Multi-Flow Complex Event Optimization in the Edge: A Smart Street Scenario
Abstract
1. Introduction
- In the real-world, multiple independent CEP flows can co-exist together; focusing on optimizing one of them can harm the performance of other, therefore optimizing them together can prevent the performance degradation of specific paths.
- Different optimization goals exists in the literature, and this study aims to improve the performance of the worse performing path, so that at any time, the worse case delay is reduced as much as possible.
- Enforcing data to be stored at the task location can harm different CEP paths that utilize the same data, and can cause specific devices to be overloaded in terms of bandwidth utilization rate. Therefore, a flexible and shared data placement mechanism is required to adapt dynamic load changes during CEP operations.
- Introducing a multi-consumer, multi-flow-oriented complex event flow optimization that can optimize the critical path across independent complex event flows to reduce delays while leveraging the underlying shared database infrastructure. A two-step optimization model is proposed, which minimizes the expected maximum bandwidth usage and further minimizes the delay with consideration of the CEP path relationship.
- The developed approach is experimented on a bandwidth-constrained smart street scenario that aims to distribute multiple flow tasks across distributed small-scale IoT devices. Furthermore, different cost considerations for existing heuristics are experimented on to observe their performances as well. Delay, data loss ratios, expected device loads, and delivery ratios are reported for different quality time windows.
- Providing the proposed solutions as well as the heuristic implementations within an open source library [8] that automates the distribution and execution of CEP codes and related data across small-scale IoT environments.
2. Literature Review and Background
2.1. CEP in Smart Environments and Edge Computing
2.2. Data Management in IoT
2.3. Other Related Studies
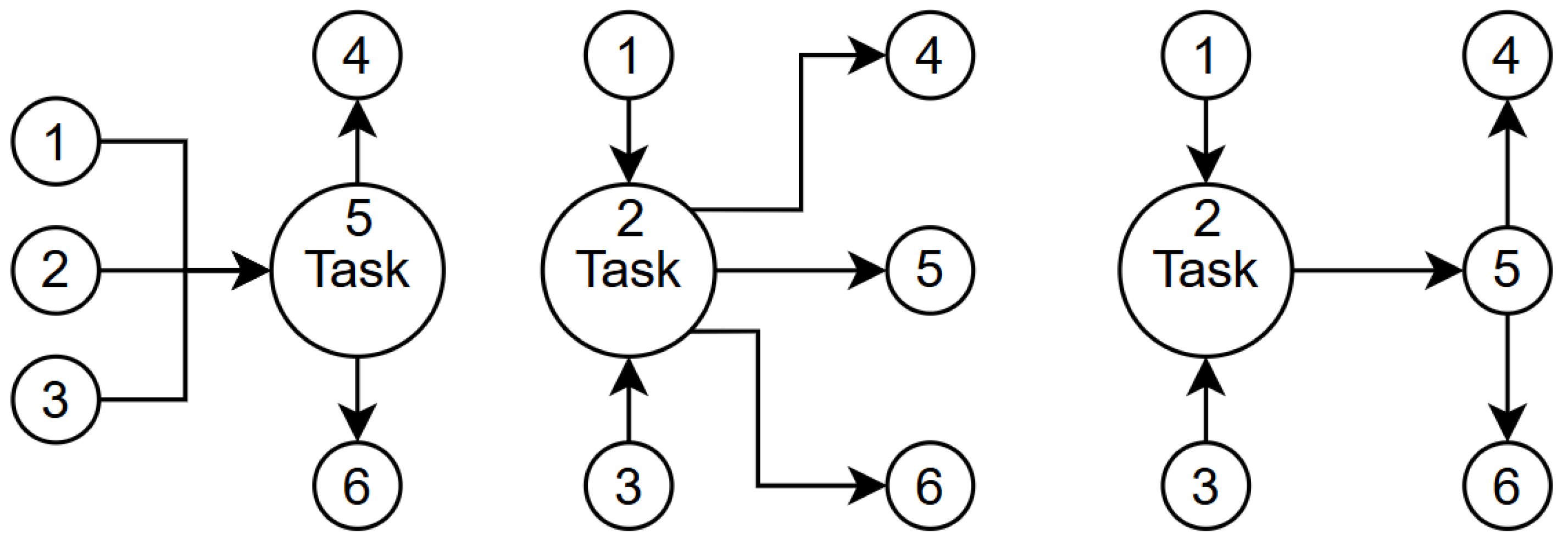
3. Problem Formulation
3.1. Optimization Goal and Critical Path Problem
3.2. Mathematical Formulation
3.3. Complexity of the Optimization
4. Methodology
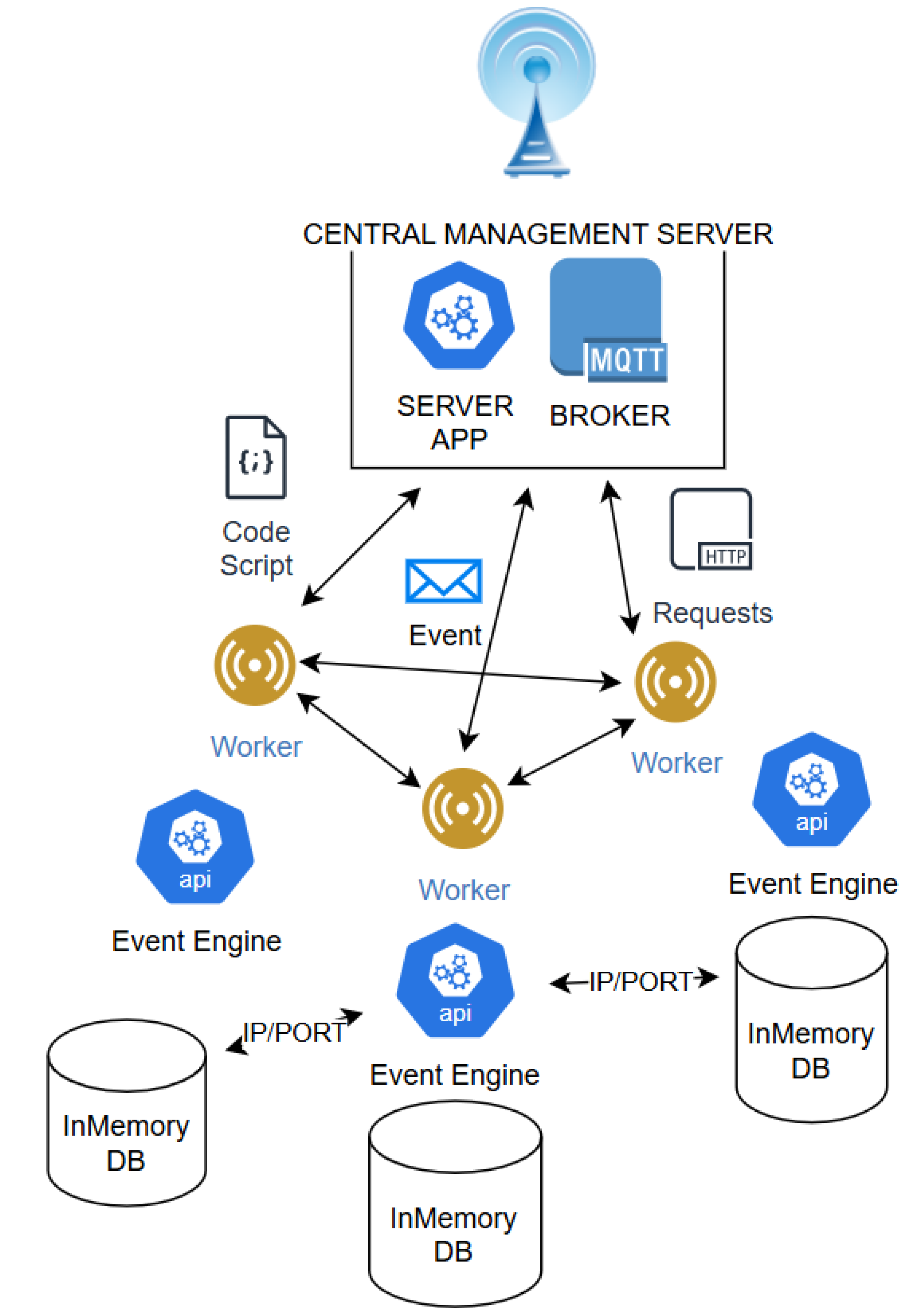
4.1. CEP IoT Infrastructure
4.1.1. CEP Code and Data Management Library
4.1.2. Distributed Shared Database Management
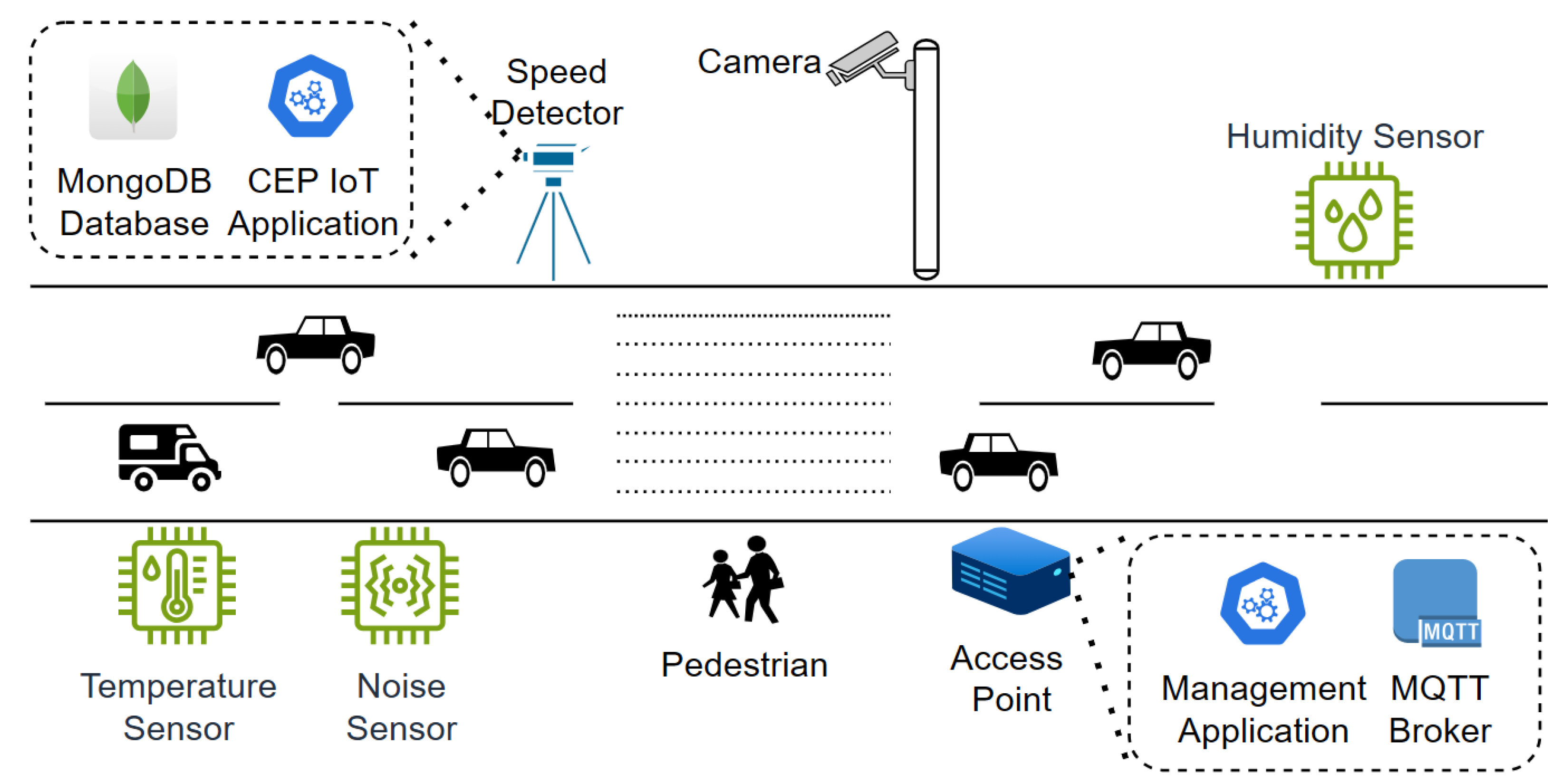
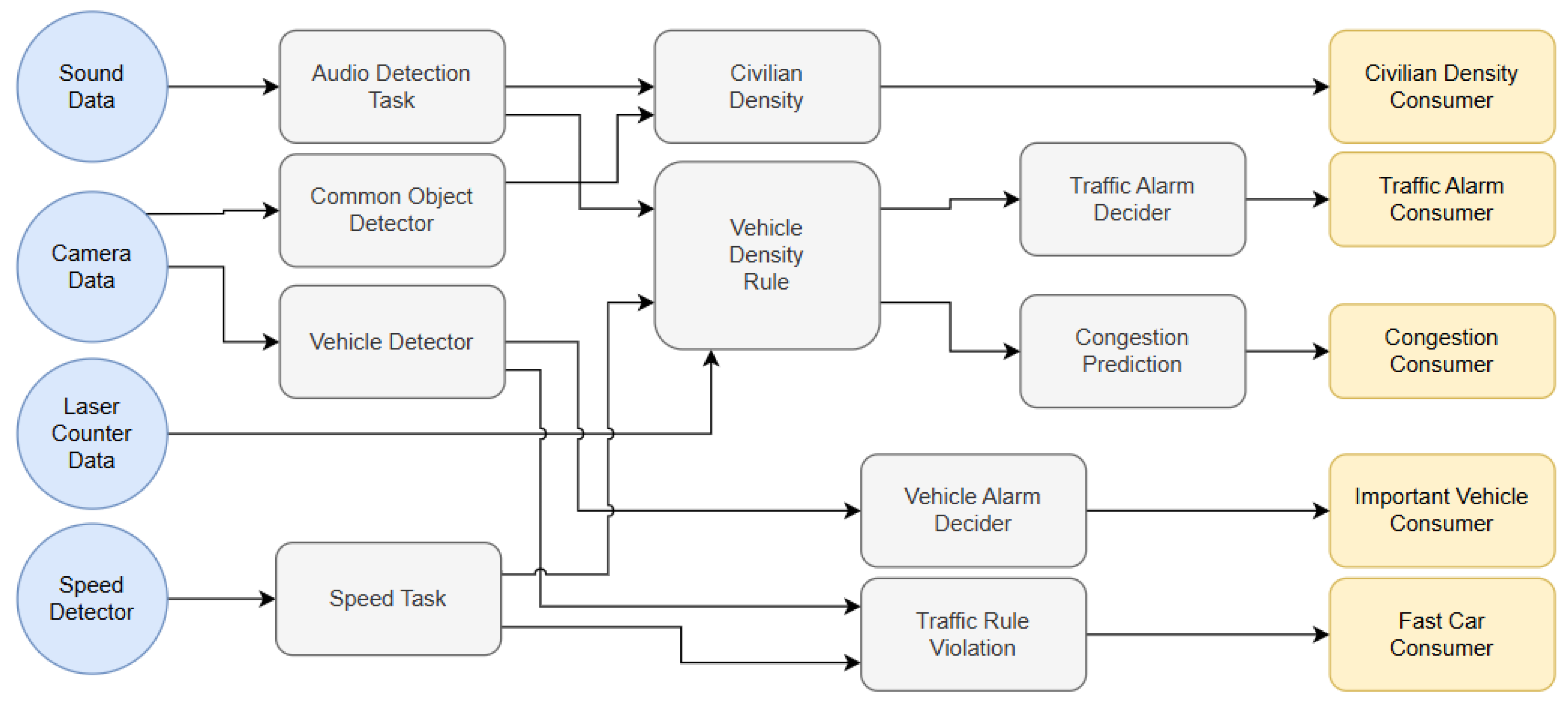
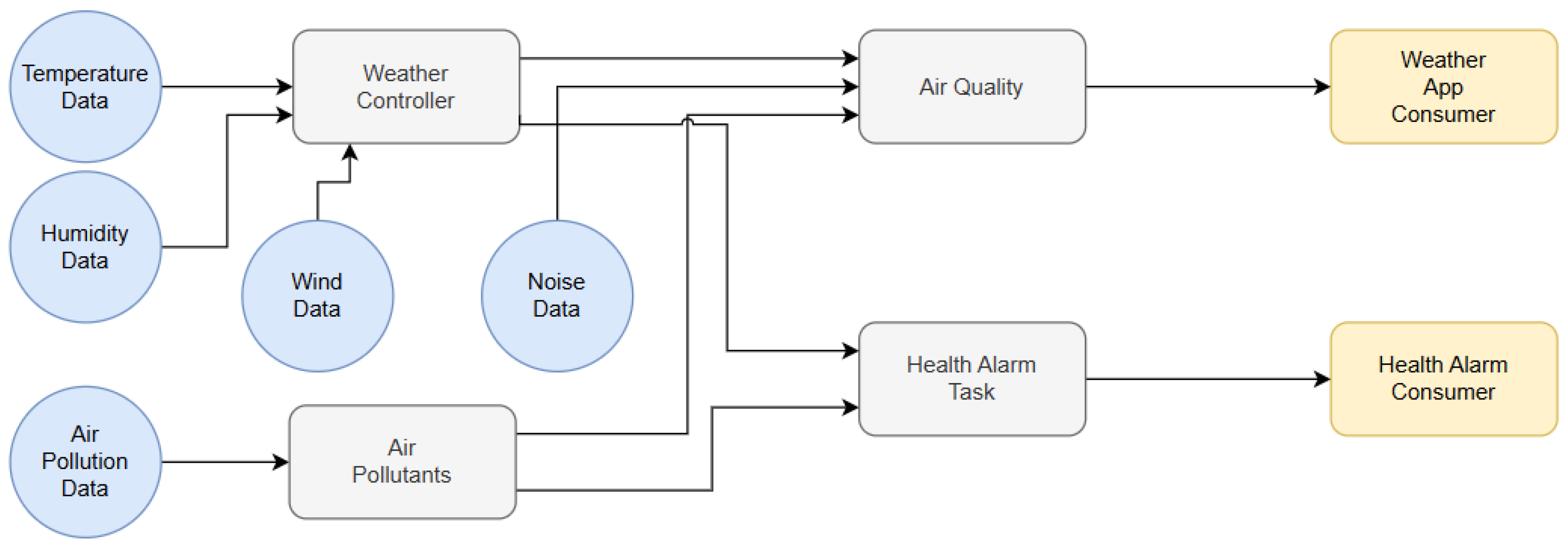
4.2. Smart Street Scenario
4.3. Optimization
| Algorithm 1: Code and data placement using any optimization method |
Data: CEP and worker settings. Result: Code and data I/O assignments. Collect execution statistics; Create DAG via pub/sub topics of CEP; Run the requested optimization using any optimization method; Optimization returns the assignments; return |
4.4. Heuristic Approaches
4.4.1. Producer-Oriented
4.4.2. Consumer-Oriented
4.4.3. Genetic Algorithm
| Algorithm 2: Code and data placement using genetic algorithm approach |
 |
4.4.4. Relaxation
| Algorithm 3: Code and data placement using relaxation approach |
 |
4.4.5. Constrained Programming
| Algorithm 4: Code and data I/O assignment management using constrained programming |
 |
5. Evaluation
5.1. Scalability
5.2. Limitations
5.3. Threats to Validity
6. Conclusions
- The mathematical model connected independent CEP flows together in order to prevent ignoring specific paths.
- Across all paths, the worst-performing path is optimized, which the proposed model performed better than the approaches in the literature.
- Flexible data placement mechanisms allowed devices to store/fetch data remotely when required, which helped the proposed model to have reduced worker load compared to non-shared approaches.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| CEP | Complex Event Processing |
| RSU | Roadside Unit |
| MQTT | Message Queuing Telemetry Transport |
| VSM | Virtual Shared Memory |
| DAG | Directed Acyclic Graph |
| RPi | Raspberry Pi |
References
- Kumar, R.; Kori, N.; Chaurasiya, V.K. Real-time data sharing, path planning and route optimization in urban traffic management. Multimed. Tools Appl. 2023, 82, 36343–36361. [Google Scholar] [CrossRef]
- Choochotkaew, S.; Yamaguchi, H.; Higashino, T.; Shibuya, M.; Hasegawa, T. EdgeCEP: Fully-Distributed Complex Event Processing on IoT Edges. In Proceedings of the 2017 13th International Conference on Distributed Computing in Sensor Systems (DCOSS), Ottawa, ON, Canada, 5–7 June 2017; pp. 121–129. [Google Scholar] [CrossRef]
- Lan, L.; Shi, R.; Wang, B.; Zhang, L.; Jiang, N. A Universal Complex Event Processing Mechanism Based on Edge Computing for Internet of Things Real-Time Monitoring. IEEE Access 2019, 7, 101865–101878. [Google Scholar] [CrossRef]
- Foundation, P.S. Python.org: The Official Website of the Python Programming Language. 2025. Available online: https://www.python.org/ (accessed on 12 November 2025).
- MongoDB, Inc. MongoDB.com: The World’s Leading Modern Database. 2025. Available online: https://www.mongodb.com/ (accessed on 12 November 2025).
- Yan, Y.; Zhang, Y.; Deng, G.; Sun, Y.; Qiu, T. Efficient Complex Event Processing Over Concurrent Event Streams. In Proceedings of the 2024 Sixth International Conference on Next Generation Data-driven Networks (NGDN), Shenyang, China, 26–28 April 2024; pp. 140–143. [Google Scholar] [CrossRef]
- RPT Ltd. Raspberry Pi 4 Model B: Your Tiny, Dual-Display, Desktop Computer. 2025. Available online: https://www.raspberrypi.com/products/raspberry-pi-4-model-b/ (accessed on 12 November 2025).
- Uyanık, H. Mullti_FLOW_CEP: CEP Automation Library. GitHub Repository. 2025. Available online: https://github.com/HalitU/mullti_flow_cep (accessed on 25 July 2025).
- Yar, H.; Imran, A.S.; Khan, Z.A.; Sajjad, M.; Kastrati, Z. Towards Smart Home Automation Using IoT-Enabled Edge-Computing Paradigm. Sensors 2021, 21, 4932. [Google Scholar] [CrossRef]
- Nasir, M.; Muhammad, K.; Ullah, A.; Ahmad, J.; Wook Baik, S.; Sajjad, M. Enabling automation and edge intelligence over resource constraint IoT devices for smart home. Neurocomputing 2022, 491, 494–506. [Google Scholar] [CrossRef]
- Martins, I.; Resende, J.S.; Sousa, P.R.; Silva, S.; Antunes, L.; Gama, J. Host-based IDS: A review and open issues of an anomaly detection system in IoT. Future Gener. Comput. Syst. 2022, 133, 95–113. [Google Scholar] [CrossRef]
- Lotfian Delouee, M.; Koldehofe, B.; Degeler, V. AQuA-CEP: Adaptive Quality-Aware Complex Event Processing in the Internet of Things. In Proceedings of the 17th ACM International Conference on Distributed and Event-Based Systems, New York, NY, USA, 27–30 June 2023; DEBS’23. pp. 13–24. [Google Scholar] [CrossRef]
- Keertikumar, M.; Shubham, M.; Banakar, R.M. Evolution of IoT in smart vehicles: An overview. In Proceedings of the 2015 International Conference on Green Computing and Internet of Things (ICGCIoT), Greater Noida, India, 8–10 October 2015; pp. 804–809. [Google Scholar] [CrossRef]
- Choochotkaew, S.; Yamaguchi, H.; Higashino, T. A Self-Organized Task Distribution Framework for Module-Based Event Stream Processing. IEEE Access 2019, 7, 6493–6509. [Google Scholar] [CrossRef]
- Cai, X.; Kuang, H.; Hu, H.; Song, W.; Lü, J. Response Time Aware Operator Placement for Complex Event Processing in Edge Computing. In Service-Oriented Computing; Pahl, C., Vukovic, M., Yin, J., Yu, Q., Eds.; Springer: Cham, Switzerland, 2018; pp. 264–278. [Google Scholar] [CrossRef]
- Luthra, M.; Koldehofe, B.; Höchst, J.; Lampe, P.; Rizvi, A.H.; Kundel, R.; Freisleben, B. INetCEP: In-Network Complex Event Processing for Information-Centric Networking. In Proceedings of the 2019 ACM/IEEE Symposium on Architectures for Networking and Communications Systems (ANCS), Cambridge, UK, 24–25 September 2019; pp. 1–13. [Google Scholar] [CrossRef]
- Wei, B.; Lin, D.; Ding, S. A Constraint-based Approach to Edge Resource Allocation for Complex Event Processing. In Proceedings of the 2020 IEEE/WIC/ACM International Joint Conference on Web Intelligence and Intelligent Agent Technology (WI-IAT), Melbourne, Australia, 14–17 December 2020; pp. 526–531. [Google Scholar] [CrossRef]
- Li, B.; Dong, W.; Guan, G.; Zhang, J.; Gu, T.; Bu, J.; Gao, Y. Queec: QoE-aware Edge Computing for IoT Devices under Dynamic Workloads. ACM Trans. Sens. Netw. 2021, 17, 27. [Google Scholar] [CrossRef]
- Luthra, M.; Koldehofe, B.; Danger, N.; Weisenberger, P.; Salvaneschi, G.; Stavrakakis, I. TCEP: Transitions in operator placement to adapt to dynamic network environments. J. Comput. Syst. Sci. 2021, 122, 94–125. [Google Scholar] [CrossRef]
- Cao, J.; Huang, H.; Qian, S. CLOSED: A Cloud-Edge Dynamic Collaborative Strategy for Complex Event Detection. In Proceedings of the 2022 IEEE International Conference on Web Services (ICWS), Barcelona, Spain, 11–15 July 2022; pp. 73–78. [Google Scholar] [CrossRef]
- Fu, C.; Calinescu, G.; Wang, K.; Li, M.; Xue, C.J. Energy-Aware Real-Time Task Scheduling on Local/Shared Memory Systems. In Proceedings of the 2016 IEEE Real-Time Systems Symposium (RTSS), Porto, Portugal, 29 September–2 December 2016; pp. 269–278. [Google Scholar] [CrossRef]
- Karlsson, M.; Stenström, P. Effectiveness of Dynamic Prefetching in Multiple-Writer Distributed Virtual Shared-Memory Systems. J. Parallel Distrib. Comput. 1997, 43, 79–93. [Google Scholar] [CrossRef]
- Ahn, S.; Kim, J.; Lim, E.; Kang, S. Soft Memory Box: A Virtual Shared Memory Framework for Fast Deep Neural Network Training in Distributed High Performance Computing. IEEE Access 2018, 6, 26493–26504. [Google Scholar] [CrossRef]
- Li, M.; Hawrylak, P.; Hale, J. Concurrency Strategies for Attack Graph Generation. In Proceedings of the 2019 2nd International Conference on Data Intelligence and Security (ICDIS), South Padre Island, TX, USA, 28–30 June 2019; pp. 174–179. [Google Scholar] [CrossRef]
- Ben Salah, N.; Bellamine Ben Saoud, N. Adaptive data placement in the Fog infrastructure of IoT applications with dynamic changes. Simul. Model. Pract. Theory 2022, 119, 102557. [Google Scholar] [CrossRef]
- Mohamed, A.a.; Abualigah, L.; Alburaikan, A.; Khalifa, H.A.E.W. AOEHO: A New Hybrid Data Replication Method in Fog Computing for IoT Application. Sensors 2023, 23, 2189. [Google Scholar] [CrossRef]
- Sun, D.; Gao, S.; Liu, X.; You, X.; Buyya, R. Dynamic redirection of real-time data streams for elastic stream computing. Future Gener. Comput. Syst. 2020, 112, 193–208. [Google Scholar] [CrossRef]
- Slo, A.; Bhowmik, S.; Rothermel, K. State-Aware Load Shedding From Input Event Streams in Complex Event Processing. IEEE Trans. Big Data 2022, 8, 1340–1357. [Google Scholar] [CrossRef]
- Verma, P.; Tiwari, R.; Hong, W.C.; Upadhyay, S.; Yeh, Y.H. FETCH: A Deep Learning-Based Fog Computing and IoT Integrated Environment for Healthcare Monitoring and Diagnosis. IEEE Access 2022, 10, 12548–12563. [Google Scholar] [CrossRef]
- Zhang, M.; Yang, Z.; Yan, J.; Ali, S.; Ding, W.; Wang, G. Task-load aware and predictive-based workflow scheduling in cloud-edge collaborative environment. J. Reliab. Intell. Environ. 2022, 8, 35–47. [Google Scholar] [CrossRef]
- Huang, B.; Liu, X.; Xiang, Y.; Yu, D.; Deng, S.; Wang, S. Reinforcement learning for cost-effective IoT service caching at the edge. J. Parallel Distrib. Comput. 2022, 168, 120–136. [Google Scholar] [CrossRef]
- Sun, Z.; Guan, X.; Wang, J.; Liu, F.; Cui, H. New Problems in Distributed Inference for DNN Models on Robotic IoT. In Proceedings of the 2024 Workshop on Advanced Tools, Programming Languages, and PLatforms for Implementing and Evaluating Algorithms for Distributed Systems, New York, NY, USA, 17 June 2024; ApPLIED’24. pp. 1–9. [Google Scholar] [CrossRef]
- Dehury, C.K.; Jakovits, P.; Srirama, S.N.; Giotis, G.; Garg, G. TOSCAdata: Modeling data pipeline applications in TOSCA. J. Syst. Softw. 2022, 186, 111164. [Google Scholar] [CrossRef]
- Cecilia, J.M.; Morales-García, J.; Imbernón, B.; Prades, J.; Cano, J.C.; Silla, F. Using remote GPU virtualization techniques to enhance edge computing devices. Future Gener. Comput. Syst. 2023, 142, 14–24. [Google Scholar] [CrossRef]
- De Lucia, G.; Lapegna, M.; Romano, D. Unlocking the potential of edge computing for hyperspectral image classification: An efficient low-energy strategy. Future Gener. Comput. Syst. 2023, 147, 207–218. [Google Scholar] [CrossRef]
- Yadav, P.; Salwala, D.; Curry, E. VID-WIN: Fast Video Event Matching With Query-Aware Windowing at the Edge for the Internet of Multimedia Things. IEEE Internet Things J. 2021, 8, 10367–10389. [Google Scholar] [CrossRef]
- Meslin, A.; Rodriguez, N.; Endler, M. Scalable Mobile Sensing for Smart Cities: The MUSANet Experience. IEEE Internet Things J. 2020, 7, 5202–5209. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Puliafito, C.; Mingozzi, E.; Longo, F.; Puliafito, A.; Rana, O. Fog Computing for the Internet of Things: A Survey. ACM Trans. Internet Technol. 2019, 19, 18. [Google Scholar] [CrossRef]
- Perron, L.; Didier, F. CP-SAT v9.12. 2024. Google. Available online: https://developers.google.com/optimization/cp/cp_solver/ (accessed on 12 November 2025).
- Ghosh, R.; Simmhan, Y. Distributed Scheduling of Event Analytics across Edge and Cloud. ACM Trans. Cyber-Phys. Syst. 2018, 2, 24. [Google Scholar] [CrossRef]
- Chen, S.; Tang, B.; Yang, Q.; Liu, Y. Operator Placement for IoT Data Streaming Applications in Edge Computing Environment. In Algorithms and Architectures for Parallel Processing; Meng, W., Lu, R., Min, G., Vaidya, J., Eds.; Springer: Cham, Switzerland, 2023; pp. 605–619. [Google Scholar] [CrossRef]
- Pietzuch, P.; Ledlie, J.; Shneidman, J.; Roussopoulos, M.; Welsh, M.; Seltzer, M. Network-Aware Operator Placement for Stream-Processing Systems. In Proceedings of the 22nd International Conference on Data Engineering (ICDE’06), Atlanta, GA, USA, 3–7 April 2006; p. 49. [Google Scholar] [CrossRef]
- Luthra, M.; Koldehofe, B.; Weisenburger, P.; Salvaneschi, G.; Arif, R. TCEP: Adapting to Dynamic User Environments by Enabling Transitions between Operator Placement Mechanisms. In Proceedings of the 12th ACM International Conference on Distributed and Event-Based Systems, New York, NY, USA, 25–29 June 2018; DEBS’18. pp. 136–147. [Google Scholar] [CrossRef]
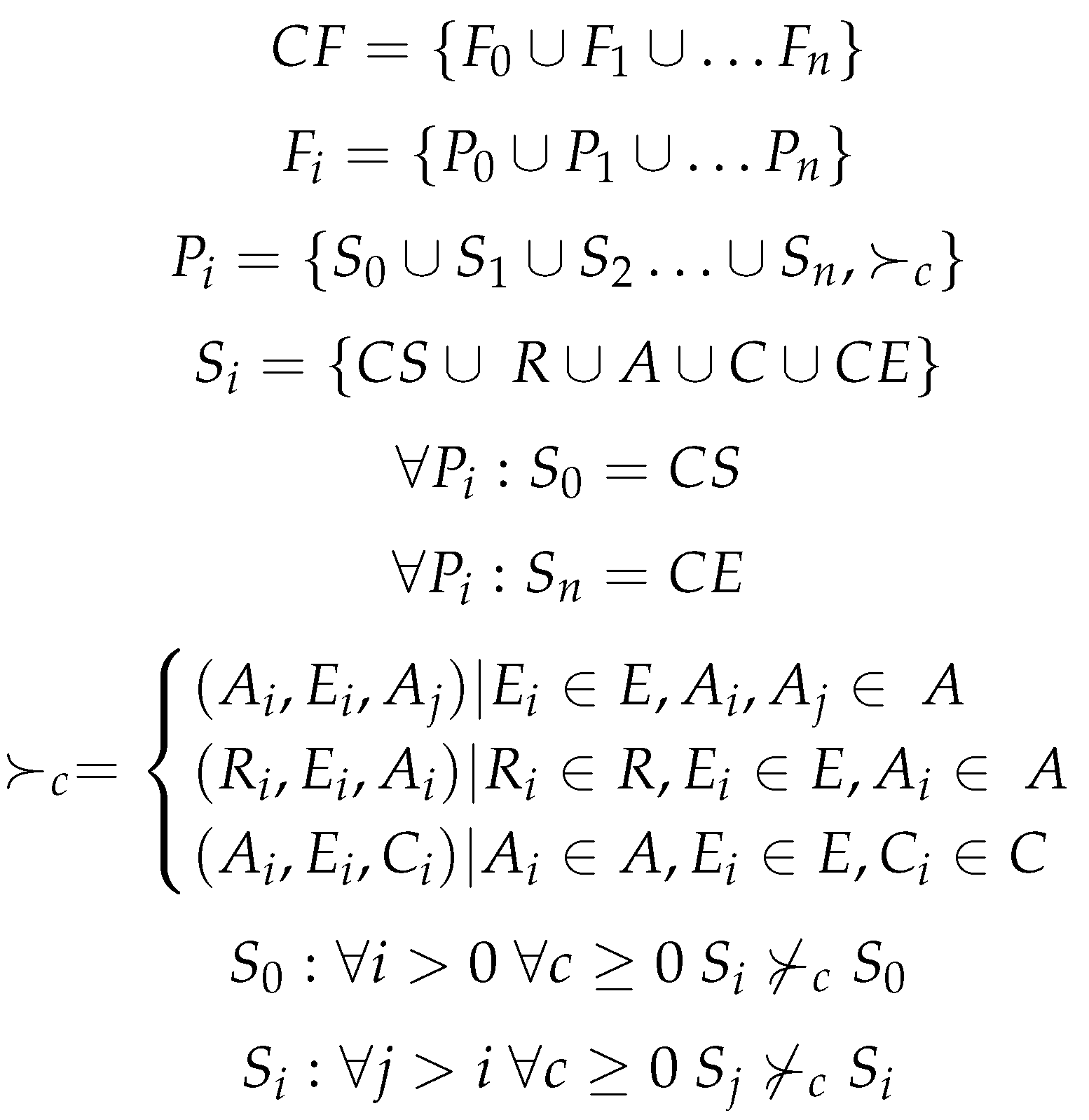
| Study | Year | Shared Memory | Critical-Path Optimization | Edge-Only Support | Library Provided | Custom Code Execution |
|---|---|---|---|---|---|---|
| [14] | 2018 | Δ | ✓ | ✓ | ✓ | ✓ |
| [15] | 2018 | × | ✓ | ✓ | Δ | × |
| [16] | 2019 | Δ | Δ | Δ | ✓ | Δ |
| [17] | 2020 | × | ✓ | ✓ | Δ | × |
| [18] | 2021 | × | ✓ | ✓ | Δ | × |
| [19] | 2021 | × | ✓ | Δ | ✓ | Δ |
| [20] | 2022 | × | ✓ | Δ | Δ | × |
| [12] | 2023 | × | Δ | Δ | Δ | × |
| This Study | - | ✓ | ✓ | ✓ | ✓ | ✓ |
| Notation | Definition | Notation | Definition |
|---|---|---|---|
| Complex flow cluster | External input load (bytes) | ||
| Single flow | External output load (bytes) | ||
| Flow path | Worker Task load | ||
| Path steps | Task unit cost | ||
| Raw data source | Placement choice | ||
| Event trigger | n | Number of actions | |
| Action code | Oscillation penalty | ||
| Static consumer | Step delay (seconds) | ||
| Connection | Path delay (seconds) | ||
| Cluster starting point | Execution delay (seconds) | ||
| Cluster ending point | Previous placements | ||
| Worker node | Delay (seconds) | ||
| Code placement | Bandwidth (Bps) | ||
| Source data placement | BW utilization ratio | ||
| Action data placement | BW utilization penalty | ||
| Worker External I/O load (bytes) |
| Equation | Description |
|---|---|
| (1) | Each source data is stored at a single location. |
| (2) | Each action output is stored at a single location. |
| (3) | Each CEP step action is executed at a one device. |
| (4) | Sum of external I/O load cannot exceed devices BW capacity. |
| (5) | Each worker can support a limited number of task executions. |
| (6) | Maximum BW load across workers are minimized. |
| (7) | Data I/O is penalized if the source/target changes from prior location. |
| (8) | Critical path delay across all CEP paths are minimized. |
| Parameter | Value | Unit |
|---|---|---|
| Processor Availability | 1.0 | count |
| Production Frequency Per Sensor | 3 | Hz |
| Load Change Frequency | 90 | seconds |
| Per Task Data Sizes | 20–50 | KB |
| Simulation Duration | 600 | seconds |
| MQTT QoS Level | 1 | value |
| Bandwidth Limit | 512 | KB/s |
| Oscillation Penalties | 1.1 | value |
| Experiment Repetition | 10 | value |
| Relaxation Approach | Max Consumer Delay (s) | Max Worker Bandwidth Load (%) | 1 sec. Delivery Ratio (%) | Algorithm Runtime |
|---|---|---|---|---|
| SUM_DELAY | 1.39 | 78.62 | 64.28 | 1182.02 |
| SUM_DELAY_H | 4.09 | 78.96 | 31.58 | 7722.60 |
| MAX_DELAY_H | 6.26 | 98.65 | 35.06 | 7836.47 |
| SUM_BW_H | 6.82 | 78.51 | 21.92 | 7776.24 |
| SUM_BW | 7.06 | 78.46 | 14.78 | 1122.54 |
| MAX_BW_H | 19.37 | 97.90 | 5.64 | 7675.95 |
| MAX_DELAY | 21.46 | 94.50 | 16.24 | 1180.39 |
| MAX_BW | 56.12 | 86.05 | 17.83 | 1160.54 |
| Genetic Algorithm Approach | Max Consumer Delay (s) | Max Worker Bandwidth Load (%) | 1 sec. Delivery Ratio (%) | Algorithm Runtime |
|---|---|---|---|---|
| SUM_DELAY | 5.10 | 85.91 | 65.74 | 13,096.74 |
| SUM_DELAY_H | 18.04 | 79.14 | 28.76 | 15,802.74 |
| SUM_BW_H | 24.02 | 95.81 | 15.50 | 17,521.21 |
| SUM_BW | 37.79 | 80.88 | 11.72 | 12,540.10 |
| MAX_BW | 59.03 | 87.80 | 0.10 | 10,499.58 |
| MAX_DELAY | 66.82 | 79.24 | 0.06 | 12,943.26 |
| MAX_DELAY_H | 87.53 | 100.07 | 0.24 | 19,616.72 |
| MAX_BW_H | 89.81 | 97.04 | 0.04 | 16,761.02 |
| PATH | 90.98 | 79.12 | 0.03 | 14,889.43 |
| PATH_H | 116.44 | 100.79 | 0.02 | 20,912.23 |
| Constraint Programming Approach | Max Consumer Delay (s) | Max Worker BW Load (%) | 1 sec. Delivery Ratio (%) | Algorithm Runtime |
|---|---|---|---|---|
| CP_DDAG | 0.67 | 71.80 | 91.94 | 4205.20 |
| CP_DAG | 0.95 | 73.37 | 77.14 | 5423.58 |
| CP_MAX_LOAD | 1.79 | 78.99 | 62.54 | 3219.86 |
| Optimization Approach | Min Consumer Delay (s) | Max Consumer Delay (s) | Processing Ratio (%) | Max Worker BW Load (%) |
|---|---|---|---|---|
| CP_DDAG | 0.13 | 0.67 | 99.99 | 71.80 |
| RELAX SUM DELAY | 0.13 | 1.39 | 99.91 | 78.62 |
| GA SUM DELAY | 0.12 | 5.10 | 100.00 | 85.91 |
| CONS | 0.11 | 95.54 | 89.03 | 89.89 |
| PROD | 0.28 | 103.48 | 78.61 | 87.20 |
| Optimization Approach | Algorithm Runtime (s) | 1 sec. Delivery Ratio (%) | 4 sec. Delivery Ratio (%) | 10 sec.+ Delivery Ratio (%) |
| CP_DDAG | 4205.20 | 91.94 | 97.22 | 1.15 |
| RELAX SUM DELAY | 1182.02 | 64.28 | 91.00 | 0.56 |
| GA SUM DELAY | 13,096.74 | 65.74 | 73.17 | 19.00 |
| CONS | 84.98 | 0.00 | 0.36 | 94.67 |
| PROD | 130.33 | 0.00 | 0.22 | 97.50 |
| Optimization Method | Max Consumer Delay (s) | Max Worker BW Load (%) | 1 sec. Delivery Ratio (%) | 10 sec.+ Delivery Ratio |
|---|---|---|---|---|
| CP_DDAG | 1.07 | 72.86 | 56.67 | 1.44 |
| RLX_DELAY | 6.89 | 79.24 | 0.06 | 19.22 |
| GA_DELAY | 61.07 | 78.60 | 0.06 | 96.61 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Uyanık, H.; Ovatman, T. Multi-Flow Complex Event Optimization in the Edge: A Smart Street Scenario. IoT 2025, 6, 72. https://doi.org/10.3390/iot6040072
Uyanık H, Ovatman T. Multi-Flow Complex Event Optimization in the Edge: A Smart Street Scenario. IoT. 2025; 6(4):72. https://doi.org/10.3390/iot6040072
Chicago/Turabian StyleUyanık, Halit, and Tolga Ovatman. 2025. "Multi-Flow Complex Event Optimization in the Edge: A Smart Street Scenario" IoT 6, no. 4: 72. https://doi.org/10.3390/iot6040072
APA StyleUyanık, H., & Ovatman, T. (2025). Multi-Flow Complex Event Optimization in the Edge: A Smart Street Scenario. IoT, 6(4), 72. https://doi.org/10.3390/iot6040072







