Collateral Damage from Offensive Cyber Operations—A Systematic Literature Review
Abstract
1. Introduction
1.1. Research Goals
- What research exists on cyber collateral damage (CCD)?
- How can this body of research be analyzed in terms of common themes, the research intensity over time, and references to identify and describe research trends and gaps?
1.2. Layout of This Paper
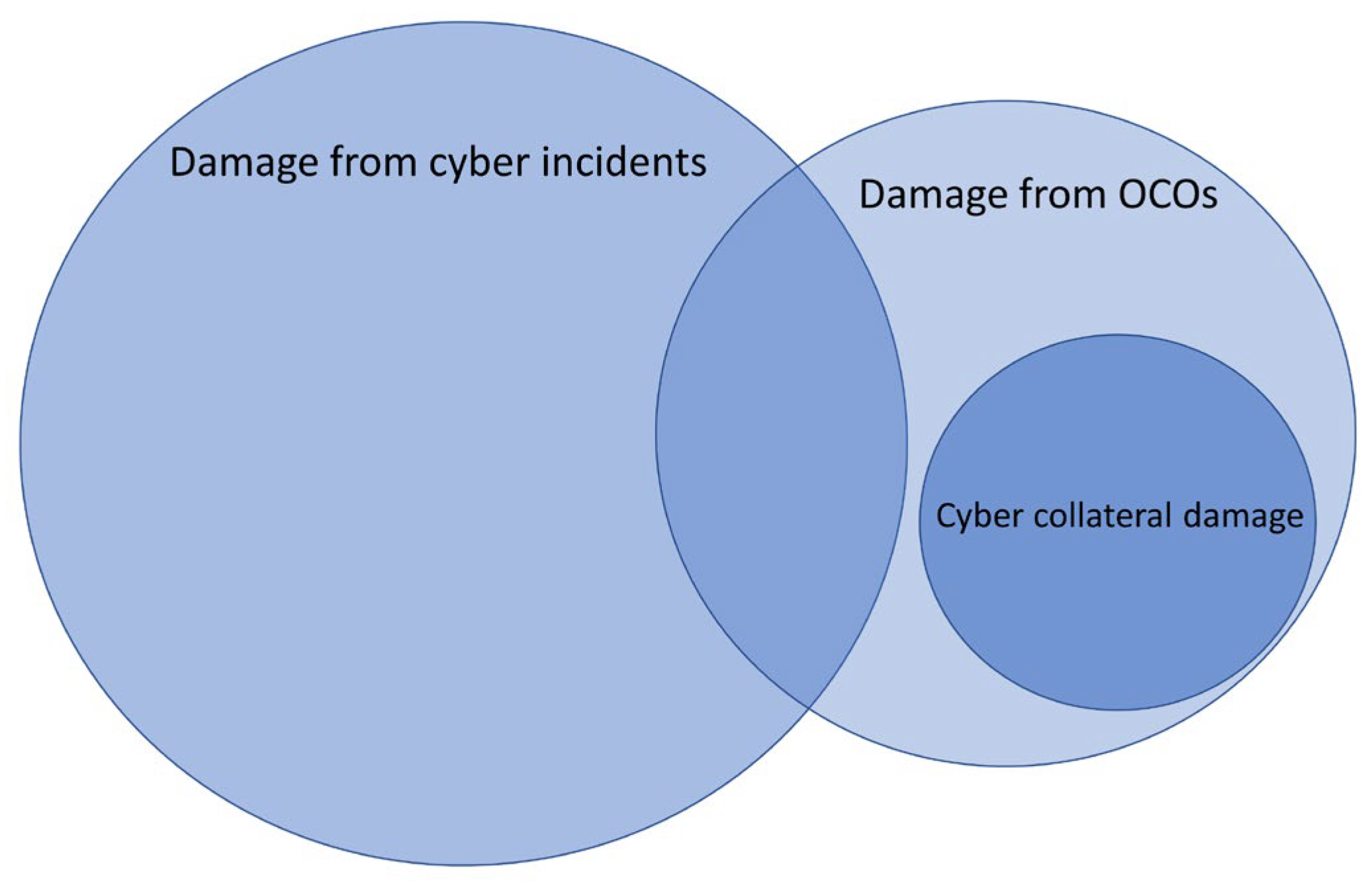
2. Collateral Damage Within the Cyberspace Context
- Unintended, damaging consequences from operations against legal and legitimate targets, e.g., in the conduct of a declared cyberwar;
- Damage from intentional operations against civilian targets, e.g., South Korean banks and television stations in 2013;
- Damage from the reuse of discovered or reverse-engineered technology, e.g., the WannaCry ransomware.
2.1. Prior Literature Reviews
- Maathuis, Pieters, and van der Berg give a review narrowly focused on CCD as it pertains to targeting and military doctrine—six sources are found [17].
- Maathuis, Pieters, and van den Berg present another review on the military and legal dimensions of CCD [18]. This paper cites five sources on military (targeting) dimensions and nine sources on legal dimensions, and they argue that “from an extensive review of the scientific literature […], one can conclude that military cyber operations lack models and methodologies for planning, execution, and assessment, although the effects of their use can impact […] collateral civilian and military actors and systems”.
- Focusing on a review of the literature in the adjacent research area of cyberattack taxonomies and ontologies, Grant also presents a secondary review on CCD [19]. The scope of this review is based solely on papers published in the proceedings of the International Conference on Cyber Conflict. Eight papers are reviewed.
2.2. Definitions
3. Materials and Methods
3.1. Sources and Search Methodology
- Scopus, which “uniquely combines a comprehensive, expertly curated abstract and citation database with enriched data and linked scholarly literature across a wide variety of disciplines”, indexing 82 million resources;
- IEEE Xplore, “delivering full text access to the world’s highest quality technical literature in engineering and technology” and indexing 5.8 million items;
- Springer Link, “providing researchers with access to millions of scientific documents from journals, books, series, protocols, reference works and proceedings” and indexing 14.5 million resources;
- Elsevier’s ScienceDirect, “the world’s leading source for scientific, technical, and medical research” and indexing more than 15 million scientific articles;
- ProQuest, which “powers research in academic, corporate, government, public and school libraries around the world with unique content”, indexing “millions of resources”.
3.2. Inclusion Criteria (IC)
- Title;
- Keywords; or
- Abstract.
3.3. Exclusion Criteria (EC)
- Duplicates between search engines;
- Written in a language other than English;
- Not published in an academic/scientific context, e.g., featuring in trade journals, or not a research paper, e.g., conference track descriptions; or
- Irrelevant, i.e., papers that fit the search criteria but were not relevant to the question of civilian harm from cyber operations, as determined by coding the text for keywords [26].
3.4. Search Outcomes
3.5. Limitations
4. Results
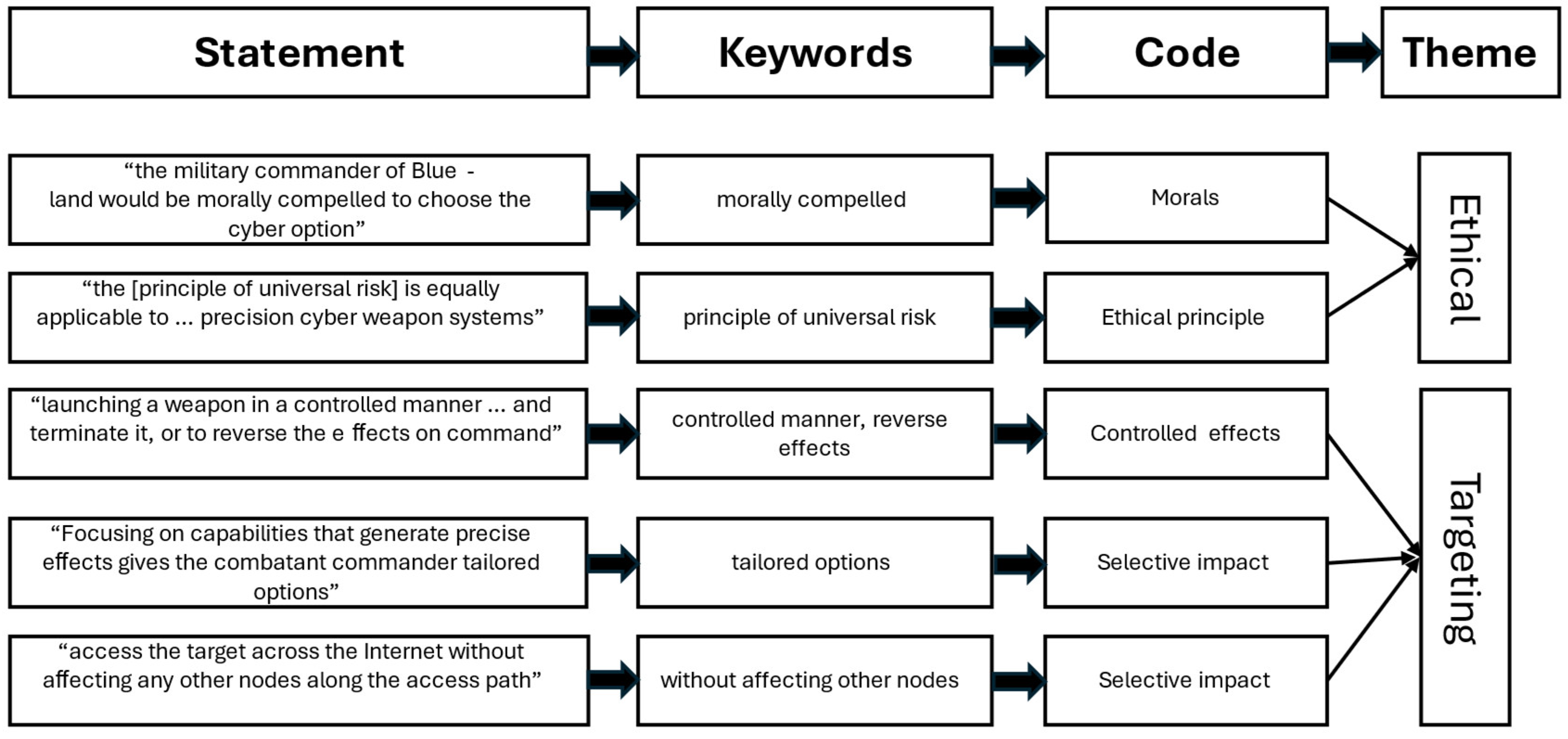
4.1. Categories and Thematic Analysis
- Does this paper concern legal aspects of CCD and the (legal, rather than ethical) permissibility and constraints at play?
- Does this paper concern the targeting of cyber operations specifically to avoid or minimize CCD?
- Does this paper concern ethical aspects of CCD (frameworks and processes to determine whether an attack is justified)?
- Does this paper concern the economically adverse outcomes of CCD and the potential costs to the target and civil society, e.g., by quantifying it?
- Does this paper attempt to model and estimate CCD from the perspective of the attacker?
- Does this paper seek to create a taxonomy or definition of CCD types?
4.2. Legal Aspects of Cyberwarfare and the Permissibility of Collateral Damage
4.3. Targeting in Cyber Operations—Collateral Damage Considerations
- No commonly accepted definitions exist for concepts like “cyberwar”, “information war”, or “collateral damage”;
- Collateral damage is undesirable and illegal and must be taken into account; and
- Cyber effects are difficult to measure.
4.4. Ethical Aspects of Collateral Damage from Offensive Cyber Operations
4.5. Econometric Aspects of Cyber Collateral Damage
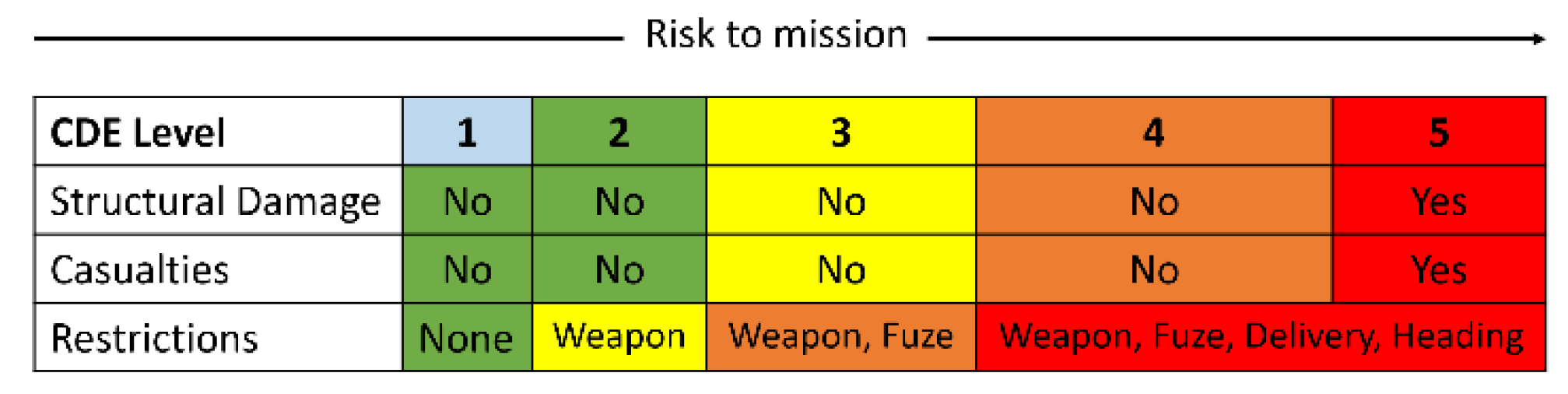
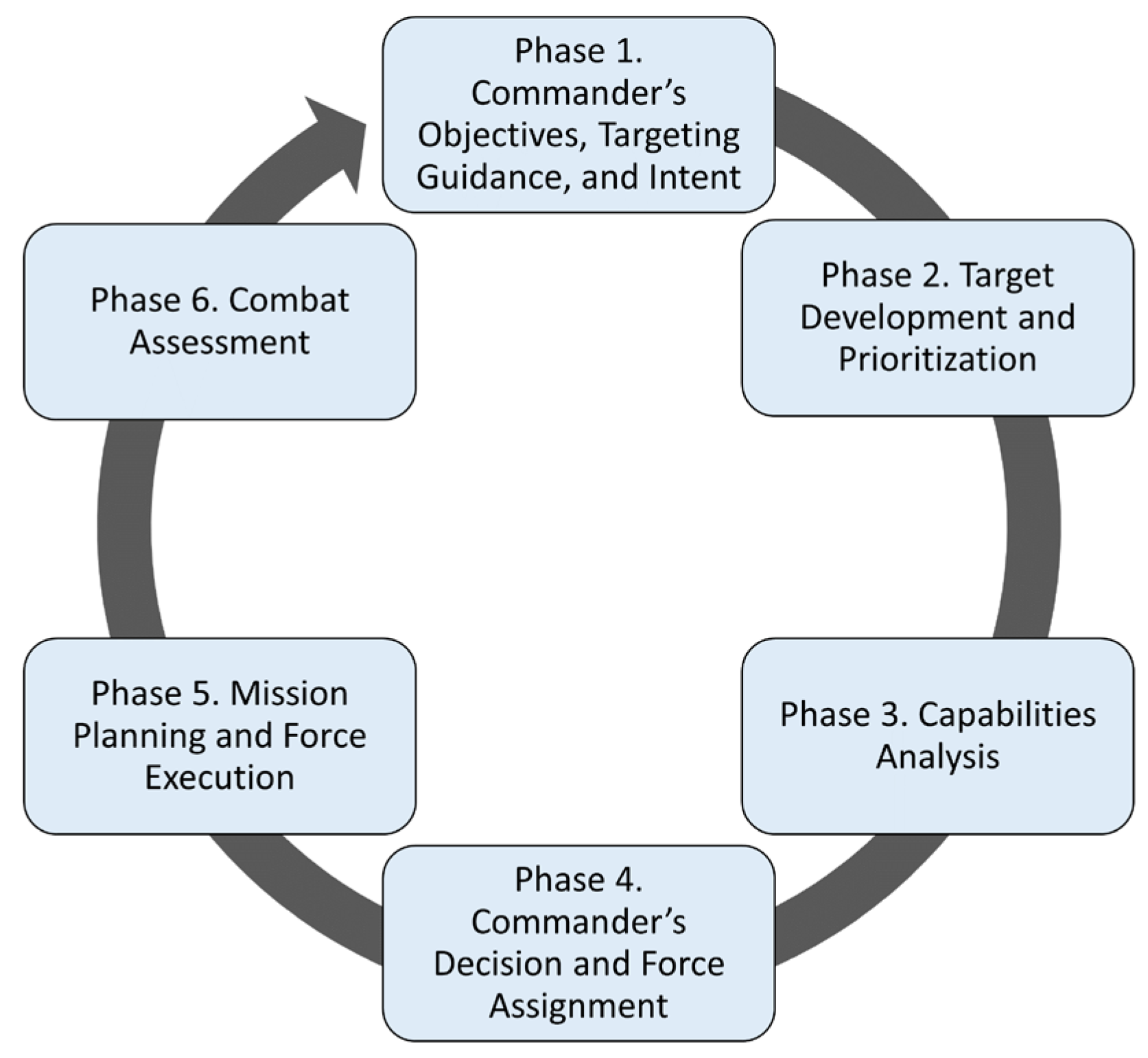
4.6. Collateral Damage Estimation, Modeling, and Assessment
| Process Step | Description |
|---|---|
| CDE 1 | Target validation, initial assessment |
| CDE 2 | General, target size assessment |
| CDE 3 | Weaponeering assessment |
| CDE 4 | Refined assessment |
| CDE 5 | Casualty assessment |
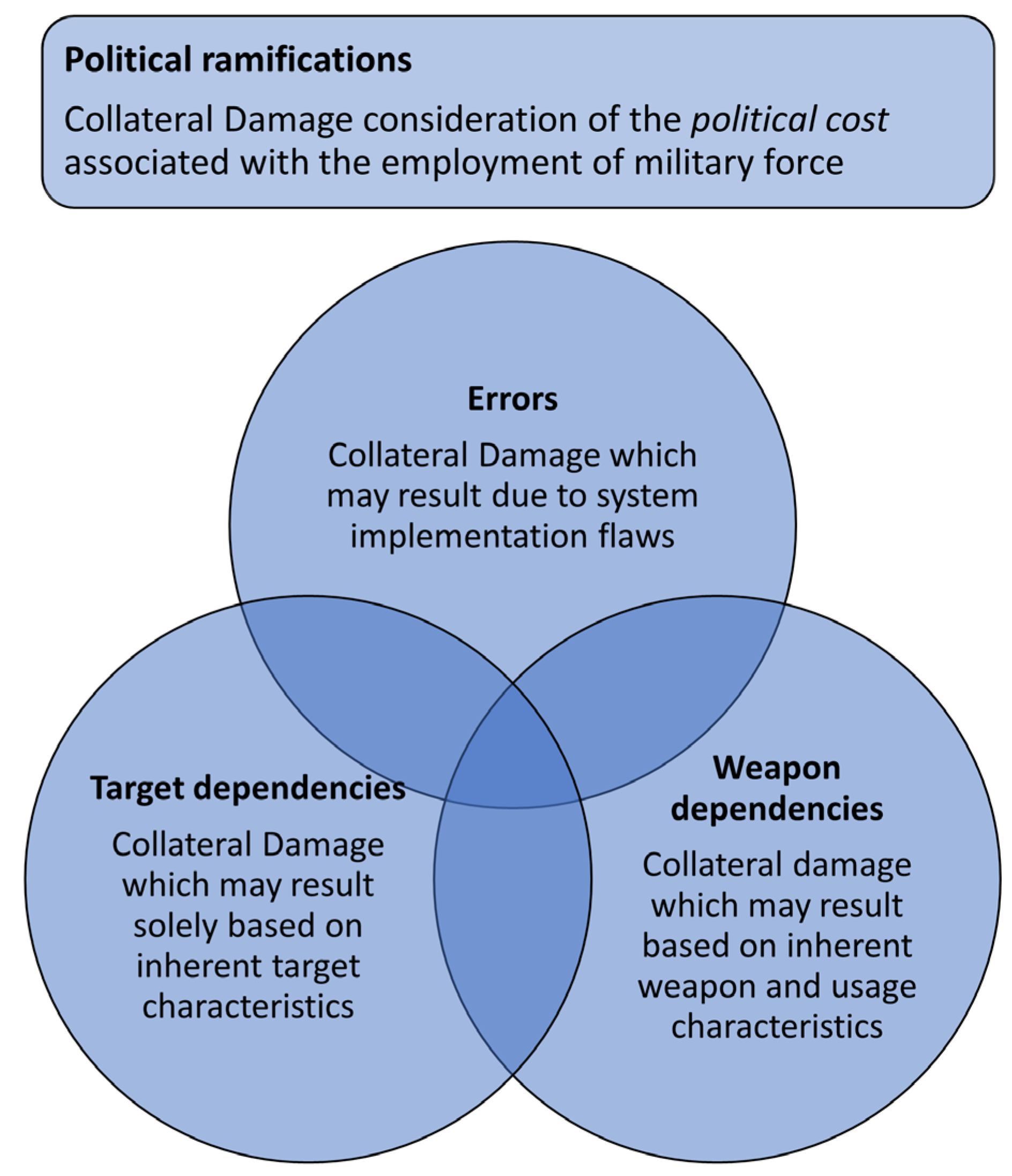
4.7. Taxonomies of Cyber Collateral Damage
- Direct collateral damage;
- Errors in targeting;
- Costs of recovering from direct damage due to a cyberweapon;
- Costs of attack propagation;
- Costs of attack analysis and the development of mitigation measures;
- Psychological damage;
- Costs of vulnerability disclosure.
4.8. Notable Contributions Outside Categories
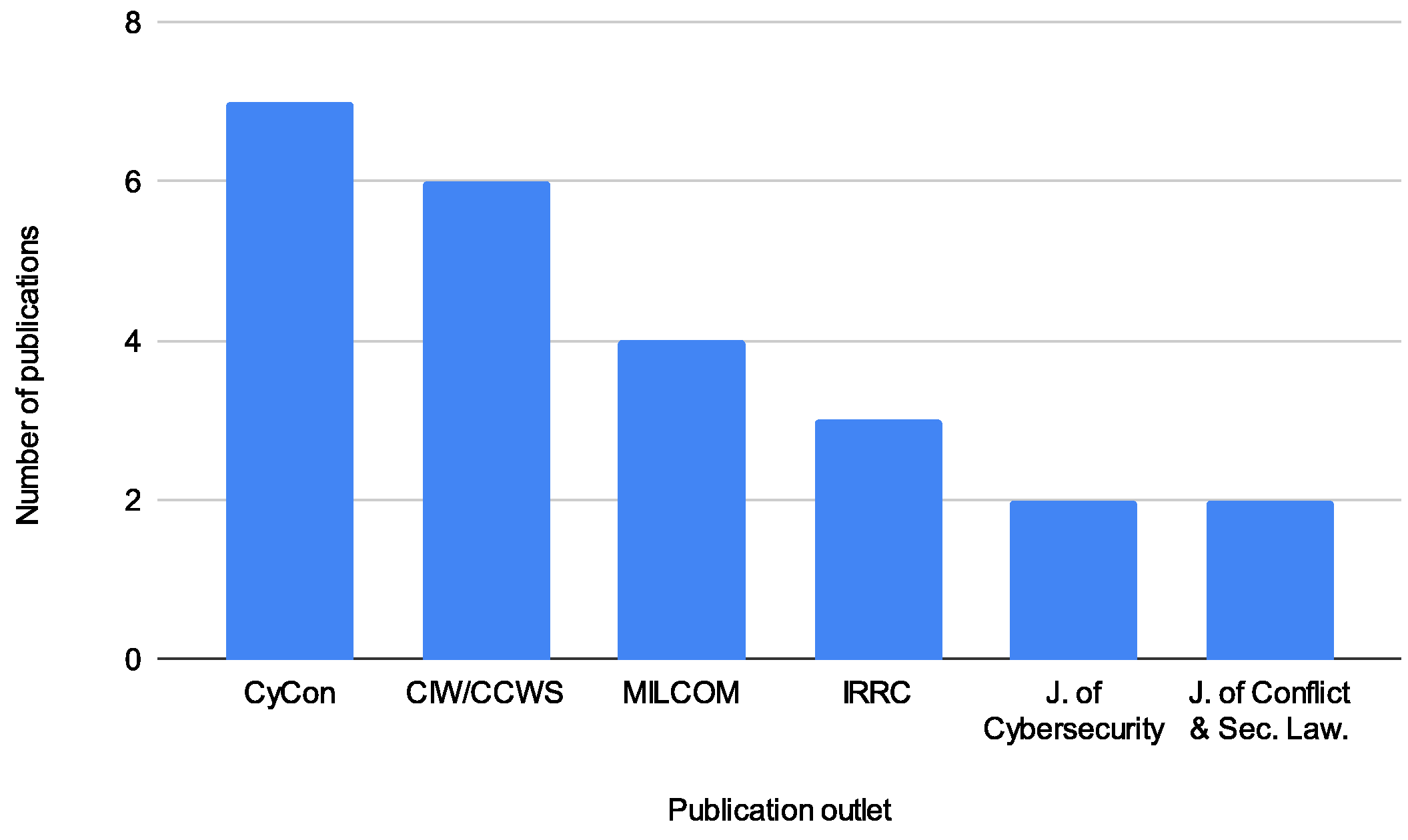
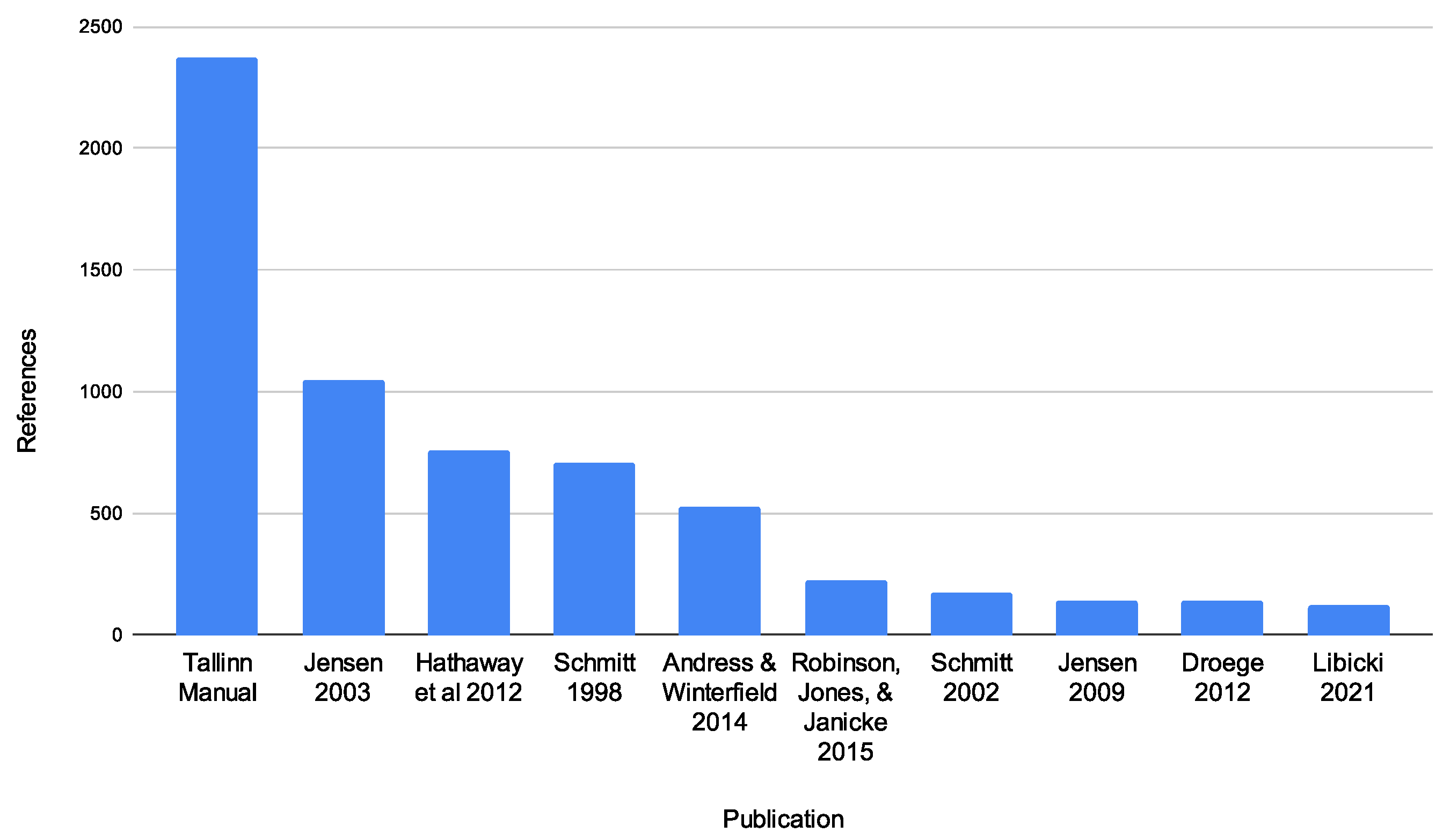
4.9. Bibliographic Analysis
5. Discussion
5.1. Research Trends and Gaps
5.2. Legal Responses to Cyberattacks in Theory and Practice
5.3. The Use of AI in Collateral Damage Estimation and Assessment
5.4. Future Research Opportunities
6. Conclusions
Funding
Acknowledgments
Conflicts of Interest
Appendix A
| Scientific Database | Search String |
|---|---|
| IEEE Xplore | ((“All Metadata”:“Cyber” OR “All Metadata”:“Cyberspace” OR “All Metadata”:“Computer Network Attack”) AND “Full Text & Metadata”:“Collateral Damage”) |
| Scopus | (TITLE-ABS-KEY (“cyber” OR “cyberspace” OR “computer network attack”) AND ALL(“collateral damage”)) |
| ScienceDirect | Title, Abstract, Keywords:(“cyber” OR “cyberspace” OR “computer network attack”) AND (“collateral damage”) |
| Springer Link | ((“offensive cyber operation” OR “cyberspace operation” OR “computer network attack”) AND (“collateral damage”)) OR (cyber NEAR “collateral damage”) |
| ProQuest | ((“offensive cyber operation” OR “cyberspace operation” OR “computer network attack”) AND (“collateral damage”)) OR (cyber NEAR “collateral damage”) Limit to: Peer Reviewed |
Appendix B
| Title | Authors | Publication | Year | Prominence |
|---|---|---|---|---|
| The principle of proportionality in an era of high technology | Beard J. | Complex Battlespaces: The Law of Armed Conflict and the Dynamics of Modern Warfare | 2018 | 1 |
| Precision cyber weapon systems: An important component of a responsible national security strategy? | Hare F.B. | Contemporary Security Policy | 2019 | 3 |
| International Conflict and Security Law: PRINCIPLES OF INTERNATIONAL LAW | Blank L.R. | International Conflict and Security Law: Principles of International Law | 2023 | 1 |
| Assessment Methodology for Collateral Damage and Military (Dis) Advantage in Cyber Operations | Maathuis C.; Pieters W., Van Den Berg J. | Proceedings—IEEE Military Communications Conference, MILCOM | 2018 | 3 |
| Is the principle of distinction still relevant in cyberwarfare? | Bannelier K. | Research Handbook on International Law and Cyberspace | 2021 | 2 |
| Recommendations for Enhancing the Results of Cyber Effects | Orye E., Maennel O.M. | International Conference on Cyber Conflict, CYCON | 2019 | 3 |
| Tackling uncertainty through probabilistic modelling of proportionality in military operations | Maathuis C., Chockalingam S. | European Conference on Information Warfare and Security, ECCWS | 2023 | 3 |
| Collateral damage outcomes are prominent in cyber warfare, despite targeting | Hirsch C. | Proceedings of the 13th International Conference on Cyber Warfare and Security, ICCWS 2018 | 2018 | 2 |
| Restraint under conditions of uncertainty: Why the United States tolerates cyberattacks | Kaminska M. | Journal of Cybersecurity | 2021 | 2 |
| Distinctive ethical challenges of cyberweapons | Rowe N.C. | Research Handbook on International Law and Cyberspace | 2015 | 1 |
| Building an ontology for planning attacks that minimize collateral damage: Literature survey | Grant T. | 14th International Conference on Cyber Warfare and Security, ICCWS 2019 | 2019 | 3 |
| Proportionality in cyber targeting | Roscini M. | Routledge Handbook of War, Law and Technology | 2019 | 1 |
| Decision support model for effects estimation and proportionality assessment for targeting in cyber operations | Maathuis C., Pieters W., van den Berg J. | Defence Technology | 2021 | 2 |
| The ethics of cyberweapons in warfare | Rowe N.C. | International Journal of Technoethics | 2010 | 2 |
| Deterring strategic cyberattack | Elliott D. | IEEE Security and Privacy | 2011 | 1 |
| Ethics of cyber war attacks | Rowe N.C. | Cyber Warfare and Cyber Terrorism | 2007 | 2 |
| A non-militarised approach to cyber-security | Adams A., Reich P., Weinstein S. | 11th European Conference on Information Warfare and Security 2012, ECIW 2012 | 2012 | 1 |
| Malware is called malicious for a reason: The risks of weaponizing code | Cobb S., Lee A. | International Conference on Cyber Conflict, CYCON | 2014 | 3 |
| Considering internal vulnerabilities and the attacker’s knowledge to model the impact of cyber events as geometrical prisms | González-Granadillo G., et al. | Proceedings—15th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, 10th IEEE International Conference on Big Data Science and Engineering | 2016 | 1 |
| Moral Cyber Weapons | Denning D.E., Strawser B.J. | Ethics of information warfare (Law, Governance and Technology Series) | 2014 | 2 |
| Exploring the prudent limits of automated cyber attack | Caton J.L. | International Conference on Cyber Conflict, CYCON | 2013 | 1 |
| Cyber warfare: Issues and challenges | Robinson M., Jones K., Janicke H. | Computers and Security | 2015 | 2 |
| Fighting power, targeting and cyber operations | Ducheine P., Van Haaster J. | International Conference on Cyber Conflict, CYCON | 2014 | 2 |
| Towards reversible cyberattacks | Rowe N.C. | 9th European Conference on Information Warfare and Security 2010, ECIW 2010 | 2010 | 2 |
| Determining the utility of cyber vulnerability implantation: The heartbleed bug as a cyber operation | Sigholm J., Larsson E. | Proceedings—IEEE Military Communications Conference, MILCOM | 2014 | 3 |
| A control measure framework to limit collateral damage and propagation of cyber weapons | Raymond D., Conti G., Cross T., Fanelli R. | International Conference on Cyber Conflict, CYCON | 2013 | 3 |
| The principle of distinction and Cyber war in international armed conflicts | Dinstein Y. | Dinstein Y. | 2012 | 3 |
| A methodology for cyber operations targeting and control of collateral damage in the context of lawful armed conflict | Fanelli R., Conti G | 2012 4th International Conference on Cyber Conflict, CYCON 2012—Proceedings | 2012 | 3 |
| Understanding Cyber Collateral Damage | Romanosky S., Goldman Z. | Journal of National Security Law & Policy | 2017 | 3 |
| Deterrence Theory and the Challenge of Applying It to Cyber Warfare | Mazanec B.M., Thayer B.A. | Deterring Cyber Warfare: Bolstering Strategic Stability in Cyberspace | 2015 | 1 |
| Wired Warfare: Computer Network Attack and Jus in Bello | Schmitt M.N. | International Review of the Red Cross | 2002 | 2 |
| Section II: Cyber Operations | Dinstein Y., Dahl A.W. | Oslo Manual on Select Topics of the Law of Armed Conflict | 2020 | 2 |
| Challenges of civilian distinction in cyberwarfare | Rowe N.C. | Ethics and Policies for Cyber Operations | 2016 | 3 |
| The Ethics of Cyberattack | Lee S.P. | The Ethics of Information Warfare | 2014 | 1 |
| Permissible Preventive Cyberwar: Restricting Cyber Conflict to Justified Military Targets | Lucas G.R. | The Ethics of Information Warfare | 2014 | 2 |
| Conceptualization and cases of study on cyber operations against the sustainability of the tactical edge | Monge M.A.S., Vidal J.M. | Future Generation Computer Systems | 2021 | 1 |
| Cyber Warfare. Techniques, Tactics and Tools for Security Practitioners, 2nd edition | Andress J., Winterfeld S. | Syngress | 2014 | 1 |
| Cyber Vulnerability Implantation Revisited | Sigholm J., Larsson E. | MILCOM 2021–2021 IEEE Military Communications Conference (MILCOM) | 2021 | 3 |
| An analysis for a just cyber warfare | Taddeo M. | 2012 4th International Conference on Cyber Conflict (CYCON 2012) | 2012 | 1 |
| Cyber Offense and Targeting | Couretas J.M. | An Introduction to Cyber Analysis and Targeting | 2022 | 2 |
| Wired warfare 3.0: Protecting the civilian population during cyber operations | Schmitt M.N. | International Review of the Red Cross | 2019 | 3 |
| Joint Targeting in Cyberspace | Smart S.J. | Air & Space Power Journal | 2011 | 2 |
| Cyber weapons and precision-guided munitions | Acton J. | Understanding cyber conflict: Fourteen analogies | 2017 | 3 |
| An Examination of the Operational Requirements of Weaponised Malware | Easttom C. | Journal of Information Warfare | 2018 | 1 |
| Cyber Warfare: Applying the Principle of Distinction in an Interconnected Space | Geiß R., Lahmann H. | Israel Law Review | 2012 | 3 |
| Get off my cloud: cyber warfare, international humanitarian law, and the protection of civilians | Droege C. | International Review of the Red Cross | 2012 | 3 |
| Humanitarian Law: Developing International Rules for the Digital Battlefield | O’Donnell, B.T., Kraska, J.C. | Journal of Conflict & Security Law | 2003 | 3 |
| Cyber Warfare and Precautions Against the Effects of Attacks | Jensen E.T. | Texas Law Review | 2009 | 2 |
| The Strategic Promise of Offensive Cyber Operations | Smeets M. | Strategic Studies Quarterly | 2018 | 1 |
| Responding to International Cyber Attacks as Acts of War | Sklerov M. | Inside Cyber Warfare | 2009 | 2 |
| International Law and Information Operations | Wingfield T. | Cyberpower and National Security | 2009 | 2 |
| Computer Network Attack and the Use of Force in International Law: Thoughts on a Normative Framework | Schmitt M.N. | Columbia Journal of Transnational Law | 1998 | 1 |
| Tallinn Manual 2.0 on the International Law Applicable to Cyber Warfare * | Schmitt M.N. (ed.) | Cambridge University Press | 2017 | 3 |
| The Law of Cyber-Attack | Hathaway O., et al. | California Law Review | 2012 | 1 |
| Conceptualizing Financial Loses as a Result of Advanced Persistent Threats | Levine C. | Honors College Theses | 2013 | 1 |
| Cyber-attacks, cryptocurrencies, and cyber-security | Caporale G.M., et al. | CESifo, Munich | 2020 | 1 |
| The Ingredients of Cyber Weapons | Repel D., Hersee S. | 10th International Conference on Cyber Warfare and Security (ICCWS) | 2015 | 1 |
| Limiting the undesired impact of cyber weapons: technical requirements and policy implications | Bellovin S.M., Landau S., Lin H.S. | Journal of Cybersecurity | 2017 | 3 |
| Cyberneutrality: Discouraging Collateral Damage | Kohler K. | ETH CSS Policy Perspectives | 2022 | 3 |
| Civilians in Cyberwarfare: Casualties | Brenner S., Clarke L. | Science and Technology Law Review | 2017 | 3 |
| Cyber House Rules: On War, Retaliation and Escalation | Cavaiola L., Gompert D., Libicki M. | Survival | 2015 | 2 |
| Cyber Warfare & Inadvertent Escalation | Acton J. | Daedalus | 2020 | 2 |
| Avoiding civilian harm from military cyber operations during armed conflicts | Lawson E., Macák K. | ICRC Expert Meeting | 2020 | 3 |
| Distinction and Proportionality in Cyber War: Virtual Problems with a Real Solution | Pascucci P. | Minnesota Journal of International Law | 2017 | 3 |
| Proportionality in Attack on Data: Balancing Military Advantage and Collateral Damage in Cyberspace | Normelli N. | Uppsala University | 2021 | 3 |
| Unexpected Consequences From Knock-On Effects: A Different Standard for Computer Network Operations? | Jensen E.T. | American University International Law Review 18, No. 5 | 2003 | 3 |
| Effects Assessment for Targeting Decisions Support in Military Cyber Operations | Maathuis C. | TU Delft | 2020 | 3 |
| On Cyberwarfare | Schreier F. | Geneva Centre for the Democratic Control of Armed Forces | 2015 | 2 |
| Cyberspace in Peace and War * | Libicki M.C. | Naval Institute Press | 2021 | 3 |
| Cyberspace Operations Collateral Damage-Reality or Misconception? | Bertoli G., Marvel L. | Cyber Defense Review | 2017 | 3 |
| Applicability of Jus in Bello in Cyber Space: Dilemmas and Challenges | Wang Q. | International Journal of Cyber Warfare and Terrorism | 2014 | 2 |
| Human Centered Explainable AI Framework for Military Cyber Operations | Maathuis C. | MILCOM 2023–2023 IEEE Military Communications Conference | 2023 | 2 |
| The Weaponization of Artificial Intelligence in Cybersecurity: A Systematic Review | Nobles C. | Procedia Computer Science | 2024 | 2 |
| Towards Econometric Estimation of the Cost of Cyber Conflict | Larsson E., Sigholm J. | Procedia Computer Science | 2024 | 3 |
References
- Aiyer, B.; Caso, J.; Russell, P.; Sorel, M. Mckinsey: New Survey Reveals $2 Trillion Market Opportunity for Cybersecurity Technology and Service Providers. 2022. Available online: https://www.mckinsey.com/capabilities/risk-and-resilience/our-insights/cybersecurity/new-survey-reveals-2-trillion-dollar-market-opportunity-for-cybersecurity-technology-and-service-providers (accessed on 30 January 2024).
- IBM Security; the Ponemon Institute. Cost of a Data Breach Report 2022. 2022. Available online: https://www.ibm.com/downloads/cas/3R8N1DZJ (accessed on 31 January 2024).
- Hanson, F.; Uren, T. Australia’s Offensive Cyber Capability. 2018. Available online: https://www.aspi.org.au/report/australias-offensive-cyber-capability (accessed on 31 January 2024).
- Farwell, J.P.; Rohozinski, R. Stuxnet and the Future of Cyber War. Survival 2011, 53, 23–40. [Google Scholar] [CrossRef]
- U.S. Department of Justice. Three North Korean Military Hackers Indicted in Wide-Ranging Scheme to Commit Cyberattacks and Financial Crimes Across the Globe. 2022. Available online: https://www.justice.gov/opa/pr/three-north-korean-military-hackers-indicted-wide-ranging-scheme-commit-cyberattacks-and (accessed on 1 February 2024).
- Schelling, T.C. Dispersal, deterrence, and damage. Oper. Res. 1961, 9, 363–370. [Google Scholar] [CrossRef]
- U.S. Air Force. Air Force Doctrine Publication 3–60, Targeting. 2021. Available online: https://www.doctrine.af.mil/Portals/61/documents/AFDP_3-60/3-60-AFDP-TARGETING.pdf (accessed on 1 February 2024).
- Schmitt, M.N. (Ed.) Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar]
- Arquilla, J.; Ronfeldt, D. Cyberwar is coming! Comp. Strategy 1993, 12, 141–165. [Google Scholar] [CrossRef]
- Lee, E.A.; Seshia, S.A. Introduction to Embedded Systems: A Cyber-Physical Systems Approach, 2nd ed.; MIT Press: Cambridge, MA, USA, 2017. [Google Scholar]
- Romanosky, S.; Goldman, Z. Cyber Collateral Damage. Procedia Comput. Sci. 2016, 95, 10–17. [Google Scholar] [CrossRef][Green Version]
- U.S. Air Force. Intelligence Targeting Guide, Attachment 7. 1998. Available online: https://irp.fas.org/doddir/usaf/afpam14-210/part20.htm (accessed on 1 February 2024).
- Romanosky, S.; Goldman, Z. Understanding Cyber Collateral Damage. J. Natl. Secur. Law Policy 2017, 9, 233–257. [Google Scholar]
- Dinstein, Y. The Principle of Distinction and Cyber War in International Armed Conflicts. J. Confl. Secur. Law 2012, 17, 261–277. [Google Scholar] [CrossRef]
- Ablon, L.; Binnendijk, A.; Hodgson, Q.E.; Lilly, B.; Romanosky, S.; Senty, D.; Thompson, J.A. Operationalizing Cyberspace as a Military Domain, Perspective, RAND Corporation 2019. Available online: https://www.rand.org/content/dam/rand/pubs/perspectives/PE300/PE329/RAND_PE329.pdf (accessed on 30 January 2024).
- U.S. Department of Defense. Department of Defense Law of War Manual; William S. Hein & Company: Getzville, NY, USA, 2023.
- Maathuis, C.; Pieters, W.; Van den Berg, J. Assessment Methodology for Collateral Damage and Military (Dis)Advantage in Cyber Operations. In Proceedings of the MILCOM 2018—2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Maathuis, C.; Pieters, W.; van den Berg, J. Decision support model for effects estimation and proportionality assessment for targeting in cyber operations. Def. Technol. 2021, 17, 352–374. [Google Scholar] [CrossRef]
- Grant, T. Building an Ontology for Planning Attacks That Minimize Collateral Damage: Literature Survey. In Proceedings of the 14th International Conference on Cyber Warfare & Security (ICCWS 2019), Stellenbosch, South Africa, 28 February–1 March 2019; pp. 78–86. [Google Scholar]
- University of York Centre for Reviews and Dissemination. What Are the Criteria for the Inclusion of Reviews on DARE? 2014. Available online: https://www.ncbi.nlm.nih.gov/books/NBK285222/ (accessed on 31 January 2024).
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef]
- Vaismoradi, M.; Snelgrove, S. Theme in Qualitative Content Analysis and Thematic Analysis. Forum Qual. Soc. Res. 2019, 20, 3. [Google Scholar] [CrossRef]
- Wanyama, S.B.; McQuaid, R.W.; Kittler, M. Where you search determines what you find: The effects of bibliographic databases on systematic reviews. Int. J. Soc. Res. Methodol. 2022, 25, 409–422. [Google Scholar] [CrossRef]
- Gusenbauer, M. Google Scholar to overshadow them all? Comparing the sizes of 12 academic search engines and bibliographic databases. Scientometrics 2019, 118, 177–214. [Google Scholar] [CrossRef]
- Schmitt, M.N. Wired warfare: Computer network attack and jus in bello. Int. Rev. Red Cross 2002, 84, 365–399. [Google Scholar] [CrossRef]
- Naeem, M.; Ozuem, W.; Howell, K.; Ranfagni, S. A Step-by-Step Process of Thematic Analysis to Develop a Conceptual Model in Qualitative Research. Int. J. Qual. Methods 2023, 22, 1–18. [Google Scholar] [CrossRef]
- Randolph, J.J.; Bednarik, R. Publication Bias in the Computer Science Education Research Literature. J. Univers. Comput. Sci. 2008, 14, 575–589. [Google Scholar]
- Robinson, M.; Jones, K.; Janicke, H. Cyber warfare: Issues and challenges. Comput. Secur. 2015, 49, 70–94. [Google Scholar] [CrossRef]
- Hare, F.B. Precision cyber weapon systems: An important component of a responsible national security strategy? Contemp. Secur. Policy 2019, 40, 193–213. [Google Scholar] [CrossRef]
- Hathaway, O.A.; Crootof, R.; Levitz, P.; Nix, H.; Nowlan, A.; Perdue, W.; Spiegel, J. The Law of Cyber-Attack. Calif. Law Rev. 2012, 100, 817–885. [Google Scholar]
- Wingfield, T. International law and information operations. In Cyberpower and National Security; Kramer, F.D., Starr, S.H., Wentz, L.K., Eds.; NDU Press: Washington, DC, USA, 2009; pp. 525–542. [Google Scholar]
- Sklerov, M. Responding to International Cyber Attacks as Acts of War. In Inside Cyber Warfare; Carr, J., Ed.; O’Reilly Media: Sebastopol, CA, USA, 2009. [Google Scholar]
- Wang, Q. Applicability of Jus in Bello in Cyber Space: Dilemmas and Challenges. Int. J. Cyber Warf. Terror. 2014, 4, 43–62. [Google Scholar] [CrossRef]
- Schmitt, M.N. Computer Network Attack and the Use of Force in International Law: Thoughts on a Normative Framework. Columbia J. Transnatl. Law 1998, 37, 885. [Google Scholar]
- Jensen, E.T. Unexpected Consequences From Knock-On Effects: A Different Standard for Computer Network Operations? Am. Univ. Int. Law Rev. 2003, 18, 1145–1188. [Google Scholar]
- O’Donnell, B.T.; Kraska, J.C. Humanitarian Law: Developing International Rules for the Digital Battlefield. J. Confl. Secur. Law 2003, 8, 133–160. [Google Scholar] [CrossRef]
- Efrony, D.; Shany, Y. A Rule Book on the Shelf? Tallinn Manual 2.0 on Cyberoperations and Subsequent State Practice. Am. J. Int. Law 2018, 112, 583–657. [Google Scholar] [CrossRef]
- Normelli, N. Proportionality in Attack on Data: Balancing Military Advantage and Collateral Damage in Cyberspace; Uppsala University: Uppsala, Sweden, 2021. [Google Scholar]
- Pascucci, P. Distinction and Proportionality in Cyberwar: Virtual Problems with a Real Solution. Minn. J. Int. Law 2017, 26, 419–460. [Google Scholar]
- Bannelier, K. Is the principle of distinction still relevant in cyberwarfare? From doctrinal discourse to States’ practice. In Research Handbook on International Law and Cyberspace; Tsagourias, N., Buchan, R., Eds.; Edward Elgar Publishing: Cheltenham, UK, 2015; pp. 343–365. [Google Scholar]
- Beard, J.M. The principle of proportionality in an era of high technology. In Complex Battlespaces: The Law of Armed Conflict and the Dynamics of Modern Warfare; Ford, C.M., Williams, W.S., Eds.; Oxford University Press: Oxford, UK, 2018. [Google Scholar]
- Geiß, R.; Lahmann, H. Cyber Warfare: Applying the Principle of Distinction in an Interconnected Space. Isr. Law Rev. 2012, 45, 381–399. [Google Scholar] [CrossRef]
- Jensen, E.T. Cyber Warfare and Precautions Against the Effects of Attacks. Tex. Law Rev. 2009, 88, 1533–1569. [Google Scholar]
- Brenner, S.W.; Clarke, L.L. Civilians in Cyberwarfare: Casualties. SMU Sci. Technol. Law Rev. 2010, 13, 249–282. [Google Scholar]
- Schmitt, M.N. Wired warfare 3.0: Protecting the civilian population during cyber operations. Int. Rev. Red Cross 2019, 101, 333–355. [Google Scholar] [CrossRef]
- Droege, C. Get off my cloud: Cyber warfare, international humanitarian law, and the protection of civilians. Int. Rev. Red Cross 2013, 94, 533–578. [Google Scholar] [CrossRef]
- Dinstein, Y.; Dahl, A.W. Section II: Cyber Operations. In Oslo Manual on Select Topics of the Law of Armed Conflict; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Fanelli, R.; Conti, G. A methodology for cyber operations targeting and control of collateral damage in the context of lawful armed conflict. In Proceedings of the 2012 4th International Conference on Cyber Conflict (CYCON 2012), Tallinn, Estonia, 5–8 June 2012; pp. 1–13. [Google Scholar]
- Ducheine, P.; van Haaster, J. Fighting power, targeting and cyber operations. In Proceedings of the 2014 6th International Conference On Cyber Conflict (CyCon 2014), Tallinn, Estonia, 3–6 June 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 303–327. [Google Scholar] [CrossRef]
- Orye, E.; Maennel, O.M. Recommendations for Enhancing the Results of Cyber Effects. In Proceedings of the 2019 11th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 28–31 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–19. [Google Scholar] [CrossRef]
- Denning, D.E. Stuxnet: What Has Changed? Future Internet 2012, 4, 672–687. [Google Scholar] [CrossRef]
- Hirsch, C. Collateral damage outcomes are prominent in cyber warfare, despite targeting. In Proceedings of the 13th International Conference on Cyber Warfare and Security, ICCWS 2018, Washington, DC, USA, 8–9 March 2018; Chen, J.Q., Ed.; Curran Associates, Inc.: Washington, DC, USA, 2018; pp. 281–286. [Google Scholar]
- Cavaiola, L.J.; Gompert, D.C.; Libicki, M. Cyber House Rules: On War, Retaliation and Escalation. Survival 2015, 57, 81–104. [Google Scholar] [CrossRef]
- Acton, J.M. Cyber weapons and precision guided munitions. In Understanding Cyber Conflict: Fourteen Analogies; Perkovich, G., Levite, A.E., Eds.; Georgetown University Press: Washington, DC, USA, 2017; pp. 45–60. [Google Scholar]
- Smart, S.J. Joint Targeting in Cyberspace. Air Space Power J. 2011, 25, 65–74. [Google Scholar]
- Couretas, J.M. Cyber Offense and Targeting. In An Introduction to Cyber Analysis and Targeting; Springer International Publishing: Cham, Switzerland, 2022; pp. 151–172. [Google Scholar] [CrossRef]
- Monge, M.A.S.; Vidal, J.M. Conceptualization and cases of study on cyber operations against the sustainability of the tactical edge. Future Gener. Comput. Syst. 2021, 125, 869–890. [Google Scholar] [CrossRef]
- Libicki, M. Cyberspace in Peace and War, 2nd ed.; Naval Institute Press: Annapolis, MD, USA, 2021. [Google Scholar]
- Denning, D.E.; Strawser, B.J. Moral Cyber Weapons. In The Ethics of Information Warfare; Taddeo, M., Floridi, L., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 85–103. [Google Scholar]
- Lucas, G.R. Permissible Preventive Cyberwar: Restricting Cyber Conflict to Justified Military Targets. In The Ethics of Information Warfare; Taddeo, M., Floridi, L., Eds.; Springer International Publishing: Cham, Switzerland, 2014; p. 73. [Google Scholar]
- Rowe, N.C. The Ethics of Cyberweapons in Warfare. Int. J. Cyberethics 2009, 1, 20–31. [Google Scholar]
- Rowe, N.C. Ethics of cyberwar attacks. In Cyber War and Cyber Terrorism; Colarik, A., Janczewski, L., Eds.; The Idea Group: Hershey, PA, USA, 2007. [Google Scholar]
- Rowe, N.C. Distinctive Ethical Challenges of Cyberweapons. In Research Handbook on International Law and Cyberspace; Tsagourias, N., Ed.; Edward Elgar Publishing: Cheltenham, UK, 2015; pp. 307–325. [Google Scholar]
- Gorman, S.; Barnes, J.E. Cyber Combat: Act of War—Pentagon Sets Stage for U.S. to Respond to Computer Sabotage with Military Force, The Wall Street Journal. 2011. Available online: https://www.wsj.com/articles/SB10001424052702304563104576355623135782718 (accessed on 31 January 2024).
- Murray, S.F. The Moral and Ethical Implications of Precision-Guided Munitions; Maxwell AFB School of Advanced Air and Space Studies: Montgomery, AL, USA, 2007. [Google Scholar]
- Rowe, N.C. Challenges of Civilian Distinction in Cyberwarfare. In Ethics and Policies for Cyber Operations: A NATO Cooperative Cyber Defense Centre of Excellence Initiative; Taddeo, M., Glorioso, L., Eds.; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Cobb, S.; Lee, A. Malware is called malicious for a reason: The risks of weaponizing code. In Proceedings of the 2014 6th International Conference On Cyber Conflict (CyCon 2014), Tallinn, Estonia, 3–6 June 2014; pp. 71–84. [Google Scholar]
- Nakashima, E.; Timberg, C. NSA officials worried about the day its potent hacking tool would get loose. Then it did. Washington Post, 16 May 2017. [Google Scholar]
- Brück, T.; de Groot, O.J.; Bozzoli, C. How Many Bucks in a Bang: On the Estimation of the Economic Costs of Conflict. In The Oxford Handbook of the Economics of Peace and Conflict; Garfinkel, M.R., Skaperdas, S., Eds.; Oxford University Press: Oxford, UK, 2012. [Google Scholar]
- Stiglitz, J.E.; Bilmes, L.J. Estimating the Costs of War: Methodological Issues, with Applications to Iraq and Afghanistan. In The Oxford Handbook of the Economics of Peace and Conflict; Garfinkel, M.R., Skaperdas, S., Eds.; Oxford University Press: Oxford, UK, 2012. [Google Scholar]
- Levine, C. Conceptualizing Financial Loses as a Result of Advanced Persistent Threats. Bachelor’s Thesis, Pace University, New York, NY, USA, 2013. [Google Scholar]
- Sigholm, J.; Larsson, E. Cyber Vulnerability Implantation Revisited. In Proceedings of the MILCOM 2021—2021 IEEE Military Communications Conference (MILCOM), San Diego, CA, USA, 29 November–2 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 464–469. [Google Scholar] [CrossRef]
- Sigholm, J.; Larsson, E. Determining the Utility of Cyber Vulnerability Implantation: The Heartbleed Bug as a Cyber Operation. In Proceedings of the 2014 IEEE Military Communications Conference, Baltimore, MD, USA, 6–8 October 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 110–116. [Google Scholar] [CrossRef]
- Larsson, E.; Sigholm, J. Towards econometric estimation of the cost of cyber conflict. Procedia Comput. Sci. 2024, 246, 2635–2644. [Google Scholar] [CrossRef]
- Kohler, K. Cyberneutrality: Discouraging Collateral Damage. CSS Policy Perspect. 2022, 10, 1–4. [Google Scholar]
- Lilly, B.; Geers, K.; Rattray, G.; Koch, R. Business@War: The IT Companies Helping to Defend Ukraine. In Proceedings of the 2023 15th International Conference on Cyber Conflict: Meeting Reality (CyCon), Tallinn, Estonia, 30 May–2 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 71–83. [Google Scholar] [CrossRef]
- Bogdanowicz, Z.R.; Patel, K. Quick Collateral Damage Estimation Based on Weapons Assigned to Targets. IEEE Trans. Syst. Man. Cybern Syst. 2015, 45, 762–769. [Google Scholar] [CrossRef]
- Joint Targeting School. Collateral Damage Estimation Qualification Course Syllabus. 2021. Available online: https://www.jcs.mil/Portals/36/Documents/Doctrine/training/jts/col_damage_course_syllabus2021.pdf (accessed on 31 January 2024).
- Maathuis, C.; Chockalingam, S. Tackling Uncertainty Through Probabilistic Modelling of Proportionality in Military Operations. Eur. Conf. Cyber Warf. Secur. 2023, 22, 276–284. [Google Scholar] [CrossRef]
- Maathuis, C. Effects Assessment for Targeting Decisions Support in Military Cyber Operations; Delft University of Technology: Delft, The Netherlands, 2020. [Google Scholar]
- European Union Military Committee. Avoiding and Minimizing Collateral Damage in EU-Led Military Operations Concept, Brussels. 2016. Available online: https://data.consilium.europa.eu/doc/document/ST-5785-2016-INIT/en/pdf (accessed on 30 January 2024).
- Raymond, D.; Conti, G.; Cross, T.; Fanelli, R. A control measure framework to limit collateral damage and propagation of cyber weapons. In Proceedings of the 2013 5th International Conference on Cyber Conflict (CYCON 2013), Tallinn, Estonia, 4–7 June 2013; pp. 1–16. [Google Scholar]
- Bertoli, G.; Marvel, L. Cyberspace Operations Collateral Damage—Reality or Misconception? Cyber Def. Rev. 2017, 2, 53–62. [Google Scholar]
- Smeets, M. The Strategic Promise of Offensive Cyber Operations. Strateg. Stud. Q. 2018, 12, 90–113. [Google Scholar]
- Lawson, E.; Mačák, K. Avoiding Civilian Harm from Military Cyber Operations During Armed Conflicts; International Committee of the Red Cross: Geneva, Switzerland, 2021. [Google Scholar]
- Rowe, N.C. Towards reversible cyberattacks. In Proceedings of the 9th European Conference on Information Warfare and Security, Thessaloniki, Greece, 1–2 July 2010; Demergis, J., Ed.; Curran Associates, Inc.: Red Hook, NY, USA, 2010. [Google Scholar]
- Hu, Y. Efficient, high-quality force-directed graph drawing. Math. J. 2005, 10, 37–71. [Google Scholar]
- U.S. Cyber Command. Improving Targeting Support to Cyber Operations. 2016. Available online: https://nsarchive.gwu.edu/sites/default/files/documents/6379795/National-Security-Archive-USCYBERCOM-Joint.pdf (accessed on 1 February 2024).
- United States Department of Defense. Summary 2023 Cyber Strategy of the Department of Defense; United States Department of Defense: Arlington County, VA, USA, 2023.
- Soesanto, S. The IT Army of Ukraine: Structure, Tasking, and Ecosystem; Center for Security Studies: Zürich, Switzerland, 2022. [Google Scholar]
- Tidy, J. Meet the Hacker Armies on Ukraine’s Cyber Front Line, BBC 2023. Available online: https://www.bbc.com/news/technology-65250356 (accessed on 30 January 2024).
- Lin, P.; Allhoff, F.; Abney, K. Is Warfare the Right Frame for the Cyber Debate? In The Ethics of Information Warfare; Floridi, L., Taddeo, M., Eds.; Springer: Cham, Switzerland, 2014; pp. 39–59. [Google Scholar]
- Backman, S. Making Sense of Large-scale Cyber Incidents: International Cybersecurity Beyond Threat-Based Security Perspectives. Doctoral Dissertation, Stockholm University, Stockholm, Sweden, 2023. [Google Scholar]
- Ghafur, S.; Kristensen, S.; Honeyford, K.; Martin, G.; Darzi, A.; Aylin, P. A retrospective impact analysis of the WannaCry cyberattack on the NHS. NPJ Digit. Med. 2019, 2, 98. [Google Scholar] [CrossRef] [PubMed]
- Preis, B.; Susskind, L. Municipal Cybersecurity: More Work Needs to be Done. Urban Aff. Rev. 2022, 58, 614–629. [Google Scholar] [CrossRef]
- Kniesner, T.J.; Leeth, J.D.; Sullivan, R.S. A new approach to evaluate safety and force protection investments: The value of a statistical life. In Military Cost-Benefit Analysis: Theory and Practice; Melese, F., Richter, A., Solomon, B., Eds.; Routledge: London, UK, 2015; pp. 237–260. [Google Scholar]
- Rohlfs, C.; Sullivan, R. The Cost-Effectiveness of Armored Tactical Wheeled Vehicles for Overseas US Army Operations. Def. Peace Econ. 2013, 24, 293–316. [Google Scholar] [CrossRef][Green Version]
- Franco, M.F.; Künzler, F.; von der Assen, J.; Feng, C.; Stiller, B. RCVaR: An economic approach to estimate cyberattacks costs using data from industry reports. Comput. Secur. 2024, 139, 103737. [Google Scholar] [CrossRef]
- Wilson, B.; Goughnour, T.; McKernan, M.; Karode, A.; Tierney, D.; Arena, M.V.; Vermeer, M.J.D.; Perez, H.; Levedahl, A. A Cost Estimating Framework for U.S. Marine Corps Joint Cyber Weapons; RAND Corporation: Santa Monica, CA, USA, 2023. [Google Scholar]
- Andersson, K.; Bang, M.; Marcus, C.; Persson, B.; Sturesson, P.; Jensen, E.; Hult, G. Military utility: A proposed concept to support decision-making. Technol. Soc. 2015, 43, 23–32. [Google Scholar] [CrossRef][Green Version]
- van Haaster, J. On Cyber: The Utility of Military Cyber Operations During Armed Conflict; University of Amsterdam: Amsterdam, The Netherlands, 2019. [Google Scholar]
- Schulze, M. Cyber in War: Assessing the Strategic, Tactical, and Operational Utility of Military Cyber Operations. In Proceedings of the 2020 12th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 26–29 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 183–197. [Google Scholar] [CrossRef]
- Danielson, S.; Conway, P.; Vonasch, A. What I don’t know can hurt you: Collateral combat damage seems more acceptable when bystander victims are unidentified. PLoS ONE 2024, 19, e0298842. [Google Scholar] [CrossRef]
- Microsoft. Microsoft Digital Defense Report 2024. 2024. Available online: https://www.microsoft.com/en-us/security/security-insider/intelligence-reports/microsoft-digital-defense-report-2024 (accessed on 29 October 2024).
- Karagiannopoulos, V.; Reid, I. US Sanctions on Iranian Hackers Highlight Growing Concern About the Islamic Republic’s Cyberwarriors, The Conversation. 2024. Available online: https://theconversation.com/us-sanctions-on-iranian-hackers-highlight-growing-concern-about-the-islamic-republics-cyberwarriors-228718 (accessed on 6 November 2024).
- United Nations General Assembly, United Nations Resolution 75/240. 2020. Available online: https://meetings.unoda.org/open-ended-working-group-on-information-and-communication-technologies-2021 (accessed on 5 November 2024).
- Nobles, C. The Weaponization of Artificial Intelligence in Cybersecurity: A Systematic Review. Procedia Comput. Sci. 2024, 239, 547–555. [Google Scholar] [CrossRef]
- Maathuis, C. Human Centered Explainable AI Framework for Military Cyber Operations. In Proceedings of the MILCOM 2023—2023 IEEE Military Communications Conference: Communications Supporting Military Operations in a Contested Environment, Boston, MA, USA, 30 October–3 November 2023; IEEE: Boston, MA, USA, 2023; pp. 260–267. [Google Scholar]
- Torre, D.; Abualhaija, S.; Sabetzadeh, M.; Briand, L.; Baetens, K.; Goes, P.; Forastier, S. An AI-assisted Approach for Checking the Completeness of Privacy Policies Against GDPR. In Proceedings of the 2020 IEEE 28th International Requirements Engineering Conference (RE), Zurich, Switzerland, 31 August–4 September 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 136–146. [Google Scholar] [CrossRef]
- Angelov, P.P.; Soares, E.A.; Jiang, R.; Arnold, N.I.; Atkinson, P.M. Explainable artificial intelligence: An analytical review. WIREs Data Min. Knowl. Discov. 2021, 11, e1424. [Google Scholar] [CrossRef]
- Ghassemi, M.; Oakden-Rayner, L.; Beam, A.L. The false hope of current approaches to explainable artificial intelligence in health care. Lancet Digit. Health 2021, 3, 745–750. [Google Scholar] [CrossRef]
- Valeriano, B. Harvard Dataverse: Dyadic Cyber Incident Dataset v 2.0, 2022. Available online: https://dataverse.harvard.edu/dataset.xhtml?persistentId=doi:10.7910/DVN/CQOMYV (accessed on 20 January 2024).
- Cyber Peace Institute. Cyber Attacks in Times of Conflict. Available online: https://cyberconflicts.cyberpeaceinstitute.org/ (accessed on 22 September 2024).
- Maness, R.C.; Valeriano, B.; Hedgecock, K.; Jensen, B.M.; Macias, J.M. Codebook for the Dyadic Cyber Incident and Campaign Dataset (DCID) Version 2.0. 2022. Available online: https://a678132e-4067-4ed4-800a-239c80659fd1.filesusr.com/ugd/4b99a4_ca35bdb6bd55443e890d2dab86910b4c.pdf (accessed on 20 January 2024).
- Rid, T. Cyber War Will Not Take Place. J. Strateg. Stud. 2012, 35, 5–32. [Google Scholar] [CrossRef]



| Database | Search Results |
|---|---|
| Scopus | 170 |
| Springer Link | 147 |
| ScienceDirect | 87 |
| IEEE Xplore | 225 |
| ProQuest | 87 |
| Topic (Cluster) | Number of Papers |
|---|---|
| Legal | 24 |
| Targeting | 16 |
| Ethical | 14 |
| Econometric | 8 |
| Estimation, modeling, and assessment | 5 |
| Taxonomy | 3 |
| Level of Prominence | Papers Found |
|---|---|
| Main topic of paper (3) | 30 |
| Deeply explored or recurring topic (2) | 22 |
| Limited analysis of topic (1) | 22 |
| Authors | Year | Title |
|---|---|---|
| Dinstein Y. | 2012 | The principle of distinction and cyber war in international armed conflicts |
| Romanosky S., Goldman Z. | 2017 | Understanding Cyber Collateral Damage * |
| Schmitt M. N. | 2019 | Wired warfare 3.0: Protecting the civilian population during cyber operations |
| Geiß R.; Lahmann H. | 2012 | Cyber Warfare: Applying the Principle of Distinction in an Interconnected Space |
| Droege C. | 2012 | Get off my cloud: cyber warfare, international humanitarian law, and the protection of civilian |
| O’Donnell B.T.; Kraska J.C. | 2003 | Humanitarian Law: Developing International Rules for the Digital Battlefield |
| Brenner S.; Clarke L. | 2017 | Civilians in Cyberwarfare: casualties |
| Pascucci P. | 2017 | Distinction and Proportionality in Cyber War: Virtual Problems with a Real Solution |
| Normelli N. | 2021 | Proportionality in Attack on Data: Balancing Military Advantage and Collateral Damage in Cyberspace |
| Schmitt M. (ed) | 2017 | Tallinn Manual 2.0 on the International Law Applicable to Cyber Warfare * |
| Jensen E.T. | 2003 | Unexpected Consequences From Knock-On Effects: A Different Standard for Computer Network Operations? |
| Bannelier K. | 2021 | Is the principle of distinction still relevant in cyberwarfare? From doctrinal discourse to States’ practice |
| Ducheine P.; Van Haaster J. | 2014 | Fighting power, targeting and cyber operations |
| Schmitt M.N. | 2002 | Wired Warfare: Computer Network Attack and Jus in Bello |
| Dinstein Y.; Dahl A.W. | 2020 | Oslo Manual on Select Topics of the Law of Armed Conflict, Section II: Cyber Operations |
| Wang Q. | 2014 | Applicability of Jus in Bello in Cyber Space: Dilemmas and Challenges |
| Jensen E.T. | 2009 | Cyber Warfare and Precautions Against the Effects of Attacks |
| Sklerov M. | 2009 | Responding to International Cyber Attacks as Acts of War |
| Wingfield T. | 2009 | International Law and Information Operations |
| Schreier F. | 2015 | On Cyberwarfare |
| Authors | Year | Title |
|---|---|---|
| Hare F.B. | 2019 | Precision cyber weapon systems: An important component of a responsible national security strategy? |
| Maathuis C.; Pieters W.; Van Den Berg J. | 2018 | Assessment Methodology for Collateral Damage and Military (Dis)Advantage in Cyber Operations |
| Orye E.; Maennel O.M. | 2019 | Recommendations for Enhancing the Results of Cyber Effects |
| Fanelli R.; Conti G. | 2012 | A methodology for cyber operations targeting and control of collateral damage in the context of lawful armed conflict |
| Acton J. | 2017 | Cyber weapons and precision-guided munitions |
| Bellovin S.M.; Landau S.; Lin H.S. | 2017 | Limiting the undesired impact of cyber weapons: technical requirements and policy implications |
| Lawson E.; Mačák K. | 2020 | Avoiding civilian harm from military cyber operations during armed conflicts |
| Libicki M.C. | 2021 | Cyberspace in Peace and War * |
| Maathuis C.; Pieters W.; van den Berg J. | 2021 | Decision support model for effects estimation and proportionality assessment for targeting in cyber operations |
| Hirsch C. | 2018 | Collateral damage outcomes are prominent in cyber warfare, despite targeting |
| Couretas J.M. | 2022 | Cyber Offense and Targeting |
| Smart S.J. | 2011 | Joint Targeting in Cyberspace |
| Ducheine P.; Van Haaster J. | 2014 | Fighting power, targeting and cyber operations |
| Attack Modality | Collateral Damage Risk |
|---|---|
| Replicating attack vectors | Complicated and expensive clean-up |
| Drive-by attacks | Scattershot approach, many unintended targets |
| Supply chain attacks | Scattershot approach, many unintended targets |
| Third-party DDoS (bots) | Use of third party causes unpredictable results |
| Flooding attacks (DDoS) | Spillover to adjacent systems/networks |
| Authors | Year | Title |
|---|---|---|
| Hare F.B. | 2019 | Precision cyber weapon systems: An important component of a responsible national security strategy? |
| Kaminska M. | 2021 | Restraint under conditions of uncertainty: Why the United States tolerates cyberattacks |
| Rowe N.C. | 2010 | The ethics of cyberweapons in warfare |
| Rowe N.C. | 2007 | Ethics of cyber war attacks |
| Cobb S.; Lee A. | 2014 | Malware is called malicious for a reason: The risks of weaponizing code |
| Denning D.E.; Strawser B.J. | 2014 | Moral Cyber Weapons |
| Rowe N.C. | 2016 | Challenges of Civilian Distinction in Cyberwarfare |
| Lucas Jr. G.R. | 2014 | Permissible Preventive Cyberwar: Restricting Cyber Conflict to Justified Military Targets |
| Acton J. | 2020 | Cyber Warfare & Inadvertent Escalation |
| Authors | Year | Title |
|---|---|---|
| Hare F.B. | 2019 | Precision cyber weapon systems: An important component of a responsible national security strategy? |
| Sigholm J.; Larsson E. | 2014 | Determining the utility of cyber vulnerability implantation: The heartbleed bug as a cyber operation |
| Rowe N.C. | 2016 | Challenges of Civilian Distinction in Cyberwarfare |
| Sigholm J.; Larsson E. | 2021 | Cyber Vulnerability Implantation Revisited |
| Kohler K. | 2022 | Cyberneutrality: Discouraging Collateral Damage |
| Larsson E.; Sigholm J. | 2024 | Towards Econometric Estimation of the Cost of Cyber Conflict |
| Authors | Year | Title |
|---|---|---|
| Maathuis C.; Pieters W.; Van Den Berg J. | 2018 | Assessment Methodology for Collateral Damage and Military (Dis)Advantage in Cyber Operations |
| Orye E.; Maennel O.M. | 2019 | Recommendations for Enhancing the Results of Cyber Effects |
| Maathuis C.; Chockalingam S. | 2023 | Tackling uncertainty through probabilistic modelling of proportionality in military operations |
| Maathuis C.; Pieters W.; van den Berg J. | 2020 | Decision support model for effects estimation and proportionality assessment for targeting in cyber operations |
| Maathuis C. | 2021 | Effects Assessment for Targeting Decisions Support in Military Cyber Operations |
| Authors | Year | Title |
|---|---|---|
| Raymond D.; Conti G.; Cross T.; Fanelli R. | 2013 | A control measure framework to limit collateral damage and propagation of cyber weapons |
| Bertoli G.; Marvel L. | 2017 | Cyberspace Operations Collateral Damage-Reality or Misconception? |
| Rowe N.C. | 2021 | Distinctive ethical challenges of cyberweapons |
| Authors | Year | Title |
|---|---|---|
| Smeets M. | 2018 | The Strategic Promise of Offensive Cyber Operations |
| Lawson E.; Mačák K. | 2017 | Avoiding civilian harm from military cyber operations during armed conflicts |
| Rowe N.C. | 2010 | Towards reversible cyberattacks |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Larsson, E. Collateral Damage from Offensive Cyber Operations—A Systematic Literature Review. J. Cybersecur. Priv. 2025, 5, 35. https://doi.org/10.3390/jcp5020035
Larsson E. Collateral Damage from Offensive Cyber Operations—A Systematic Literature Review. Journal of Cybersecurity and Privacy. 2025; 5(2):35. https://doi.org/10.3390/jcp5020035
Chicago/Turabian StyleLarsson, Emil. 2025. "Collateral Damage from Offensive Cyber Operations—A Systematic Literature Review" Journal of Cybersecurity and Privacy 5, no. 2: 35. https://doi.org/10.3390/jcp5020035
APA StyleLarsson, E. (2025). Collateral Damage from Offensive Cyber Operations—A Systematic Literature Review. Journal of Cybersecurity and Privacy, 5(2), 35. https://doi.org/10.3390/jcp5020035





