A Survey on Botnets, Issues, Threats, Methods, Detection and Prevention
Abstract
:1. Introduction
2. Definition of Botnets
3. Infection Methods
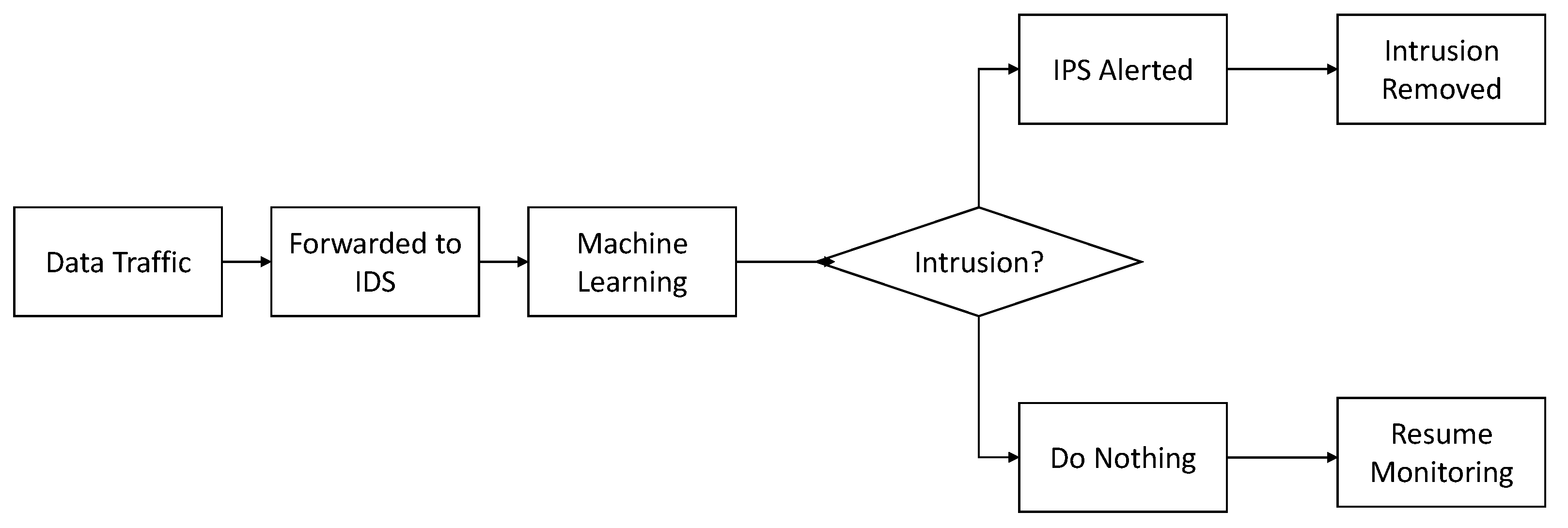
4. Detection Methods
4.1. Detection Types
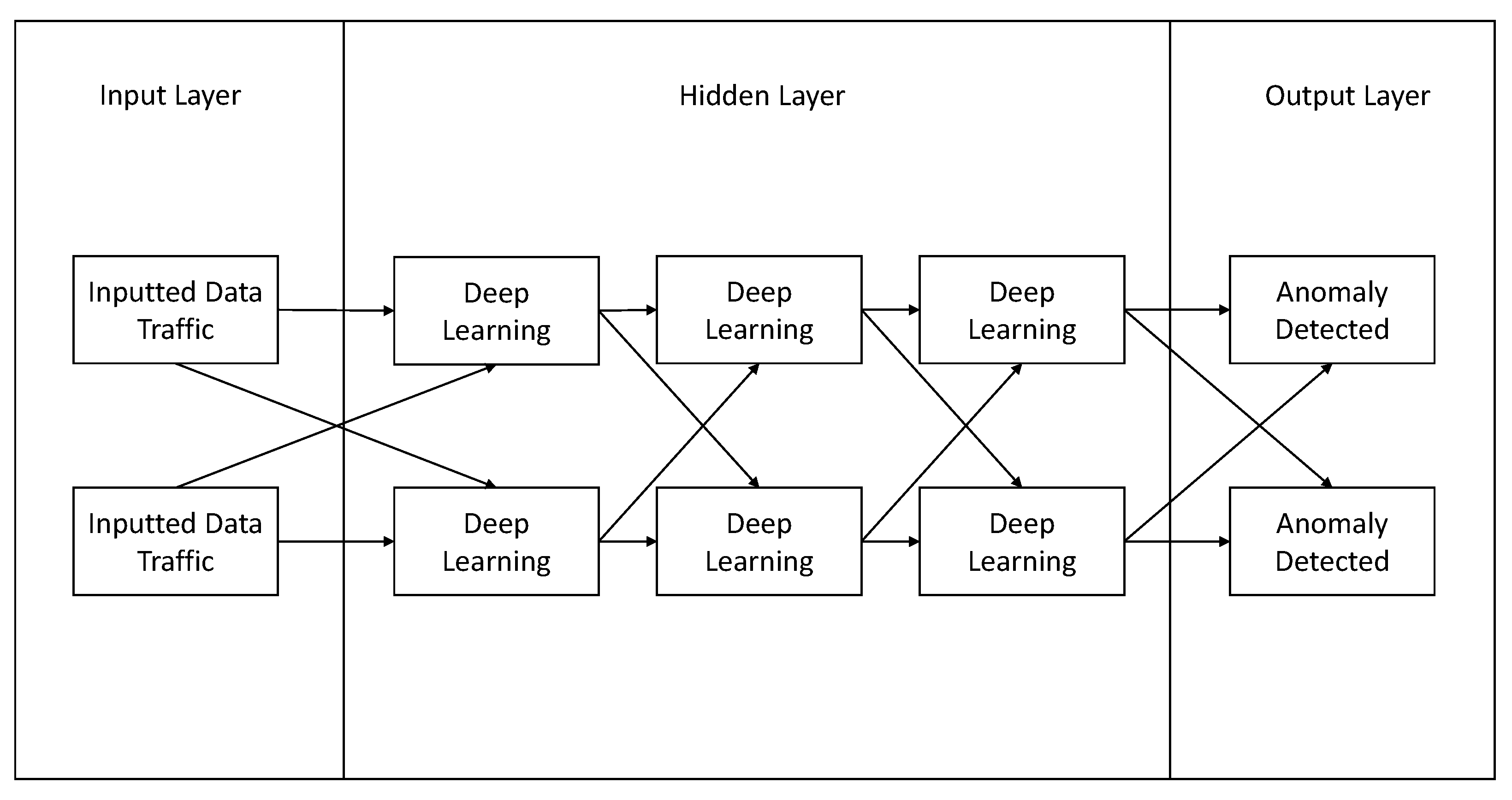
4.2. Machine Learning Based Detection
4.3. Fuzzy Logic Based Detection
4.4. Phishing Detection
4.5. Packer Detection
5. Prevention and Mitigation Strategies
6. Machine Learning Algorithms Comparisons
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhang, X.; Upton, O.; Beebe, N.L.; Choo, K.K.R. IoT Botnet Forensics: A Comprehensive Digital Forensic Case Study on Mirai Botnet Servers. Forensic Sci. Int. Digit. Investig. 2020, 32, 300926. [Google Scholar] [CrossRef]
- Kabay, M. Kraken the Botnet: The Ethics of Counter-Hacking. 2009. Available online: https://www.networkworld.com/article/2265704/kraken-the-botnet--the-ethics-of-counter-hacking.html (accessed on 30 December 2021).
- Chen, S.C.; Chen, Y.R.; Tzeng, W.G. Effective Botnet Detection Through Neural Networks on Convolutional Features. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 372–378. [Google Scholar] [CrossRef]
- Prowell, S.; Kraus, R.; Borkin, M. CHAPTER 1—Denial of Service. In Seven Deadliest Network Attacks; Prowell, S., Kraus, R., Borkin, M., Eds.; Syngress: Boston, MA, USA, 2010; pp. 1–21. [Google Scholar] [CrossRef]
- Silva, S.S.; Silva, R.M.; Pinto, R.C.; Salles, R.M. Botnets: A survey. Comput. Netw. 2013, 57, 378–403. [Google Scholar] [CrossRef]
- Cope, J. What’s a Peer-to-Peer (P2P) Network? 2002. Available online: https://www.computerworld.com/article/2588287/networking-peer-to-peer-network.html (accessed on 30 December 2021).
- Cooke, E.; Jahanian, F.; McPherson, D. The Zombie Roundup: Understanding, Detecting, and Disrupting Botnets. SRUTI 2005, 5, 6. [Google Scholar]
- Tunggal, A.T. What is an Open Port?: Definition and Free Checking Tools for 2021: UpGuard. 2021. Available online: https://www.upguard.com/blog/open-port (accessed on 30 December 2021).
- Abbas, S.G.; Hashmat, F.; Shah, G.A.; Zafar, K. Generic signature development for IoT Botnet families. Forensic Sci. Int. Digit. Investig. 2021, 38, 301224. [Google Scholar] [CrossRef]
- Liu, D.; Barber, B.; DiGrande, L. CHAPTER 9—Access Control Lists. In Cisco CCNA/CCENT Exam 640-802, 640-822, 640-816 Preparation Kit; Liu, D., Barber, B., DiGrande, L., Eds.; Syngress: Boston, MA, USA, 2009; pp. 331–384. [Google Scholar] [CrossRef]
- Hanna, K.T. What Is Network Flooding and How Does It Work? 2021. Available online: https://www.techtarget.com/searchnetworking/definition/flooding (accessed on 30 December 2021).
- Garre, J.T.M.; Pérez, M.G.; Ruiz-Martínez, A. A novel Machine Learning-based approach for the detection of SSH botnet infection. Future Gener. Comput. Syst. 2021, 115, 387–396. [Google Scholar] [CrossRef]
- Chakraverty, S.; Goel, A.; Misra, S. Towards Extensible and Adaptable Methods in Computing; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and Other Botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Jeong, O.R.; Kim, C.; Kim, W.; So, J. Botnets: Threats and responses. Int. J. Web Inf. Syst. 2011, 7, 6–17. [Google Scholar] [CrossRef]
- Feily, M.; Shahrestani, A.; Ramadass, S. A survey of botnet and botnet detection. In Proceedings of the 2009 Third International Conference on Emerging Security Information, Systems and Technologies, Athens, Greece, 18–23 June 2009; pp. 268–273. [Google Scholar]
- Hong, J. The state of phishing attacks. Commun. ACM 2012, 55, 74–81. [Google Scholar] [CrossRef]
- Khonji, M.; Iraqi, Y.; Jones, A. Phishing detection: A literature survey. IEEE Commun. Surv. Tutor. 2013, 15, 2091–2121. [Google Scholar] [CrossRef]
- Jia, Y.; Chen, Y.; Dong, X.; Saxena, P.; Mao, J.; Liang, Z. Man-in-the-browser-cache: Persisting HTTPS attacks via browser cache poisoning. Comput. Secur. 2015, 55, 62–80. [Google Scholar] [CrossRef]
- Scott, B. What Is a Dictionary Attack? 2020. Available online: https://www.techtarget.com/searchsecurity/definition/dictionary-attack (accessed on 30 December 2021).
- Nam, J.; Choo, K.K.R.; Kim, M.; Paik, J.; Won, D. Dictionary attacks against password-based authenticated three-party key exchange protocols. KSII Trans. Internet Inf. Syst. (TIIS) 2013, 7, 3244–3260. [Google Scholar]
- Mitchell, B. What Is a Network Sniffer? 2021. Available online: https://www.lifewire.com/definition-of-sniffer-817996 (accessed on 30 December 2021).
- Miller, M. What’s the Difference between Offline and Online Password Attacks? 2021. Available online: https://www.triaxiomsecurity.com/whats-the-difference-between-offline-and-online-password-attacks (accessed on 30 December 2021).
- Satoh, A.; Nakamura, Y.; Ikenaga, T. A flow-based detection method for stealthy dictionary attacks against Secure Shell. J. Inf. Secur. Appl. 2015, 21, 31–41. [Google Scholar] [CrossRef]
- Karim, A.; Salleh, R.B.; Shiraz, M.; Shah, S.A.A.; Awan, I.; Anuar, N.B. Botnet detection techniques: Review, future trends, and issues. J. Zhejiang Univ. Sci. C 2014, 15, 943–983. [Google Scholar] [CrossRef]
- Ahmed, M.; Naser Mahmood, A.; Hu, J. A survey of network anomaly detection techniques. J. Netw. Comput. Appl. 2016, 60, 19–31. [Google Scholar] [CrossRef]
- Hayes, M.A.; Capretz, M.A. Contextual anomaly detection framework for big sensor data. J. Big Data 2015, 2, 1–22. [Google Scholar] [CrossRef] [Green Version]
- Chen, R.; Niu, W.; Zhang, X.; Zhuo, Z.; Lv, F. An effective conversation-based botnet detection method. Math. Probl. Eng. 2017, 2017, 4934082. [Google Scholar] [CrossRef] [Green Version]
- Rahim, A.; Bin Muhaya, F.T. Discovering the botnet detection techniques. In Security Technology, Disaster Recovery and Business Continuity; Springer: Berlin/Heidelberg, Germany, 2010; pp. 231–235. [Google Scholar]
- García, S.; Grill, M.; Stiborek, J.; Zunino, A. An empirical comparison of botnet detection methods. Comput. Secur. 2014, 45, 100–123. [Google Scholar] [CrossRef]
- Lavin, A.; Ahmad, S. Evaluating real-time anomaly detection algorithms–the Numenta anomaly benchmark. In Proceedings of the 2015 IEEE 14th International Conference on Machine Learning and Applications (ICMLA), Miami, FL, USA, 9–11 December 2015; pp. 38–44. [Google Scholar]
- Alhajri, R.; Zagrouba, R.; Al-Haidari, F. Survey for anomaly detection of IoT botnets using machine learning auto-encoders. Int. J. Appl. Eng. Res. 2019, 14, 2417–2421. [Google Scholar]
- Jordan, J. Introduction to Autoencoders. 2018. Available online: https://www.jeremyjordan.me/autoencoders/ (accessed on 30 December 2021).
- Ashraf, J.; Keshk, M.; Moustafa, N.; Abdel-Basset, M.; Khurshid, H.; Bakhshi, A.D.; Mostafa, R.R. IoTBoT-IDS: A Novel Statistical Learning-enabled Botnet Detection Framework for Protecting Networks of Smart Cities. Sustain. Cities Soc. 2021, 27, 103041. [Google Scholar] [CrossRef]
- Mahmoud, M.S.; Xia, Y. Chapter 9—Cyberphysical Security Methods. In Networked Control Systems; Mahmoud, M.S., Xia, Y., Eds.; Butterworth-Heinemann: Oxford, UK, 2019; pp. 389–456. [Google Scholar] [CrossRef]
- Rathore, S.; Park, J.H. Semi-supervised learning based distributed attack detection framework for IoT. Appl. Soft Comput. 2018, 72, 79–89. [Google Scholar] [CrossRef]
- Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. An anomaly mitigation framework for iot using fog computing. Electronics 2020, 9, 1565. [Google Scholar] [CrossRef]
- Ippolito, P.P. Feature Extraction Techniques. 2019. Available online: https://towardsdatascience.com/feature-extraction-techniques-d619b56e31be (accessed on 30 December 2021).
- Tobiyama, S.; Yamaguchi, Y.; Shimada, H.; Ikuse, T.; Yagi, T. Malware detection with deep neural network using process behavior. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; Volume 2, pp. 577–582. [Google Scholar]
- Laskowski, N.; Contributor, T. What Are Recurrent Neural Networks and How Do They Work? 2021. Available online: https://www.techtarget.com/searchenterpriseai/definition/recurrent-neural-networks (accessed on 30 December 2021).
- Firdausi, I.; Lim, C.; Erwin, A.; Nugroho, A.S. Analysis of machine learning techniques used in behavior-based malware detection. In Proceedings of the 2010 Second International Conference on Advances in Computing, Control, and Telecommunication Technologies, Jakarta, Indonesia, 2–3 December 2010; pp. 201–203. [Google Scholar]
- Kaushik, S. An Introduction to Clustering and Different Methods of Clustering. 2016. Available online: https://www.analyticsvidhya.com/blog/2016/11/an-introduction-to-clustering-and-different-methods-of-clustering/ (accessed on 30 December 2021).
- Seither, J. Anomaly Detection: (Dis-)advantages of k-Means Clustering. 2017. Available online: https://www.inovex.de/de/blog/disadvantages-of-k-means-clustering/ (accessed on 30 December 2021).
- Zhang, X.; Gu, C.; Lin, J. Support Vector Machines for Anomaly Detection. In Proceedings of the 6th World Congress on Intelligent Control and Automation, Dalian, China, 21–23 June 2006; pp. 2594–2598. [Google Scholar]
- Afonja, T. Kernel Functions. 2018. Available online: https://towardsdatascience.com/kernel-function-6f1d2be6091 (accessed on 30 December 2021).
- Statinfer. 204.6.8 SVM: Advantages Disadvantages and Applications. 2019. Available online: https://statinfer.com/204-6-8-svm-advantages-disadvantages-applications/ (accessed on 30 December 2021).
- Kumar, B.J.; Naveen, H.; Kumar, B.P.; Sharma, S.S.; Villegas, J. Logistic regression for polymorphic malware detection using ANOVA F-test. In Proceedings of the 2017 International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), Coimbatore, India, 17–18 March 2017; pp. 1–5. [Google Scholar]
- Brownlee, J. How to Calculate Precision, Recall, and F-Measure for Imbalanced Classification. 2020. Available online: https://machinelearningmastery.com/precision-recall-and-f-measure-for-imbalanced-classification/ (accessed on 30 December 2021).
- Butler, B. What Is Fog Computing? Connecting the Cloud to Things. 2018. Available online: https://www.networkworld.com/article/3243111/what-is-fog-computing-connecting-the-cloud-to-things.html (accessed on 30 December 2021).
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 13–17 August 2012; pp. 13–16. [Google Scholar]
- George, A.; Dhanasekaran, H.; Chittiappa, J.; Challagundla, L.; Nikkam, S.; Abuzaghleh, O. Internet of Things in health care using fog computing. In Proceedings of the 2018 IEEE Long Island Systems, Applications and Technology Conference (LISAT), Farmingdale, NY, USA, 4 May 2018; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Tsikerdekis, M.; Zeadally, S.; Schlesener, A.; Sklavos, N. Approaches for preventing honeypot detection and compromise. In Proceedings of the 2018 Global Information Infrastructure and Networking Symposium (GIIS), Thessaloniki, Greece, 23–25 October 2018; pp. 1–6. [Google Scholar]
- Mukherjee, L. What Is a Honeypot in Network Security? Definition, Types and Uses. Available online: https://sectigostore.com/blog/what-is-a-honeypot-in-network-security-definition-types-uses (accessed on 30 December 2021).
- Joshi, C.; Ranjan, R.K.; Bharti, V. A Fuzzy Logic based feature engineering approach for Botnet detection using ANN. J. King Saud Univ.-Comput. Inf. Sci. 2021, in press. [Google Scholar] [CrossRef]
- Chai, W. What Is Fuzzy Logic? 2021. Available online: https://www.techtarget.com/searchenterpriseai/definition/fuzzy-logic (accessed on 30 December 2021).
- Moghimi, M.; Varjani, A.Y. New rule-based phishing detection method. Expert Syst. Appl. 2016, 53, 231–242. [Google Scholar] [CrossRef]
- Abu-Nimeh, S.; Nappa, D.; Wang, X.; Nair, S. A comparison of machine learning techniques for phishing detection. In Proceedings of the Anti-Phishing Working Groups 2nd Annual eCrime Researchers Summit, Pittsburgh, PA, USA, 4–5 October 2007; pp. 60–69. [Google Scholar]
- Kaspersky. All about Phishing Scams and Prevention: What You Need to Know. 2021. Available online: https://www.kaspersky.com/resource-center/preemptive-safety/phishing-prevention-tips (accessed on 30 December 2021).
- Guzella, T.S.; Caminhas, W.M. A review of machine learning approaches to spam filtering. Expert Syst. Appl. 2009, 36, 10206–10222. [Google Scholar] [CrossRef]
- Dedeturk, B.K.; Akay, B. Spam filtering using a logistic regression model trained by an artificial bee colony algorithm. Appl. Soft Comput. 2020, 91, 106229. [Google Scholar] [CrossRef]
- Devi, D.; Nandi, S. Detection of packed malware. In Proceedings of the First International Conference on Security of Internet of Things, Kollam, India, 17–19 August 2012; pp. 22–26. [Google Scholar]
- Bergenholtz, E.; Casalicchio, E.; Ilie, D.; Moss, A. Detection of metamorphic malware packers using multilayered LSTM networks. In Proceedings of the International Conference on Information and Communications Security, Copenhagen, Denmark, 24–26 August 2020; pp. 36–53. [Google Scholar]
- Alexander, M.; Wanner, R. Methods for understanding and reducing social engineering attacks. SANS Inst. 2016, 1, 1–32. [Google Scholar]
- Saleem, J.; Hammoudeh, M. Defense methods against social engineering attacks. In Computer and Network Security Essentials; Springer: Berlin/Heidelberg, Germany, 2018; pp. 603–618. [Google Scholar]
- Bhandari, P. Botnet Detection and Prevention Techniques: A Quick Guide. 2021. Available online: https://www.xenonstack.com/insights/what-are-botnets (accessed on 30 December 2021).
- Kirushnaamoni, R. Defenses to curb online password guessing attacks. In Proceedings of the 2013 International Conference on Information Communication and Embedded Systems (ICICES), Chennai, India, 21–22 February 2013; pp. 317–322. [Google Scholar]
- Wang, X.; Yan, Z.; Zhang, R.; Zhang, P. Attacks and defenses in user authentication systems: A survey. J. Netw. Comput. Appl. 2021, 188, 103080. [Google Scholar] [CrossRef]
- Klein, D. Relying on firewalls? Here’s why you’ll be hacked. Netw. Secur. 2021, 2021, 9–12. [Google Scholar] [CrossRef]
- Gupta, B.B.; Joshi, R.C.; Misra, M. Distributed denial of service prevention techniques. arXiv 2012, arXiv:1208.3557. [Google Scholar] [CrossRef] [Green Version]
- Vayansky, I.; Kumar, S. Phishing—Challenges and solutions. Comput. Fraud. Secur. 2018, 2018, 15–20. [Google Scholar] [CrossRef]
- Tuan, T.A.; Long, H.V.; Son, L.H.; Kumar, R.; Priyadarshini, I.; Son, N.T.K. Performance evaluation of Botnet DDoS attack detection using machine learning. Evol. Intell. 2020, 13, 283–294. [Google Scholar] [CrossRef]
- Nguyen, G.L.; Dumba, B.; Ngo, Q.D.; Le, H.V.; Nguyen, T.N. A collaborative approach to early detection of IoT Botnet. Comput. Electr. Eng. 2022, 97, 107525. [Google Scholar] [CrossRef]
| Positive | Negative | |
|---|---|---|
| Positive | Malware Packet | Normal Packet but labelled as Botnet Packet |
| Negative | Botnet Packet labelled as a Non-botnet Packet | Normal Packet |
| Positive | Negative | |
|---|---|---|
| Positive | Spam | Spam Email classified as Non-Spam |
| Negative | Non-Spam Email but classified as Spam | Non-Spam |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Owen, H.; Zarrin, J.; Pour, S.M. A Survey on Botnets, Issues, Threats, Methods, Detection and Prevention. J. Cybersecur. Priv. 2022, 2, 74-88. https://doi.org/10.3390/jcp2010006
Owen H, Zarrin J, Pour SM. A Survey on Botnets, Issues, Threats, Methods, Detection and Prevention. Journal of Cybersecurity and Privacy. 2022; 2(1):74-88. https://doi.org/10.3390/jcp2010006
Chicago/Turabian StyleOwen, Harry, Javad Zarrin, and Shahrzad M. Pour. 2022. "A Survey on Botnets, Issues, Threats, Methods, Detection and Prevention" Journal of Cybersecurity and Privacy 2, no. 1: 74-88. https://doi.org/10.3390/jcp2010006
APA StyleOwen, H., Zarrin, J., & Pour, S. M. (2022). A Survey on Botnets, Issues, Threats, Methods, Detection and Prevention. Journal of Cybersecurity and Privacy, 2(1), 74-88. https://doi.org/10.3390/jcp2010006






