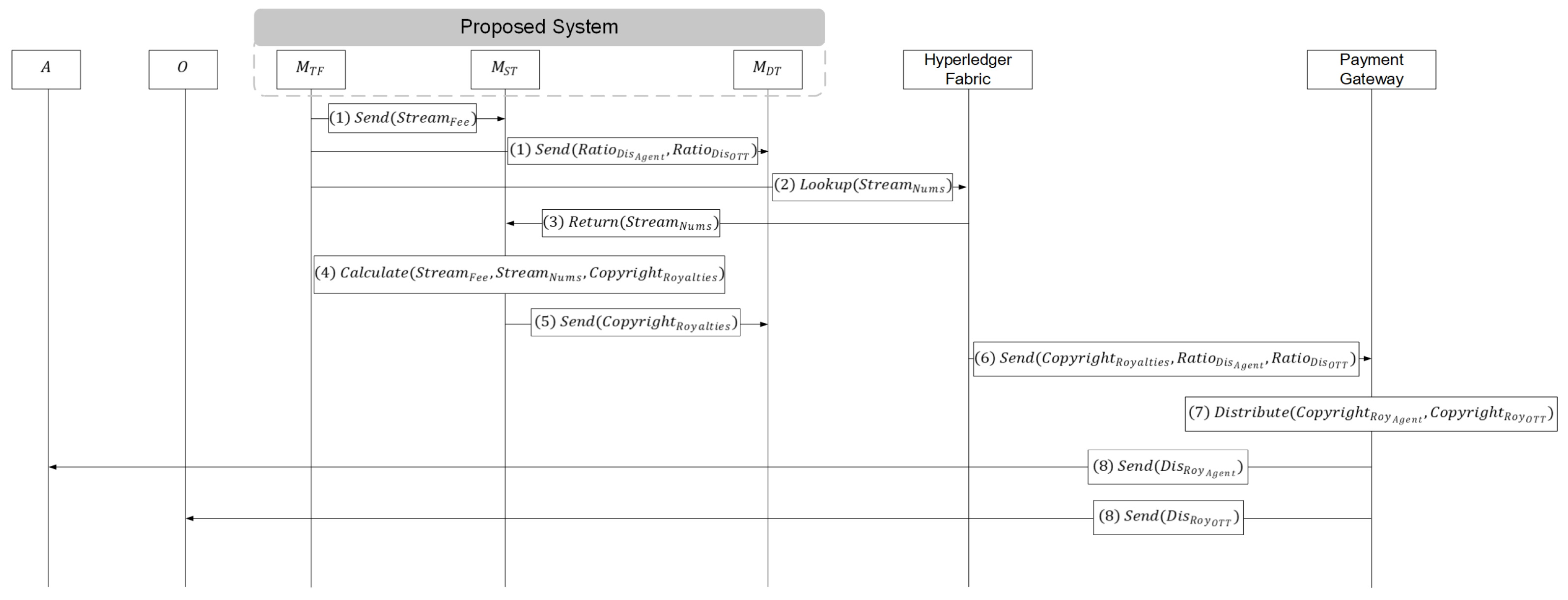
4.3. Settlement/Distribution Phase
- (1)
- In the ‘Register’ phase as described earlier, , after receiving from in Step (28), extracts and sends it to . Additionally, it sends and to .
- (2)
- queries Hyperledger Fabric for .
- (3)
- Hyperledger Fabric returns to .
- (4)
- calculates by multiplying the , received from in Step (1), with the obtained from Hyperledger Fabric in Step (3).
- (5)
- then sends the calculated to .
- (6)
- sends the , received from in Step (5), along with and , received from in Step (1), to the Payment Gateway.
- (7)
- The Payment Gateway, based on the received and , allocates to A and to O.
- (8)
- Finally, the Payment Gateway sends the allocated amounts to A and to O, as distributed in Step (7).
5. Main Modules
5.1. Agreement Module
- Using a threshold key generation algorithm, a key pair (P, V) is produced. The set S={,,⋯,} represents a collection of ‘shared secret keys’, designed to split the secret key into n parts for distribution among multiple participants involved in the signing. The public key, P, is utilized for verifying the generated signature, and a verification key, V, is also created to validate the shared values of the signature.
- Each participant generates a signature share value, , using their individual shared secret key and the message m.
- The signature share value for each participant is verified through P and V.
- The single signature value is formed by combining a set of t verified signature share values {, , ⋯, }, in accordance with the previously established threshold t.
- Using the P, is then utilized to validate the signature corresponding to m.
5.2. ODRL Transfer Module
6. Analysis
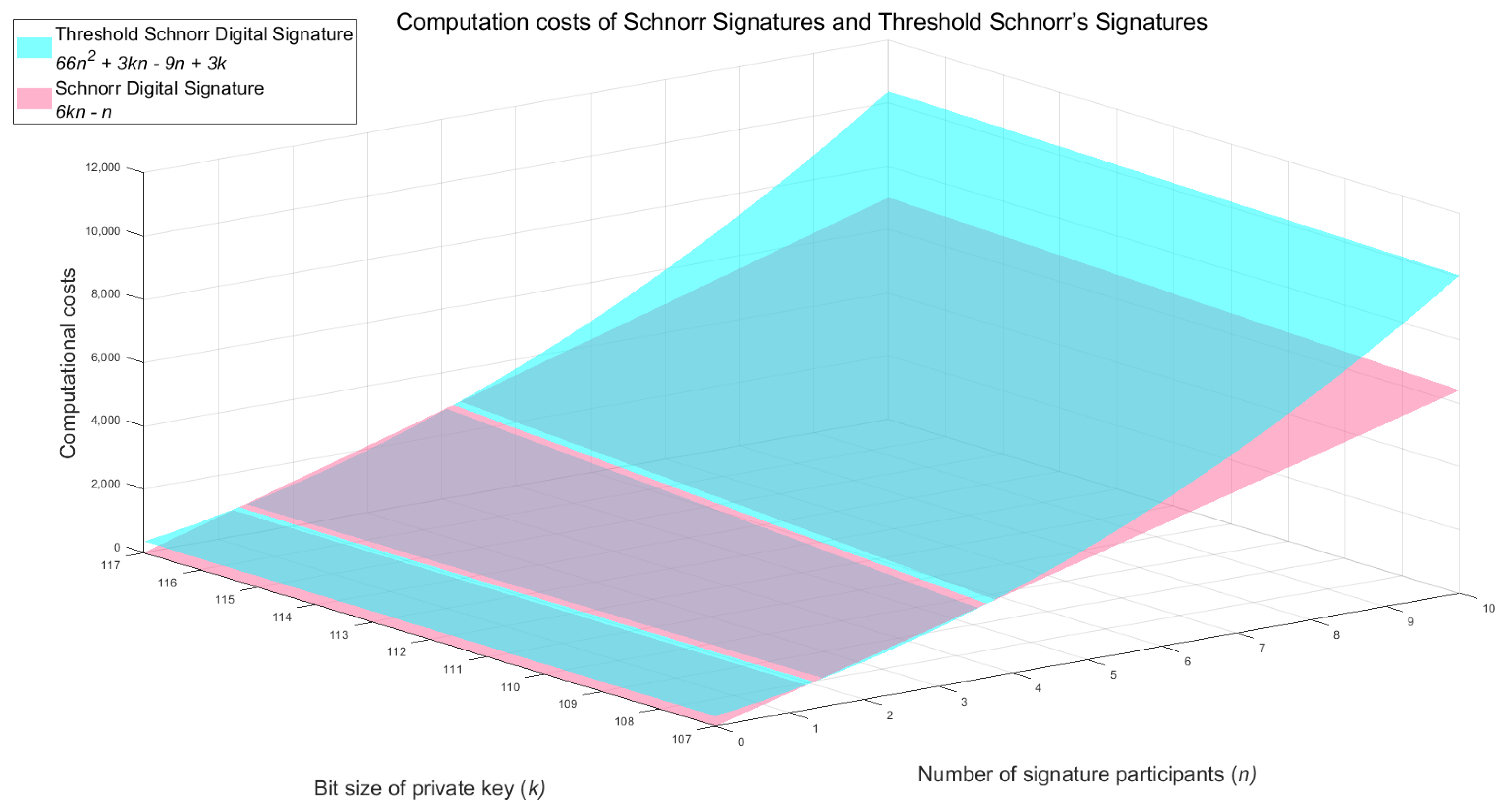
6.1. Performance Analysis
| Algorithm 1 Square-and-Multiply. |
Require: and
|
- (1)
- The Key Authentication Center (KAC) selects two random prime numbers, and , and identifies an element g with order q.
- (2)
- The user establishes a private key by choosing a random number s from .
- (3)
- The public key V is derived by calculating p.
- (4)
- For creating a signature for the message M, the signer selects a random number r from and computes p.
- (5)
- Using the one-way hash function , the value is calculated, followed by q, using the derived e value.
- (6)
- The derived signature values from Step (5) are transmitted to the verifier.
- (7)
- The verifier conducts signature verification by calculating p with the received signature values .
- (1)
- The signing participant selects a random number s from as their private key and derives the public key V by calculating p.
- (2)
- A trustworthy dealer chooses a secret polynomial q and distributes to each participant . Here, is a public value, while , calculated based on it, is a secret value.
- (3)
- Participant computes the secret value q. is the Lagrange coefficient q, leading to q.
- (4)
- The dealer selects a secret polynomial q, satisfying and , and then distributes to each participant . Here, r is a secret entrusted value meeting . is a public value, and the computed is a secret value sent to .
- (5)
- Signing participant calculates the secret value q, and the total trust value r is then computed as q.
- (6)
- The signature aggregator broadcasts the message M to be signed to all signing participants. Any participant in the signature process can assume the role of the signature aggregator.
- (7)
- Each signing participant computes their partial commitment value, p, and then broadcasts it.
- (8)
- Signatory participant selects t values from , calculates and q, and sends the resulting pair to the signature aggregator.
- (9)
- The signature aggregator compiles the final signature value by processing the t partial signatures with the same e value.
- (10)
- The verifier conducts signature verification using the received signature value , following the same method as the Schnorr Digital Signature, by calculating p.
6.2. Functional Analysis
7. Discussion
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kim, A.; Kim, M. A study on blockchain-based music distribution framework: Focusing on copyright protection. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Island, Republic of Korea, 21–23 October 2020; pp. 1921–1925. [Google Scholar]
- Lee, L. A Study on the Management Plan of Copyright Contracts Using Blockchain Technology: Blockchain-based Copyright Contracts Centered on Music Copyrights. Korea Serv. Manag. Soc. 2019, 23, 218–236. [Google Scholar]
- Kim, Y.; Park, B.; Kim, S.-Y. A selective encryption/decryption method of sensitive music usage history information on theme, background and signal music blockchain network. J. Web Eng. 2022, 21, 1265–1282. [Google Scholar] [CrossRef]
- Kim, Y.; Park, B.; Kim, S.-Y. A Usage History Information Generation and Inquiry Method for Theme, Background and Signal Music Based on Hyperledger Fabric. J. Mob. Multimed. 2022, 18, 1811–1828. [Google Scholar] [CrossRef]
- Top 15 Threats to Video Content Distribution Services. Available online: https://www.verimatrix.com/blog/top-15-threats-to-video-content-distribution-services (accessed on 20 December 2023).
- Hyperledger Fabric Structure. Available online: https://hcnam.tistory.com/19 (accessed on 20 December 2023).
- Cachin, C. Architecture of the hyperledger blockchain fabric. Workshop Distrib. Cryptocurrencies Consens. Ledgers 2016, 310, 4. [Google Scholar]
- A Blockchain Platform for the Enterprise Hyperledger Fabric. Available online: https://hyperledger-fabric.readthedocs.io/en/latest/index.html (accessed on 20 December 2023).
- Pelekoudas-Oikonomou, F.; Ribeiro, J.; Mantas, G.; Bashashi, F.; Sakellari, G.; Gonzalez, J. A tutorial on the implementation of a hyperledger fabric-based security architecture for IoMT. In Proceedings of the 2023 IFIP Networking Conference (IFIP Networking), Barcelona, Spain, 12–15 June 2023; pp. 1–6. [Google Scholar]
- Shammar, E.A.; Zahary, A.T.; AL-Shargabi, A.A. An attribute-based access control model for Internet of things using hyperledger fabric blockchain. Wirel. Commun. Mob. Comput. 2022, 2022, 6926408. [Google Scholar] [CrossRef]
- Pancari, S.; Rashid, A.; Zheng, J.; Patel, S.; Wang, Y.; Fu, J.A. Systematic Comparison between the Ethereum and Hyperledger Fabric Blockchain Platforms for Attribute-Based Access Control in Smart Home IoT Environments. Sensors 2023, 23, 7046. [Google Scholar] [PubMed]
- Al-Sumaidaee, G.; Alkhudary, R.; Zilic, Z.; Swidan, A. Performance analysis of a private blockchain network built on Hyperledger Fabric for healthcare. Inf. Process. Manag. 2023, 60, 103160. [Google Scholar] [CrossRef]
- Liang, X.; Zhao, Q.; Zhang, Y.; Liu, H.; Zhang, Q. EduChain: A highly available education consortium blockchain platform based on Hyperledger Fabric. Concurr. Comput. Pract. Exp. 2023, 35, e6330. [Google Scholar] [CrossRef]
- Kwon, S.; Park, J.; Lee, T.; Oh, S.; Lee, J.-H. Decentralized identifier based illegal digital content distribution tracking system using the format-preserving encryption algorithm. Softw. Pract. Exp. 2022. [Google Scholar] [CrossRef]
- Wang, S.; Yuan, Y.; Wang, X.; Li, J.; Qin, R.; Wang, F.Y. An overview of smart contract: Architecture, applications, and future trends. In Proceedings of the 2018 IEEE Intelligent Vehicles Symposium (IV), Changshu, China, 26–30 June 2018; pp. 108–113. [Google Scholar]
- Mohanta, B.K.; Panda, S.S.; Jena, D. An overview of smart contract and use cases in blockchain technology. In Proceedings of the 2018 9th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Bengaluru, India, 10–12 July 2018; pp. 1–4. [Google Scholar]
- Zou, W.; Lo, D.; Kochhar, P.S.; Le, X.B.D.; Xia, X.; Feng, Y.; Chen, Z.; Xu, B. Smart contract development: Challenges and opportunities. IEEE Trans. Softw. Eng. 2019, 47, 2084–2106. [Google Scholar] [CrossRef]
- Sharma, P.; Jindal, R.; Borah, M.D. A review of smart contract-based platforms, applications, and challenges. Clust. Comput. 2023, 26, 395–421. [Google Scholar] [CrossRef]
- Beckert, B.; Herda, M.; Kirsten, M.; Schiffl, J. Formal specification and verification of Hyperledger Fabric chaincode. In Proceedings of the 3rd Symposium on Distributed Ledger Technology (SDLT-2018) Co-Located with ICFEM, Gold Coast, Australia, 12 November 2018; pp. 44–48. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Foschini, L.; Gavagna, A.; Martuscelli, G.; Montanari, R. Hyperledger fabric blockchain: Chaincode performance analysis. In Proceedings of the ICC 2020 IEEE International Conference on Communications (ICC), Virtual, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Son, S. Analysis of transaction flow and smart contract procedures of Ethereum and Hyperledger Fabric. In Proceedings of the Korea Communications Society Conference, Yongpyeong, Republic of Korea, 23–25 January 2019; pp. 205–206. [Google Scholar]
- ODRL Information Model 2. Available online: https://www.w3.org/TR/odrl-model (accessed on 23 August 2023).
- Mobility Data Share. Available online: https://www.pentasecurity.co.kr/mobility-data-sharing (accessed on 20 December 2023).
- Dam, T.; Krimbacher, A.; Neumaier, S. Policy Patterns for Usage Control in Data Spaces. arXiv 2023, arXiv:23011289. [Google Scholar]
- Roshankish, S.; Fornara, N. Exploration of norms and policies in digital fashion domain using semantic web technologies. In International Conference on Human-Computer Interaction; Springer International Publishing: Cham, Switzerland, 2021; pp. 384–395. [Google Scholar]
- Choi, C.-J.; Joe, Y.J.; Shin, D.-M. Design of a Blockchian-based KRW Transfer System for Settlement and Distribution of Digital Content Copyright Fees. J. Softw. Assess. Valuat. JSAV 2023, 19, 21–30. [Google Scholar]
- Zheng, X.; Su, J.; Si, Y.; Wang, B. Research on Short Video Copyright Transaction and Protection Mechanism Based on Blockchain NFT. In Proceedings of the 2022 7th International Conference on Modern Management and Education Technology (MMET 2022), Xiamen, China, 23–25 September 2022; pp. 574–581. [Google Scholar]
- Varaprasada, R.K.; Panda, S.K. A design model of copyright protection system based on distributed ledger technology. In Computer Communication, Networking and IoT: Proceedings of 5th ICICC 2021; Springer Nature: Singapore, 2022; pp. 127–141. [Google Scholar]
- Li, J.; Grintsvayg, A.; Kauffman, J.; Fleming, C. LBRY: A blockchain-based decentralized digital content marketplace. In Proceedings of the 2020 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Oxford, UK, 3–6 August 2020; pp. 42–51. [Google Scholar]
- Kim, Y.; Park, B.; Jang, S.; Kim, S.Y. A Study on Copyright Usage Permission Platform Based on Blockchain for Distribution of Theme, Background and Signal Music. J. Semicond. Disp. Technol. 2021, 20, 18–24. [Google Scholar]
- Mukta, R.; Martens, J.; Paik, H.Y.; Lu, Q.; Kanhere, S.S. Blockchain-based verifiable credential sharing with selective disclosure. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; pp. 959–966. [Google Scholar]
- Maesa, D.D.F.; Lisi, A.; Mori, P.; Ricci, L.; Boschi, G. Self sovereign and blockchain based access control: Supporting attributes privacy with zero knowledge. J. Netw. Comput. Appl. 2023, 212, 103577. [Google Scholar] [CrossRef]
- Kim, J.; Kim, G.; Ryou, J. DID Authentication Method for Secure Multi-Party Signature in Blockchain. J. Korean Inst. Commun. Inf. Sci. 2023, 48, 1368. [Google Scholar]
- Negre, C.; Plantard, T. Efficient regular modular exponentiation using multiplicative half-size splitting. J. Cryptogr. Eng. 2017, 7, 245–253. [Google Scholar] [CrossRef]
- Morita, H.; Schuldt, J.C.; Matsuda, T.; Hanaoka, G.; Iwata, T. On the security of the schnorr signature scheme and DSA against related-key attacks. In Proceedings of the Information Security and Cryptology—ICISC 2015: 18th International Conference, Seoul, Republic of Korea, 25–27 November 2015; pp. 25–27. [Google Scholar]
- Nyang, D.; Kwon, T. Efficient Threshold Schnorr’s Signature Scheme. J. Korea Inst. Inf. Secur. Cryptol. JKIISC 2004, 7, 69–74. [Google Scholar]
- Joint Authorship Does Not Require Writing Contribution. Available online: https://www.pinsentmasons.com/out-law/news/joint-authorship-does-not-require-writing-contribution (accessed on 21 December 2023).
- Principles of Joint Authorship. Available online: https://www.dacbeachcroft.com/en/gb/articles/2021/march/principles-of-joint-authorship (accessed on 21 December 2023).
- Lee, G. The study on Recent Issues Concerning Joint Works. Chung-Ang Law Assoc. 2021, 23, 113–156. [Google Scholar]


| Component | Description |
|---|---|
| Channel | Components that establish and manage group permissions for transactions on a Blockchain network by group |
| Organization | Components that manage permissions to peer nodes by organization within a Blockchain network as well as access to network participants |
| Peer Node | Components that process transactions on a Blockchain network, manage and store ledger and chaincode (Maintain Blockchain network) |
| Ordering Service Node | Components that contain information about channels within the Blockchain network and act as administrators |
| Membership Service Provider (MSP) | Components that perform roles related to identity authentication in the Blockchain network to achieve access control and manage the roles and privileges of each component |
| Certificate Authority (CA) | Components that act as a certification authority in the Blockchain network, providing the information required for encryption authentication in MSP to achieve access control and manage the roles and privileges of each component. |
| Item | Smart Contract | Chaincode |
|---|---|---|
| Language | Solidity, Vyper | Go, JavaScript |
| IDE | Remix, Truffle | Chaincoder, Goland |
| Node Communication Interface | JSON-RPC | gRPC |
| Access Control | Not Supported | Supported |
| Deployment Policy | Deployed to all nodes within the Blockchain network | Deployed only to authorized nodes within the channel |
| Availability of Updates | Not Supported | Supported |
| Lifecycle | 1. Generation process 2. Deployment process 3. Calling process | 1. Generation and packaging process 2. Deployment process 3. Calling process |
| Class | Description |
|---|---|
| Policy | This Class forms the fundamental structure of ODRL and is composed of subclasses such as ‘Set’, ‘Offer’, and ‘Agreement’. It defines the ‘Action’ of the ‘Party’ concerning a specific ‘Asset’, thereby clearly articulating ‘Permission’, ‘Prohibition’, and ‘Duty’. |
| Asset | This Class represents the content and services that are the subjects of the rules, such as digital books, music, and streaming videos. The subclass ‘AssetCollection’, which groups together multiple assets, is particularly useful for uniformly applying the same rights expressions to numerous contents or services |
| Party | This Class represents entities that participate in and perform specific roles within the rules, which can include groups, individuals, or organizations. The ‘Party’ can be categorized into ‘Assigner’, who establishes and proposes policies, and ‘Assignee’, who accepts these policies. Additionally, it includes the subclass ‘PartyCollection’, which is used for grouping and representing multiple entities. |
| Action | This Class represents actions that the ‘Party’ can perform on an ‘Asset’, such as streaming and downloading. |
| Constraint | This Class represents conditions and restrictions applied to the subclasses of ‘Rule’, namely ‘Permission’, ‘Prohibition’, and ‘Duty’, thereby providing a more detailed explanation of the scope and application of authority. |
| Rule | This Class, through its subclasses ‘Permission’, ‘Prohibition’, and ‘Duty’, restricts the actions of ‘Party’ regarding the ‘Asset’. |
| Ref | Copyright Distribution Management Method | Privacy Protection Method | Royalty Settlement and Distribution Method | Smart Contract Signing Method | User Permission Check Method |
|---|---|---|---|---|---|
| [1] | O | X | X | X | X |
| [27] | O | X | O | X | X |
| [28] | O | X | O | X | X |
| [29] | O | X | X | X | X |
| [30] | O | Δ | X | X | X |
| [31] | O | X | O | X | X |
| [4] | O | X | O | X | X |
| [3] | O | O | X | X | X |
| Notation | Description |
|---|---|
| A | Agent with multiple copyright holders |
| O | OTT service |
| C | Consumer |
| Large number of consumers | |
| Trusted copyright institution | |
| Verify Module of OTT service | |
| Register Module of OTT service | |
| Agreement module | |
| ODRL update module | |
| OTT service ODRL policy module | |
| ODRL transfer module | |
| Settlement module | |
| ODRL generator module | |
| Service validation module | |
| Distribution module | |
| Copyright transaction related agreement | |
| Digital content | |
| Copyright transaction agreement terms and conditions | |
| Copyright registration certificate for digital content | |
| ODRL for agent | |
| ODRL for contract | |
| ODRL for consumer | |
| Information about digital content | |
| Information about OTT digital content | |
| Verified OTT digital content | |
| Information regarding payment | |
| Distribution ratio to agent | |
| Distribution ratio to OTT service | |
| Amount per stream | |
| Number of streams | |
| Amount paid by consumer | |
| Service access rights | |
| Copyright royalties | |
| Signed contracts | |
| Shared signatures | |
| Single signature created by aggregating shared signatures | |
| Message notifying that registration of digital content within the OTT service has been completed | |
| Consumer’s account information | |
| Payment rate plan | |
| Payment method | |
| Information on the amount paid by the consumer | |
| Hash value of digital content | |
| Number of plays for digital content | |
| Copyright royalties to be distributed to agent | |
| Copyright royalties to be distributed to OTT service | |
| Copyright royalties distributed to agent | |
| Copyright royalties distributed to OTT service | |
| Function of sending | |
| Function of extracting y from x | |
| Update function with the addition of y to x | |
| Function for aggregating x to generate y | |
| Function of verifying x by comparing it with y | |
| Function of dividing x into y | |
| Function to generate z based on x and y | |
| Function of registering x and y | |
| Function of storing x and y | |
| Function to search y based on x | |
| Function that returns x | |
| Function of checking z based on x and y | |
| Function that increases x based on y | |
| Function of calculating z based on the operations of x and y | |
| Function of distributing x and y |
| Extracted Information | Description |
|---|---|
| Refers to the amount charged per playback of , which varies for each piece of digital . | |
| Represents the distribution ratio of among copyright holders, established for transparent settlement and distribution, considering multiple joint copyright holders. | |
| Describes the information about the ratio basis for settlements between A and O, derived from the earned by providing O to multiple . | |
| Indicates the of of O regarding what actions they can perform with accessed through the service. These may include streaming and storing . |
| Step | Schnorr Digital Signature Computation Volume |
|---|---|
| Process (1) | - |
| Process (2) | - |
| Process (3) | |
| Process (4) | |
| Process (5) | 1 |
| Process (6) | - |
| Process (7) |
| Step | Threshold Schnorr Digital Signature Computation Volume |
|---|---|
| Process (1) | |
| Process (2) | |
| Process (3) | |
| Process (4) | |
| Process (5) | |
| Process (6) | - |
| Process (7) | |
| Process (8) | n |
| Process (9) | 0 |
| Process (10) |
| Schnorr Digital Signature | Threshold Schnorr Digital Signature Used in the Proposed System | |
|---|---|---|
| Signature Generation | ||
| Signature Verification |
| Ref | Copyright Distribution Management Function | Smart Contract Signing Function | Royalty Settlement and Distribution Function | Privacy Protection Function | User Permission Check Function |
|---|---|---|---|---|---|
| [1] | O | X | X | X | X |
| [27] | O | X | O | X | X |
| [28] | O | X | O | X | X |
| [29] | O | X | X | X | X |
| [30] | O | X | X | Δ | X |
| [31] | O | X | O | X | X |
| [4] | O | X | O | X | X |
| [3] | O | X | X | X | X |
| Proposed System | O | O | O | O | O |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Son, W.; Kwon, S.; Oh, S.; Lee, J.-H. Automated Over-the-Top Service Copyright Distribution Management System Using the Open Digital Rights Language. Electronics 2024, 13, 336. https://doi.org/10.3390/electronics13020336
Son W, Kwon S, Oh S, Lee J-H. Automated Over-the-Top Service Copyright Distribution Management System Using the Open Digital Rights Language. Electronics. 2024; 13(2):336. https://doi.org/10.3390/electronics13020336
Chicago/Turabian StyleSon, Wooyoung, Soonhong Kwon, Sungheun Oh, and Jong-Hyouk Lee. 2024. "Automated Over-the-Top Service Copyright Distribution Management System Using the Open Digital Rights Language" Electronics 13, no. 2: 336. https://doi.org/10.3390/electronics13020336
APA StyleSon, W., Kwon, S., Oh, S., & Lee, J.-H. (2024). Automated Over-the-Top Service Copyright Distribution Management System Using the Open Digital Rights Language. Electronics, 13(2), 336. https://doi.org/10.3390/electronics13020336












