Attribute-Centric and Synthetic Data Based Privacy Preserving Methods: A Systematic Review
Abstract
:1. Introduction
- Resolution of privacy versus utility trade-off: How to safeguard user privacy while still allowing data miners/analysts to maximally extract the enclosed knowledge from the personal data.
- Preventing the misuse of personal data: How to enable fair and impartial decision making concerning real-world entities, and restricting target profiling (or discrimination about a minor community).
- Enhancing the quality of personal data for the well-being of societies: How to improve the quality of the data when they are either small or of low quality to enable better data mining and decision making.
- We discuss the major research tracks in the information privacy domain with a specific emphasis on attribute-centric anonymization methods that were recently developed to address the privacy versus utility trade-off.
- We discuss synthetic data generation methods and the role of synthetic data as a privacy-enhancing technology, as well as a data quality enhancement technology.
- We highlight the various privacy-enhancing technologies that are widely used to preserve the privacy of the personal data enclosed in heterogeneous formats.
- We suggest promising research tracks for future work that require the immediate attention of the privacy community amid the rapid rise in digitization.
- To the best of the authors’ knowledge, this is the first work that discusses two feature-oriented privacy-enhancing technologies (i.e., attribute-centric and synthetic data) from a much broader perspective. We hope to provide a solid foundation for future research by making a timely contribution to this line of work.
2. Privacy Preserving Data Publishing and Major Research Tracks
2.1. Privacy Preserving Data Publishing
2.2. Privacy Models
2.3. Major Research Tracks in Privacy Preserving Data Publishing
2.4. Attribute-Centric and Synthetic-Data-Based Privacy-Preserving Methods
3. Discussion on Attribute-Centric Privacy-Preserving Methods
4. Discussion on Synthetic Data-Based Privacy Methods
5. Famous Privacy Enhancing Technologies That Are Widely Used for Privacy Preservation
6. Promising Future Research and Development Directions
7. Conclusions and Future Work
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wieringa, J.; Kannan, P.K.; Ma, X.; Reutterer, T.; Risselada, H.; Skiera, B. Data analytics in a privacy-concerned world. J. Bus. Res. 2021, 122, 915–925. [Google Scholar] [CrossRef]
- Sweeney, L. Simple demographics often identify people uniquely. Health 2000, 671, 1–34. [Google Scholar]
- Majeed, A.; Lee, S. Anonymization techniques for privacy preserving data publishing: A comprehensive survey. IEEE Access 2020, 9, 8512–8545. [Google Scholar] [CrossRef]
- Sweeney, L. k-anonymity: A model for protecting privacy. Int. J. Uncertain. Fuzziness-Knowl.-Based Syst. 2002, 10, 557–570. [Google Scholar] [CrossRef]
- Machanavajjhala, A.; Kifer, D.; Gehrke, J.; Venkitasubramaniam, M. l-diversity: Privacy beyond k-anonymity. ACM Trans. Knowl. Discov. Data (TKDD) 2007, 1, 3-es. [Google Scholar] [CrossRef]
- Li, N.; Li, T.; Venkatasubramanian, S. t-closeness: Privacy beyond k-anonymity and l-diversity. In Proceedings of the 2007 IEEE 23rd International Conference on Data Engineering, Istanbul, Turkey, 17–20 April 2007; pp. 106–115. [Google Scholar]
- Dwork, C. Differential privacy: A survey of results. In International Conference on Theory and Applications of Models of Computation; Springer: Berlin/Heidelberg, Germany, 2008; pp. 1–19. [Google Scholar]
- Chen, Y.; Gan, W.; Wu, Y.; Philip, S.Y. Privacy-Preserving Federated Mining of Frequent Itemsets. Inf. Sci. 2023, 625, 504–520. [Google Scholar] [CrossRef]
- Qiu, S.; Pi, D.; Wang, Y.; Liu, Y. Novel trajectory privacy protection method against prediction attacks. Expert Syst. Appl. 2023, 213, 118870. [Google Scholar] [CrossRef]
- Kaur, H.; Hooda, N.; Singh, H. k-anonymization of social network data using Neural Network and SVM: K-NeuroSVM. J. Inf. Secur. Appl. 2023, 72, 103382. [Google Scholar] [CrossRef]
- Payton, T.; Claypoole, T. Privacy in the Age of Big Data: Recognizing Threats, Defending Your Rights, and Protecting Your Family; Rowman & Littlefield: Lanham, MD, USA, 2023. [Google Scholar]
- Majeed, A.; Hwang, S.O. When AI meets Information Privacy: The Adversarial Role of AI in Data Sharing Scenario. IEEE Access 2023, 11, 76177–76195. [Google Scholar] [CrossRef]
- Song, J.; Wang, W.; Gadekallu, T.R.; Cao, J.; Liu, Y. Eppda: An efficient privacy-preserving data aggregation federated learning scheme. IEEE Trans. Netw. Sci. Eng. 2022. [Google Scholar] [CrossRef]
- Strickland, E. Andrew Ng, AI Minimalist: The Machine-Learning Pioneer Says Small is the New Big. IEEE Spectrum. 2022, 59, 22–50. [Google Scholar] [CrossRef]
- Whang, S.E.; Roh, Y.; Song, H.; Lee, J.G. Data collection and quality challenges in deep learning: A data-centric ai perspective. VLDB J. 2023, 32, 791–813. [Google Scholar] [CrossRef]
- El Emam, K. Seven ways to evaluate the utility of synthetic data. IEEE Secur. Priv. 2020, 18, 56–59. [Google Scholar] [CrossRef]
- Li, J.; Cairns, B.J.; Li, J.; Zhu, T. Generating synthetic mixed-type longitudinal electronic health records for artificial intelligent applications. NPJ Digit. Med. 2023, 6, 98. [Google Scholar] [CrossRef] [PubMed]
- Figueira, A.; Vaz, B. Survey on synthetic data generation, evaluation methods and GANs. Mathematics 2022, 10, 2733. [Google Scholar] [CrossRef]
- James, S.; Harbron, C.; Branson, J.; Sundler, M. Synthetic data use: Exploring use cases to optimise data utility. Discov. Artif. Intell. 2021, 1, 15. [Google Scholar] [CrossRef]
- Hoang, A.T.; Carminati, B.; Ferrari, E. Protecting Privacy in Knowledge Graphs with Personalized Anonymization. IEEE Trans. Dependable Secur. Comput. 2023. [Google Scholar] [CrossRef]
- Fan, Y.; Shi, X.; Zhang, S.; Tong, Y. Anonymous Methods Based on Multi-Attribute Clustering and Generalization Constraints. Electronics 2023, 12, 1897. [Google Scholar] [CrossRef]
- Yao, L.; Wang, X.; Hu, H.; Wu, G. A Utility-aware Anonymization Model for Multiple Sensitive Attributes Based on Association Concealment. IEEE Trans. Dependable Secur. Comput. 2023. [Google Scholar] [CrossRef]
- De Pascale, D.; Cascavilla, G.; Tamburri, D.A.; Van Den Heuvel, W.J. Real-world K-Anonymity applications: The KGen approach and its evaluation in fraudulent transactions. Inf. Syst. 2023, 115, 102193. [Google Scholar] [CrossRef]
- Aldeen, Y.A.A.S.; Salleh, M.; Razzaque, M.A. A comprehensive review on privacy preserving data mining. SpringerPlus 2015, 4, 1–36. [Google Scholar] [CrossRef] [PubMed]
- Mendes, R.; Vilela, J.P. Privacy-preserving data mining: Methods, metrics, and applications. IEEE Access 2017, 5, 10562–10582. [Google Scholar] [CrossRef]
- Rathi, M.; Rajavat, A. Analysing Cryptographic and Random Data Sanitization Techniques in Privacy Preserving Data Mining. In Emerging Strategies in Research—Going Beyond Disciplinary Boundaries; Allied Publishers: New Delhi, India, 2023; Volume 83. [Google Scholar]
- Naresh, V.S.; Thamarai, M. Privacy-preserving data mining and machine learning in healthcare: Applications, challenges, and solutions. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2023, 13, e1490. [Google Scholar] [CrossRef]
- Gao, Y.; Chen, L.; Han, J.; Wu, G.; Susilo, W. IoT Privacy-preserving Data Mining with Dynamic Incentive Mechanism. IEEE Internet Things J. 2023. [Google Scholar] [CrossRef]
- Feng, J.; Yang, L.T.; Ren, B.; Zou, D.; Dong, M.; Zhang, S. Tensor recurrent neural network with differential privacy. IEEE Trans. Comput. 2023. [Google Scholar] [CrossRef]
- Karanasios, S. The pursuit of relevance and impact: A review of the immediate response of the information systems field to COVID-19. Inf. Syst. J. 2022, 32, 856–887. [Google Scholar] [CrossRef]
- Antons, D.; Breidbach, C.F.; Joshi, A.M.; Salge, T.O. Computational literature reviews: Method, algorithms, and roadmap. Organ. Res. Methods 2023, 26, 107–138. [Google Scholar] [CrossRef]
- Carvalho, T.; Moniz, N.; Faria, P.; Antunes, L. Survey on Privacy-Preserving Techniques for Data Publishing. arXiv 2022, arXiv:2201.08120. [Google Scholar]
- Pujol, D.; Machanavajjhala, A. Equity and Privacy: More Than Just a Tradeoff. IEEE Secur. Priv. 2021, 19, 93–97. [Google Scholar] [CrossRef]
- Cao, X.; Cao, Y.; Pappachan, P.; Nakamura, A.; Yoshikawa, M. Differentially Private Streaming Data Release Under Temporal Correlations via Post-processing. In IFIP Annual Conference on Data and Applications Security and Privacy; Springer Nature: Cham, Switzerland, 2023; pp. 184–200. [Google Scholar]
- Torra, V.; Navarro-Arribas, G. Attribute disclosure risk for k-anonymity: The case of numerical data. Int. J. Inf. Secur. 2023, 1–10. [Google Scholar] [CrossRef]
- Hathaliya, J.J.; Tanwar, S. An exhaustive survey on security and privacy issues in Healthcare 4.0. Comput. Commun. 2020, 153, 311–335. [Google Scholar] [CrossRef]
- Srinivasan, K.; Rathee, G.; Raja, M.R.; Jaglan, N.; Mahendiran, T.V.; Palaniswamy, T. Secure multimedia data processing scheme in medical applications. Multimed. Tools Appl. 2022, 81, 9079–9090. [Google Scholar] [CrossRef]
- Liu, B.; Ding, M.; Shaham, S.; Rahayu, W.; Farokhi, F.; Lin, Z. When machine learning meets privacy: A survey and outlook. Acm Comput. Surv. (CSUR) 2021, 54, 1–36. [Google Scholar] [CrossRef]
- Gadad, V.; Sowmyarani, C.N. Incremental Diversity: An Efficient Anonymization Technique for PPDP of Multiple Sensitive Attributes. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 3. [Google Scholar] [CrossRef]
- Stadler, T.; Oprisanu, B.; Troncoso, C. Synthetic data–anonymisation groundhog day. In Proceedings of the 31st USENIX Security Symposium (USENIX Security 22), BOSTON, MA, USA, 10–12 August 2022; pp. 1451–1468. [Google Scholar]
- Chen, L.; Zeng, L.; Mu, Y.; Chen, L. Global Combination and Clustering based Differential Privacy Mixed Data Publishing. IEEE Trans. Knowl. Data Eng. 2023. [Google Scholar] [CrossRef]
- Chakraborty, C.; Othman, S.B.; Almalki, F.A.; Sakli, H. FC-SEEDA: Fog computing-based secure and energy efficient data aggregation scheme for Internet of healthcare Things. Neural Comput. Appl. 2023, 1–17. [Google Scholar] [CrossRef]
- Li, W.; Ding, W.; Sadasivam, R.; Cui, X.; Chen, P. His-GAN: A histogram-based GAN model to improve data generation quality. Neural Netw. 2019, 119, 31–45. [Google Scholar] [CrossRef]
- Liu, H.; Tian, Y.; Peng, C.; Wu, Z. Privacy-utility equilibrium data generation based on Wasserstein generative adversarial networks. Inf. Sci. 2023, 642, 119069. [Google Scholar] [CrossRef]
- Ren, Z.; Zhu, Y.; Liu, Z.; Feng, K. Few-shot GAN: Improving the performance of intelligent fault diagnosis in severe data imbalance. IEEE Trans. Instrum. Meas. 2023, 72, 3516814. [Google Scholar] [CrossRef]
- Hongbin, F.; Zhi, Z. Privacy-Preserving Data Aggregation Scheme Based on Federated Learning for IIoT. Mathematics 2023, 11, 214. [Google Scholar] [CrossRef]
- Paul, M.; Maglaras, L.; Ferrag, M.A.; AlMomani, I. Digitization of healthcare sector: A study on privacy and security concerns. ICT Express 2023, 9, 571–588. [Google Scholar] [CrossRef]
- Muneeswari, G.; Varun, S.S.; Hegde, R.; Priya, S.S.; Shermila, P.J.; Prasanth, A. Self-diagnosis platform via IOT-based privacy preserving medical data. Meas. Sens. 2023, 25, 100636. [Google Scholar] [CrossRef]
- Xie, H.; Zheng, J.; He, T.; Wei, S.; Hu, C. TEBDS: A Trusted Execution Environment-and-Blockchain-supported IoT data sharing system. Future Gener. Comput. Syst. 2023, 140, 321–330. [Google Scholar] [CrossRef]
- Liu, C.; Chen, S.; Zhou, S.; Guan, J.; Ma, Y. A novel privacy preserving method for data publication. Inf. Sci. 2019, 501, 421–435. [Google Scholar] [CrossRef]
- Hewage, U.H.W.A.; Sinha, R.; Naeem, M.A. Privacy-preserving data (stream) mining techniques and their impact on data mining accuracy: A systematic literature review. Artif. Intell. Rev. 2023, 56, 10427–10464. [Google Scholar] [CrossRef]
- Terziyan, V.; Malyk, D.; Golovianko, M.; Branytskyi, V. Encryption and Generation of Images for Privacy-Preserving Machine Learning in Smart Manufacturing. Procedia Comput. Sci. 2023, 217, 91–101. [Google Scholar] [CrossRef]
- Qin, C.; Wu, L.; Meng, W.; Xu, Z.; Li, S.; Wang, H. A privacy-preserving blockchain-based tracing model for virus-infected people in cloud. Expert Syst. Appl. 2023, 211, 118545. [Google Scholar] [CrossRef]
- Kumuthini, J.; Zass, L.; Chaouch, M.; Fadlelmola, F.M.; Mulder, N.; Radouani, F.; Ras, V.; Samtal, C.; Tchamga, M.S.; Sathan, D.; et al. Genomics Data Sharing; Academic Press: Cambridge, MA, USA, 2023; pp. 111–135. [Google Scholar]
- Yang, X.; Yi, X.; Kelarev, A.; Rylands, L.; Lin, Y.; Ryan, J. Protecting Private Information for Two Classes of Aggregated Database Queries. Informatics 2022, 9, 66. [Google Scholar] [CrossRef]
- Lin, C.-H.; Yu, C.-M.; Huang, C.-Y. DPView: Differentially Private Data Synthesis Through Domain Size Information. IEEE Internet Things J. 2022, 9, 15886–15900. [Google Scholar] [CrossRef]
- Sei, Y.; Andrew, J.; Okumura, H.; Ohsuga, A. Privacy-preserving collaborative data collection and analysis with many missing values. IEEE Trans. Dependable Secur. Comput. 2023, 20, 2158–2173. [Google Scholar] [CrossRef]
- Krishna, S.; Murthy, U.V. Evolutionary tree-based quasi identifier and federated gradient privacy preservations over big healthcare data. Int. J. Electr. Comput. Eng. 2022, 12, 903. [Google Scholar] [CrossRef]
- Chong, K.M.; Malip, A. Bridging unlinkability and data utility: Privacy preserving data publication schemes for healthcare informatics. Comput. Commun. 2022, 191, 194–207. [Google Scholar] [CrossRef]
- Breger, A.; Selby, I.; Roberts, M.; Babar, J.; Gkrania-Klotsas, E.; Preller, J.; Sánchez, L.E.; Rudd, J.H.F.; Aston, J.A.D.; Weir-McCall, J.R. A pipeline to further enhance quality, integrity and reusability of the NCCID clinical data. Sci. Data 2023, 10, 493. [Google Scholar] [CrossRef] [PubMed]
- Majeed, A. Attribute-centric anonymization scheme for improving user privacy and utility of publishing e-health data. J. King Saud-Univ.-Comput. Inf. Sci. 2019, 31, 426–435. [Google Scholar] [CrossRef]
- Onesimu, J.A.; Karthikeyan, J.; Eunice, J.; Pomplun, M.; Dang, H. Privacy preserving attribute-focused anonymization scheme for healthcare data publishing. IEEE Access 2022, 10, 86979–86997. [Google Scholar] [CrossRef]
- Hui, T.; Wee-Chung, L.A.; Earnest, F. A scheme of hybrid privacy protection and utility levels for medical data. arXiv 2022, arXiv:2204.13880. [Google Scholar]
- Khan, M.S.; Anjum, A.; Saba, T.; Rehman, A.; Tariq, U. Improved generalization for secure personal data publishing using deviation. IT Prof. 2021, 23, 75–80. [Google Scholar] [CrossRef]
- Zhang, S.; Li, X. Differential privacy medical data publishing method based on attribute correlation. Sci. Rep. 2022, 12, 15725. [Google Scholar] [CrossRef]
- Sadhya, D.; Chakraborty, B. Quantifying the Effects of Anonymization Techniques over Micro-databases. IEEE Trans. Emerg. Top. Comput. 2022, 10, 1979–1992. [Google Scholar] [CrossRef]
- Srijayanthi, S.; Sethukarasi, T. Design of privacy preserving model based on clustering involved anonymization along with feature selection. Comput. Secur. 2023, 126, 103027. [Google Scholar] [CrossRef]
- Canbay, Y.; Sagiroglu, S.; Vural, Y. A Mondrian-based Utility Optimization Model for Anonymization. In Proceedings of the 2019 4th International Conference on Computer Science and Engineering (UBMK), Samsun, Turkey, 11–15 September 2019; pp. 709–714. [Google Scholar]
- Arca, S.; Hewett, R. Analytics on anonymity for privacy retention in smart health data. Future Internet 2021, 13, 274. [Google Scholar] [CrossRef]
- Zouinina, S.; Bennani, Y.; Rogovschi, N.; Lyhyaoui, A. Data anonymization through collaborative multi-view microaggregation. J. Intell. Syst. 2020, 30, 327–345. [Google Scholar] [CrossRef]
- Yan, Y.; Eyeleko, A.H.; Mahmood, A.; Li, J.; Dong, Z.; Xu, F. Privacy preserving dynamic data release against synonymous linkage based on microaggregation. Sci. Rep. 2022, 12, 2352. [Google Scholar] [CrossRef] [PubMed]
- Lee, S.; Shin, W.Y. Utility-Embraced Microaggregation for Machine Learning Applications. IEEE Access 2022, 10, 64535–64546. [Google Scholar] [CrossRef]
- Yan, Y.; Sun, Z.; Mahmood, A.; Xu, F.; Dong, Z.; Sheng, Q.Z. Achieving Differential Privacy Publishing of Location-Based Statistical Data Using Grid Clustering. ISPRS Int. J. Geo-Inf. 2022, 11, 404. [Google Scholar] [CrossRef]
- Thanga Revathi, S.; Gayathri, A.; Kalaivani, J.; Christo, M.S.; Pelusi, D.; Azees, M. Cloud-Assisted Privacy-Preserving Method for Healthcare Using Adaptive Fractional Brain Storm Integrated Whale Optimization Algorithm. Secur. Commun. Netw. 2021, 2021, 6210054. [Google Scholar] [CrossRef]
- Anand, K.; Vijayaraj, A.; Vijay Anand, M. Privacy preserving framework using Gaussian mutation based firebug optimization in cloud computing. J. Supercomput. 2022, 1, 1–24. [Google Scholar]
- Anand, K.; Vijayaraj, A.; Vijay Anand, M. An enhanced bacterial foraging optimization algorithm for secure data storage and privacy-preserving in cloud. Peer-to-Peer Netw. Appl. 2022, 15, 2007–2020. [Google Scholar] [CrossRef]
- Canbay, Y.; Vural, Y.; Sagiroglu, Ş. OAN: Outlier record-oriented utility-based privacy preserving model. J. Fac. Eng. Archit. Gazi Univ. 2020, 35, 355–368. [Google Scholar]
- Onesimu, J.A.; Karthikeyan, J.; Sei, Y. An efficient clustering-based anonymization scheme for privacy-preserving data collection in IoT based healthcare services. Peer-to-Peer Netw. Appl. 2021, 14, 1629–1649. [Google Scholar] [CrossRef]
- Xie, M.; Huang, M.; Bai, Y.; Hu, Z. The anonymization protection algorithm based on fuzzy clustering for the ego of data in the internet of things. J. Electr. Comput. Eng. 2017, 2017, 2970673. [Google Scholar] [CrossRef]
- Yang, L.; Chen, X.; Luo, Y.; Lan, X.; Wang, W. IDEA: A utility-enhanced approach to incomplete data stream anonymization. Tsinghua Sci. Technol. 2021, 27, 127–140. [Google Scholar] [CrossRef]
- Li, H.; Guo, F.; Zhang, W.; Wang, J.; Xing, J. (a, k)-Anonymous scheme for privacy-preserving data collection in IoT-based healthcare services systems. J. Med. Syst. 2018, 42, 1–9. [Google Scholar] [CrossRef]
- Altameem, A.; Kovtun, V.; Al-Ma’aitah, M.; Altameem, T.; Fouad, H.; Youssef, A.E. Patient’s data privacy protection in medical healthcare transmission services using back propagation learning. Comput. Electr. Eng. 2022, 102, 108087. [Google Scholar] [CrossRef]
- Nayahi, J.J.; Kavitha, V. Privacy and utility preserving data clustering for data anonymization and distribution on Hadoop. Future Gener. Comput. Syst. 2017, 74, 393–408. [Google Scholar] [CrossRef]
- Ashkouti, F.; Khamforoosh, K.; Sheikhahmadi, A.; Khamfroush, H. DHkmeans-ℓ-diversity: Distributed hierarchical K-means for satisfaction of the ℓ-diversity privacy model using Apache Spark. J. Supercomput. 2022, 78, 2616–2650. [Google Scholar] [CrossRef]
- Solanki, P.; Garg, S.; Chhikaniwala, H. Preserve Privacy on Streaming Data During the Process of Mining Using User Defined Delta Value. In Innovative Data Communication Technologies and Application: Proceedings of ICIDCA 2021, Singapore, 24 February 2022; Springer Nature Singapore: Singapore, 2022; pp. 197–212. [Google Scholar]
- Eyupoglu, C.; Aydin, M.A.; Zaim, A.H.; Sertbas, A. An efficient big data anonymization algorithm based on chaos and perturbation techniques. Entropy 2018, 20, 373. [Google Scholar]
- Liu, F.; Cheng, Z.; Chen, H.; Wei, Y.; Nie, L.; Kankanhalli, M. Privacy-preserving synthetic data generation for recommendation systems. In Proceedings of the 45th International ACM SIGIR Conference on Research and Development in Information Retrieval, Madrid, Spain, 6 July 2022; pp. 1379–1389. [Google Scholar]
- Rankin, D.; Black, M.; Bond, R.; Wallace, J.; Mulvenna, M.; Epelde, G. Reliability of supervised machine learning using synthetic data in health care: Model to preserve privacy for data sharing. JMIR Med. Inform. 2020, 8, e18910. [Google Scholar] [CrossRef]
- Chen, R.J.; Lu, M.Y.; Chen, T.Y.; Williamson, D.F.; Mahmood, F. Synthetic data in machine learning for medicine and healthcare. Nat. Biomed. Eng. 2021, 5, 493–497. [Google Scholar] [CrossRef]
- Hahn, W.; Schütte, K.; Schultz, K.; Wolkenhauer, O.; Sedlmayr, M.; Schuler, U.; Eichler, M.; Bej, S.; Wolfien, M. Contribution of Synthetic Data Generation towards an Improved Patient Stratification in Palliative Care. J. Pers. Med. 2022, 12, 1278. [Google Scholar] [CrossRef]
- Gonzales, A.; Guruswamy, G.; Smith, S.R. Synthetic data in health care: A narrative review. PLoS Digit. Health 2023, 2, e0000082. [Google Scholar] [CrossRef] [PubMed]
- Chen, X.; Wang, C.; Yang, Q.; Hu, T.; Jiang, C. Locally differentially private high-dimensional data synthesis. Sci. China Inf. Sci. 2023, 66, 1–8. [Google Scholar] [CrossRef]
- De Cristofaro, E. What Is Synthetic Data? The Good, The Bad, and The Ugly. arXiv 2023, arXiv:2303.01230. [Google Scholar]
- Harder, F.; Adamczewski, K.; Park, M. Dp-merf: Differentially private mean embeddings with randomfeatures for practical privacy-preserving data generation. In Proceedings of the International Conference on Artificial Intelligence and Statistics, San Diego, CA, USA, 18 March 2021; pp. 1819–1827. [Google Scholar]
- Lee, J.; Kim, M.; Jeong, Y.; Ro, Y. Differentially Private Normalizing Flows for Synthetic Tabular Data Generation. In Proceedings of the AAAI Conference on Artificial Intelligence, Palo Alto, CA, USA, 28 June 2022; Volume 36, pp. 7345–7353. [Google Scholar]
- Jälkö, J.; Lagerspetz, E.; Haukka, J.; Tarkoma, S.; Honkela, A.; Kaski, S. Privacy-preserving data sharing via probabilistic modeling. Patterns 2021, 2, 100271. [Google Scholar] [CrossRef]
- Yale, A.; Dash, S.; Dutta, R.; Guyon, I.; Pavao, A.; Bennett, K.P. Generation and evaluation of privacy preserving synthetic health data. Neurocomputing 2020, 416, 244–255. [Google Scholar] [CrossRef]
- Lenatti, M.; Paglialonga, A.; Orani, V.; Ferretti, M.; Mongelli, M. Characterization of Synthetic Health Data Using Rule-Based Artificial Intelligence Models. IEEE J. Biomed. Health Inform. 2023, 27, 3760–3769. [Google Scholar] [CrossRef]
- Bhanot, K.; Pedersen, J.; Guyon, I.; Bennett, K.P. Investigating synthetic medical time-series resemblance. Neurocomputing 2022, 494, 368–378. [Google Scholar] [CrossRef]
- Nikolentzos, G.; Vazirgiannis, M.; Xypolopoulos, C.; Lingman, M.; Brandt, E. Synthetic electronic health records generated with variational graph autoencoders. NPJ Digit. Med. 2023, 6, 83. [Google Scholar] [CrossRef]
- Hernandez, M.; Epelde, G.; Beristain, A.; Álvarez, R.; Molina, C.; Larrea, X.; Alberdi, A.; Timoleon, M.; Bamidis, P.; Konstantinidis, E. Incorporation of synthetic data generation techniques within a controlled data processing workflow in the health and wellbeing domain. Electronics 2022, 11, 812. [Google Scholar] [CrossRef]
- Kuo, N.I.; Polizzotto, M.N.; Finfer, S.; Garcia, F.; Sönnerborg, A.; Zazzi, M.; Böhm, M.; Kaiser, R.; Jorm, L.; Barbieri, S. The Health Gym: Synthetic health-related datasets for the development of reinforcement learning algorithms. Sci. Data 2022, 9, 693. [Google Scholar] [CrossRef]
- Rodriguez-Almeida, A.J.; Fabelo, H.; Ortega, S.; Deniz, A.; Balea-Fernandez, F.J.; Quevedo, E.; Soguero-Ruiz, C.; Wägner, A.M.; Callico, G.M. Synthetic Patient Data Generation and Evaluation in Disease Prediction Using Small and Imbalanced Datasets. IEEE J. Biomed. Health Inform. 2022, 27, 2670–2680. [Google Scholar] [CrossRef]
- Banerjee, S.; Bishop, T.R. dsSynthetic: Synthetic data generation for the DataSHIELD federated analysis system. BMC Res. Notes 2022, 15, 230. [Google Scholar] [CrossRef] [PubMed]
- Larrea, X.; Hernandez, M.; Epelde, G.; Beristain, A.; Molina, C.; Alberdi, A.; Rankin, D.; Bamidis, P.; Konstantinidis, E. Synthetic Subject Generation with Coupled Coherent Time Series Data. Eng. Proc. 2022, 18, 7. [Google Scholar]
- Venugopal, R.; Shafqat, N.; Venugopal, I.; Tillbury, B.M.; Stafford, H.D.; Bourazeri, A. Privacy preserving Generative Adversarial Networks to model Electronic Health Records. Neural Netw. 2022, 153, 339–348. [Google Scholar] [CrossRef]
- Yoshikawa, H.; Uchiyama, A. Privacy-preserving data augmentation for thermal sensation dataset based on variational autoencoder. In Proceedings of the 9th ACM International Conference on Systems for Energy-Efficient Buildings, Cities, and Transportation, Boston, MA, USA, 9 November 2022; pp. 286–287. [Google Scholar]
- Hyun, J.; Lee, Y.; Son, H.M.; Lee, S.H.; Pham, V.; Park, J.U.; Chung, T.M. Synthetic Data Generation System for AI-Based Diabetic Foot Diagnosis. SN Comput. Sci. 2021, 2, 345. [Google Scholar] [CrossRef]
- Zhang, A.; Xing, L.; Zou, J.; Wu, J.C. Shifting machine learning for healthcare from development to deployment and from models to data. Nat. Biomed. Eng. 2022, 4, 1–6. [Google Scholar] [CrossRef] [PubMed]
- Yale, A.; Dash, S.; Bhanot, K.; Guyon, I.; Erickson, J.S.; Bennett, K.P. Synthesizing quality open data assets from Private Health Research Studies. In Business Information Systems Workshops: BIS 2020 International Workshops, Colorado Springs, CO, USA, 8–10 June 2020; Springer: Cham, Switzerland; pp. 324–335.
- Narteni, S.; Orani, V.; Ferrari, E.; Verda, D.; Cambiaso, E.; Mongelli, M. A New XAI-based Evaluation of Generative Adversarial Networks for IMU Data Augmentation. In Proceedings of the 2022 IEEE International Conference on E-health Networking, Application & Services (HealthCom), Genoa, Italy, 17–19 October 2022; pp. 167–172. [Google Scholar]
- Raveendran, R.; Raj, E.D. Deep Generative Models Under GAN: Variants, Applications, and Privacy Issues. In Proceedings of the 7th International Conference on Information System Design and Intelligent Applications (India 2022), Hyderabad, India, 25–26 February 2022; Volume 28, pp. 93–105. [Google Scholar]
- Li, M.; Zhuang, D.; Chang, J.M. MC-GEN: Multi-level clustering for private synthetic data generation. Knowl.-Based Syst. 2023, 21, 110239. [Google Scholar] [CrossRef]
- Shahani, S.; Abraham, J. Techniques for Privacy-Preserving Data Aggregation in an Untrusted Distributed Environment. In Proceedings of the 6th Joint International Conference on Data Science & Management of Data (10th ACM IKDD CODS and 28th COMAD), Mumbai, India, 4–7 January 2023; pp. 286–287. [Google Scholar]
- Hindistan, Y.S.; Yetkin, E.F. A Hybrid Approach with GAN and DP for Privacy Preservation of IIoT Data. IEEE Access. 2023, 1, 5837–5849. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhu, Y.; Zhou, Y.; Yuan, J. Frequency Estimation Mechanisms under (ϵ, δ)-Utility-optimized Local Differential Privacy. IEEE Trans. Emerg. Top. Comput. 2023. [Google Scholar] [CrossRef]
- Nair, A.K.; Sahoo, J.; Raj, E.D. Privacy preserving Federated Learning framework for IoMT based big data analysis using edge computing. Comput. Stand. Interfaces 2023, 4, 103720. [Google Scholar] [CrossRef]
- Zhang, Z.; Xu, X.; Xiao, F. LGAN-DP: A novel differential private publication mechanism of trajectory data. Future Gener. Comput. Syst. 2023, 141, 692–703. [Google Scholar] [CrossRef]
- Duan, S.; Liu, C.; Han, P.; Jin, X.; Zhang, X.; He, T.; Pan, H.; Xiang, X. HT-Fed-GAN: Federated Generative Model for Decentralized Tabular Data Synthesis. Entropy 2023, 25, 88. [Google Scholar] [CrossRef]
- Cheng, K.; Tahir, R.; Eric, L.K.; Li, M. An analysis of generative adversarial networks and variants for image synthesis on MNIST dataset. Multimed. Tools Appl. 2020, 79, 13725–13752. [Google Scholar] [CrossRef]
- Castelli, M.; Manzoni, L. Generative models in artificial intelligence and their applications. Appl. Sci. 2022, 12, 4127. [Google Scholar] [CrossRef]
- Ma, Z.; Wang, J.; Gai, K.; Duan, P.; Zhang, Y.; Luo, S. Fully homomorphic encryption-based privacy-preserving scheme for cross edge blockchain network. J. Syst. Archit. 2023, 134, 102782. [Google Scholar] [CrossRef]
- Zhang, M.; Huang, S.; Shen, G.; Wang, Y. PPNNP: A privacy-preserving neural network prediction with separated data providers using multi-client inner-product encryption. Comput. Stand. Interfaces 2023, 84, 103678. [Google Scholar] [CrossRef]
- Li, X.; Xu, L.; Zhang, H.; Xu, Q. Differential privacy preservation for graph auto-encoders: A novel anonymous graph publishing model. Neurocomputing 2023, 521, 113–125. [Google Scholar] [CrossRef]
- Guo, S.; Wang, X.; Long, S.; Liu, H.; Hai, L.; Sam, T.H. A federated learning scheme meets dynamic differential privacy. CAAI Trans. Intell. Technol. 2023. [Google Scholar] [CrossRef]
- Liu, X.; Chen, Y. Group effect-based privacy-preserving data aggregation for mobile crowdsensing. Comput. Netw. 2023, 222, 109507. [Google Scholar] [CrossRef]
- Chen, Q.; Ni, Z.; Zhu, X.; Xia, P. Differential privacy histogram publishing method based on dynamic sliding window. Front. Comput. Sci. 2023, 17, 174809. [Google Scholar] [CrossRef]
- Gao, H.; He, N.; Gao, T. SVeriFL: Successive verifiable federated learning with privacy-preserving. Inf. Sci. 2023, 622, 98–114. [Google Scholar] [CrossRef]
- Ouyang, L.; Wang, F.-Y.; Tian, Y.; Jia, X.; Qi, H.; Wang, G. Artificial identification: A novel privacy framework for federated learning based on blockchain. IEEE Trans. Comput. Soc. Syst. 2023. [Google Scholar] [CrossRef]
- Singh, S.K.; Yang, L.T.; Park, J.H. FusionFedBlock: Fusion of blockchain and federated learning to preserve privacy in industry 5.0. Inf. Fusion 2023, 90, 233–240. [Google Scholar] [CrossRef]
- Liu, M.; Zhang, Z.; Chai, W.; Wang, B. Privacy-preserving COVID-19 contact tracing solution based on blockchain. Comput. Stand. Interfaces 2023, 83, 103643. [Google Scholar] [CrossRef] [PubMed]
- Raveendran, A.; Dhanapal, R. A non-interactive privacy preserved training technique based on hybrid deep learning. Optik 2023, 273, 170420. [Google Scholar] [CrossRef]
- Cai, H.; Zhu, X.; Wen, P.; Han, W.; Wu, L. A Survey of Few-Shot Learning for Image Classification of Aerial Objects. In China Aeronautical Science and Technology Youth Science Forum; Springer Nature: Singapore, 2023; pp. 570–582. [Google Scholar]
- Zhang, D.; Ren, L.; Shafiq, M.; Gu, Z. A Privacy Protection Framework for Medical Image Security without Key Dependency Based on Visual Cryptography and Trusted Computing. Comput. Intell. Neurosci. 2023, 2023, 6758406. [Google Scholar] [CrossRef]
- Huang, P.H.; Tu, C.H.; Chung, S.M.; Wu, P.Y.; Tsai, T.L.; Lin, Y.A.; Dai, C.Y.; Liao, T.Y. SecureTVM: A TVM-Based Compiler Framework for Selective Privacy-Preserving Neural Inference. ACM Trans. Des. Autom. Electron. Syst. 2023, 28, 1–28. [Google Scholar] [CrossRef]
- Chen, K. Confidential High-Performance Computing in the Public Cloud. IEEE Internet Comput. 2023, 27, 24–32. [Google Scholar] [CrossRef]
- Abdul-Jabbar, M.D.; Aldeen, Y.A. State-of-the-Art in Data Integrity and Privacy-Preserving in Cloud Computing. J. Eng. 2023, 29, 42–60. [Google Scholar] [CrossRef]
- Tall, A.M.; Zou, C.C. A Framework for Attribute-Based Access Control in Processing Big Data with Multiple Sensitivities. Appl. Sci. 2023, 13, 1183. [Google Scholar] [CrossRef]
- Kunchala, A.; Bouroche, M.; Schoen-Phelan, B. Towards A Framework for Privacy-Preserving Pedestrian Analysis. In Proceedings of the IEEE/CVF Winter Conference on Applications of Computer Vision, Waikoloa, HI, USA, 2–7 January 2023; pp. 4370–4380. [Google Scholar]
- Tai, R.; Lin, L.; Zhu, Y.; Su, R. Privacy-preserving co-synthesis against sensor–actuator eavesdropping intruder. Automatica 2023, 150, 110860. [Google Scholar] [CrossRef]
- Kulkarni, Y.R.; Jagdale, B.; Sugave, S.R. Optimized key generation-based privacy preserving data mining model for secure data publishing. Adv. Eng. Softw. 2023, 175, 103332. [Google Scholar] [CrossRef]
- Saleous, H.; Ismail, M.; AlDaajeh, S.H.; Madathil, N.; Alrabaee, S.; Choo, K.-K.R.; Al-Qirim, N. COVID-19 pandemic and the cyberthreat landscape: Research challenges and opportunities. Digit. Commun. Netw. 2023, 9, 211–222. [Google Scholar] [CrossRef] [PubMed]
- Feng, Y.; Luo, Y.; Yang, J. Cross-platform privacy-preserving CT image COVID-19 diagnosis based on source-free domain adaptation. Knowl.-Based Syst. 2023, 23, 110324. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Luo, Y.; Liu, L.; Fu, S. pCOVID: A Privacy-Preserving COVID-19 Inference Framework. In Algorithms and Architectures for Parallel Processing: Proceedings of the 22nd International Conference, ICA3PP 2022, Copenhagen, Denmark, 10–12 October 2022; Springer Nature: Cham, Switzerland, 2023; pp. 21–42. [Google Scholar]
- Dhasarathan, C.; Hasan, M.K.; Islam, S.; Abdullah, S.; Mokhtar, U.A.; Javed, A.R.; Goundar, S. COVID-19 health data analysis and personal data preserving: A homomorphic privacy enforcement approach. Comput. Commun. 2023, 199, 87–97. [Google Scholar] [CrossRef]
- Sei, Y.; Ohsuga, A. Private true data mining: Differential privacy featuring errors to manage Internet-of-Things data. IEEE Access 2022, 10, 8738–8757. [Google Scholar] [CrossRef]
- Boubiche, D.E.; Imran, M.; Maqsood, A.; Shoaib, M. Mobile crowd sensing–taxonomy, applications, challenges, and solutions. Comput. Hum. Behav. 2019, 101, 352–370. [Google Scholar] [CrossRef]
- Ota, F.K.; Meira, J.A.; Frank, R.; State, R. Towards Privacy Preserving Data Centric Super App. In Proceedings of the 2020 Mediterranean Communication and Computer Networking Conference (MedComNet), Arona, Italy, 17–19 June 2020; pp. 1–4. [Google Scholar]
- Wang, W.; Li, X.; Qiu, X.; Zhang, X.; Zhao, J.; Brusic, V. A privacy preserving framework for federated learning in smart healthcare systems. Inf. Process. Manag. 2023, 60, 103167. [Google Scholar] [CrossRef]
- Muthukrishnan, G.; Kalyani, S. Differential Privacy with Higher Utility through Non-identical Additive Noise. arXiv 2023, arXiv:2302.03511. [Google Scholar]
- Majeed, A.; Hwang, S.O. Quantifying the Vulnerability of Attributes for Effective Privacy Preservation Using Machine Learning. IEEE Access. 2023, 11, 4400–4411. [Google Scholar] [CrossRef]
- Dina, A.S.; Siddique, A.B.; Manivannan, D. Effect of Balancing Data Using Synthetic Data on the Performance of Machine Learning Classifiers for Intrusion Detection in Computer Networks. IEEE Access 2022, 10, 96731–96747. [Google Scholar] [CrossRef]
- Zhao, J.; Cheong, K.H. Obfuscating community structure in complex network with evolutionary divide-and-conquer strategy. IEEE Trans. Evol. Comput. 2023. [Google Scholar] [CrossRef]
- Pan, Y.L.; Chen, J.C.; Wu, J.L. Towards a Controllable and Reversible Privacy Protection System for Facial Images through Enhanced Multi-Factor Modifier Networks. Entropy 2023, 25, 272. [Google Scholar] [CrossRef]
- Slavković, A.; Seeman, J. Statistical data privacy: A song of privacy and utility. Annu. Rev. Stat. Its Appl. 2023, 10, 189–218. [Google Scholar] [CrossRef]
- Fu, N.; Ni, W.; Hu, H.; Zhang, S. Multidimensional grid-based clustering with local differential privacy. Inf. Sci. 2023, 623, 402–420. [Google Scholar] [CrossRef]
- Chen, J.; Xue, J.; Wang, Y.; Huang, L.; Baker, T.; Zhou, Z. Privacy-Preserving and Traceable Federated Learning for data sharing in industrial IoT applications. Expert Syst. Appl. 2023, 213, 119036. [Google Scholar] [CrossRef]
- Brunotte, W.; Specht, A.; Chazette, L.; Schneider, K. Privacy explanations—A means to end-user trust. J. Syst. Softw. 2023, 195, 111545. [Google Scholar] [CrossRef]
- Stergiou, C.L.; Bompoli, E.; Psannis, K.E. Security and Privacy Issues in IoT-Based Big Data Cloud Systems in a Digital Twin Scenario. Appl. Sci. 2023, 13, 758. [Google Scholar] [CrossRef]
- Dhirani, L.L.; Mukhtiar, N.; Chowdhry, B.S.; Newe, T. Ethical Dilemmas and Privacy Issues in Emerging Technologies: A Review. Sensors 2023, 23, 1151. [Google Scholar] [CrossRef]

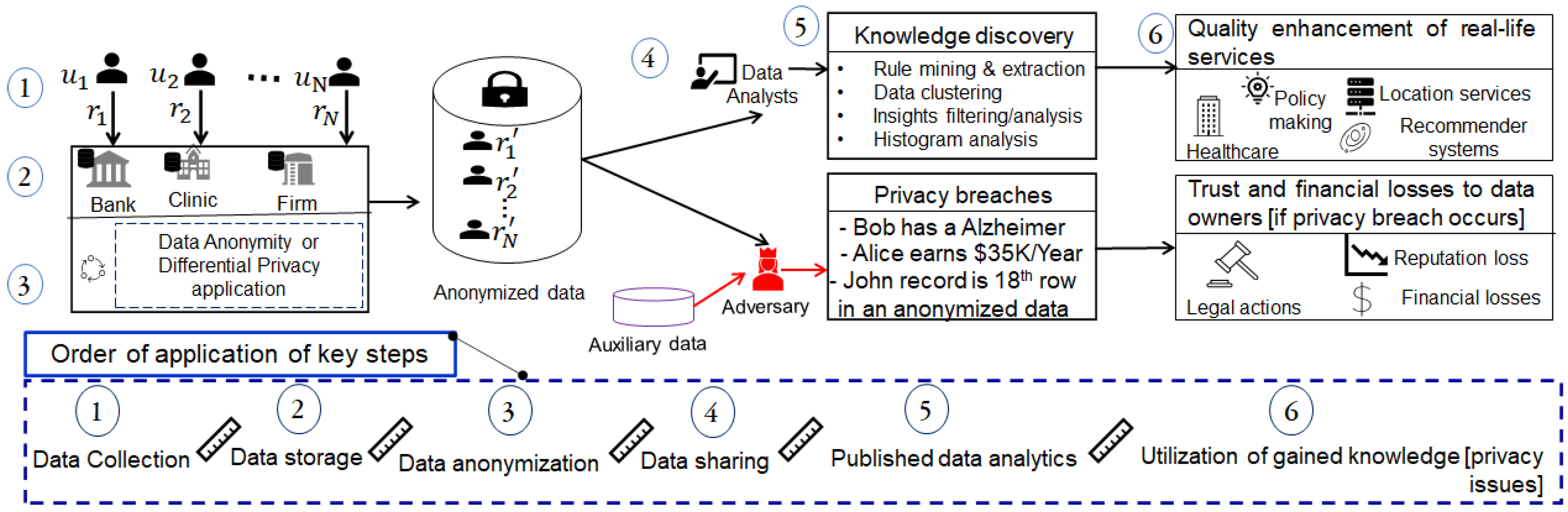

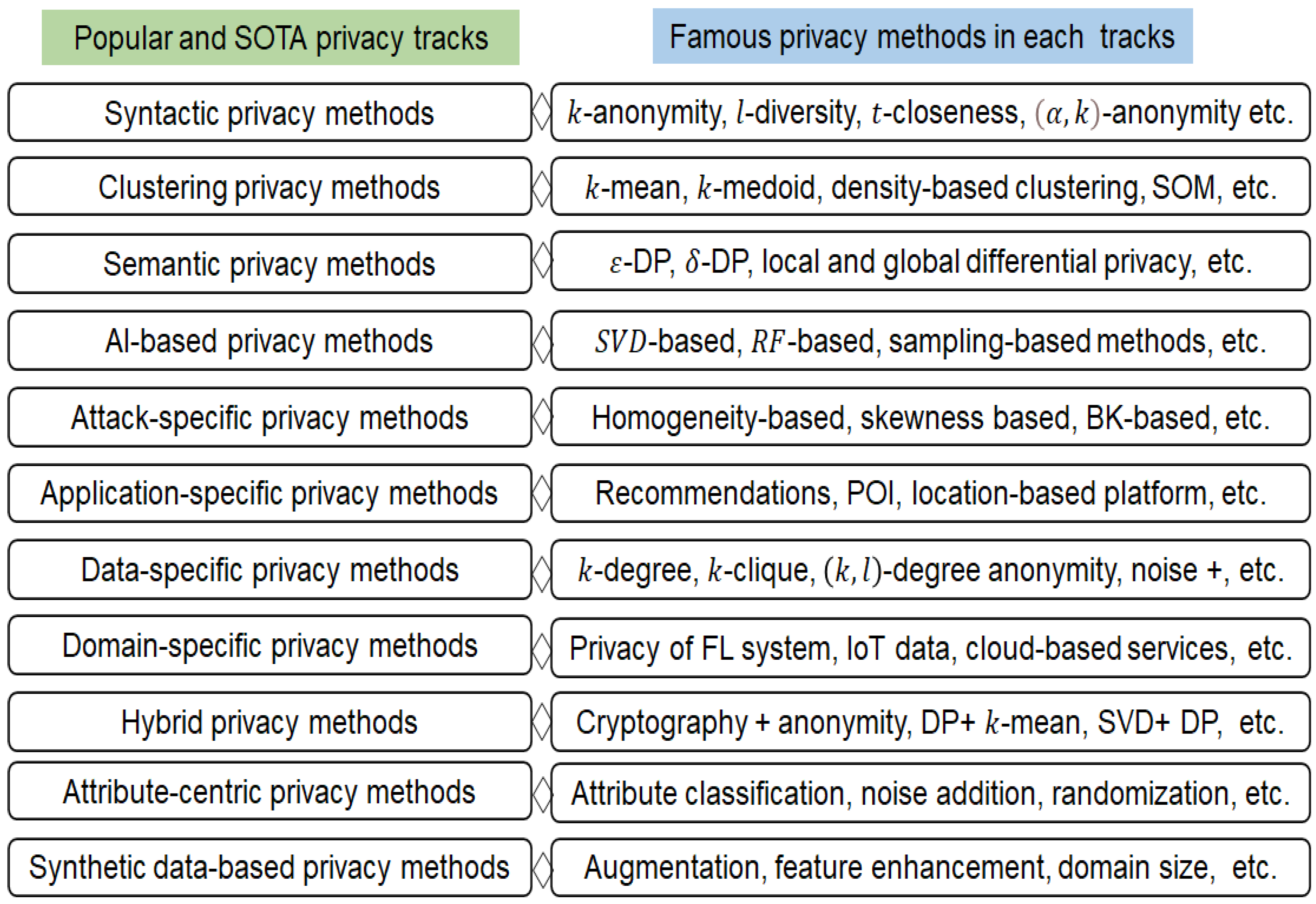
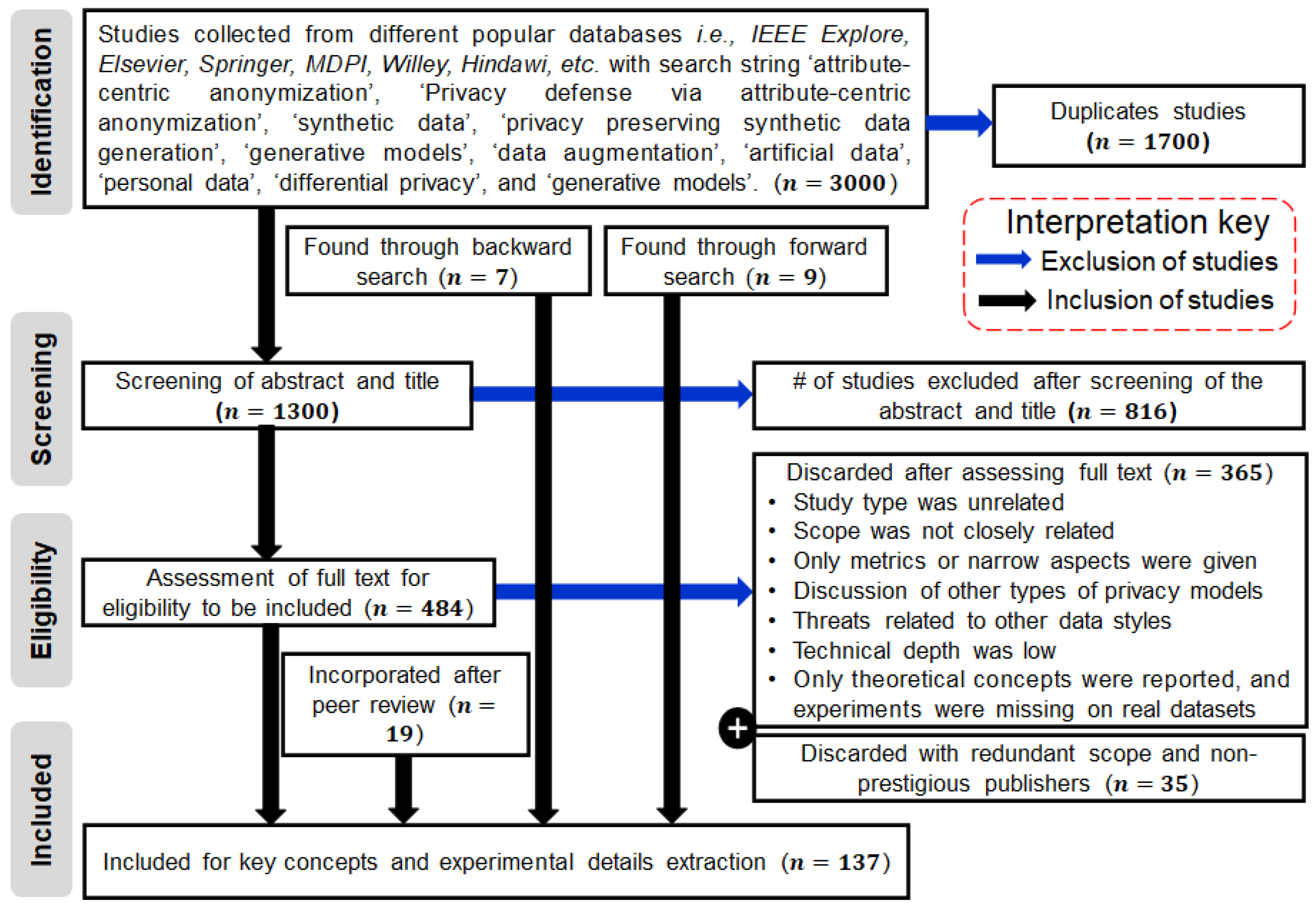

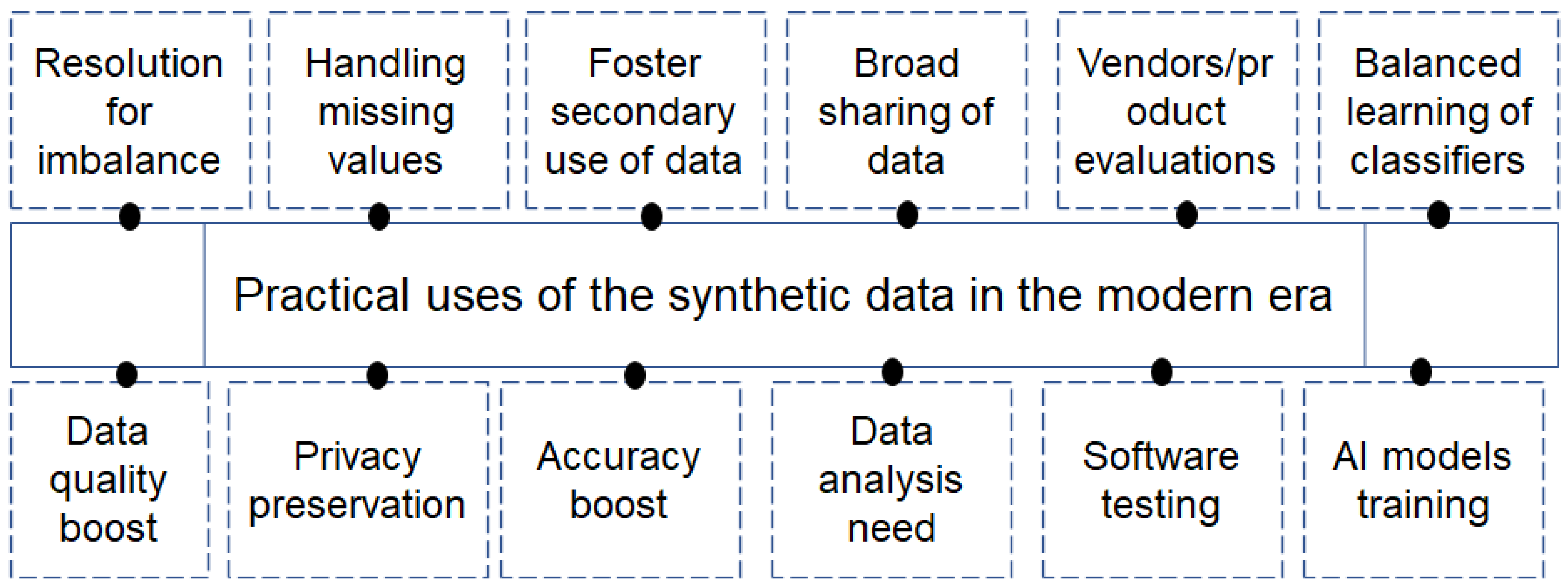
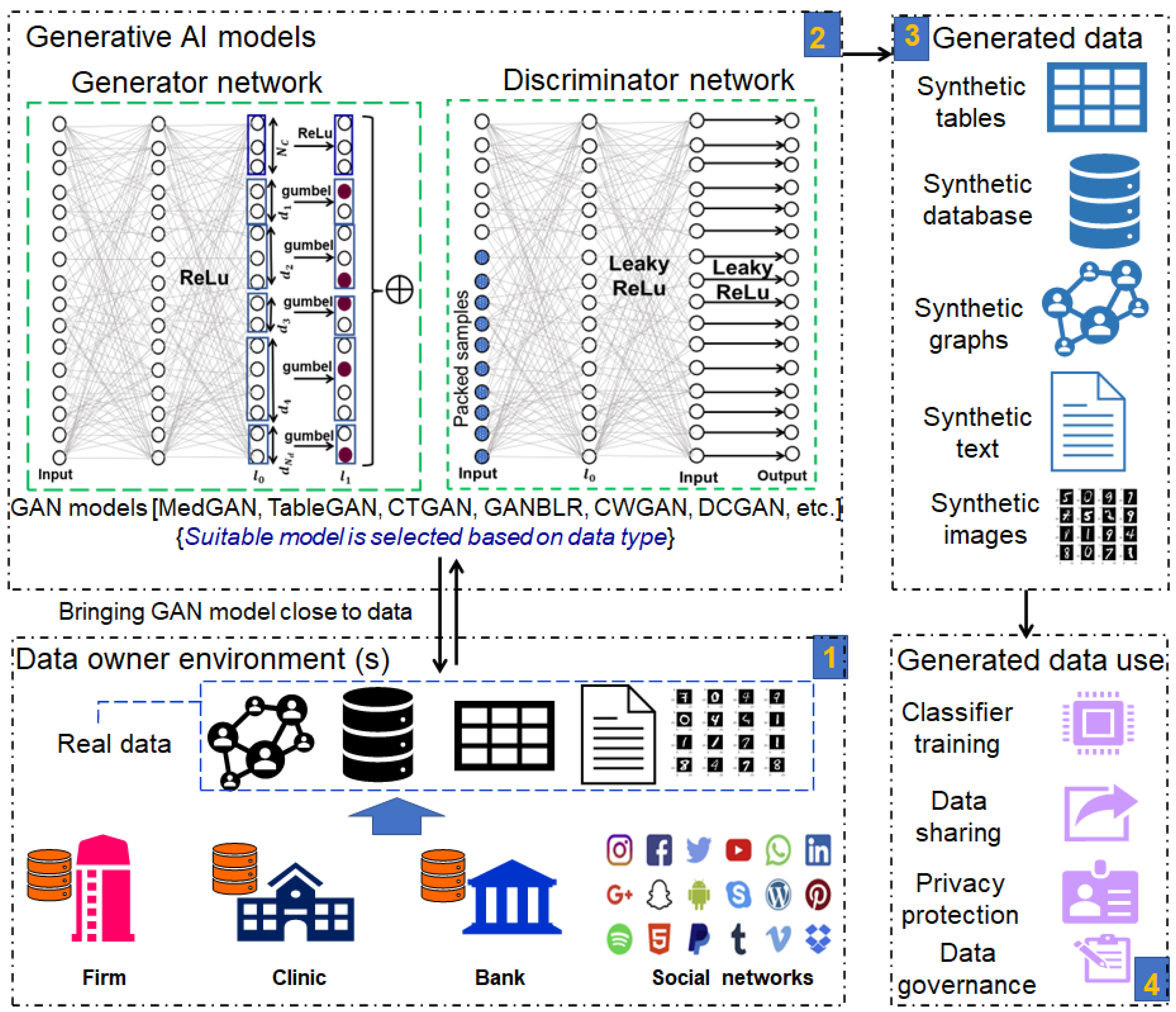
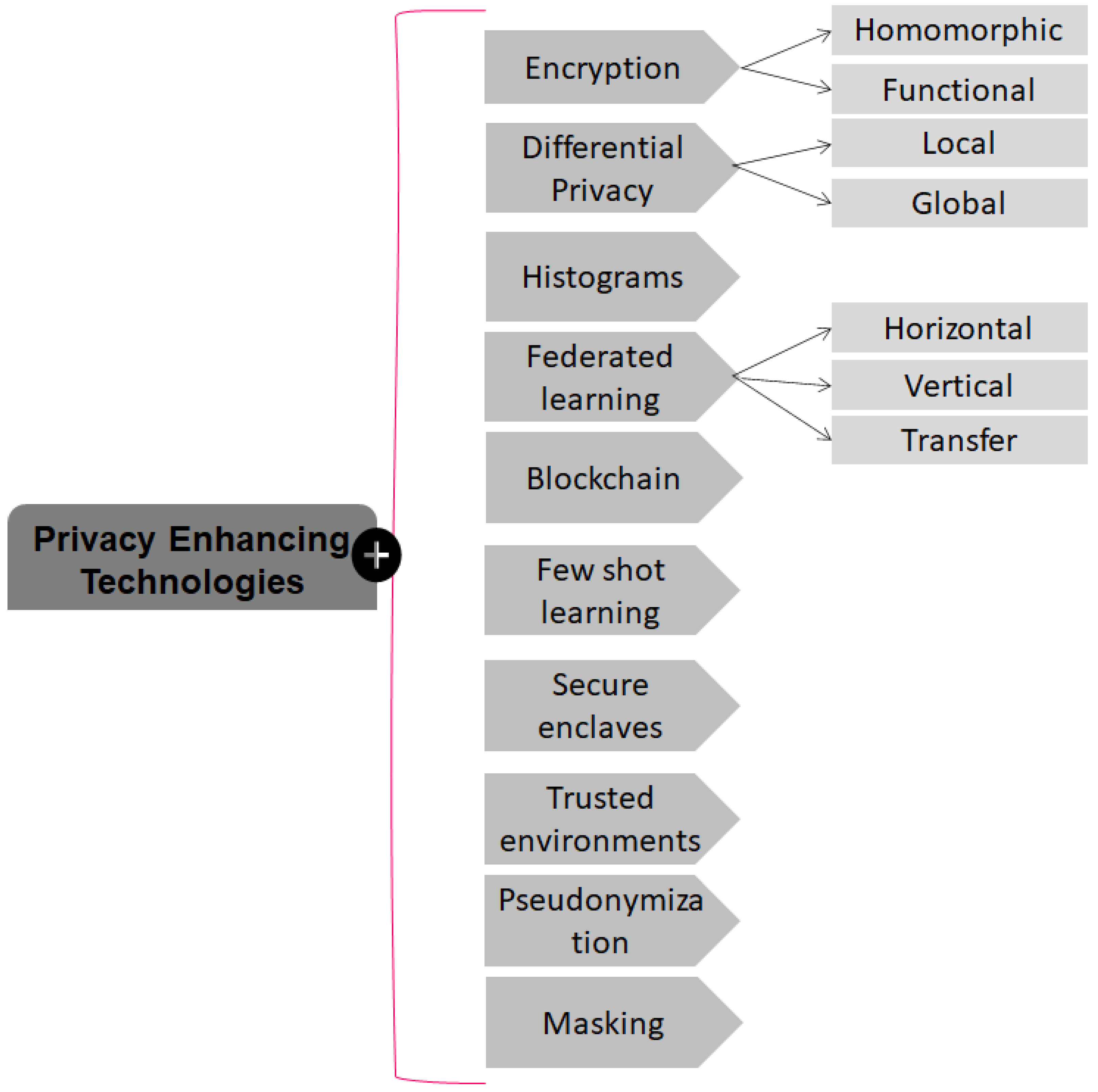


| Proposed Approach | Challenge (s) | Benefits | Contribution (s) | Reference |
|---|---|---|---|---|
| FL-based micro aggregation | Privacy–utility trade-off | Privacy in IIoT domains | Strong defense against recent privacy threats | Hongbin et al. [46] |
| Anonymization based techniques | Security and privacy challenges | Strong privacy of health data | Uncover privacy and security needs | Paul et al. [47] |
| Similarity-based analysis | Privacy in medical diagnosis | Strong privacy in cloud setting | A low-cost privacy-preserving framework | Muneeswari et al. [48] |
| Blockchain-based system | Privacy protection of real data | Privacy of sensors data | A robust defense mechanism | Xie et al. [49] |
| ML + CPD method | Privacy–utility trade-off | Application in SSA and MSA scenarios | A hybrid method for PPDP | Liu et al. [50] |
| PPDSM and PPDM methods | Privacy in data mining | Protection of confidential data | Analysis of various methods | Hewage et al. [51] |
| CV autoencoders | Identity protection in image data | Privacy of image data | Low cost perturbation methods | Terziyan et al. [52] |
| Blockchain-based system | Privacy of virus-infected users | Virus control and mitigation | Effective approach for privacy protection | Qin et al. [53] |
| Archive and data commons | Disclosure of sensitive data | Privacy of genomics data | Proposed ways to address privacy issues | Kumuthini et al. [54] |
| PPQE method | Privacy of confidential data | Responsible use of data | Reliable perturbation methods | Yang et al. [55] |
| DPView system | High-dimensional data handling | Better utility of SD | Data curation with privacy | Lin et al. [56] |
| DP model | Missing values handling | Informative analysis of COVID-19 data | Curating better data | Sei et al. [57] |
| Techniques Used | Objective (s) | Application Area | Study Type | Data Type | Reference |
|---|---|---|---|---|---|
| Fixed intervals + IDs generation | Privacy–utility trade-off | Healthcare | Technical | Real | Majeed et al. [61] |
| Fixed intervals+ Improved ℓ-diversity | Privacy–utility trade-off | Healthcare | Technical | Real | Onesimu et al. [62] |
| Hybrid schemes | Privacy–utility enhancement | Medical data | Technical | Real | Hui et al. [63] |
| Uncertainty + deviation | Privacy–utility enhancement | General scenarios | Technical | Real | Khan et al. [64] |
| DP + tree model | Data utility and patient’s privacy | Medical data | Technical | Real | Zhang et al. [65] |
| Three syntactic models | Privacy–utility enhancement | General scenarios | Technical | Real | Sadhya et al. [66] |
| Feature selection + anonymization | Data utility enhancement | General scenarios | Technical | Real | Srijayanthi et al. [67] |
| Mondrian approach | Data utility enhancement | General scenarios | Technical | Real | Canbay et al. [68] |
| Analytical approach | Privacy–utility enhancement | Smart health data | Technical | Real | Arca et al. [69] |
| k-CMVM and Constrained-CMVM | Utility enhancement | General scenarios | Technical | Real | Zouinina et al. [70] |
| Micro-aggregation approach | Privacy enhancement | dynamic data release | Technical | Real | Yan et al. [71] |
| Util-MA approach | Reduction in Iloss | Machine learning applications | Technical | Real and synthetic | Lee et al. [72] |
| Grid clustering + DP | Query accuracy | Location data sharing | Technical | Real and synthetic | Yan et al. [73] |
| AFBSO + WOA | Privacy and utility enhancement | Healthcare data | Technical | Synthetic | Thanga et al. [74] |
| GM-FBO algorithm | Preserving privacy of SHD | Cloud computing | Technical | Real | Anand et al. [75] |
| CGBFO-GC algorithm | Multi-privacy objectives | Cloud computing | Technical | Real | Anand et al. [76] |
| OAN model | Compute cost reduction | General scenarios | Theoretical | Synthetic | Canbay et al. [77] |
| Clustering method | Privacy and utility enhancement | IoT environments | Technical | Real | Onesimu et al. [78] |
| Fuzzy clustering | Privacy and utility enhancement | Industrial IoT | Technical | Real | Xie et al. [79] |
| IDEA method | Effectively preserving utility. | General scenarios | Technical | Real | Yang et al. [80] |
| -anonymous | Better privacy and data quality | IoT-based healthcare | Technical | Real | Li et al. [81] |
| BL approach | Data Security | Medical healthcare | Technical | Real | Altameem et al. [82] |
| Clustering approach | Data Security and utility | General scenarios | Technical | Real | Nayahi et al. [83] |
| DHkmeans-ℓ-diversity | SA privacy protection | Big data era | Technical | Real | Ashkouti et al. [84] |
| -value approach | Data mining | Information retrieval | Technical | Real | Solanki et al. [85] |
| CAP approach | PPDP and PPDM | Knowledge discovery and mining | Technical | Real | Eyupoglu et al. [86] |
| Techniques Used | Objective (s) | Application Area | Study Type | Data Type | Reference |
|---|---|---|---|---|---|
| DP+ MERF approach | produce tabular and image data with privacy guarantees | General scenarios | Technical | Real | Harder et al. [94] |
| DP-HFlow method | Privacy protection in data sharing | General Scenarios | Technical | Real | Lee et al. [95] |
| Probabilistic modeling | Anonymized synthetic data sharing | Open science | Technical | Real and synthetic | Jälkö et al. [96] |
| HealthGAN model | Better data analysis | Education and research | Technical | Synthetic | Yale et al. [97] |
| GAN+ XAI | High quality SD generation | Health data | Technical | Real | Lenatti et al. [98] |
| HealthGAN model | Capturing trends from TSD | Medical domain | Technical | Real and synthetic | Bhanot et al. [99] |
| VGAE model | Yield artificial trajectories with PPP | Electronic health | Technical | Synthetic | Nikolentzos et al. [100] |
| VITALISE model | Compliance-based data use | Health and well-being domain | Technical | Real | Hernandez et al. [101] |
| GAN model | Reduce risk of SA disclosure | Fitness related | Technical | Real | Kuo et al. [102] |
| SDG framework | Privacy preservation and CP | Medical domain | Technical | Real | Rodriguez et al. [103] |
| dsSynthetic package | Data harmonization | General scenarios | Technical | Real | Banerjee et al. [104] |
| STSG approach | Privacy guarantees in TSD | General scenarios | Theoretical | Real | Larrea et al. [105] |
| pGAN model | Privacy guarantees in EHR | Medical domain | Technical | Real | Venugopal et al. [106] |
| VAE model | Fixation of bias and privacy | Medical domain | Technical | Real and synthetic | Yoshikawa et al. [107] |
| Neural-Prophet model | Maintaining validity of MD | Medical systems | Technical | Real | Hyun et al. [108] |
| Transformer models | Accurate clinical predictions with privacy guarantees | healthcare | Technical | Real | Zhang et al. [109] |
| HealthGAN model | Privacy, utility, and resemblance | Healthcare domain | Technical | Real | Yale et al. [110] |
| GANs models | Data augmentation | General scenarios | Technical | Real | Narteni et al. [111] |
| GAN model | Control on various privacy risks | Big data apps | Theoretical | Real | Raveendran et al. [112] |
| MC-GEN model | Privacy guarantees in classification tasks | ML applications | Technical | Real | Li et al. [113] |
| PPEA model | Better utility of data | Distributed environments | Technical | Real | Shahani et al. [114] |
| DP+ GAN | Higher privacy guarantees | Industrial IoT | Technical | Real | Hindistan et al. [115] |
| -ULDP | Strong privacy protection | General scenarios | Technical | Real, synthetic | Zhang et al. [116] |
| Fed Select Framework | Strong privacy guarantees in FL | IoMT settings | Technical | Real | Nair et al. [117] |
| LGAN + DP | Privacy-utility trade-off | ML applications | Technical | Real | Zhang et al. [118] |
| HT-Fed-GAN model | Privacy–utility trade-off | machine learning tasks | Technical | Real | Duan et al. [119] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Majeed, A. Attribute-Centric and Synthetic Data Based Privacy Preserving Methods: A Systematic Review. J. Cybersecur. Priv. 2023, 3, 638-661. https://doi.org/10.3390/jcp3030030
Majeed A. Attribute-Centric and Synthetic Data Based Privacy Preserving Methods: A Systematic Review. Journal of Cybersecurity and Privacy. 2023; 3(3):638-661. https://doi.org/10.3390/jcp3030030
Chicago/Turabian StyleMajeed, Abdul. 2023. "Attribute-Centric and Synthetic Data Based Privacy Preserving Methods: A Systematic Review" Journal of Cybersecurity and Privacy 3, no. 3: 638-661. https://doi.org/10.3390/jcp3030030
APA StyleMajeed, A. (2023). Attribute-Centric and Synthetic Data Based Privacy Preserving Methods: A Systematic Review. Journal of Cybersecurity and Privacy, 3(3), 638-661. https://doi.org/10.3390/jcp3030030





