Big Data and Energy Security: Impacts on Private Companies, National Economies and Societies
Abstract
:1. Introduction
- (1)
- The concept of an economic loss is familiar to private individuals, corporations as well as governments due to the commonality of economic principles.
- (2)
- The concept of an economic loss resonates within a society, as well as with public and private sector since it serves as a direct feedback loop which triggers immediate call for action.
- (3)
- Parsimony reflects the most basic rational behavior and requirement for public and private households to pursue sustainable finances.
- (4)
- Since economic practice manifests a common way to facilitate the exchange of needs in every country and society, economic integration of the values of countries or societies provide a solid level of coherence.
- (5)
- Our proposed concept of energy security mitigating economic loss for the public and private sector, as well as society, differentiates in a significant way from common approaches to break down energy security as a simple connectivity, accessibility, and affordability issue by considering the needs and fears of energy consumers and producers.
- (6)
- The depth reached by our concept to classify the impact of economic acting into the different branches of public and private sector helps to better understand motives and reactions of agents acting in a certain way, thus revealing the path to energy security.
- (7)
- The strive for economic well-being can be assumed for any rational agent involved in the pursuit for energy security, especially in a theoretical setting.
- (8)
- The field utility can be actually measured once energy security is pursued and conducted as it manifests in the economic well-being of countries and societies.
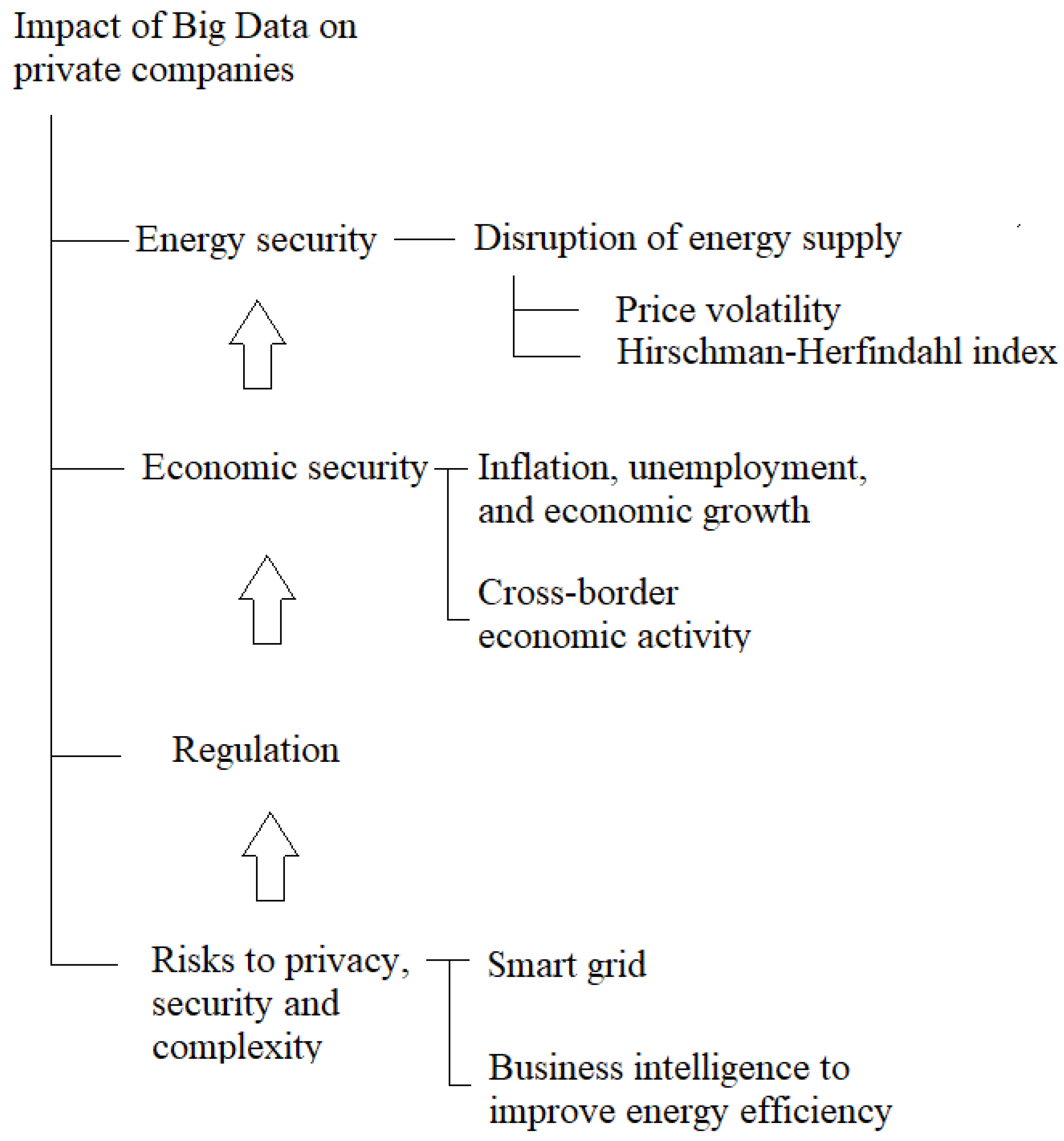
2. Big Data and Its Impact on Private Companies
2.1. Big Data for Energy Security
2.2. Big Data for Energy Usage Optimization
Impact of Big Data Regulation on National Energy Security
2.3. New Technologies for Big Data Generation and Utilization
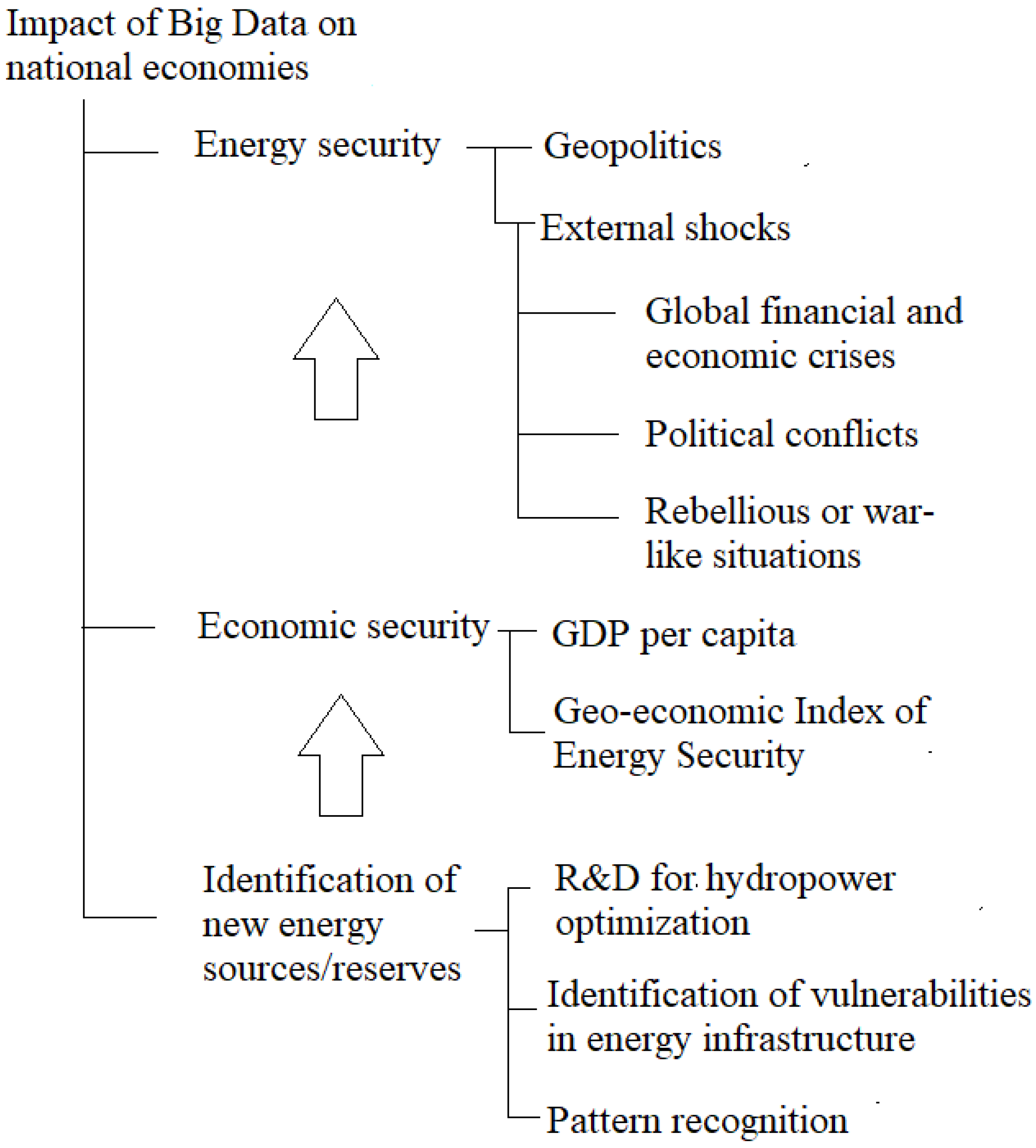
3. Big Data and Its Impact on National Economies
3.1. Big Data in Geopolitics
3.2. Big Data for Identification of Energy Security-Relevant Issues
Big Data to Enhance Economic Growth
3.3. New Technologies Generating and Using Big Data in Geopolitics
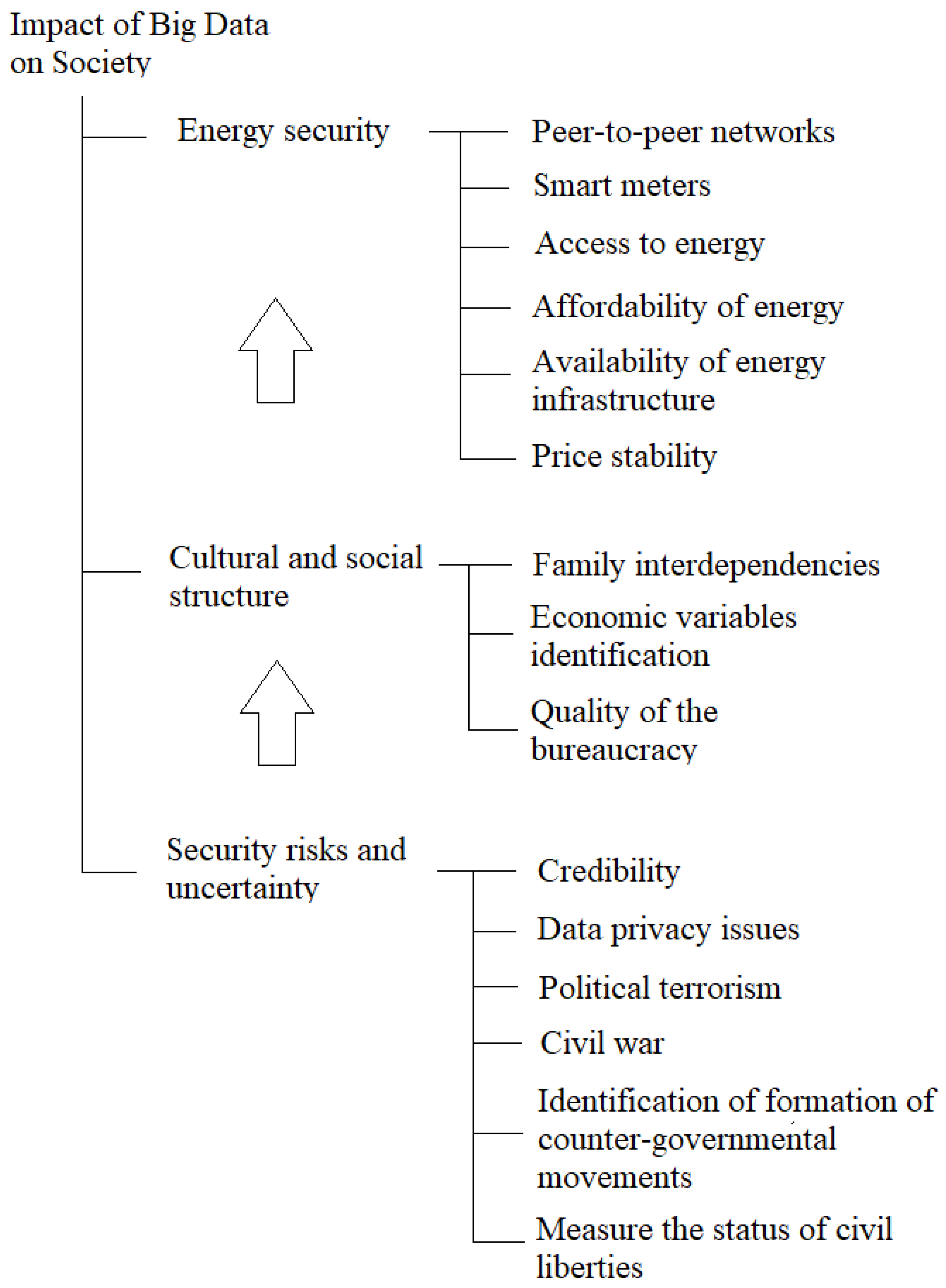
4. Impact on Society
4.1. Big Data, Energy Security and Cultural Changes
4.2. Big Data and Privacy Issues
4.3. New Technologies Affecting Society
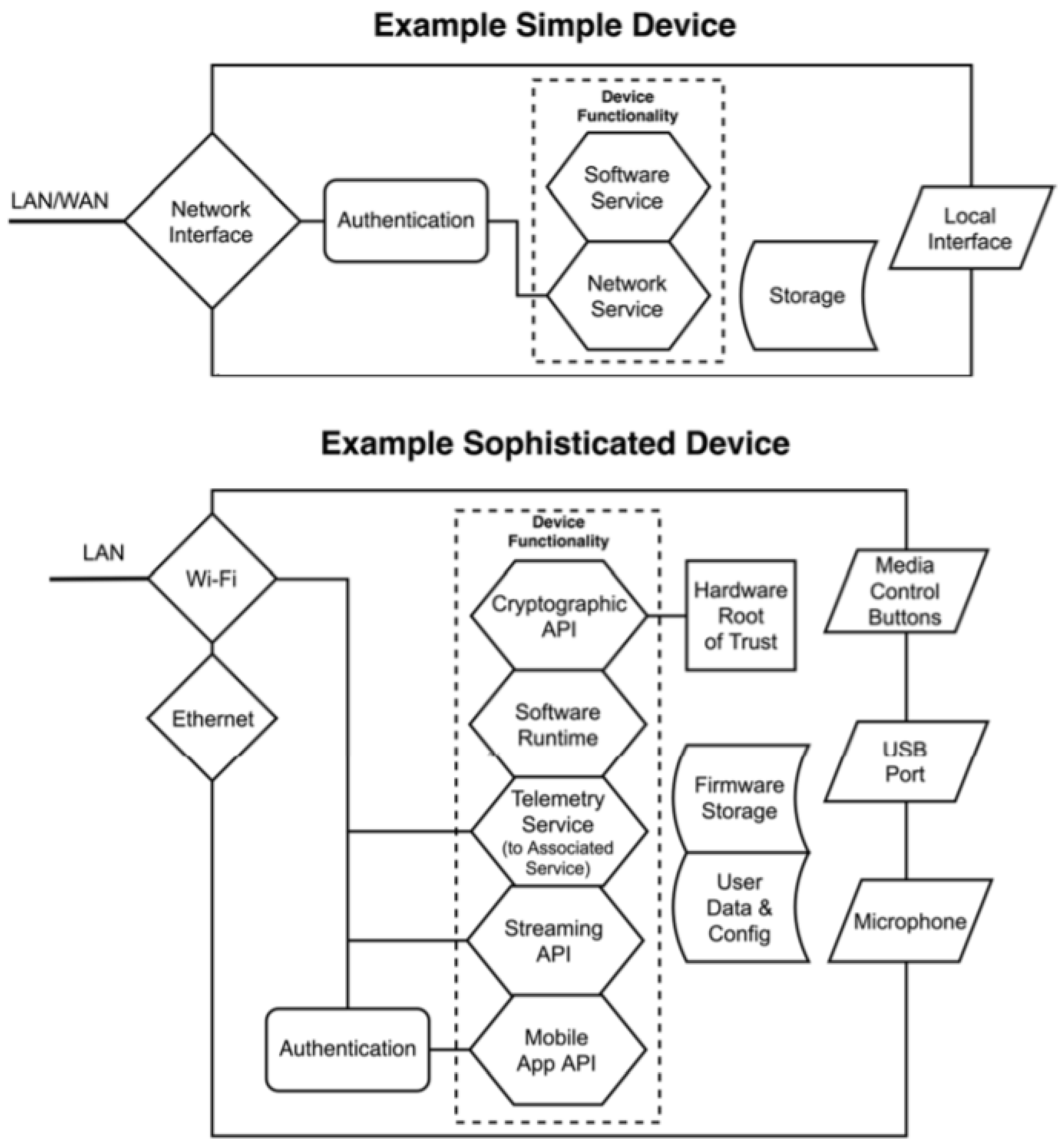
5. IoT Applications
5.1. IoT Architecture for Big Data Generation and Processing
5.2. IoT for Energy Security
5.3. IoT for Energy Issues
- Communication networks: Public, private, wired, and wireless communication networks that can be used as the communication infrastructure for smart grid [55].
- Cybersecurity: Determining measures to guarantee availability, integrity, and confidentiality of the communication and control systems which are required to manage, operate, and protect smart grid infrastructures [56].
- Distributed energy resources: Using different kinds of generation (e.g., renewable energies) and/or storage systems (batteries, plug-in electric cars with bi-directional chargers) that are connected to distributed systems [57].
- Distribution grid management: Trying to maximize the performance of components in distribution systems such as feeders and transformers and integrate them with transmission systems, increase reliability, increase the distribution system efficiency, and improve the management of distributed renewable energy sources [58].
- Electric transportation: Integrating plug-in electric vehicles in a large-scale [59].
- Energy efficiency: Providing mechanisms for different kinds of customers to modify their energy usage during peak hours and optimizing the balance between power supply and demand [60].
- Energy storage: Using direct or indirect energy storage technologies such as pumped hydroelectric storage technology [61].
- Wide-area monitoring: Monitoring of power system components over a large geographic area to optimize their performance and preventing problems before they happen [62].
5.4. IoT in Temperature Sensing
6. Use Case: Practical Issues and Challenges
6.1. Risks to Energy Supply
6.2. Use Case of Big Data Applications for Energy Security
6.3. Implications for Big Data Applications
6.4. Conclusions Drawn from Use Case
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Appendix A
| Impact on | Field | Author | Content |
|---|---|---|---|
| Private companies | Ambient energy harvesting | Yildiz [27] | Variety of techniques are available for energy scavenging. |
| SMART RFIDs | R. Kanan and D. Petrovic [28] | SMART RFIDs maintain and increase value across a supply chain. | |
| Energy security | Jun et al. [13] | Economic security dominates supply security and is therefore the main driver for total security cost. | |
| Energy security | Cable [14] | Understanding effects of inflation, unemployment, and economic growth, on energy security. | |
| Privacy and Security risks | Sriramoju [15] | Big Data mining such as risks to privacy, security and complexity. | |
| Big Data mining | Intel [16] | MapReduce can help in analyzing Big Data and bring about business intelligence. | |
| Big Data mining | Hackl et al. [17] | Analyze Sweden’s largest chemical cluster, its utility system and energy efficiency. | |
| Smart Grid | Jiang et al. [18] | Analyzing real-time energy consumption. | |
| Energy security | Zhou et al. [19] | How Big Data drives smart energy management. | |
| Energy security | Diamantoulakis et al. [22] | Scalability and flexibility can enable efficient processing of the large data volumes. | |
| Energy security | Zhou et al. [20], Vale et al. [21] | Most important factor for energy market price stability is predictive analytics. | |
| IoT and security | Sen et al. [45] | An important unmet need for security solutions is context awareness. | |
| Smart Grid | Bekara [48] | Analyzes security issues and challenges for the IoT-based Smart Grid. | |
| National Economies | Energy supply | Radovanovic et al. [29] | Measurement of energy security in a global economic and geopolitical sense. |
| Energy security | Le and Nguyen [32] | Energy security enhances economic growth. | |
| Economic security | IMF [33] | Economic security contribute to the rise of private investment. | |
| Energy security | Bohi and Toman [97] | How does energy security changed over time from the focus on military preparedness. | |
| Energy security | Cherp et al. [30] | Provides overview of significance of global energy security issues. | |
| Energy security | McDowell and Goldstein [34] | Digital object architecture is important for IoT. | |
| Cybersecurity of the IoT | Carr and Lesniewska [35] | Global climate governance is an early model of a onsensual rules-based approach to tackle cybersecurity issues of the IoT. | |
| Energy supply | Hossein et al. [47] | Integration of renewable energy and optimization of energy use are key enablers of sustainable energy transitions and mitigating climate change. | |
| Society | Fog Computing | Bonomi et al. [41] | IoT requires mobility support and geo-distribution in addition to location awareness and low latency. |
| Economic security | Houseknecht and Abdel Aal [36] | Shifts from informal to formal arrangements for economic security leads to change in the structural features of the family. | |
| Smart technologies | Liu [37] | Smart grid enables both utility providers and customers to transfer, monitor, predict, and manage energy usage effectively and costly. | |
| Privacy risks | Zhang [40] | Improve privacy protection legal mechanism, establish a privacy protection agency, improve of people’s awareness, quality of data. | |
| Privacy risks | Liu [37] | Wireless sensor networks raise new security challenges. | |
| Communication | Khan et al. [42] | Communication will change from human-to-human to human-to-machine. | |
| Edge computing | Shi et al. [43] | Improves response time, battery life, bandwidth cost saving, data safety and privacy. | |
| Smart technologies | Marres [39] | Digital technologies create weak deterministic ideas about principal drivers of social change. | |
| Privacy risks | Tawalbeh et al. [46] | Identify different security and privacy issue of IoT-based systems. | |
| Device security | Trappe et al. [49] | IoT’s future will rely on our ability to adequately secure hard-to-secure, resource-sparse devices. |
References
- Energy Security—Areas of Work—IEA. Available online: https://www.iea.org/areas-of-work/ensuring-energy-security (accessed on 20 August 2020).
- US Energy Association. Available online: https://usea.org/about-usea (accessed on 21 August 2020).
- Kruyt, B.; van Vuuren, D.P.; de Vries, H.J.K.; Groenenberg, H. Indicators for energy security. Energy Policy 2009, 37, 2166–2181. [Google Scholar] [CrossRef]
- Sovacool, B.K.; Mukherjee, I. Conceptualizing and measuring energy security: A synthesized approach. Energy 2011, 36, 5343–5355. [Google Scholar] [CrossRef]
- Ang, B.W.; Choong, W.L.; Ng, T.S. Energy security: Definitions, dimensions and indexes. Renew. Sustain. Energy Rev. 2015, 42, 1077–1093. [Google Scholar] [CrossRef]
- Chalvatzis, K.; Hooper, E. Energy security vs. climate change: Theoretical framework development and experience in selected EU electricity markets. Renew. Sustain. Energy Rev. 2009, 13, 2703–2709. [Google Scholar] [CrossRef] [Green Version]
- Yergin, D. Ensuring energy security. Foreign Aff. 2006, 85, 69–82. [Google Scholar] [CrossRef]
- Mueller-Kraenner, S. Energy Security: Re-Measuring the World; Earthscan: London, UK, 2008. [Google Scholar]
- Chester, L. Conceptualisingenergy security and making explicit its polysemic nature. Energy Policy 2010, 38, 887–895. [Google Scholar] [CrossRef]
- Gellings, C.W.; Samotyj, M.; Howe, B. The future’s smart delivery system [electric power supply]. IEEE Power Energy Mag. 2004, 2, 40–48. [Google Scholar] [CrossRef]
- Goertz, G. Social Science Concepts: A User’s Guide; Princeton University Press: Princeton, NJ, USA, 2006. [Google Scholar]
- Gerring, J. What makes a concept good? A criterial framework for understanding concept formation in the social sciences. Polity 1999, 31, 357–393. [Google Scholar] [CrossRef]
- Jun, E.; Kim, W.; Chang, S.H. The analysis of security cost for different energy sources. Appl. Energy 2009, 86, 1894–1901. [Google Scholar] [CrossRef]
- Cable, V. What is international economic security? Int. Aff. 1995, 71, 305–324. [Google Scholar] [CrossRef]
- Sriramoju, S.B. Opportunities and security implications of bid data mining. Int. J. Res. Sci. Eng. 2017, 3, 44–58. Available online: https://www.researchgate.net/publication/321097052_OPPORTUNITIES_AND_SECURITY_IMPLICATIONS_OF_BIG_DATA_MINING (accessed on 12 December 2021).
- Intel IT Center. Distributed Data Mining and Big Data; Intel: Santa Clara, CA, USA, 2012; Available online: https://www.intel.com/content/dam/www/public/us/en/documents/white-papers/distributed-data-mining-paper.pdf (accessed on 12 December 2021).
- Hackl, R.; Andersson, E.; Harvey, S. Targeting for energy efficiency and improved energy collaboration between different companies using total site analysis (TSA). Energy 2011, 36, 4609–4615. [Google Scholar] [CrossRef] [Green Version]
- Jiang, H.; Wang, K.; Wang, Y.; Gao, M.; Zhang, Y. Energy big data: A survey. IEEE Access 2016, 4, 3844–3861. [Google Scholar] [CrossRef]
- Zhou, K.; Fu, C.; Yang, S. Big data driven smart energy management: From big data to big insights. Renew. Sustain. Energy Rev. 2016, 56, 215–225. [Google Scholar] [CrossRef]
- Zhou, K.; Yang, S.; Shen, C. A review of electric load classification in smart grid environment. Renew. Sustain. Energy Rev. 2013, 24, 103–110. [Google Scholar] [CrossRef]
- Vale, Z.; Morais, H.; Ramos, S.; Soares, J.; Faria, P. Using data mining techniques to support DR programs definition in smart grids. In Proceedings of the IEEE Power and Energy Society General Meeting, Detroit, MI, USA, 24–28 July 2011; pp. 1–8. [Google Scholar] [CrossRef]
- Diamantoulakis, P.D.; Kapinas, V.M.; Karagiannidis, G.K. Big data analytics for dynamic energy management in smart grids. Big Data Res. 2015, 2, 94–101. [Google Scholar] [CrossRef] [Green Version]
- Research & Advisory Group. Break-Even Oil Prices: The Risks of an Extended Price War for OPEC-Plus; Energy Intelligence: New York, NY, USA, 2020; Available online: http://www2.energyintel.com/BreakEvenOilPricesT (accessed on 4 October 2020).
- Regulation (EU) 2015/757 of the European Parliament and of the Council of 29 April 2015 on the Monitoring, Reporting and Verification of Carbon Dioxide Emissions from Maritime Transport, and Amending Directive 2009/16/EC. Off. J. Eur. Union 2015, L123/55. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32015R0757&from=EL (accessed on 20 August 2020).
- Taleb, N. The Black Swan: The Impact of the Highly Improbable; Penguin Press: London, UK, 2008. [Google Scholar]
- TradeLens: Digital Global Supply Chain. Available online: https://www.tradelens.com/ (accessed on 4 October 2020).
- Yildiz, F. Potential ambient energy-harvesting sources and techniques. J. Technol. Stud. 2009, 35, 40–48. [Google Scholar] [CrossRef]
- Kanan, R.; Petrovic, D. Rapid prototyping system for RFID sensing applications. In Proceedings of the Smart SysTech 2012, European Conference on Smart Objects, Systems and Technologies, Osnabrueck, Germany, 12–13 June 2012; pp. 1–7. [Google Scholar]
- Radovanović, M.; Filipović, S.; Golušin, V. Geo-economic approach to energy security measurement-principal component analysis. Renew. Sustain. Energy Rev. 2018, 82, 1691–1700. [Google Scholar] [CrossRef]
- Cherp, A.; Adenikinju, A.; Goldthau, A.; Hernandez, F.; Hughes, L.; Jansen, J.; Jewell, J.; Olshanskaya, M.; Soares de Oliveira, R.; Sovacool, B.; et al. Chapter 5: Energy and security. In Global Energy Assessment: Toward a Sustainable Future; GEA Writing Team, Ed.; Cambridge University Press and IIASA: Cambridge, UK, 2012; pp. 325–384. Available online: http://pure.iiasa.ac.at/id/eprint/10062/ (accessed on 4 October 2020).
- International Atomic Energy Agency. Financing of New Nuclear Power Plants, Nuclear Energy Series No. NG-T-4.2; IAEA: Vienna, Austria, 2008. [Google Scholar]
- Le, T.-H.; Nguyen, C.P. Is energy security a driver for economic growth? Evidence from a global sample. Energy Policy 2019, 129, 436–451. [Google Scholar] [CrossRef]
- Poirson, H. Economic Security, Private Investment, and Growth in Developing Countries; Working paper WP/98/4; International Monetary Fund: Washington, DC, USA, 1998; Available online: https://www.imf.org/external/pubs/ft/wp/wp9804.pdf (accessed on 4 October 2020).
- McDowell, R.M.; Goldstein, G.M. The authoritarian internet power grab. Wall Street J. 2016. Available online: www.wsj.com/articles/the-authoritarian-Internet-power-grab-1477436573 (accessed on 12 December 2021).
- Carr, M.; Lesniewska, F. Internet of things, cybersecurity and governing wicked problems: Learning from climate change governance. Int. Relat. 2020, 34, 391–412. [Google Scholar] [CrossRef]
- Houseknecht, S.K.; Abdel Aal, M. Forms of economic security and the family. J. Comp. Fam. Stud. 1998, 29, 429–449. [Google Scholar] [CrossRef]
- Liu, Y. Wireless sensor network applications in smart grid: Recent trends and challenges. Int. J. Distrib. Sens. Netw. 2012, 8, 492819. [Google Scholar] [CrossRef]
- Potential Benefits to Society Through Smart Metering Initiatives. Available online: https://www.smart-energy.com/regional-news/north-america/potential-benefits-to-society-through-smart-metering-initiatives/ (accessed on 23 May 2020).
- Marres, N. On some uses and abuses of topology in the social analysis of technology (or the problem with smart meters). Theory Cult. Soc. 2012, 29, 288–310. [Google Scholar] [CrossRef] [Green Version]
- Zhang, D. Big data security and privacy protection. In Proceedings of the 8th International Conference on Management and Computer Science, Shenyang, China, 10–12 August 2018; pp. 275–278. [Google Scholar] [CrossRef] [Green Version]
- Flavio, B.; Rodolfo, M.; Jiang, Z.; Sateesh, A. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing (MCC ’12), Association for Computing Machinery, New York, NY, USA, 13–16 August 2012. [Google Scholar] [CrossRef]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future internet: The internet of things architecture, possible applications and key challenges, 2012. In Proceedings of the 10th International Conference on Frontiers of Information Technology, Islamabad, Pakistan, 17–19 December 2012; pp. 257–260. [Google Scholar] [CrossRef] [Green Version]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- ETSI European Standard, CYBER.; Cyber Security for Consumer Internet of Things: Baseline Requirements, ETSI EN 303 645 V2.1.1 (2020-06), June 2020. Available online: https://www.etsi.org/deliver/etsi_en/303600_303699/303645/02.01.01_60/en_303645v020101p.pdf (accessed on 12 December 2021).
- Sen, S.; Koo, J.; Bagchi, S. TRIFECTA: Security, energy efficiency, and communication capacity comparison for wireless IoT devices. IEEE Internet Comput. 2018, 22, 74–81. [Google Scholar] [CrossRef] [Green Version]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT privacy and security: Challenges and solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Hossein Motlagh, N.; Mohammadrezaei, M.; Hunt, J.; Zakeri, B. Internet of Things (IoT) and the energy sector. Energies 2020, 13, 494. [Google Scholar] [CrossRef] [Green Version]
- Bekara, C. Security issues and challenges for the IoT-based smart grid. Procedia Comput. Sci. 2014, 34, 532–537. [Google Scholar] [CrossRef] [Green Version]
- Trappe, W.; Howard, R.; Moore, R.S. Low-Energy security: Limits and opportunities in the Internet of Things. IEEE Secur. Privacy 2015, 13, 14–21. [Google Scholar] [CrossRef]
- Chen, Q.; Liu, N.; Wang, C.; Zhang, J. Optimal power utilizing strategy for PV-based EV charging stations considering Real-time price. In Proceedings of the 2014 IEEE Conference and Expo Transportation Electrification Asia-Pacific (ITEC Asia-Pacific), Beijing, China, 31 August–3 September 2014; pp. 1–6. [Google Scholar]
- Pazouki, S.; Mohsenzadeh, A.; Ardalan, S.; Haghifam, M.-R. Simultaneous Planning of PEV Charging Stations and DGs Considering Financial, Technical, and Environmental Effects. Can. J. Electr. Comput. Eng. 2015, 38, 238–245. [Google Scholar] [CrossRef]
- Pazouki, S.; Mohsenzadeh, A.; Haghifam, M.-R.; Ardalan, S. Simultaneous Allocation of Charging Stations and Capacitors in Distribution Networks Improving Voltage and Power Loss. Can. J. Electr. Comput. Eng. 2015, 38, 100–105. [Google Scholar] [CrossRef]
- Ghasempour, A. Internet of Things in smart grid: Architecture, applications, services, key technologies, and challenges. Inventions 2019, 4, 22. [Google Scholar] [CrossRef] [Green Version]
- NIST Releases Final Version of Smart Grid Framework. Available online: https://www.nist.gov/smartgrid/upload/NIST-SP-1108r3.pdf (accessed on 16 January 2019).
- Mouftah, H.T.; Erol-Kantarci, M.; Rehmani, M.H. Communication architectures and technologies for advanced smart grid services. In Transportation and Power Grid in Smart Cities: Communication Networks and Services, 1st ed.; Mouftah, H.T., Erol-Kantarci, M., Rehmani, M.H., Eds.; Wiley: Hoboken, NJ, USA, 2019; pp. 217–245. [Google Scholar]
- Zhao, Z.; Chen, G. An overview of cyber security for smart grid. In Proceedings of the 2018 IEEE 27th International Symposium on Industrial Electronics, Cairns, Australia, 13–15 June 2018; pp. 1127–1131. [Google Scholar]
- Refaat, S.S.; Abu-Rub, H.; Trabelsi, M.; Mohamed, A. Reliability evaluation of smart grid system with large penetration of distributed energy resources. In Proceedings of the 2018 IEEE International Conference on Industrial Technology (ICIT), Lyon, France, 20–22 February 2018; pp. 1279–1284. [Google Scholar]
- Refaat, S.S.; Mohamed, A.; Kakosimos, P. Self-healing control strategy; challenges and opportunities for distribution systems in smart grid. In Proceedings of the 2018 IEEE 12th International Conference on Compatibility, Power Electronics and Power Engineering (CPE-POWERENG 2018), Doha, Qatar, 10–12 April 2018; pp. 1–6. [Google Scholar]
- Jarvis, R.; Moses, P. Smart grid congestion caused by plug-in electric vehicle charging. In Proceedings of the 2019 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 7–8 February 2019; pp. 1–5. [Google Scholar]
- Rafiei, S.; Bakhshai, A. A review on energy efficiency optimization in Smart Grid. In Proceedings of the 38th Annual Conference on IEEE Industrial Electronics Society, Montreal, QC, Canada, 25–28 October 2012; pp. 5916–5919. [Google Scholar]
- Akaber, P.; Moussa, B.; Debbabi, M.; Assi, C. Automated post-failure service restoration in smart grid through network reconfiguration in the presence of energy storage systems. IEEE Syst. J. 2019, 1–10. [Google Scholar] [CrossRef]
- Qi, F.; Yu, P.; Chen, B.; Li, W.; Zhang, Q.; Jin, D.; Zhang, G.; Wang, Y. Optimal planning of smart grid communication network for interregional wide-area monitoring protection and control system. In Proceedings of the 2018 IEEE International Conference on Energy Internet (ICEI), Beijing, China, 21–25 May 2018; pp. 190–195. [Google Scholar]
- Ghasempour, A. Optimum packet service and arrival rates in advanced metering infrastructure architecture of smart grid. In Proceedings of the 2016 IEEE Green Technologies Conference (IEEE GreenTech 2016), Kansas City, MO, USA, 6–8 April 2016; pp. 1–5. [Google Scholar]
- Ghasempour, A.; Gunther, J.H. Finding the optimal number of aggregators in machine-to-machine advanced metering infrastructure architecture of smart grid based on cost, delay, and energy consumption. In Proceedings of the 2016 13th IEEE Annual Consumer Communications & Networking Conference (IEEE CCNC 2016), Las Vegas, NV, USA, 9–12 January 2016; pp. 960–963. [Google Scholar]
- Ghasempour, A. Optimized scalable decentralized hybrid advanced metering infrastructure for smart grid. In Proceedings of the 2015 IEEE International Conference on Smart Grid Communications (IEEE SmartGridComm 2015), Miami, FL, USA, 2–5 November 2015; pp. 223–228. [Google Scholar]
- Aileni, R.M. Healthcare predictive model based on big data fusion from biomedical sensors. In Proceedings of the Conference eLearning and Software for Education eLSE, Bucharest, Romania, 21–22 April 2016; Carol I” National Defense University Publishing House: Bucharest, Romania, 2016; pp. 328–333. [Google Scholar]
- Plageras, A.P.; Psannis, K.E.; Stergiou, C.; Wang, H.; Gupta, B.B. Efficient IoT-based sensor big data collection–processing and analysis in smart buildings. Future Gener. Comput. Syst. 2018, 82, 349–357. [Google Scholar] [CrossRef]
- Huang, Y.; Chen, Z.-X.; Yu, T.; Huang, X.-Z.; Gu, X.-F. Agricultural remote sensing big data: Management and applications. J. Integr. Agric. 2018, 17, 1915–1931. [Google Scholar] [CrossRef]
- Jiang, P.; Winkley, J.; Zhao, C.; Munnoch, R.; Min, G.; Yang, L.T. An intelligent information forwarder for healthcare big data systems with distributed wearable sensors. IEEE Syst. J. 2014, 10, 1147–1159. [Google Scholar] [CrossRef]
- Zaslavsky, A.; Perera, C.; Georgakopoulos, D. Sensing as a service and big data. arXiv 2013, arXiv:1301.0159. [Google Scholar]
- Westbrook, P. Big data on the horizon from a new generation of distributed optical fiber sensors. APL Photonics 2020, 5, 020401. [Google Scholar] [CrossRef] [Green Version]
- Tang, B.; Chen, Z.; Hefferman, G.; Pei, S.; Wei, T.; He, H.; Yang, Q. Incorporating intelligence in fog computing for big data analysis in smart cities. IEEE Trans. Ind. Inform. 2017, 13, 2140–2150. [Google Scholar] [CrossRef]
- Zhang, Y.; Ma, S.; Yang, H.; Lv, J.; Liu, Y. A big data driven analytical framework for energy-intensive manufacturing industries. J. Clean. Prod. 2018, 197, 57–72. [Google Scholar] [CrossRef]
- Syed, A.; Gillela, K.; Venugopal, C. The future revolution on big data. Future 2013, 2, 2446–2451. [Google Scholar]
- Dai, H.-N.; Wang, H.; Xu, G.; Wan, J.; Imran, M. Big data analytics for manufacturing internet of things: Opportunities, challenges and enabling technologies. Enterp. Inf. Syst. 2020, 14, 1279–1303. [Google Scholar] [CrossRef] [Green Version]
- Ahmad, I.; Ayub, A.; Kano, M.; Cheema, I.I. Gray-box soft sensors in process industry: Current practice, and future prospects in era of big data. Processes 2020, 8, 243. [Google Scholar] [CrossRef] [Green Version]
- Lee, C.-H.; Yang, H.-C.; Lin, S.-J. Incorporating big data and Social Sensors in a Novel Early Warning System of Dengue Outbreaks. In Proceedings of the 2015 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, Paris, France, 25–28 August 2015; pp. 1428–1433. [Google Scholar]
- Bakytbekov, A.; Nguyen, T.Q.; Li, W.; Cottrill, A.L.; Zhang, G.; Strano, M.S.; Salama, K.N.; Shamim, A. Multi-source ambient energy harvester based on RF and thermal energy: Design, testing, and IoT application. Energy Sci. Eng. 2020, 8, 3883–3897. [Google Scholar] [CrossRef]
- Data and Statistics. Available online: https://www.iea.org/data-and-statistics?country=FRANCE&fuel=Energy%20supply&indicator=TPESbySource (accessed on 5 November 2020).
- Climatic Research Unit: Data: High-Resolution Datasets: CRUTS 4.04: CRU CY 4.04. Available online: https://crudata.uea.ac.uk/cru/data/hrg/cru_ts_4.04/crucy.2004161557.v4.04/countries/ (accessed on 30 September 2020).
- Database-Eurostat. Available online: https://ec.europa.eu/eurostat/web/energy/data/database?p_p_id=NavTreeportletprod_WAR_NavTreeportletprod_INSTANCE_QAMy7Pe6HwI1&p_p_lifecycle=0&p_p_state=normal&p_p_mode=view&p_p_col_id=column-2&p_p_col_count=1 (accessed on 30 September 2020).
- CAC Oil & Gas Historical Rates (FROG). Available online: https://www.investing.com/indices/cac-oil---gas-historical-data (accessed on 30 September 2020).
- Wieczorek-Kosmala, M. Weather risk management in energy sector: The Polish case. Energies 2020, 13, 945. [Google Scholar] [CrossRef] [Green Version]
- Hassani, H.; Huang, X.; Silva, E. Big data and climate change. BIG DATA and Cogn. Comput. 2019, 3, 12. [Google Scholar] [CrossRef] [Green Version]
- Medina, H.; Tian, D.; Marin, F.R.; Chirico, G.B. Comparing GEFS, ECMWF, and post processing methods for ensemble precipitation forecasts over Brazil. J. Hydrometeorol. 2019, 20, 773–790. [Google Scholar] [CrossRef]
- Hassani, H.; Yeganegi, M.R.; Beneki, C.; Unger, S.; Moradghaffari, M. Big data and energy poverty alleviation. Big Data Cogn. Comput. 2019, 3, 50. [Google Scholar] [CrossRef] [Green Version]
- Del Real, A.J.; Dorado, F.; Durán, J. Energy demand forecasting using deep learning: Applications for the French grid. Energies 2020, 13, 2242. [Google Scholar] [CrossRef]
- Bhattacharyya, S.C.; Timilsina, G.R. Energy Demand Models for Policy Formulation, a Comparative Study of Energy Demand Models; The World Bank Development Research Group Environment and Energy Team: Washington, DC, USA, 2009; Available online: https://openknowledge.worldbank.org/bitstream/handle/10986/4061/WPS4866.pdf (accessed on 10 November 2020).
- Amjady, N.; Hemmati, M. Energy price forecasting-problems and proposals for such predictions. IEEE Power Energy Mag. 2006, 4, 20–29. [Google Scholar] [CrossRef]
- Weron, R. Electricity price forecasting: A review of the state-of-the-art with a look into the future. Int. J. Forecast. 2014, 1030–1081. [Google Scholar] [CrossRef] [Green Version]
- Andriosopoulos, D.; Doumpos, M.; Pardalos, P.M.; Zopounidis, C. Computational approaches and data analytics in financial services: A literature review. J. Oper. Res. Soc. 2019, 70, 1581–1599. [Google Scholar] [CrossRef]
- Hassani, H.; Beneki, C.; Unger, S.; Mazinani, M.T.; Yeganegi, M.R. Text mining in big data analytics. Big Data Cogn. Comput. 2020, 4, 1. [Google Scholar] [CrossRef] [Green Version]
- Cerchiello, P.; Giudici, P. Big data analysis for financial risk management. J. Big Data 2016, 3, 18. [Google Scholar] [CrossRef] [Green Version]
- Kou, G.; Chao, X.; Peng, Y.; Alsaadi, F.E.; Herrera-Viedma, E. Machine learning methods for systemic risk analysis in financial sectors. Technol. Econ. Dev. Econ. 2019, 25, 716–742. [Google Scholar] [CrossRef]
- Chen, A.S.; Leung, M.T.; Pan, S.; Chou, C.-Y. Financial hedging in energy market by cross-learning machines. Neural Comput. Applic. 2020, 32, 10321–10335. [Google Scholar] [CrossRef]
- Lie, E.A.; Gullaksen, M.F. Using Machine Learning to Improve Hedging of Power Prices in the Nordic Market: A Study of How Predictions of the Nordic System Price can be Used for Norwegian Hydropower Producer’s Hedging Strategies. Master’s Thesis, Economics and Business Administration, Norwegian School of Economics, Bergen, Norway, 2019. Available online: https://openaccess.nhh.no/nhh-xmlui/bitstream/handle/11250/2644902/masterthesis.pdf?sequence=1 (accessed on 25 November 2020).
- Bohi, T.; Toman, M. The Economics of Energy Security; Kluwer Academic Publishers: Boston, MA, USA, 1996. [Google Scholar] [CrossRef]



| Country | Annual Average Temperature | Annual Minimum Temperature | Annual Maximum Temperature | Natural Gas Price | Electricity Price | |
|---|---|---|---|---|---|---|
| Germany | Natural Gas Price | −0.2772 | −0.2676 | −0.3719 | - | 0.6643 |
| Electricity Price | −0.5929 | −0.5916 | −0.6421 | 0.6643 | - | |
| EWI1 | −0.3782 | −0.4770 | −0.4854 | 0.8167 | 0.95 | |
| UK | Natural Gas Price | −0.0456 | −0.0599 | 0.1757 | - | 0.8322 |
| Electricity Price | −0.1333 | −0.1094 | −0.0598 | 0.8322 | - | |
| FTUB0500 | 0.3669 | 0.3015 | 0.3684 | 0.0839 | −0.2587 | |
| France | Natural Gas Price | −0.3636 | −0.3233 | −0.3923 | - | 0.1468 |
| Electricity Price | 0.5384 | 0.5975 | 0.4658 | 0.1468 | - | |
| FROG | 0.4182 | 0.4834 | 0.3109 | −0.2308 | 0.3287 |
| Country | Estimated Regression Model | R2 | |
|---|---|---|---|
| Germany | Natural Gas Price Forecasting EFquation | 0.1431 | |
| Electricity Price Forecasting Equation | 0.3695 | ||
| EWI1 Forecasting Equation | 0.2478 | ||
| Natural Gas Price/EWI1 Coefficient Ration | - | ||
| Electricity Price/EWI1 Coefficient Ratio | - | ||
| France | Electricity Price Forecasting Equation | 0.284 | |
| FROG Forecasting Equation | 0.1445 | ||
| Electricity Price/FROG Coefficient Ratio | - |
| Usage of Big Data | Benefits |
|---|---|
| Impact on private companies | Prevailing balance in supply and demand Ensuring stable energy price Reduction of uncertainty in energy prices and supply Contribute to efficiency in distribution of energy between providers and consumers Coordination of electricity generation Reduction of costs for energy providers and consumers Energy load classification including energy resources scheduling, load forecasting, optimal energy resources scheduling |
| Impact on national economies | Market stability meaning little or no market disruptions Identification of new reserves to be extracted at cheaper costs Identification of profitable and secure investment regimes Identification of vulnerabilities in infrastructure and development of new technologies to increase safety Forecasting of weather changes to optimize energy generation Identification of cross sectoral vulnerabilities Real time adjustment and coordination across different energy providers Contribution to definition of decision-makers rules Contribution to good governance while identifying lack of transparency risks and potentials for conflicts |
| Impact on society | Contribution to an increase of social and economic security Provision of energy access Mitigate the risk of unprotected and unexpected impact of immediate as well as prolonged changing weather conditions |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hassani, H.; Komendantova, N.; Kroos, D.; Unger, S.; Yeganegi, M.R. Big Data and Energy Security: Impacts on Private Companies, National Economies and Societies. IoT 2022, 3, 29-59. https://doi.org/10.3390/iot3010002
Hassani H, Komendantova N, Kroos D, Unger S, Yeganegi MR. Big Data and Energy Security: Impacts on Private Companies, National Economies and Societies. IoT. 2022; 3(1):29-59. https://doi.org/10.3390/iot3010002
Chicago/Turabian StyleHassani, Hossein, Nadejda Komendantova, Daniel Kroos, Stephan Unger, and Mohammad Reza Yeganegi. 2022. "Big Data and Energy Security: Impacts on Private Companies, National Economies and Societies" IoT 3, no. 1: 29-59. https://doi.org/10.3390/iot3010002
APA StyleHassani, H., Komendantova, N., Kroos, D., Unger, S., & Yeganegi, M. R. (2022). Big Data and Energy Security: Impacts on Private Companies, National Economies and Societies. IoT, 3(1), 29-59. https://doi.org/10.3390/iot3010002








