Abstract
Utilizing unmanned aerial vehicles (UAVs) as mobile access points or base stations has emerged as a promising solution to address the excessive traffic demands in wireless networks. This paper investigates improving the detector performance at the unmanned aerial vehicle base stations (UAV-BSs) in an uplink grant-free non-orthogonal multiple access (GF-NOMA) system by considering the activity state (AS) temporal correlation of the different user equipments (UEs) in the time domain. The Bernoulli Gaussian-Markov chain (BG-MC) probability model is used for exploiting both the sparsity and slow change characteristic of the AS of the UE. The GAMP Bernoulli Gaussian-Markov chain (GAMP-BG-MC) algorithm is proposed to improve the detector performance, which can utilize the bidirectional message passing between the neighboring time slots to fully exploit the temporally correlated AS of the UE. Furthermore, the parameters of the BG-MC model can be updated adaptively during the estimation procedure with unknown system statistics. Simulation results show that the proposed algorithm can improve the detection accuracy compared to existing methods while keeping the same order complexity.
1. Introduction
Recently, unmanned aerial vehicle (UAV) assisted communications, such as UAV base stations (UAV-BSs), have garnered significant research interest for their ability to provide rapid and widespread connectivity [1,2,3]. The UAV-BS system can offer a cost-effective and innovative solution to managing fluctuating traffic demands, especially in scenarios where traditional infrastructure-based base stations, which are expensive and slow to deploy, are not financially viable. The UAV-BS can be a data collector for sensor networks in remote or restricted areas [4]. Additionally, it can function as an emergency BS when existing ones fail due to natural disasters or become overwhelmed by sudden surges in traffic [5,6]. However, the large number of potential user equipments (UEs) makes UAV-BS communication difficult and complicated.
Currently, grant-free non-orthogonal multiple access (GF-NOMA) is a promising candidate to support UAV-BS communications. The non-orthogonal multiple access (NOMA) technique enables the system resource block to simultaneously serve multiple UEs [7,8]. At the same time, the grant-free (GF) scheme allows UEs to transmit data to the UAV-BS directly without waiting for its permission, which can decrease the access delay and reduce the control overhead for coordination [9]. In the case of applying GF-NOMA to uplink, recovering the transmitted signal through designing efficient multi-UEs detection methods is challenging, not only due to the large number of UEs present in the cell but also because they are randomly accessing the network in each access slot. However, UEs are only sporadically and randomly activated in practical massive machine-type communications (mMTC) systems, which brings sparsity of the transmitted slots in the time-frequency resource grid [10], which can be changed across different slots within a single frame [11,12]. Furthermore, once a UE is activated for performing the data transmission, it typically requires several consecutive time slots. Then, this UE will be deactivated for a certain period until the next transmission. This activation and deactivation is denoted as activity state (AS), and it exhibits a temporal correlation [13]. Consequently, to enhance the performance of the detectors in a GF-NOMA system, the existing methods incorporate not only the exploitation of sparsity but also the temporal correlation information provided by AS.
According to the literature of GF-NOMA, detectors based on message passing (MP) algorithms [12,13,14] have a better performance compared to conventional compressed sensing (CS) methods. In [12], the authors exploited the temporal correlation of the active UE and modeled it by a Markov process. The authors in [13] utilized the sparse Basianyes learing (SBL) and pattern coupled sparse Basianyes learing (PCSBL) models to formulate the slow change of the UEs AS, then proposed the SBL-based multi-UEs detection algorithms, outperforming CS methods. Then, [14] further embedded the generalized approximate message passing (GAMP) algorithm with the SBL and PCSBL models, and proposed the GAMP sparse Basianyes learing (GAMP-SBL) and the GAMP pattern coupled sparse Basianyes learing (GAMP-PCSBL) detector algorithms, which can reduce the complexity. However, the SBL and PCSBL models mainly consider the sparse structure of the UE activity. Motivated by [12], we find that the Markov chain (MC) better captures the slow change of the AS features with successive time slots and the active UE sparsity simultaneously. Furthermore, differing from [12], the hybrid message passing (HMP) rule [15] is used to update the parameters of the MC on the factor graph (FG) to improve the convergence speed.
This paper focuses on designing a high-performance MP algorithm, resulting in the GAMP-BG-MC detector algorithm for the UAV-BS-based uplink GF-NOMA system. The main contributions of this paper are summarized as follows.
- The BG-MC model is employed to jointly exploit both the sparse structure of the active UE and the slow change feature in consecutive time slots of the AS. Indeed, the performance of the UAV-BS detector can be improved by updating the AS while considering the temporal correlation. Hence, both the forward messages from the previous slot and the backward messages from the next slot are considered in the MP algorithm at each iteration.
- Making use of the HMP rule, the GAMP-BG-MC algorithm is proposed to detect the UAV-BS received signal of multiple superimposed UEs. The proposed GAMP-BG-MC algorithm not only calculates the more accurate posterior probability density function (PDF) of the transmitted signal but also adaptively learns the parameters of the prior model during the estimation procedure. Simulation results show that the GAMP-BG-MC algorithm has a better signal-to-noise ratio (SNR) performance as compared to the GAMP-SBL [13,14] and the GAMP-PCSBL [14] algorithms, respectively, while keeping the complexity.
The remaining parts of this paper are organized as follows. Section 2 introduces the system model of the UAV-based uplink GF-NOMA network. Section 3 proposes the GAMP-BG-MC algorithm as the adaptive UAV-BS detector. Then, the numerical results of the proposed algorithm are given in Section 4. Finally, the conclusions of this paper are presented in Section 5.
Notation: Boldface lowercase and uppercase letters denote vectors and matrices; and denote transposition and conjugation, respectively. The expectation of a function w.r.t. a PDF is expressed as ; denotes x following a complex Gaussian distribution with mean and variance v. is the Dirac delta function.
2. System Model and Factor Graph
2.1. System Model
A typical GF-NOMA system is considered [14], where the UAV-BS is equipped with a single antenna. K potential single-antenna UEs under the service area of a UAV-BS perform GF-NOMA random access (RA), sharing the same bandwidth resource and transmitting signals to the UAV-BS, as illustrated in Figure 1. The transmission is assumed to utilize the multi-carrie code division multiple access (MC-CDMA) scheme detailed in [16], which belongs to the NOMA techniques. The MC-CDMA is a hybrid scheme combing code division multiple access (CDMA) and orthogonal frequency-division multiplexing (OFDM), making the MC-CDMA signal tolerant against frequency selective channels, inter-symbol interference (ISI), and inter-carrier interference (ICI) through the use of cyclic prefix and equalization [17]. The uplink transmission of the UEs is multiplexed over N frequency-divided subcarriers. In each time slot, the ASs of different UEs are assumed to be independent of each other, of which are active and transmit packets to the BS. The active rate is used to indicate the percentage of active UEs. The active UE k sends the complex symbol from a predefined complex signal constellation and spreads it over the N sub-carriers. Meanwhile, the inactive UE is considered to be transmitting a zero symbol . The received signal at the BS for the j-th time slot can be expressed as
where denotes the complex channel response matrix, representing the spread codes of K UEs over N sub-carriers. is the transmitted signal from K UEs. denotes the additive white Gaussian noise (AWGN) with the variance . The received signals span J continuous time slots and are represented as a multiple measurement vector (MMV) model, [14]
where denotes the transmitted signal matrix and the noise is . In a practical mMTC scenario, the potential UEs keep their AS in some random consecutive time slots within the entire frame [10]. As shown in Figure 1, the AS of the UE exhibits a temporal correlation in the time domain, which promotes the sparse structure of signal in (2). The task of multi-UEs detection is to estimate the sparse transmitted signal from the received signal with the unknown UE activity value.
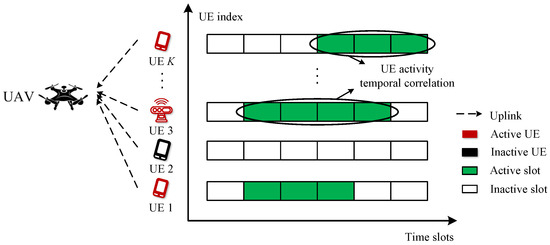
Figure 1.
The left part of the figure denotes the uplink transmission from UEs to the base station (BS). The right part of the figure indicates the sparse and temporally correlated structures of the transmit signal .
2.2. Probabilistic Formulation
From (2), the hidden variable is defined, where . Then, the detector transfer function can be written as
The conditional PDF can be further factorized as
The hard constraint factors provided by can be concretely represented as
where denotes the element in the n-th row and k-th column of .
For the channel prior model, the BG-MC probability model [18] is utilized, which can exploit both the block sparse structure and the slow change of the UE AS feature simultaneously. Each element has a conditionally independent distribution given by
where denotes the MC state implicating if the UE is active () or inactive () at the j time slot; is a non-negative hyperparameter controlling the sparsity of the transmitted signal .
Similar to [12,18,19], the stationary first-order MC is employed to effectively capture the slow evolution of UE AS across time slots. The MC here is given by
with the initial probability given by , and the transition probability is expressed as
The MC is characterized by parameters and for different UEs. Differing from [12,18], the parameters are considered as variables, with the prior given by the Beta distributions
where , and can control the initial values of and , respectively. Meanwhile, the precision term can be modeled as the Gamma distribution [20], i.e.,
where the initial values of are controlled by the parameters . The main assumptions considered in the system model are summarized in Table 1.

Table 1.
Main Considered Assumptions.
2.3. Factor Graph Representation
Based on (2) and (4)–(10), the joint PDF of all unknown variables given by the observation can be factorized as
The factor graph of (11) is illustrated in Figure 2. In addition, local functions and their corresponding distributions are shown in Table 2. The novel MP algorithm is designed in the next Section.
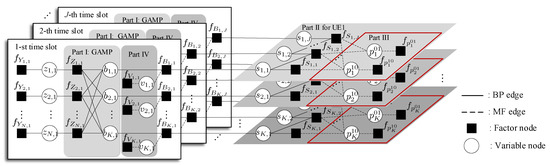
Figure 2.
Factor graph representation for UAV-BS-based GF-NOMA detectors.

Table 2.
Functions of the factor nodes in Figure 2.
3. Adaptive UAV-BS Detector Based on the HMP Rule
In this section, the efficient GAMP algorithm is utilized to obtain the likelihood function for the signal . The novel GAMP-BG-MC algorithm is proposed, which can adaptively update the parameters and obtain the accurate marginal posterior PDF.
3.1. Computation of the HMP for GAMP-BG-MC Algorithm
The probability model in (6) is implicit in the mix of linear and non-linear functional relationships, i.e., the product and summation operations among the variables as well as the updating of the Gaussian variance, while the single or combined MP rules are unavailable to calculate all the messages directly. Fortunately, the HMP rule proposed in [15] can tackle the message computation problems with the mix of linear and nonlinear models. The idea of the HMP rule [15] is that the FG groups all factor nodes into one set, , while clustering all edges, , into two sets, and , depicted as solid and dashed lines in Figure 2, respectively. For edges, the messages use the equations (Equations (5) and (6) in [15]) to calculate the messages. Consequently, Equations (7)–(9) in [15] are used to calculate the messages on the . For the convenience of MP algorithm design, the factor graph is divided into four parts, as shown in Figure 2. Part I is the GAMP algorithm to calculate the likelihood function and Part II denotes the MC part for each UE in the time domain. Then, the transition probability automatic update is Part III, and Part IV is used to update the Gaussian variance. Then, the message calculation procedure will be derived separately.
3.1.1. Part I GAMP Part Messages
The GAMP algorithm is used to obtain the likelihood messages of the variable based on the received signal . The detailed scheme of the GAMP algorithm [21] is summarized in Algorithm 1. In Algorithm 1, the input message is and the output message is obtained after one iteration. At the beginning of Algorithm 1, the belief expectation and variance of the variable , denoted as , are first initialized. These values will be updated during the following iterations. In Algorithm 1, lines 1–2, the symbols denote the expectation and variance of the message , respectively. In addition, denotes an intermediate variable, which will be updated during the iteration. Finally, Algorithm 1 outputs the message , as shown in lines 4–5.
| Algorithm 1: GAMP algorithm |
Input: Received signal , channel matrix Output: Initialize: // Update right output messages:
// Update left output messages:
|
3.1.2. Part II MC Part Messages
Firstly, the beliefs and can be initialized, and the parameters are updated later in (26). The MC downward messages are obtained by the HMP rule (Equations (5) and (6) in [15]) as
where
where denote the constants and are defined as
where .
3.1.3. Part III Transition Probability Update Part
Given the prior messages and , the beliefs update by and , where the parameters are updated through
and the parameters can be calculated in Equation (24).
3.1.4. Part IV Variance Update Part
The message going out of the MC part from to can be computed by Equation (6) in [15].
where
To update the variance of the BG-MC channel prior distribution, the combined beliefs have to be calculated first using Equation (8) in [15] as
where
and the temporary variable is defined in (13).
Given the prior message , the belief of variance variable can be expressed as , where the parameters are updated through
With the parameters updated in (32), the message from the factor node to the variable node can be computed by the HMP rule (Equation (5) in [15]) as
Finally, the belief of the variable can be expressed as
with the parameter . Then, the algorithm outputs the mean and variance of the belief as
3.2. Message Passing Scheduling
The message passing scheme was summarized in the proposed GAMP-BG-MC algorithm, as shown in Algorithm 2. Specifically, the Part I messages are first calculated in parallel at each time slot, as shown in Section 3.1.1, which contains Algorithm 1 and the message going into the Part II. Then, the MC messages can be calculated in sequence in lines 4–7. In Part III, the parameters of can be updated in lines 8–10. After that, the accuracy of the outgoing messages in Part IV can be improved by updating the MC part messages, again based on the updated hyperparameters . In the final step, the parameters of variance and the calculated output estimated data are updated with lines 12–15 in Part IV.
| Algorithm 2: GAMP-BG-MC algorithm |
 |
4. Simulation Results
This section compares the performance of the proposed GAMP-BG-MC algorithm. As a benchmark, we consider the state-of-the-art algorithms GAMP-SBL [13,14] and GAMP-PCSBL [14], referred to as SBL and PCSBL in the following. Referring to [14], the BPSK modulation scheme is employed in all simulations. To ensure the reproducibility of the results, the simulation setup is described as follows. The simulations were conducted using MATLAB as the programming language, utilizing its built-in functions for matrix operations and signal processing. The parameters used in the experiments are summarized in Table 3. The experiments are conducted in two scenarios compared with the benchmark algorithms. One is the UE activity with temporal correlation, i.e., the UE will transmit the data partially during the whole frame, here denoted as “Partial”. The other is an extreme phenomenon where the UE keeps transmitting data fully to the frame, referred to as “Full”.

Table 3.
Parameter settings for the experiment.
For the initialization, according to [15], the prior parameters are , , , and the belief parameters are initialized with the same values of the priors. All the experiments are obtained by averaging Monte Carlo realizations. The experiments use the symbol error rate (SER), defined as , as a performance metric; is the number of UE whose symbol is erroneously decoded. The per-iteration complexity of the BG-MC is , and it is in the same order as the SBL and PCSBL. However, the iteration number of the BG-MC will always be small, as shown in Figure 3.
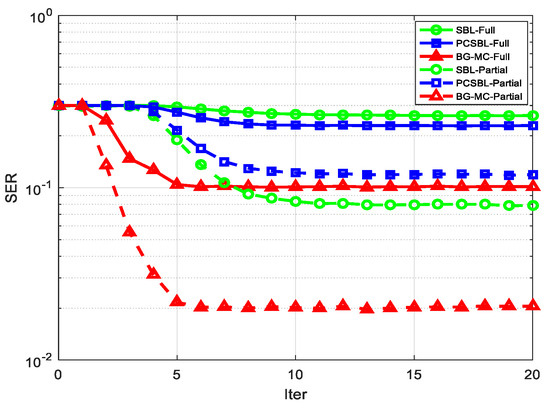
Figure 3.
SER vs. Iteration with .
Figure 3 gives the convergence speed of the three algorithms under SNR = 9 dB, with two scenarios. The proposed BG-MC algorithm has the fastest convergence speed compared with the SBL and PCSBL algorithms in both scenarios, which demonstrates that the proposed algorithm can capture the AS correlation more accurately than the other two algorithms. Especially in the “Partial” scenario, the proposed algorithm converges faster and performs better than the comparison algorithm.
In Figure 4, the simulations compare the average SER performance as a function of the SNRs. The simulation results show that the BG-MC algorithm performs better in the two scenarios. Further, the results show that the PCSBL is better than the SBL in the second scheme and the PCSBL is efficient in characterizing the block sparse structure, while the BG-MC is more accurate, not only in the block sparse structure but also in the cluster sparse structure. The reason for this is that the BG-MC can update the statistic parameters automatically, which is suitable for the practice system.
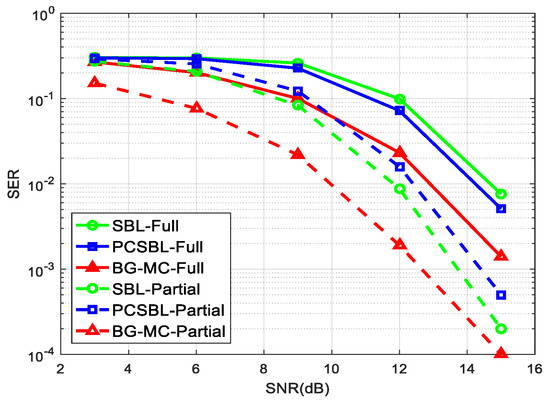
Figure 4.
SER vs. SNR with .
Figure 5 shows the SER performances as a function of the UE active rate under SNR = 9 dB. The BG-MC algorithm outperforms the benchmark algorithms in almost all ranges of , especially in the first scenario, which validates the effectiveness of the proposed algorithm.
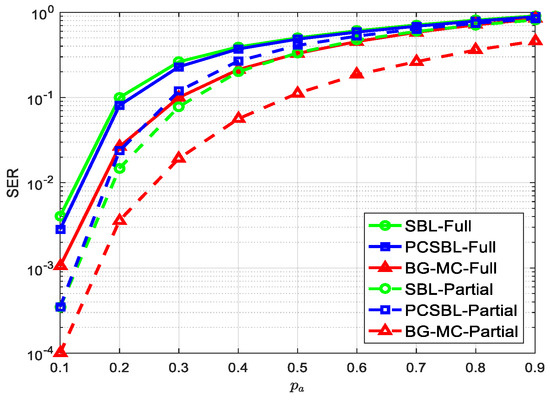
Figure 5.
SER vs. with dB.
5. Conclusions
This work proposed an uplink GF-NOMA message-passing detector for UAV-assisted communications. The BG-MC model was first developed to accurately characterize the slow change feature of the AS of all UEs under a GF-NOMA system. Based on the HMP rule, this work designed the GAMP-BG-MC algorithm and tested it with the two scenarios. Numerical results demonstrated that the proposed algorithm not only has a faster convergence speed but also achieves a better SER performance.
In future work, it will be interesting to investigate the impact of channel fading on the multi-user symbol detection in UAV-based GF-NOMA systems, while considering a comprehensive channel model for UAV communication and developing robust detection algorithms that can adapt to varying channel conditions in UAV communication scenarios.
Author Contributions
Conceptualization, P.S. and Z.W.; methodology, Y.S.; software, Y.Z.; validation, Y.S., Y.Z. and X.L.; formal analysis, P.S.; investigation, Z.W.; writing—original draft preparation, Y.S. and K.C.-H.; writing—review and editing, K.C.-H.; funding acquisition, Z.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Science and Technology Research Project of Henan Province under Grants 242102211107; the Natural Science Foundation of China, Grant/Award Number: 61901417; the Natural Science Foundation of Henan, Grant/Award Number: 222300420504; Academic Degrees Graduate Education Reform Project of Henan Province, Grant/Award Number: 2021SJGLX262Y and 2023SJGLX370Y; Postgraduate Education Reform and Quality Improvement Project of Henan Province, Grant/Award Number: YJS2024AL141; Foundation and frontier project of Nanyang, Grant/Award Number: JCQY008.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Bor-Yaliniz, I.; Yanikomeroglu, H. The new Frontier in RAN heterogeneity: Multi-tier drone-cells. IEEE Commun. Mag. 2016, 54, 48–55. [Google Scholar] [CrossRef]
- Dapper e Silva, T.; Emygdio de Melo, C.F.; Cumino, P.; Rosário, D.; Cerqueira, E.; Pignaton de Freitas, E. STFANET: SDN-based topology management for flying Ad hoc network. IEEE Access 2019, 7, 173499–173514. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, H.; Zhao, H. An SDN framework for UAV backbone network towards knowledge centric networking. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018; pp. 456–461. [Google Scholar]
- Wang, Z.; Duan, L.; Zhang, R. Adaptive deployment for UAV-aided communication networks. IEEE Trans. Wirel. Commun. 2019, 18, 4531–4543. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Unmanned Aerial Vehicle with Underlaid Device-to-Device Communications: Performance and Tradeoffs. IEEE Trans. Wirel. Commun. 2016, 15, 3949–3963. [Google Scholar] [CrossRef]
- Seo, J.B.; Pack, S.; Jin, H. Uplink NOMA random access for UAV-assisted communications. IEEE Trans. Veh. Technol. 2019, 68, 8289–8293. [Google Scholar] [CrossRef]
- Dai, L.; Wang, B.; Yuan, Y.; Han, S.; Chih-lin, I.; Wang, Z. Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Commun. Mag. 2015, 53, 74–81. [Google Scholar] [CrossRef]
- Farajzadeh, A.; Ercetin, O.; Yanikomeroglu, H. UAV data collection over NOMA backscatter networks: UAV altitude and trajectory optimization. In Proceedings of the 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar]
- Liu, L.; Larsson, E.G.; Yu, W.; Popovski, P.; Stefanovic, C.; de Carvalho, E. Sparse Signal Processing for Grant-Free Massive Connectivity: A Future Paradigm for Random Access Protocols in the Internet of Things. IEEE Signal Proc. Mag. 2018, 35, 88–99. [Google Scholar] [CrossRef]
- Li, B.; Zheng, J.; Gao, Y. Compressed sensing based multiuser detection of grant-free NOMA with dynamic user activity. IEEE Commun. Lett. 2021, 26, 143–147. [Google Scholar] [CrossRef]
- Gao, Y.; Zheng, J.; Li, B. Multiuser detection of GF-NOMA with dynamic-active users and temporal-correlated channels. IEEE Commun. Lett. 2022, 26, 2380–2384. [Google Scholar] [CrossRef]
- Yuan, W.; Wu, N.; Guo, Q.; Ng, D.W.K.; Yuan, J.; Hanzo, L. Iterative joint channel estimation, user activity tracking, and data detection for FTN-NOMA systems supporting random access. IEEE Trans. Commun. 2020, 68, 2963–2977. [Google Scholar] [CrossRef]
- Zhang, X.; Fan, P.; Liu, J.; Hao, L. Bayesian learning-based multiuser detection for grant-free NOMA systems. IEEE Trans. Wirel. Commun. 2022, 21, 6317–6328. [Google Scholar] [CrossRef]
- Zhang, X.; Fan, P.; Li, H.; Quan, X. Generalized approximate message passing based Bayesian learning detectors for uplink grant-free NOMA. IEEE Trans. Veh. Technol. 2023, 72, 15057–15061. [Google Scholar] [CrossRef]
- Song, Y.; Zhang, C.; Lu, X.; Saggese, F.; Wang, Z. Hybrid message passing algorithm for downlink FDD massive MIMO-OFDM channel estimation. IEEE Trans. Wirel. Commun. 2023, 23, 4596–4609. [Google Scholar] [CrossRef]
- Frison, C.I.; Mora, H.R.C.; de Almeida, C. MC-CDMA and SCMA performance and complexity comparison in overloaded scenarios. In Proceedings of the 2019 IEEE Colombian Conference on Communications and Computing (COLCOM), Barranquilla, Colombia, 5–7 June 2019; pp. 1–6. [Google Scholar]
- Carvajal Mora, H.R.; Garzón, N.V.O.; de Almeida, C. Mean bit error rate evaluation of MC-CDMA cellular systems employing multiuser-maximum-likelihood detector. IEEE Trans. Veh. Technol. 2017, 66, 9838–9851. [Google Scholar] [CrossRef]
- Kuai, X.; Chen, L.; Yuan, X.; Liu, A. Structured turbo compressed sensing for downlink massive MIMO-OFDM channel estimation. IEEE Trans. Wirel. Commun. 2019, 18, 3813–3826. [Google Scholar] [CrossRef]
- Zhu, W.; Tao, M.; Yuan, X.; Guan, Y. Message Passing-Based Joint User Activity Detection and Channel Estimation for Temporally Correlated Massive Access. IEEE Trans. Commun. 2023, 71, 3576–3591. [Google Scholar] [CrossRef]
- Pedersen, N.L.; Manchón, C.N.; Shutin, D.; Fleury, B.H. Application of Bayesian hierarchical prior modeling to sparse channel estimation. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 3487–3492. [Google Scholar]
- Mo, L.; Lu, X.; Yuan, J.; Zhang, C.; Wang, Z.; Popovski, P. Generalized Unitary Approximate Message Passing for Double Linear Transformation Model. IEEE Trans. Signal Process. 2023, 71, 1524–1538. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).