1. Introduction
Chaotic systems are dynamic systems that exhibit chaotic behaviour. They have been extensively studied and have been used to solve real-world problems including numerical weather prediction [
1] and market analysis [
2]. Due to their properties such as ergodicity, sensitivity to initial conditions, and random-like behaviour, researchers have started looking into designing cryptosystems based on chaos. Parallels are often drawn between chaos and cryptography, whereby certain chaotic properties can be mapped directly to cryptographic requirements, as noted by Kocarev back in 2001 [
3]. However, Kocarev also pointed out numerous problems with chaos-based cryptographic algorithms, noting that using real numbers makes practical realization and circuit implementation difficult. He also observed that chaos-based methods were not analysed using techniques developed within the field of cryptography and that many designs are ad hoc in nature.
Despite years of research, the fundamental issues in chaos-based encryption remain unresolved, as noted by multiple researchers [
3,
4,
5,
6]. Most existing work continues to focus predominantly on image encryption [
7,
8,
9,
10], with authors often claiming that conventional symmetric-key algorithms are unsuitable due to the high correlation between image pixels or due to their inefficiency in handling bulk data [
11,
12,
13]. However, such claims are not only inconsistent with real-world practice—where block ciphers are routinely and effectively used to secure various types of media—but have also been directly challenged in prior studies [
14]. This highlights a persistent misconception in the field and underscores the need for chaos-based encryption schemes that are grounded in sound cryptographic principles and that are rigorously evaluated.
Although chaos theory could, theoretically, be used to build practical cryptosystems, the current research direction still focuses on
security through obscurity, whereby the cryptographic algorithms are very complex and rely on high-dimensional chaotic maps. Both design complexity and reliance on real numbers prevent the use of cryptanalytic tools to evaluate the security margin of these algorithms. We have reviewed recently proposed ciphers in
Section 3 to verify that these problems are still prevalent. As a result, the majority of chaos-based algorithms are only of academic interest and see no real-world applications. Although some may question the need (or lack thereof) for chaos-based encryption algorithms, the study of chaos-based cryptosystems could lead to new findings that could supplement existing tools in conventional cryptography.
Contributions: In this paper, we address this problem by taking a contrasting approach to that of current chaos-based cryptography research and answer the following question:
How can we design a minimalistic chaos-based cryptosystem that still fulfils all the same requirements as the current ”state-of-the-art”? The main goal is to move away from
security through obscurity and align the design of a chaos-based cryptosystem with the well-studied security notions in conventional cryptography. This will not only provide more confidence in the design but also facilitate third-party cryptanalysis efforts to provide accurate security bounds. As such, we study the use of well-known design paradigms such as the substitution–permutation network (SPN) and Feistel constructions in the context of image encryption. We begin by taking a look at some recently proposed chaos-based image ciphers to see if they have overcome at least some of the key problems highlighted in the past [
6,
15]. Then, we propose a simple chaos-based image cipher based on SPN and analyze the minimum number of rounds required to achieve a similar statistical security as the current state of the art in chaos-based cryptography. We also study the impact of changing its underlying chaotic map to other more complex ones.
Our extensive experiments show that the combination of a simple SPN configuration and a simple chaotic map is sufficient to provide similar performances to those demonstrated in existing work. These experiments are not intended to demonstrate superiority over existing schemes, but rather to show that a minimalistic and transparent design can meet widely accepted statistical security benchmarks, as used in prior chaos-based cryptography work. Next, we introduce a new chaos-based block cipher based on the Feistel construction. Note that the design goal of this block cipher is not acting as a replacement for mainstream block ciphers, such as AES, but to show that it is possible to use chaotic maps as a nonlinear component in a way that facilitates cryptanalytic efforts. We show that we can estimate the security margin of the proposed cipher against differential cryptanalysis using a standard approach of counting the number of active nonlinear components and obtaining the upper-bound differential probability of the chaotic map. For comparison with existing chaos-based ciphers (which are almost exclusively image ciphers), we used the proposed block cipher in the CBC mode of operation to encrypt images. Despite having a simpler design, the proposed cipher has equivalent statistical properties to the current state of the art. The main contributions of this paper are summarized below.
An in-depth analysis of minimalistic SPN configurations for image encryption based on chaos-based cryptography.
Empirical proof that changing the underlying chaotic map has minimal impact on statistical results, as long as the map is operating within its chaotic region.
A new chaos-based block cipher based on the well-understood Feistel design paradigm with a provable upper bound security against differential cryptanalysis.
Empirical proof that a simple block cipher design can have similar statistical properties as the current state of the art in chaos-based encryption.
The remainder of the paper is organized as follows:
Section 2 provides preliminary information related to the proposed work, including the various chaotic maps used and metrics commonly used to evaluate chaos-based ciphers.
Section 3 delves into the analysis of recent chaos-based image ciphers.
Section 4 investigates minimalistic SPN configurations for image encryption, while
Section 5 introduces the proposed chaos-based block cipher and its use in image encryption. The experimental results are described in
Section 6; the paper is concluded in
Section 7.
3. Analysis of Recent Chaos-Based Image Ciphers
In this section, we focus on practical implementation issues of 14 recently proposed chaos-based cryptosystems that rely on digitized chaotic maps; some of these issues have already been discussed in
Section 1. Specifically, our analysis is limited to newly proposed symmetric-key encryption algorithms that employ chaotic maps as their primary source of entropy, including image ciphers. We thoroughly investigated whether the 14 analyzed chaos-based cryptosystems have made progress in resolving the implementation problems listed below, some of which were previously identified in [
6].
Table 1 presents a comprehensive analysis of 14 recent chaos-based cryptographic algorithms, highlighting significant implementation challenges. Firstly, the use of high-dimensional (HD) maps poses a significant challenge due to their complexity and heavy resource demand. Using a combination of simpler chaotic maps (CCMs) rather than higher-dimensional maps has similar drawbacks. Higher computational cost (HCC) is related to the computational efficiency of the cryptographic algorithms themselves due to their inherent design. The design complexity (DC) of these algorithms also makes it difficult to perform third-party cryptanalysis in order to verify their security margins. As such, designers have no other option but to resort to statistical security testing. Reliance on statistical-based security tests (ROST) alone does not guarantee that a cipher is resistant to cryptanalytic attacks.
Unfortunately, it appears that most of these issues remain unaddressed, evidenced by the successful publication of new cryptosystems with these problems in reputable journals. Our findings are aligned with previous research highlighting the fundamental challenges of chaos-based cryptography that hinder its real-world applicability and reputation in the cryptographic community. New designs still seem to promote security through obscurity, as outlined in
Section 1. Consequently, many of these algorithms remain only of academic interest rather than being used in real-world applications.
In our paper, we will address all of the aforementioned issues. We show that there is no need for high-dimensional or complex combinations of chaotic maps in cipher design by focusing just on simple, well-understood chaotic maps covered in
Section 2.1. By using basic chaotic maps and well-studied yet simple design paradigms, we demonstrate that it is possible to design ciphers with strong security properties that can be analyzed using classical cryptanalysis techniques such as differential cryptanalysis.
4. Analysis of Optimal SPN Configurations for Image Encryption
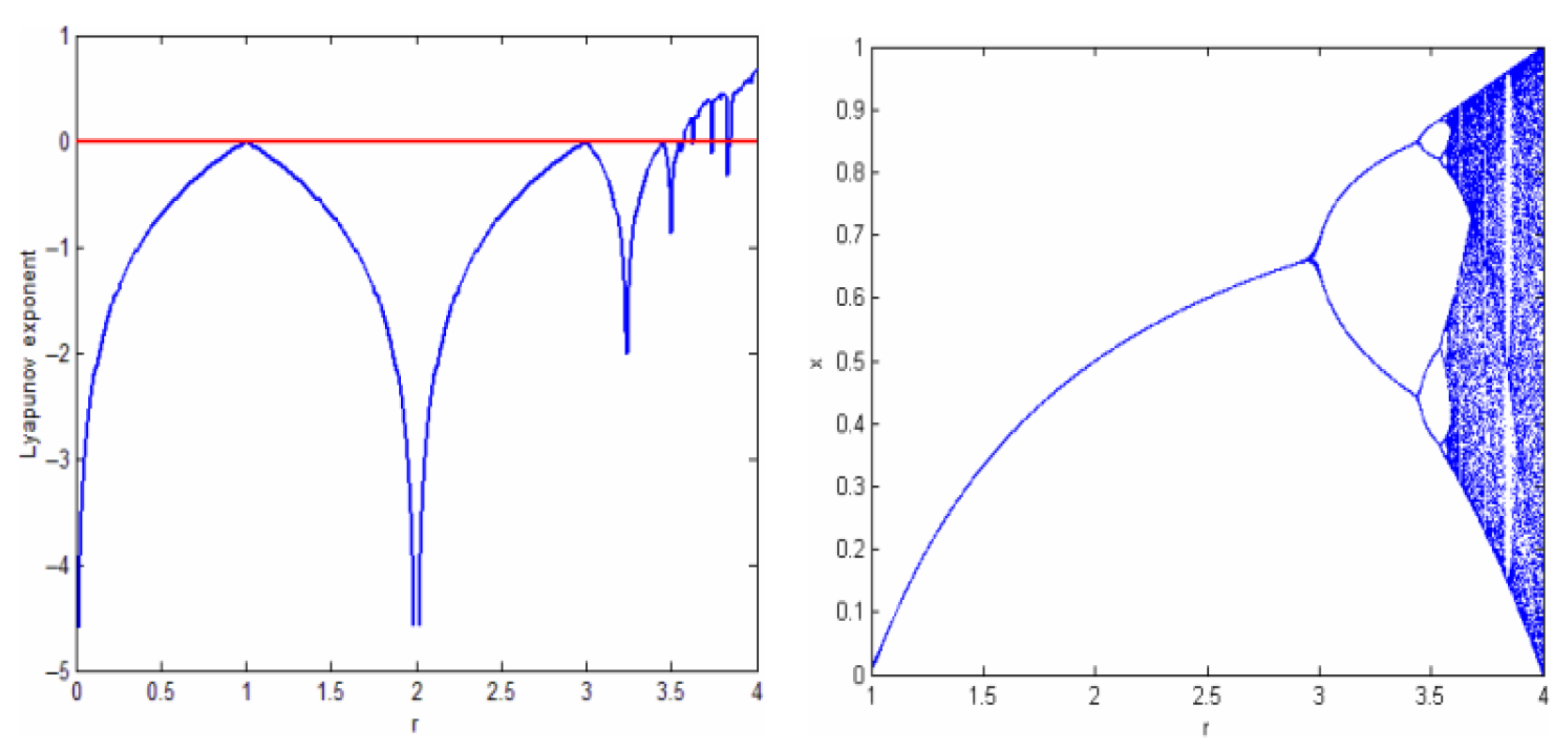
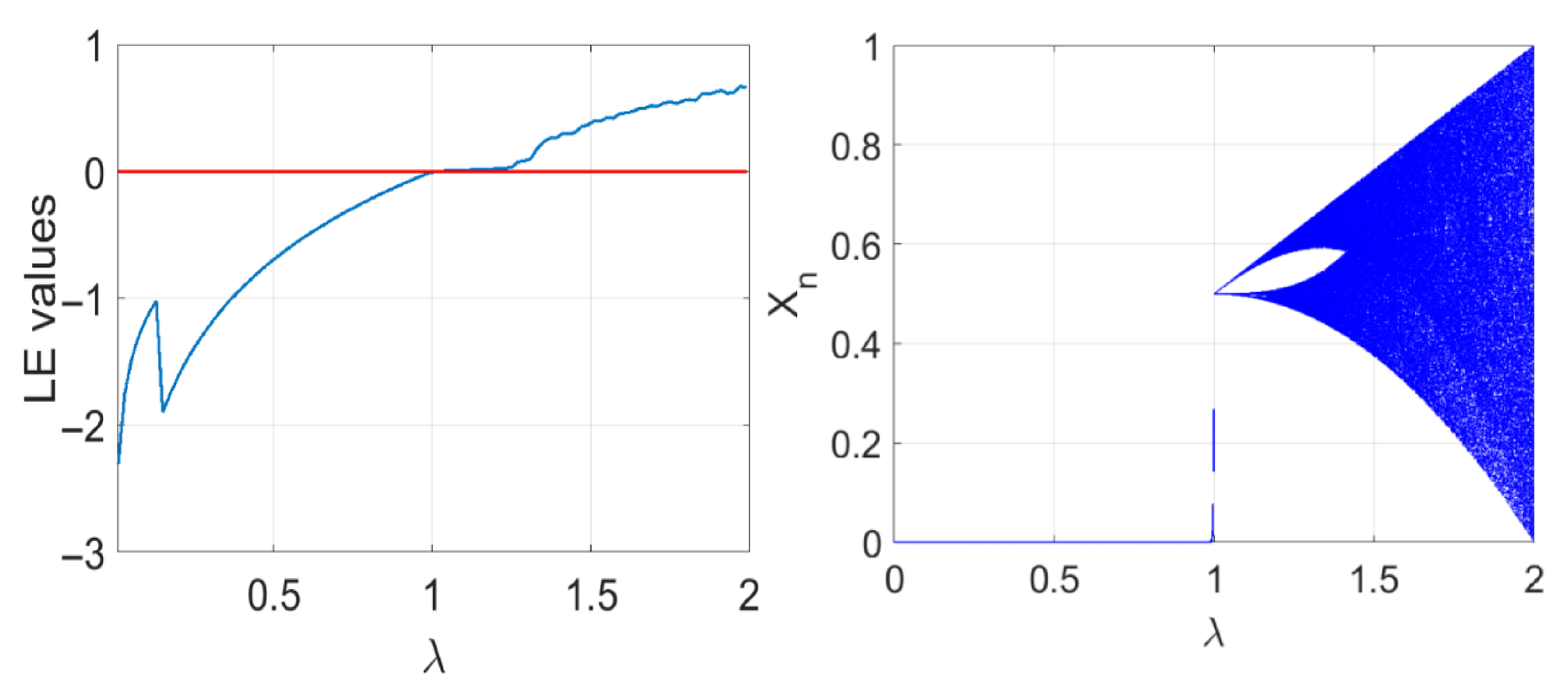
In this section, our goal is to identify a minimalistic configuration for image encryption based on the SPN. We want to show that to achieve the statistical properties that most chaos-based image ciphers are trying to attain, a complex design or the use of a high-dimensional chaotic map is not necessary. Therefore, all experiments were performed on simple one-dimensional maps. The parameters were chosen from standard values that are frequently used in the literature to ensure chaotic behaviour and to make the experiment reproducible and comparable with existing studies. Specifically, we used parameter for the logistic map, for the tent map, , and for the Henon map, as well as for the Piecewise linear map. These values were chosen to maintain high sensitivity to initial conditions while keeping the system simple and reproducible. To ensure consistency with the literature on chaos-based cryptography, we denote the substitution of each pixel as the modification of each pixel value based on a random sequence generated using a chaotic map and not the use of a substitution box. Permutation, on the other hand, refers to the shuffling of pixel positions to remove correlation between neighboring pixels.
4.1. SPN Cipher Design
The image encryption is designed based on the SPN, which operates on a plainimage with 256 × 256 pixels and also returns a cipherimage block of the same size. In this SPN, the encryption phase consists of three processes, which are pixel substitution, pixel permutation, and diffusion. Pixel substitution obscures the pixel values using a random sequence generated using a chaotic map to achieve confusion, pixel permutation shuffles pixel positions to remove correlation between the neighbouring pixels, and pixel diffusion modifies pixel values based on other pixel values in the plainimage. Thus, all pixels of the plainimage will be diffused throughout the resulting cipherimage. The following steps describe the encryption algorithm (decryption algorithm is just the inverse of the steps):
Step 1: Read plainimage (original image); is the size of the image P, where m = 256 and n = 256.
Step 2: Input secret key and parameter r into the algorithm and iterate the chaotic map N times and obtain the key array; the size of the array is N.
Step 3 (Substitution): Encrypt each element of the plainimage using the key array generated by the chaotic map (i.e., modifying the original pixels with the key array obtained from Step 2 using XOR operation).
Step 4 (Substitution): Modify each pixel in the plainimage P using values from all other adjacent pixels in the horizontal and vertical directions. Modification is performed using the XOR operation; for pixels at the edge of the plainimage, we take pixels from the opposite edge as the adjacent pixel (pixel row and column numbers wrap around).
Step 5 (Permutation): Shuffle the pixel positions based on the output of the logistic map. The chaotic map is used to determine row and column numbers within the plainimage. The current pixel at position will be swapped with a pixel , where and are obtained by iterating the chaotic map. The and values are obtained from the chaotic map’s state, X, after each iteration by converting X into a number between 1 and the maximum number of rows or columns; in our case, this value is 256. This is calculated using a ceiling function and simple linear scaling, .
Step 6: The resulting image obtained from Step 5 is the cipherimage .
4.2. Ranking Method for SPN Configurations
In the ranking process, the performance of various substitution–permutation (SP) configurations is evaluated using widely accepted statistical security metrics. To quantify and compare the performance of each configuration, the results for each metric were linearly scaled between 0 and 100, where a score of 100 corresponds to the ideal outcome for that metric (e.g., maximum entropy, minimum correlation, and maximum NPCR and UACI values). These scaled scores were then aggregated to produce an overall security score for each configuration. This approach provides a transparent and reproducible approach for selecting optimal SPN configurations. The scaling for each of the metrics is described as follows:
Irregular Deviation (ID) Score: For a 256 × 256 image, the worst-case scenario occurs when all the pixels have a value of zero (0), except for one instance where the value is 255. As the sum of (1:256) equals 65,536, it is possible to calculate the worst ID result as 255 × 256 + 65,280 = 130,560. On the other hand, the ideal result for ID is 0 (no difference between the cipher text distribution and a uniform distribution).
Maximum Deviation (MD) Score: The maximum value for a 256 × 256-pixel image is when the plain text has pixels with gray levels of 0 and the cipher text has pixels with gray levels of 255. Since the summation of (1:256) = 65,536, the highest MD is 65,536 × 3 = 196,608.
Deviation from Uniform Histogram (DUH) Score: The cipherimage achieves the best histogram deviation when its pixels show a high probability of closely matching pixel values from a uniform histogram. The DUH values range between 0 and 1, where 0 implies perfect uniform distribution and 1 represents a complete departure from uniformity. Hence, the best scenario is when the value is not equal to 1.
Entropy Score: An 8-bit gray level image attains an optimal entropy value of 8 [
39], signifying a well-balanced distribution of pixel values that reflects the information within the image.
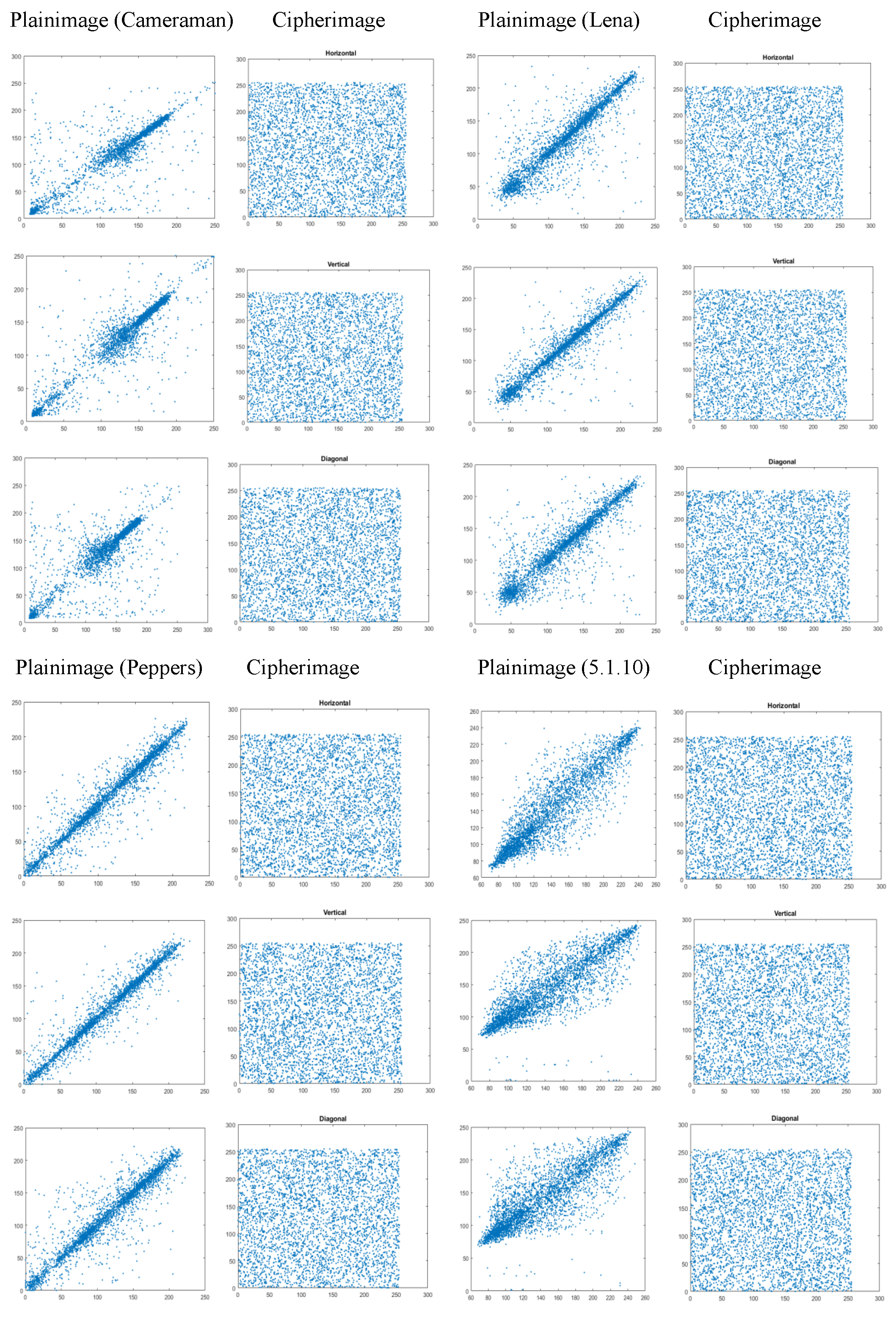
Correlation Coefficient (CC) Score: When CC values approach 0, this indicates a minimal correlation between neighbouring pixels in an encrypted image, while CC values close to 1 or −1 signify a strong pixel correlation [
19]. Since we consider three pixel directions (horizontal, vertical, and diagonal), it is possible to calculate the total CC score by summing the results from each direction, as follows:
where,
represent correlation coefficient horizontal,
denotes correlation coefficient vertical, and
represents correlation coefficient diagonal.
Number of Pixel Change Rate (NPCR) Score: In the ideal scenario, the value of NPCR is considered optimal when it is greater than or equal to the average value (99.5693%) [
40], indicating a high sensitivity to small changes in the plainimage.
Unified Average Change Intensity (UACI) Score: Ideally, the UACI value should be close to 33.46355% [
40]. As such, a max score of 100 should be given for results close to the aforementioned value.
4.3. Experimental Results Comparing SP Configurations
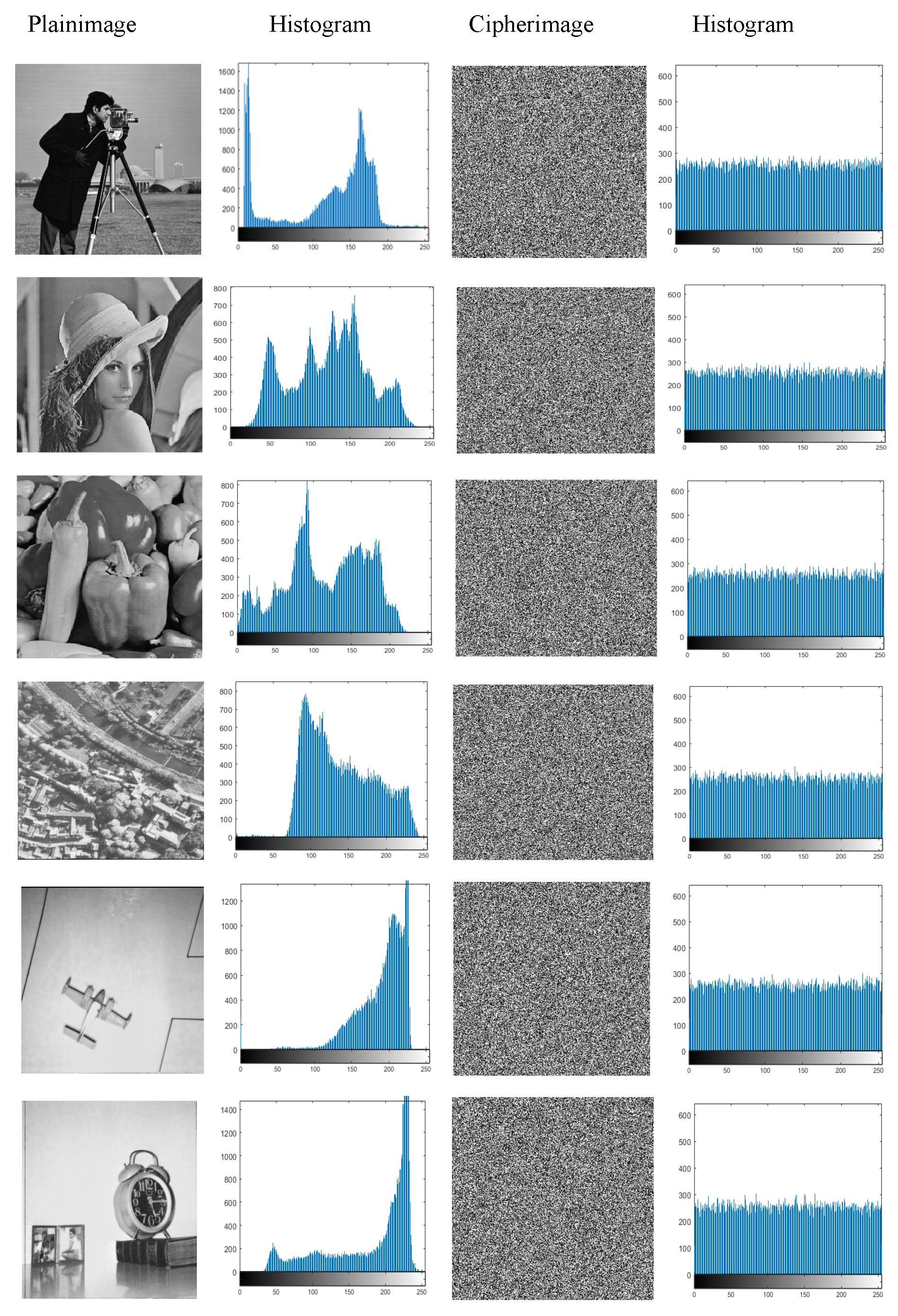
Experiments were performed using MATLAB 2021a on a PC with a 64-bit operating system, Intel Core i-5 CPU (2.60 GHz), and 8 GB memory. Standard test plainimages such as the Cameraman, Lena, and Pepper images of 256 × 256 pixels in size were used in our experiments as they are also commonly used in the field. The optimum configuration substitution–permutation (SP) combinations in this experiment are listed in
Table 2, while the average results of three images using four different chaotic maps are presented in
Table 3,
Table 4,
Table 5 and
Table 6.
4.4. Discussion
We have provided an extensive analysis of the performance of the substitution–permutation (SP) ciphers, using various statistical methods and comparing them with several recently proposed schemes, as shown in
Table 3,
Table 4,
Table 5 and
Table 6. One of the chosen examples in [
9] relies on a hyperchaotic 4D Chen system to generate keys and construct six S-boxes, alongside the Mersenne Twister PRNG. Another scheme employs a 6D memristor hyperchaotic system together with multiple rounds of scrambling, diffusion, and S-box substitution [
41]. In [
42], the designers proposed a scheme that combines a 5D hyperchaotic system with elliptic curve operations and S-box transformations. Finally, in [
43], their proposed cipher integrates three separate stages using cellular automata, an S-box built from modular inverses and permutations, and the Lorenz system.
In contrast, our experiments demonstrated that the use of simple constructions and chaotic maps is sufficient to eliminate statistical biases. Changing the underlying chaotic map also has minimal impact on the cipher’s performance. As shown in
Table 3,
Table 4, and
Table 6, the proposed configurations either match or outperform the other chaos-based image ciphers with complex designs. This provides evidence that we do not need complex constructions or high-dimensional chaotic maps to improve security, as they complicate efforts to verify security claims using cryptanalytic methods.
Based on the performance metrics described in
Section 2.2, where 100 implies that the cipher achieves the ideal results for a particular metric and 0 implies otherwise, the optimal configurations listed in
Table 2 have better statistical properties compared to the chaos-based image ciphers used as benchmarks [
9,
41,
42,
43]. Since all of the proposed configurations perform similarly, SP or PS would provide the ideal trade-off between statistical performance and computational cost. Overall, the findings of this experiment show the advantage of adopting a minimalistic approach for encryption schemes, producing robust statistical results without excessive complexity, as well as that changing the underlying chaotic maps does not affect the results.
5. Chaotic Feistel Block Cipher (CFBC)
In this section, we investigate if a conventional block cipher can be designed using a chaotic map as a building block. Our design goal is for the cipher to have a simple, well-understood design that can facilitate third-party cryptanalysis efforts. We use the logistic map with its control parameter set to
. The decision to go with a simple one-dimensional map is to demonstrate that robust security can be attained without relying on complex chaotic systems. We propose a chaos-based block cipher based on the extended version of the original Feistel network, known as the generalized Feistel network (GFN) [
44]. The GFN structure has been used in the design of ciphers such as WARP [
45] and TWINE [
46]. The aim of CFBC is not to propose a real-world-ready cipher, but to demonstrate how simple chaos-based substitutions can be embedded into a well-understood cryptographic structure while remaining analyzable using standard techniques.
The proposed block cipher has a block size of 128 bits, which is divided into eight sub-blocks . The choice of branches (i.e., 16-bit sub-blocks) is motivated by the fixed-point implementation of the chaotic map, which uses 32-bit precision. The choice of 32-bit precision is a trade-off between sensitivity and computational overhead. Using 32 bits leaves a sufficiently large fractional state to extract 16 bits, while preserving high sensitivity to input differences. Then, half of these sub-blocks undergo mixing using the round function, followed by a permutation of the k sub-blocks.
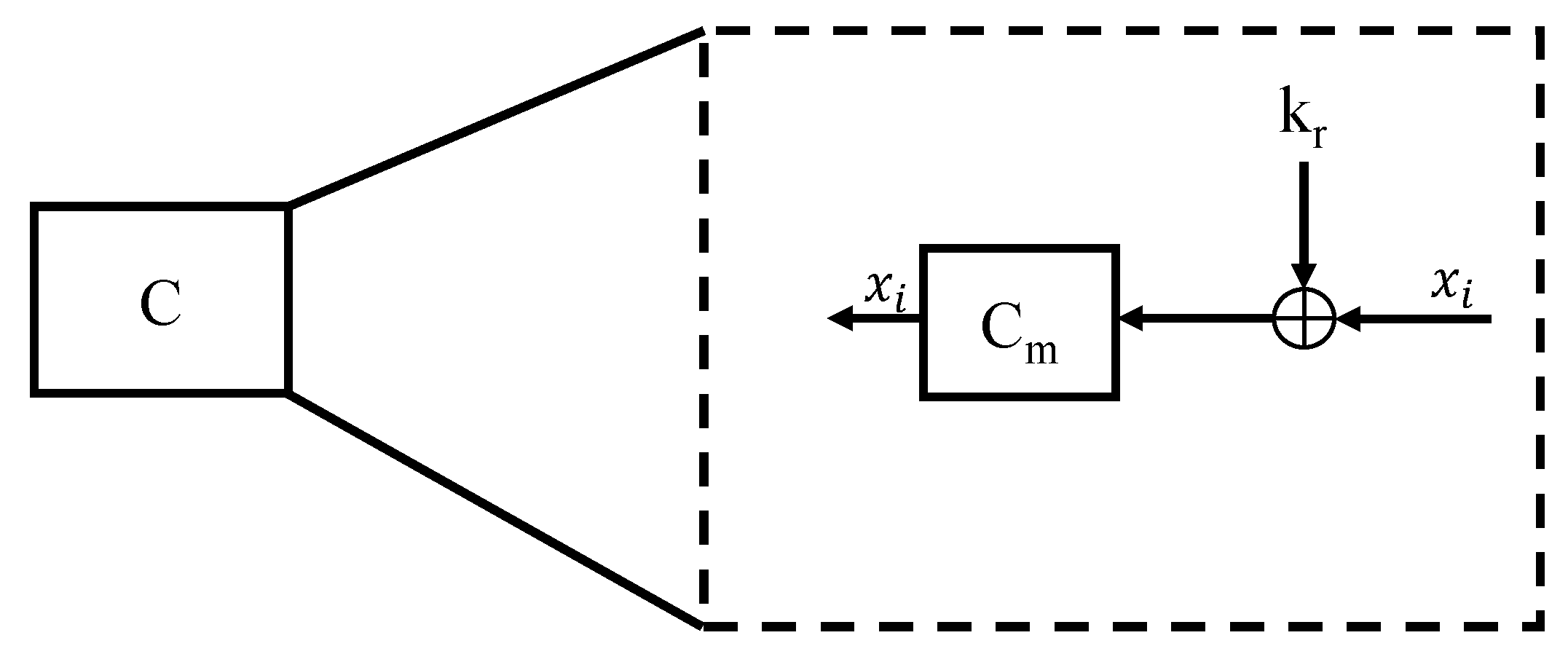
The use of the Feistel structure is motivated by several factors. Firstly, it allows for the use of the same code for both encryption and decryption processes, potentially reducing the implementation cost of decryption. The second factor is that the Feistel network allows the use of a one-way round function. Chaotic maps, which serve as the nonlinear component of the round function (which we refer to as the C-function), exhibit one-way behaviour. The architecture of the proposed CFBC is shown in
Figure 3.
The C-Function provides nonlinearity to the cipher. The C-Function is defined as follows:
where
is the chaotic map,
is a 16-bit sub-block of message bits, and
is a 16-bit sub-block of the round key, as illustrated in
Figure 4. The output of the C-function is calculated as follows:
An XOR operation is performed between and to obtain .
The current state X of the chaotic map in 16-bit fixed-point representation is XOR-ed with .
The chaotic map (logistic map) is then iterated.
The 16 least-significant bits of the chaotic map’s state, X, are extracted as the output of the C-function.
After applying the C-function to half of the plain text blocks, the output is XOR-ed with their corresponding halves, as shown in
Figure 3, before undergoing a block-wise permutation or block shuffle. The permutation pattern employed in this cipher is illustrated in
Table 7. This particular permutation pattern is known as the No.1 shuffle [
44]. This pattern is chosen due to its ability to achieve complete diffusion in just six rounds, which is a fewer number of rounds compared to other types of block shuffles for
branches. The minimum number of activated nonlinear functions evaluated for differential and linear cryptanalysis for No.1 shuffle is also superior [
44]. The number of activated nonlinear functions serves as a basis for our analysis of the cipher’s security against differential cryptanalysis.
Both the block size and key size of the proposed block cipher are 128 bits. The block cipher requires a minimum of 6 rounds to ensure maximal diffusion but we recommend at least 20 rounds to be secure against attacks such as differential cryptanalysis (see
Section 5.2). The initial values for the employed chaotic map ()the logistic map) are
and
. These are public, fixed values that are not part of the secret key. To perform computations on real numbers, we use a 32-bit fixed-point representation where 2 of the most-significant bits represent integers and the 30 least-significant bits represent fractions. The use of fixed-point representation instead of floating point improves analyzability as it allows us to see how each bit in a real number is used in processing. The 128-bit secret key plays a crucial role in generating round keys. The key schedule of the proposed block cipher is as follows:
The 128-bit secret key is divided into eight 16-bit registers.
The logistic map is iterated once for each register.
Bits from the logistic map’s state variable (represented as fixed-point numbers) are extracted after each iteration, where the least-significant bits are XOR-ed with the current value of each register.
The round key is obtained from all eight updated registers.
All steps are repeated to obtain round keys for other rounds.
5.1. Ciphertext Randomness Testing
Block ciphers are widely used cryptographic primitives that serve as fundamental building blocks for other cryptographic algorithms, including hash functions and pseudo-random number generators. At the very least, the ciphertexts generated from a block cipher must exhibit essential properties such as high complexity, non-period behaviour, and uniform distribution. To assess the statistical randomness of CFBC, we apply the NIST SP 800-22 test suite. To generate test samples, we create random cipher texts by randomly flipping a single bit of an arbitrary plain text. Each test is conducted with a fixed significance level , and the quality of the sequence is determined by its corresponding p value. If the p value is greater than 0.01, the generated sequence successfully passes the test; otherwise, it fails. A sample size of 100 binary sequences is utilized for each test, with a bit length of for each sequence.
The first test sample is obtained by encrypting a plain text consisting of interleaved bit values of 1 s and 0 s. Subsequent test samples are generated by randomly flipping a single bit in the plain text. The results presented in
Table 8 demonstrate that CFBC successfully passed all 15 sub-tests of the NIST test suite. This indicates that the outputs of the block cipher exhibit desirable characteristics of randomness, even distribution, and complexity.
The ENT test consist of five tests for randomness, and the results are presented in
Table 9. The entropy test measures the information density of the sequence, represented as the number of bits per byte, and quantifies the expected information contained in the generated sequence. CFBC exhibits a maximum level of entropy (ideal value 8), indicating a high degree of randomness. The chi-square test shows that the generated sequence is random and highly sensitive to errors in PRNG. The arithmetic mean for CFBC (calculated as the sum of all bytes in the generated file divided by the file length) is very close to random, falling within the mean range of 127 ± 0.01. Moreover, the Monte Carlo value converges to pi with an error of 0.01% for CFBC, further confirming the sequence’s proximity to randomness. Lastly, the serial correlation coefficient test demonstrates that there is no correlation between each byte and the previous byte in the sequence.
5.2. Security Against Differential Cryptanalysis
In this section, we show that it is indeed possible to analyze the security of a chaos-based cipher using conventional cryptanalysis methods. We use differential cryptanalysis as an example. Other attacks such as linear cryptanalysis can be trivially extended based on our findings. Note that we do not rely on statistical tests but instead perform analysis based on the differential property of the C-function and the number of active nonlinear functions. This approach is commonly used to estimate the security of S-box-based block ciphers against differential cryptanalysis, by counting the number of active S-boxes. We demonstrate a provable upper-bound of security against differential cryptanalysis for CFBC.
By using fixed-point representation to compute real numbers, we can compute the difference propagation through the logistic map. We use 32-bit fixed-point numbers where the two most-significant bits represent integers and the thirty least-significant bits represent the fraction. The choice of using a 32-bit fixed-point representation directly affects the precision of the logistic map’s internal state and hence its differential properties. Increasing the precision of the fixed-point representation expands the state space and leads to finer granularity in difference propagation. This enhanced sensitivity, especially in the least-significant bits, can result in lower differential probabilities and thus a higher security margin. This is analogous to using 8-bit S-boxes rather than 4-bit S-boxes in conventional block ciphers. Conversely, using fewer bits could lead to higher differential probabilities. Therefore, the bounds we present should be interpreted as specific to the 32-bit fixed-point configuration, with the potential for tighter bounds under higher precision.
Since the logistic map’s state variable is , only 30 fraction bits are active at any time. We can then compute the differential distribution table (DDT) by taking as the input to the logistic map, while is the output—similar to how the DDT is computed for any substitution box. However, computing the full DDT is computationally expensive since it would be equivalent to computing the differential distribution for a 30-bit S-box. As such, we first limit the search space to only the 18 most-significant fractional bits. This implies that the differential probability obtained is only an upper bound and that the actual probability would be much lower if all 30 bits were taken into consideration. After we identify the input-to-output difference propagation with the highest probability, we then consider all bits involved in the C-function and recompute the actual probability for the target differences.
Experimentally, the upper bound of the differential probability of the C-function is approximately , where the difference propagation is . For 20 rounds of the cipher, the No.1 block shuffle would lead to 30 active nonlinear functions, which leads to an upper-bound differential probability of . There is a significant security margin of or 313 bits against a differential attack.
As with different S-box choices in conventional ciphers, changing the chaotic map or the bit-precision configuration would lead to different differential profiles. Exploring such variants presents an interesting direction for future work. Note that we only focus on differential cryptanalysis as a baseline measure of security. Our goal is to demonstrate that chaotic components, when used within a well-understood design paradigm like GFN, can be meaningfully assessed using conventional cryptanalytic techniques. Future work may extend this to other forms of cryptanalysis (e.g., linear or boomerang attacks).
5.3. An Image Encryption Scheme Based on CFBC
Conventionally, block ciphers only need to provide proof of resistance against various attacks, such as differential cryptanalysis in the previous section, and do not need to be applied specifically to encrypt images. However, one of the common arguments in many papers for proposing new chaos-based image ciphers is that mainstream block ciphers are inadequate for image encryption. We want to, instead, show that our proposed block cipher can be applied to image encryption and attain similar statistical properties touted by past chaos-based image ciphers. The encryption phase comprises three main steps—reshaping the plainimage to obtain a one-dimensional array; CBC encryption; and, finally, reshaping the encrypted one-dimensional array to obtain the cipherimage. Each of these steps is elaborated below.
Reshaping the image: The plainimage undergoes a reshaping process before encryption is applied. This process scales each pixel value in the plainimage to a 16-bit word. Each pixel value, which ranges between 0 and 255, is linearly scaled to fall between 0 and 65,535. For example, a pixel value of 189 () will be expanded and stored as (). All pixels will be stored in a one-dimensional array of 65,536 16-bit words.
CBC Encryption: The one-dimensional array is encrypted 8 words at a time (128-bit blocks) using CFBC in cipher block chaining (CBC) mode. In this process, an initialization vector (IV) based on the numbers of pi is chosen, which is an example of
nothing up my sleeve numbers, which are commonly used in cryptography [
47]. The encryption starts by XOR-ing the IV with the first image block, generating a chaining value for the first block. This chaining value is then encrypted using the block cipher (CFBC) algorithm, producing the first cipher text block. For subsequent blocks, the chaining value (the result of the previous block’s encryption) is XOR-ed with the plain text block. This operation ensures that each block’s encryption depends on the encryption of the previous block, providing the chaining effect. The resulting cipher text represents the encrypted array.
Reshaping the array: The encrypted array is reshaped to form the cipherimage by reversing Step 1.