1. Introduction
In recent years, the rapid development of mobile communication technology and the widespread adoption of smart mobile devices have led to explosive growth in data traffic [
1]. To ensure the quality of communication services, future networks urgently need to meet performance demands such as ultra-low latency, ultra-high reliability, ultra-high density, and ultra-high security [
2,
3]. However, deploying more ground base stations (BSs) is not an ideal solution from a cost perspective. Therefore, caching is considered a technology with the potential to reduce transmission latency in cellular networks [
4,
5].
In caching networks, small BS caching architectures significantly reduce system latency and increase the number of serviceable users compared to conventional macro BS caching networks [
6,
7,
8,
9,
10,
11]. In [
6], a proactive, cooperative caching strategy for a multi-cell network is proposed to meet the demand of the user, effectively reducing the latency of the network. In [
7], the authors deploy micro BSs within the traditional BS network to expand its storage space, and utilize macro BSs to control the caching strategies of micro BSs, addressing user requests during different time periods. The work in [
8] proposed a two-tier heterogeneous Internet of Things (IoTs) network which simultaneously operates with edge micro BSs and cache-enabled IoT devices to improve the cache hit rate. In [
9], the authors consider a two-tier heterogeneous caching network, where the most popular content is cached in the macro BS, and the remaining content is cached randomly in the small BS. To address the randomness of user trajectories, a three-tier network consisting of Macro-BSs, micro-BSs, and pico-BSs is established to maximize the amount of cached content [
10]. In [
11], the authors focus on a cache-enabled heterogeneous network, where MUs can flexibly schedule their traffic between traditional sub-6 GHz macro cells and dense millimeter-wave small cells. Unfortunately, the fixed location of BSs has some drawbacks. Firstly, serving users with trajectory randomness by deploying more micro BSs will lead to severe resource wastage. Additionally, frequent user handovers between networks must also be considered.
Due to the flexible mobility, cache-enabled unmanned aerial vehicles (UAVs) can dynamically adjust their positions based on the caching needs of specific ground users and intelligently store content according to specific requests [
12]. Some recent works focused on the applications of the cache-enabled UAVs [
13,
14,
15,
16,
17]. The authors in [
13] investigated a cache-enabled UAV emergency communication network, where the UAVs are regarded as aerial BSs to assist damaged cellular networks. In [
14], an adjustable cache distribution model was developed to support caching in UAV networks. Moreover, the average service success probability of cache placement was studied to evaluate the performance of heterogeneous UAV networks [
15]. The work in [
16] proposed a layered caching scheme using scalable video coding for cache-enabled multi-UAV networks to balance video content quality and diversity. The aforementioned studies still regarded a single UAV and multiple users within the same jurisdiction as the benchmark unit. This paper refers to it as a traditional UAV caching network. When UAVs could not meet user requirements, they were connected to the BS via direct wireless links. Compared to the BS, nearby available UAVs can provide faster access services. The absence of UAV cooperation may lead to increased latency for uncached content. Therefore, a user-centric cooperation approach for cache-enabled UAV networks was proposed, where a user-centric UAV group is formed for each user to increase cache hit probability, thus reducing latency [
17]. However, such a cooperation mechanism did not consider the interaction among UAVs. When the number of UAVs is small, collaborating with dynamically flying UAVs to serve one user might reduce the cache hit probability for others. As a result, it is impossible to guarantee the quality of service (QoS) for users in the jurisdiction of those UAVs. Additionally, a large UAV group could lead to resource dissipation, and uneven distribution of demand and storage capacity might further exacerbate this issue. In a multi-UAV network, considering collaboration to allocate resources reasonably to ensure resource utilization while guaranteeing the QoS for users in the jurisdiction needs to be addressed urgently.
Recently, integrating individual social attributes with device-to-device (D2D) communications has also shown significant application potential for collaboration mechanisms in terrestrial networks [
18,
19,
20]. A network that combines social selfishness with D2D link quality optimization was proposed to enable effective collaboration [
18]. However, D2D communication for user caching devices, such as a smartphone, often involves user privacy policies, posing certain risks to overall resource planning in the user layer. Fortunately, UAVs with social attributes are considered public resources. The cached content of UAV does not require the permission of the users in the jurisdiction and is not subject to the privacy agreement. Thus, they possess tremendous potential and should be studied in depth. To the best of our knowledge, developing a multi-UAV network that considers the interaction among UAVs to enhance resource utilization and introduces social attributes to guarantee QoS for users has yet to be investigated in prior research.
To tackle the aforementioned issue, this paper bridges this gap by proposing a cache-enabled multi-UAV socially aware network (SAN), which considers resource utilization and user QoS. In the network, UAVs prioritize connecting to nearby available UAVs to enhance interaction at the UAV layer. Meanwhile, UAVs possess social attributes that enable them to decide whether to assist other UAVs with task offloading. Specifically, UAVs reserve storage space of different sizes according to different social attributes. These storage spaces are integrated into a huge resource pool to optimize and allocate resources uniformly. Among them, “selfish” UAVs with less storage space can only provide less help to other UAVs, while “selfless” UAVs with more storage space can provide more help. The proposed network can be transitioned into an ad hoc network or a traditional cache-enabled UAV network by adjusting the proportion of assistant UAVs, which demonstrates the extremely strong universality of the proposed network. The key contributions of this work are as follows:
Novel Socially Aware UAV Network Model: We propose a cache-enabled multi-UAV SAN, where UAVs possess inherent social attributes, providing a novel architecture for controlling cooperation and resource allocation.
Comprehensive Multi-Objective Formulation: We formulate the caching deployment as a multi-objective optimization problem (MOOP) that captures the fundamental trade-off between the cached content diversity (a proxy for fairness) and the aggregation of the request probability (RP) (a proxy for efficiency).
Advanced Algorithmic Solution: To address this MOOP, we transform it into a form that is easily solvable by the multi-objective particle swarm optimization (MOPSO) algorithm. The Pareto optimal solution set is approximated by establishing the MOPSO algorithm with a mutation strategy for the proposed MOOP.
In-depth simulation Evaluation: The simulation demonstrates the substantial advantages of social attributes on the caching resource allocation when demand and storage capacity are not evenly distributed. The gain of constraints imposed by social attributes can promote the diversity of cached content. Furthermore, two approaches—the establishment of a constructor and the adjustment of constraints—are thoroughly examined to balance the objective functions.
The remainder of this paper is organized as follows.
Section 2 details the system model of the proposed cache-enabled multi-UAV SAN framework.
Section 3 presents the MOPSO with a mutation strategy-based proposed MOOP.
Section 4 provides and discusses the simulation results. Finally,
Section 5 concludes the paper.
3. Solution Approach
In this section, the caching strategy optimization for multi-UAV SAN is examined. It is intrinsically tough because P1 is a discrete MOOP and an NP-hard problem [
19]. Thus, we re-encode the variables and transform P1 into a solvable form that applies to the MOPSO algorithm. A MOPSO algorithm with a mutation strategy based on the Pareto model is proposed to solve P1.
3.1. Problem Transformation
The objective functions and the bivariate variables are discrete, which results in the non-convexity of P1. To adapt to the MOPSO algorithm, the variables are transformed into the variables , which are a set of . represent the index set of cached contents in UAV m, and their sizes are no greater than , assuming that UAV m caches the 1st, 3rd, 5th, and 7th content items in , .
Theorem 1. In P1, the constraint (13c) is a sufficient condition for the constraint . Here, denotes the quantity of elements for vector .
Proof. We assume that . Because and are incremented within . Then an uncached content always exists that makes and . So the solution set is not inferior to , let up to . □
Theorem 1 states that UAV
m can always fetch
contents, which means that UAV
m has
schemes, so we define the mapping
,
Table 2 summarizes the key symbols and their meanings as used in
Section 3. The MOOP P1 can be rewritten as follows:
where
and
in (15e) and (15d), respectively. (15b) specifies that each UAV selects one caching strategy from
alternative strategies. (15c) mandates that the number of cached items per UAV is strictly equal to its capacity limit. (15d) requires that the intersection between cached content and local demand on each UAV must exceed a threshold ratio. (15e) ensures that the intersection between cached content and the total demand of the system satisfies the QoS requirement.
3.2. MOPSO Algorithm with Mutation Strategy
The MOPSO algorithm with a mutation strategy exhibits capabilities in rapid convergence and global optimization. The critical steps of the algorithm are illustrated, including mutation strategy, density estimation, and setting of step size and direction. The detailed process is shown in Algorithm 1.
| Algorithm 1: A MOPSO Algorithm with Mutation Strategy for Multi-UAV Caching Strategy. |
Phase 1: Initialization
- 1.
Set population size , max iterations , learning factors , inertia weight bounds , and mutation coefficient . Initialize positions , velocities and the external archive .
Phase 2: Iterative Optimization
- 2.
Set iteration counter . - 3.
repeat - 4.
for each particle do - 5.
Update velocity based on its inertia, cognitive component (distance to ), and social component (distance to ) via (18). - 6.
Update position by applying the new velocity to the old position via (21). - 7.
end - 8.
Apply mutation strategy to to generate for population diversity, then select the next generation population . - 9.
Evaluate the new population by calculating fitness and penalty values. - 10.
Update the historical best for each particle by comparing its new solution with its previous best. - 11.
Update the external archive : combine with the current population , remove all dominated solutions, and if necessary, use density estimation to prune the archive to its maximum size. Then, select a new from . - 12.
. - 13.
until or the stopping criterion (e.g., convergence) is met.
Phase 3: Output |
- 14.
return The final set of non-dominated solutions stored in the archive .
|
Calculation of penalty function: The penalty function
guides the population for the constraints in P2. During the execution of the algorithm, the precedence of the penalty function value supersedes that of the fitness function.
Density estimation: In the process of identifying optimal solutions within a population, the random selection process may inadvertently lead to individuals who have identical fitness function values predominantly occupying the elite population. Consequently, despite these individuals having a high frequency of occurrence, they may not contribute to the diversity required for effective evolutionary progress. To augment the population diversity, density estimation is employed to select the individuals with the least frequency of fitness function values in the elite population. Thus, the population can constantly explore minorities, thereby avoiding falling into the local optimal solution.
Setting of step size and direction: The selection of step size and direction profoundly affects the convergence speed of the MOPSO algorithm. If the step size is excessively large, it becomes too easy to surpass the optimal solution and results in a solution explosion. Conversely, it will lead to a slow convergence rate and increase the likelihood of falling into the local optimal solution. The velocity
and position
of the particles are updated as
where mod denotes the modular operator. The notation description is detailed in
Table 3. Equation (
21) illustrates that when the step size exceeds the boundaries of the feasible domain, it is recalibrated through the remainder operation. This mechanism is also a means to prevent the solution from exploding.
Mutation strategy: A mutation strategy is employed to enhance the diversity within the population. During the mutation process, the mutation probability
is calculated by the mutation coefficient
,
This calculation yields the upper and lower bounds of the mutation range. In the mutation process, the mutation operation randomly selects one dimension of a particle and randomly generates a new value for it within the predefined mutation range, while the remaining dimensions of the particle remain unaltered.
Complexity and convergence of Algorithm 1: is defined as the total amount of user requests for UAV
m. The population size is
. The computational complexity of each step is shown in Algorithm 1. In general, the number of the particles is larger than UAVs, so
. Meanwhile,
. Thus, the computational complexity of Algorithm 1 is
. Refs. [
22,
23] concluded that the MOPSO algorithm could converge globally to the Pareto optimal solution set by introducing a mutation strategy. The measure
defined the convergence of the algorithm, i.e.,
. Different from the continuous function in [
22], the non-dominated solution set
is sequentially connected in the
lth iteration. Next, the edge points
and
are obtained. Finally, two line segments that start from
and
are perpendicular to the Y-axis and X-axis, respectively. The closed area mentioned above is
. The generation method for this closed region is also suitable for cases where the non-dominated solution set is a single point.
4. Simulation Results
In this section, numerical results are provided to elaborate the advantages of cache-enabled multi-UAV SAN. We consider a multi-UAV scenario with
, where user requests
and storage capacity
are set in different schemes, which is detailed in
Table 4. In S1,
is set as
,
, and
, respectively. We set Algorithm 1 with parameters
,
,
,
,
,
, and
.
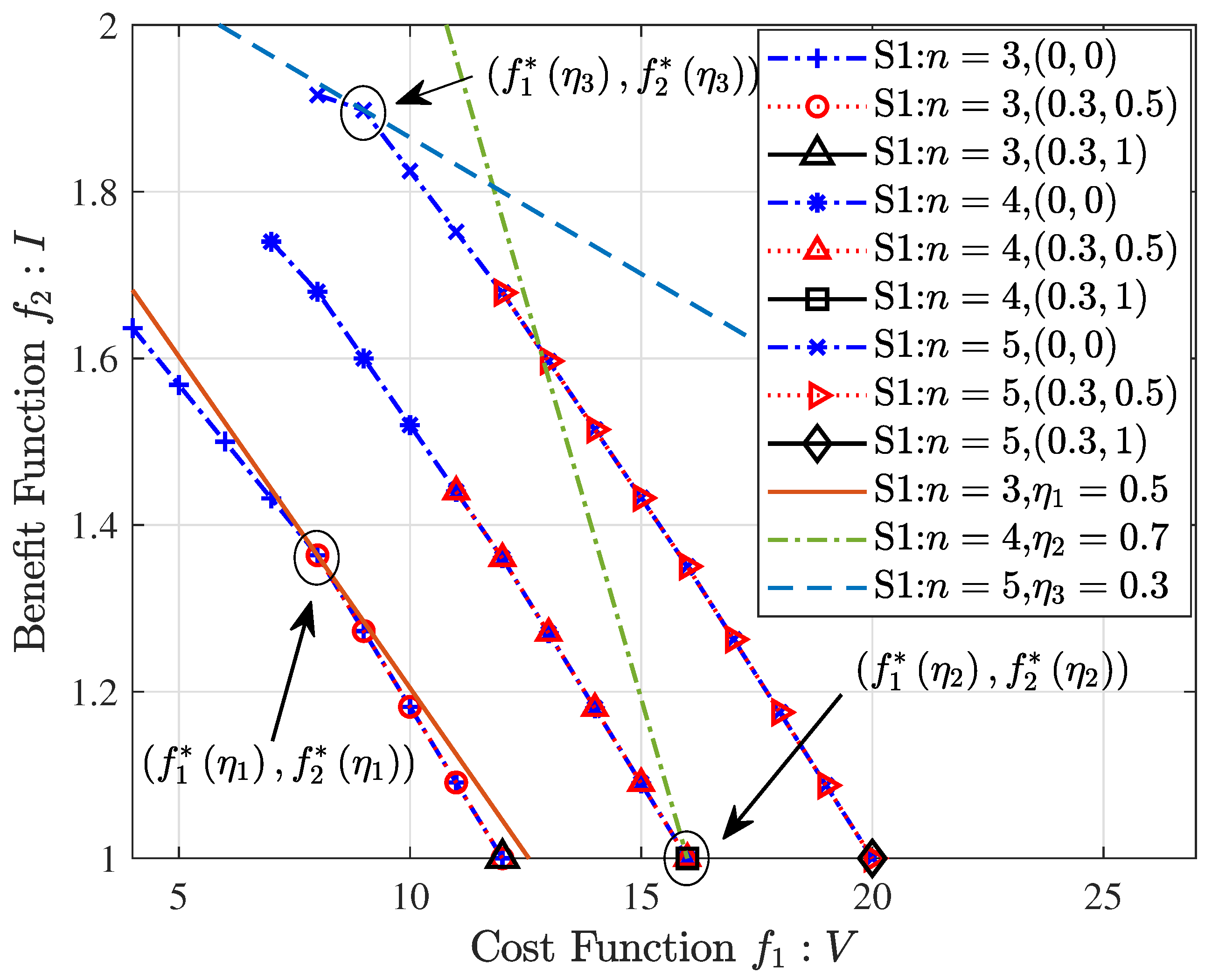
Figure 2 shows the Pareto front approximation of S1. An inverse relationship is observed between
and
. The observation that low RP contents replace the higher leads to an augmentation of diversity, and vice versa. A conventional approach to the compromise between
and
is to establish a constructor
where
represents the weight coefficient of
and can control whether the system tends towards
or
.
As depicted in
Figure 2, the optimal point
can be calculated by the linear function
and the Pareto optimal solution set. Subsequently, the optimal configuration scheme
can be obtained. In S1, the Pareto front approximation continues to expand towards higher values as
n increases. When the diversity of cached contents remains constant, an increase in cache capacity causes multi-UAV to sequentially cache existing contents from high RP to low RP until the cache limit is reached. This not only augments the total RP but also enhances the connectivity of the network. On the contrary, an increase in cache capacity ensures the storage of more contents when the total RP remains unchanged. It elucidates that enhancements in storage capacity can significantly elevate the gain of the diversity and total RP for the network.
Figure 2 displays that the solution set that satisfies (13d) and (13e) is a subset of the unconstrained solution set in each Pareto front approximation. Relaxing constraint (13d) results in an increase in network connectivity. Conversely, enforcing this constraint leads to a decrease in connectivity. By manipulating the parameter
, we can effectively balance the risks associated with latency and network stability. The connectivity can serve as a quantifiable metric for assessing these risks. When constraint (13e) is relaxed, the diversity of cached contents will decrease; otherwise, it will increase. In scenarios involving a lower
, the system can utilize the additional available space to cache existing high RP content, thereby ensuring profitability after satisfying a smaller portion of the content restrictions. This strategy helps to enhance content diversity and profitability while ensuring network performance. In summary, adjusting
and
has a significant impact on the connectivity, latency, content diversity, and profitability of the network. The gain of
and
jointly promotes the diversity of cached content. Therefore, the method on balancing
and
can also be obtained by adjusting
and
. Concurrently, more efficient and reliable solutions can be designed for UAV network systems by optimizing these parameters and constraints.
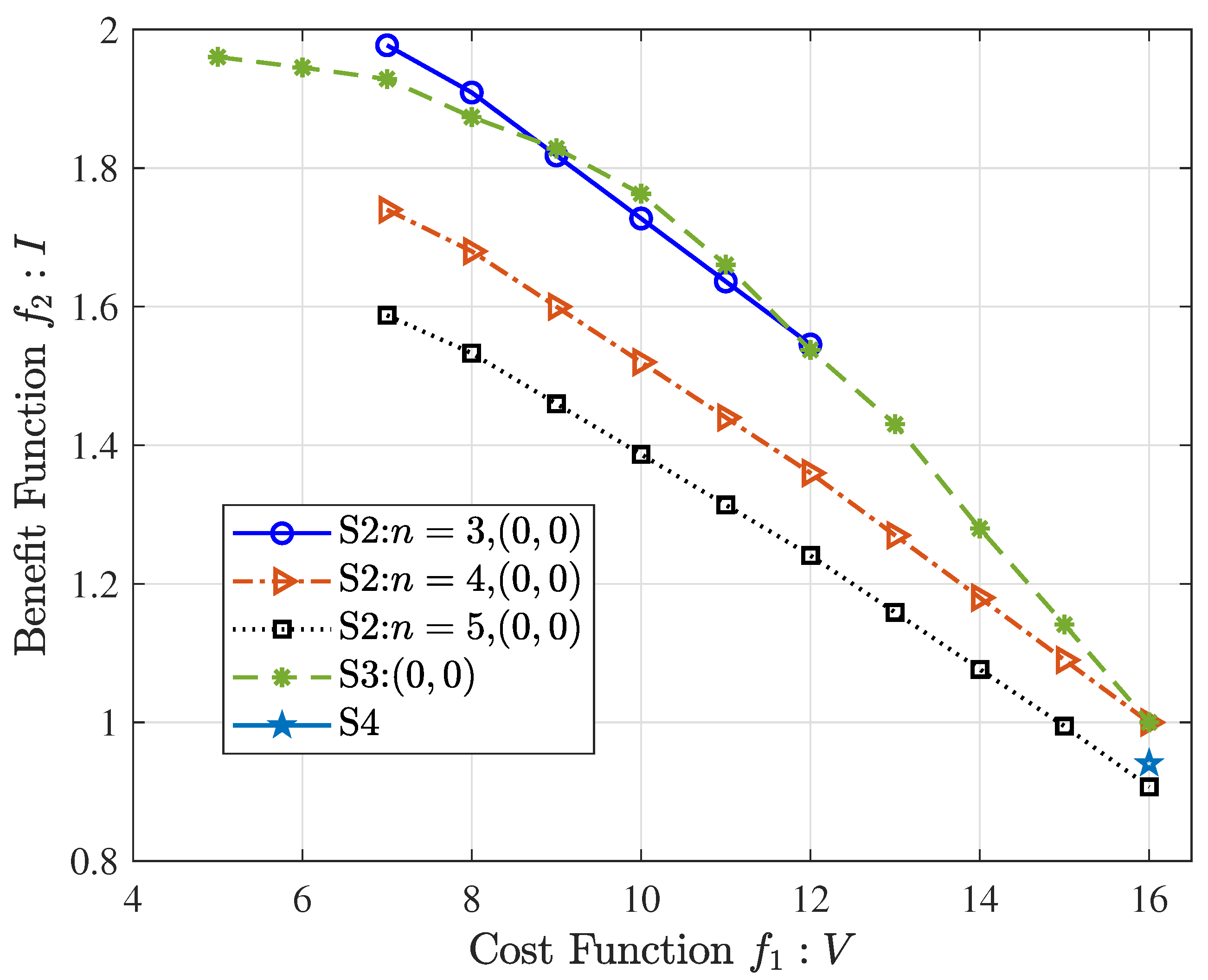
Figure 3 displays the Pareto front approximation of S2, S3, and S4. In S2,
completely exceeds
as
n increases, resulting in a continual contraction of the Pareto front toward smaller values. When
, the UAVs have the idle space after fulfilling diversity requirements. The idle space will cache contents with higher RP until the space is fully occupied. As
exceeds
, the UAVs must abandon some low RP contents to prioritize the total RPs. This leads to the contraction of the Pareto front. It is worth noting that the social attributes make the storage space of multi-UAV a cohesive entity, which transforms the relationship between
and
into the relationship between the aggregate quantity of request contents
and total storage space
. In fact, the various relationships between
and its corresponding
simultaneously exist in a network, as in S3. The UAV social network can adjust the overall storage space to mitigate resource scarcity among other UAVs. Comparing S3 with S4, the benefits of networks devoid of social attributes diminish significantly. Since the UAVs only rely on local content to serve the users within their jurisdiction, it reduces the total profit of the network.
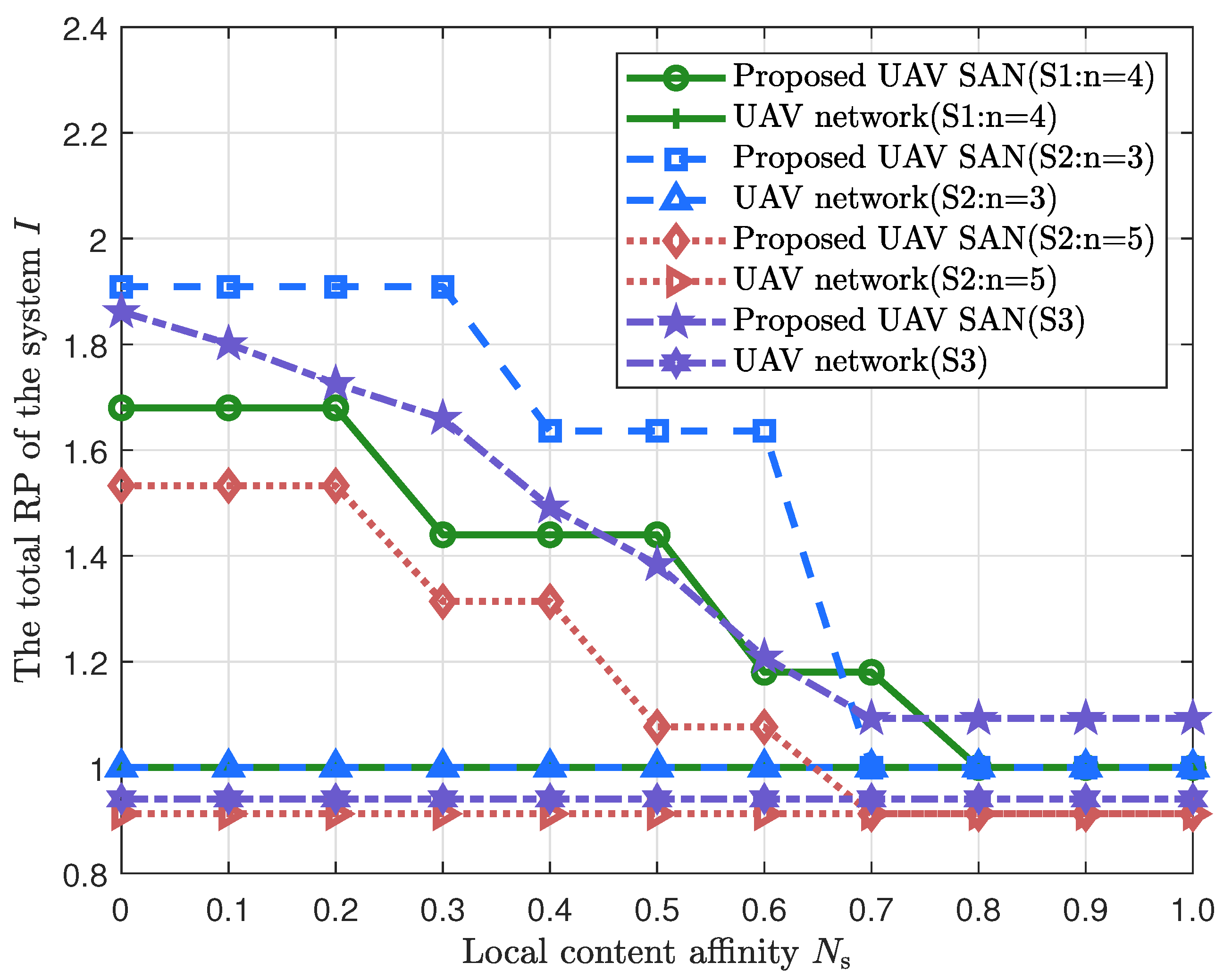
Figure 4 illustrates the impact of parameter
on overall network performance. To demonstrate the advantages of social attributes, we compare the proposed UAV SAN with conventional UAV networks in [
13,
15]. In the SAN, the total system RP decreases as
increases, consistent with trends in
Figure 2. The system must maintain a minimum cached content number to preserve network connectivity for RP maximization, resulting in stable RP during low
phases. As n increases, RP gradually declines—aligning with
Figure 2. Critically, SAN consistently achieves higher RP than conventional networks due to the latter’s isolated UAV layers that cannot cooperatively cache high-RP content. Increasing
reduces unconstrained storage space, forcing systems to deprioritize high-RP content for low-RP items. Notably, in both S2 and S3 schemes, SAN’s RP strictly dominates conventional networks.
Figure 5 characterizes the impact of
on network performance. Increasing
compresses unconstrained storage space, weakening network connectivity and driving a decline in total system RP. At maximum
, RP of SAN converges with conventional networks under demand-uniform scenarios, indicating that SAN degenerates to conventional networks when devices operate in absolute selfishness states. As
n rises, resource scarcity forces systems to prioritize high-RP content over low-RP items, further reducing RP. Crucially, in S3 (demand-maldistributed scenarios), UAV storage limitations prevent full selfishness, resulting in total RP of SAN superiority over conventional networks.“Selfish” UAVs prioritize their own demands at the expense of overall system gain. An increase in such “selfish” UAVs diminishes the collective resource pool and causes severe network degradation. Ultimately, all nodes lose interaction capability, resulting in catastrophic resource wastage.
Figure 6 presents the total system RP under UAV disconnection scenarios. To demonstrate the stability advantages of SAN, we simulate scenarios with exactly one UAV disconnecting at a probability
.
is defined as probability of disconnection. Results show that greater UAV storage capacity reduces disconnection impact—i.e., storage sufficiency directly enhances network robustness. Crucially, UAV SAN maintains significantly higher RP than conventional UAV networks after post-disconnection, confirming its superior stability.
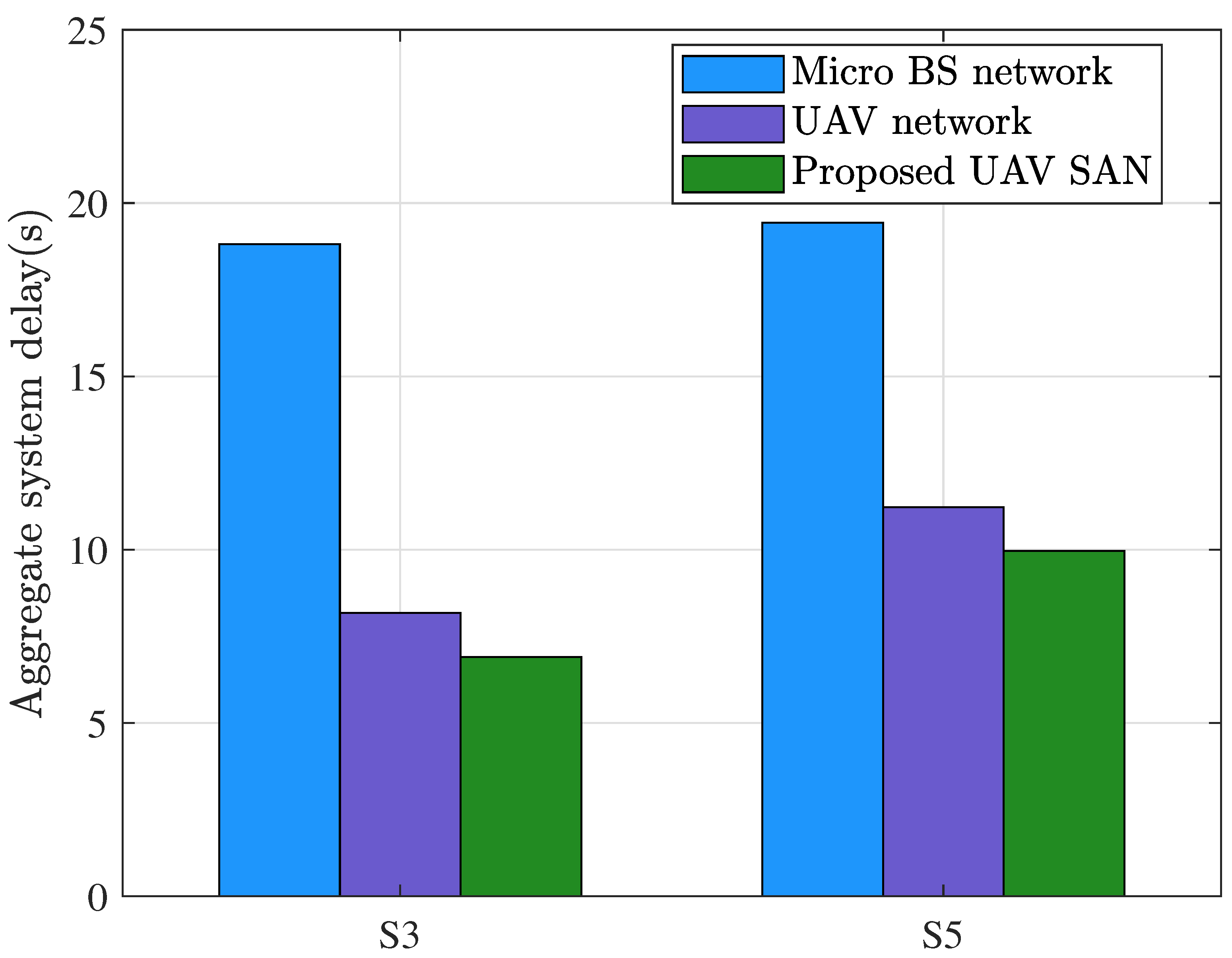
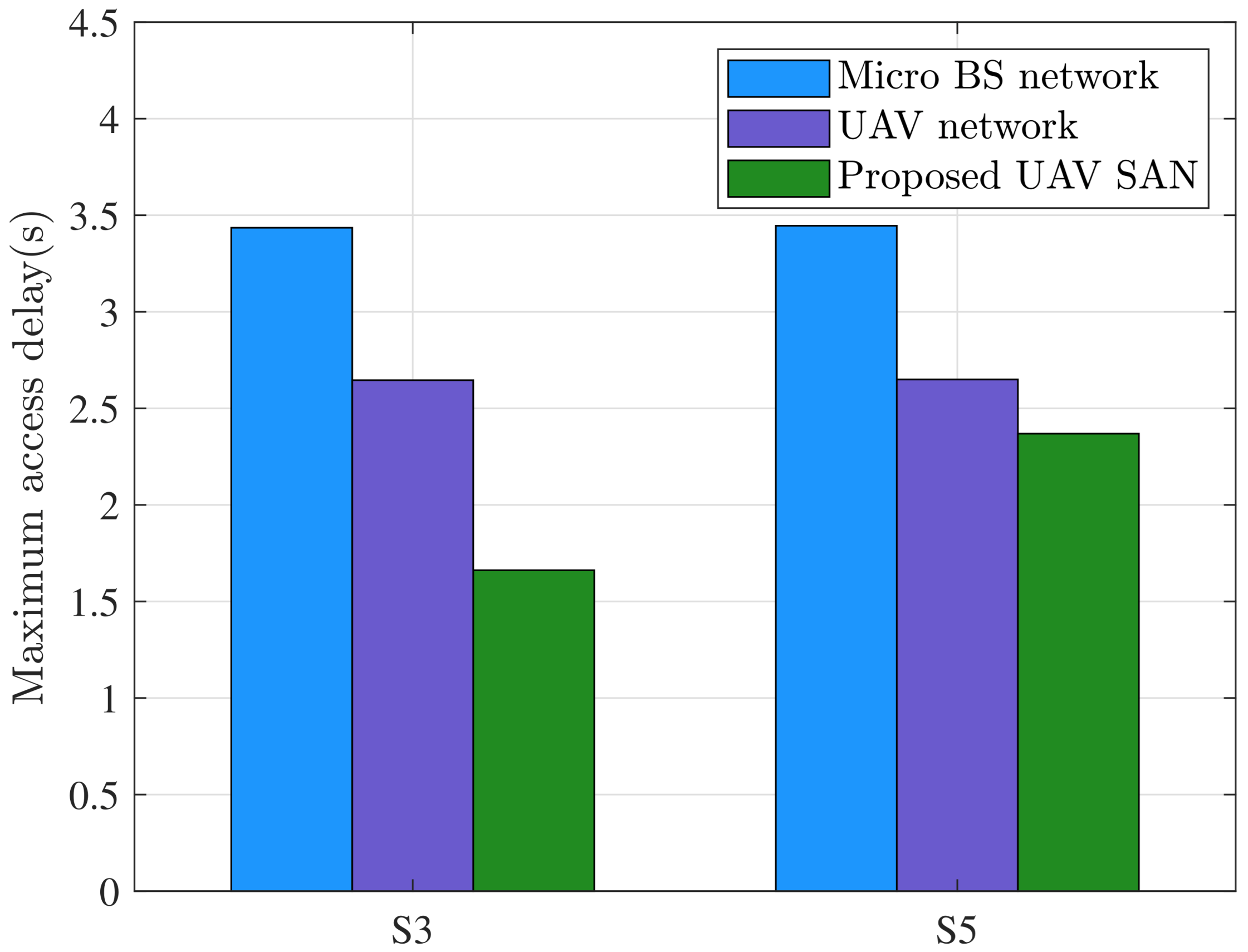
Figure 7 and
Figure 8 compare delay performance across micro BS networks [
6,
7], UAV networks [
13,
15], and the proposed UAV SAN. Simulation parameters are specified in
Table 5. Comparing S3 and S5, the severely maldistributed demand (S5) increases system delay because high-demand content must be fetched from distant micro BSs and neighboring UAVs, extending communication paths and amplifying delay. In both S3 and S5, UAV networks significantly outperform micro BSs in maximum access delay and aggregate system delay. Crucially, UAV SAN further reduces both delay metrics through its integrated social architecture.
Figure 9 reveals the convergence of S1. The convergence curves of
converge before 2000 iterations, while the curve of
converges around 7000 iterations. The increase in
n significantly broadens the feasible range, which leads to a decrease in convergence speed.
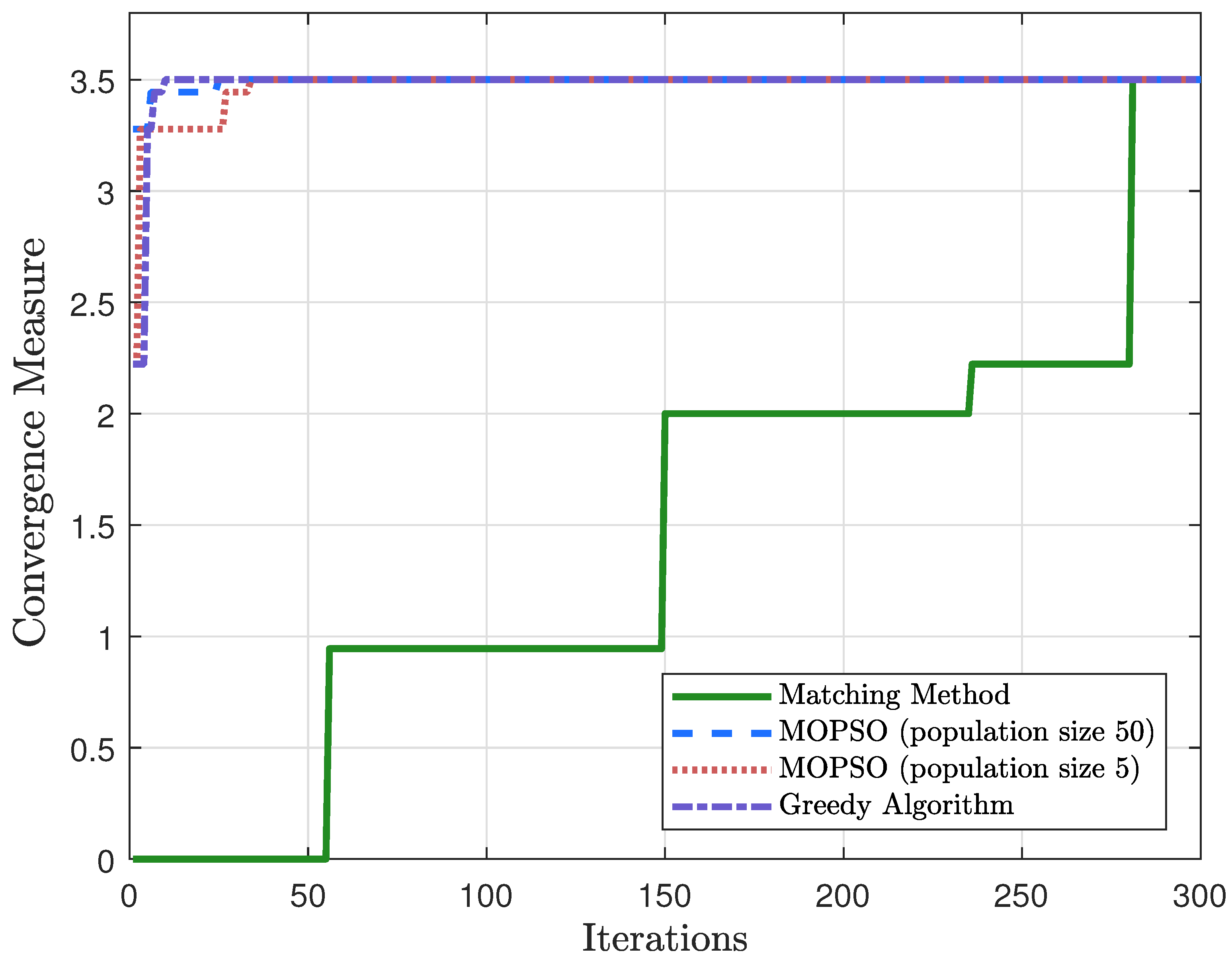
Figure 10 demonstrates that the MOPSO algorithm exhibits significantly stronger convergence than the matching method. While the greedy algorithm achieves rapid convergence, its substantial computational overhead per iteration leads to a notable increase in overall runtime. Moreover, increasing the population size accelerates the convergence of the MOPSO algorithm.
5. Conclusions
In this paper, we addressed the pressing challenge of optimizing resource allocation in cache-enabled multi-UAV networks, where imbalances in user demand and storage capacity can degrade performance. We introduced a novel cache-enabled multi-UAV socially aware network (SAN) that incorporates “selfish” and “selfless” social attributes to intelligently control the degree of cooperation among UAVs. To balance the competing goals of network-wide efficiency and fairness to user groups, we formulated the caching deployment strategy as a multi-objective optimization problem (MOOP), aiming to simultaneously maximize the aggregated request probability (a proxy for QoS) and the diversity of cached content (a proxy for fairness). The MOPSO algorithm demonstrates superior convergence speed and enhanced exploration capability in 10-objective problems compared to other metaheuristics (e.g., NSGA-II). Furthermore, through the problem transformation proposed in this paper, it effectively reduces the feasible region relative to conventional binary encoding schemes, thereby substantially lowering computational complexity. Confronting the NP-hard nature of this discrete MOOP, we designed an effective solution based on a Multi-Objective Particle Swarm Optimization (MOPSO) algorithm, enhanced with a mutation strategy to ensure population diversity and prevent premature convergence to local optima. The algorithm efficiently approximates the Pareto optimal front, offering network operators a valuable set of optimal trade-off solutions rather than a single, rigid operating point.
The simulation results validated the efficacy of our approach and yielded several key insights. Firstly, the introduction of the social awareness mechanism provides a significant performance gain over traditional, non-cooperative caching schemes, particularly in realistic scenarios with uneven distributions of user requests and storage resources. By enabling collaboration, the framework allows the collective storage of all UAVs to be utilized as a cohesive whole, effectively mitigating localized resource shortages. Secondly, our results confirmed the fundamental trade-off between maximizing content diversity and total request probability, demonstrating the validity of the MOOP formulation. Finally, we demonstrated that the social constraint parameters, and , serve as effective tools for tuning network behavior, allowing for a deliberate balance between fairness and efficiency to meet diverse operational requirements. determines the priority level of UAV cells, while governs the priority of the entire macro zone. Thus, the configuration of and is traffic-dependent. In high-traffic venues (e.g., stadiums), both and can be set to prioritize user demands in cells and macro zones. During low-traffic periods, and can be reduced to release resources for neighboring cells and macro zones. The convergence of the proposed algorithm was also verified, confirming its robustness and suitability for this complex optimization task.