Security Authentication of Dual Chaotic Image Watermarking in Spatial Domain with Spatial and Frequency Domain Characteristics Analysis
Abstract
:1. Introduction
2. Spatial Domain Chaotic Watermarking
2.1. True Color Model
2.2. Suboptimal Secure Hashing with Variable Length
2.3. Chaotic Logistic Map Watermark Generator
2.4. Host Image Shuffling and Watermark Embedding
2.5. Parametric Modulation for Chaotic Logistic Map
3. Dual Chaotic Scrambling to Enhance Security
4. Numerical Simulations of Digital Watermarking
5. Security Analysis in Spatial and Frequency Domains
5.1. NPCR (Number of Pixel Change Rate)
5.2. UACI (Unified Average Changing Intensity)
5.3. Discrete Entropy
5.4. Relative Entropy
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Schilling, R.; Harris, S. Fundamental of Digital Signal Processing Using Matlab; Cengage Learning: Boston, MA, USA, 2005. [Google Scholar]
- Lathi, B. Modern Digital and Analog Communication Systems; Oxford University Press: Oxford, UK, 2009. [Google Scholar]
- Pareeka, N.; Patidara, V.; Suda, K. Image Encryption Using Chaotic Logistic Map. Image Vis. Comput. 2006, 24, 926–934. [Google Scholar] [CrossRef]
- Ye, Z.; Yin, H.; Ye, Y. Information Security Analysis of Deterministic Encryption and Chaotic Encryption in Spatial Domain and Frequency Domain. In Proceedings of the 2017 International Conference on Electrical Engineering, Computing Science and Automatic Control, Mexico City, Mexico, 20–22 September 2017. [Google Scholar]
- Huang, C.; Nien, H. Multi Chaotic Systems Based Pixel Shuffle for Image Encryption. Opt. Commun. 2009, 282, 2123–2127. [Google Scholar] [CrossRef]
- Shan, M.; Chang, J.; Zhong, Z.; Hao, B. Double Image Encryption Based On Discrete Multiple-Parameter Fractional Fourier Transform And Chaotic Maps. Opt. Commun. 2012, 285, 4227–4234. [Google Scholar] [CrossRef]
- Chetan, K.; Nirmala, S. An Efficient And Secure Robust Watermarking Scheme For Document Images Using Integer Wavelets and Block Coding Of Binary Watermarks. J. Inf. Secur. Appl. 2015, 24–25, 13–24. [Google Scholar] [CrossRef]
- Asikuzzaman, M.; Pickering, M. An Overview of Digital Video Watermarking. IEEE Trans. Circuits Syst. Video Technol. 2018, 28, 2131–2153. [Google Scholar] [CrossRef]
- Tefas, A.; Nikolaidis, A. Performance Analysis of Correlation-Based Watermarking Schemes Employing Markov Chaotic Sequences. IEEE Trans. Signal Process. 2003, 51, 1979–1992. [Google Scholar] [CrossRef]
- Chen, S.; Leung, H. Ergodic Chaotic Parameter Modulation with Application to Digital Image Watermarking. IEEE Trans. Image Process. 2005, 14, 1590–1602. [Google Scholar] [CrossRef] [PubMed]
- Chen, S.; Leung, H. Chaotic Watermarking for Video Authentication in Surveillance Applications. IEEE Trans. Circuits Syst. Video Technol. 2008, 18, 704–709. [Google Scholar] [CrossRef]
- Ye, Z.; Mohamadian, H.; Yin, H. Impact of Fractional Orders on Characteristics of Chaotic Dynamical Systems. Int. J. Electr. Electron. Data Commun. 2017, 5, 72–77. [Google Scholar]
- Keyvanpour, M.R.; Merrikh-Bayatb, F. An Effective Chaos-Based Image Watermarking Scheme Using Fractal Coding. Procedia Comput. Sci. 2011, 3, 89–95. [Google Scholar] [CrossRef]
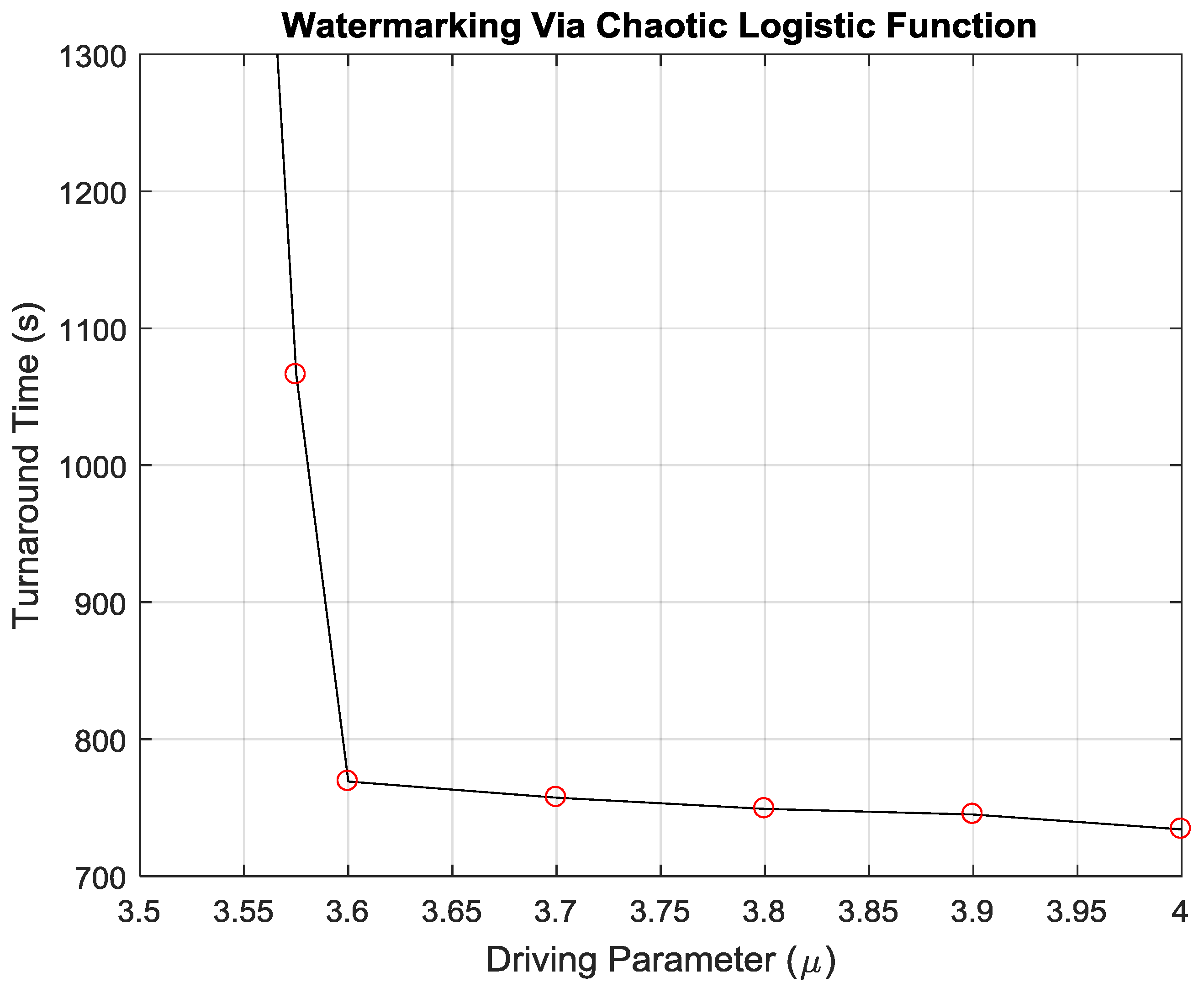


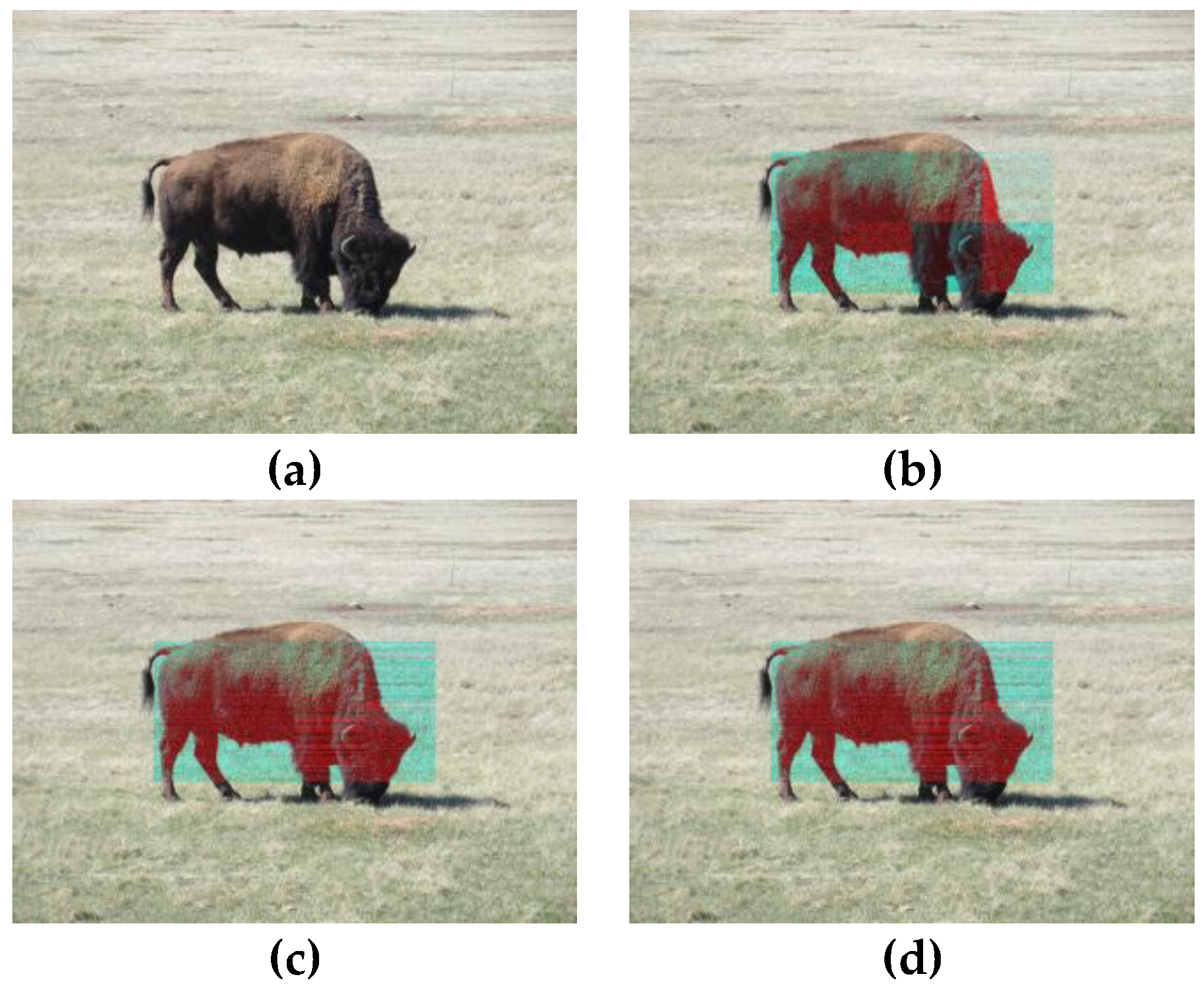
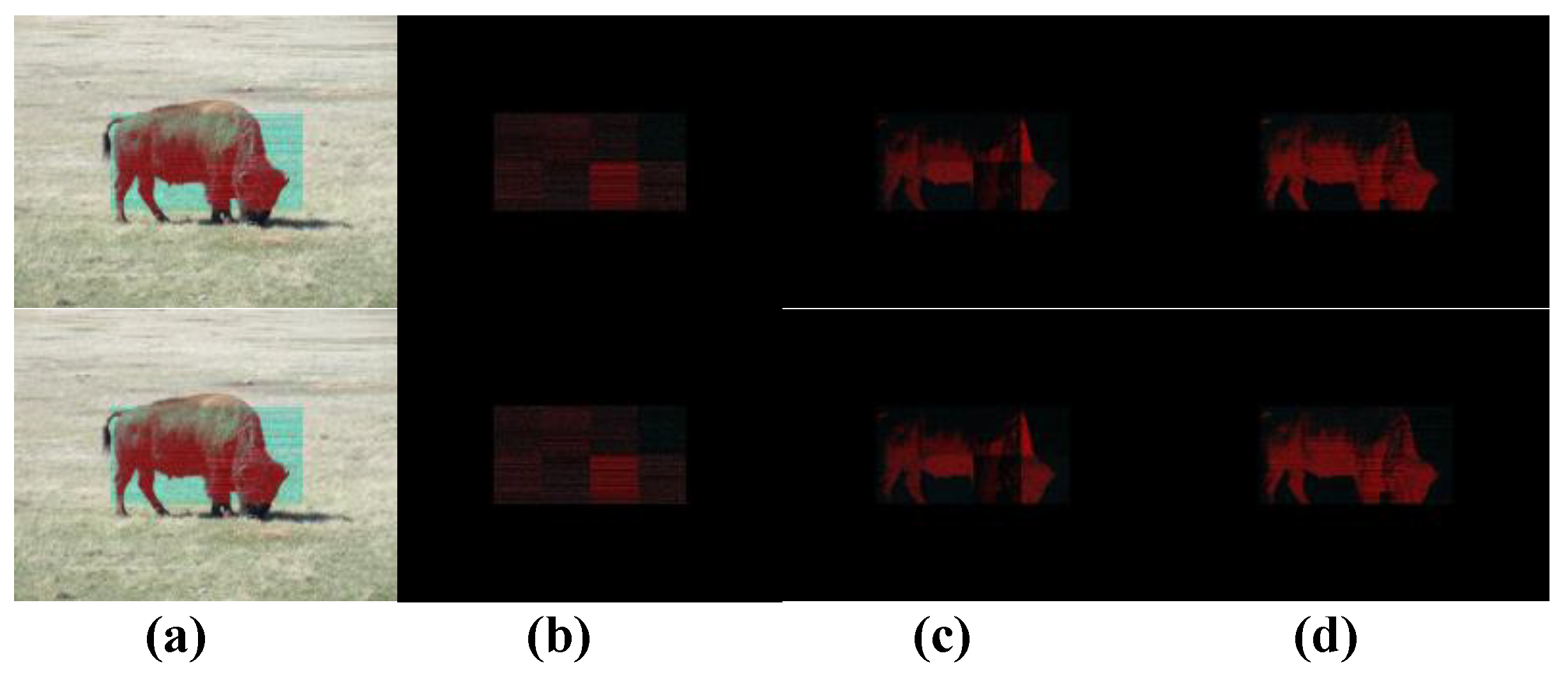
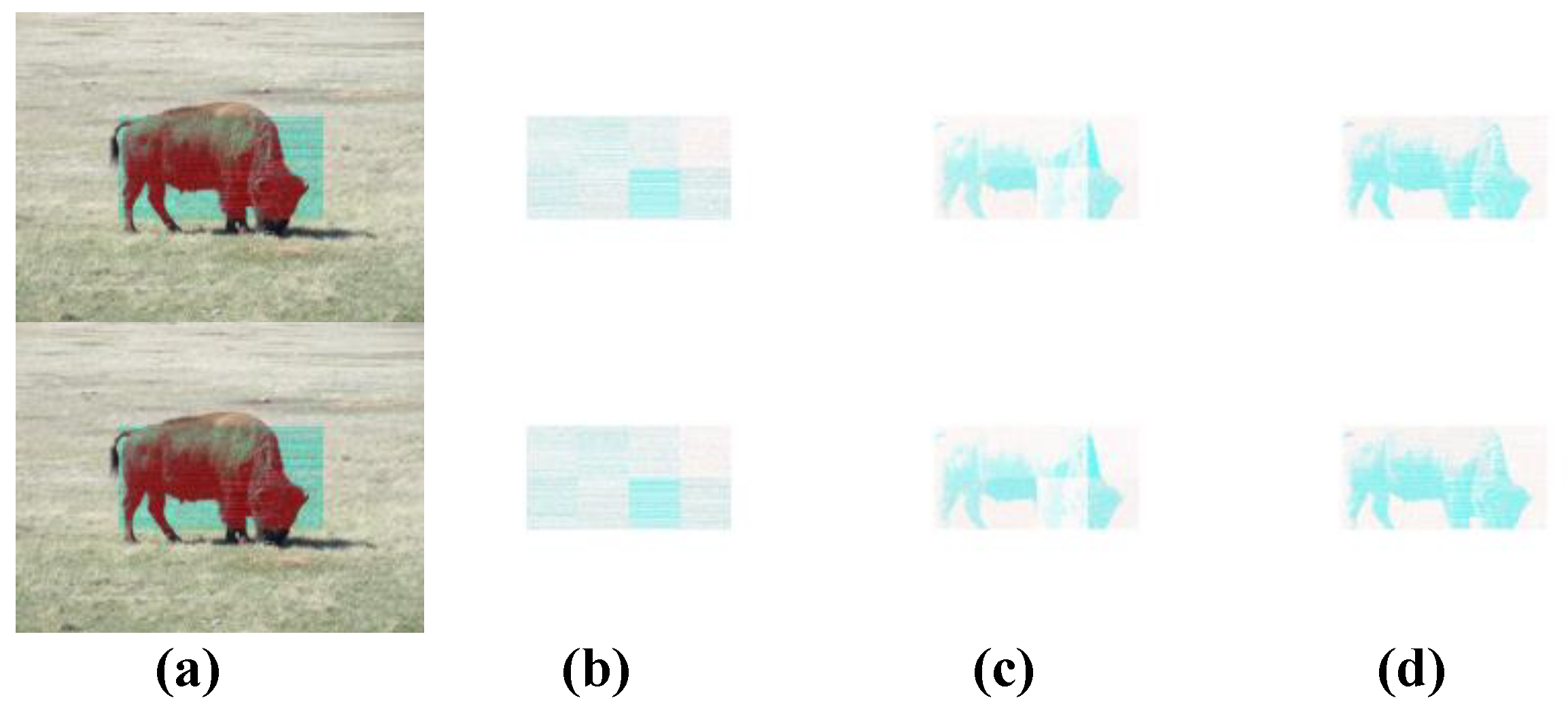
| μ Outcomes | μ = 3.6 | μ = 3.7 | μ = 3.8 | μ = 3.9 | μ = 4.0 |
|---|---|---|---|---|---|
| Chaotic Watermarking | 0.9883 | 0.9884 | 0.9882 | 0.9884 | 0.9886 |
| Dual Chaotic Watermarking | 0.9909 | 0.9909 | 0.9910 | 0.9911 | 0.9912 |
| Mismatch Chaotic Shuffling | 0.9895 | 0.9895 | 0.9895 | 0.9895 | 0.9895 |
| Mismatch Dual Watermark | 0.9894 | 0.9895 | 0.9894 | 0.9895 | 0.9895 |
| μ Outcomes | μ = 3.6 | μ = 3.7 | μ = 3.8 | μ = 3.9 | μ = 4.0 |
|---|---|---|---|---|---|
| Chaotic Watermarking | 0.1200 | 0.1201 | 0.1201 | 0.1199 | 0.1199 |
| Dual Chaotic Watermarking | 0.1426 | 0.1425 | 0.1425 | 0.1424 | 0.1421 |
| Mismatch Chaotic Shuffling | 0.6600 | 0.6600 | 0.6600 | 0.6600 | 0.6600 |
| Mismatch Dual Watermark | 0.6601 | 0.6601 | 0.6601 | 0.6601 | 0.6601 |
| RGB Discrete Entropy | Red | Green | Blue |
|---|---|---|---|
| Source A | 2.6470 | 2.6116 | 2.3542 |
| Chaotic Watermarking | 2.6551 | 2.6241 | 2.3564 |
| Dual Chaotic Watermarking | 2.6761 | 2.6443 | 2.3861 |
| Source B | 2.5103 | 2.4543 | 2.6716 |
| Chaotic Watermarking | 2.5277 | 2.4689 | 2.6985 |
| Dual Chaotic Watermarking | 2.5872 | 2.5522 | 2.7729 |
| Source C | 2.1757 | 2.1772 | 2.2911 |
| Chaotic Watermarking | 2.2327 | 2.2338 | 2.3550 |
| Dual Chaotic Watermarking | 2.2931 | 2.3444 | 2.4673 |
| RGB Relative Entropy | Red | Green | Blue |
|---|---|---|---|
| Source A | |||
| Chaotic Watermarking | 0.0041 | 0.0176 | 0.0079 |
| Dual Chaotic Watermarking | 0.0047 | 0.0455 | 0.0177 |
| Source B | |||
| Chaotic Watermarking | 0.0220 | 0.0132 | 0.0021 |
| Dual Chaotic Watermarking | 0.0285 | 0.0222 | 0.0039 |
| Source C | |||
| Chaotic Watermarking | 0.0089 | 0.0115 | 0.0113 |
| Dual Chaotic Watermarking | 0.0122 | 0.0131 | 0.0133 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ye, Z.; Yin, H.; Ye, Y. Security Authentication of Dual Chaotic Image Watermarking in Spatial Domain with Spatial and Frequency Domain Characteristics Analysis. Appl. Syst. Innov. 2018, 1, 40. https://doi.org/10.3390/asi1040040
Ye Z, Yin H, Ye Y. Security Authentication of Dual Chaotic Image Watermarking in Spatial Domain with Spatial and Frequency Domain Characteristics Analysis. Applied System Innovation. 2018; 1(4):40. https://doi.org/10.3390/asi1040040
Chicago/Turabian StyleYe, Zhengmao, Hang Yin, and Yongmao Ye. 2018. "Security Authentication of Dual Chaotic Image Watermarking in Spatial Domain with Spatial and Frequency Domain Characteristics Analysis" Applied System Innovation 1, no. 4: 40. https://doi.org/10.3390/asi1040040
APA StyleYe, Z., Yin, H., & Ye, Y. (2018). Security Authentication of Dual Chaotic Image Watermarking in Spatial Domain with Spatial and Frequency Domain Characteristics Analysis. Applied System Innovation, 1(4), 40. https://doi.org/10.3390/asi1040040





