Digital Technologies’ Risks and Opportunities: Case Study of an RFID System
Abstract
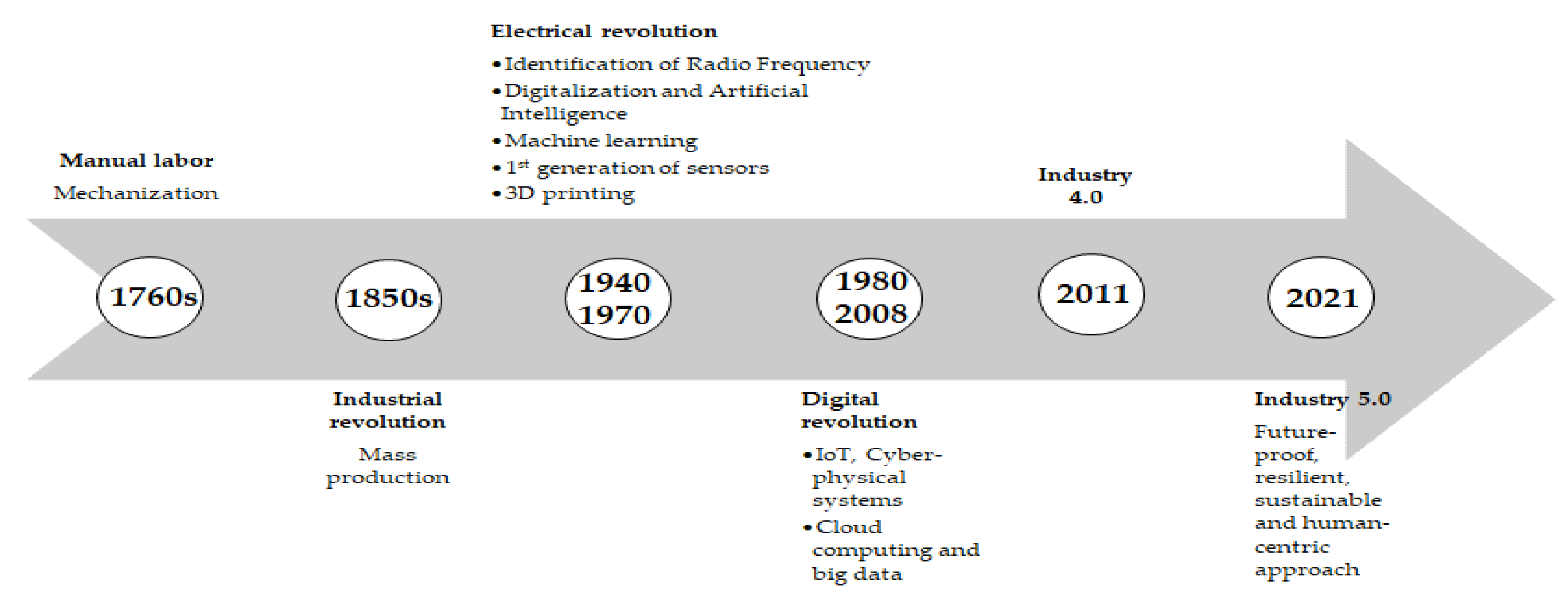
1. Introduction
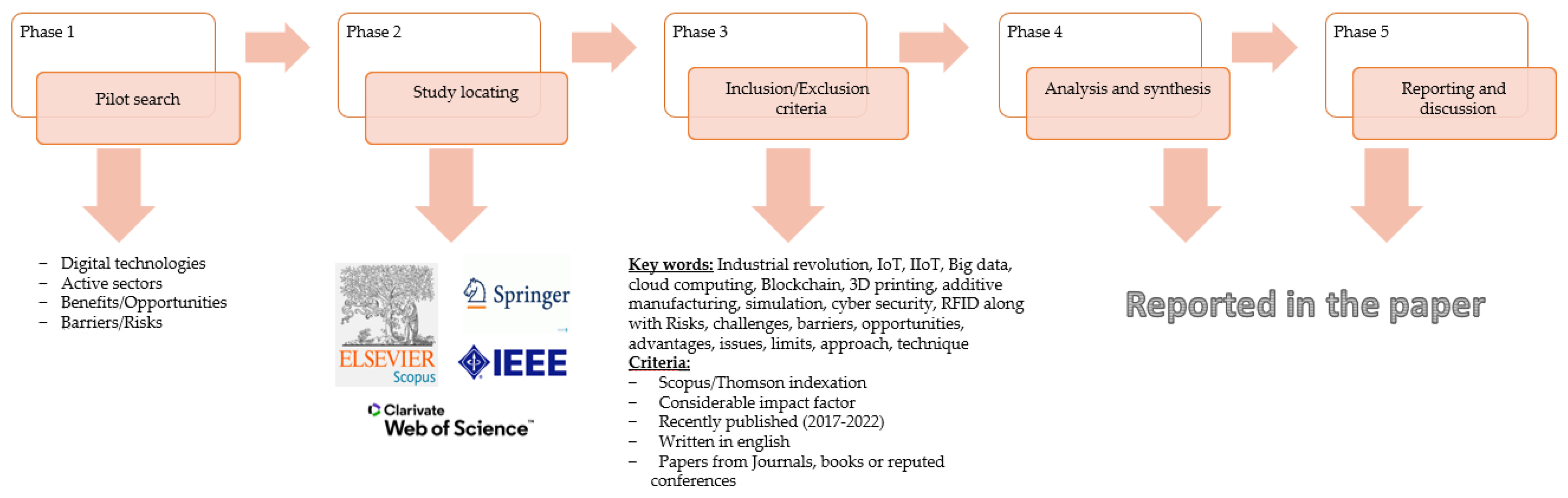
2. Contribution and Research Methodology
3. X.0 Technologies
3.1. 3D printing/Additive Manufacturing (AM)
3.2. Augmented Reality
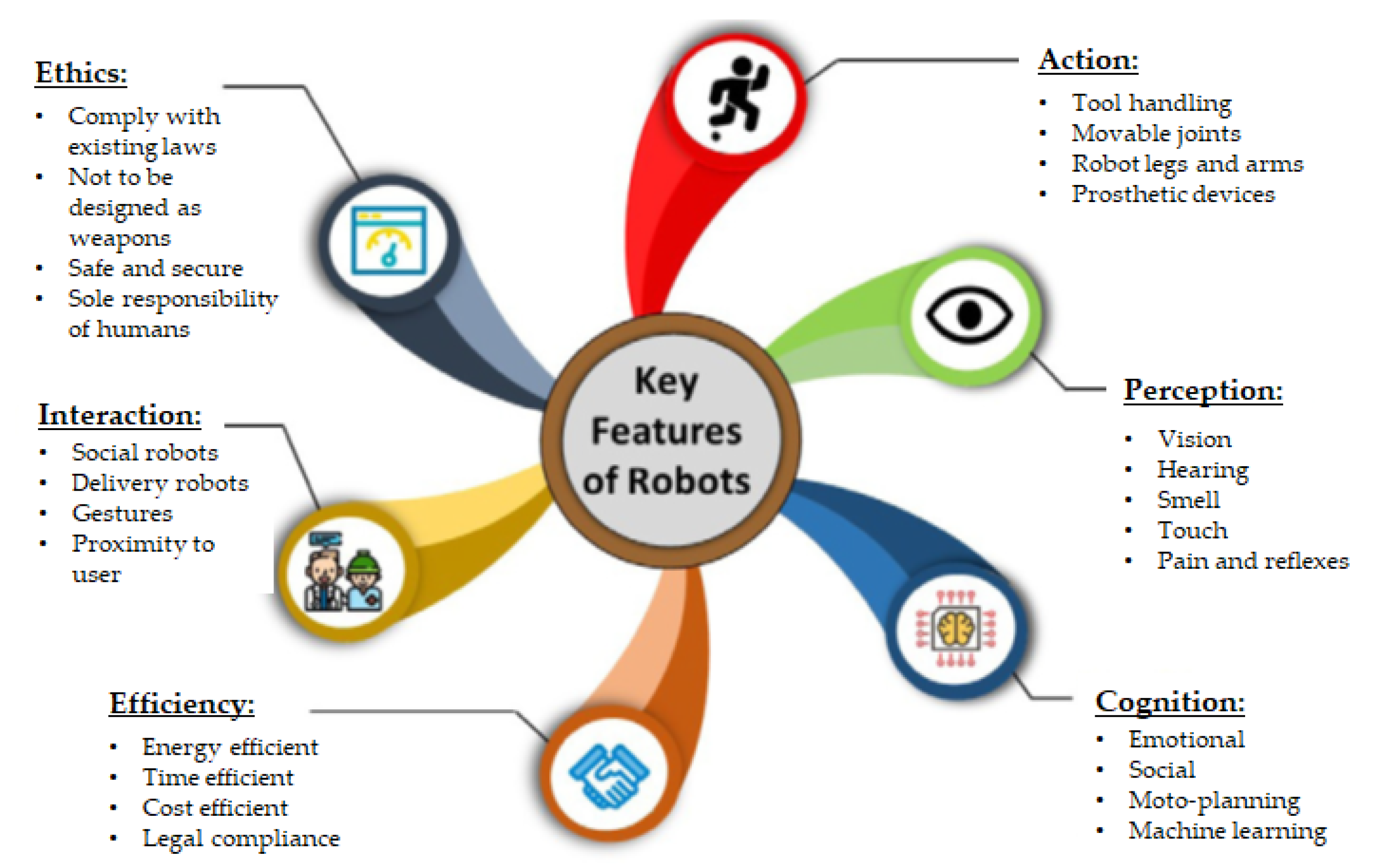
3.3. Robotics
3.4. Cybersecurity
3.5. Blockchain
- −
- distribution: a resilient and secured system through storage of information on multiple computers;
- −
- traceability: all transactions are traceable;
- −
- anonymity: addresses’ owners’ name is only used to prove the ownership of a private key. Transactions can be done anonymously;
- −
- decentralization: transactions are managed without a central authority;
- −
- immutability: once accepted, it is not possible to modify data;
- −
- cost friendly: open-source software with low maintenance costs;
- −
- autonomy: data exchange, record, and update are performed in a trustworthy environment using consensus-based specifications and protocols. Therefore, it ensures the authenticity of the recorded transaction on the blockchain without human intervention.
3.6. IoT/IIoT
3.7. Big Data
3.8. Cloud Computing
3.9. Radio-Frequency Identification (RFID)
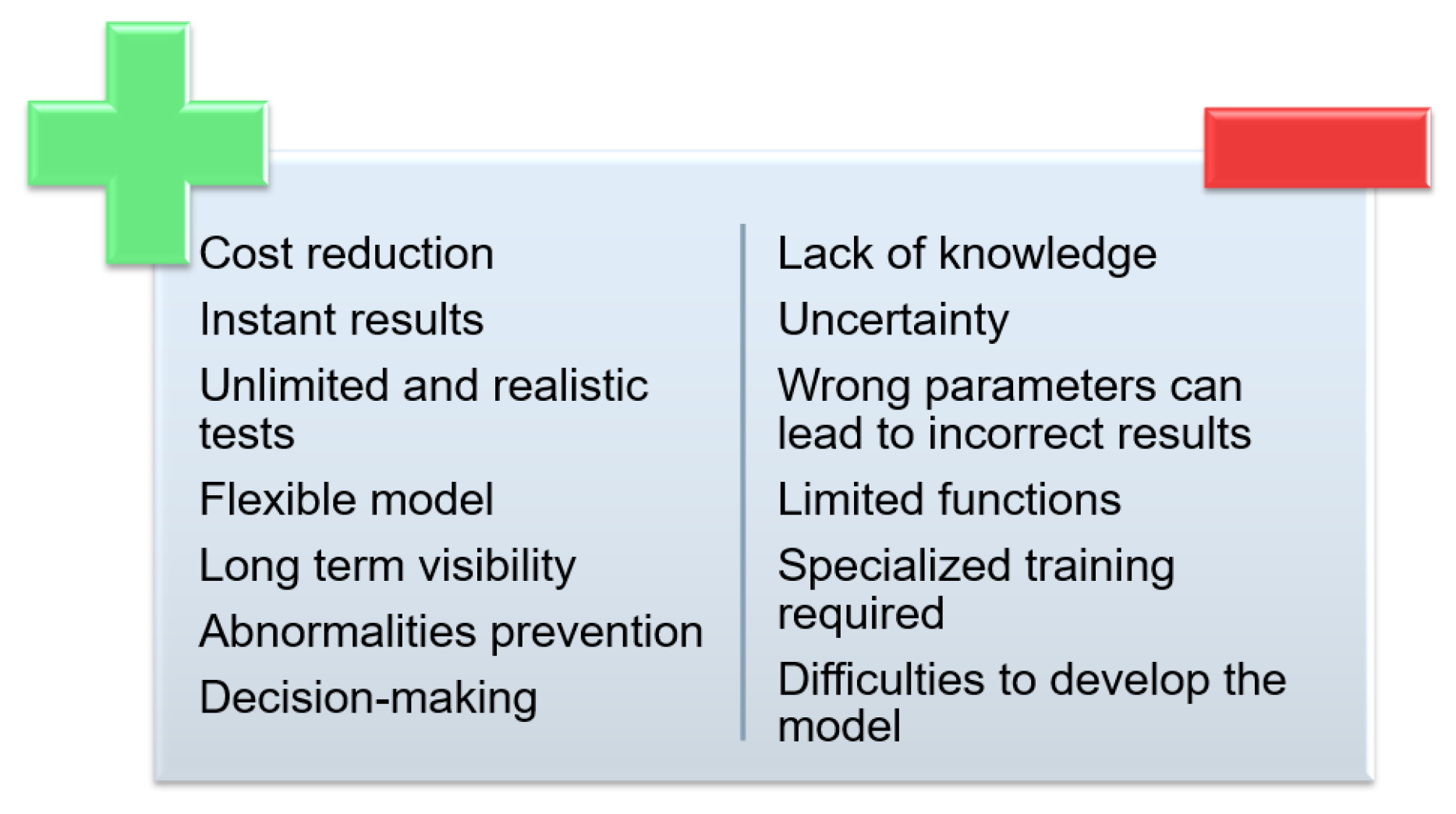
3.10. Simulation
3.11. Analysis and Discussion
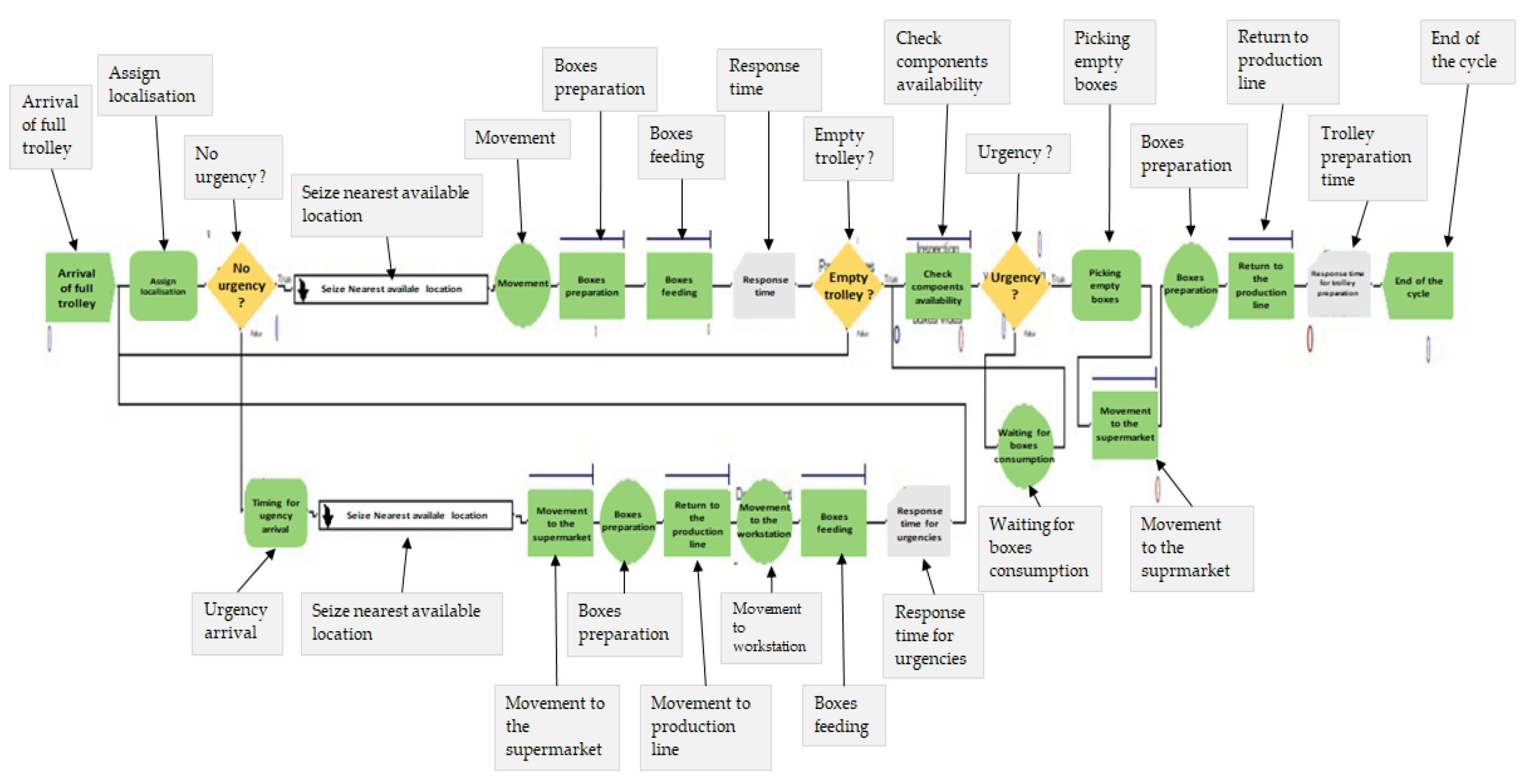
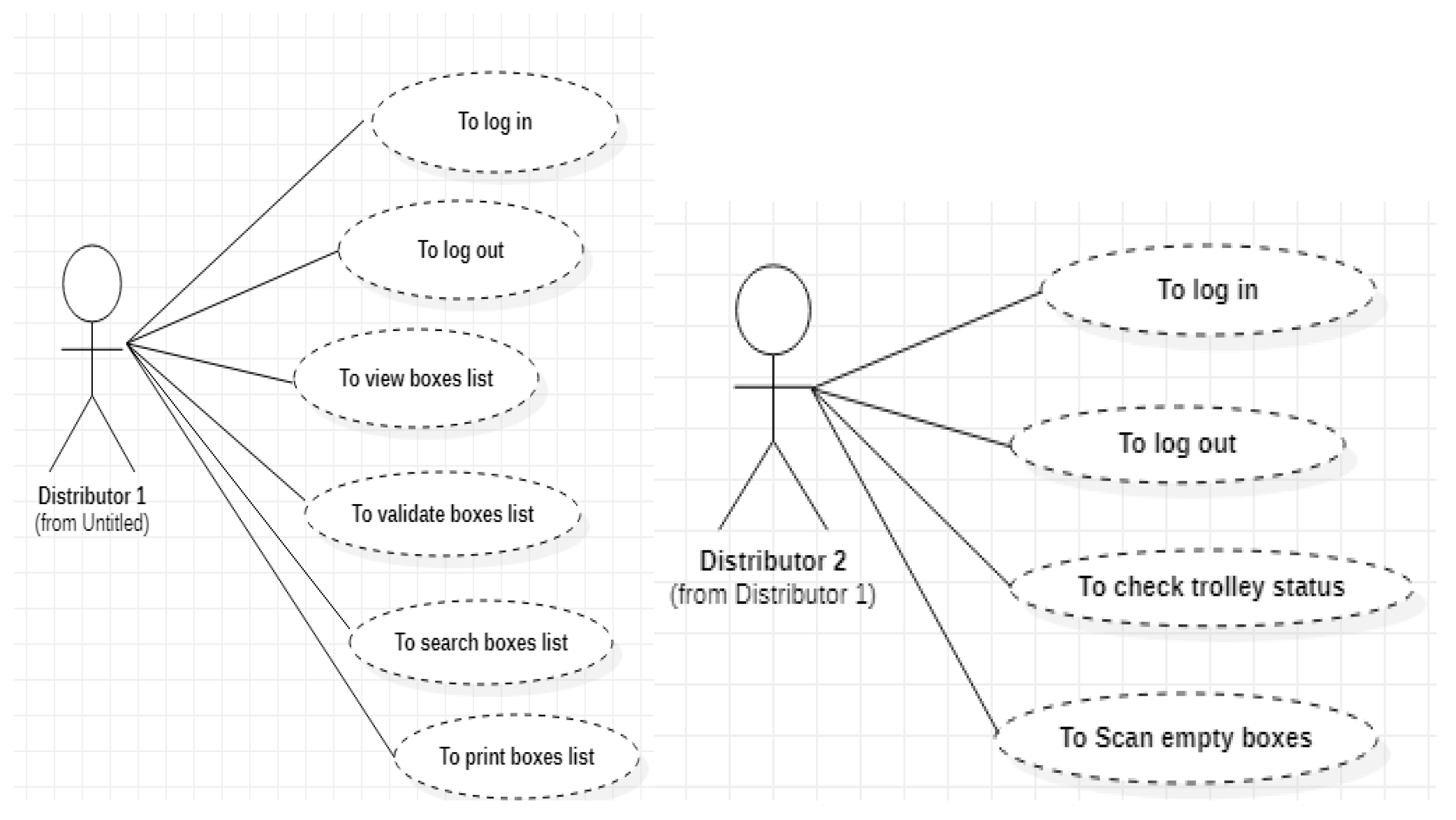
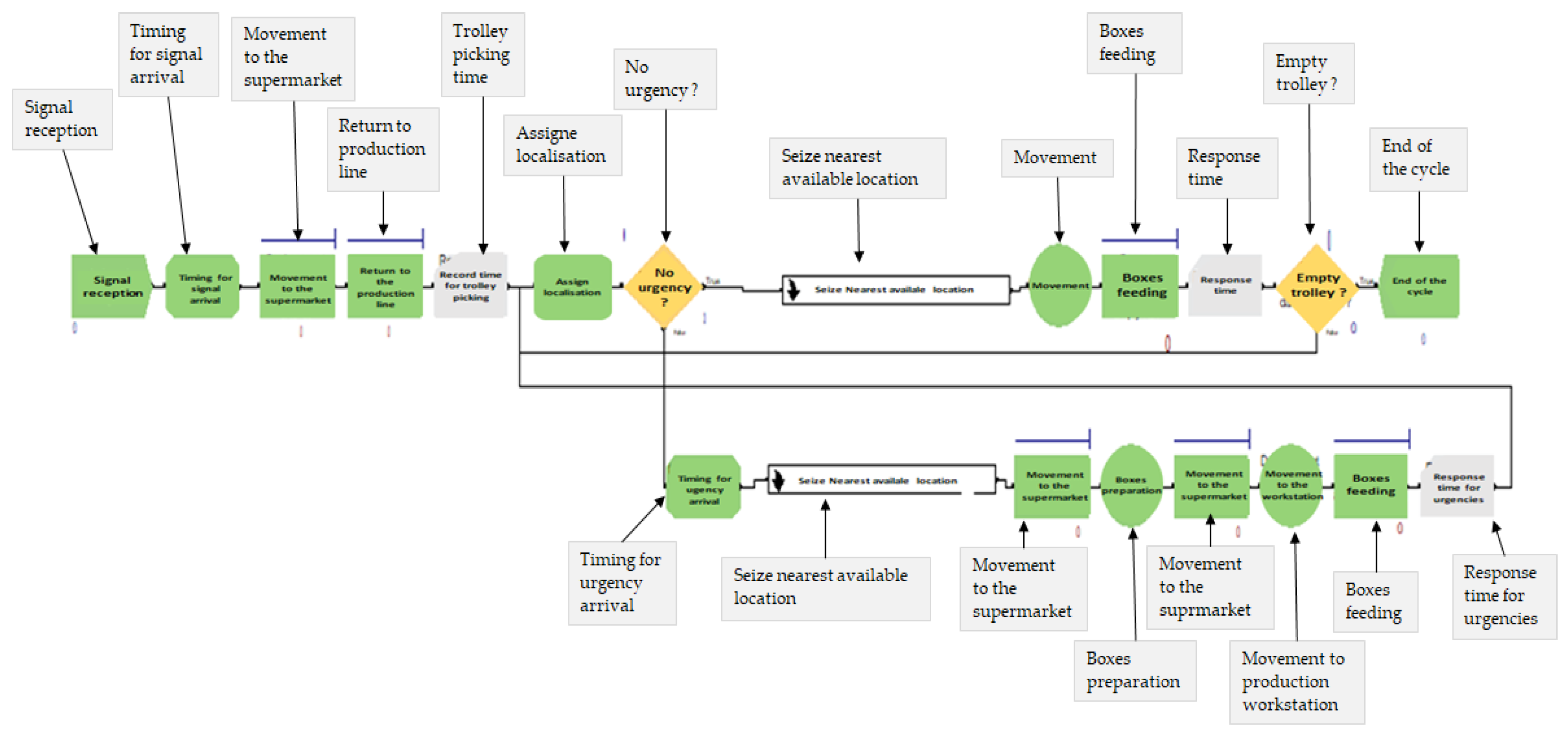
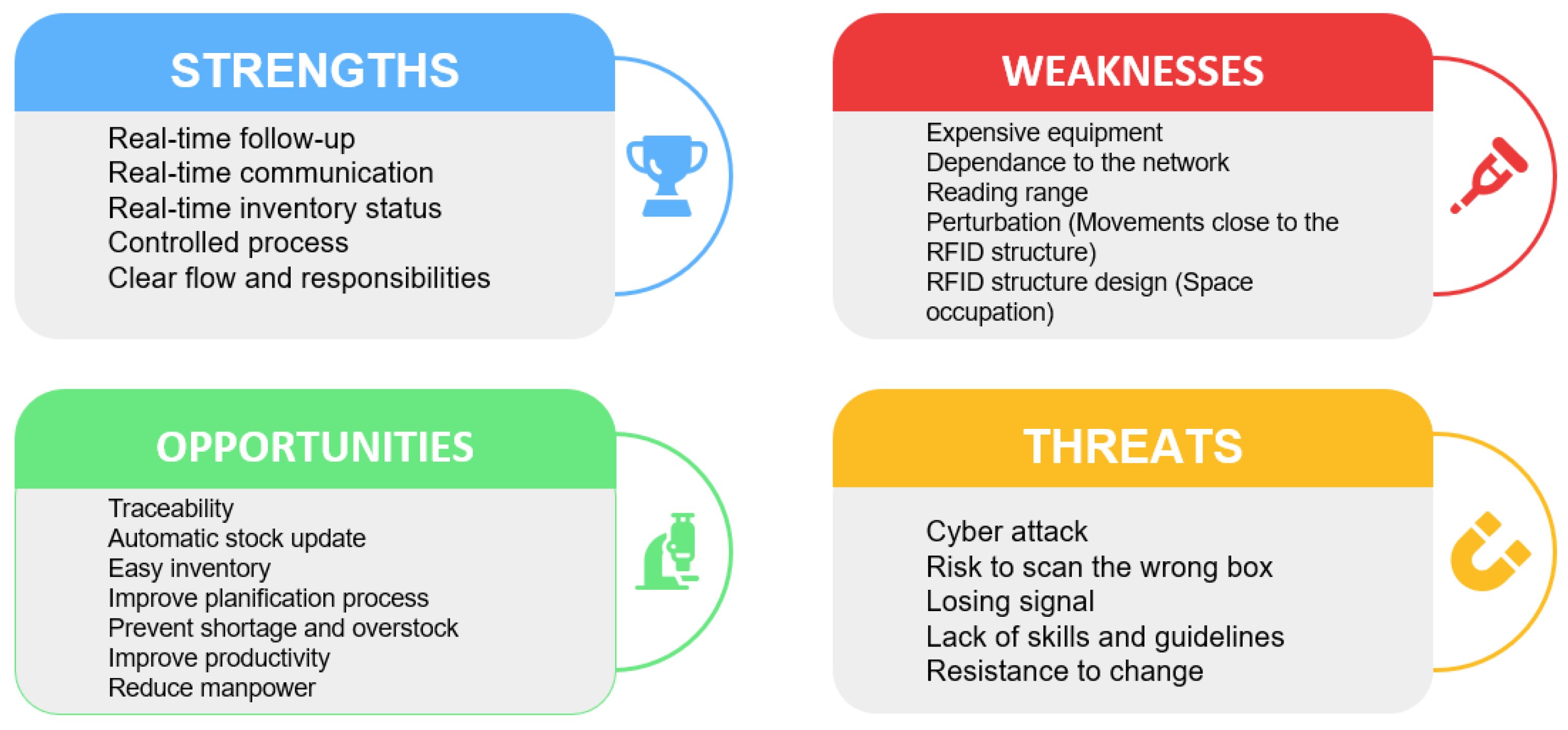
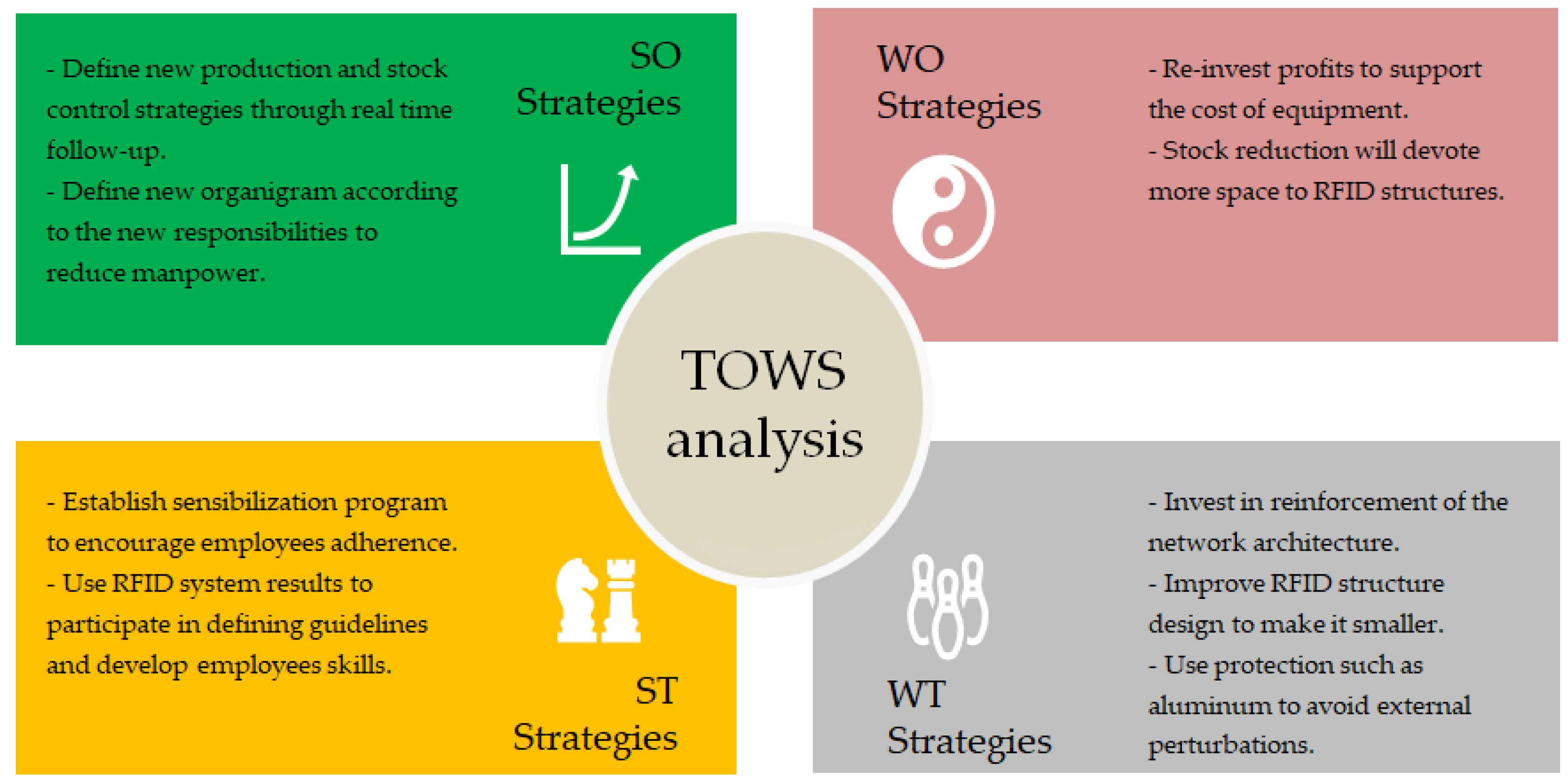
4. Case study Simulation: Risks and Opportunities of an RFID System
5. Conclusions and Perspectives
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Marzano, G.; Martinovs, A. Teaching Industry 4.0. Soc. Integr. Educ. Proc. Int. Sci. Conf. 2020, 2, 69–76. [Google Scholar] [CrossRef]
- Gallab, M.; Bouloiz, H.; Kébé, A.S.; Tkiouat, M. Opportunities and Challenges of the Industry 4.0 in industrial companies: A Survey on Moroccan firms. J. Ind. Bus. Econ. 2021, 48, 413–439. [Google Scholar] [CrossRef]
- Relich, M. The impact of ICT on labor productivity in the EU. Inf. Technol. Dev. 2017, 23, 706–722. [Google Scholar] [CrossRef]
- Marina, M.; Abrar Ali, D.; Mukund, J.; Izabela, N. Lean manufacturing and Industry 4.0 combinative application: Practices and perceived benefits. IFAC PapersOnLine 2021, 54, 288–293. [Google Scholar]
- McKiea, M.G.; Jonesb, R.; Milesc, J.; Jonesd, I.R. Improving Lean Manufacturing Systems and Tools Engagement Through the Utilisation of Industry 4.0. Improved Communication and a People Recognition Methodology in a UK Engine Manufacturing Centre. Procedia Manuf. 2021, 55, 371–382. [Google Scholar] [CrossRef]
- ISO 31000.2018; Risk Management—Guidelines. International Organization for Standardization ISO Central Secretariat: Geneva, Switzerland, 2018.
- Sishi, M.; Telukdarie, A. Implementation of Industry 4.0 technologies in the mining industry—A case study. Int. J. Min. Miner. Eng. 2020, 11, 1–22. [Google Scholar] [CrossRef]
- Frank, A.G.; Dalenogare, L.S.; Ayala, N.F. Industry 4.0 technologies: Implementation patterns in Manufacturing companies. Int. J. Prod. Econ. 2019, 210, 15–26. [Google Scholar] [CrossRef]
- Xiaoyong, T.; Wu, L.; Gu, D.; Yuan, S.; Zhao, Y.; Li, X.; Ouyang, L.; Song, B.; Gao, T.; He, J.; et al. Roadmap for Additive Manufacturing: Toward Intellectualization and Industrialization. Chin. J. Mech. Eng. Addit. Manuf. Front. 2022, 1, 100014. [Google Scholar]
- Jandyal, A.; Chaturvedi, I.; Wazir, I.; Ankush, R.; Haq, M.I.U. 3D printing–A review of processes, materials and applications in industry 4.0. Sustain. Oper. Comput. 2022, 3, 33–42. [Google Scholar] [CrossRef]
- Davies, S. 3D Printing is the new face of medicine. Financial Times, 14 November 2013. [Google Scholar]
- Petrick, I.J.; Simpson, T.W. 3D Printing disrupts Manufacturing: How economies of one create new rules of competition. Res. -Technol. Manag. 2013, 56, 12–16. [Google Scholar] [CrossRef]
- Sandström, C.G. The non-disruptive emergence of an ecosystem for 3D printing–insights from the hearing aid industry’s transition 1989–2008. Technol. Forecast. Soc. Chang. 2016, 102, 160–168. [Google Scholar] [CrossRef]
- Wohlers, T. Wohlers Report 2020: 3D Printing and Additive Manufacturing Global State of the Industry; Technical Report; Wohlers Associates: Fort Collins, CO, USA, 2020. [Google Scholar]
- Shahrubudin, N.; Koshy, P.; Alipal, J.C.; Kadir, M.H.A.; Lee, T.C. Challenges of 3D printing technology for manufacturing biomedical products: A case study of Malaysian manufacturing firms. Heliyon 2020, 6, e03734. [Google Scholar] [CrossRef]
- Li, J.Q.; Yuy, F.R.; Deng, G.; Luo, C.; Ming, Z.; Yan, Q. Industrial Internet: A survey on the enabling technologies, applications, and challenge. IEEE Commun. Surv. Tutor. 2017, 19, 1504–1526. [Google Scholar] [CrossRef]
- Deshpande, A.; Kim, I. The effects of augmented reality on improving spatial problem solving for object assembly. Adv. Eng. Inform. 2018, 38, 760–775. [Google Scholar] [CrossRef]
- Chytas, D.; Johnson, E.O.; Piagkou, M.; Mazarakis, A.; Babis, G.C.; Chronopoulos, E.; Nikolaou, V.S.; Lazaridis, N.; Natsis, K. The role of augmented reality in anatomical education: An overview. Ann. Anat. Anat. Anz. 2020, 229, 151463. [Google Scholar] [CrossRef] [PubMed]
- Ibáñez, M.-B.; Delgado-Kloos, C. Augmented reality for stem learning: A systematic review. Comput. Educ. 2018, 123, 109–123. [Google Scholar] [CrossRef]
- Ameri, G.; Rankin, A.; Baxter, J.S.; Moore, J.; Ganapathy, S.; Peters, T.M.; Chen, E.C. Development and evaluation of an augmented reality ultrasound guidance system for spinal anesthesia: Preliminary results. Ultrasound Med. Biol. 2019, 45, 2736–2746. [Google Scholar] [CrossRef] [PubMed]
- Nee, A.; Ong, S. Virtual and augmented reality applications in Manufacturing. IFAC Proc. Vol. 2013, 46, 15–26. [Google Scholar] [CrossRef]
- Lamberti, F.; Manuri, F.; Sanna, A.; Paravati, G.; Pezzolla, P.; Montuschi, P. Challenges, opportunities, and future trends of emerging techniques for augmented reality-based maintenance. IEEE Trans. Emerg. Top. Comput. 2014, 2, 411–421. [Google Scholar] [CrossRef]
- Loizeau, Q.; Danglade, F.; Ababsa, F.; Merienne, F. Evaluating added value of aug-mented reality to assist aeronautical maintenance workers—Experimentation on on-field use case. In Virtual Reality and Augmented Reality; Bourdot, P., Interrante, V., Nedel, L., Magnenat-Thalmann, N., Zachmann, G., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 151–169. [Google Scholar]
- Setti, A.; Bosetti, P.; Ragni, M. Artool-augmented reality platform for machining setup and maintenance. In Proceedings of SAI Intelligent Systems Conference (IntelliSys); Bi, Y., Kapoor, S., Bhatia, R., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 457–475. [Google Scholar]
- Parida, K.; Bark, H.; Lee, P.S. Emerging thermal technology enabled augmented reality. Adv. Funct. Mater. 2021, 31, 2007952. [Google Scholar] [CrossRef]
- Segovia, D.; Ramírez, H.; Mendoza, M.; Mendoza, M.; Mendoza, E.; González, E. Machining and dimensional validation training using augmented reality for a lean process. Procedia Comput. Sci. 2015, 75, 195–204. [Google Scholar] [CrossRef]
- Mourtzis, D.; Zogopoulos, V.; Vlachou, E. Augmented reality application to support remote maintenance as a service in the robotics industry. Procedia CIRP 2017, 63, 46–51. [Google Scholar] [CrossRef]
- Mourtzis, D.; Angelopoulos, J.; Panopoulos, N. A framework for automatic generation of augmented reality maintenance & repair instructions based on convolutional neural networks. Procedia CIRP 2020, 93, 977–982. [Google Scholar]
- Jeffri, N.F.S.; Rambli, D.R.A. A review of augmented reality systems and their effects on mental workload and task performance. Heliyon 2021, 7, e06277. [Google Scholar] [CrossRef] [PubMed]
- Zhang, P.; Liu, H.; Li, H.; Wang, J.J. The application of navigation system based on augmented reality head-mounted devices in spine surgery. Neurosci. Inform. 2022, 2, 100076. [Google Scholar] [CrossRef]
- Balco, P.; Bajzík, P.; Škovierová, K. Virtual and Augmented Reality in Manufacturing Companies in Slovakia. Procedia Comput. Sci. 2022, 1, 313–320. [Google Scholar] [CrossRef]
- Carl, B.; Bopp, M.; Saß, B.; Nimsky, C. Microscope-based augmented reality in degenerative spine surgery: Initial experience. World Neurosurg. 2019, 128, e541–e551. [Google Scholar] [CrossRef]
- Anon. IFR Press Conference. 2019. Available online: https://ifr.org/downloads/press2018/IFR%20World%20Robotics%20Presentation%20-%2018%20Sept%202019.pdf (accessed on 25 June 2022).
- Aditya, U.S.P.S.; Singh, R.; Singh, P.K.; Kalla, A. A Survey on Blockchain in Robotics: Issues, Opportunities, Challenges and Future Directions. J. Netw. Comput. Appl. 2021, 196, 103245. [Google Scholar]
- Lin, P.; Abney, K.; Bekey, G. Robot ethics: Mapping the issues for a mechanized world. Artif. Intell. 2011, 175, 942–949. [Google Scholar] [CrossRef]
- Flechsig, C.; Anslinger, F.; Lasch, R. Robotic Process Automation in purchasing and supply management: A multiple case study on potentials, barriers, and implementation. J. Purch. Supply Manag. 2022, 28, 100718. [Google Scholar] [CrossRef]
- Bauer, W.; Bender, M.; Braun, M.; Rally, P.; Scholtz, O. Lightweight Robots in Manual Assembly—Best to Start Simply! Examining Companies’ Initial Experiences with Lightweight Robots; Fraunhofer Institute for Industrial Engineering IAO: Stuttgart, Germany, 2016. [Google Scholar]
- Zinn, M.; Roth, B.; Khatib, O.; Salisbury, J.K. A new actuation approach for human friendly robot design. Int. J. Robot. Res. 2004, 23, 379–398. [Google Scholar] [CrossRef]
- Riek, L.; Howard, D. A code of ethics for the human-robot interaction profession. Proc. We Robot 2014. Available online: https://ssrn.com/abstract=2757805 (accessed on 25 June 2022).
- Kopacek, P. Roboethics. IFAC Proc. Vol. 2012, 45, 67–72. [Google Scholar] [CrossRef]
- Rao, R.V.; Selvamani, K. Data Security Challenges and Its Solutions in Cloud Computing. Procedia Comput. Sci. 2015, 48, 204–209. [Google Scholar] [CrossRef]
- Cao, L.; Li, Y.; Zhang, J.; Jiang, Y.; Han, Y.; Wei, J. Electrical load prediction of healthcare buildings through single and ensemble learning. Energy Rep. 2020, 6, 2751–2767. [Google Scholar] [CrossRef]
- Chen, M. Smart city and cyber-security; technologies used, leading challenges and future recommendations. Energy Rep. 2021, 7, 7999–8012. [Google Scholar]
- Zheng, Y.; Li, Z.; Xu, X.; Zhao, Q. Dynamic defenses in cyber security: Techniques, methods and challenges. Digit. Commun. Netw. 2020, 8, 422–435. [Google Scholar] [CrossRef]
- Uchendu, B.; Nurse, J.R.; Bada, M.; Furnell, S. Developing a cyber security culture: Current practices and future needs. Comput. Secur. 2021, 109, 102387. [Google Scholar] [CrossRef]
- Gunes, B.; Kayisoglu, G.; Bolat, P. Cyber security risk assessment for seaports: A case study of a container port. Comput. Secur. 2021, 103, 102196. [Google Scholar] [CrossRef]
- Chaum, D. Computer Systems Established, Maintained, and Trusted by Mutually Suspicious Groups. Ph. D Thesis, University of California, Berkeley, CA, USA, 1982. [Google Scholar]
- Angelis, J.; da Silva, E.R. Blockchain adoption: A value driver perspective. Bus. Horiz. 2019, 62, 307–314. [Google Scholar] [CrossRef]
- Gatteschi, V.; Lamberti, F.; Demartini, C.; Pranteda, C.; Santamaria, V. To blockchain or not to blockchain: That is the question. IT Prof. 2018, 20, 62–74. [Google Scholar] [CrossRef]
- Hoy, M.B. An introduction to the blockchain and its implications for libraries and medicine. Med. Ref. Serv. Q 2017, 36, 273–279. [Google Scholar] [CrossRef] [PubMed]
- Panetta, K. Gartner the CIO’s Guide to Blockchain. 2019. Available online: https://www.gartner.com/smarterwithgartner/the-cios-guide-to-blockchain/ (accessed on 25 June 2022).
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. BlockChain technology: Beyond Bitcoin. Appl. Innov. Rev. 2016, 2, 71. [Google Scholar]
- Marchesi, L.; Marchesi, M.; Tonelli, R.; Lunesu, M.I. A blockchain architecture for industrial applications. Blockchain Res. Appl. 2022, 3, 100088. [Google Scholar] [CrossRef]
- Chen, Y.; Chen, H.; Zhang, Y.; Han, M.; Siddula, M.; Cai, Z. A survey on blockchain systems: Attacks, defenses, and privacy preservation. High Confid. Comput. 2022, 2, 100048. [Google Scholar] [CrossRef]
- Munim, Z.H.; Balasubramaniyan, S.; Kouhizadeh, M.; Hossain, N.U.I. Using Bayesian Best Worst Method to assess blockchain technology adoption in the Norwegian oil and gas industry. J. Ind. Inf. Integr. 2022, 28, 100346. [Google Scholar]
- Fang, L.; Li, Z.; He, Z. Research on the progress in cross-chain technology of blockchains. J. Softw. 2019, 30, 1649–1660. [Google Scholar]
- Iqbal, M.; Matulevičius, R. Exploring sybil and double-spending risks in blockchain systems. IEEE Access 2021, 9, 76153–76177. [Google Scholar] [CrossRef]
- Yli-Huumo, J.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where Is Current Research on Blockchain Technology? A Systematic Review. PLoS ONE 2016, 11, e0163477. [Google Scholar] [CrossRef]
- Hassani, H.L.; Bahnasse, A.; Martin, E.; Roland, C.; Bouattane, O.; Diouri, M.E.M. Vulnerability and security risk assessment in a IIoT environment in compliance with standard IEC 62443. Procedia Comput. Sci. 2021, 191, 33–40. [Google Scholar] [CrossRef]
- Florea, B.C. Blockchain and internet of things data provider for smart applications. In Proceedings of the 7th Mediterranean Conference on Embedded Computing (MECO), Budva, Montenegro, 10–14 June 2018. [Google Scholar] [CrossRef]
- Kumar, R.L.; Khan, F.; Kadry, S.; Rho, S. A Survey on blockchain for industrial Internet of Things. Alex. Eng. J. 2022, 61, 6001–6022. [Google Scholar] [CrossRef]
- Mosenia, A.; Jha, N.K. A comprehensive study of the security of Internet-of-Things. IEEE Trans. Emerg. Top. Comput. 2017, 5, 586–602. [Google Scholar] [CrossRef]
- Lu, X.; Niyato, D.; Jiang, H.; Kim, D.I.; Xiao, Y.; Han, Z. Ambient Backscatter Assisted Wireless Powered Communications. IEEE Wirel. Commun. 2018, 25, 170–177. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of threats to the Internet of Things. IEEE Commun. Surv. Tutor. 2018, 21, 1636–1675. [Google Scholar] [CrossRef]
- Conoscenti, M.; Vetro, A.; De Martin, J.C. Peer to peer for privacy and decentralization in the internet of things. In Proceedings of the IEEE/ACM 39th IEEE International Conference on Software Engineering Companion, Buenos Aires, Argentina, 20–28 May 2017. [Google Scholar]
- Fisher, C.K.; Smith, A.M.; Walsh, J.R. Machine learning for comprehensive forecasting of Alzheimer’s Disease progression. Sci. Rep. 2019, 9, 13622. [Google Scholar] [CrossRef]
- Davenport, T.H.; Harris, J.G.; David, W.; Jacobson, A.L. Data to knowledge to results: Building an analytic capability. Calif. Manag. Rev. 2001, 43, 117–138. [Google Scholar] [CrossRef]
- Arunachalam, D.; Kumar, N.; Kawalek, J.P. Understanding big data analytics capabilities in supply chain management: Unravelling the issues, challenges and implications for practice. Transport. Res. Part E Log. Transport. Rev. 2018, 114, 416–436. [Google Scholar] [CrossRef]
- Ward, J.S.; Barker, A. Undefined by Data: A Survey of Big Data Definitions. arXiv 2013, arXiv:1309.5821. [Google Scholar]
- Balachandran, B.M.; Prasad, S. Challenges and Benefits of Deploying Big Data Analytics in the Cloud for Business Intelligence. Procedia Comput. Sci. 2017, 112, 1112–1122. [Google Scholar] [CrossRef]
- Blackburn, R.; Lurz, K.; Priese, B.; Göb, R.; Darkow, I.L. A predictive analytics approach for demand forecasting in the process industry. Int. Transact. Operat. Res. 2015, 22, 407–428. [Google Scholar] [CrossRef]
- Gunasekaran, A.; Papadopoulos, T.; Dubey, R.; Wamba, S.F.; Childe, S.J.; Hazen, B.; Akter, S. Big data and predictive analytics for supply chain and organizational performance. J. Bus. Res. 2017, 70, 308–317. [Google Scholar] [CrossRef]
- Richey, R.G., Jr.; Morgan, T.R.; xLindsey-Hall, K.; Adams, F.G. A global exploration of big data in the supply chain. Int. J. Phys. Distribut. Log. Manag. 2016, 46, 710–739. [Google Scholar] [CrossRef]
- Mell, P.; Grance, T. The NIST Definition of Cloud Computing; National Institute of Standards and Technology Special Publication: Gaithersburg, MD, USA, 2011. [Google Scholar]
- Avram, M.G. Advantages and challenges of adopting cloud computing from an enterprise perspective. Procedia Technol. 2014, 12, 529–534. [Google Scholar] [CrossRef]
- Vasiljeva, T.; Shaikhulina, S.; Kreslins, K. Cloud Computing: Business Perspectives, Benefits and Challenges for Small and Medium Enterprises (Case of Latvia). Procedia Eng. 2017, 178, 443–451. [Google Scholar] [CrossRef]
- Han, H.; Fei, S.; Yan, Z.; Zhou, X. A survey on blockchain-based integrity auditing for cloud data. Digit. Commun. Netw. 2022, 8, 591–603. [Google Scholar] [CrossRef]
- Chetouane, F. An Overview on RFID Technology Instruction and Application. IFAC PapersOnLine 2015, 48, 382–387. [Google Scholar] [CrossRef]
- Wamba, S.F.; Lefebvre, L.A.; Bendavid, Y.; Lefebvre, É. Exploring the impact of RFID technology and the EPC network on mobile B2B eCommerce: A case study in the retail industry. Int. J. Prod. Econ. 2008, 112, 614–629. [Google Scholar] [CrossRef]
- Wamba, S.F. Achieving Supply Chain Integration using RFID Technology: The Case of Emerging Intelligent B-to-B e-Commerce Processes in a Living Laboratory. Bus. Process Manag. J. 2012, 18, 58–81. [Google Scholar] [CrossRef]
- Duroc, Y.; Tedjini, S. RFID: A key technology for Humanity. Comptes Rendus Phys. 2018, 19, 64–71. [Google Scholar] [CrossRef]
- Gunasekaran, A.; Ngai, E.W. Build-to-order supply chain management: A literature review and framework for development. J. Oper. Manag. 2005, 23, 423–451. [Google Scholar] [CrossRef]
- Abugabah, A.; Nizamuddin, N.; Abuqabbeh, A. A review of challenges and barriers implementing RFID technology in the Healthcare sector. Procedia Comput. Sci. 2020, 170, 1003–1010. [Google Scholar] [CrossRef]
- Liu, X.; Yin, J.; Liu, Y.; Zhang, S.; Guo, S.; Wang, K. Vital signs monitoring with RFID: Opportunities and challenges. IEEE Netw. 2019, 33, 126–132. [Google Scholar] [CrossRef]
- Gaukler, G.M.; Seifert, R.W. Seifert. Applications of RFID in supply chains. In Trends in Supply Chain Design and Management; Springer: London, UK, 2007; pp. 29–48. [Google Scholar]
- Kuo, C.-H.; Chen, H.-G. The critical issues about deploying RFID in the healthcare industry by service perspective. In Proceedings of the 41st Annual Hawaii International Conference on System Sciences (HICSS 2008), Waikoloa, HI, USA, 7–10 January 2008; p. 111. [Google Scholar]
- Gallab, M.; Bouloiz, H.; Tkiouat, M. Modeling and simulation of complex industrial systems. In Modeling and Simulation: Of Complex Industrial Systems; LAP LAMBERT Academic Publishing: Saarbrücken, Germany, 2019. [Google Scholar]
- Gajsek, B.; Marolt, J.; Rupnik, B.; Lerher, T.; Sternad, M. Using Maturity Model and Discrete-Event. Int. J. Simul. Model. 2019, 18, 488–499. [Google Scholar] [CrossRef] [PubMed]
- Lima, F.; de Carvalho, C.N.; Acardi, M.B.; dos Santos, E.G.; de Miranda, G.B.; Maia, R.F.; Massote, A.A. Digital manufacturing tools in the simulation of collaborative robots: Towards Industry 4.0. Braz. J. Oper. Prod. Manag. 2019, 16, 261–280. [Google Scholar] [CrossRef]
- Duplakova, D.; Teliskova, M.; Duplak, J.; Torok, J.; Hatala, M.; Steranka, J.; Radchenko, S. Determination of optimal production process using scheduling and simulation software. Int. J. Simul. Model. 2018, 17, 609–622. [Google Scholar] [CrossRef] [PubMed]
- Naciri, L.; Mouhib, Z.; Gallab, M.; Nali, M.; Abbou, R.; Kebe, A. Lean and industry 4.0: A leading harmony. Procedia Comput. Sci. 2022, 200, 394–406. [Google Scholar] [CrossRef]
- Bianco, D.; Bueno, A.; Godinho Filho, M.; Latan, H.; Ganga, G.M.D.; Frank, A.G.; Jabbour, C.J.C. The role of Industry 4.0 in developing resilience for manufacturing companies during COVID-19. Int. J. Prod. Econ. 2023, 256, 108728. [Google Scholar] [CrossRef]
- Tiwari, K.; Khan, M.S. Sustainability accounting and reporting in the industry 4.0. J. Clean. Prod. 2020, 258, 120783. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A. Industry 4.0 applications in medical field: A brief review. Cur. Med. Res. Pract. 2019, 9, 102–109. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A.; Singh, R.P.; Suman, R.; Gonzalez, E.S. Understanding the adoption of Industry 4.0 technologies in improving environmental sustainability. Sustain. Oper. Comput. 2022, 3, 203–217. [Google Scholar] [CrossRef]
- Arnold, C.; Kiel, D.; Voigt, K.I. How the industrial internet of things changes business models in different manufacturing industries. Int. J. Innov. Manag. 2016, 20, 1640015. [Google Scholar] [CrossRef]
- Ibarra, D.; Ganzarain, J.; Igartua, J.I. Business model innovation through Industry 4.0: A review. Procedia Manfacturing 2018, 22, 4–10. [Google Scholar] [CrossRef]
- Bylya, O.I.; Ward, M.; Krishnamurty, B.; Tamang, S.; Vasin, R.A. Modelling challenges for incremental bulk processes despite advances in simulation technology: Example issues and approaches. Procedia Eng. 2017, 207, 2358–2363. [Google Scholar] [CrossRef]
- Booch, G.; Rumbaugh, J.; Jacobson, I. The Unified Modeling Language User Guide; 6th printing; Addison Wesley: North York, ON, Canada, 2000. [Google Scholar] [CrossRef]
- Gallab, M.; Mouhib, Z.; Naciri, L.; Kebe, S.A.; Nali, M.; Abbou, R.; Di Nardo, M. Aeronautics 4.0: Modeling and Simulation of a Smart Tool. In Proceedings of the 2022 The 3rd International Conference on Industrial Engineering and Industrial Management (IEIM 2022), Barcelona, Spain, 12–14 January 2022; ACM: New York, NY, USA, 2022. [Google Scholar] [CrossRef]
- Bakhtari, A.R.; Waris, M.M.; Mannan, B.; Sanin, C.; Szczerbicki, E. Assessing Industry 4.0 Features Using SWOT Analysis. In Proceedings of the Intelligent Information and Database Systems: 12th Asian Conference, ACIIDS 2020, Phuket, Thailand, 23–26 March 2020; Springer: Singapore, 2020. [Google Scholar]



| Opportunities | Easy/Quick Process | Efficiency | Flexibility | Precision | Interactivity | Decision Support | Data Protetction | Traceability |
|---|---|---|---|---|---|---|---|---|
| 3D printing /Additive manufacturing (AM) | [9,10] | [9,10] | [15] | [15] | ||||
| Augmented reality | [29] | [17] | [29] | |||||
| Robotics | [34,36] | [35,37] | ||||||
| Cyber security | [45] | |||||||
| Blockchain | [53,54] | [53,54] | ||||||
| IoT/IIoT | [60] | [61] | ||||||
| Big data | [68] | [66,67] | [66,67] | |||||
| Cloud computing | [69] | [69] | [69] | |||||
| Radio-Frequency Identification (RFID) | [78,79] | [77,78,79] | [77] | |||||
| Simulation | [86,89] | [86,89] | [86,87,88] |
| Risks | Expensive /Time-Consuming Process | Poor Properties | Limited Choice | Lack of Skills /Guidelines | Data Accuracy | Safety/Cyber Security | Complexity | Resistance to Change |
|---|---|---|---|---|---|---|---|---|
| 3D printing/Additive manufacturing (AM) | [10] | [16] | [10] | [16] | ||||
| Augmented reality | [32] | [31] | [31] | [31] | ||||
| Robotics | [36] | [38] | [35,39] | |||||
| Cyber security | [46] | |||||||
| Blockchain | [53] | [55] | [54,56,57] | [57] | ||||
| IoT/IIoT | [63,64] | [63,64] | [60,62] | |||||
| Big data | [68] | [72] | [70] | [68] | ||||
| Cloud computing | [76] | [74] | [76] | [74] | ||||
| Radio-Frequency Identification (RFID) | [82] | [84] | [83] | [85] | [77] | [77] | ||
| Simulation | [90] | [90] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Naciri, L.; Gallab, M.; Soulhi, A.; Merzouk, S.; Di Nardo, M. Digital Technologies’ Risks and Opportunities: Case Study of an RFID System. Appl. Syst. Innov. 2023, 6, 54. https://doi.org/10.3390/asi6030054
Naciri L, Gallab M, Soulhi A, Merzouk S, Di Nardo M. Digital Technologies’ Risks and Opportunities: Case Study of an RFID System. Applied System Innovation. 2023; 6(3):54. https://doi.org/10.3390/asi6030054
Chicago/Turabian StyleNaciri, Lina, Maryam Gallab, Aziz Soulhi, Safae Merzouk, and Mario Di Nardo. 2023. "Digital Technologies’ Risks and Opportunities: Case Study of an RFID System" Applied System Innovation 6, no. 3: 54. https://doi.org/10.3390/asi6030054
APA StyleNaciri, L., Gallab, M., Soulhi, A., Merzouk, S., & Di Nardo, M. (2023). Digital Technologies’ Risks and Opportunities: Case Study of an RFID System. Applied System Innovation, 6(3), 54. https://doi.org/10.3390/asi6030054







