From Context to Action: Establishing a Pre-Chain Phase Within the Cyber Kill Chain
Abstract
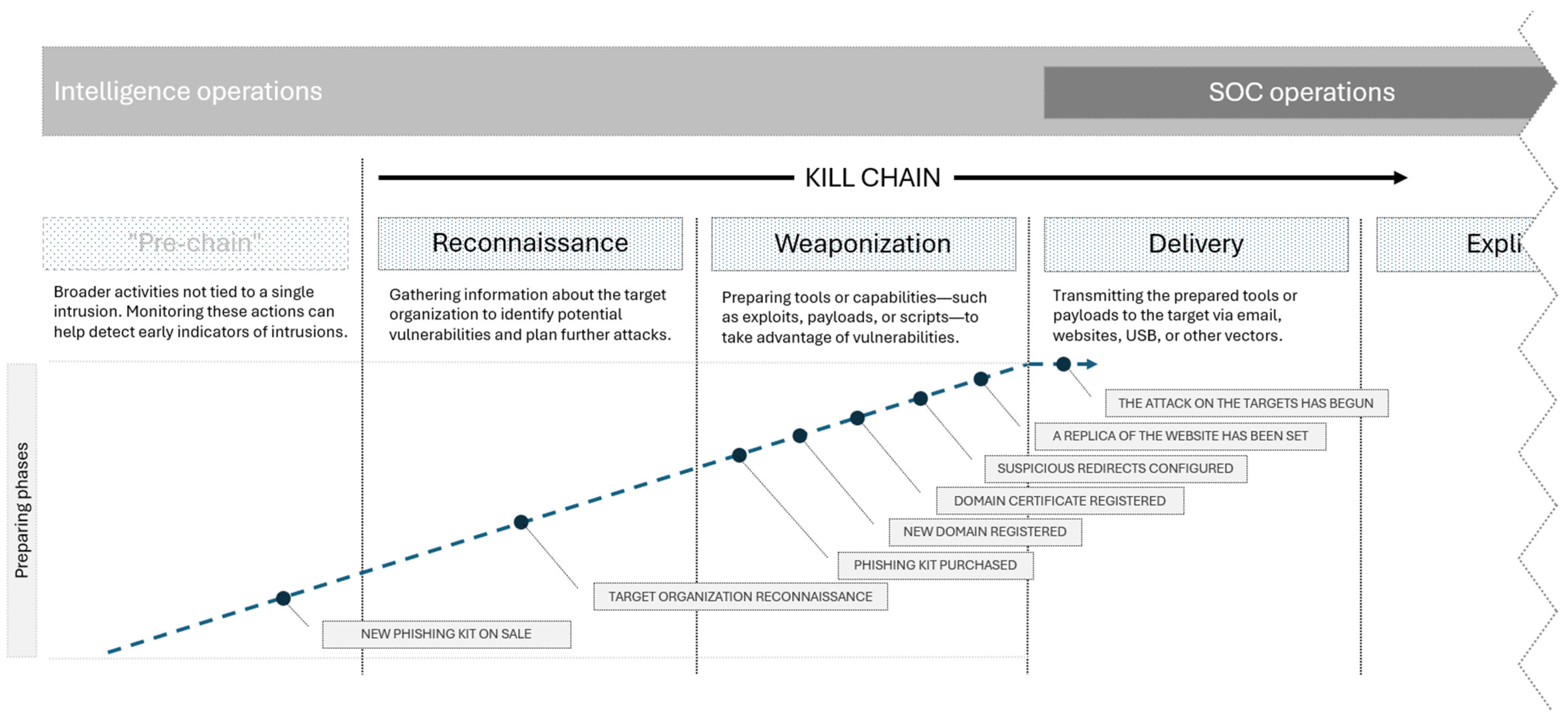
1. Introduction
2. Related Works
2.1. Variants of the Kill Chain and Related Frameworks
2.2. Preliminary Alerts from External Infrastructure Indicators
2.3. Threat Intelligence Derived from Internet Discussions and Illicit Ecosystems
2.4. CaaS as a Macro-Signal
2.5. Subtle Indicators and Foresight Analysis
2.6. Morphological Analysis as a Method of Structuring
2.7. Resilience Engineering and Preemptive Governance
2.8. Syntheses of IOT Security as a Contextual Framework
2.9. Where Contemporary Literature Is Deficient
- Integration of methods: Early-warning systems identify signal sources (domain/CT dynamics, online conversations), yet they fail to integrate them into a reproducible, auditable, kill-chain-compatible organizing methodology that produces outputs (watchlists, thresholds, courses of action). GMA offers the requisite structuring capability but is underutilized in cybersecurity [4,5].
- Governance coupling: Resilience guidance advocates for proactive measures, yet the majority of implementations are reactive and focused on security teams; the literature inadequately specifies how legal, communications, or procurement functions can be activated by contextual signals to increase costs for attackers at an earlier stage [12].
3. Methods
3.1. Research Design
3.2. Analytical Framework: STEMPLES+
3.3. Data Elicitation and Brainstorming Process
3.4. Structuring with GMA
3.5. Operationalization into IOT
3.6. Proposed Methodological Workflow
4. Case Studies
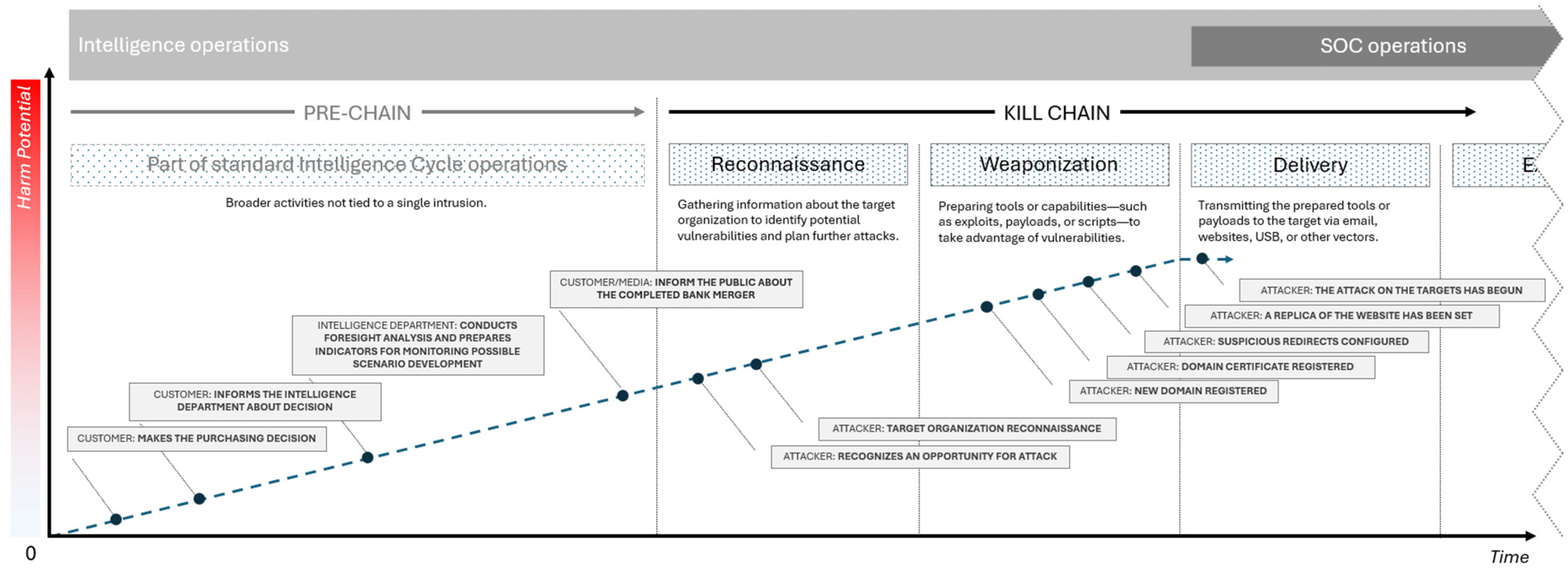
4.1. Bank X Merger
4.2. Phishing Kit on the Dark Web
4.3. Wartime Donation Scams
4.4. Generalizability Across Threat Environments
5. Results
5.1. Structured Scenario Generation and Validation
5.2. Quantified Lead-Time Advantage
- Organizational milestones (e.g., mergers) provided medium-range anticipation windows (two to three weeks).
- Illicit-market signals provided long-range anticipation windows (more than one month).
- Geopolitical crises provided short-range anticipation windows (a few days).
6. Discussion
7. Conclusions
8. Limitations and Future Works
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kazimierczak, M.; Habib, N.; Chan, J.H.; Thanapattheerakul, T. Impact of AI on the Cyber Kill Chain: A Systematic Review. Heliyon 2024, 10, e40699. [Google Scholar] [CrossRef] [PubMed]
- Muller, L.P. Cybersecurity in Practice: The Vigilant Logic of Kill Chains and Threat Construction. Eur. J. Int. Secur. 2024, 10, 231–251. [Google Scholar] [CrossRef]
- Ritchey, T. General Morphological Analysis: An Overview. Acad. Lett. 2022, 4620. [Google Scholar] [CrossRef]
- Johansen, I. Scenario Modelling with Morphological Analysis. Technol. Forecast. Soc. Change 2018, 126, 116–125. [Google Scholar] [CrossRef]
- Ritchey, T. General Morphological Analysis as a Basic Scientific Modelling Method. Technol. Forecast. Soc. Change 2018, 126, 81–91. [Google Scholar] [CrossRef]
- Hiltunen, E. The Future Sign and Its Three Dimensions. Futures 2008, 40, 247–260. [Google Scholar] [CrossRef]
- Holopainen, M.; Toivonen, M. Weak Signals: Ansoff Today. Futures 2012, 44, 198–205. [Google Scholar] [CrossRef]
- Agten, P.; Joosen, W.; Piessens, F.; Nikiforakis, N. Seven Months’ Worth of Mistakes: A Longitudinal Study of Typosquatting Abuse. In Proceedings of the Network and Distributed System Security Symposium 2015, San Diego, CA, USA, 8–11 February 2015. [Google Scholar] [CrossRef]
- AlSabah, M.; Nabeel, M.; Boshmaf, Y.; Choo, E. Content-Agnostic Detection of Phishing Domains Using Certificate Transparency and Passive DNS. In Proceedings of the 25th International Symposium on Research in Attacks, Intrusions and Defenses, Limassol, Cyprus, 26–28 October 2022; Association for Computing Machinery: New York, NY, USA, 2022; pp. 446–459. [Google Scholar] [CrossRef]
- Sood, A.K.; Enbody, R.J. Crimeware-as-a-Service—A Survey of Commoditized Crimeware in the Underground Market. Int. J. Crit. Infrastruct. Prot. 2013, 6, 28–38. [Google Scholar] [CrossRef]
- European Union Agency for Law Enforcement Cooperation. Cyber-Attacks: The Apex of Crime as a Service; University of Lucknow: Lucknow, India, 2023; Available online: https://op.europa.eu/en/publication-detail/-/publication/1eaea077-5768-11ee-9220-01aa75ed71a1/language-en (accessed on 1 March 2022).
- Ross, R.; Pillitteri, V.; Graubart, R.; Bodeau, D.; McQuaid, R. Developing Cyber-Resilient Systems; National Institute of Standards and Technology (U.S.): Gaithersburg, MA, USA, 2021. [CrossRef]
- Kim, H.; Kwon, H.; Kim, K.K. Modified Cyber Kill Chain Model for Multimedia Service Environments. Multimed. Tools Appl. 2018, 78, 3153–3170. [Google Scholar] [CrossRef]
- Panahnejad, M.; Mirabi, M. APT-Dt-KC: Advanced Persistent Threat Detection Based on Kill-Chain Model. J. Supercomput. 2022, 78, 8644–8677. [Google Scholar] [CrossRef]
- Ahmed, Y.; Asyhari, A.T.; Arafatur Rahman, M. A Cyber Kill Chain Approach for Detecting Advanced Persistent Threats. Comput. Mater. Contin. 2021, 67, 2497–2513. [Google Scholar] [CrossRef]
- Kintis, P.; Miramirkhani, N.; Lever, C.; Chen, Y.; Romero-Gómez, R.; Pitropakis, N.; Nikiforakis, N.; Antonakakis, M. Hiding in Plain Sight. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 569–586. [Google Scholar] [CrossRef]
- Sapienza, A.; Bessi, A.; Damodaran, S.; Shakarian, P.; Lerman, K.; Ferrara, E. Early Warnings of Cyber Threats in Online Discussions. In Proceedings of the 2017 IEEE International Conference on Data Mining Workshops (ICDMW), New Orleans, LA, USA, 18–21 November 2017; pp. 667–674. [Google Scholar] [CrossRef]
- Sapienza, A.; Ernala, S.K.; Bessi, A.; Lerman, K.; Ferrara, E. DISCOVER: Mining Online Chatter for Emerging Cyber Threats. In WWW ‘18: Companion Proceedings of the Web Conference 2018; International World Wide Web Conferences Steering Committee: Geneva, Switzerland, 2018; pp. 983–990. [Google Scholar] [CrossRef]
- Ansoff, H.I. Managing Strategic Surprise by Response to Weak Signals. Calif. Manag. Rev. 1975, 18, 21–33. [Google Scholar] [CrossRef]
- Peripheral Vision: Detecting the Weak Signals That Will Make Or Break Your Company. Available online: https://cir.nii.ac.jp/crid/1970023484886007978 (accessed on 22 December 2025).
- Mendonça, S.; Cardoso, G.; Caraça, J. The Strategic Strength of Weak Signal Analysis. Futures 2011, 44, 218–228. [Google Scholar] [CrossRef]
- Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A. Internet of Things: Security and Solutions Survey. Sensors 2022, 22, 7433. [Google Scholar] [CrossRef]
- Ritchey, T. Modeling Alternative Futures with General Morphological Analysis. World Futures Rev. 2011, 3, 83–94. [Google Scholar] [CrossRef]
- Ainslie, S.; Thompson, D.; Maynard, S.; Ahmad, A. Cyber-Threat Intelligence for Security Decision-Making: A Review and Research Agenda for Practice. Comput. Secur. 2023, 132, 103352. [Google Scholar] [CrossRef]
- NATO Defense College. Insight; NATO Defense College: Rome, Italy, 2024; ISSN 3006-5380. [Google Scholar]
- Assessing Cyber Capabilities with STEMPLES Plus. Available online: https://treadstone71.com/index.php/intelligence-briefs/stemples-plus-as-a-framework-to-assess-cyber-capabilities (accessed on 21 June 2025).
- NIST Cybersecurity Framework. Available online: https://www.nist.gov/cyberframework (accessed on 21 June 2025).
- HelpUkrainian. Available online: https://x.com/HelpUkrainian (accessed on 27 February 2022).
- Support Ukraine. Available online: https://urlscan.io/result/74c092f2-b02c-43a1-9872-39858a03983d/ (accessed on 28 February 2022).
- Donate Ukraine. Available online: https://urlscan.io/result/8aef5c24-26ca-48b0-8921-c9b8a4b9a347/ (accessed on 1 March 2022).



| Theory/Author | Core Concept | Analytical Mechanism | Relevance to IOT Framework |
|---|---|---|---|
| Ansoff’s Weak Signals (1975) [19] | Weak signals are early, ambiguous indicators of emerging discontinuities. | Detect deviations before they become trends; interpret faint cues as potential precursors of strategic change. | Provides the theoretical basis for treating early contextual anomalies (e.g., domain-registration clusters) as anticipatory threat indicators. |
| Hiltunen’s Futures Cone & Weak-Signal Taxonomy (2008) [6] | Weak signals consist of three elements: the signal, the issue, and the interpretation. | Categorizes signals by their visibility, novelty, and potential impact; emphasizes interpretive discipline. | Aligns with the IOT method of separating raw cues from analyst-generated interpretations, improving transparency and reproducibility. |
| Holopainen & Toivonen’s Multidimensional Weak-Signal Framework (2012) [7] | Weak signals arise from interacting socio-cultural, technological, and psychological domains. | Identifies cross-domain interactions that amplify or suppress early signals. | Supports the use of the STEMPLES+ framework for identifying multidomain triggers that precede threat-actor preparation. |
| Day & Schoemaker’s Peripheral Vision (2006) [20] | Organizations need structured mechanisms to detect early signals at the periphery. | Recommends systematic scanning routines and structured sense-making processes. | Conceptually aligned with the scanning → GMA → IOT pathway, reinforcing the need for disciplined horizon scanning. |
| Mendonça et al. Early Warning Signals (2004) [21] | Focus on early warning of extreme events by modeling how minor anomalies accumulate. | Uses deviation patterns, event clustering, and thresholds to anticipate disruptive outcomes. | Justifies the threshold-based escalation logic in IOT, where multiple weak signals coalesce into actionable warnings. |
| Framework | Domains Covered | Applicability in Cyber Foresight | Key Limitations |
|---|---|---|---|
| PESTEL | Political, Economic, Social, Technological, Environmental, Legal | Broad macro-environmental scanning; used in cyber foresight. | Lacks Military/Security dimensions, limited cyber focus. |
| STEEPLE | PESTEL + Ethical | Adds an ethical dimension to macro analysis. | Still lacks cyber-specific domains. |
| NIST CSF | Risk functions, not domain-based scanning | Strong operational risk management relevance. | Not suitable for horizon scanning or driver-based modeling. |
| PMESII-PT | Political, Military, Economic, Social, Information, Infrastructure, Physical Environment, Time | Robust for high-level geopolitical and conflict-environment analysis; incorporates relevant structural factors. | Optimized for military/state-level planning; insufficient granularity for organizational cyber-threat anticipation; limited incorporation of cultural/psychological micro-drivers. |
| STEMPLES+ | Social, Technical, Economic, Military, Political, Legal, Education, Security, +(Cultural, Demographic, Psychological, Religious) | Broadest coverage; applied in intelligence analysis. | Requires adaptation and interdisciplinary expertise. |
| Dimension | Scope in Cyber Landscape |
|---|---|
| Social | Societal norms, values, digital literacy, online behaviors, narratives on social networks, impact of disinformation on trust [6,7]. |
| Technological | Access to technology, technological innovation rates, vulnerabilities in digital infrastructure, adoption of AI and automation, and availability of cyber-tools [12]. |
| Economic | Market conditions, the digital economy, financial incentives for cybercrime, cryptocurrency adoption, and the cost of exploits or access-broker services [11]. |
| Military | Cyber force capabilities, hybrid warfare, military conflicts influencing cyber operations, and nation-state-sponsored campaigns [11]. |
| Political | National regulations, cyber policies, sanctions regimes, and political motivations are driving state or non-state actors in cyberspace [2]. |
| Legal/Legislative | Laws and compliance regimes shaping digital space (e.g., GDPR, NIS2), obligations for critical infrastructure, and liability frameworks [27]. |
| Environmental | The energy demands of data centers, the environmental sustainability of ICT, and resource dependencies can create vulnerabilities [7]. |
| Educational | Availability and quality of cybersecurity training, public awareness programs, and academic-industry partnerships for threat monitoring [26]. |
| Ethical | Dilemmas in AI surveillance, boundaries of lawful interception, and ethical issues in offensive cyber operations [4]. |
| Security | Protection of critical infrastructure, national CERT capacity, detection tools, response readiness, and data-leak incidents [12,24]. |
| Psychological | Impact of fear, uncertainty, and doubt (FUD) on public trust; use of psychological operations in campaigns; perception of safety [6,7]. |
| Religious | Influence of religion on community trust and vulnerability; exploitation of religious events for fraud or propaganda [6,7]. |
| Cultural | Cross-cultural differences in online privacy and surveillance norms, digital discrimination, and tolerance for online misinformation [4,6]. |
| Demographic | Generational divides in technology use, digital divides, and targeting of vulnerable groups (e.g., the elderly in banking fraud) [6,7]. |
| Advantages | Limitations |
|---|---|
| Captures a broader set of socio-technical drivers compared to classical PESTEL-type frameworks. | Requires a larger and more diverse set of experts for effective brainstorming and analysis. |
| Enables synthesis of diverse contextual events into coherent scenarios, enriching foresight. | Complexity may slow down analyses when rapid assessments are required. |
| Provides flexibility to incorporate emerging domains (e.g., cultural, demographic, psychological). | Risk of producing overly broad scenarios if not properly bounded. |
| Directly applicable to intelligence-led cybersecurity monitoring and IOT generation. | Higher resource requirements compared to lighter frameworks such as PESTEL or STEEPLE. |
| Dimension | What? Incentive | Why? Why Is It an Incentive? | How? How Is It Exploited? | When? When Is It Most Likely to Be Exploited? |
|---|---|---|---|---|
| Social | Economic crisis | Exploits public dissatisfaction | Offers “quick loans” using the Bank X brand | During announcements and throughout the crisis |
| Increased public discussion of investments | Exploits a lack of financial knowledge | Promotes high-return investments | During intensive media and social media coverage | |
| Presence of anti-elitist narratives | Exploits distrust in banks/system | Fake services with messages like “Banks are lying, buy credit from us” | When negative news about bank profits or state favoritism spreads | |
| Technological | Introduction of new banking technology (e.g., video calls via mobile app) | Exploits the client’s unfamiliarity with new features | Impersonates a banker, sends fake activation via messaging apps to install malware | After official announcements of new features |
| Mobile banking app update | Exploits the adoption period | Sends fake update notifications with a malicious app | After the announcement and during rollout | |
| Online banking redesign | Exploits transition confusion | Lures clients to fake “new-look” websites to steal credentials | During official rebranding or design rollout | |
| Planned service outage | Exploits downtime urgency | Provides “emergency access” via phishing site | While official services are unavailable | |
| Economic | Rising interest rates | Exploits client dissatisfaction | Sends fraudulent “refinancing/freeze” offers | After banks/government announce increases |
| Bank X acquires another bank | Exploits brand/identity confusion | Fake “migration verification” messages | After public merger/acquisition announcements | |
| Launch of a new service/brand | Exploits the client adoption period | Fake promotions mimicking the new service | During intensive marketing campaigns | |
| Aggressive credit promotion | Exploits heightened loan demand | Fake offers with even better terms | During high-volume advertising campaigns | |
| Military | Banks and NGOs collect war-related donations | Exploits public solidarity | Fake donation appeals in the bank’s name | During official fundraising campaigns |
| Outbreak of war | Exploits fear and distrust in the financial system | Fake “urgent security” messages, requests for transfers | In the early stages of armed conflict | |
| Government announces higher benefits for veterans | Exploits veterans’ lack of awareness | Fake verification forms to capture sensitive data | Around announcements and during payouts | |
| Political | New tax on savings/investments | Exploits the saver/investor dissatisfaction | Fake tax-avoidance update requests | Around law announcements and enforcement |
| Law enabling cryptocurrency use | Exploits increased public interest | Fake investment invitations in crypto | Around announcements and rollout | |
| Introduction of sanctions | Exploits the fear of blocked accounts | Fake urgent data verification to avoid sanctions | During media coverage of sanctions | |
| Legal | New EU regulatory frameworks | Exploits transition to compliance | Fake data-update requests for GDPR/NIS2 compliance | During required client confirmations |
| National bank tightens credit rules | Exploits frustration with access | Fake “fast loan approval” offers | After the announcement and enforcement | |
| New AML/CTF law enters into force | Exploits mandatory updates | Fake urgent compliance requests | During legislative transition | |
| Educational | Bank X launches student packages with the university | Exploits student demand | Fake “special student offer” sites | During the marketing campaign |
| Start of academic year | Exploits student rush for accounts | Fake fast-registration offers | August–October | |
| Security | New phishing kit on the Dark Web | Exploits the tool availability | Attacks with a pre-made phishing kit | After the kit is advertised |
| Data leak of Bank X clients | Exploits compromised data | Personalized phishing messages | Once the data is circulating | |
| Ransomware attack on another bank | Exploits fear/distrust | Fake urgent “verification” campaigns | Immediately after a high-profile attack | |
| Religion | Religious holidays (donation season) | Exploits generosity sentiment | Fake donation calls | During religious holidays (e.g., Christmas, Easter) |
| Local government pays Christmas bonuses | Exploits vulnerable groups’ interests | Fake “bonus confirmation” forms | During the holiday season | |
| Demographic | New government subsidy for the elderly | Exploits the elderly population | Fake subsidy registration forms | Around announcement and payout |
| Social psychology | Spread of financial disinformation | Exploits fear and distrust | Fake “emergency protection” instructions via links | Immediately after disinformation campaigns |
| IOT Type | Data Source | Example Baseline Method | Threshold Definition | Action Triggered |
| Look-alike domain registrations | Daily domain-registration feed | 90-day mean (μ) and standard deviation (σ) | IOT triggers when the daily count ≥ μ + 2σ | Registrar takedown; targeted monitoring |
| Suspicious CT issuances | Certificate Transparency logs | 14-day moving average | Surges ≥ 200% of the moving average | Verify issuer/requester; blocklist patterns |
| Reactivation of dormant domains | Passive DNS/WHOIS history | Median daily reactivation rate | Activation if the rate exceeds the 95th percentile | Manual review; takedown preparation |
| Dark Web advertisement of phishing kits | Underground forum monitoring | Frequency of posts per actor per 60-day window | Threshold ≥ 1 post when actor was inactive for >60 days | Extract artefacts into watchlists; sector alert |
| Brand-related social-media anomalies | Social-media API counts | z-score relative to 30-day baseline | z ≥ 3 flagged as anomalous | Awareness campaign; SOC surge monitoring |
| Date | Event Description | Masked Domain Format |
|---|---|---|
| 17 August 2024 | Public announcement of successful merger | — |
| 28 August 2024 | Registration of two domains with combined bank names | ●●●●●●●.com; ●●●●●●●●.com |
| 12 September 2024 | Registration of one suspicious domain | ●●●●●●.com |
| 13 September 2024 | Registration of one suspicious domain | ●●●●●●●●.com |
| 17 September 2024 | Registration of one suspicious domain | ●●●●●●●.com |
| 18 September 2024 | Registration of one suspicious domain | ●●●●●●●.net |
| 24 September 2024 | Registration of one suspicious domain | ●●●●●●●.info |
| 25 September 2024 | Registration of one suspicious domain | ●●●●●●●.com |
| 30 September 2024 | Registration of one suspicious domain | ●●●●●●●.info |
| 2 October 2024 | Registration of one suspicious domain | ●●●●●●●.net |
| 4 October 2024 | Registration of one suspicious domain | ●●●●●●.net |
| 13 October 2024 | Registration of one suspicious domain | ●●●●-●●●.com |
| 15 October 2024 | Registration of one suspicious domain | ●●●●-●●●.net |
| 17 October 2024 | Registration of one suspicious domain | ●●●●●●.info |
| 12 November 2024 | Registration of one suspicious domain | ●●●●●●●●.com |
| 14 November 2024 | Registration of two suspicious domains | ●●●●●●●.net; ●●●●-●●●●.com |
| 18 November 2024 | Registration of three suspicious domains | ●●●●-●●●●.net; ●●●●●●●●.com; ●●●●●●●●●●.info |
| 19 November 2024 | Registration of one suspicious domain | ●●●●●●●●●●.net |
| 21 November 2024 | Registration of one suspicious domain | ●●●●●●●●●●.com |
| Event | Operations |
|---|---|
| The customer informs the intelligence team about the upcoming bank merger | Intelligence team prepares foresight analysis, configures data sources, defines indicators (keywords, brand permutations) |
| The intelligence department & customer jointly develop an early-warning plan | Pre-emptive client awareness campaign launched two months before public media announcement |
| The media publishes official news of the bank merger | Adversary recognizes opportunity and starts preparing resources |
| Adversary registers brand-lookalike domains | Intelligence monitors new domain registrations with merger-related keywords |
| Adversary registers TLS certificates for fake domains | Intelligence monitors CT logs for anomalous certificates |
| Adversary redirects domains to benign websites to preserve reputation | Intelligence tracks suspicious redirects and cross-references with passive DNS |
| Adversary deploys phishing infrastructure | Intelligence performs periodic scanning of suspicious domains (favicon.ico, title, body) and initiates takedown procedures |
| Date | Event Description | Masked Domain Format |
|---|---|---|
| 16 February 2025 | Threat actor KrakenBite advertises a phishing kit containing replicas of Croatian bank services | — |
| 31 March 2025 | Registration of a suspicious domain | ●●●●●●.com |
| 31 March 2025 | Confirmed attack using domain ●●●●●●.com and KrakenBite kit | ●●●●●●.com |
| 18 May 2025 | Registration of a suspicious domain | ●●●●●●●.com |
| 19 May 2025 | Confirmed attack using domain ●●●●●●●.com and KrakenBite kit | ●●●●●●●.com |
| 4 June 2025 | Registration of a suspicious domain | ●●●●●.com |
| 5 June 2025 | Confirmed attack using domain ●●●●●.com and KrakenBite kit | ●●●●●.com |
| Event | Operations |
|---|---|
| Programmer (KrakenBite) advertises phishing kit on Dark Web forum | The intelligence department monitors underground markets and flags advertisements |
| Adversary (buyer) recognizes the opportunity and acquires the kit | Intelligence team assesses advertised templates and extracts IOT (targeted brands, domains, code patterns) |
| Intelligence department & customer design early-warning plan | Awareness campaigns for banking clients, warning of increased phishing attempts |
| Adversary registers brand-lookalike domains | Intelligence monitors new domain registrations and detects suspicious permutations |
| Adversary registers TLS certificates for malicious domains | Intelligence tracks anomalous certificate issuances in CT logs |
| Adversary deploys phishing infrastructure using kit templates | Intelligence performs periodic scans for favicon, title, and body patterns; initiates takedown procedures |
| Customer amplifies awareness messaging | Clients warned of fraudulent replicas; SOC monitors for increased phishing reports |
| Date | Event Description | Domain Format |
|---|---|---|
| 31 December 2018 | Initial registration of the domain was later reused for fraud | helpukraine.info |
| 11 February 2022 | Domain re-registered shortly before the invasion | helpukraine.info |
| 22 February 2022 | Registration of the domain prior to invasion | supportukraine.today |
| 24 February 2022 | Start of the Russian military invasion | — |
| 27 February 2022 | Registration of fraudulent donation domain | donate-ukraine.info |
| Event | Operations |
|---|---|
| Geopolitical tension rises—military build-up near the Ukrainian border | Intelligence monitors geopolitical signals and prepares IOT watchlists with relevant keywords (e.g., Ukraine, support, donate) |
| Adversary registers domains with humanitarian keywords | Intelligence monitors new domain registrations; CERT sets automated alerts for keyword combinations. |
| Adversary re-registers dormant domain (e.g., helpukraine.info) | Intelligence identifies anomalous reactivations and correlates with geopolitical context |
| Adversary deploys fraudulent donation websites | Intelligence scans websites for suspicious content; CERT prepares takedown requests |
| Adversary/social media accounts promote fraudulent domains | Intelligence monitors social media for domain distribution; customer warns clients/public |
| The customer and intelligence team coordinate awareness campaigns | Media releases official communication to inform the public about scams |
| CERT/government blocks malicious domains for institutions | Proactive disruption of fraudulent infrastructure at the national level |
| Case Study | Contextual Trigger | Type of Signal Observed | Lead-Time Gained | Defensive Opportunities Enabled |
|---|---|---|---|---|
| Bank X merger | Public announcement of merger and acquisition | Surge in brand-lookalike domain registrations; anomalous TLS certificates | ~14–21 days before phishing sites became active | Registrar takedowns, targeted monitoring of suspicious domains, and pre-emptive client awareness campaigns |
| KrakenBite phishing kit | Underground forum advertisement of a phishing kit | Dark Web sale notice; advertised HTML templates and email formats | ~6 weeks before the first confirmed phishing attack | Extraction of technical artefacts into IOT watchlists; tailored detection rules; advanced warning to banking sector clients |
| Wartime donation scams | Geopolitical escalation (Russian invasion of Ukraine) | Re-registration and creation of donation-themed domains; coordinated social media promotion | ~5–12 days around the onset of hostilities | CERT-level alerts; national media awareness campaigns; rapid takedowns of fraudulent donation sites |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.
Share and Cite
Kopal, R.; Alikavazović, B.; Morić, Z. From Context to Action: Establishing a Pre-Chain Phase Within the Cyber Kill Chain. J. Cybersecur. Priv. 2026, 6, 5. https://doi.org/10.3390/jcp6010005
Kopal R, Alikavazović B, Morić Z. From Context to Action: Establishing a Pre-Chain Phase Within the Cyber Kill Chain. Journal of Cybersecurity and Privacy. 2026; 6(1):5. https://doi.org/10.3390/jcp6010005
Chicago/Turabian StyleKopal, Robert, Bojan Alikavazović, and Zlatan Morić. 2026. "From Context to Action: Establishing a Pre-Chain Phase Within the Cyber Kill Chain" Journal of Cybersecurity and Privacy 6, no. 1: 5. https://doi.org/10.3390/jcp6010005
APA StyleKopal, R., Alikavazović, B., & Morić, Z. (2026). From Context to Action: Establishing a Pre-Chain Phase Within the Cyber Kill Chain. Journal of Cybersecurity and Privacy, 6(1), 5. https://doi.org/10.3390/jcp6010005






