FedPrIDS: Privacy-Preserving Federated Learning for Collaborative Network Intrusion Detection in IoT
Abstract
1. Introduction
- A privacy-preserving federated learning framework specifically designed for network intrusion detection that maintains data privacy while enabling collaborative learning (FedPrIDS).
- Implementation of adaptive differential privacy mechanisms with formal privacy guarantees (epsilon-delta privacy) tailored to network IDS data.
- Introduction of a novel hybrid feature selection approach that achieves speedup over un-tailored methods.
- A novel approach for increased detection effectiveness compared to single-organization NIDS detection.
2. Related Work
3. Methodology
3.1. Datasets
3.2. System Architecture
3.3. Global Model
| Algorithm 1 Global Model Initialization and Update |
Require: Number of features d, Hidden dimensions Ensure: Initialized global model 1: Initialize global model parameters randomly 2: 3: 4: 5:
6: for round to T do 7: Broadcast to all participants 8: Collect local updates from organizations 9: Secure aggregation() 10: end for 11: return
|
3.4. Local Model Architecture and Training
| Algorithm 2 Local Model Training with Privacy Protection |
Require:
Global model , Local dataset , Local epochs E, Learning rate , Privacy parameters Ensure:
Updated local model 1: 2:
Initialize optimizer with learning rate 3:
Compute noise scale: where 4:
for epoch to E do 5:
for each batch in do 6:
7: 8:
Compute gradients: 9:
Apply gradient clipping: 10:
Add DP noise: 11:
Update parameters: 12:
end for 13:
Update learning rate: 14: end for 15: return
|
- : privacy budget controlling the privacy–utility trade-off.
- : failure probability (typically ).
- C: gradient clipping bound ensuring bounded sensitivity.
| Parameter | Notation | Value | Description |
|---|---|---|---|
| Optimization Parameters | |||
| Learning Rate (initial) | 0.001 | Adam optimizer initial learning rate | |
| Learning Rate Decay | 0.95 | Exponential decay factor per epoch | |
| Batch Size | B | 128 | Training batch size |
| Local Epochs | E | 5 | Epochs per federated round |
| Weight Decay | 1 | L2 regularization coefficient | |
| Adam Beta Parameters | 0.9, 0.999 | Adam optimizer momentum parameters | |
| Neural Network Architecture | |||
| Dropout Rate (Layers 1–2) | 0.3 | Dropout probability for hidden layers | |
| Dropout Rate (Layer 3) | 0.2 | Dropout probability for output layer | |
| Hidden Layer Neurons | 256, 128, 64 | Neural network layer dimensions | |
| Input Features | d | Variable | Number of input features per dataset |
| Privacy and Security Parameters | |||
| Privacy Budget | 0.5–2.0 | Differential privacy epsilon parameter | |
| Privacy Failure Prob. | 1 | Differential privacy delta parameter | |
| DP Noise Scale | Variable | Differential privacy noise std deviation | |
| Gradient Clip Norm | C | 1.0 | Maximum gradient norm for clipping |
| Federated Learning Configuration | |||
| Organizations | N | 5 | Total participating organizations |
| Federated Rounds | T | 20 | Total federated learning rounds |
| Data Weight | Variable | Data size-based aggregation weight | |
| Performance Weight | Variable | Performance-based aggregation weight | |
| Weight Factors | 0.7, 0.3 | Data and performance weight coefficients | |
| Feature Selection Parameters | |||
| Variance Threshold | 0.01 | Minimum variance for feature selection | |
| Correlation Threshold | 0.9 | Maximum correlation for feature removal | |
| Target Features | k | Variable | Selected features per dataset |
3.5. Feature Extraction and Data Processing
| Algorithm 3 Optimized Hybrid Feature Selection |
Require:
Raw features , Target labels , Target features k Ensure:
Selected features 1: Step 1: Lightning Variance Filter 2: Compute feature variances: for 3: Remove low-variance features: 4: Step 2: Correlation Analysis 5: Compute correlation matrix: 6:
Remove highly correlated features: 7:
Step 3: Mutual Information Selection 8: Compute MI scores: for each feature 9: Select top-k features: 10:
11:
return
|
3.6. Model Aggregation
| Algorithm 4 Weighted Model Aggregation with Security Measures |
Require:
Local models , Data sizes , Performance losses Ensure: Updated global model 1:
Security Pre-processing: 2: Receive encrypted model updates using secure aggregation protocol 3: Decrypt model parameters with authenticated organizational keys 4: Outlier Detection: 5: for each model do 6: Compute median model: 7: Compute distance: 8: Compute MAD: 9: if then 10: Mark as outlier and exclude from aggregation 11: end if 12: end for 13: Compute Aggregation Weights: 14: ▹ Data contribution weight 15: ▹ Performance quality weight 16: ▹ Combined weight 17: ▹ Normalized final weight 18: Weighted Parameter Aggregation: 19: Initialize: 20: for each parameter layer p in neural network do 21: 22: end for 23: Model Integrity Verification: 24: Evaluate aggregated model on validation data: 25: Get previous round loss: 26: Set tolerance threshold: ▹ 5% degradation tolerance 27: if
then 28: Reject current aggregation 29: ▹ Revert to previous model 30: end if 31: return
|
4. Implementation
4.1. Fictitious Organizational Scenario
4.2. Implementation Details
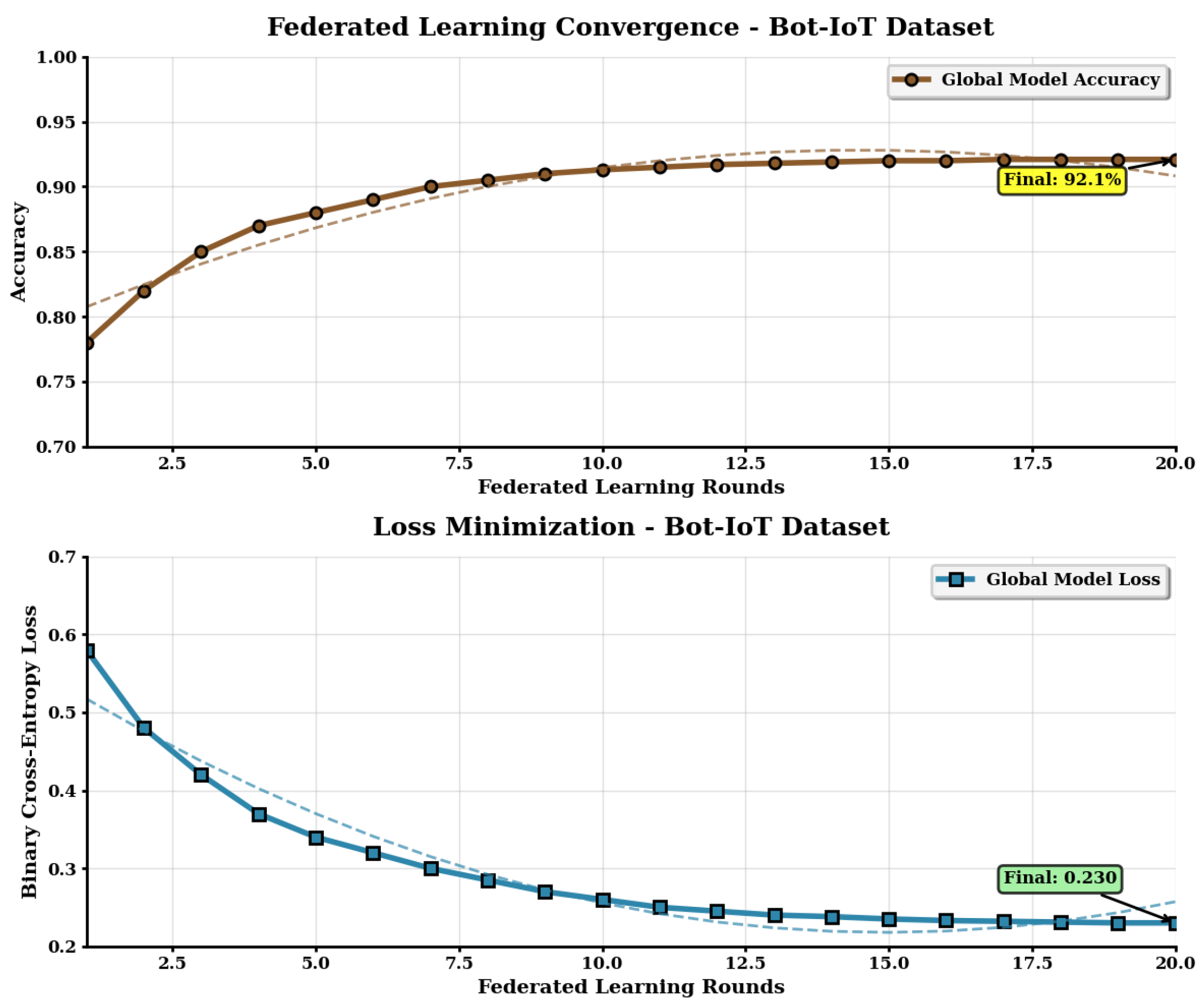
5. Results
5.1. Benefits and Costs
5.2. Organization-Specific Performance Analysis
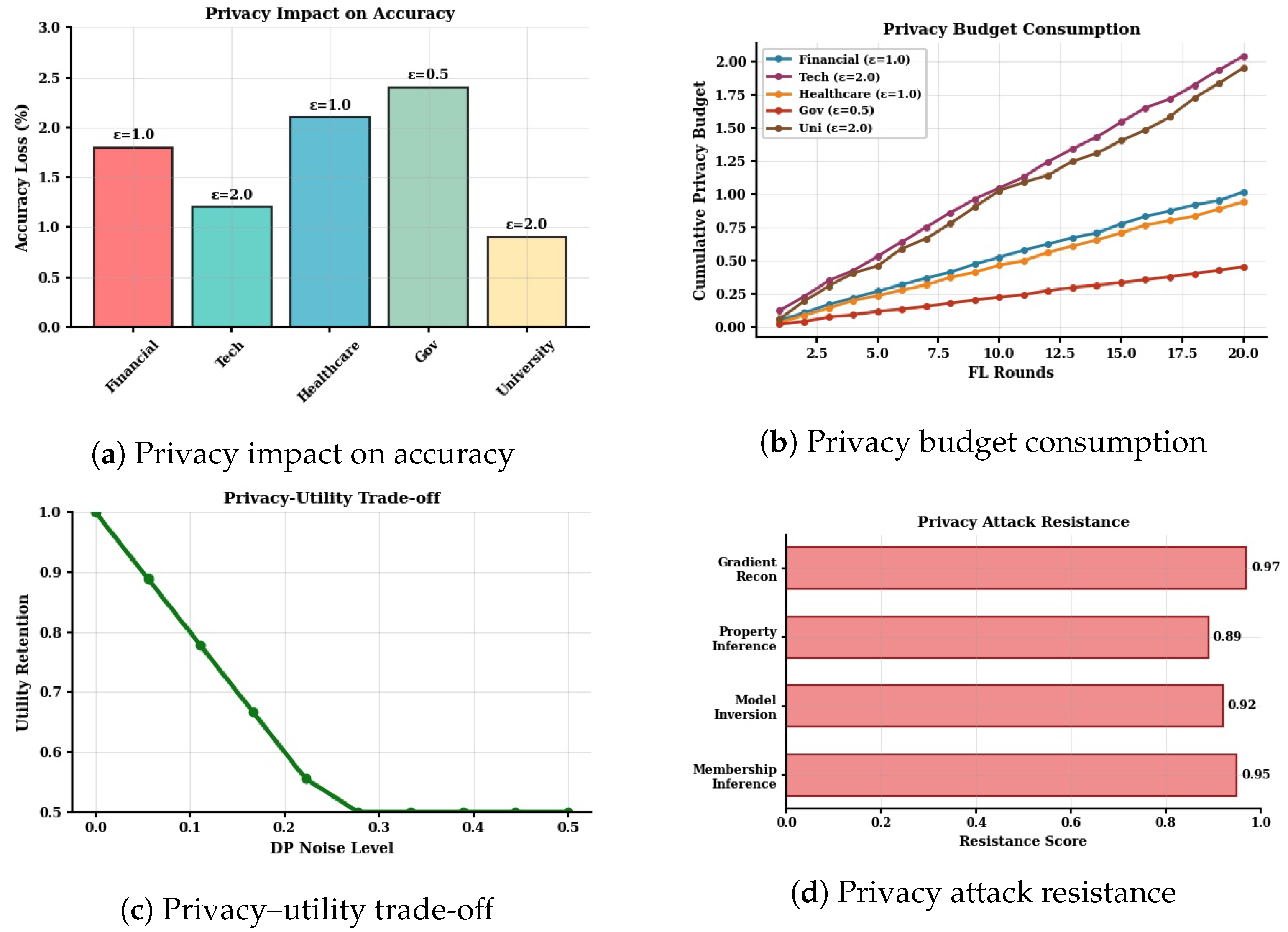
5.3. Privacy Preservation Analysis
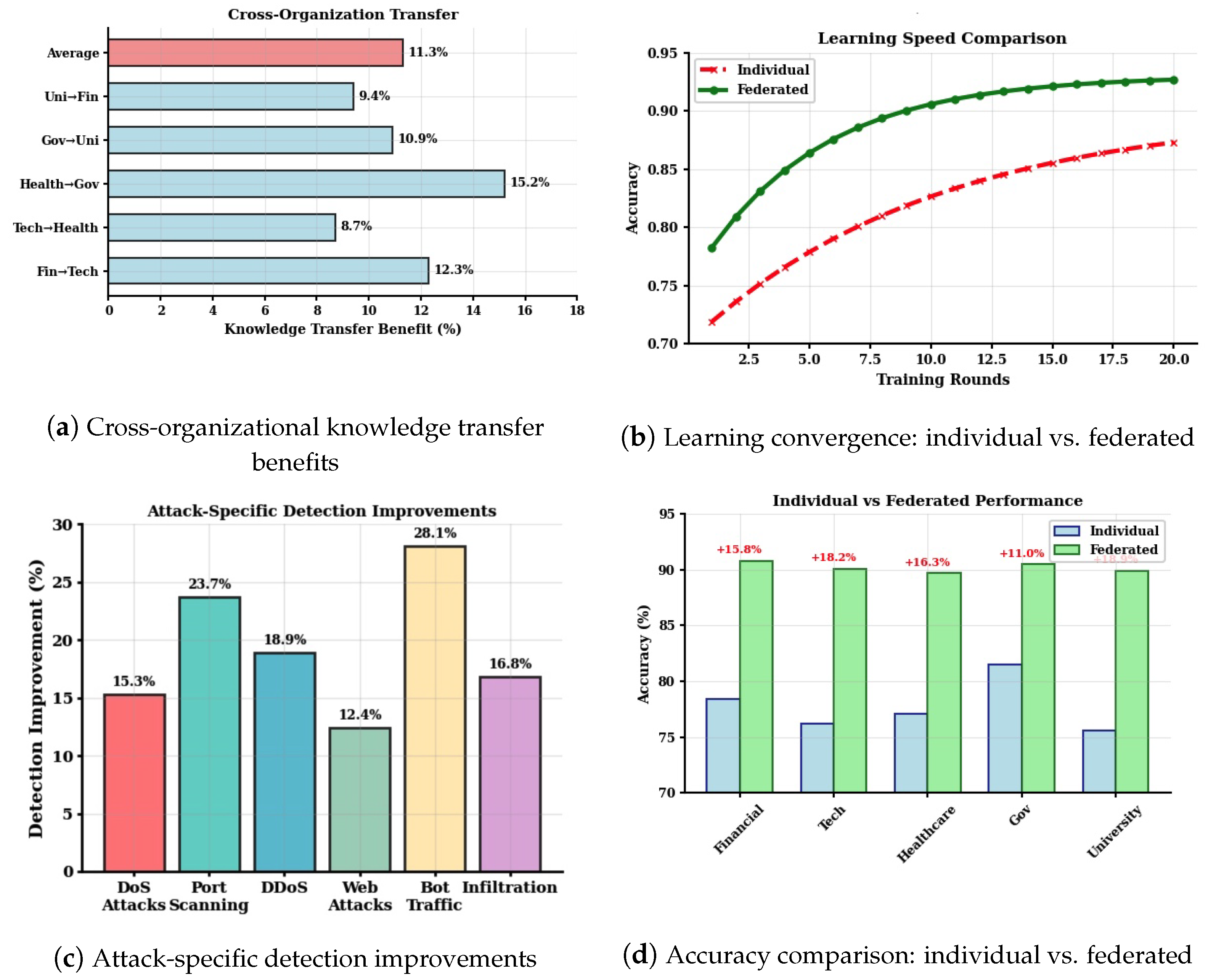
5.3.1. Knowledge Transfer and Attack-Specific Improvement
5.3.2. Federated Learning Benefits
6. Limitations
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- BitLyft Cybersecurity. Why Traditional Security Methods May No Longer Be Enough. Available online: https://www.bitlyft.com/resources/why-traditional-security-methods-may-no-longer-be-enough (accessed on 19 August 2025).
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Network Anomaly Detection: Methods, Systems and Tools. IEEE Commun. Surv. Tutor. 2014, 16, 303–336. [Google Scholar] [CrossRef]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; Arcas, B.A.y. Communication-Efficient Learning of Deep Networks from Decentralized Data. In Proceedings of the 20th International Conference on Artificial Intelligence and Statistics, Lauderdale, FL, USA, 20–22 April 2017; Volume 54, pp. 1273–1282. [Google Scholar]
- Li, T.; Sahu, A.K.; Talwalkar, A.; Smith, V. Federated Learning: Challenges, Methods, and Future Directions. IEEE Signal Process. Mag. 2020, 37, 50–60. [Google Scholar] [CrossRef]
- Janati Idrissi, M.; Alami, H.; El Mahdaouy, A.; El Mekki, A.; Oualil, S.; Yartaoui, Z.; Berrada, I. Fed-ANIDS: Federated Learning for Anomaly-based Network Intrusion Detection Systems. Expert Syst. Appl. 2023, 234, 121000. [Google Scholar] [CrossRef]
- Agrawal, S.; Sarkar, S.; Aouedi, O.; Yenduri, G.; Piamrat, K.; Alazab, M.; Bhattacharya, S.; Maddikunta, P.K.R.; Gadekallu, T.R. Federated Learning for Intrusion Detection System: Concepts, Challenges and Future Directions. Comput. Commun. 2022, 195, 346–361. [Google Scholar] [CrossRef]
- Zhao, Y.; Chen, J.; Wu, D.; Teng, J.; Yu, S. Multi-Task Network Anomaly Detection using Federated Learning. In Proceedings of the 10th International Symposium on Information and Communication Technology, Hanoi, Vietnam, 4–6 December 2019; pp. 273–279. [Google Scholar] [CrossRef]
- Nguyen, T.D.; Marchal, S.; Miettinen, M.; Fereidooni, H.; Asokan, N.; Sadeghi, A.R. DÏoT: A Federated Self-learning Anomaly Detection System for IoT. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–10 July 2019; pp. 756–767. [Google Scholar] [CrossRef]
- Rahman, S.A.; Tout, H.; Talhi, C.; Mourad, A. Internet of Things Intrusion Detection: Centralized, On-Device, or Federated Learning? IEEE Netw. 2020, 34, 310–317. [Google Scholar] [CrossRef]
- Amiri-Zarandi, M.; Dara, R.A.; Lin, X. SIDS: A Federated Learning Approach for Intrusion Detection in IoT Using Social Internet of Things. Comput. Netw. 2023, 228, 110005. [Google Scholar] [CrossRef]
- Chethun. CIC-IDS-2017 Network Intrusion Dataset. 2023. Available online: https://www.kaggle.com/datasets/chethuhn/network-intrusion-dataset (accessed on 7 August 2025).
- Wells, D. UNSW-NB15 Dataset. 2023. Available online: https://www.kaggle.com/datasets/mrwellsdavid/unsw-nb15 (accessed on 21 August 2025).
- Venkateswaran, V. Bot-IoT Dataset. 2023. Available online: https://www.kaggle.com/datasets/vigneshvenkateswaran/bot-iot (accessed on 21 August 2025).
- Dwork, C.; Roth, A. The Algorithmic Foundations of Differential Privacy. Found. Trends Theor. Comput. Sci. 2014, 9, 211–407. [Google Scholar] [CrossRef]
- Yang, Q.; Liu, Y.; Chen, T.; Tong, Y. Federated Machine Learning: Concept and Applications. ACM Trans. Intell. Syst. Technol. 2019, 10, 1–19. [Google Scholar] [CrossRef]
- Al-Qatf, M.; Lasheng, Y.; Al-Habib, M.; Al-Sabahi, K. Deep Learning Approach Combining Sparse Autoencoder with SVM for Network Intrusion Detection. IEEE Access 2018, 6, 52843–52856. [Google Scholar] [CrossRef]
- Farahnakian, F.; Heikkonen, J. A Deep Auto-Encoder Based Approach for Intrusion Detection System. In Proceedings of the 2018 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon, Republic of Korea, 11–14 February 2018; pp. 178–183. [Google Scholar] [CrossRef]
- Zavrak, S.; İskefiyeli, M. Anomaly-Based Intrusion Detection From Network Flow Features Using Variational Autoencoder. IEEE Access 2020, 8, 108346–108358. [Google Scholar] [CrossRef]
- Tharewal, S.; Ashfaque, M.W.; Banu, S.S.; Uma, P.; Hassen, S.M.; Shabaz, M. Intrusion Detection System for Industrial Internet of Things Based on Deep Reinforcement Learning. Wirel. Commun. Mob. Comput. 2022, 2022, 9023719. [Google Scholar] [CrossRef]
- Alhajjar, E.; Maxwell, P.; Bastian, N. Adversarial Machine Learning in Network Intrusion Detection Systems. Expert Syst. Appl. 2021, 186, 115782. [Google Scholar] [CrossRef]
- Bonawitz, K.; Ivanov, V.; Kreuter, B.; Marcedone, A.; McMahan, H.B.; Patel, S.; Ramage, D.; Segal, A.; Seth, K. Practical Secure Aggregation for Privacy-Preserving Machine Learning. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1175–1191. [Google Scholar] [CrossRef]
- Liu, Y.; Kang, Y.; Zou, T.; Pu, Y.; He, Y.; Ye, X. Vertical Federated Learning: Concepts, Advances, and Challenges. IEEE Trans. Knowl. Data Eng. 2024, 36, 3615–3634. [Google Scholar] [CrossRef]
- Liu, Y.; Kang, Y.; Xing, C.; Chen, T.; Yang, Q. A Secure Federated Transfer Learning Framework. IEEE Intell. Syst. 2020, 35, 70–82. [Google Scholar] [CrossRef]
- Goodfellow, I.; Bengio, Y.; Courville, A. Deep Learning; MIT Press: Cambridge, MA, USA, 2016. [Google Scholar]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep Learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef] [PubMed]
- Srivastava, N.; Hinton, G.; Krizhevsky, A.; Sutskever, I.; Salakhutdinov, R. Dropout: A Simple Way to Prevent Neural Networks from Overfitting. J. Mach. Learn. Res. 2014, 15, 1929–1958. [Google Scholar]
- Kingma, D.P.; Ba, J. Adam: A Method for Stochastic Optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar]
- Snort Project. Snort—Network Intrusion Detection Prevention System. Open Source Intrusion Prevention System. Available online: https://www.snort.org/ (accessed on 21 August 2025).
- Open Information Security Foundation. Suricata: Open Source Threat Detection Engine. Available online: https://suricata.io/ (accessed on 21 August 2025).
- Zeek Project. Zeek Network Security Monitor. Available online: https://zeek.org/ (accessed on 21 August 2025).
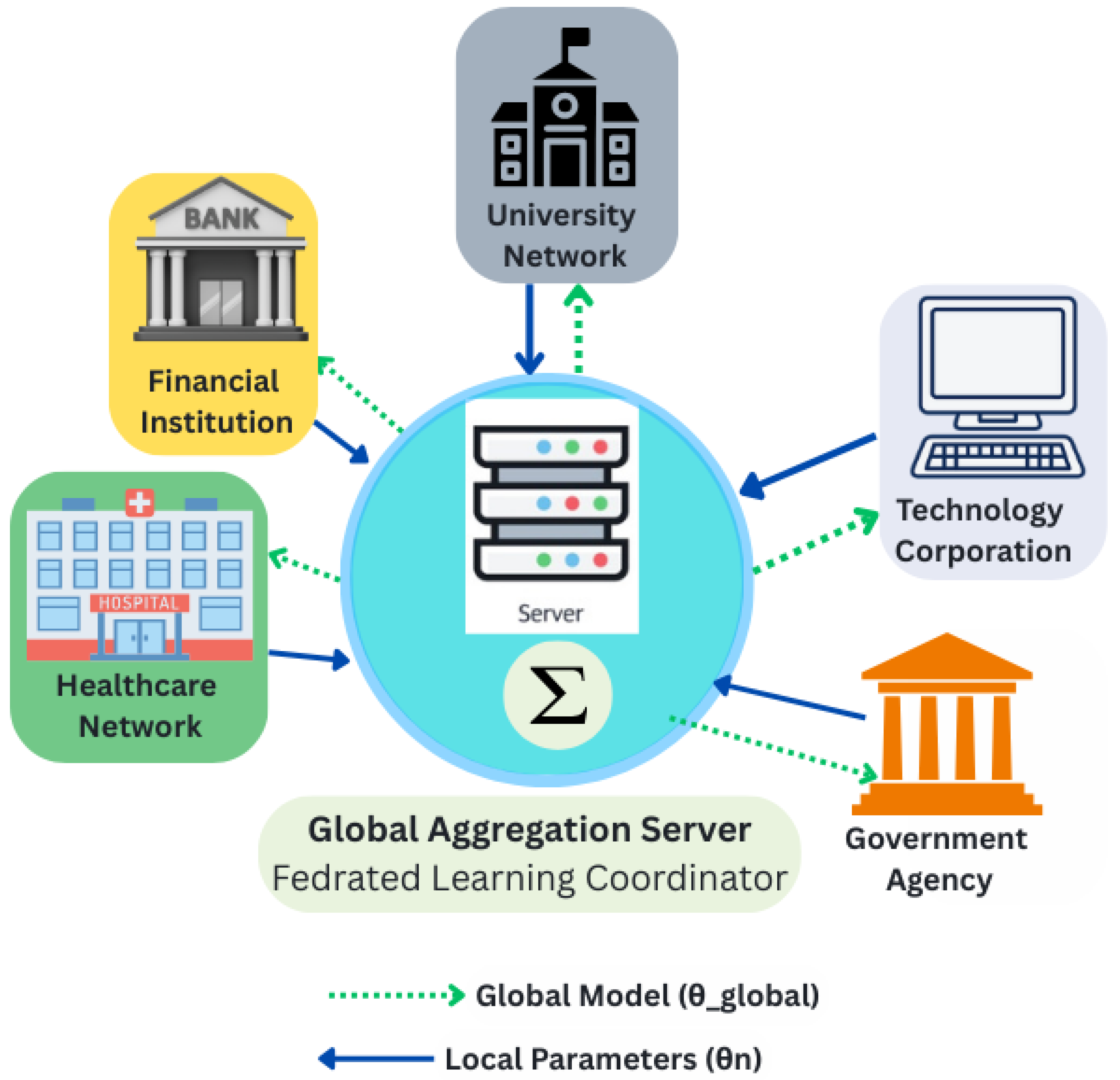
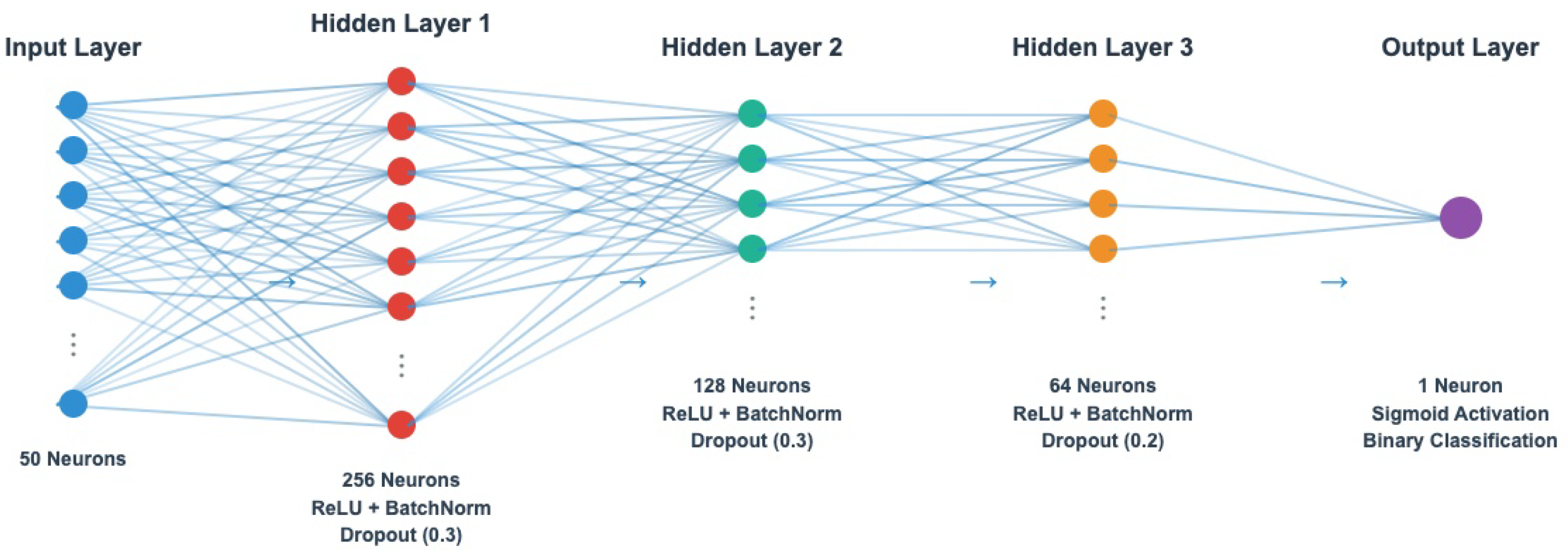
| Approach | Privacy Mechanism | Feature Selection | Multi-Dataset Eval. | Org. Types | Real-Time Capable |
|---|---|---|---|---|---|
| Janati et al. [5] | Basic | None | Single | Generic | No |
| Zhao et al. [7] | None | Static | Single | Generic | No |
| Nguyen et al. [8] | Encryption | IoT-specific | Single | IoT only | Limited |
| Amiri et al. [10] | Social-trust | None | Single | IoT only | No |
| FedPrIDS (Ours) | Differential Privacy (-DP) | Hybrid Adaptive | Three datasets | Diverse | Yes |
| Metric | CIC-IDS-2017 | UNSW-NB15 | Bot-IoT |
|---|---|---|---|
| Original Features (78/42/115) | |||
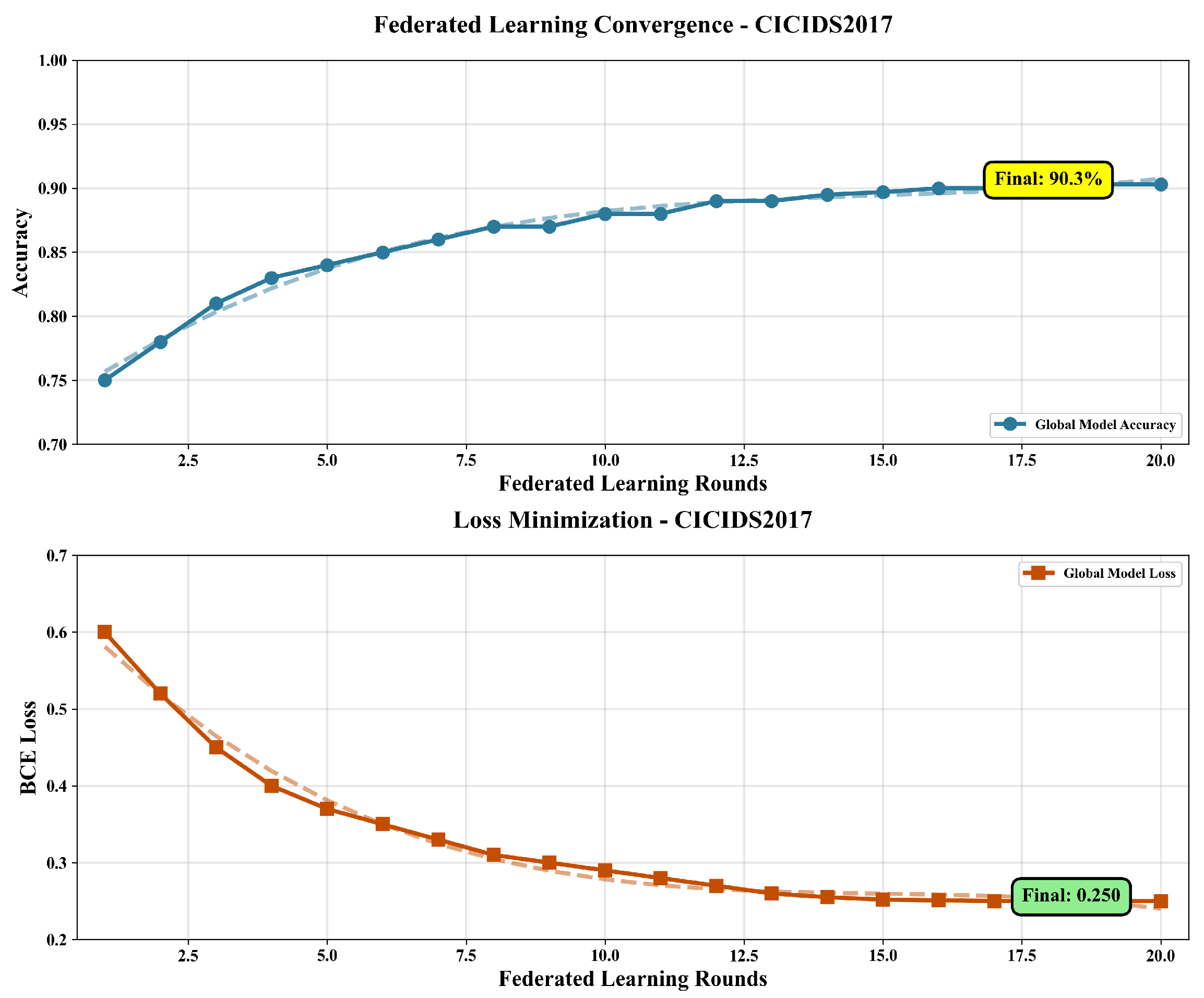
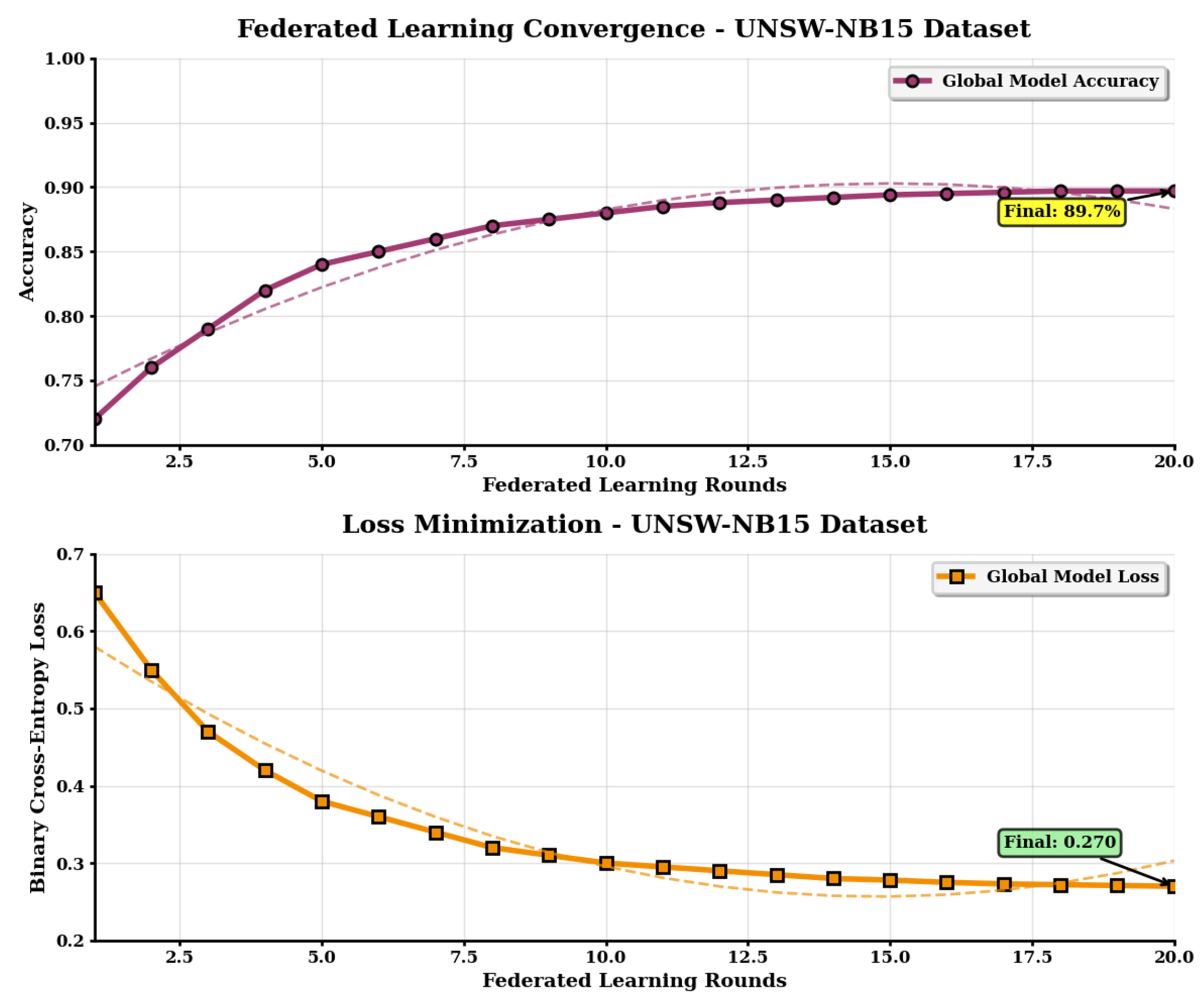
| Accuracy | 90.45% | 89.82% | 92.23% |
| Precision | 89.78% | 88.56% | 91.68% |
| Recall | 57.12% | 61.45% | 62.51% |
| F1-Score | 69.82% | 71.38% | 73.58% |
| Preprocessing Time (s) | 22.34 | 14.67 | 45.89 |
| Selected Features (50/30/80) | |||
| Accuracy | 90.30% | 89.70% | 92.10% |
| Precision | 89.64% | 88.43% | 91.56% |
| Recall | 56.86% | 61.24% | 62.34% |
| F1-Score | 69.58% | 71.20% | 73.40% |
| Preprocessing Time (s) | 13.98 | 8.42 | 28.67 |
| Improvement with Feature Selection | |||
| Accuracy Change | −0.15% | −0.12% | −0.13% |
| Time Reduction | 37.4% | 42.6% | 37.5% |
| Org. Type | Data | Priv. | Federated Acc. (%) | Individual Acc. (%) | Priv. | Collab. | Net | ||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Qual. | Level | CIC | UNS | Bot | CIC | UNS | Bot | Loss | Gain | Benefit | |
| Financial | 95% | 90.8 | 89.4 | 92.3 | 78.4 | 77.0 | 79.9 | 1.8% | 12.4% | +10.6% | |
| Technology | 90% | 90.1 | 89.9 | 92.0 | 75.4 | 75.2 | 77.3 | 1.2% | 14.7% | +13.5% | |
| Healthcare | 85% | 89.7 | 89.1 | 91.8 | 77.9 | 77.3 | 80.0 | 2.1% | 11.8% | +9.7% | |
| Government | 88% | 90.5 | 89.6 | 92.5 | 79.6 | 78.7 | 81.6 | 2.4% | 10.9% | +8.5% | |
| University | 80% | 89.9 | 90.2 | 91.9 | 74.6 | 74.9 | 77.5 | 0.9% | 15.3% | +14.4% | |
| Average | – | – | 90.2 | 89.6 | 92.1 | 77.2 | 76.6 | 79.3 | 1.7% | 13.0% | +11.3% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2026 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license.
Share and Cite
Mankotia, S.; Conte de Leon, D.; Rimal, B.P. FedPrIDS: Privacy-Preserving Federated Learning for Collaborative Network Intrusion Detection in IoT. J. Cybersecur. Priv. 2026, 6, 10. https://doi.org/10.3390/jcp6010010
Mankotia S, Conte de Leon D, Rimal BP. FedPrIDS: Privacy-Preserving Federated Learning for Collaborative Network Intrusion Detection in IoT. Journal of Cybersecurity and Privacy. 2026; 6(1):10. https://doi.org/10.3390/jcp6010010
Chicago/Turabian StyleMankotia, Sameer, Daniel Conte de Leon, and Bhaskar P. Rimal. 2026. "FedPrIDS: Privacy-Preserving Federated Learning for Collaborative Network Intrusion Detection in IoT" Journal of Cybersecurity and Privacy 6, no. 1: 10. https://doi.org/10.3390/jcp6010010
APA StyleMankotia, S., Conte de Leon, D., & Rimal, B. P. (2026). FedPrIDS: Privacy-Preserving Federated Learning for Collaborative Network Intrusion Detection in IoT. Journal of Cybersecurity and Privacy, 6(1), 10. https://doi.org/10.3390/jcp6010010






