Abstract
With the rapid advancement of unmanned system technologies, their applications in transportation, scientific research, economy, resource exploration, and military fields have become increasingly widespread. The navigation system, as a fundamental component of unmanned systems, plays a crucial role in ensuring their stability and reliability. However, as technology evolves, interference targeting Global Navigation Satellite Systems (GNSSs) has escalated, posing significant challenges in the research of unmanned systems. Navigation interference not only disrupts the normal operation of unmanned systems but also emerges as a pivotal element in counter-unmanned system strategies. This paper provides a comprehensive review of the classification of GNSS navigation interference and its potential impacts, thoroughly analyzing and comparing the strengths and weaknesses of various anti-GNSS interference technologies. Finally, the paper offers insights into the future development trends of anti-interference technologies for unmanned systems, aiming to provide valuable references for future research.
1. Introduction
With the progress of the economy, society, and technology, unmanned platforms represented by unmanned aerial vehicles (UAVs), unmanned ground vehicles (UGVs), and unmanned surface vessels (USVs) have been increasingly applied in fields such as transportation, resource exploration, national defense and military, and scientific research, demonstrating enormous development potential [1,2,3,4,5].
For unmanned systems, the navigation system is of great significance. Generally, an integrated navigation system composed of sensors such as GNSS receiver and Inertial Navigation Systems (INSs) provides unmanned systems with information on position, velocity, and attitude. In particular, unmanned systems operating in large-scale outdoor environments (e.g., UAVs, UGVs, and USVs) rely on a GNSS-based navigation system to obtain absolute position information [4,5,6,7,8]. For example, a UAV is equipped with a variety of navigation sensors such as INSs, satellite navigation, magnetometer, barometer, and ranging sensor to provide it with multi-source navigation information, as shown in the Figure 1.
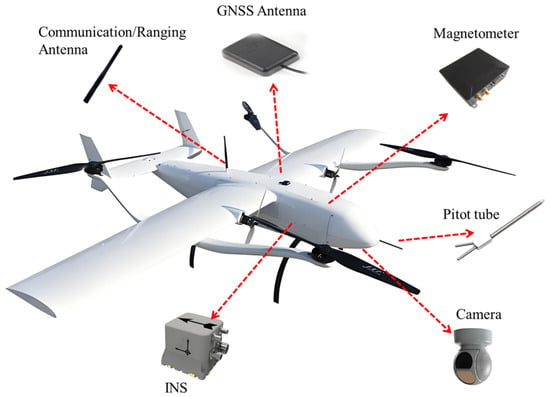
Figure 1.
Schematic diagram of navigation sensor installed on unmanned platform (UAV).
Typically, GNSSs and INSs are complementary, forming the basic configuration of integrated navigation for unmanned systems. Additionally, some unmanned systems are equipped with other sensors such as cameras, radars, rangefinders, loggers, and odometers. However, these sensors have various drawbacks. For instance, cameras and LiDARs can only be used in scenarios with distinct features, like urban areas or indoor spaces with obvious landmarks, but not in feature-scarce environments such as oceans and deserts. Moreover, they are susceptible to weather and environmental conditions. Rangefinders also have limited usage ranges. Loggers and odometers usually require frequent and precise calibration of installation errors and are prone to cumulative errors. Navigation sensors can be divided into autonomous and non-autonomous types. Autonomous navigation sensors do not require external signals, and non-autonomous sensors do not. INSs and GNSSs are representatives of autonomous and non-autonomous navigation sensors, respectively.
As fundamental sensors for unmanned system navigation, due to the high-altitude orbits of GNSS navigation satellites and the spread-spectrum modulation technology commonly used in satellite signals, the signal spectrums are typically broadened and buried in noise. The signal level transmitted to the ground is generally only about −130 dBm. This makes GNSS receivers vulnerable to various intentional and unintentional electromagnetic interferences, which can lead to instability and errors in the navigation system [4,5]. These issues may further jeopardize the mission execution of unmanned systems and even result in more severe consequences, such as crashes. Therefore, enhancing the anti-interference and anti-deception capabilities of navigation signal receiving systems has become one of the current research hotspots.
The main motivation of this paper is as follows: Considering the increasingly widespread application of unmanned platforms such as drones in various industries, a GNSS is the primary sensor used for drone positioning. However, the technology of GNSS spoofing and jamming is becoming more advanced, and the cost of related equipment is decreasing, leading to more frequent malicious interference targeting drone GNSSs. These malicious interferences can have negative impacts on the application of drones in agriculture, transportation, logistics, and exploration surveys.
This paper aims to provide a comprehensive review of anti-GNSS interference technologies and evaluate their potential applications and development in drones, offering references for subsequent related research. The main contributions of this paper are as follows:
- (1)
- A systematic review of the challenges posed by GNSS interference to unmanned systems and various methods to address GNSS interference. The anti-interference methods are categorized into seven types, including multi-antenna-based anti-interference methods; signal authentication-based anti-interference methods; signal acquisition, tracking, and processing-based anti-interference methods; external sensor-based anti-interference methods; etc.
- (2)
- A comparison of the advantages and disadvantages of each method, and an evaluation of their application scenarios, advantages, and disadvantages in unmanned platforms.
- (3)
- A prospective outlook on the further development of anti-GNSS interference technologies applicable to unmanned platforms.
3. Research Status of Anti-GNSS Interference Technology
The operational principle of GNSS terminals involves the reception of GNSS signals by a GNSS antenna, followed by signal processing to derive observation data. These data are then utilized to compute critical navigation parameters, such as position, velocity, and time (PVT). Based on this operational framework, anti-GNSS interference techniques can be categorized into two primary levels: signal-level and information-level interference mitigation.
At the signal level, the focus is on processing the raw radio-frequency (RF) signals received by the GNSS antenna. This level of interference mitigation aims to filter out or suppress interference signals before they affect subsequent processing stages. Techniques at this level are particularly effective against suppressive interference, which refers to intentional or unintentional signals that degrade the quality of the desired GNSS signal. At the information level, interference mitigation strategies are implemented during the post-reception signal processing phase. This approach leverages specific parameters or features extracted from the GNSS signals to detect or identify the presence of interference. For example, changes in the carrier-to-noise ratio (CNR) or deviations in signal quality metrics can serve as indicators of potential interference. Information-level techniques are often employed to enhance the robustness of GNSS receivers against various types of interference, including both intentional jamming and unintentional spectral overlaps.
The development of advanced anti-GNSS interference technologies has become increasingly critical due to the growing reliance on GNSS systems in applications ranging from navigation to timing to surveying. Researchers continue to explore innovative methods to improve the resilience of GNSS receivers against diverse interference sources, ensuring reliable performance in challenging environments.
3.1. Multi-Element Antenna-Based Anti-GNSS Interference Technology
3.1.1. Application of Multi-Array Antenna in Anti-Suppressing Jamming
GNSS suppression interference often occurs together with GNSS deception interference, so suppression detection and anti-interference are also very important for combating deception interference. Multi-element antenna-based anti-interference technology is the most common method and primarily relies on two advanced techniques: adaptive nulling technology and digital multi-beam technology [10]. Due to its insensitivity to interference bandwidth, it can effectively suppress narrowband and broadband suppression interference, such as continuous wave interference, sweep frequency interference, or pulse interference. Adaptive nulling technology dynamically adjusts the weighting vectors of the antenna array based on the spatial variations of the signal’s location. By forming a main beam in the direction of the target signal and creating nulls in the directions of interfering signals, this technique effectively suppresses interference while maintaining the integrity of the desired signal [11]. Similarly, digital multi-beam technology implements adaptive beamforming in the baseband using digital methods. This approach enhances the output signal-to-noise ratio (SNR) of useful signals while simultaneously suppressing interference signals.
Multiple anti-interference techniques in array signal processing are commonly used, including time-domain filtering, frequency-domain filtering, spatial adaptive filtering, space-time adaptive filtering, space-frequency adaptive filtering, and digital multi-beam technology.
An array antenna with N elements can form up to N-1 nulls in space, meaning it can simultaneously suppress up to N-1 interferers from different directions, such as a 4-element antenna suppressing three interferers from different directions. Common adaptive beamforming algorithms include the minimum variance distortionless response (MVDR) beamformer and the linearly constrained minimum variance (LCMV). Anti-interference algorithms based on digital multi-beam technology include the least mean squares (LMS) algorithm, the recursive least squares (RLS) algorithm, etc. Multi element antennas can significantly improve the anti-interference ability of receivers. For example, a 4-element anti-interference antenna can increase the improvement amplitude by 60–80 dB or even higher, and a 7-element antenna can increase the anti-interference ability to over 90 dB.
Anti-interference algorithms based on digital multi-beam require prior knowledge to perform normal anti-interference processing, so the angle estimation of interference signals is needed, with commonly used algorithms including multiple signal classification (MUSIC), the estimation of signal parameters via rotational invariance techniques (ESPRIT), compressed sensing (CS), etc.
Figure 3 shows a layout diagram of an 8-element GNSS anti-interference antenna. Figure 4 shows the antenna array factor for a different number N of array elements.
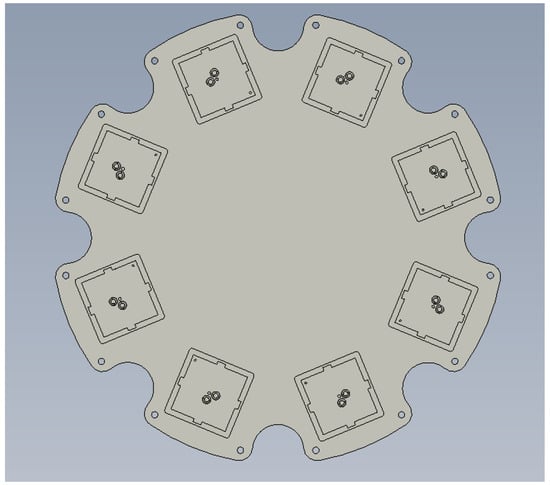
Figure 3.
The 8-element GNSS anti-interference antenna layout diagram.
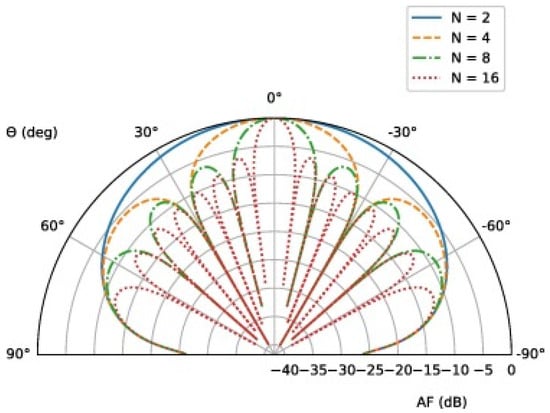
Figure 4.
Antenna array factor for different number N of array elements when and [12].
In summary, anti-interference techniques based on array antennas represent a critical front-end solution for mitigating GNSS interference. These methods are well-suited to counteract various types of suppression interference and high-power deceptive interference. Significant progress has already been achieved in this field, with numerous practical applications demonstrated. However, while array antenna-based anti-interference technology can mitigate interference within a certain range, the continuous advancement of GNSS interference techniques poses challenges. More sophisticated interference devices may eventually surpass the protective capabilities of array antennas, potentially compromising navigation system performance.
Moreover, the baseline length between antenna elements in an array is proportional to the wavelength of the received signals. Consequently, a single antenna array cannot simultaneously enhance the anti-interference performance of navigation signals operating at different frequencies. For example, the GPS L1, L2, and L5 frequencies correspond to center frequencies of 1575.42 MHz, 1227.60 MHz, and 1176.45 MHz, respectively, with corresponding wavelengths of approximately 19 cm, 24.4 cm, and 25.5 cm. Additionally, the anti-interference capability of array antennas is closely related to the number and size of the array elements. This inherent design tradeoff inevitably leads to increased size, weight, and power consumption. While these characteristics are acceptable for larger platforms (e.g., unmanned aerial vehicles with substantial dimensions), they present significant challenges for smaller platforms, such as miniature drones, where size and power constraints are critical limiting factors.
3.1.2. Spatial Direction Detection-Based Anti-Spoofing Using Multi-Antenna Arrays
Beyond suppressing jamming interference, multi-element antenna arrays can exploit signal direction-of-arrival (DOA) information for spoofing detection. Two primary approaches exist [13]. The first one is a consistency check of signal directions; this method does not require prior knowledge of true DOA values. Spoofing is detected when multiple signals arrive from the same direction. Genuine satellite signals originate from distinct locations in the sky, while spoofing signals from a single transmitter exhibit consistent carrier phase, amplitude, and Doppler frequency, enabling detection via antenna arrays or receiver motion [14,15]. The second one is Angle-of-Arrival (AOA) Detection, which calculates the AOA of received signals and compares it with the expected AOA of genuine satellites. Detection accuracy depends on baseline orientation knowledge. Well-designed receivers achieve carrier phase measurement precision of 1/40th of the carrier wavelength, translating to 3° AOA accuracy with a 0.1m baseline. Spoofing signals typically originate from a single transmitter, making their DOA inconsistent with genuine satellites [16].
Daneshmand et al. proposed an anti-spoofing method for multipath environments using spatial and temporal processing to estimate spoofing channel coefficients and suppress interference [16]. Zhang et al. developed a two-stage interference suppression scheme using antenna arrays to first eliminate high-power interference and then remove spoofing signals via subspace projection. However, this approach requires more array elements than the sum of interference and satellite signals, increasing hardware costs and computational complexity [17]. Broumandan et al. distinguished spoofing from genuine signals based on shared spatial characteristics for single-transmitter spoofing scenarios [18]. Montgomery et al. studied anti-spoofing using dual-antenna arrays by comparing theoretical and actual carrier phase differences under known baseline conditions [19].
While effective, these spatial detection methods impose additional constraints on receiver deployment. With fewer array elements, they primarily detect spoofing; with more elements, they suppress single-direction spoofing but at higher hardware and algorithmic costs.
3.2. Anti-Interference Technologies Based on Signal Encryption or Authentication
Anti-interference technologies based on signal encryption or authentication aim to enhance the security and reliability of satellite navigation systems by preventing spoofing attacks and ensuring the authenticity of navigation signals. These techniques involve adding encrypted or authenticated markers to satellite navigation signals, allowing receivers to verify whether the signals originate from legitimate satellites and whether the signal/messages have been tampered with. Such methods represent a critical anti-deception measure on the GNSS system side.
Satellite navigation signals consist of three components: carrier waves, pseudorandom codes, and navigation messages. The newly added authentication markers can be embedded in either the navigation messages or the spread spectrum codes, leading to two distinct authentication approaches: Navigation Message Authentication (NMA) [20] and Spread Spectrum Code Authentication (SCA) [21], Figure 5 shows the schematic diagram of them.
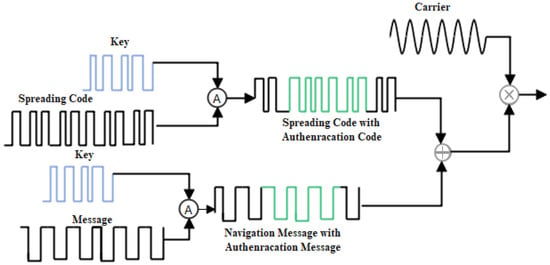
Figure 5.
Schematic Diagram of NMA and SCA [22].
Galileo system announced its Navigation Authentication Service (NAS) plan in 2016, providing Open Service Navigation Message Authentication (OSNMA) for the Galileo-E1B signal. Currently, test signals are available, and the official service is scheduled to commence since 2023. Similarly, the Japanese Quasi-Zenith Satellite System (QZSS) [23] and the Indian Navigation Constellation (NavIC) [24] have conducted in-orbit testing and validation of navigation message authentication technologies. Additionally, the U.S. Air Force Research Lab has proposed the Chip Message Robust Authentication (CHIMERA) enhancement for the L1C signal. In particular, the Chimera fast channel allows users to authenticate the received GPS signal once every 1.5 or 6s, depending on the out-of-band source utilized for receiving the fast channel marker key concept, which has undergone technical testing [25,26]. Chen et al. designed the service architecture for the next-generation BeiDou system’s authentication mechanism and analyzed the associated technical challenges [22].
NMA implements navigation source authentication through bit-level message verification, offering three principal advantages: compatibility with existing signal infrastructures requiring minimal hardware modifications, preservation of legacy modulation schemes through receiver software upgrades, and cost efficiency with deployment costs lower than hardware-based solutions. The Galileo E1 OSNMA processing logic is shown in Figure 6.
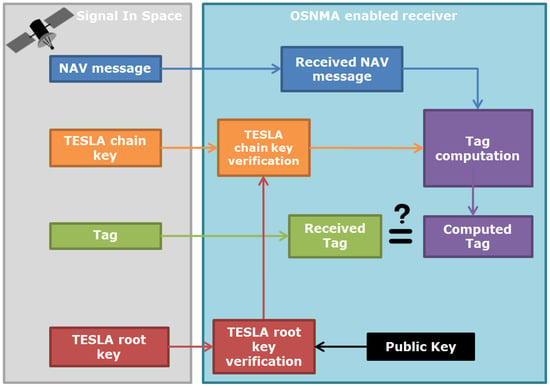
Figure 6.
OSNMA processing logic [27].
SCA enhances security through pseudo-range-domain spoofing resistance, leveraging unpredictable code-phase alterations in the power domain. The CHIMERA signal exemplifies this through its TMBOC (Time-Multiplexed Binary Offset Carrier) modulation scheme, which partitions 1ms intervals into 31 segments containing 33 chips each, as shown in Figure 7. Dynamic authentication replaces 29 BOC(1,1) chips per segment while preserving 4 BOC(6,1) pilot chips, coupled with dual-channel authentication—fast (1 ms) for real-time validation and slow (3–6 s) for key synchronization.
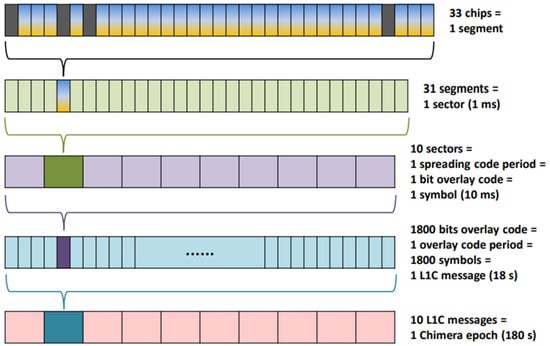
Figure 7.
The structure of the Chimera L1C signal [28].
Compared with NMA, SCA can provide spoofing protection in the pseudo-range domain, and it has higher security. However, the SCA authentication chip needs to be delayed to the user receiver; the receiver needs to buffer the sampled data so the implementation cost of the receiver is relatively costly.
Anti-interference methods based on signal authentication are primarily designed to counteract generative spoofing attacks by verifying the integrity and authenticity of GNSS signals. However, these methods may face limitations in addressing real-time replay spoofing attacks, as such attacks exploit the delay between signal transmission and reception. Additionally, implementing these authentication techniques requires upgrades to receiver hardware and software, posing challenges for legacy systems that lack the necessary infrastructure for authentication.
In summary, while signal encryption and authentication technologies represent a promising approach to enhancing GNSS security, their widespread adoption depends on overcoming technical and implementation barriers. Continued research and collaboration between international organizations and researchers are essential to address these challenges and ensure the robustness of satellite navigation systems against increasingly sophisticated interference threats. This type of technology can defend against the generated type of spoofing but not the replayed type because the replayed spoofing retains all the signal authentication [29].
3.3. Anti-Interference Technologies in Signal Acquisition, Tracking, and Processing
3.3.1. Anti-Interference Method Based on Front-End Filtering Technology
The signal received by the antenna enters the RF front-end of the receiver, which mainly includes bandpass filters, amplifiers, mixers, automatic gain controllers, and analog-to-digital converters to complete the functions of RF signal adjustment, down conversion mixing, IF signal filtering and amplification, and analog-to-digital conversion. During this process, interference suppression can be achieved through front-end filtering technology. Front-end filtering techniques include time-domain adaptive filtering methods, frequency-domain filtering methods, spatial filtering, and transform domain filtering. Among them, time-domain filtering adopts digital signal processing methods to design finite impulse response filters or infinite impulse response filters based on the different autocorrelation characteristics of navigation signals and interference signals, effectively suppressing interference; frequency domain filtering separates interference signals from input signals based on their different spectral characteristics in the frequency domain or transform domain, with a certain signal loss. Frequency domain filtering has a good suppression effect on narrowband interference, such as narrowband continuous wave interference, sweep frequency interference, or pulse interference [30,31].
3.3.2. Received Power Monitoring
Anti-spoofing techniques based on received power monitoring (RPM) can be implemented by either monitoring the absolute received signal strength or observing changes in the automatic gain control (AGC) gain of the RF channel [32,33,34]. This method is particularly effective in scenarios where spoofing signals are significantly stronger than genuine satellite signals. However, when the strength difference between spoofing and satellite signals is minimal, RPM-based anti-spoofing algorithms may fail to detect the interference effectively [35].
3.3.3. Signal Quality Monitoring
During the initial phase of a spoofing attack, the combined effect of both spoofing and genuine signals distorts the spreading code correlation function. By monitoring the integration results of the tracking loop, spoofing signals can be detected. In signal quality monitoring (SQM)-based anti-spoofing detection, metrics such as slope and increment are used to monitor potential distortions and anomalies in the signal correlation peak [36,37,38]. A critical challenge lies in distinguishing between multipath effects and spoofing signals while maintaining high detection accuracy and minimizing false alarms. Wesson introduced a power distortion detector in 2018, which categorizes received signals into categories such as no interference, multipath, or spoofing based on the joint distribution of received power and correlation function distortion [39].
3.3.4. Doppler Shift Consistency Check
The relative motion between the satellite and the receiver causes Doppler shifts in both the carrier frequency and the spreading code of GNSS signals. Genuine satellite signals exhibit consistent Doppler shifts between the carrier and spreading code, maintaining a fixed proportion. Simple spoofing sources may fail to maintain this proportion, enabling detection through consistency checks [40]. Once a receiver locks onto a genuine satellite signal and establishes a position fix, it can predict the next doppler shift based on the receiver and satellite motion. By comparing the predicted value with the measured value, spoofing interference can be identified when the deviation exceeds a predefined threshold [14,41,42]. For example, Li et al. proposed a spoofing detection method called the Q-channel signal component (QSC), as shown in Figure 8; the basic idea is to exploit the spoofing-induced feature by transforming the correlator output into the frequency domain [29].
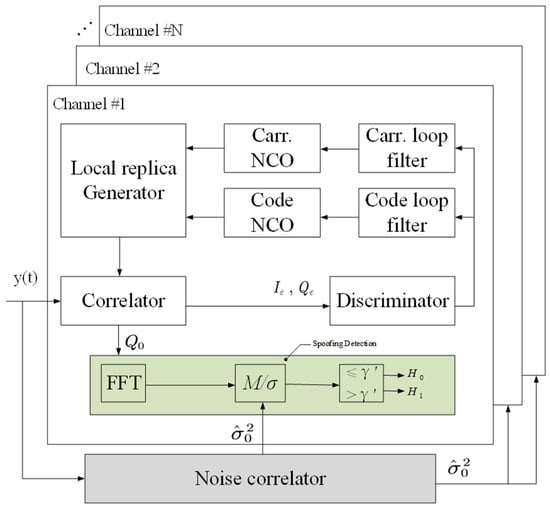
Figure 8.
A block diagram of the tracking loop architecture with spoofing detection.
3.3.5. Multi-Peak Correlation Detection
When a spoofing signal and a genuine satellite signal have a code-phase difference exceeding one chip, two correlation peaks appear in the code-phase dimension of the receiver’s capture results. By introducing multi-peak detection algorithms, spoofing signals can be identified. Multiple correlation peaks can be assigned to different tracking channels for subsequent processing to isolate spoofing signals [43,44]. Dehghanian et al. developed a multi-hypothesis testing method for detecting spoofing attacks during the acquisition phase, demonstrating its effectiveness in urban multipath environments [32].
3.3.6. Multi-Correlator-Based Anti-Spoofing Techniques
Both multipath signals and spoofing interference share similarities with genuine satellite signals, including identical ranging codes and distortions in the autocorrelation function, leading to erroneous pseudo-range measurements. Therefore, some multipath mitigation algorithms can be adapted for anti-spoofing applications. The multipath estimating delay lock loop (MEDLL) is a typical multi-correlator-based algorithm designed for multipath suppression [45]. It enhances traditional receiver tracking structures by incorporating additional correlators to estimate the amplitude, pseudocode phase, and carrier phase of both satellite and multipath signals. Subsequent processing removes multipath contributions, yielding accurate positioning results. However, anti-spoofing applications require addressing unique challenges:
- Spoofing Detection: Spoofing suppression algorithms can be quickly activated under spoofing conditions.
- Spoofing Component Identification: Unlike multipath signals, which are always delayed relative to genuine signals, spoofing signals exhibit complex behaviors, requiring new identification methods.
- Spoofing Suppression: High-energy spoofing signals can dominate receiver tracking loops, causing genuine signals to vanish from correlator outputs, necessitating feedback mechanisms to maintain a lock on genuine signals.
Blanco-Delgado analyzed MEDLL’s principles and derived improved interpolation-based MEDLL algorithms to enhance parameter estimation accuracy [46]. Gross extended MEDLL with a power-distortion maximum-likelihood (PD-ML) detector, simultaneously monitoring received power and correlation function distortion to classify interference types [47]. Guo applied MEDLL to estimate parameters of replayed spoofing signals, identifying delayed signals as spoofing and suppressing them [48]. However, this method is ineffective against generated spoofing signals with advanced pseudocode phases.
3.3.7. Using RAIM and Its Improved Algorithms
The receiver autonomous integrity monitoring (RAIM) algorithm detects faulty satellites by analyzing pseudo-range residuals after receiver positioning. While RAIM can exclude one or more spoofed satellite signals, it fails when all spoofing signals are consistent. Wei introduced a time-domain differencing RAIM algorithm combining carrier doppler checks with RAIM for broader applicability [49]. Li proposed a stochastic traversal RAIM method effective against spoofing when more than four genuine signals are available [50]. Kuusniemi adapted Advanced RAIM (ARAIM) for multipath navigation consistency monitoring, achieving partial spoofing suppression but with limited applicability [51].
3.4. Interference Recognition Using Auxiliary Information of External Sensors
Unmanned platforms typically integrate sensors like INSs, Odometry, LiDAR, visual sensors, and high-stability clocks alongside GNSS receivers. These sensors can provide spoofing-immune measurements that aid in detecting GNSS interference, particularly spoofing attacks [52].
Anti-spoofing techniques leveraging auxiliary devices primarily rely on monitoring abnormal changes in the GNSS receiver’s position or time. If the receiver’s position, velocity, or time variations exceed predefined thresholds, a spoofing event is inferred to be present. Common auxiliary devices include INSs, LiDAR, accelerometers, visual sensors, high-stability clocks, and odometers [53]. Among these, the most widely employed method involves utilizing INS data, with primary algorithms focusing on detecting anomalies through innovation information within GNSS/INS integrated navigation systems. This approach effectively identifies spoofing interference [54,55,56,57,58,59,60,61,62,63].
Chip-scale atomic clocks (CSACs), characterized by their high frequency accuracy and stability, maintain precise time references over extended periods. These clocks can assist in detecting time-based spoofing by analyzing discrepancies in receiver clock offsets. For example, Liu Yang et al. developed a CSAC-assisted spoofing detection algorithm based on differences between receiver clock biases under spoofing conditions and those from authentic signals [64]. The experimental results demonstrated significant improvements in spoofing detection performance compared to methods using temperature-compensated crystal oscillators (TCXOs) or pressure-controlled TCXOs (PTCXOs). Hu et al. also analyzed the influence of deception signals on the target receiver clock frequency drift and established a receiver clock frequency drift model in uniform circular motion, then calculated the correlation values between clock frequency drift and cosine function. This method can detect deception jamming signals and prevent the occurrence of a false alarm by monitoring the normalized circle correlation values [65].
Visual sensors, on the other hand, estimate carrier motion trajectories by analyzing image sequences. These trajectories can be fused with GNSS positioning results to enhance spoofing detection. Specifically targeting spoofing threats faced by UAVs, Varshosaz developed a visual sensor-based spoofing detection algorithm. This algorithm compares the relative flight trajectory derived from visual sensors with the absolute trajectory provided by GNSSs, employing drift error constraints to mitigate the effects of spoofing interference [66].
In summary, the integration of INSs and other sensors with GNSSs significantly enhances the ability to detect and counteract spoofing interference. Methods such as innovation-based detection, high-stability clock assistance, and visual sensor trajectory comparison offer robust solutions for improving the reliability and security of GNSS-based navigation systems. These techniques not only address the limitations of GNSSs in adversarial environments but also provide a comprehensive framework for ensuring accurate and trustworthy navigation in unmanned platforms.
3.5. Application of Artificial Intelligence in Anti-Spoofing Technology
In recent years, artificial intelligence (AI) technology has experienced rapid development, leading to an increasing focus on AI-based methods for detecting spoofing interference in addition to traditional anti-spoofing algorithms [67,68]. For instance, Manesh proposed a GPS spoofing detection method based on artificial neural networks (ANNs). By analyzing five key parameters—the number of satellites, signal-to-noise ratio (SNR), pseudo-range, doppler frequency, and carrier phase—this method developed a spoofing detection model after analyzing existing data [69]. However, the current availability of spoofing scenarios and datasets remains limited. Existing publicly available datasets only cover partial spoofing scenarios, which restricts the adaptability of AI-based spoofing detection algorithms to all possible spoofing environments.
Moreover, most existing anti-spoofing techniques based on single-antenna GNSS receivers are limited to detecting spoofing interference and issuing alerts, without the ability to recover accurate positioning, velocity, and timing (PVT) information [68,70,71,72,73]. This limitation highlights the need for further advancements in both detection and mitigation strategies.
Recent studies have explored various AI-driven approaches to enhance spoofing detection capabilities. KORIUM M S et al. developed an image-based intrusion detection system for identifying GPS spoofing cyberattacks using deep learning methodologies [71]. Their approach combined convolutional neural networks (CNNs) with Principal Component Analysis (PCA) to reduce feature dimensionality. Additionally, they employed data augmentation to expand the size and diversity of the training dataset and utilized transfer learning to improve model performance, even with limited data. This resulted in a fast, accurate, and generalizable method for detecting GNSS spoofing attacks.
TALAEI KHOEI T et al. investigated the impact of model parameters and dataset characteristics on the performance of machine learning techniques for detecting GNSS spoofing attacks. They evaluated how hyperparameters, regularization parameters, dataset size, correlated features, and imbalanced datasets affect six widely used machine learning methods: Classification and Regression Decision Tree, artificial neural network, Random Forest, Logistic Regression, Gaussian Naïve Bayes, and Support Vector Machine [72]. This study provides valuable insights into optimizing machine learning models for spoofing detection under diverse conditions.
To address the growing threat of GPS spoofing to small UAVs, ALANAZI A et al. proposed an innovative hybrid architecture named the Self-Supervised Deep Representation Learning (SSRL) Approach [73], which integrates Long Short-Term Memory (LSTM) and Gated Recurrent Unit (GRU) models to detect attacks on small UAVs. Additionally, they developed two other architectures—LSTM-Recurrent Neural Network (RNN) and Deep Neural Network (DNN)—to detect GPS spoofing attacks. These approaches demonstrate the potential of SSRL in enhancing spoofing detection capabilities for UAVs.
Despite these advancements, AI-based anti-interference techniques still face significant limitations. The scarcity of realistic GNSS interference scenarios and datasets hinders the development of robust spoofing detection algorithms capable of operating across all possible environments. Furthermore, current AI-based methods are primarily focused on detecting interference and issuing alerts rather than recovering accurate navigation information. Addressing these limitations will require collaborative efforts to develop comprehensive datasets, refine detection algorithms, and integrate mitigation strategies to ensure reliable navigation in adversarial environments.
3.6. Anti-Spoofing Methods Based on Cooperative Navigation
In modern unmanned systems, multiple platforms often operate in coordinated formations to accomplish complex tasks. This collaborative setup provides an opportunity to leverage mutual observation data among platforms to detect and mitigate spoofing interference. Cooperative navigation, which relies on the relative positioning and mutual observation data between platforms, offers a robust framework for identifying discrepancies in GNSS signals caused by spoofing attacks [74].
In such systems, each platform can share its GNSS-derived PVT data with others in the formation. By cross-referencing this information with independent measurements, such as radio-based ranging or radar-derived bearing and range data, deviations caused by spoofing interference can be detected. For instance, in simple spoofing scenarios where multiple platforms receive identical false GNSS signals, cooperative navigation can exploit the consistency of mutual observations to identify inconsistencies in the GNSS-derived PVT data. If the GNSS positioning results deviate significantly from the relative positioning data derived from mutual observations, it indicates the presence of spoofing interference [75,76].
This method integrates mutual observation data, such as radio-based ranging information or radar-derived azimuth-range information, into the navigation system to enhance the detection of spoofing interference. By comparing the GNSS positioning results with the relative positioning data obtained from mutual observations, the system can effectively identify and mitigate GNSS spoofing attacks. This approach not only improves the robustness of the navigation system but also provides a reliable means to ensure the integrity of GNSS signals in adversarial environments.
3.7. Integrated Anti-Spoofing Methods Based on Multiple Approaches
In the realm of GNSSs, no single anti-interference method is capable of completely mitigating the effects of spoofing interference. Therefore, it is imperative to adopt a multi-method approach, selecting and combining several techniques based on constraints such as size, weight, power consumption (SWaP), and operational requirements. This integrated strategy not only enhances anti-interference performance but also improves the stability, robustness, and survivability of unmanned systems in challenging electromagnetic environments [77,78].
Xu et al. integration of MEDLL and INSs for spoofing mitigation, they developed a method that combines the MEDLL structure with INSs. By utilizing INS-derived position estimates, this approach calculates the true pseudo-range and identifies satellite signals by comparing the estimated pseudo-range with the INS-derived pseudo-range [79]. This integration effectively distinguishes between genuine and spoofed signals, providing a robust solution for anti-spoofing applications.
Shang et al. enhanced spoofing detection and mitigation using GNSS/INS integration; they addressed the limitations of traditional GNSS/INS-based anti-spoofing algorithms, which primarily focus on detection without restoring correct positioning results. Their approach employs the multi-correlator structure, typically used in multipath suppression algorithms, to estimate parameters for both genuine and spoofed signals. By leveraging the high short-term precision of INSs, they successfully identified spoofed signals. The identified spoofing signals are then fed back into the tracking loop to cancel their effects, ensuring that the receiver remains locked onto authentic satellite signals. Furthermore, they incorporated a robust Kalman filtering algorithm into the GNSS/INS integrated navigation system to mitigate the impact of outliers in parameter estimation and identification results, thereby improving positioning accuracy [80,81]. This method achieves both spoofing detection and recovery of accurate positioning results. Khanafseh and Tanil introduced a method that integrates RAIM into GNSS/INS combined measurements. By analyzing the time series of estimation residuals, they achieved effective spoofing detection [82]. Similarly, Liu et al. enhanced the detection performance of GNSS/INS integrated systems by applying measurement mean and innovation mean techniques, commonly used in autonomous integrity monitoring, to detect spoofing interference across various scenarios. This approach significantly improves the system’s ability to detect spoofing interference of different types. Gioia et al. investigated interference mitigation strategies for multi-layered multi-constellation GNSS systems, focusing on enhancing system resilience against spoofing and interference [83]. Vagle et al. examined the performance of single-antenna and multi-antenna GPS receivers in automotive navigation under spoofing, interference, and GPS-denied conditions [84]. Their research emphasized the benefits of integrating INSs with odometry data for improved robustness in challenging environments. Fan et al. proposed a method combining INSs with a three-element antenna array to detect single-source spoofing and multi-transmitter spoofing attacks. This approach exploits spatial diversity to distinguish between genuine and spoofed signals. However, the proposed algorithm requires the platform to be in motion, limiting its application to dynamic platforms such as vehicles [85]. Bhamidipati et al. explored the use of Chimera signals, which combine pseudorandom noise (PRN) codes from different satellites, to enhance navigation robustness. By implementing elastic filtering techniques during two consecutive Chimera cycles, they reduced navigation errors caused by spoofing interference during the transition period between cycles [86].
The integration of multiple anti-spoofing methods represents a promising strategy to enhance the resilience of GNSS systems against spoofing interference. Sun et al. refined the conventional SQM metrics and proposed a multi-parameter GNSS joint spoofing detection method based on spatio-temporal variational auto-encoders [87]. Their model demonstrated high precision in detecting unknown spoofing interference by utilizing a clean signal as a training dataset.
By combining techniques such as MEDLL/INS integration, robust Kalman filtering, RAIM, and antenna array-based detection, researchers have demonstrated significant improvements in spoofing detection and mitigation. These advancements not only improve navigation accuracy but also enhance the survivability of unmanned systems in adversarial environments. Future research should focus on optimizing these integrated approaches to address remaining challenges, such as reducing computational complexity and improving real-time performance.
4. Summary and Outlook
From the foregoing discussion, it is evident that while numerous methods exist for detecting spoofing attacks, they can broadly be categorized into two main approaches: (1) spoofing detection techniques based solely on satellite signals and (2) external-device-assisted spoofing detection methods, such as those incorporating INSs.
However, most existing anti-spoofing technologies are limited in their ability to not only detect spoofing but also recover accurate positioning and timing information. As spoofing techniques evolve, the initiation and execution of spoofing attacks become increasingly covert. For instance, tethered spoofing attacks adaptively generate deceptive signals based on the real-time position of the target receiver, causing the spoofed trajectory to change slowly relative to the receiver’s true trajectory. This slow variation avoids abrupt changes in position or velocity that could be detected by anti-spoofing algorithms. Consequently, the performance of existing GNSS/INS-based anti-spoofing algorithms diminishes in detecting such sophisticated spoofing attacks. Even if the presence of spoofing is detected, most anti-spoofing algorithms fail to suppress the deceptive signals or utilize authentic satellite signals effectively, resulting in degraded navigation continuity and precision. Furthermore, there is a paucity of research into intelligent anti-spoofing algorithms that integrate kinematic models of unmanned systems with multi-sensor fusion techniques.
The reliability of navigation systems for unmanned systems remains a complex challenge. Despite significant advancements in unmanned systems and navigation technology, the vulnerability of navigation systems to malicious interference and sensor malfunctions persists. This vulnerability is exacerbated by constraints related to SWaP and cost. To enhance the trustworthiness of navigation systems, the following trends and recommendations are proposed:
- (1)
- Regarding the development of low-cost GNSS spoofing detection techniques, research should focus on identifying spoofing attacks using affordable antenna arrays or signal-processing methods, enabling widespread adoption without compromising performance.
- (2)
- Techniques should be further combined with interference signals from array antennas and authentic satellite signals to carry out the identification and removal of deceptive interference signals.
- (3)
- Regarding robust combined navigation algorithms, researchers should investigate more resilient INS/GNSS integration algorithms capable of isolating the influence of corrupted GNSS signals while maintaining navigation accuracy and continuity. This could involve advanced filtering techniques or adaptive algorithms that account for external disturbances.
5. Conclusions
This paper has examined the critical role of navigation systems in unmanned applications and highlighted the vulnerabilities posed by GNSS attacks, including their classification and potential consequences. It has also reviewed existing solutions and strategies to counteract these threats and restore navigation information integrity. Looking ahead, the paper provides insights into future directions for enhancing the trustworthiness of navigation systems in unmanned applications. By addressing these challenges and exploring innovative solutions, it is possible to develop more resilient and reliable navigation systems capable of operating in adversarial environments.
Author Contributions
Writing—review and editing, P.J., X.G. and H.W.; resources, G.P.; supervision, B.L.; project administration, Z.N.; funding acquisition, Y.G. All authors have read and agreed to the published version of the manuscript.
Funding
This study was funded by National Natural Science Foundation of China, grant number 62103424.
Data Availability Statement
Not applicable.
DURC Statement
Current research is limited to the unmanned platform navigation technology field, which is beneficial to the improvement of accuracy and robustness of unmanned platform navigation system and does not pose a threat to public health or national security. Authors acknowledge the dual-use potential of the research involving GNSS anti-interference technologies and confirm that all necessary precautions have been taken to prevent potential misuse. As an ethical responsibility, authors strictly adhere to relevant national and international laws about DURC. Authors advocate for responsible deployment, ethical considerations, regulatory compliance, and transparent reporting to mitigate misuse risks and foster beneficial outcomes.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| GNSS | Global Navigation Satellite Systems |
| UAV | unmanned aerial vehicle |
| UGV | unmanned ground vehicle |
| USV | unmanned surface vessels |
| INS | Inertial Navigation Systems |
| CNR | carrier-to-noise ratio |
| SNR | signal-to-noise ratio |
| NMA | Navigation Message Authentication |
| SCA | Spectrum Code Authentication |
| OSMNA | Open Service Navigation Message Authentication |
| QZSS | Quasi-Zenith Satellite System |
| CHIMERA | Chip Message Robust Authentication |
| PRM | Received Power Monitoring |
| SQM | Signal Quality Monitoring |
| MEDLL | Multipath Estimating Delay Lock Loop |
| PD-ML | power-distortion maximum-likelihood |
| RAIM | Receiver autonomous integrity monitoring |
| DOA | direction-of-arrival |
| AOA | Angle-of-Arrival |
| CSAC | Chip-scale atomic clock |
| TCXO | temperature-compensated crystal oscillators |
| LSTM | Long Short-Term Memory |
| SSRL | Self-Supervised Deep Representation Learning |
| GRU | Gated Recurrent Unit |
| RNN | Recurrent Neural Network |
| DNN | Deep Neural Network |
| PRN | pseudorandom noise |
References
- Mousazadeh, H.; Jafarbiglu, H.; Abdolmaleki, H.; Omrani, E.; Monhaseri, F.; Abdollahzadeh, M.; Mohammadi-Aghdam, A.; Kiapei, A.; Salmani-Zakaria, Y.; Makhsoos, A. Developing a navigation, guidance and obstacle avoidance algorithm for an Unmanned Surface Vehicle (USV) by algorithms fusion. Ocean. Eng. 2018, 159, 56–65. [Google Scholar] [CrossRef]
- Wu, J.; Li, R.; Li, J.; Zou, M.; Huang, Z. Cooperative unmanned surface vehicles and unmanned aerial vehicles platform as a tool for coastal monitoring activities. Ocean Coast. Manag. 2023, 232, 106421. [Google Scholar] [CrossRef]
- Paull, L.; Saeedi, S.; Seto, M.; Li, H. AUV navigation and localization: A review. IEEE J. Ocean. Eng. 2014, 39, 131–149. [Google Scholar] [CrossRef]
- Shin, B.; Park, M.; Jeon, S.; So, H.; Kim, G.; Kee, C. Spoofing Attack Results Determination in Code Domain Using a Spoofing Process Equation. Sensors 2019, 19, 293. [Google Scholar] [CrossRef] [PubMed]
- Wu, Z.; Zhang, Y.; Yang, Y.; Liang, C.; Liu, R. Spoofing and Anti-Spoofing Technologies of Global Navigation Satellite System: A Survey. IEEE Access 2020, 8, 165444–165496. [Google Scholar] [CrossRef]
- Li, P.; Li, W.; Cui, Z.; Yang, P.; Chen, C.; You, B.; Wang, J. UGV Navigation in Complex Environment: An Approach Integrating Security Detection and Obstacle Avoidance Control. IEEE Trans. Intell. Veh. 2024, 1–14. [Google Scholar] [CrossRef]
- Dissanayaka, D.; Wanasinghe, T.R.; De Silva, O.; Jayasiri, A.; Mann, G.K.I. Review of Navigation Methods for UAV-Based Parcel Delivery. IEEE Trans. Autom. Sci. Eng. 2024, 21, 1068–1082. [Google Scholar] [CrossRef]
- Akhihiero, D.; Olawoye, U.; Das, S.; Gross, J. Cooperative Localization for GNSS-Denied Subterranean Navigation: A UAV–UGV Team Approach. Navig. J. Inst. Navig. 2024, 71, 677. [Google Scholar] [CrossRef]
- Bao, L.; Zhu, Y.; Cao, K.; Bao, L.; Zhu, Y.; Cao, K. Modeling and test on spoof jamming forBeidou navigation signal. J. Nav. Univ. Eng. 2019, 31, 23–27. [Google Scholar]
- Hu, Y.; Bian, S.; Li, B.; Zhou, L. A Novel Array-Based Spoofing and Jamming Suppression Method for GNSS Receiver. IEEE Sens. J. 2018, 18, 2952–2958. [Google Scholar] [CrossRef]
- Ni, S.; Ren, B.; Chen, F.; Gao, L.; Feng, X. Analysis of anti-spoofing performance of GNSS multi-beam anti-jamming receiver. J. Natl. Univ. Def. Technol. 2023, 45, 87–94. [Google Scholar]
- Razgūnas, M.; Rudys, S.; Aleksiejūnas, R. GNSS 2 × 2 antenna array with beamforming for multipath detection. Adv. Space Res. 2023, 71, 4142–4154. [Google Scholar] [CrossRef]
- Lee, Y.; Yeom, J.S.; Noh, J.H.; Lee, S.J.; Jung, B.C. A Novel GNSS Spoofing Detection Technique with Array Antenna-Based Multi-PRN Diversity. J. Position. Navig. Timing 2021, 10, 169–177. [Google Scholar]
- He, L.; Li, H.L.T.E.; Lu, M. Dual-antenna GNSS spoofing detection method based on Doppler frequency difference of arrival. Gps Solut. 2019, 23, 78. [Google Scholar] [CrossRef]
- Magiera, J. A Multi-Antenna Scheme for Early Detection and Mitigation of Intermediate GNSS Spoofing. Sensors 2019, 19, 2411. [Google Scholar] [CrossRef]
- Daneshmand, S.; Jafarnia-Jahromi, A.; Broumandan, A. GNSS Spoofing Mitigation in Multipath Environments Using Space-Time Processing. In Proceedings of the 2013 European Navigation Conference (ENC 2013), Vienna, Austria, 23–25 April 2013. [Google Scholar]
- Zhang, J.; Cui, X.; Xu, H.; Lu, M. A Two-Stage Interference Suppression Scheme Based on Antenna Array for GNSS Jamming and Spoofing. Sensors 2019, 19, 3870. [Google Scholar] [CrossRef]
- Broumandan, A.; Jafarnia-Jahromi, A.; Dehghanian, V.; Nielsen, J.; Lachapelle, G. GNSS spoofing detection in handheld receivers based on signal spatial correlation. In Proceedings of the 2012 IEEE/ION Position, Location and Navigation Symposium, Myrtle Beach, SC, USA, 23–26 April 2012; pp. 479–487. [Google Scholar]
- Montgomery, P.Y.; Humphreys, T.E.; Ledvin, B.M. Receiver-Autonomous Spoofing Detection: Experimental Results of a Multi-antenna Receiver Defense Against a Portable Civil GPS Spoofer. In Proceedings of the Institute of Navigation 2009 International Technical Meeting (ITM 2009), Anoheim, CA, USA, 26–28 January 2009. [Google Scholar]
- Paonni, J.T.C.A. Securing GNSS: An End-to-end Feasibility Analysis for the Galileo Open-service. In Proceedings of the 27th International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2014), Tampa, FL, USA, 8–12 September 2014. [Google Scholar]
- Gkougkas, E.; Pany, T.; Eissfeller, B. Sensitivity Analysis of Potential Future Authentication Components for Open Service GNSS Signals. In Proceedings of the 31st International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2018), Miami, FL, USA, 24–28 September 2018. [Google Scholar]
- Chen, X.; Luo, R.; Liu, T.; Yuan, H.; Wu, H. Satellite Navigation Signal Authentication in GNSS: A Survey on Technology Evolution, Status, and Perspective for BDS. Remote Sens. 2023, 15, 1462. [Google Scholar] [CrossRef]
- Manandhar, D.; Shibasaki, R. GNSS Signal Authentication using QZSS Signal and Evaluation of Key Performance Indicators. In Proceedings of the 2023 International Technical Meeting of The Institute of Navigation, ITM 2023, Long Beach, CA, USA, 27–30 January 2023. [Google Scholar]
- Pravin, P. Navigation Message Authentication (NMA) for NavIC SPS; ICG-16: Abu Dhabi, United Arab Emirates, 2022. [Google Scholar]
- Mina, T.; Kanhere, A.; Shetty, A.; Gao, G. GPS Spoofing-Resilient Filtering Using Self-Contained Sensors and Chimera Signal Enhancement. Navig. (Inst. Navig.) 2024, 71, navi.636. [Google Scholar] [CrossRef]
- Mina, T.; Kanhere, A.; Kousik, S.; Gao, G. Stochastic Reachability-Based GPS Spoofing Detection with Chimera Signal Enhancement. Navig. J. Inst. Navig. 2023, 70, 616. [Google Scholar] [CrossRef]
- EU. Document Subject to Terms of Use and Disclaimers OSNMA Receiver Guidelines; Issue 1.3.; EU: Brussels, Belgium, 2024.
- Nicola, M.; Motella, B.; Gamba, M.T. The Chimera Solution: Performance Assessment; German Institute of Navigation—DGON: Bonn, Germany, 2020; pp. 1–10. [Google Scholar]
- Li, S.; Tang, X.; Lin, H.; Wang, F. GNSS spoofing detection based on frequency domain processing. Measurement 2025, 242, 115872. [Google Scholar] [CrossRef]
- Kazim, S.A. Enhancing Jamming Resilience in GNSS-Based Localization for Safety-Critical Land Transportation: Towards an Optimized Mitigation Approach Focusing User Requirements; Université Gustave Eiffel: Champs-sur-Marne, France, 2024. [Google Scholar]
- Scott, L. Interference: Origins, Effects, and Mitigation. In Position, Navigation, and Timing Technologies in the 21st Century; Wiley: Hoboken, NJ, USA, 2020; pp. 619–653. [Google Scholar]
- Dehghanian, V.; Nielsen, J.; Lachapelle, G. GNSS Spoofing Detection based on Receiver C/N0 Estimates. In Proceedings of the Proceedings of the 25th International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS 2012), Nashville, TN, USA, 17–21 September 2012; pp. 2875–2884. [Google Scholar]
- Deng, M.; Wang, H.; Ming, D.; Chen, Y. GNSS Spoofing Detection Based on Abnormal Receiver Noise and Carrier-to-Noise Ratio Metric. In Proceedings of the 2022 IEEE 22nd International Conference on Communication Technology (ICCT), Nanjing, China, 11–14 November 2022. [Google Scholar]
- Ghizzo, E.; Djelloul, E.; Lesouple, J.; Milner, C.; Macabiau, C. Assessing jamming and spoofing impacts on GNSS receivers: Automatic gain control (AGC). Signal Process 2025, 228, 109762. [Google Scholar] [CrossRef]
- Akos, D.M. Who’s afraid of the spoofer? GPS/GNSS spoofing detection via automatic gain control (agc). Navig. J. Inst. Navig. 2012, 59, 281–290. [Google Scholar] [CrossRef]
- Blum, R.; Dütsch, N.; Stoeber, C.; Dampf, J.; Pany, T. New and existing signal quality monitoring metrics tested against simulations and time synchronized signal generator attacks. In Proceedings of the 33rd International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2020), Online, 21–25 September 2020; pp. 3835–3853. [Google Scholar]
- Yanfeng, H.; Shaofeng, B.; Kejin, C.; Bing, J. GNSS spoofing detection based on new signal quality assessment model. GPS Solut. 2018, 22, 28. [Google Scholar]
- Maoyou, L.; Xu, L.; Ziyang, M.; Zheng, Y. GNSS spoofing detection for single antenna receivers via CNR variation monitoring. J. Syst. Eng. Electron. 2024, 35, 1276–1286. [Google Scholar]
- Wesson, K.D.; Gross, J.N.; Humphreys, T.E.; Evans, B.L. GNSS Signal Authentication Via Power and Distortion Monitoring. IEEE Trans. Aerosp. Electron. Syst. 2018, 54, 739–754. [Google Scholar] [CrossRef]
- Wang, Z.; Li, H.; Wen, J.; Lu, M. GNSS Spoofing Discrimination Method Based on Doppler Frequency Double Difference for Multiple Independent Moving Receivers. In Proceedings of the Institute of Navigation International Technical Meeting, San Diego, CA, USA, 27–30 January 2025. [Google Scholar]
- Shuli, D.; Taotao, Z.; Min, L. A GNSS Anti-Spoofing Technology Based on Power Detection. In Proceedings of the 2019 IEEE 8th Joint International Information Technology and Artificial Intelligence Conference (ITAIC), Chongqing, China, 24–26 May 2019. [Google Scholar]
- Li, H.; Hong, L.; Mingquan, L. Global navigation satellite system spoofing-detection technique based on the Doppler ripple caused by vertical reciprocating motion. IET Radar Sonar Navig. 2019, 13, 1655–1664. [Google Scholar] [CrossRef]
- Yang, B.; Tian, M.; Ji, Y.; Cheng, J.; Xie, Z.; Shao, S. Research on GNSS Spoofing Mitigation Technology Based on Spoofing Correlation Peak Cancellation. IEEE Commun. Lett. 2022, 26, 3024–3028. [Google Scholar] [CrossRef]
- Li, J.; Zhu, X.; Ouyang, M.; Li, W.; Chen, Z.; Dai, Z. Research on multi-peak detection of small delay spoofing signal. IEEE Access 2020, 8, 151777–151787. [Google Scholar] [CrossRef]
- van Nee, R.D.J.; Siereveld, J.; Engineer, I.O.E.A. The multipath estimating delay lock loop: Approaching theoretical accuracy limits. In Proceedings of the 1994 IEEE Position, Location and Navigation Symposium—PLANS’94, Las Vegas, NV, USA, 11–15 April 1994. [Google Scholar]
- Blanco-Delgado, N.; Nunes, F.D. Multipath Estimation in Multicorrelator GNSS Receivers using the Maximum Likelihood Principle. IEEE Trans. Aerosp. Electron. Syst. 2012, 48, 3222–3233. [Google Scholar] [CrossRef]
- Gross, J.N.; Kilic, C.; Humphreys, T.E. Maximum-Likelihood Power-Distortion Monitoring for GNSS-Signal Authentication. IEEE Trans. Aerosp. Electron. Syst. 2019, 55, 469–475. [Google Scholar] [CrossRef]
- Guo, Y.; Miao, L.; Zhang, X. Spoofing detection and mitigation in a multi-correlator gps receiver based on the maximum likelihood principle. Sensors 2019, 19, 37. [Google Scholar] [CrossRef] [PubMed]
- Wei, Y.; Li, H.; Peng, C.; Lu, M. Time Domain Differential RAIM Method for Spoofing Detection Applications. In Proceedings of the 10th China Satellite Navigation Conference (CSNC), Beijing, China, 22–25 May 2019; Sun, J., Yang, C., Yang, Y., Eds.; Springer: Singapore, 2019; Volume 563, pp. 606–614. [Google Scholar]
- Li, J.; Li, H.; Peng, C.; Wen, J.; Lu, M. Research on the random traversal RAIM method for anti-spoofing applications. In Proceedings of the 10th China Satellite Navigation Annual Conference, Beijing, China, 22–25 May 2019. [Google Scholar]
- Kuusniemi, H.; Blanch, J.; Chen, Y.; Lo, S.; Innac, A.; Ferrara, G.; Honkala, S.; Bhuiyan, M.Z.H.; Thombre, S.; Söderholm, S.; et al. Feasibility of Fault Exclusion Related to Advanced RAIM for GNSS Spoofing Detection. In Proceedings of the 30th International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2017), Portland, OR, USA, 25–29 September 2017. [Google Scholar]
- Moafipoor, S.; Bock, L.; Fayman, J.A. Resilient Sensor Management for Dismounted Assured-PNT. In Proceedings of the Institute of Navigation International Technical Meeting, San Diego, CA, USA, 21–24 January 2020. [Google Scholar]
- Liu, Y.; Li, S.; Fu, Q.; Liu, Z. Impact Assessment of GNSS Spoofing Attacks on INS/GNSS Integrated Navigation System. Sensors 2018, 18, 1433. [Google Scholar] [CrossRef] [PubMed]
- Liu, Y.; Li, S.; Fu, Q.; Liu, Z.; Zhou, Q. Analysis of Kalman Filter Innovation-Based GNSS Spoofing Detection Method for INS/GNSS Integrated Navigation System. IEEE Sens. J. 2019, 19, 5167–5178. [Google Scholar] [CrossRef]
- Yimin, W.; Hong, L.; Mingquan, L. Spoofing profile estimation-based GNSS spoofing identification method for tightly coupled MEMS INS/GNSS integrated navigation system. IET Radar Sonar Navig. 2020, 14, 216–225. [Google Scholar] [CrossRef]
- Ke, Y.; Lv, Z.; Zhang, C.; Deng, X.; Zhou, W.; Song, D. Tightly Coupled GNSS/INS Integration Spoofing Detection Algorithm Based on Innovation Rate Optimization and Robust Estimation. IEEE Access 2022, 10, 72444–72457. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, H.; Sun, C.; Bai, L.; Feng, W. Enhanced GNSS Spoofing Detector via Multiple-Epoch Inertial Navigation Sensor Prediction in a Tightly-Coupled System. IEEE Sens. J. 2022, 22, 8633–8647. [Google Scholar] [CrossRef]
- Tanil, C.; Khanafseh, S.; Joerger, M.; Pervan, B. An INS Monitor to Detect GNSS Spoofers Capable of Tracking Vehicle Position. IEEE Trans. Aerosp. Electron. Syst. 2018, 54, 131–143. [Google Scholar] [CrossRef]
- Song, J.; Wu, H.; Guo, X.; Li, S.; Gong, Y.; Zhang, Y.; Li, Y. Credible Navigation Algorithm for GNSS Attack Detection Using Auxiliary Sensor System. Appl. Sci. 2021, 11, 6321. [Google Scholar] [CrossRef]
- Ceccato, M.; Formaggio, F.; Laurenti, N.; Tomasin, S. Generalized Likelihood Ratio Test for GNSS Spoofing Detection in Devices With IMU. IEEE Trans. Inf. Forensic Secur. 2021, 16, 3496–3509. [Google Scholar] [CrossRef]
- Zhong, L.; Liu, J.; Li, R.; Wang, R. Approach for Detecting Soft Faults in GPS/INS Integrated Navigation based on LS-SVM and AIME. J. Navig. 2017, 70, 561–579. [Google Scholar] [CrossRef]
- Zhang, C.; Zhao, X.; Pang, C.; Wang, Y.; Zhang, L.; Feng, B. Improved Fault Detection Method Based on Robust Estimation and Sliding Window Test for INS/GNSS Integration. J. Navig. 2020, 73, 776–796. [Google Scholar] [CrossRef]
- Wei, Y.; Li, H.; Lu, M. A Steady-State Spoofing Detection and Exclusion Method Based on Raw IMU Measurement. IEEE Sens. J. 2022, 22, 3529–3539. [Google Scholar] [CrossRef]
- Liu, Y.; Li, S.; Fu, Q.; Zhou, Q. Chip-scale atomic clock aided INS/GNSS integrated navigation system spoofing detection method. J. Chin. Inert. Technol. 2019, 27, 654–660. [Google Scholar]
- Hu, Y.; Cao, K.; Bian, S.; Li, B.; Ye, X. GNSS spoofing detection algorithm based on clock frequency drift monitoring. Xi Tong Gong. Cheng Yu Dian Zi Ji Shu 2015, 37, 1629–1632. [Google Scholar]
- Varshosaz, M.; Afary, A.; Mojaradi, B.; Saadatseresht, M.; Ghanbari Parmehr, E. Spoofing Detection of Civilian UAVs Using Visual Odometry. ISPRS Int. J. Geo-Inf. 2020, 9, 6. [Google Scholar] [CrossRef]
- Sowah, R.A.; Ofori-Amanfo, K.B.; Mills, G.A.; Koumadi, K.M. Detection and Prevention of Man-in-the-Middle Spoofing Attacks in MANETs Using Predictive Techniques in Artificial Neural Networks (ANN). J. Comput. Netw. Commun. 2019, 2019, 4683982. [Google Scholar] [CrossRef]
- AL-Syouf, R.A.; AL-Jarrah, R.M.B.O. Machine learning approaches to intrusion detection in unmanned aerial vehicles (UAVs). Neural Comput. Appl. 2024, 36, 18009–18041. [Google Scholar] [CrossRef]
- Manesh, M.R.; Kenney, J.; Hu, W.C.; Devabhaktuni, V.K.; Kaabouch, N. Detection of GPS Spoofing Attacks on Unmanned Aerial Systems. In Proceedings of the 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2018. [Google Scholar]
- Liang, C.; Miao, M.; Ma, J.; Yan, H.; Zhang, Q.; Li, X.; Li, T. Detection of GPS Spoofing Attack on Unmanned Aerial Vehicle System. In Machine Learning for Cyber Security; Springer: Cham, Switzerland, 2019; pp. 123–139. [Google Scholar]
- Korium, M.S.; Saber, M.; Ahmed, A.M.; Narayanan, A.; Nardelli, P.H.J. Image-based intrusion detection system for GPS spoofing cyberattacks in unmanned aerial vehicles. Ad. Hoc. Netw. 2024, 163, 103597. [Google Scholar] [CrossRef]
- Talaei Khoei, T.; Ismail, S.; Shamaileh, K.A.; Devabhaktuni, V.K.; Kaabouch, N. Impact of Dataset and Model Parameters on Machine Learning Performance for the Detection of GPS Spoofing Attacks on Unmanned Aerial Vehicles. Appl. Sci. 2023, 13, 383. [Google Scholar] [CrossRef]
- Alanazi, A. SSRL-UAVs: A Self-Supervised Deep Representation Learning Approach for GPS Spoofing Attack Detection in Small Unmanned Aerial Vehicles. Drones 2024, 8, 515. [Google Scholar] [CrossRef]
- Rustamov, A.; Gogoi, N.; Minetto, A.; Dovis, F.; Inst, N. GNSS Anti-Spoofing Defense Based on Cooperative Positioning. In Proceedings of the 33rd International Technical Meeting of the Satellite-Division-of-The-Institute-of-Navigation (ION GNSS), Online, 21–25 September 2020; pp. 3326–3337. [Google Scholar]
- Li, Z.; Xu, J.; Guo, Q. Cooperative Location Method of Muti-UAV System under Environment of Communication Jamming based on Tri-Layer Trust Model. In Proceedings of the 2018 IEEE 4th Information Technology and Mechatronics Engineering Conference (ITOEC), Chongqing, China, 14–16 December 2018; p. 108112. [Google Scholar]
- Sun, J.; Yang, C.; Guo, S. A Cooperative Anti-spoofing Technology Based on Subspace Projection. In Proceedings of the China Satellite Navigation Conference (CSNC) 2018 Proceedings, Harbin, China, 23–25 May 2018; Sun, J., Yang, C., Guo, S., Eds.; Springer Singapore Pte. Limited: Singapore, 2018; Volume 498, pp. 91–100. [Google Scholar]
- Yan, Z.; Chen, X.; Tang, X.; Ruotsalainen, L. A Novel Carrier Loop Based on Adaptive LM-QN Method in GNSS Receivers. IEEE Trans. Veh. Technol. 2022, 71, 5259–5271. [Google Scholar] [CrossRef]
- Wang, Y.; Sun, F.; Wang, X.; Hao, J.; Xiao, K. Full-domain collaborative deployment method of multiple interference sources and evaluation of its deployment effect. Def. Technol. 2023, 2, 572–595. [Google Scholar] [CrossRef]
- Xu, R.; Ding, M.Y.; Meng, Q.; Liu, J.Y. Spoofing interference identification technique of MEDLL aided GNSS/INS system. J. Chin. Inert. Technol. 2018, 26, 223–230. [Google Scholar]
- Shang, X.; Sun, F.; Zhang, L.; Wang, D.; Ke, Y. INS aided GNSS spoofing identification and suppression method. J. Chin. Inert. Technol. 2022, 30, 181–187. [Google Scholar]
- Shang, X.; Sun, F.; Liu, B.; Zhang, L.; Cui, J. GNSS Spoofing Mitigation With a Multicorrelator Estimator in the Tightly Coupled INS/GNSS Integration. EEE Trans. Instrum. Meas. 2023, 72, 1–12. [Google Scholar] [CrossRef]
- Islam, S.; Bhuiyan, M.Z.H.; Paakkonen, I.; Saajasto, M.; Makela, M.; Kaasalainen, S. Impact analysis of spoofing on different-grade GNSS receivers. In Proceedings of the 2023 IEEE/ION Position, Location and Navigation Symposium (PLANS), Monterey, CA, USA, 24–27 April 2023; pp. 492–499. [Google Scholar]
- Gioia, C.; Borio, D. Multi-layered Multi-Constellation Global Navigation Satellite System Interference Mitigation. Navig. J. Inst. Navig. 2023, 70, 596. [Google Scholar] [CrossRef]
- Vagle, N.; Broumandan, A.; Lachapelle, G. Multiantenna GNSS and Inertial Sensors/Odometer Coupling for Robust Vehicular Navigation. IEEE Internet Things J. 2018, 5, 4816–4828. [Google Scholar] [CrossRef]
- Fan, G.; Huang, Y.; Wu, W.; Zhu, X.; Sun, G. Detection of spoofing threats by inertial assisted three elements antenna. J. Natl. Univ. Def. Technol. 2017, 39, 91–95. [Google Scholar]
- Bhamidipati, S.; Gao, G. GPS Spoofing Mitigation and Timing Risk Analysis in Networked Phasor Measurement Units via Stochastic Reachability. Navig. J. Inst. Navig. 2023, 70, 574. [Google Scholar] [CrossRef]
- Sun, P.; Xiong, H.; Shah, D.H.; Liu, Y.; Zhou, B. Multi-Parameter Joint GNSS Spoofing Detection Based on TSVAE. IEEE Trans. Aerosp. Electron. Syst. 2024, 61, 3373–3386. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).