Assessing the Security and Privacy of Baby Monitor Apps
Abstract
:1. Introduction
- RQ1
- How is the confidentiality of the video streams of the baby monitor applications ensured?
- RQ2
- How compliant are the data practices of the baby monitor applications with the respective privacy policies?
- Considering that the confidentiality of private video footage is an integral part of privacy protection, we evaluated the security measures used to protect the monitoring streams and identified several security issues that threaten their confidentiality.
- By analyzing network connections and transferred data during baby monitoring sessions, we compared the apps’ behavior with the declared data practices of their privacy policies. We examined the statements and transparency of the privacy policies and assessed the privacy implications of the use of the baby monitor app in the real world.
- We conducted the first in-depth analysis of network communications and corresponding network security measures implemented by popular baby monitor apps in the Android ecosystem.
2. Related Work
3. Materials and Methods
3.1. Privacy Assessment Methodology
- We reviewed the data practices declared in the app’s privacy policy and categorized the collected and shared personal data and the security level of confidential data transmission. To perform these assessments, we used the established taxonomy used for the annotation of the OPP-115 privacy policy corpus by Wilson et al. [23], as well as its refined and updated taxonomy as used for the annotation of the bilingual English and German MAPP privacy policy corpus by Arora et al. [24]. The updated taxonomy captures the introduced EU GDPR regulations and California’s CCPA/CPRA for first-party and third-party data collection. Furthermore, we did not consider the defined “Do Not Track” category in [23], as it is no longer supported by the major browsers and is considered a retired specification by the former Tracking Protection Working Group [25]. Table 2 illustrates the categories and attributes of the resulting taxonomy, accompanied by their descriptions.
- We evaluated the dangerous permissions that each app stated in the Android manifest and identified valid permissions necessary to build a video surveillance solution. Extending previously used methodology [11], we investigated possible misuse of permissions by combining dynamic and static code analysis.
- We performed a dynamic analysis of the app’s communication behavior by capturing and decrypting all network connections using a transparent proxy. In this way, we got insight into the communication destinations, the transport security mechanisms implemented, and the actual data transmitted during a baby monitoring session.
- Finally, we checked the results of the dynamic analysis for exposure of personal information and compliance with the respective privacy policy.
3.2. Reviewing the Confidentiality of Monitoring Video Streams
3.2.1. Threat Model
3.2.2. Methodology
- Using the results of a traffic capture performed during a baby monitoring session (see Section 3.1), we evaluated the collected data regarding utilized network security measures and potential clear text transmissions.
- We performed an additional security analysis for each application to identify security issues that were not detected by automatic static analysis. The analysis consisted of a manual review of the source code using JADX [28], where we focused on identifying potential issues that compromise the confidentiality of transmitted video streams.
3.3. Analysis Environment
4. Evaluation of the Privacy Policies
4.1. First-Party Collection/Use
4.2. Third-Party Collection/Use
4.3. User Access, Edit, and Deletion
4.4. Data Retention
4.5. Data Security
4.6. Policy Change
4.7. International and Specific Audiences
4.8. Contact Details for Privacy-Related Questions
5. Mobile App Analysis
5.1. App Permissions
5.2. Device Pairing
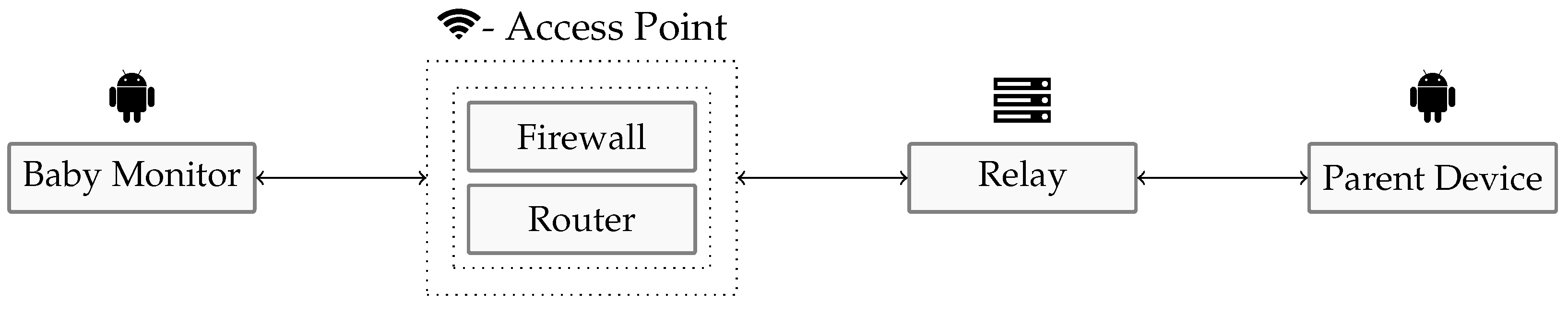
5.3. Network Communication
5.4. Privacy Leaks
5.5. Deployed Network Security Measures
5.6. Assessing the Confidentiality of Video Streams
5.6.1. Static Code Analysis
5.6.2. Security Issues Threatening the Confidentiality of Video Streams
6. Discussion & Conclusions
6.1. Security Issues and Their Impact on Video Confidentiality
6.2. Privacy Implications of Baby Monitor App Usage
6.3. Recommendations for Developers
6.4. Limitations
6.5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Vagts, H.; Beyerer, J. Security and Privacy Challenges in Modern Surveillance Systems. 2009. Available online: https://www.researchgate.net/publication/41193325_Security_and_privacy_challenges_in_modern_surveillance_systems (accessed on 13 June 2023).
- Tekeoglu, A.; Tosun, A. Investigating Security and Privacy of a Cloud-Based Wireless IP Camera: NetCam. In Proceedings of the 2015 24th International Conference on Computer Communication and Networks (ICCCN), Las Vegas, NV, USA, 3–6 August 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Obermaier, J.; Hutle, M. Analyzing the Security and Privacy of Cloud-based Video Surveillance Systems. In Proceedings of the 2nd ACM International Workshop, Virtual, 18 July 2016; pp. 22–28. [Google Scholar] [CrossRef]
- Valente, J.; Koneru, K.; Cardenas, A. Privacy and Security in Internet-Connected Cameras. In Proceedings of the 2019 IEEE International Congress on Internet of Things (ICIOT), Milan, Italy, 8–13 July 2019; pp. 173–180. [Google Scholar] [CrossRef]
- Albrecht, K.; Mcintyre, L. Privacy Nightmare: When Baby Monitors Go Bad [Opinion]. IEEE Technol. Soc. Mag. 2015, 34, 14–19. [Google Scholar] [CrossRef]
- Vlachos, V.; Stamatiou, Y.C.; Nikoletseas, S. The Privacy Flag Observatory: A Crowdsourcing Tool for Real Time Privacy Threats Evaluation. J. Cybersecur. Priv. 2023, 3, 26–43. [Google Scholar] [CrossRef]
- Andow, B.; Mahmud, S.Y.; Whitaker, J.; Enck, W.; Reaves, B.; Singh, K.; Egelman, S. Actions speak louder than words: Entity-sensitive privacy policy and data flow analysis with policheck. In Proceedings of the 29th USENIX Security Symposium (USENIX Security’20), Boston, MA, USA, 12–14 August 2020. [Google Scholar]
- Zimmeck, S.; Wang, Z.; Zou, L.; Iyengar, R.; Liu, B.; Schaub, F.; Wilson, S.; Sadeh, N.; Bellovin, S.; Reidenberg, J. Automated analysis of privacy requirements for mobile apps. In Proceedings of the 2016 AAAI Fall Symposium Series, Arlington, VA, USA, 17–19 November 2016. [Google Scholar]
- Bui, D.; Yao, Y.; Shin, K.G.; Choi, J.M.; Shin, J. Consistency analysis of data-usage purposes in mobile apps. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Virtual, 15–19 November 2021; pp. 2824–2843. [Google Scholar]
- Hussain, M.; Zaidan, A.A.; Zidan, B.B.; Iqbal, S.; Ahmed, M.M.; Albahri, O.S.; Albahri, A.S. Conceptual framework for the security of mobile health applications on android platform. Telemat. Inform. 2018, 35, 1335–1354. [Google Scholar] [CrossRef]
- Papageorgiou, A.; Strigkos, M.; Politou, E.; Alepis, E.; Solanas, A.; Patsakis, C. Security and Privacy Analysis of Mobile Health Applications: The Alarming State of Practice. IEEE Access 2018, 6, 9390–9403. [Google Scholar] [CrossRef]
- O’Loughlin, K.; Neary, M.; Adkins, E.C.; Schueller, S.M. Reviewing the data security and privacy policies of mobile apps for depression. Internet Interv. 2019, 15, 110–115. [Google Scholar] [CrossRef] [PubMed]
- Continella, A.; Fratantonio, Y.; Lindorfer, M.; Puccetti, A.; Zand, A.; Kruegel, C.; Vigna, G. Obfuscation-Resilient Privacy Leak Detection for Mobile Apps Through Differential Analysis. In Proceedings of the NDSS, San Diego, CA, USA, 1 March 2017; Volume 17. [Google Scholar]
- Valente, J.; Cardenas, A.A. Security & privacy in smart toys. In Proceedings of the 2017 Workshop on Internet of Things Security and Privacy, Dallas, TX, USA, 3 November 2017; pp. 19–24. [Google Scholar]
- Gruber, M.; Höfig, C.; Golla, M.; Urban, T.; Große-Kampmann, M. “We may share the number of diaper changes ”: A Privacy and Security Analysis of Mobile Child Care Applications. Proc. Priv. Enhancing Technol. 2022, 3, 394–414. [Google Scholar] [CrossRef]
- Liu, E.; Rao, S.; Havron, S.; Ho, G.; Savage, S.; Voelker, G.M.; McCoy, D. No Privacy Among Spies: Assessing the Functionality and Insecurity of Consumer Android Spyware Apps. Proc. Priv. Enhancing Technol. 2023, 1, 1–18. [Google Scholar] [CrossRef]
- Thankappan, M.; Rifà-Pous, H.; Garrigues, C. Multi-Channel Man-in-the-Middle attacks against protected Wi-Fi networks: A state of the art review. Expert Syst. Appl. 2022, 210, 118401. [Google Scholar] [CrossRef]
- Sivaraman, V.; Gharakheili, H.H.; Vishwanath, A.; Boreli, R.; Mehani, O. Network-level security and privacy control for smart-home IoT devices. In Proceedings of the 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Milan, Italy, 19–21 October 2015; pp. 163–167. [Google Scholar]
- European Parliament, Regulation (EU) 2016/679 (General Data Protection Regulation). 2016. Available online: https://commission.europa.eu/law/law-topic/data-protection/data-protection-eu_en (accessed on 13 June 2023).
- State of California Department of Justice. California Consumer Privacy Act (CCPA). 2020. Available online: https://oag.ca.gov/privacy/ccpa (accessed on 13 June 2023).
- Law, V. Consumer Data Protection Act. 2021. Available online: https://law.lis.virginia.gov/vacode/title59.1/chapter53/ (accessed on 13 June 2023).
- Krehling, L.; Essex, A. A Security and Privacy Scoring System for Contact Tracing Apps. J. Cybersecur. Priv. 2021, 1, 597–614. [Google Scholar] [CrossRef]
- Wilson, S.; Schaub, F.; Dara, A.A.; Liu, F.; Cherivirala, S.; Leon, P.G.; Andersen, M.S.; Zimmeck, S.; Sathyendra, K.M.; Russell, N.C.; et al. The Creation and Analysis of a Website Privacy Policy Corpus. In Proceedings of the 54th Annual Meeting of the Association for Computational Linguistics (Volume 1: Long Papers), Berlin, Germany, 7–12 August 2016; pp. 1330–1340. [Google Scholar]
- Arora, S.; Hosseini, H.; Utz, C.; Kumar, V.B.; Dhellemmes, T.; Ravichander, A.; Story, P.; Mangat, J.; Chen, R.; Degeling, M.; et al. A Tale of Two Regulatory Regimes: Creation and Analysis of a Bilingual Privacy Policy Corpus. In Proceedings of the 13th Conference on Language Resources and Evaluation, ELRA, LREC 2022, Paris, France, 20–25 June 2022; pp. 5460–5472. [Google Scholar]
- Tracking Protection Working Group. Do Not Track. World Wide Web Consortium(W3C). 2012. Available online: http://www.w3.org/2011/tracking-protection (accessed on 13 June 2023).
- Callegati, F.; Cerroni, W.; Ramilli, M. Man-in-the-middle attack to the HTTPS protocol. Secur. Privacy IEEE 2009, 7, 78–81. [Google Scholar] [CrossRef]
- Abraham, A. Mobile Security Framework (MobSF). 2023. Available online: https://github.com/MobSF/Mobile-Security-Framework-MobSF (accessed on 13 June 2023).
- Skylot. jadx-Dex to Java Decompiler. 2023. Available online: https://github.com/skylot/jadx (accessed on 13 June 2023).
- Cortesi, A.; Hils, M.; Kriechbaumer, T. (contributors) Mitmproxy: A Free and Open Source Interactive HTTPS Proxy, version 9.0. Available online: https://github.com/mitmproxy/mitmproxy (accessed on 13 June 2023).
- Sensepost, O.C. Objection-Runtime Mobile Exploration. 2023. Available online: https://github.com/sensepost/objection (accessed on 13 June 2023).
- Kuner, C.; Bygrave, L.; Docksey, C.; Drechsler, L. The EU General Data Protection Regulation (GDPR): A Commentary; Oxford University Press: Oxford, UK, 2020. [Google Scholar]
- Kazemi, R. General Data Protection Regulation (GDPR); Tredition: Hamburg, Germany, 2018. [Google Scholar]
- O’Kane, P. A Practical Guide to Managing GDPR Data Subject Access Requests, 2nd ed.; Law Brief Publishing: Somerset, UK, 2022. [Google Scholar]
- Vrabec, H.; Uršič, H. Data Subject Rights under the GDPR: With a Commentary through the Lens of the Data-Driven Economy; Oxford University Press: Oxford, UK, 2021. [Google Scholar]
- Voigt, P.; von dem Bussche, A. The EU General Data Protection Regulation (GDPR): A Practical Guide; Springer International Publishing: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Party, A.W. Guidelines on Transparency under Regulation 2016/679. 2018. Available online: https://ec.europa.eu/newsroom/article29/items/622227/en (accessed on 20 April 2023).
- Alepis, E.; Patsakis, C. Hey doc, is this normal?: Exploring android permissions in the post marshmallow era. In Proceedings of the Security, Privacy, and Applied Cryptography Engineering: 7th International Conference, SPACE 2017, Proceedings 7, Goa, India, 13–17 December 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 53–73. [Google Scholar]
- Android Open Source Project Request Runtime Permissions. Available online: https://developer.android.com/training/permissions/requesting (accessed on 13 June 2023).
- Android Open Source Project Storage updates in Android 11. 2023. Available online: https://developer.android.com/about/versions/11/privacy/storage (accessed on 13 June 2023).
- Android Open Source Project Android 13 Features and Changes List. 2023. Available online: https://developer.android.com/about/versions/13/summary (accessed on 13 June 2023).
- Rescorla, E. WebRTC Security Architecture. RFC 8827, RFC Editor. 2021. Available online: https://datatracker.ietf.org/doc/rfc8827/ (accessed on 13 June 2023).
- Mahi, R.; Matthews, P.; Rosenberg, J. Traversal Using Relays around NAT (TURN): Relay Extensions to Session Traversal Utilities for NAT (STUN). RFC 5766, RFC Editor, 2010. Available online: https://datatracker.ietf.org/doc/rfc5766/ (accessed on 13 June 2023).
- MITRE Corporation Common Weakness Enumeration. 2023. Available online: https://cwe.mitre.org/ (accessed on 20 April 2023).
- Alomar, N.; Egelman, S. Developers Say the Darnedest Things: Privacy Compliance Processes Followed by Developers of Child-Directed Apps. Proc. Priv. Enhancing Technol. 2022, 4, 24. [Google Scholar] [CrossRef]
- Li, T.; Louie, E.; Dabbish, L.; Hong, J.I. How developers talk about personal data and what it means for user privacy: A case study of a developer forum on reddit. Proc. ACM Hum.-Comput. Interact. 2021, 4, 1–28. [Google Scholar] [CrossRef]
- Ekambaranathan, A.; Zhao, J.; Van Kleek, M. “Money makes the world go around”: Identifying Barriers to Better Privacy in Children’s Apps From Developers’ Perspectives. In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems, Yokohama, Japan, 8–13 May 2021; pp. 1–15. [Google Scholar]
- Parsons, J.; Schrider, M.; Ogunlela, O.; Ghanavati, S. Understanding Developers Privacy Concerns Through Reddit Thread Analysis. arXiv 2023, arXiv:2304.07650. [Google Scholar]
- Zimmeck, S.; Goldstein, R.; Baraka, D. PrivacyFlash Pro: Automating Privacy Policy Generation for Mobile Apps. In Proceedings of the NDSS, Online, 21–25 February 2021. [Google Scholar]
- Pan, S.; Zhang, D.; Staples, M.; Xing, Z.; Chen, J.; Xu, X.; Hoang, J. A Large-scale Empirical Study of Online Automated Privacy Policy Generators for Mobile Apps. arXiv 2023, arXiv:2305.03271. [Google Scholar]
- OWASP® Foundation Secure Product Design Cheat Sheet 2023. Available online: https://cheatsheetseries.owasp.org/cheatsheets/Secure_Product_Design_Cheat_Sheet.html (accessed on 13 June 2023).
- Pradeep, A.; Paracha, M.T.; Bhowmick, P.; Davanian, A.; Razaghpanah, A.; Chung, T.; Lindorfer, M.; Vallina-Rodriguez, N.; Levin, D.; Choffnes, D. A Comparative Analysis of Certificate Pinning in Android & IOS. In Proceedings of the 22nd ACM Internet Measurement Conference, IMC’22, Nice, France, 25–27 October 2022; Association for Computing Machinery: New York, NY, USA, 2022; pp. 605–618. [Google Scholar] [CrossRef]
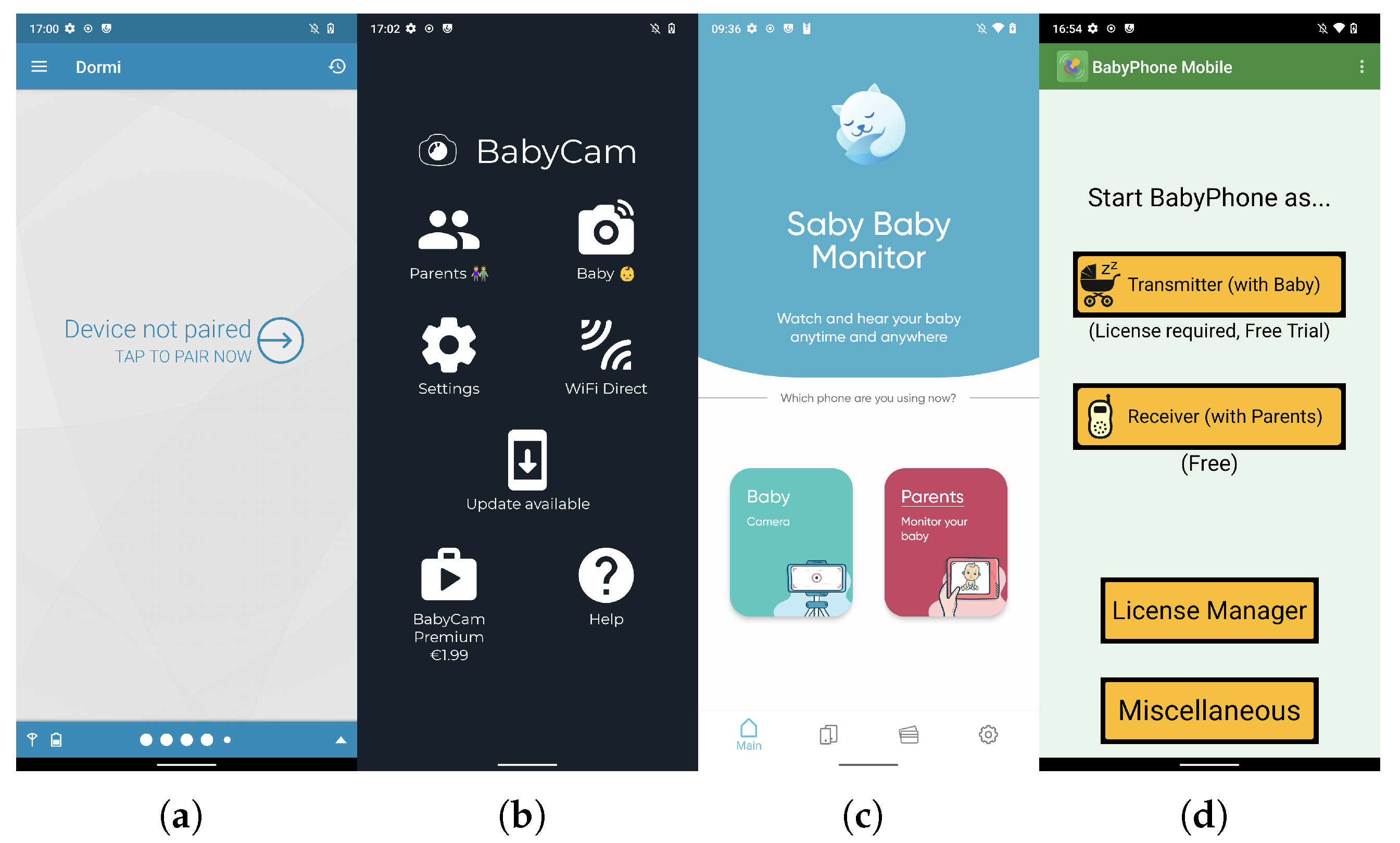





| Abbreviated Name | APK id@version | Installs | Rating |
|---|---|---|---|
| Dormi | com.sleekbit.dormi@3.4.3 | 1 Mio.+ | 4.1/5 |
| BabyCam | com.arjonasoftware.babycam@2.24 | 1 Mio.+ | 4.5/5 |
| Saby | com.saby.babymonitor3g@2.133 | 1 Mio.+ | 3.9/5 |
| Babyphone Mobile | com.babyphonemobile@3.00.1 | 100.000+ | 3.9/5 |
| Categories | Category Description | Attributes | Attribute Description |
|---|---|---|---|
| First-Party Collection/Use | Privacy practices describing data collection or data use by the company/organization owning the website or mobile app. | Information Type | What category of information is collected or tracked by the company/organization? |
| Purpose | What is the purpose of collecting or using user information? | ||
| Collection Process | How does the first party collect, track, or obtain user information? | ||
| Does/Does Not (opt) | Use to denote if the policy explicitly states that something is NOT done. | ||
| Collection Mode (opt) | Use to denote if the data collection performed by the first party is implicit (e.g., the company/organization collects the information without the user’s explicit awareness) or explicit (e.g., the user provides the information) | ||
| Anonymization (opt) | Use if it is explicitly stated whether the information or data practice is linked to the user’s identity or if it is anonymous. | ||
| User Type (opt) | Use if a practice applies specifically to users with an account or users without an account. | ||
| Choice Type (opt) | Use if user choices are explicitly offered for this practice. | ||
| Choice Scope (opt) | Use to indicate the scope of user choices. In some cases, even if user choices are not clear or specific, this attribute can be selected. | ||
| Legal Basis for Processing | The GDPR prohibits the collection and processing of personal data without a proper legal basis. Therefore, every category of personal data requires the legal basis to be clear and specific. | ||
| Third-Party Collection/Use | Privacy practices describing data sharing with third parties or data collection by third parties. A third party is a company/organization other than the first-party company/organization that owns the website or mobile app. | Information Type | What category of information is shared with, collected by, or otherwise obtained by the third party? |
| Purpose | What is the purpose of a third party receiving or collecting user information? | ||
| Entity | The third parties involved in the data practice. | ||
| Collection Process | How does the third party receive, collect, track, or see user information? | ||
| Does/Does Not (opt) | Use to denote if the policy explicitly states that something is NOT done. | ||
| Anonymization (opt) | Use if it is explicitly stated whether the information or data practice is linked to the user’s identity or if it is anonymous. | ||
| User Type (opt) | Use if this practice applies specifically to users with an account or users without an account. | ||
| User Choice (opt) | Use if user choices are explicitly offered for this practice. | ||
| Choice Scope (opt) | Use to indicate the scope of user choices. In some cases, even if user choices are not clear or specific, this attribute can be selected. | ||
| User Access, Edit and Deletion | Privacy practice that allows users to access, edit or delete the data that the company/ organization has about them. | Access Type | Options offered for users to access, edit, delete information that the company/organization has about them. |
| Access Scope | If access is offered, what data does it apply to. | ||
| User Type | Use if this practice applies specifically to users with or without an account. | ||
| Data Retention | Privacy practice specifying the retention period for collected user information. | Retention Period | Description of the retention period, i.e., how long data are stored. |
| Retention Purpose | The purpose to which the retention practice applies (may be “unspecified”). | ||
| Personal Information Type | The information type for which the retention period is specified (may be “unspecified”). | ||
| Data Security | Practice that describes how users’ information is secured and protected, e.g., from confidentiality, integrity, or availability breaches. Common practices include the encryption of stored data and online communications. | Security Measure | Policy statements that describe the type of security that the website/app implements to protect users’ information. |
| Policy Change | The company/organization’s practices concerning if and how users will be informed of changes to its privacy policy, including any choices offered to users. | Change Type | For what type of changes to the website/app’s policy are users notified? |
| Notification Type | How is the user notified when the privacy policy changes? | ||
| User Choice | What choices/options are offered to the user when the policy changes? | ||
| International and Specific Audiences | Specific audiences mentioned in the company/organization’s privacy policy, such as children or international users, for which the company/organization may provide special provisions. | Audience Type | Which audience does the policy segment refer to? |
| Other | Another aspect not covered in the other categories is discussed in the text segment. | Privacy Contact Information | The paragraph describes how to contact the company with questions, concerns, or complaints about the privacy policy. |
| Category | Attributes | Dormi | BabyCam | Saby | Babyphone Mobile |
|---|---|---|---|---|---|
| First-Party Collection/Use | Information Type | IP address and device IDs | Cookies and tracking elements | IP address and device IDs | IP address and device IDs |
| Computer information | |||||
| Purpose | Essential service or feature | Advertising or marketing | Optional service or feature | Essential service or feature | |
| Collection Process | Collected on a first-party app | Collected on first-party website/app | Collected on a first-party app | ||
| Does/Does Not | Does not share PI with any third party | Does not collect (personal) information | Does not collect PI of children | Does not analyze personal data | |
| Does not use cookies | |||||
| Collection Mode (opt) | Implicit | Implicit | Implicit | Implicit | |
| Anonymization (opt) | Identifiable | ||||
| User Type (opt) | Unspecified | ||||
| Choice Type (opt) | Do not use service | Do not use service | |||
| Choice Scope (opt) | Collection and Use | Collection and Use | |||
| Legal Basis for Processing | |||||
| Third-Party Collection/Use | Information Type | Cookies and tracking elements | IP address and device ID | Unspecified | |
| Computer information | |||||
| User online activities | |||||
| Cookies | |||||
| Unspecified | |||||
| Purpose | Advertisement or Marketing | Analytics or research | Unspecified | ||
| Essential service or feature | |||||
| Entity | Google AdSense | Google Play Services | App Store | ||
| AdMob | |||||
| Firebase Analytics | |||||
| Fabric | |||||
| Crashlytics | |||||
| Collection Process | Tracked on first-party website/app by third party | Tracked on first-party website/app by third party | Unspecified | ||
| Does/Does Not (opt) | Does not sell, trade, or transfer PI | ||||
| Anonymization (opt) | |||||
| User Type (opt) | Unspecified | ||||
| Choice Type (opt) | Opt-out link | Opt-in | |||
| Do not use service | |||||
| Choice Scope (opt) | Use | Collect and Use | |||
| User Access, Edit, and Deletion | Access Type | Unspecified | Unspecified | ||
| Access Scope | Unspecified | Unspecified | |||
| User Type (opt) | |||||
| Data Retention | Retention Period | Limited | Unspecified | Limited | |
| Indefinitely | |||||
| Retention Purpose | Perform service | Perform Service | |||
| Personal Information Type | IP address and device IDs | IP address and device IDs | |||
| User online activities | |||||
| Other | |||||
| Data Security | Security Measure | Secure data transfer | Generic | Secure data transfer | |
| Policy Change | Change Type | Unspecified | Unspecified | Unspecified | Other |
| Privacy relevant change | |||||
| Notification Type | General notice in privacy policy | General notice in privacy policy | General notice in privacy policy | General notice in privacy policy | |
| Personal notice | |||||
| User Choice | Opt-in | Unspecified | None | None | |
| Intl. and Specific Audiences | Audience Type | Europeans | Children | ||
| Other | Privacy contact information | Yes | Yes | Yes | Yes |
| Permission | Dormi | BabyCam | Saby | Babyphone Mobile |
|---|---|---|---|---|
| ACCESS_COARSE_LOCATION | ○ | ● | ○ | ○ |
| ACCESS_FINE_LOCATION | ○ | ● | ○ | ○ |
| CAMERA | ● | ● | ● | ● |
| RECORD_AUDIO | ● | ● | ● | ● |
| READ_EXTERNAL_STORAGE | ○ | ○ | ● | ○ |
| READ_PHONE_STATE | ● | ○ | ○ | ○ |
| WRITE_EXTERNAL_STORAGE | ○ | ● | ● | ○ |
| WRITE_SETTINGS | ● | ○ | ○ | ○ |
| NEARBY_WIFI_DEVICES | ○ | ● | ○ | ○ |
| POST_NOTIFICATIONS | ○ | ● | ● | ○ |
| App | Permission | Requests | Purpose | Required | |
|---|---|---|---|---|---|
| Runtime | Code | (Android 12) | |||
| Dormi | READ_PHONE_STATE | ○ | ○ | - | ○ |
| Dormi | WRITE_SETTINGS | ○ | ○ | - | ○ |
| BabyCam | ACCESS_COARSE_LOCATION | ● | ● | Wi-Fi Direct | ● |
| BabyCam | ACCESS_FINE_LOCATION | ● | ● | Wi-Fi Direct | ● |
| BabyCam | WRITE_EXTERNAL_STORAGE | ○ | ● | Image Capture | ○ |
| BabyCam | NEARBY_WIFI_DEVICES | ○ | ● | Wi-Fi Direct | ○ |
| BabyCam | POST_NOTIFICATIONS | ○ | ● | Push Notifications | ○ |
| Saby | WRITE_EXTERNAL_STORAGE | ○ | ● | Image Capture | ○ |
| Saby | READ_EXTERNAL_STORAGE | ● | ● | Image Crop, Bug Report | ● |
| Saby | POST_NOTIFICATIONS | ○ | ● | Push Notifications | ○ |
| App | Pairing | Type of Pairing | Confirmation Required |
|---|---|---|---|
| Dormi | ● | 5-digit code, valid for 120 s. | ● |
| BabyCam | ○ | - | ○ |
| Saby | ● | QR-Code, Link, 4-digit code. | ● |
| Babyphone Mobile | ● | 5-digit code, valid for 30 min. | ○ |
| App | Video Exchange | Domain/IP | Server Owner |
|---|---|---|---|
| Dormi | Relay | 34.68.30.36 | Google LLC |
| BabyCam | Client/Server | Local Router | User (App) |
| Saby | Relay | 47.242.47.214 | Xirsys |
| Babyphone Mobile | Relay | bpsvr01.papenmeier.com (194.55.15.124) | Papenmeier Software UG |
| App | Destination | Personal Information | Leak | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| IP Address | Device Name | Device UUID | Hardware Type | Parental Device Name | Parental Device UUID | User Agent | Operating System | Country/Language | Android Package | Ad Id | Child Id | Monitoring Time | |||
| Dormi | ● | ● | ● | ○ | ● | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | |
| BabyCam | Amazon | ● | ● | ○ | ● | ○ | ○ | ● | ● | ● | ● | ○ | ○ | ○ | ● |
| AppLovin | ● | ○ | ○ | ○ | ○ | ● | ○ | ○ | ● | ○ | ○ | ○ | ○ | ● | |
| AppsFlyer | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | ● | ○ | ○ | ● | |
| Github | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | ○ | ○ | ○ | ○ | ● | |
| ipify | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | |
| Liftoff | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | ● | ● | ○ | ○ | ● | |
| Moloco | ● | ○ | ○ | ○ | ○ | ○ | ● | ○ | ○ | ● | ○ | ○ | ○ | ● | |
| Saby | ● | ● | ● | ○ | ● | ● | ○ | ○ | ○ | ○ | ○ | ● | ● | ○ | |
| Meta Platforms | ● | ● | ○ | ○ | ○ | ○ | ○ | ○ | ● | ● | ● | ○ | ○ | ○ | |
| AppsFlyer | ● | ○ | ○ | ○ | ○ | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | |
| Xirsys | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ● | |
| Babyphone Mobile | Papenmeier Software | ● | ○ | ● | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ |
| App | Data Encryption | Key Exchange | Peer Authentication |
|---|---|---|---|
| Dormi | End-to-End (SRTP) | Proprietary | Anti-tamper code |
| BabyCam | - | - | Password (optional) |
| Saby | End-to-End (SRTP) | DTLS | Certificate hash |
| Babyphone Mobile | TLS | TLS | TLS Certificate |
| End-to-End (optional) | User (Password) | - |
| Security Issue | Dormi | BabyCam | Saby | Babyphone Mobile |
|---|---|---|---|---|
| Files may contain hard-coded sensitive information, such as usernames, passwords, keys, etc. | ○ | ○ | ○ | |
| The app uses SQLite Database and executes raw SQL queries. | ◑ | |||
| The app uses an insecure random number generator. | ○ | ○ | ○ | ○ |
| SHA-1 is a weak hash known to have hash collisions. | ◑ | ◑ | ◑ | |
| MD5 is a weak hash known to have hash collisions. | ◑ | ◑ | ◑ | |
| Insecure implementation of SSL. Trusting all the certificates or accepting self-signed certificates is a critical Security Hole. | ○ | |||
| The app can read/write to external storage. Any app can read data written to external storage. | ◑ | ◑ | ||
| The app uses the encryption mode CBC with PKCS5/PKCS7 padding. This configuration is vulnerable to padding oracle attacks. | ◑ | |||
| Insecure WebView implementation. Execution of user-controlled code in WebView is a critical security hole. | ◑ | |||
| Remote WebView debugging is enabled. | ◑ | |||
| IP address disclosure. | ○ | ○ |
| App | Confidentiality | Security issues |
|---|---|---|
| Dormi | ◑ | Clear text transmission of sensitive information (CWE-319). |
| Channel accessible by non-endpoint (CWE-300). | ||
| BabyCam | ○ | Clear text transmission of sensitive information (CWE-319). |
| Insufficiently protected credentials (CWE-522). | ||
| Channel accessible by non-endpoint (CWE-300). | ||
| Weak password requirements (CWE-521). | ||
| Saby | ● | - |
| Babyphone Mobile | ◑ | Weak password requirements (CWE-521). |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Schmidt, L.; Hosseini, H.; Hupperich, T. Assessing the Security and Privacy of Baby Monitor Apps. J. Cybersecur. Priv. 2023, 3, 303-326. https://doi.org/10.3390/jcp3030016
Schmidt L, Hosseini H, Hupperich T. Assessing the Security and Privacy of Baby Monitor Apps. Journal of Cybersecurity and Privacy. 2023; 3(3):303-326. https://doi.org/10.3390/jcp3030016
Chicago/Turabian StyleSchmidt, Lukas, Henry Hosseini, and Thomas Hupperich. 2023. "Assessing the Security and Privacy of Baby Monitor Apps" Journal of Cybersecurity and Privacy 3, no. 3: 303-326. https://doi.org/10.3390/jcp3030016
APA StyleSchmidt, L., Hosseini, H., & Hupperich, T. (2023). Assessing the Security and Privacy of Baby Monitor Apps. Journal of Cybersecurity and Privacy, 3(3), 303-326. https://doi.org/10.3390/jcp3030016







