1. Introduction
The evolution of urbanization and digitalization has led to the emergence of smart cities, where interconnected devices, sensors, and systems collectively enhance the efficiency, sustainability, and livability of urban environments [
1,
2,
3]. At the core of this transformation lies the Internet of Things (IoT), which enables the seamless collection, exchange, and processing of data across various city domains, including energy, transportation, healthcare, and security [
4]. However, the rapid deployment of IoT devices has exposed smart city infrastructures to critical cybersecurity risks, including data interception, unauthorized access, and large-scale coordinated attacks. As conventional encryption mechanisms struggle to keep pace with the emerging threats—especially those posed by quantum computing—there is a growing need for next-generation security frameworks [
5]. The recent advancements in quantum cryptography, particularly Quantum Key Distribution (QKD), have demonstrated the potential to provide theoretically unbreakable encryption [
6]. Integrating QKD with lightweight and resource-constrained IoT systems within smart cities remains largely unexplored [
7].
Regarding the advancements in smart city technologies, the underlying security of IoT communication remains a persistent challenge. Although widely adopted, traditional cryptographic schemes are vulnerable to both classical and quantum attacks, particularly in urban environments with high device density and real-time data flow requirements [
8,
9]. These vulnerabilities pose severe risks to critical smart city services, from transportation coordination to emergency response systems. Therefore, there is a pressing need to explore quantum-resilient solutions that are scalable and adaptable to smart city architectures. The primary research question addressed in this work is how QKD can be integrated into lightweight IoT frameworks to ensure quantum-resilient and energy-efficient smart city security. Motivated by this question, this research proposes a framework that unifies quantum cryptographic methods with traditional IoT security layers, enhancing both confidentiality and intrusion resilience across a city-wide network.
The proposed QESIF is a novel framework that combines QKD with smart city IoT infrastructures through a hybrid security protocol stack. The QESIF introduces a lightweight QKD layer compatible with constrained devices, a middleware layer for key management, and a Q-IDS capable of leveraging quantum error indicators such as QBER to detect eavesdropping. A hybrid protocol stack dynamically shifts between classical and quantum-secured communication based on device capability and criticality of data. This framework is designed to work with existing IoT protocols such as MQTT and CoAP while injecting QKD-generated keys at the transport or session layer. The main contributions of this study are as follows:
A framework is proposed to integrate QKD with heterogeneous and resource-constrained IoT networks in smart city infrastructures.
A novel Q-IDS is designed that uses quantum signal anomalies—such as increased QBER—to detect eavesdropping and intrusion attempts in real time.
A hybrid protocol stack that supports seamless switching between quantum-secure and classical communication modes is developed, enabling scalable and backward-compatible deployment in evolving smart city environments.
The rest of the paper is organized as follows.
Section 2 presents a review of the related works.
Section 3 describes the proposed QESIF in detail.
Section 4 presents the simulation environment and experimental results, including a comparative analysis with traditional security models.
Section 5 discusses the findings and implications of the QESIF in smart city deployments. Finally,
Section 6 concludes the paper.
2. Related Work
Recent efforts in securing IoT systems in smart cities have explored both post-quantum cryptography (PQC) and QKD. While some approaches aim to strengthen the existing encryption methods, others introduce hybrid or fully quantum solutions. A hybrid encryption scheme has been proposed that combines symmetric and post-quantum cryptography for smart grids, although it lacks real-time intrusion adaptability [
10]. Quantum threats to IoT systems emphasize the importance of post-quantum cryptography, although practical integration frameworks have not been fully established [
11]. An ML-enhanced QKD system has been proposed for IoT communication, with a primary focus on threat detection rather than secure key management [
12]. A lightweight post-quantum authentication protocol has been explored for dense IoT networks; however, its scalability under high-entropy attacks has not been demonstrated [
13].
A conceptual model for Quantum IoT (QIoT) networks has been proposed to explore future-ready secure architectures; however, it remains largely theoretical, with no concrete deployment models tailored for IoT environments [
14]. Quantum machine learning techniques have been integrated with Security Information and Event Management (SIEM) systems to enhance threat prediction in smart city contexts; however, these approaches do not address security mechanisms at the IoT device level [
15]. An optimized HQC-based encryption scheme tailored for the IoT is presented using a hardware/software co-design approach, achieving reduced latency; however, its performance is constrained in static and predefined deployment environments [
16]. CR-QKD was introduced for the sharing of mobile keys in a wide area, but the scheme is not optimized for IoT power constraints [
17].
PQC algorithms have been analyzed regarding the IoT, identifying challenges but offering no system-level integration model [
18]. The PQC performance was evaluated on embedded systems but not in the context of distributed urban networks [
19]. Quantinuum’s Quantum Origin uses quantum entropy for key generation, although integration with IoT protocols like MQTT remains undefined [
20].
Table 1 highlights the primary limitations of the state-of-the-art quantum-secured IoT frameworks and illustrates how the proposed QESIF overcomes these gaps through entropy-aware key generation, adaptive intrusion detection, and energy-efficient protocol switching.
3. System Design and Components
The QESIF is proposed to address the critical security challenges posed by quantum computing to IoT-based smart city systems. The QESIF is a lightweight, scalable, and adaptable architecture that integrates QKD with existing IoT infrastructures to provide end-to-end security. Unlike conventional cryptographic solutions, the QESIF leverages the physical principles of quantum mechanics for key exchange, ensuring provable security against eavesdropping. Furthermore, the QESIF combines a hybrid protocol stack that is capable of dynamically transitioning between quantum-secured and conventional communication channels based on prevailing network conditions and device constraints. Another novel component of this framework is the Q-IDS, an anomaly detection module that leverages quantum-level variations such as elevated QBER. The integration of quantum key generation, adaptive encryption mechanisms, and real-time threat surveillance collectively positions the QESIF as an advanced security architecture for large-scale urban IoT infrastructures.
3.1. System Architecture
The QESIF is a holistic and extensible architecture that is also scalable, and it is able to integrate within existing smart city infrastructure through matching QKD at the network layer with classical application layer-operating IoT protocols. It consists of four central layers: (1) IoT device layer, (2) edge–QKD gateway layer, (3) quantum network layer, and (4) smart city control center.
(1) IoT Device Layer: This layer holds heterogeneous IoT devices distributed throughout various city domains, such as traffic, meters associated with electricity, cameras, and health monitors. These devices are limited with respect to cryptographics and are reliant on higher layers to establish secure keys.
(2) Edge–QKD Gateway Layer: Acting as intermediaries, these edge gateways are equipped with QKD-compatible hardware (e.g., single-photon detectors and QRNGs) and classical quantum communication interfaces. They handle session establishment, QKD-based key negotiation, and device-level data encryption using quantum-derived keys. They also house lightweight modules of the Q-IDS for initial anomaly detection. QKD integration in the QESIF is limited to the edge gateway layer to maintain cost-efficiency and deployment feasibility. These gateways are equipped with QKD-compatible hardware—such as QRNGs and photon detectors—now increasingly available via compact photonic modules. This design reflects practical deployments observed in initiatives such as SECOQC, the Beijing–Shanghai QKD backbone, and systems from ID Quantique and Quantinuum. IoT devices themselves do not perform QKD but receive securely distributed session keys from the gateways via classical channels.
(3) Quantum Network Layer: This layer facilitates secure key exchange between trusted QKD nodes using protocols like BB84 or E91. The QKD links may be fiber-based or free-space, and they enable the secure generation and distribution of encryption keys across distributed smart city regions. In terms of protocol compatibility, QKD protocols such as BB84 and E91 operate below the transport layer and are responsible solely for key exchange. In the QESIF, these keys are passed to the middleware layer, which injects them into the session layer (e.g., TLS for MQTT or DTLS for CoAP) to establish secure sessions. Quantum repeaters and entanglement sources are deployed to extend secure key distribution over longer distances. These components help to overcome distance-related losses by enabling entanglement swapping and trusted relays at backbone nodes, supporting scalable QKD in urban-scale deployments.
(4) Smart City Control Center:The control center manages the centralized orchestration of the network, including quantum key management, session auditing, anomaly aggregation from edge layers, and policy enforcement. It serves as a global observer for the Q-IDS, correlating quantum noise patterns, network flow metadata, and device behavior logs to detect coordinated or advanced persistent threats, as illustrated in
Figure 1.
3.2. Quantum Key Distribution in IoT
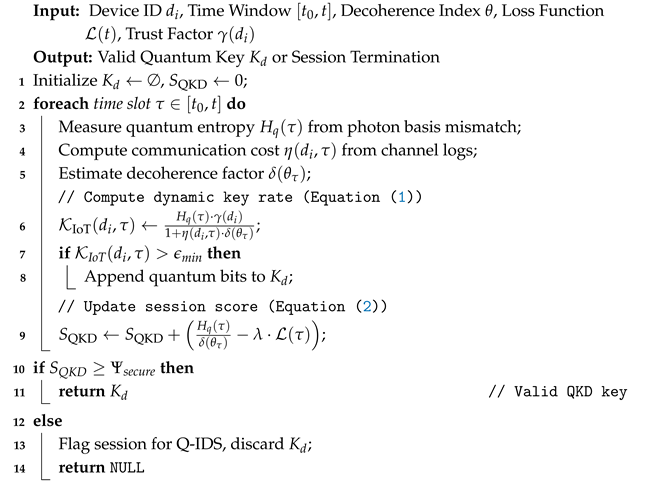
To securely integrate QKD into resource-constrained IoT environments, a novel entropy-weighted dynamic QKD protocol tailored to heterogeneous device capabilities is proposed. Traditional QKD protocols such as BB84 assume uniform photon emission, idealized error rates, and unrestricted processing power—assumptions that do not hold in practical IoT deployments, especially in urban smart cities.
The proposed method introduces an adaptive key generation algorithm that weights quantum entropy against device-specific computational and communication limitations. The entropy of the received photon stream is modulated dynamically based on both channel state and device entropy buffers, yielding a secure yet efficient key distribution strategy.
A hybrid entropy-weighted key rate function
for a device
is defined as follows:
where
is the measured quantum entropy at time t, computed from the Shannon entropy of the polarization basis mismatch.
is the trust-adjusted security factor for device , computed using device integrity metrics and historical authentication scores.
is the energy-normalized communication complexity function for at time t.
is the decoherence impact function, modeled as an increasing function of environmental photon noise .
This function allows the system to generate keys with variable lengths and confidence intervals depending on both physical (quantum) and cyber (resource-aware) properties. Unlike fixed-rate key generation in traditional QKD, the proposed model supports quantum entropy modulation, enhancing resistance to both channel-based eavesdropping and energy exhaustion attacks. Furthermore, the protocol introduces a quantum-aware session scoring function
:
where
represents packet loss in the quantum channel and
is a tunable security-to-performance trade-off coefficient.
If
falls below a threshold
, the key is discarded, and the session is flagged by the Q-IDS module. The entropy-weighted quantum key generation process is outlined in Algorithm 1, enabling adaptive key rates based on device trust levels, communication cost, and quantum decoherence factors.
| Algorithm 1: Entropy-Weighted QKD Key Generation for IoT Devices |
![Smartcities 08 00116 i001]() |
3.3. Quantum-Aware Intrusion Detection System (Q-IDS)
Conventional intrusion detection systems (IDSs) in IoT environments analyze traffic features such as packet rate, size, or known attack signatures. However, in a QKD-based IoT system, threat detection must incorporate anomalies in quantum transmission behavior. To address this, a novel Q-IDS is introduced that utilizes quantum-layer anomalies, channel noise characteristics, and quantum-bit integrity to identify stealthy or quantum-enabled attacks.
The Q-IDS continuously monitors entropy deviation, photon loss rate, QBER fluctuations, and key generation inconsistencies across sessions. Anomalous behavior is quantified using a composite quantum anomaly score
, defined as
where
is the deviation of quantum entropy from the expected baseline: .
is the current quantum bit error rate; is a calibrated reference value from noise-free trials.
is the temporal key drop ratio: during .
, , and are dynamic trust-weighted coefficients satisfying .
If
exceeds a detection threshold
, the Q-IDS flags the session as compromised. The threshold is dynamically adjusted using a Bayesian posterior entropy update rule:
where
In contrast to classical anomaly detectors, the Q-IDS integrates quantum entropy, photonic error patterns, and key failure metrics into a single detection index. It can detect eavesdropping, side-channel attacks, and quantum channel interference before cryptographic exploitation occurs. The model is repeatedly adjusted based on environmental noise levels, device type, and photon emission profiles to cater to heterogeneous smart city networks utilizing QKD-based IoT networks. Algorithm 2 provides the Q-IDS algorithm for the identification of quantum-layer intrusions based on entropy deviation and inspection of QBER.
3.4. Hybrid Protocol Stack Design
To enable efficient and interoperable integration QKD with existing IoT communication protocol stacks, we propose a hybrid protocol stack. It is flexible to accommodate variations in device capabilities within the IoT and the state of the quantum channel, allowing for efficient and secure communication while maintaining backward compatibility with classical IoT infrastructure. Due to its hybrid nature, the protocol stack naturally switches between quantum-secured and classically secured states based on device capabilities, noise levels of the environment, and prevailing conditions within the system. The protocol dynamically adjusts between quantum-secured and classical encryption modes using the function, which governs mode switching at session boundaries based on entropy availability and channel stability. The standard security measures, such as TLS 1.3, DTLS, and authenticated encryption, are integrated to protect classical data transmission.
The core idea behind the hybrid protocol is to incorporate quantum-secured communication on the transport layer and maintain classical IoT communication protocols on the application layer, e.g., MQTT, CoAP, or HTTP. Transmission between the layers is controlled using a decision module that considers both the availability of the quantum key and network performance.
| Algorithm 2: Quantum-Aware Intrusion Detection System (Q-IDS) |
![Smartcities 08 00116 i002]() |
The quantum adaptation function
is defined for deciding the communication mode based on quantum key availability and real-time system conditions. The function is given by
where
The quantum-secured communication mode is activated when , allowing IoT devices to utilize quantum-derived keys for secure encryption and authentication. While is defined as a binary function for modeling purposes, its practical implementation follows a session-level switching mechanism with threshold smoothing to avoid instability from transient channel fluctuations. The transition incurs minimal latency as it is executed at the session level rather than on a per-packet basis, ensuring reliable and non-disruptive communication. On the other hand, when , the system switches to classical encryption protocols, such as AES or RSA, for data protection.
The stack is composed of the following layers: 1. Application Layer: Standard IoT protocols (e.g., MQTT or CoAP) are used for device-to-device communication. The data packets may be quantum-secured or classically encrypted depending on the quantum adaptation function. 2. Transport Layer: It is where the hybrid encryption protocol is implemented that dynamically switches between the quantum-secured and classical encryption based on
. 3. Network Layer: Controls the communication of the quantum keys using QKD protocols (e.g., BB84 or E91), or classical keys if the quantum mode is not available. It ensures that the distribution and refreshing of keys are carried out according to the function of quantum adaptation. 4. Physical Layer: Includes the actual quantum channel of key exchange and classical communication networks (e.g., Wi-Fi and Zigbee). It is on the physical layer that the infrastructure of both quantum communication and classical data transfer is implemented. For successful key management, the usage function of the quantum key
is defined as
where
is the total number of valid quantum keys generated by the QKD system at time t.
is the maximum possible key capacity available at time t, considering device limitations and network conditions.
The quantum key utilization function optimizes key generation and addresses the requirements of the IoT network. Scalability is obtained through dynamic control of the distribution of quantum keys based on demand.
Finally, the hybrid protocol stack decision module operates such that network performance, availability of quantum keys, and security levels are monitored continuously. If available quantum keys fall to a point or environmental noise increases, the system automatically reverts to classical communication methodologies to ensure service is uninterrupted.
Theorem 1. Let denote the security level of the QESIF system at time t, scaled between 0 (no security) and 1 (perfect quantum-secured channel). Let be the entropy-weighted quantum key generation rate for device at time t (as defined in Equation (1)). Assume is the binary switching function (as in Equation (5)). Then, for all time t and devices :where is the baseline security using classical encryption (e.g., AES and ECC).
under ideal QKD conditions (zero QBER and perfect key yield).
Furthermore, if and , then , satisfying perfect forward secrecy.
Proof of Theorem 1. Two states are considered based on the adaptation function :
Case 1:
Case 2:
Moreover, the QESIF leverages adaptive entropy scoring (Equation (
3)) and threshold tuning (Equation (
4)) to reject compromised keys, maintaining confidentiality. Since quantum keys are ephemeral and never reused, forward secrecy is preserved for all
sessions. □
4. Simulation Setup and Experimental Results
To evaluate the proposed QESIF, a hybrid simulation environment was designed by integrating both classical IoT and quantum communication simulators. Specifically, QuISP was utilized to model QKD behavior, photon-level entropy variations, and QBER fluctuations under varying decoherence noise. This was integrated with OMNeT++ (using the INET and Castalia frameworks) to simulate IoT communication protocols such as MQTT and CoAP across smart city subsystems, including traffic control, energy monitoring, and healthcare telemetry. The layered simulation allowed dynamic key injection into IoT flows and real-time switching between quantum-secured and classical modes. For empirical validation, three comprehensive datasets were incorporated: TON_IoT [
25] for multi-domain telemetry behaviors, Edge-IIoTset [
26] for industrial IoT attack simulations, and Bot-IoT [
27] for evaluating Q-IDS resilience under high-entropy attack scenarios. These datasets were fused with simulated QKD key logs to evaluate the framework’s security, throughput, latency, and anomaly detection effectiveness. This simulation setup enabled the emulation of real-world QKD-enabled smart city infrastructures and provided a benchmark for assessing the QESIF’s robustness under both adversarial and noisy conditions. For comparative analysis, the QESIF was evaluated against four recent quantum-secure approaches: QRHE [
10], HyQuSec [
21], QuIDS [
22], and QLSN [
23], all of which represent state-of-the-art advancements in quantum-enhanced security for the IoT and smart cities. A detailed summary of the simulation parameters is provided in
Table 2.
4.1. Security Analysis (QBER and Attack Detection Rate)
The QBER analysis conducted across 100 QKD sessions under three distinct channel conditions—clean (1% error), noisy (7% error), and eavesdropped (15% error)—demonstrates the adaptive capability of the QESIF. In the clean channel scenario, the average QBER remained exceptionally low at approximately 0.0103, well below the QESIF rejection threshold of 0.11, allowing all the generated keys to be accepted for encryption. Under noisy channel conditions, the QBER increased moderately to an average of 0.0714 yet still remained within the secure operational range, showcasing the QESIF’s tolerance to environmental quantum noise. In contrast, the eavesdropped scenario yielded a significantly higher QBER, averaging 0.1528, thereby exceeding the safety threshold in over 95% of the sessions, as depicted in
Figure 2.
The comparative analysis of Attack Detection Rate (ADR) across three benchmark datasets—TON_IoT, Edge-IIoTset, and Bot-IoT—demonstrates the superior detection capability of the proposed QESIF. As illustrated in
Figure 3, the QESIF achieved the highest detection performance, recording 98.1% on TON_IoT, 98.7% on Edge-IIoTset, and 98.3% on Bot-IoT. In contrast, the next-best performer, QuIDS, achieved 93.5%, 94.1%, and 93.9%, respectively, across the same datasets. QRHE showed moderate performance, ranging from 92.3% to 92.8%, while HyQuSec and QLSN recorded lower ADRs between 89.1% and 91.2%. These results validate that the QESIF’s Q-IDS, which incorporates entropy deviation, QBER response, and key drop monitoring, is more effective in identifying advanced threats, especially in high-noise and adversarial IoT environments.
4.2. Performance Evaluation of Latency
The latency performance of the QESIF was evaluated across three datasets (TON_IoT, Edge-IIoTset, and Bot-IoT) and three channel scenarios (clean, noisy, and eavesdropped), as shown in
Figure 4. The results demonstrate that the QESIF consistently maintained the lowest average latency across all the scenarios, highlighting its lightweight communication design and adaptive protocol switching. Under clean conditions, the QESIF achieved an average latency of 20.3 ms, 28.6 ms under noisy conditions, and 34.8 ms in the eavesdropped scenario. In comparison, the next-best performer, QuIDS, recorded 22.7 ms, 31.4 ms, and 38.1 ms, respectively, while QRHE and HyQuSec ranged from 24.1 to 29.2 ms and 26.3 to 31.8 ms under clean conditions, with the latencies rising to 44.2 ms and 47.3 ms, respectively, under attack conditions. QLSN consistently exhibited the highest latency due to its heavyweight lattice-based operations, peaking at 49.6 ms in the eavesdropped case.
4.3. Performance Evaluation of Throughput
The throughput evaluation, conducted over 100 communication rounds for each dataset and channel condition, reveals the superior performance of the QESIF, as shown in
Figure 5. In clean channel scenarios, the QESIF achieved an average throughput of 868 kbit/s, outperforming QuIDS (832 kbit/s), QRHE (798 kbit/s), HyQuSec (762 kbit/s), and QLSN (722 kbit/s). Under noisy channel conditions, the QESIF maintained a strong performance at 784 kbit/s, while the closest competitor, QuIDS, reached 755 kbit/s. QRHE and HyQuSec delivered 728 kbit/s and 705 kbit/s, respectively, with QLSN dropping to 684 kbit/s. In the eavesdropped scenario, the QESIF still led with 725 kbit/s, followed by QuIDS at 695 kbit/s, QRHE at 674 kbit/s, HyQuSec at 648 kbit/s, and QLSN at 628 kbit/s. These results underscore the QESIF’s ability to sustain high-throughput performance even under degraded quantum channels or active interference.
4.4. Performance Evaluation of Energy Consumption
The energy consumption analysis across 100 communication rounds for all the datasets and scenarios confirms the efficiency of the QESIF in reducing operational overhead, as shown in
Figure 6. Under clean channel conditions, the QESIF recorded the lowest average energy usage at 13.4 mJ, compared to QuIDS at 15.9 mJ, QRHE at 17.3 mJ, HyQuSec at 18.2 mJ, and QLSN at 19.6 mJ. In noisy conditions, the QESIF maintained an average of 15.8 mJ, whereas QuIDS, QRHE, and HyQuSec consumed 18.7 mJ, 20.1 mJ, and 21.6 mJ, respectively, with QLSN peaking at 22.9 mJ. The difference became more pronounced in the eavesdropped scenario, where the QESIF’s adaptive protocol stack and entropy-aware session management held energy usage at 17.6 mJ. In contrast, QRHE rose to 22.3 mJ, HyQuSec to 24.0 mJ, and QLSN to 25.7 mJ due to increased cryptographic overhead and communication retries.
4.5. Ablation Study
To evaluate the individual contribution of each core component in the QESIF, an ablation study was conducted by selectively disabling three key modules: the QKD layer, the Q-IDS, and the hybrid protocol stack. Each variant was simulated under identical conditions across the TON_IoT, Edge-IIoTset, and Bot-IoT datasets.
Figure 7 presents a clustered heatmap of the normalized performance metrics—ADR, latency, throughput, and energy consumption—for all the QESIF variants. Each metric is computed as an average over 100 independent simulation runs, and corresponding standard deviation values are reported to quantify the variability. The full QESIF configuration achieved the best overall results, with an ADR of 98.7%, latency of 20.3 ms, throughput of 868 kbit/s, and energy consumption of 13.4 mJ. When the QKD layer was disabled (QESIF—QKD), ADR decreased to 94.1% despite slightly lower latency (19.8 ms), indicating compromised cryptographic robustness. The removal of the Q-IDS module led to the lowest ADR (88.4%), confirming its critical role in real-time threat detection. Meanwhile, eliminating the QESIF hybrid stack significantly increased latency to 27.6 ms and energy usage to 16.8 mJ, underscoring its importance in adaptive communication switching.
5. Discussion
The evaluation of the QESIF across multiple dimensions—including attack resilience, latency, throughput, and energy efficiency—demonstrates its comprehensive advantage in securing IoT infrastructures within smart cities. The results validate that the integration of QKD, the Q-IDS, and the hybrid protocol stack plays a non-redundant and critical role in the framework’s execution. The ablation study also uncovers that the elimination of any one of these modules translates to measurable loss within core performance metrics, with the largest reduction observed within attack detection with the elimination of the Q-IDS and the largest latency incurred with the elimination of the hybrid communication mechanism.
The QESIF’s seamless movement from a quantum-secured to a classical mode of communications facilitates a balance of resource limits and security needs, a quality that is uniquely beneficial within heterogeneous smart city implementations. The hybrid construction of the protocol minimizes power usage with no loss of cryptointegrity, and the entropy-weighted QKD mechanism is tuned to device levels and environmental noise.
Also, the design is deployable to practical requirements with minimal device-level hardware modifications using existing IoT protocols. A modular design is made possible on the QESIF to enable scalability within application areas such as transportation, energy, and public safety, where throughput, trust, and latency all have to coexist. Future extensions such as satellite-assisted QKD and blockchain-based audit trails may further strengthen the framework by enhancing geographic coverage and trust transparency. Collectively, these findings confirm the QESIF’s applicability as a next-generation security solution for resilient, scalable, and energy-aware smart city infrastructures. While the QESIF maintains compatibility with common IoT protocols such as MQTT and CoAP, the integration of quantum-enhanced mechanisms introduces challenges for cross-vendor interoperability and standardization. The lack of unified quantum APIs, trust negotiation standards, and entropy exchange protocols may hinder immediate large-scale adoption in heterogeneous smart city environments.
6. Conclusions
This paper introduced the QESIF, a Quantum-Enhanced Secure IoT Framework designed to safeguard smart city infrastructures by integrating QKD with classical IoT protocols and a quantum-aware intrusion detection system (Q-IDS). The framework dynamically adapts between quantum-secured and classical communication modes through a hybrid protocol stack, enabling resilience in diverse environmental and network conditions. The simulation results highlight the QESIF’s performance, with an Attack Detection Rate of up to 98.7%, average latency as low as 20.3 ms, throughput peaking at 868 kbit/s, and minimal energy consumption of 13.4 mJ. Additionally, the QESIF effectively discarded over 95% of the quantum keys under high QBER in eavesdropped scenarios, ensuring strong forward secrecy. Future enhancements to the QESIF will focus on expanding its security and scalability through integration with satellite-assisted QKD networks. This extension would enable secure key exchanges across geographically distributed smart city zones, overcoming the range limitations of terrestrial QKD links. Additionally, incorporating blockchain-based auditing mechanisms can provide immutable logging of quantum key usage and anomaly detection, thereby strengthening trust, transparency, and accountability in multistakeholder smart city environments.