Exploiting Cascaded Channel Signature for PHY-Layer Authentication in RIS-Enabled UAV Communication Systems
Abstract
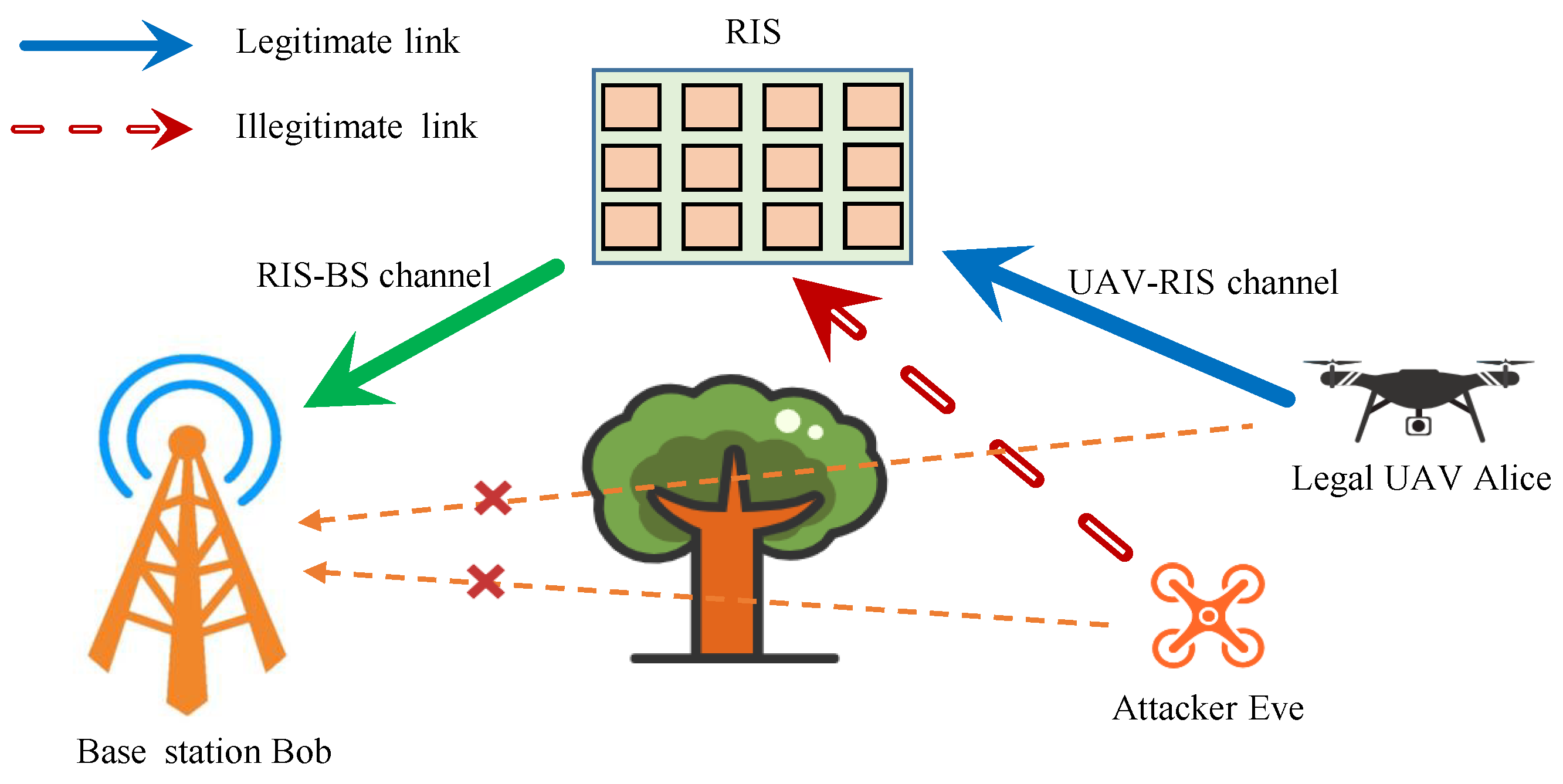
1. Introduction
1.1. Background
1.2. Related Work
1.3. Motivation and Contribution
- By leveraging the location-specific cascaded channel features’ user equipment (UE) RIS and RIS base station (BS), we propose a novel physical layer authentication scheme for RIS-enabled UAV wireless communication systems.
- Using the first-order Gauss–Markov process, we model the time-varying complicated cascaded channels involved in RIS. With the help of the coordinated descent-based estimation algorithm and least squares estimation algorithm, we fulfill the estimation of time-varying complicated cascaded channels.
- Based on a 1-bit quantizer, we exploit the extracted channel features to establish authentication verification under the framework of the hypothesis testing framework. The performance of our proposed authentication scheme is analytically evaluated by deriving the typical performance metrics, including false alarm and detection probabilities, and establishing the statistical performance analytically.
- Through extensive simulations, we verify the correctness of the theoretical models of the two probabilities. Simulation results further show how the system parameters can affect the statistical authentication performance.
2. System Model and Problem Formulation
3. Proposed PHY-Layer Authentication Scheme
3.1. Estimation of the Cascaded Channel
3.2. Channel Quantization
3.3. Authentication Decision
4. Modeling of Performance Metrics
4.1. Probability of Quantizer Output 1 under Each Hypothesis
4.2. False Alarm and Detection Probabilities
4.3. Computational Complexity
5. Evaluation
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Liu, Y.; Liu, X.; Mu, X.; Hou, T.; Xu, J.; Di Renzo, M.; Al-Dhahir, N. Reconfigurable intelligent surfaces: Principles and opportunities. IEEE Commun. Surv. Tutor. 2021, 23, 1546–1577. [Google Scholar] [CrossRef]
- Jian, M.; Alexandropoulos, G.C.; Basar, E.; Huang, C.; Liu, R.; Liu, Y.; Yuen, C. Reconfigurable intelligent surfaces for wireless communications: Overview of hardware designs, channel models, and estimation techniques. Intell. Converg. Netw. 2022, 3, 1–32. [Google Scholar] [CrossRef]
- Zhou, S.; Xu, W.; Wang, K.; Di Renzo, M.; Alouini, M.S. Spectral and energy efficiency of IRS-assisted MISO communication with hardware impairments. IEEE Wirel. Commun. Lett. 2020, 9, 1366–1369. [Google Scholar] [CrossRef]
- Alexandropoulos, G.C.; Shlezinger, N.; Del Hougne, P. Reconfigurable intelligent surfaces for rich scattering wireless communications: Recent experiments, challenges, and opportunities. IEEE Commun. Mag. 2021, 59, 28–34. [Google Scholar] [CrossRef]
- You, C.; Kang, Z.; Zeng, Y.; Zhang, R. Enabling Smart Reflection in Integrated Air-Ground Wireless Network: IRS Meets UAV. IEEE Wirel. Commun. 2021, 28, 138–144. [Google Scholar] [CrossRef]
- Mohsan, S.A.H.; Khan, M.A.; Alsharif, M.H.; Uthansakul, P.; Solyman, A.A.A. Intelligent Reflecting Surfaces Assisted UAV Communications for Massive Networks: Current Trends, Challenges, and Research Directions. Sensors 2022, 22, 5278. [Google Scholar] [CrossRef] [PubMed]
- Cicek, C.T.; Gultekin, H.; Tavli, B.; Yanikomeroglu, H. UAV Base Station Location Optimization for Next Generation Wireless Networks: Overview and Future Research Directions. In Proceedings of the 2019 1st International Conference on Unmanned Vehicle Systems-Oman (UVS), Muscat, Oman, 5–7 February 2019; pp. 1–6. [Google Scholar]
- Tarekegn, G.B.; Juang, R.; Lin, H.; Munaye, Y.Y.; Wang, L.; Bitew, M.A. Deep-Reinforcement-Learning-Based Drone Base Station Deployment for Wireless Communication Services. IEEE Internet Things J. 2022, 9, 21899–21915. [Google Scholar] [CrossRef]
- Khawaja, W.; Güvenç, I.; Matolak, D.W.; Fiebig, U.; Schneckenburger, N. A Survey of Air-to-Ground Propagation Channel Modeling for Unmanned Aerial Vehicles. IEEE Commun. Surv. Tutor. 2019, 21, 2361–2391. [Google Scholar] [CrossRef]
- Tarekegn, G.B.; Juang, R.; Lin, H.; Munaye, Y.Y.; Wang, L.; Jeng, S. Channel Quality Estimation in 3D Drone Base Station for Future Wireless Network. In Proceedings of the 30th Wireless and Optical Communications Conference, WOCC 2021, Taipei, Taiwan, 7–8 October 2021; pp. 236–239. [Google Scholar]
- Mahmood, A.; Vu, T.X.; Khan, W.U.; Chatzinotas, S.; Ottersten, B.E. Optimizing Computational and Communication Resources for MEC Network Empowered UAV-RIS Communication. In Proceedings of the IEEE Globecom 2022 Workshops, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 974–979. [Google Scholar]
- Li, N.; Li, X.; Yan, Y.; Sun, Q.; Han, Y.; Cheng, K. Joint Communication and Computing Resource Optimization for Collaborative AI Inference in Mobile Networks. In Proceedings of the 2023 IEEE 98th Vehicular Technology Conference (VTC2023-Fall), Hongkong, China, 10–13 October 2023; pp. 1–5. [Google Scholar]
- Bansal, A.; Agrawal, N.; Singh, K.; Li, C.P.; Mumtaz, S. RIS Selection Scheme for UAV-Based Multi-RIS-Aided Multiuser Downlink Network With Imperfect and Outdated CSI. IEEE Trans. Commun. 2023, 71, 4650–4664. [Google Scholar] [CrossRef]
- Liu, X.; Liu, Y.; Chen, Y. Machine Learning Empowered Trajectory and Passive Beamforming Design in UAV-RIS Wireless Networks. IEEE J. Sel. Areas Commun. 2021, 39, 2042–2055. [Google Scholar] [CrossRef]
- Zhang, J.; Woods, R.F.; Sandell, M.; Valkama, M.; Marshall, A.; Cavallaro, J.R. Radio Frequency Fingerprint Identification for Narrowband Systems, Modelling and Classification. IEEE Trans. Inf. Forensics Secur. 2021, 16, 3974–3987. [Google Scholar] [CrossRef]
- Wang, N.; Jiao, L.; Wang, P.; Li, W.; Zeng, K. Machine learning-based spoofing attack detection in mmWave 60GHz IEEE 802.11ad Networks. In Proceedings of the 39th IEEE Conference on Computer Communications, INFOCOM 2020, Toronto, ON, Canada, 6–9 July 2020; pp. 2579–2588. [Google Scholar]
- Xu, J.; Wei, D. Polarization Fingerprint-Based LoRaWAN Physical Layer Authentication. IEEE Trans. Inf. Forensics Secur. 2023, 18, 4593–4608. [Google Scholar] [CrossRef]
- Wang, N.; Li, W.; Jiao, L.; Alipour-Fanid, A.; Xiang, T.; Zeng, K. Orientation and channel-independent RF fingerprinting for 5G IEEE 802.11 ad devices. IEEE Internet Things J. 2021, 9, 9036–9048. [Google Scholar] [CrossRef]
- Xiao, L.; Greenstein, L.J.; Mandayam, N.B.; Trappe, W. Using the physical layer for wireless authentication in time-variant channels. IEEE Trans. Wirel. Commun. 2008, 7, 2571–2579. [Google Scholar] [CrossRef]
- Liu, J.; Wang, X. Physical layer authentication enhancement using two-dimensional channel quantization. IEEE Trans. Wirel. Commun. 2016, 15, 4171–4182. [Google Scholar] [CrossRef]
- Zhang, P.; Shen, Y.; Jiang, X.; Wu, B. Physical Layer Authentication Jointly Utilizing Channel and Phase Noise in MIMO Systems. IEEE Trans. Commun. 2020, 68, 2446–2458. [Google Scholar] [CrossRef]
- Xie, N.; Chen, J.; Huang, L. Physical-layer authentication using multiple channel-based features. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2356–2366. [Google Scholar] [CrossRef]
- Jing, T.; Huang, H.; Gao, Q.; Wu, Y.; Huo, Y.; Wang, Y. Multi-User Physical Layer Authentication Based on CSI Using ResNet in Mobile IIoT. IEEE Trans. Inf. Forensics Secur. 2024, 19, 1896–1907. [Google Scholar] [CrossRef]
- Tang, J.; Xu, A.; Jiang, Y.; Zhang, Y.; Wen, H.; Zhang, T. MmWave MIMO physical layer authentication by using channel sparsity. In Proceedings of the 2020 IEEE International Conference on Artificial Intelligence and Information Systems (ICAIIS), Dalian, China, 20–22 March 2020; pp. 221–224. [Google Scholar]
- Wu, Y.; Wei, D.; Guo, C.; Huang, W. Physical Layer Authentication Based on Channel Polarization Response in Dual-Polarized Antenna Communication Systems. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2144–2159. [Google Scholar] [CrossRef]
- Tang, W.; Dai, J.Y.; Chen, M.Z.; Wong, K.K.; Li, X.; Zhao, X.; Jin, S.; Cheng, Q.; Cui, T.J. MIMO transmission through reconfigurable intelligent surface: System design, analysis, and implementation. IEEE J. Sel. Areas Commun. 2020, 38, 2683–2699. [Google Scholar] [CrossRef]
- Wu, X.; Ma, S.; Yang, X. Tensor-based low-complexity channel estimation for mmWave massive MIMO-OTFS systems. J. Commun. Inf. Netw. 2020, 5, 324–334. [Google Scholar] [CrossRef]
- Zhang, R.; Cheng, L.; Wang, S.; Lou, Y.; Gao, Y.; Wu, W.; Ng, D.W.K. Integrated Sensing and Communication with Massive MIMO: A Unified Tensor Approach for Channel and Target Parameter Estimation. IEEE Trans. Wirel. Commun. 2024. Early Access. [Google Scholar]
- Wang, Z.; Liu, L.; Cui, S. Channel estimation for intelligent reflecting surface assisted multiuser communications: Framework, algorithms, and analysis. IEEE Trans. Wirel. Commun. 2020, 19, 6607–6620. [Google Scholar] [CrossRef]
- Alwazani, H.; Kammoun, A.; Chaaban, A.; Debbah, M.; Alouini, M.S. Intelligent reflecting surface-assisted multi-user MISO communication: Channel estimation and beamforming design. IEEE Open J. Commun. Soc. 2020, 1, 661–680. [Google Scholar]
- Ardah, K.; Gherekhloo, S.; de Almeida, A.L.; Haardt, M. TRICE: A channel estimation framework for RIS-aided millimeter-wave MIMO systems. IEEE Signal Process. Lett. 2021, 28, 513–517. [Google Scholar] [CrossRef]
- Ji, Z.; Yeoh, P.L.; Zhang, D.; Chen, G.; Zhang, Y.; He, Z.; Yin, H.; Li, Y. Secret key generation for intelligent reflecting surface assisted wireless communication networks. IEEE Trans. Veh. Technol. 2021, 70, 1030–1034. [Google Scholar] [CrossRef]
- Ji, Z.; Yeoh, P.L.; Chen, G.; Pan, C.; Zhang, Y.; He, Z.; Yin, H.; Li, Y. Random shifting intelligent reflecting surface for OTP encrypted data transmission. IEEE Wirel. Commun. Lett. 2021, 10, 1192–1196. [Google Scholar] [CrossRef]
- Hu, C.; Dai, L.; Han, S.; Wang, X. Two-timescale channel estimation for reconfigurable intelligent surface aided wireless communications. IEEE Trans. Commun. 2021, 69, 7736–7747. [Google Scholar] [CrossRef]
- Badiu, M.A.; Coon, J.P. Communication through a large reflecting surface with phase errors. IEEE Wirel. Commun. Lett. 2019, 9, 184–188. [Google Scholar] [CrossRef]
- Khel, A.M.T.; Hamdi, K.A. Effects of hardware impairments on IRS-enabled MISO wireless communication systems. IEEE Commun. Lett. 2021, 26, 259–263. [Google Scholar] [CrossRef]
- Özdogan, Ö.; Björnson, E.; Larsson, E.G. Intelligent Reflecting Surfaces: Physics, Propagation, and Pathloss Modeling. IEEE Wirel. Commun. Lett. 2020, 9, 581–585. [Google Scholar] [CrossRef]
- Jakes, W.C.; Cox, D.C. Microwave Mobile Communications; Wiley: Hoboken, NJ, USA, 1994. [Google Scholar]
- Masmoudi, A.; Le-Ngoc, T. Channel estimation and self-interference cancelation in full-duplex communication systems. IEEE Trans. Veh. Technol. 2016, 66, 321–334. [Google Scholar] [CrossRef]
- Jensen, T.L.; De Carvalho, E. An optimal channel estimation scheme for intelligent reflecting surfaces based on a minimum variance unbiased estimator. In Proceedings of the ICASSP 2020-2020 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Barcelona, Spain, 4–8 May 2020; pp. 5000–5004. [Google Scholar]
- Guo, H.; Lau, V.K.N. Uplink cascaded channel estimation for intelligent reflecting surface assisted multiuser MISO systems. IEEE Trans. Signal Process. 2022, 70, 3964–3977. [Google Scholar] [CrossRef]
- Björnson, E.; Sanguinetti, L. Rayleigh fading modeling and channel hardening for reconfigurable intelligent surfaces. IEEE Wirel. Commun. Lett. 2020, 10, 830–834. [Google Scholar] [CrossRef]







| References | Authentication Parameters | Application Scenario |
|---|---|---|
| [15] | CFO, IQ imbalance, and PA nonlinearities | IoT systems |
| [16] | SNR trace feature | mmWave systems |
| [17] | polarization fingerprint | LoRaWAN |
| [19] | channel frequency response | MIMO systems |
| [20] | channel impulse response | mobile MIMO scenario |
| [21] | channel gain and phase noise | MIMO systems |
| [26] | channel sparsity | mmWave systems |
| Our scheme | cascaded channel gain | RIS-UAV communication systems |
| Symbols | Description |
|---|---|
| // | Conjugate/conjugate transpose/transpose operators. |
| ⊙ | Hadamard product. |
| Absolute value operator. | |
| Pr(·) | Probability operator. |
| ≜ | Definition. |
| A diagonal matrix with vector . | |
| The vectorization of the matrix . | |
| The RIS-UAV channel with being the ith channel component. | |
| The channel for BS-RIS. | |
| The coefficient of the reflecting elements on RIS. | |
| The normalized maximum Doppler frequency. | |
| v | The mobile speed of UAV. |
| /c/ | Carrier frequency/speed of light/sampling interval. |
| Zero-order Bessel function of the first kind. | |
| Correlation coefficient for the UAV(Alice/Eve)-RIS channel. | |
| Signal power. | |
| The reflection coefficient vector of RIS in the t-th subframe. | |
| A/E | Alice/Eve. |
| A predefined threshold. | |
| The output of the quantizer of the subcascaded channel. | |
| The current signal originates from Alice/Eve. | |
| Z | The judgment threshold in the hypothesis testing. |
| The square of the difference between the current cascaded channel at time k and the previous one at time . | |
| Exponential function. | |
| The false alarm probabilities/the detection probabilities. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qin, C.; Niu, M.; Zhang, P.; He, J. Exploiting Cascaded Channel Signature for PHY-Layer Authentication in RIS-Enabled UAV Communication Systems. Drones 2024, 8, 358. https://doi.org/10.3390/drones8080358
Qin C, Niu M, Zhang P, He J. Exploiting Cascaded Channel Signature for PHY-Layer Authentication in RIS-Enabled UAV Communication Systems. Drones. 2024; 8(8):358. https://doi.org/10.3390/drones8080358
Chicago/Turabian StyleQin, Changjian, Mu Niu, Pinchang Zhang, and Ji He. 2024. "Exploiting Cascaded Channel Signature for PHY-Layer Authentication in RIS-Enabled UAV Communication Systems" Drones 8, no. 8: 358. https://doi.org/10.3390/drones8080358
APA StyleQin, C., Niu, M., Zhang, P., & He, J. (2024). Exploiting Cascaded Channel Signature for PHY-Layer Authentication in RIS-Enabled UAV Communication Systems. Drones, 8(8), 358. https://doi.org/10.3390/drones8080358








