Cooperative Target Fencing Control for Unmanned Aerial Vehicle Swarm with Collision, Obstacle Avoidance, and Connectivity Maintenance
Abstract
1. Introduction
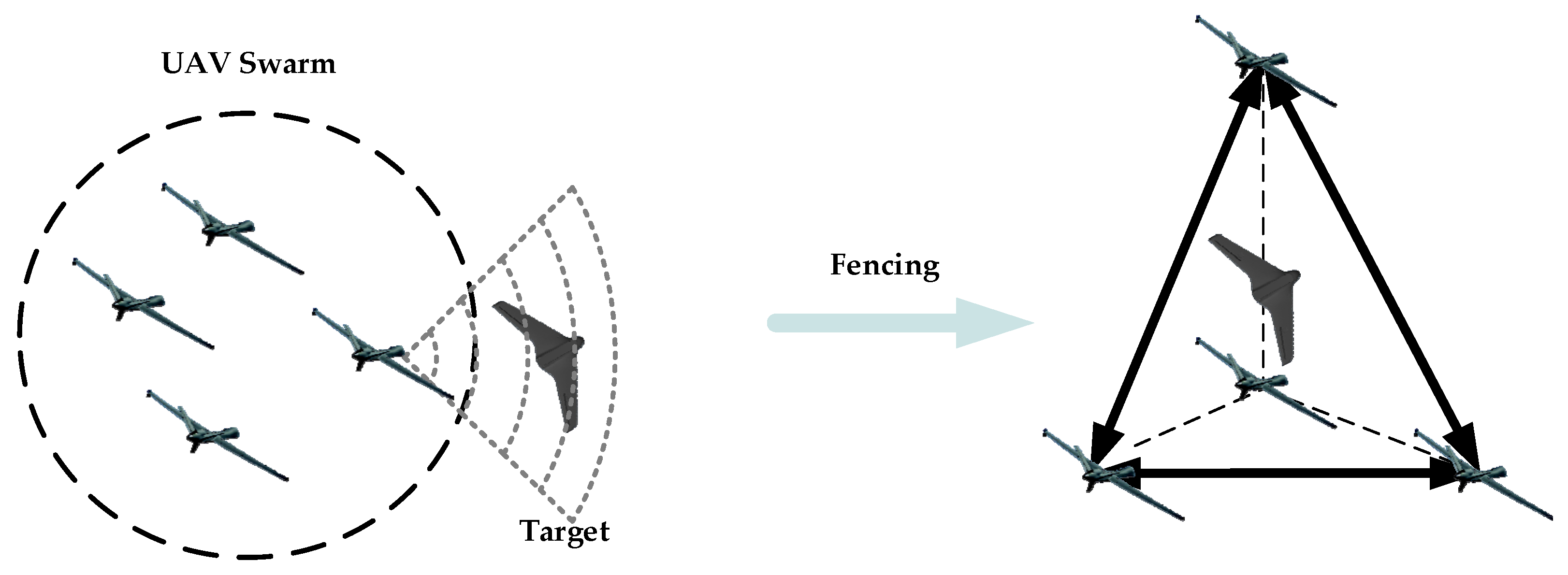
- A distributed cooperative fencing control scheme for UAV swarms is proposed, comprising a target state observer and a distributed cooperative fencing controller. Compared with most existing fencing or containment schemes [12,13,14,15], the proposed control strategy directly fences a target instead of forming a formation based on preset orientations or distances and subsequently guiding the swarm around it.
- Different from [18], which primarily focuses on defining the separation and attraction rules, we further improve the swarm self-organized behaviors during the process of fencing a target. Within a dynamic network topology, collision, obstacle avoidance, and connectivity maintenance control mechanisms are introduced for the swarm based on local interaction information, ensuring effective target fencing in complex environments while meeting security requirements.
2. Problem Formulation
2.1. Modeling of UAV Swarm
2.2. Dynamic Communication Topology
2.3. Control Objective
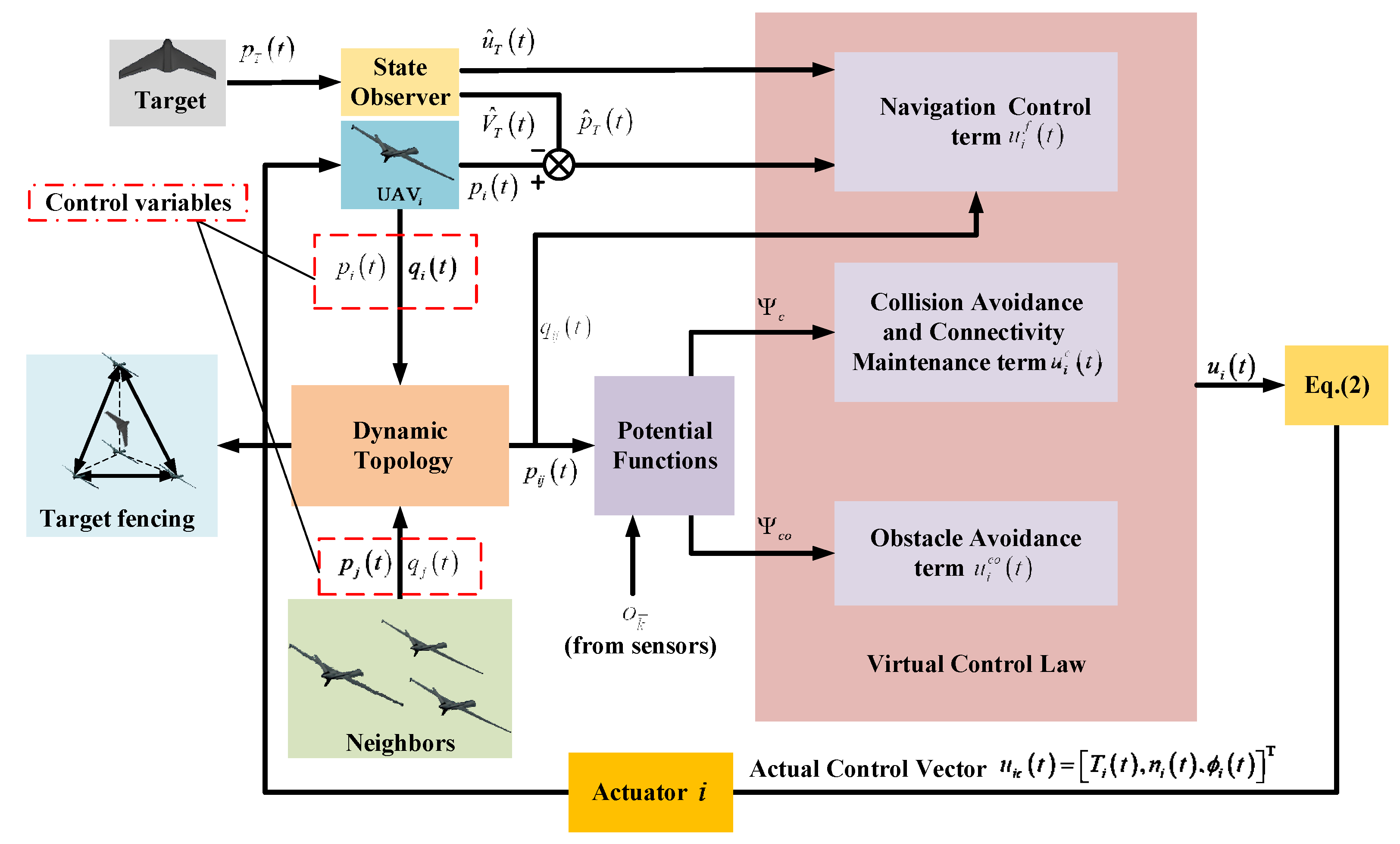
3. Main Results
3.1. Differential State Observer
3.2. Cooperative Fencing Controller
3.2.1. Navigation Control Term
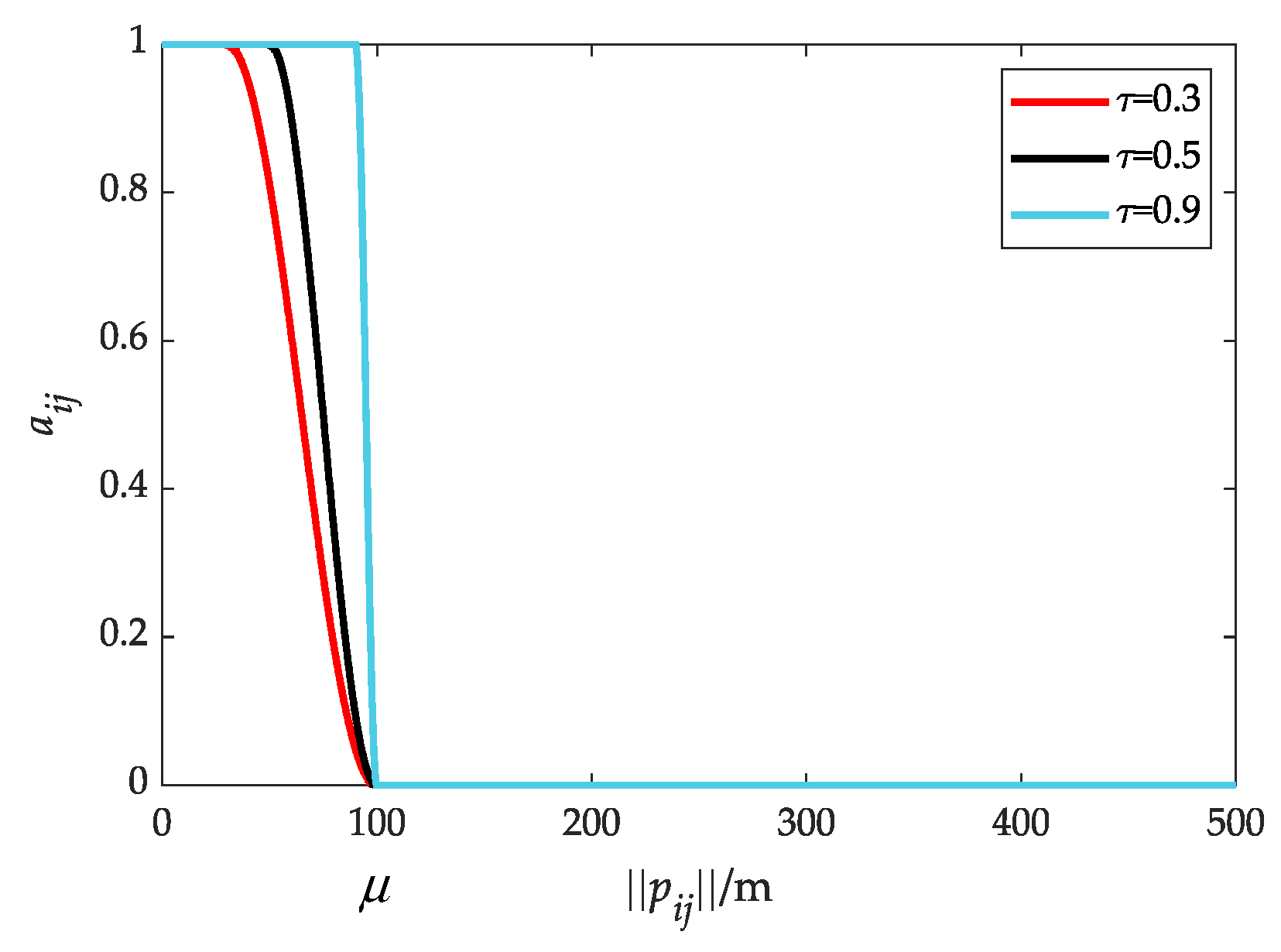
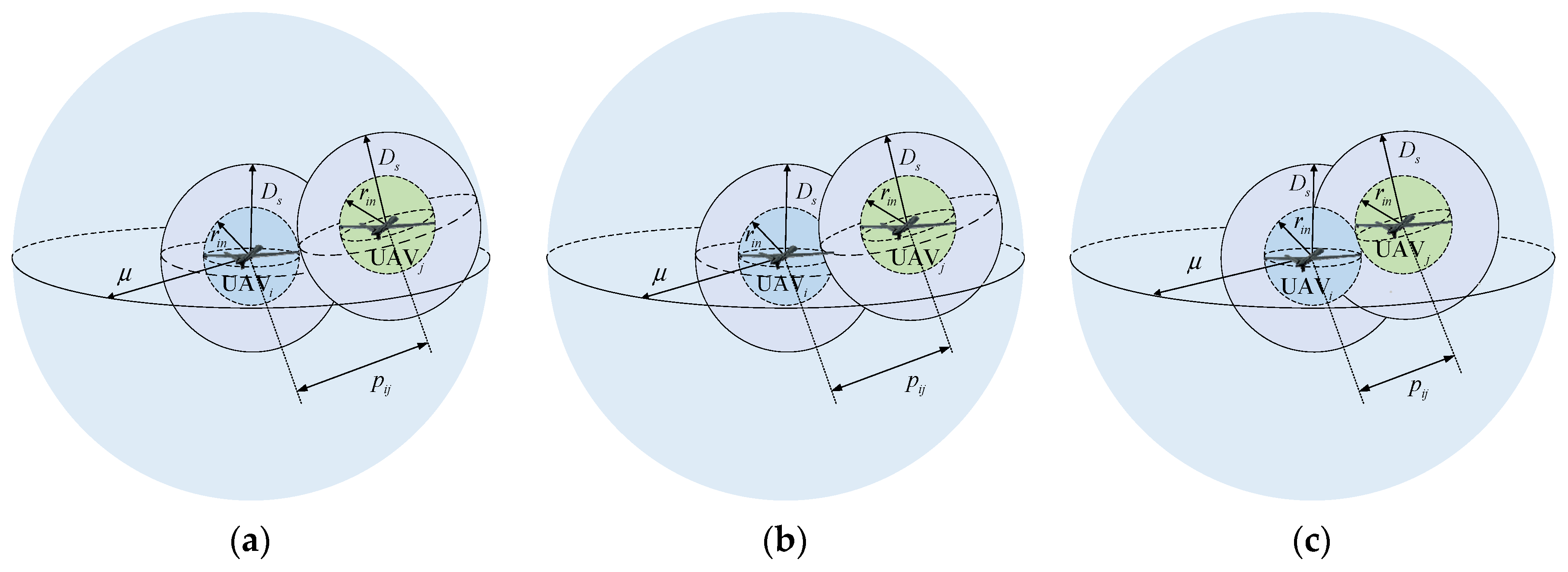
3.2.2. Collision Avoidance and Connectivity Maintenance Term
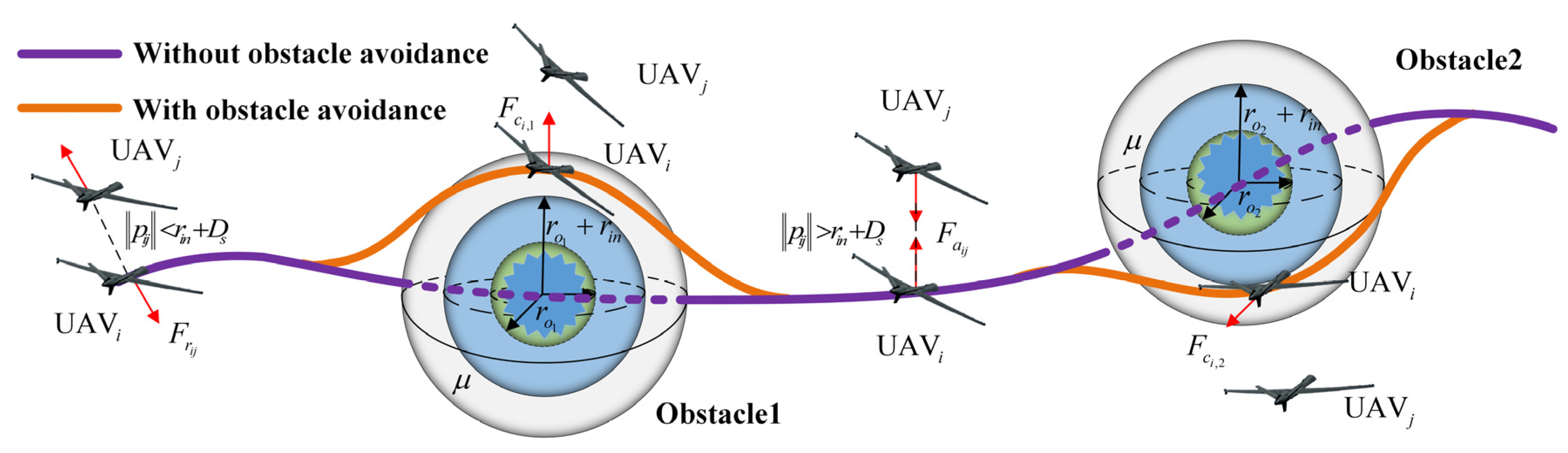
3.2.3. Obstacle Avoidance Term
3.3. Stability Analysis
4. Numerical Simulation
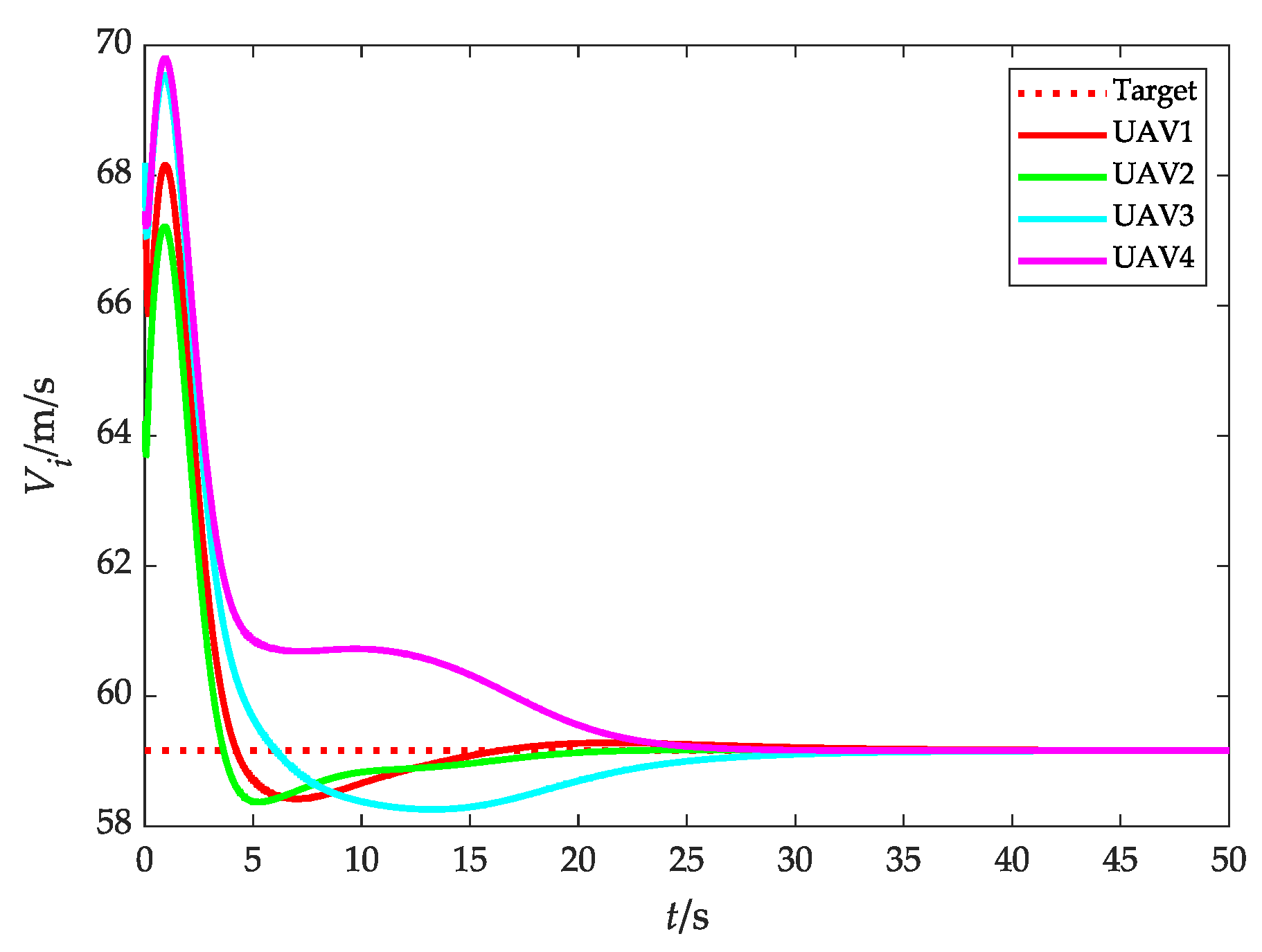
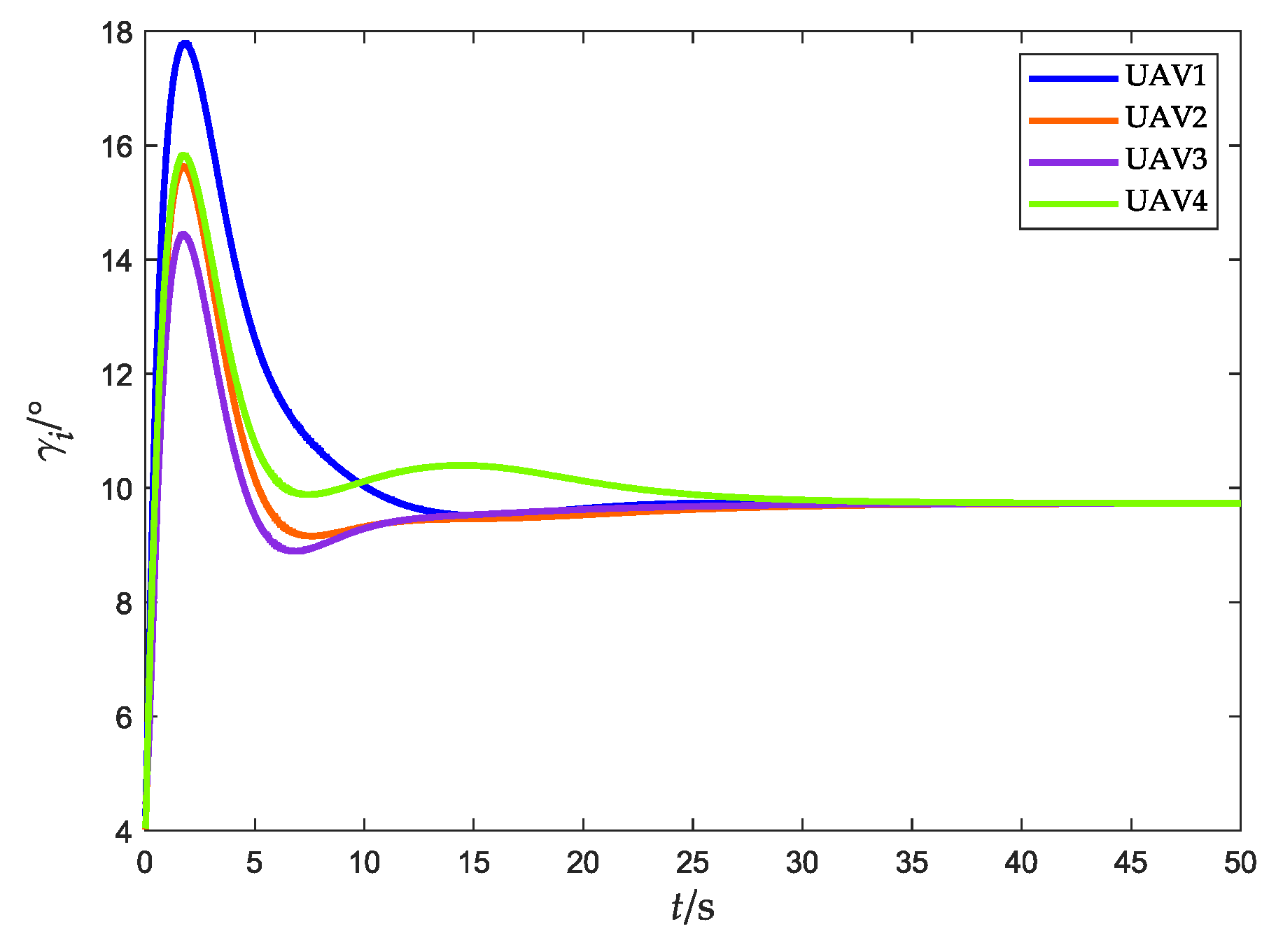
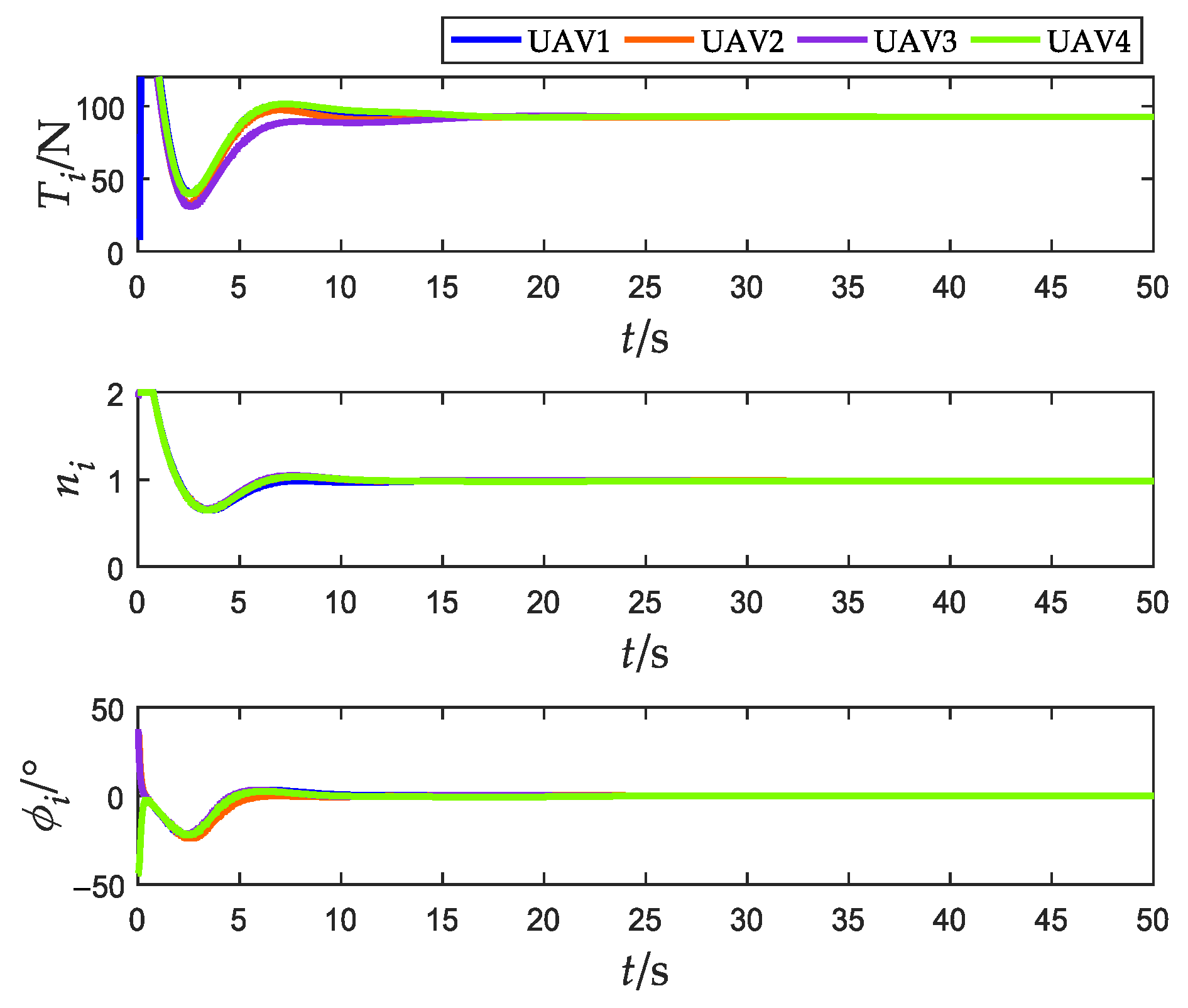
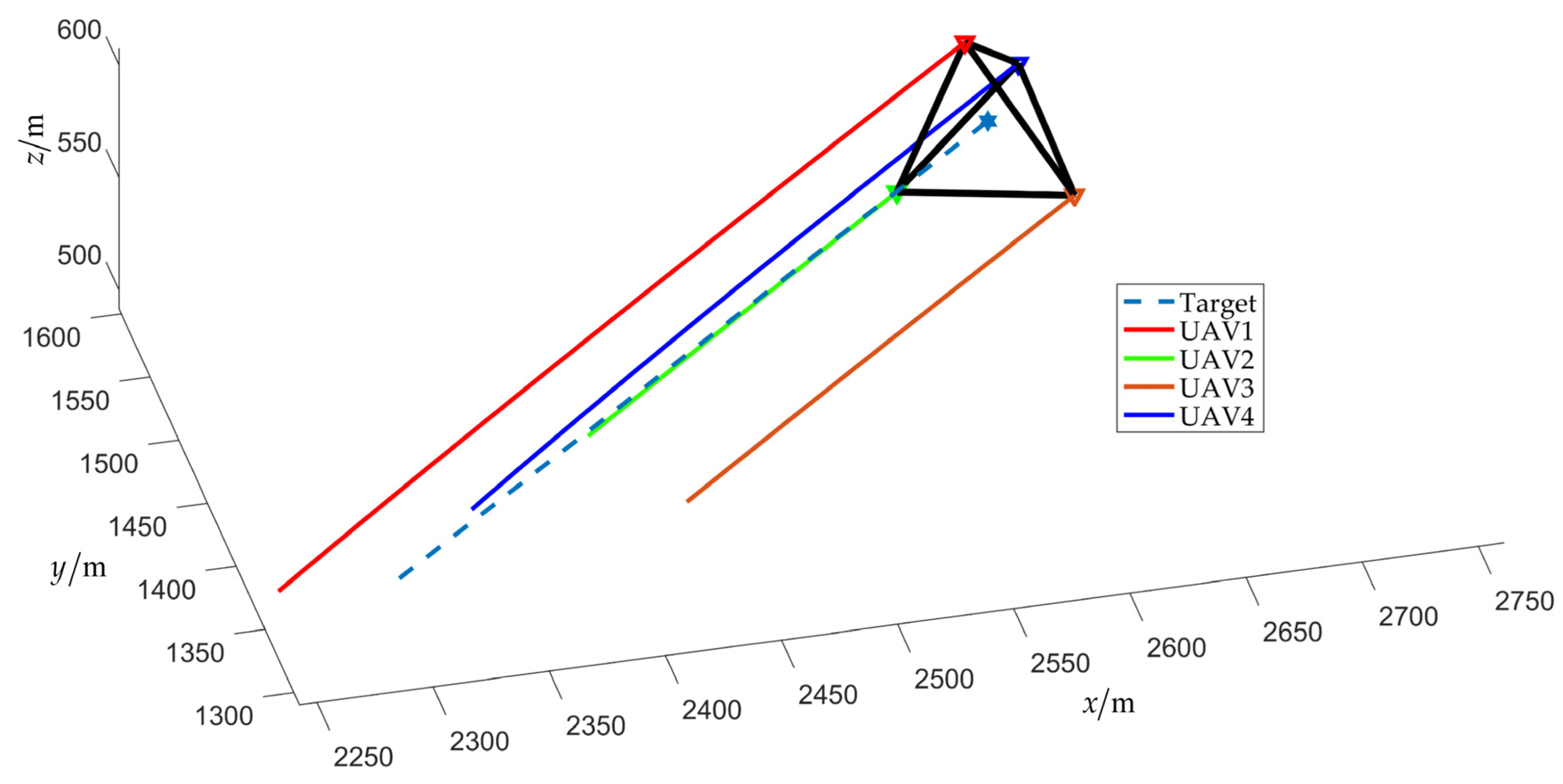
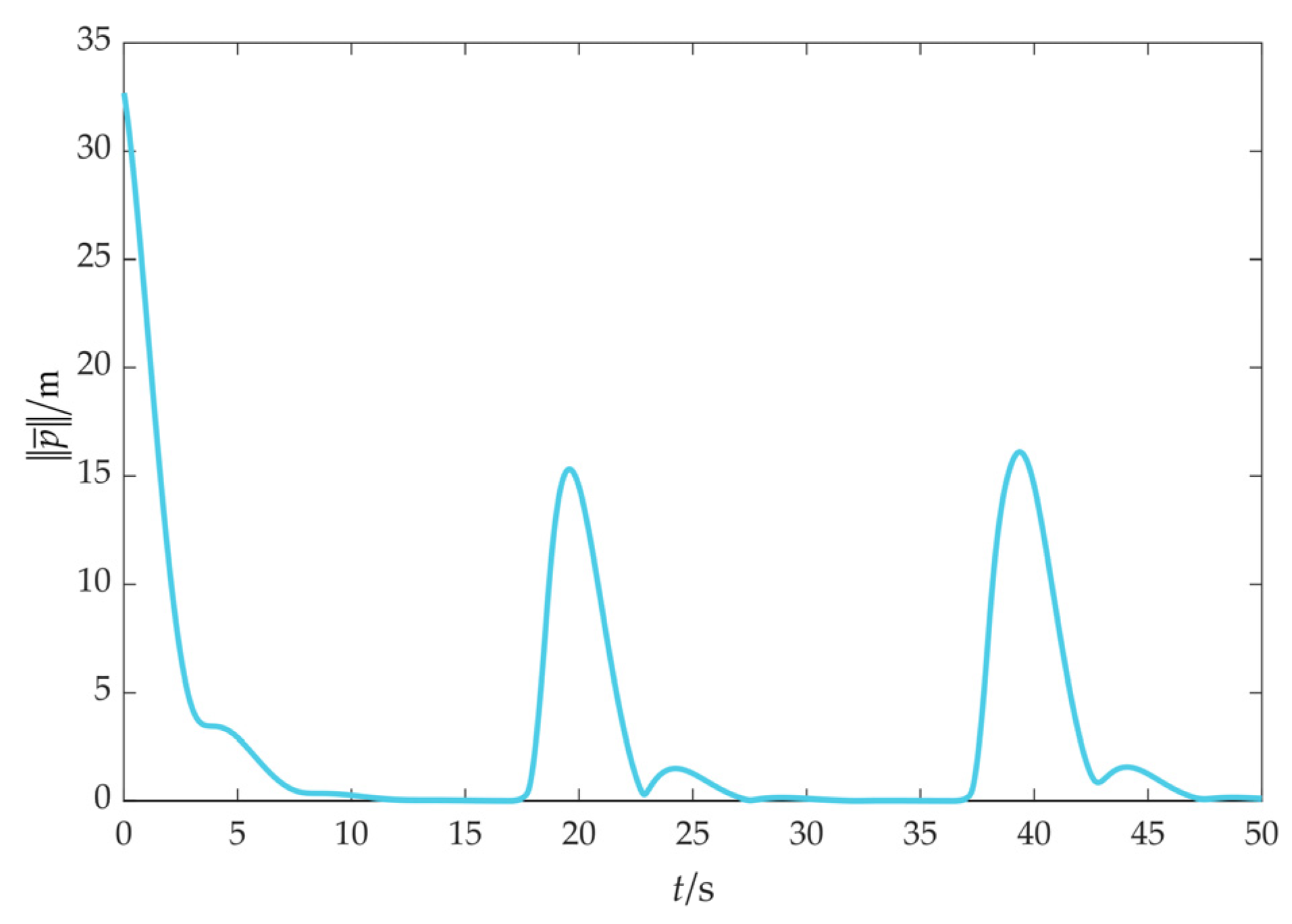
4.1. Scenario 1: Fencing a Target with a Constant Speed without Obstacles
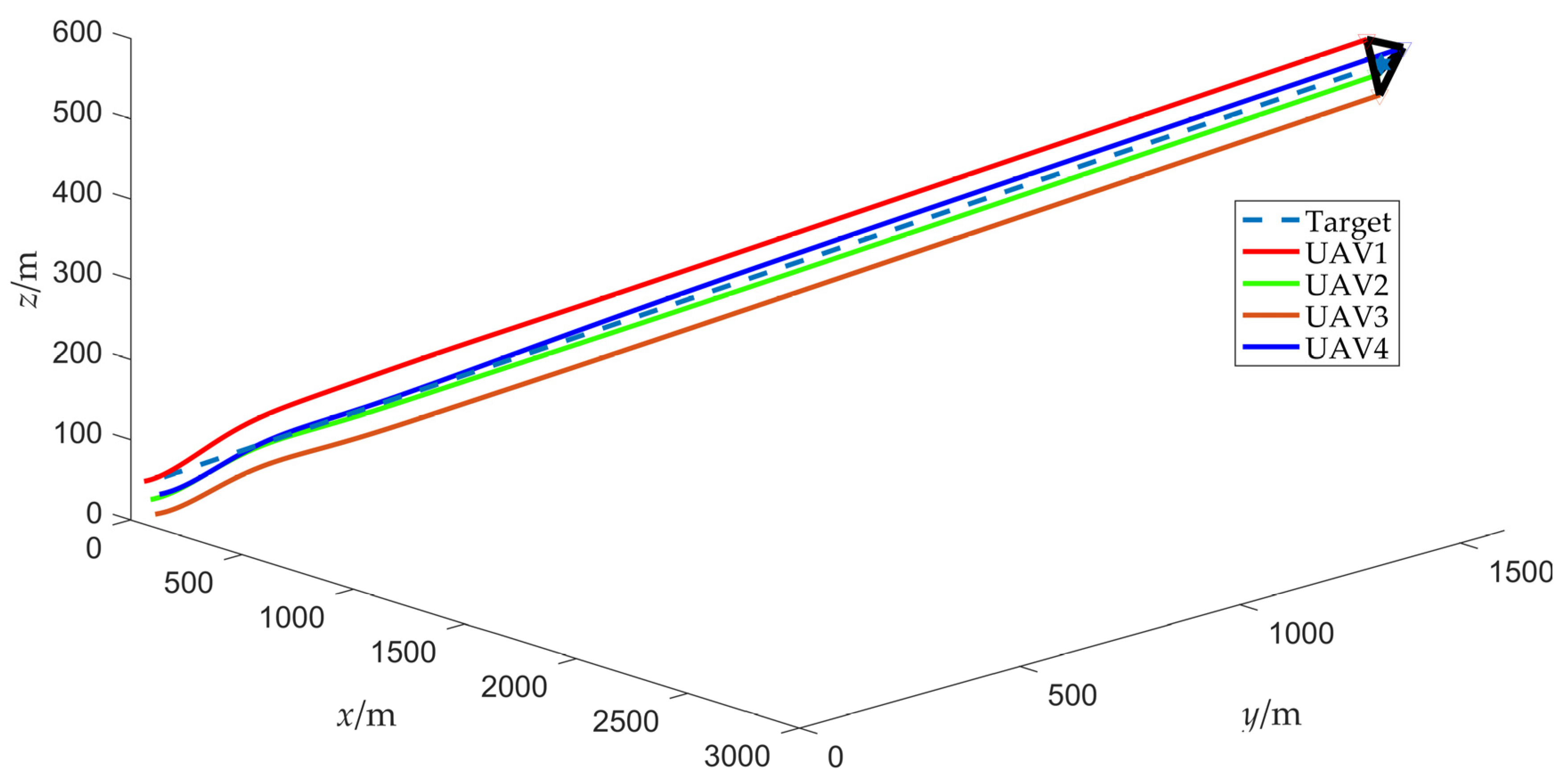
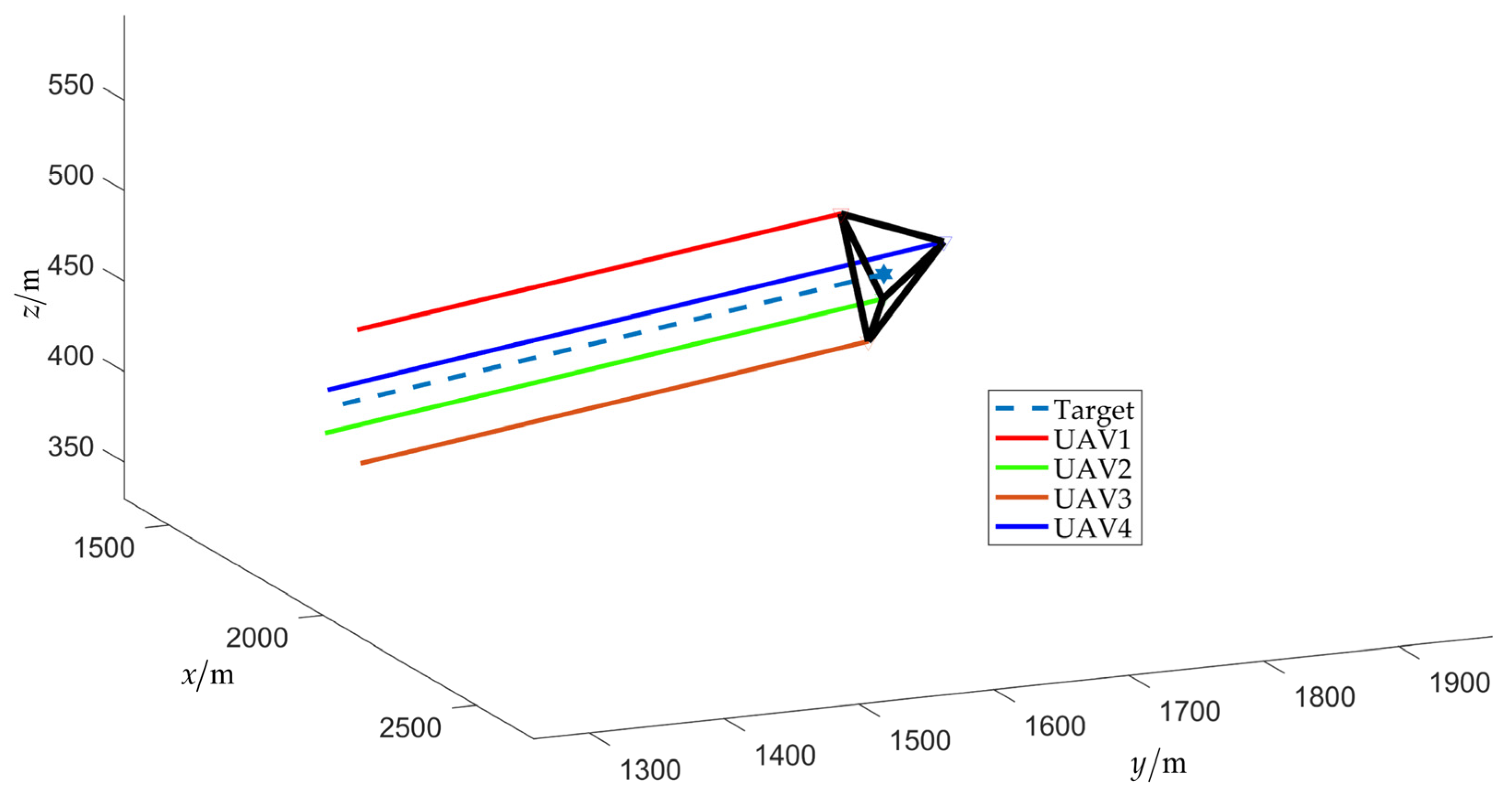
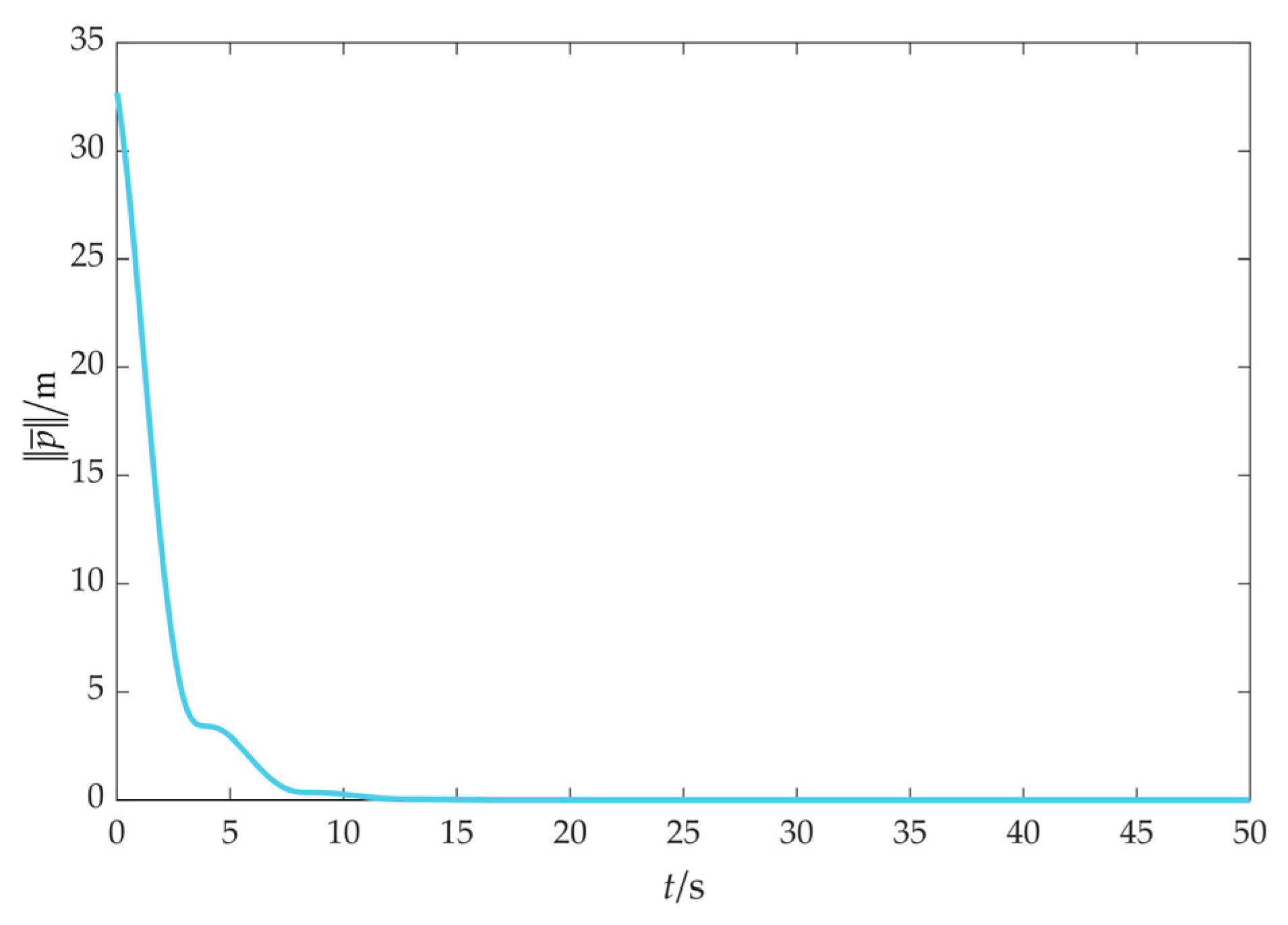
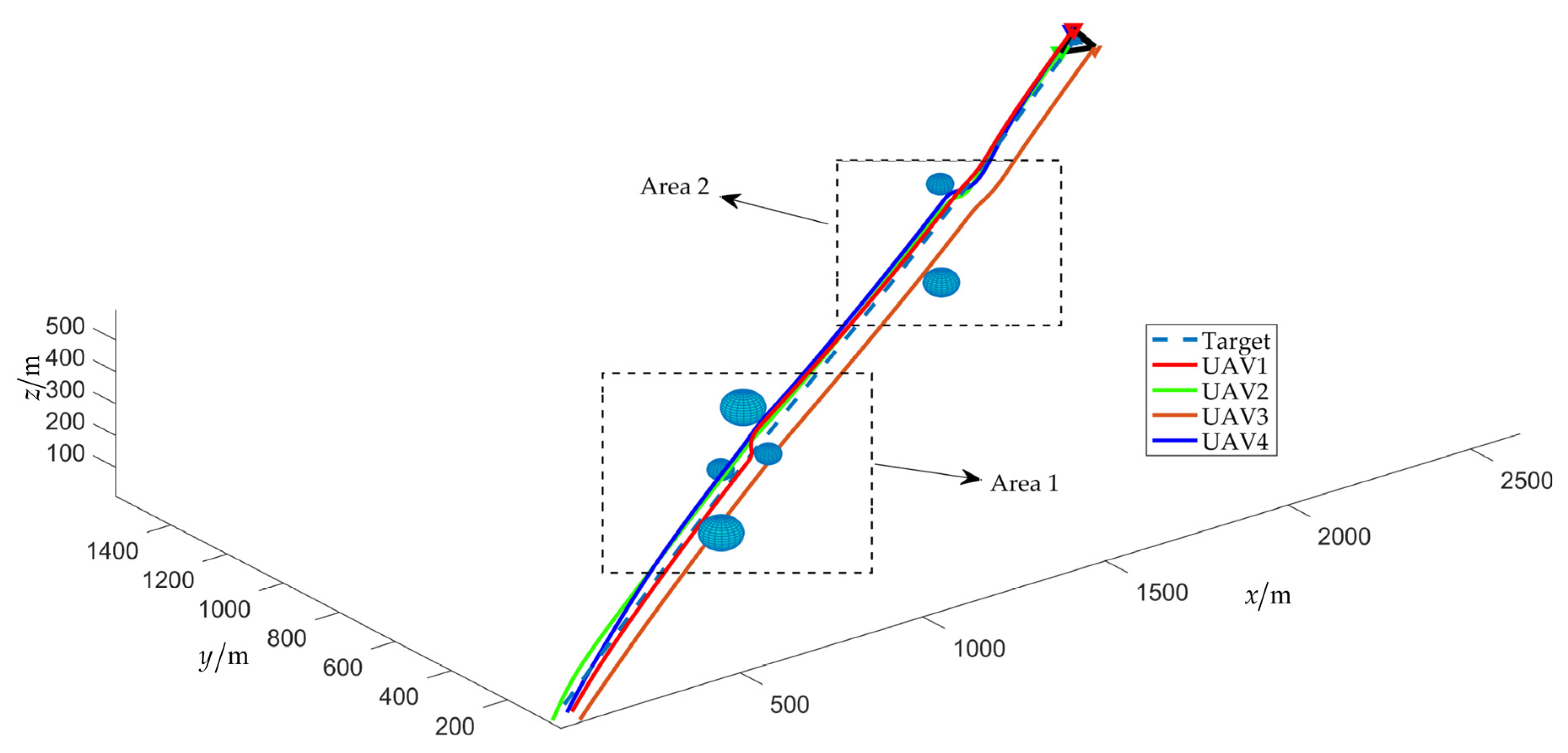
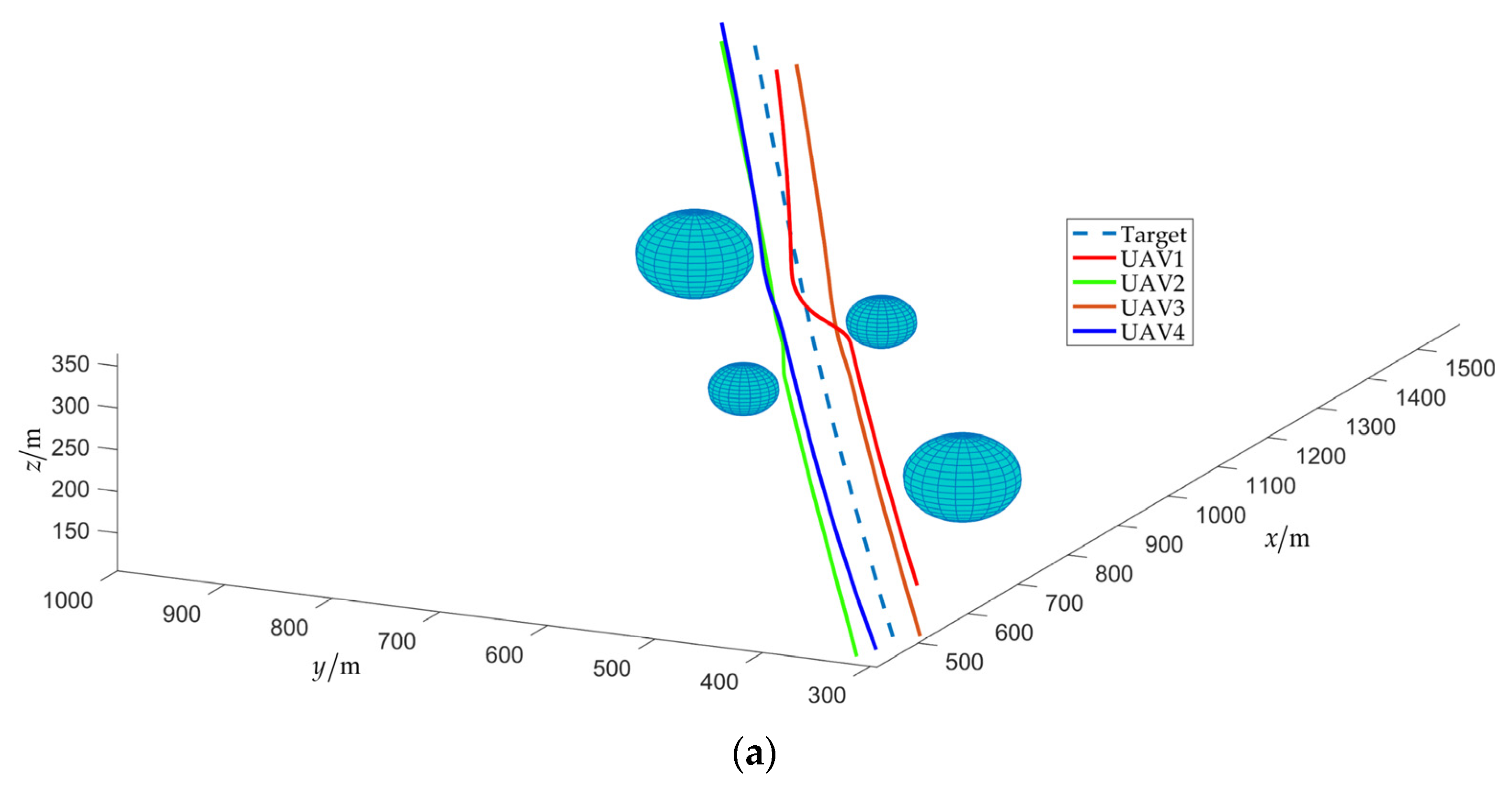
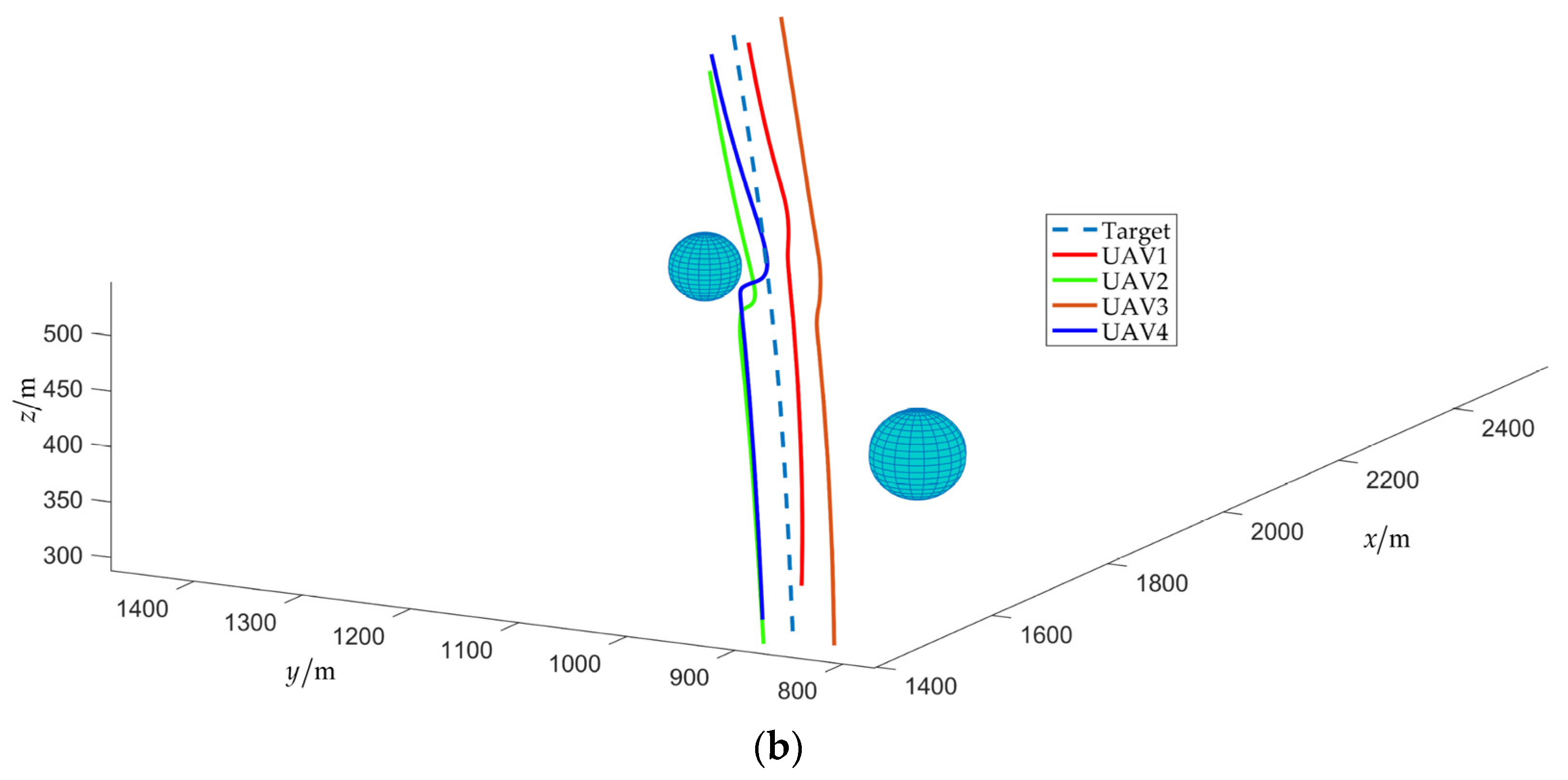
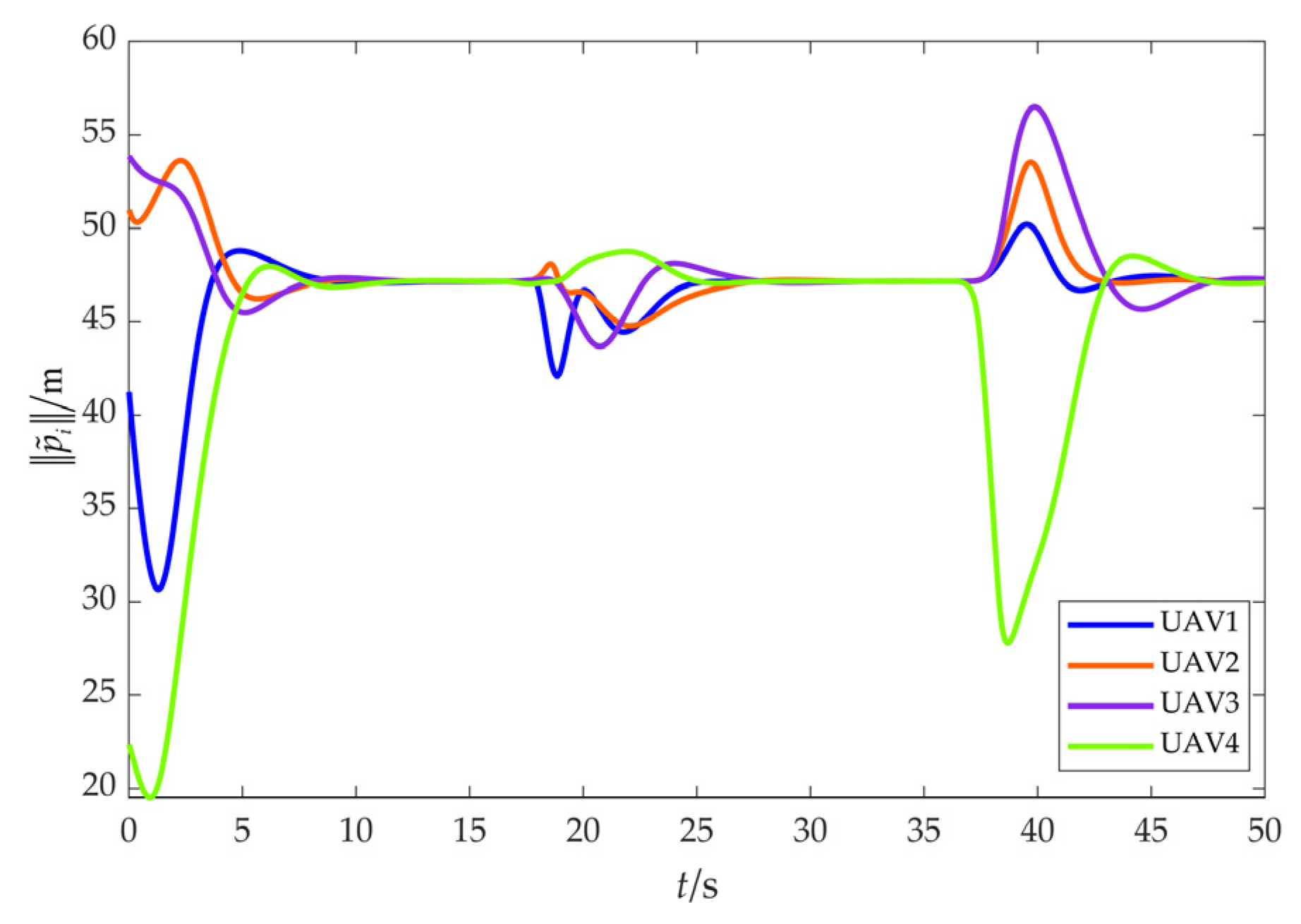
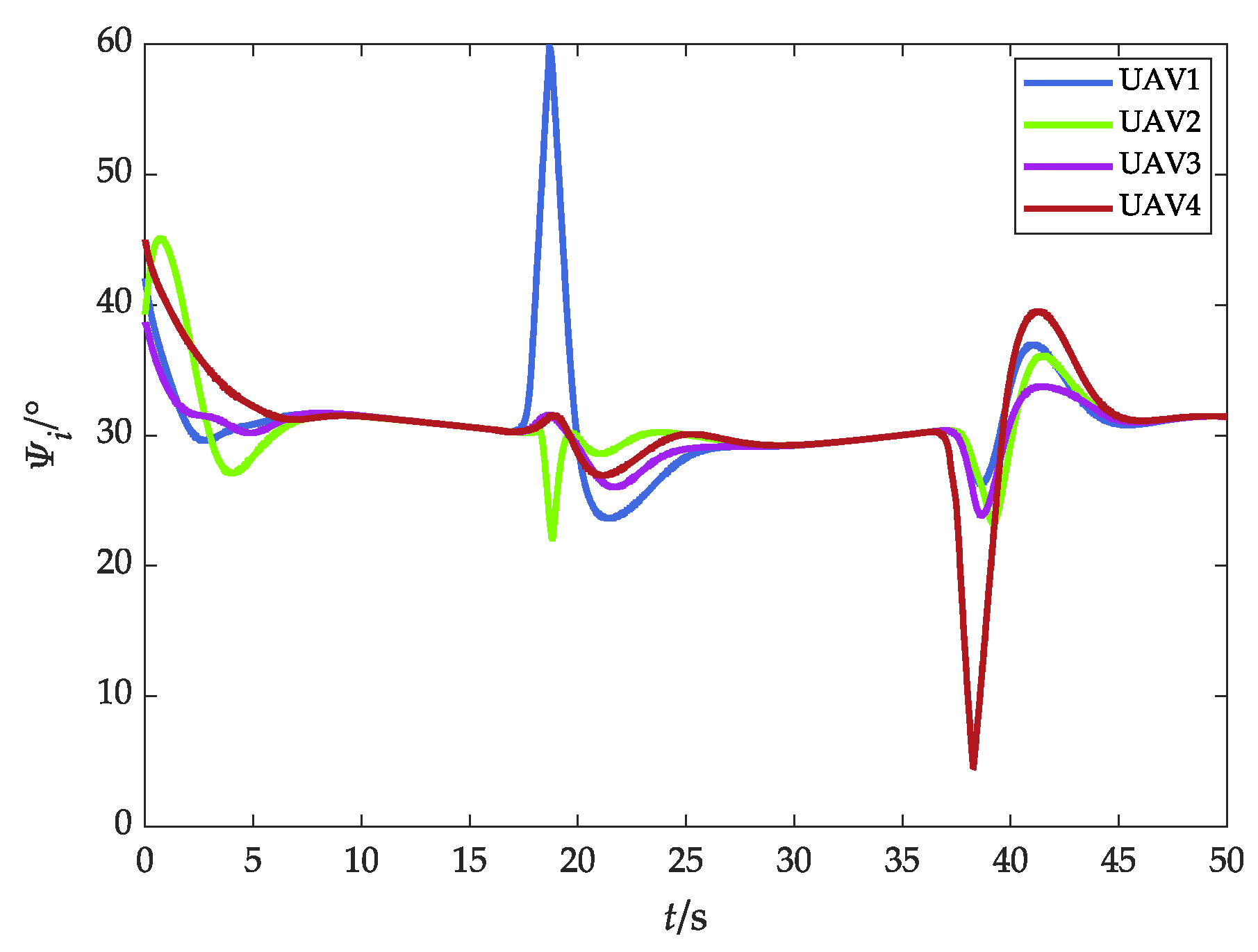
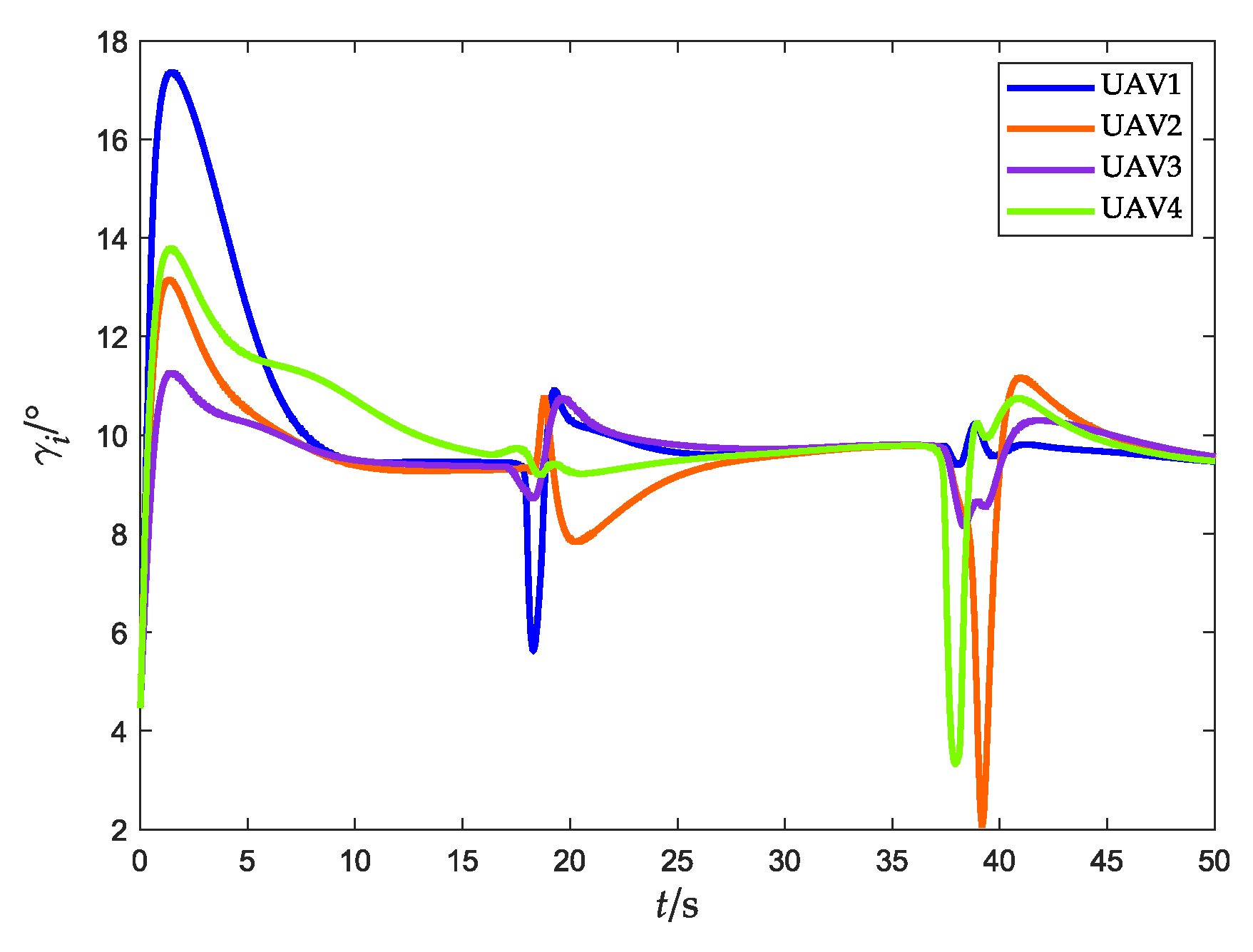
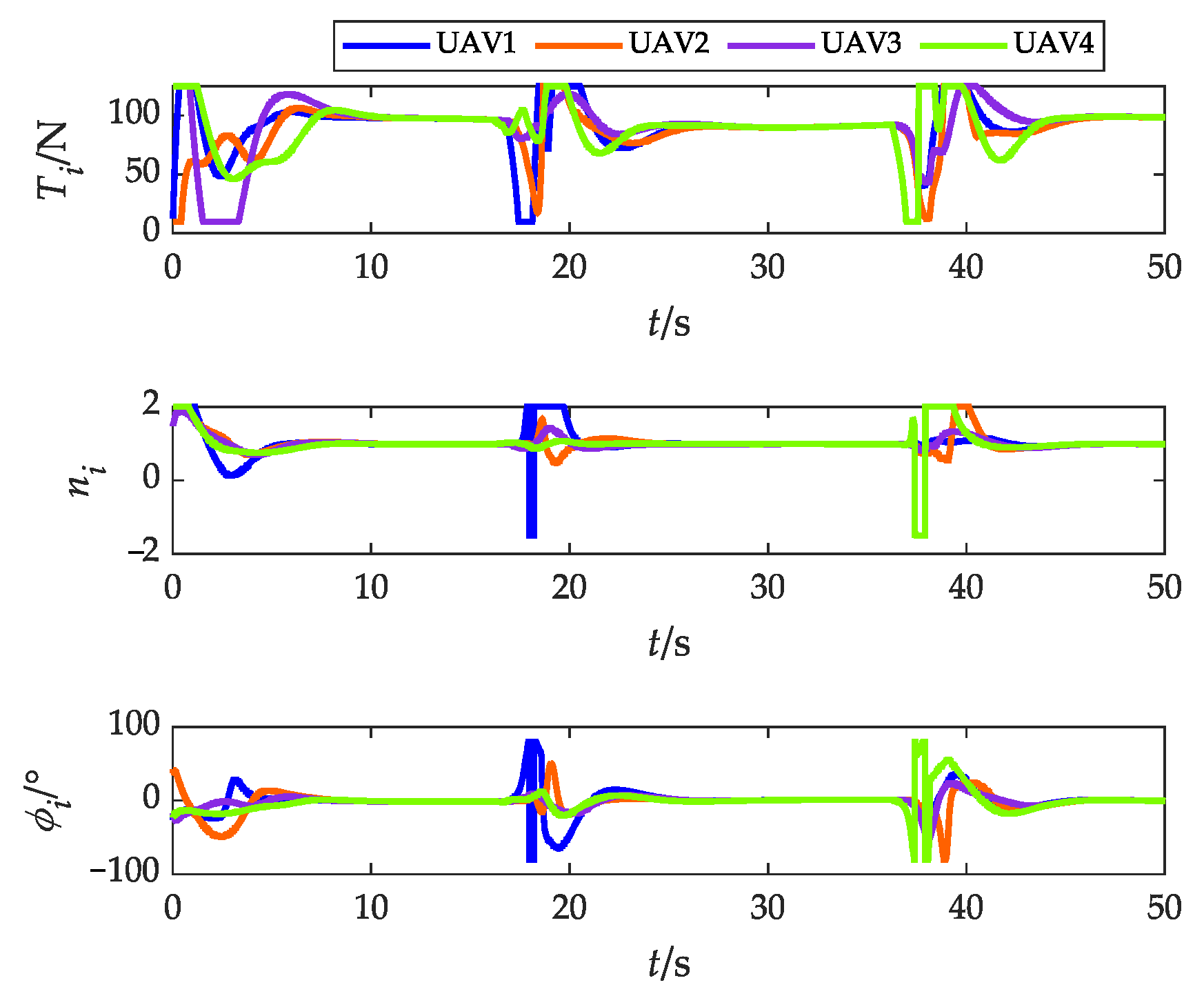
4.2. Scenario 2: Fencing a Maneuvering Target with Obstacle Avoidance
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Liu, Z.; Xiang, L.S.; Zhu, Z.M. Cooperative Standoff Target Tracking using Multiple Fixed-Wing UAVs with Input Constraints in Unknown Wind. Drones 2023, 7, 593. [Google Scholar] [CrossRef]
- Ma, B.D.; Liu, Z.B.; Zhao, W.; Yuan, J.B.; Long, H.; Wang, X.; Yuan, Z.R. Target Tracking Control of UAV Through Deep Reinforcement Learning. IEEE Trans. Intell. Transp. Syst. 2023, 24, 5983–6000. [Google Scholar] [CrossRef]
- Zhang, D.F.; Duan, H.B.; Zeng, Z.G. Leader–Follower Interactive Potential for Target Enclosing of Perception-Limited UAV Groups. IEEE. Syst. J. 2022, 16, 856–867. [Google Scholar] [CrossRef]
- Zhang, F.; Shao, X.L.; Xia, Y.; Zhang, W.D. Elliptical encirclement control capable of reinforcing performances for UAVs around a dynamic target. Def. Technol. 2024, 32, 104–119. [Google Scholar] [CrossRef]
- Hou, Y.K.; Zhao, J.; Zhang, R.Q.; Cheng, X.; Yang, L.Q. UAV Swarm Cooperative Target Search: A Multi-Agent Reinforcement Learning Approach. IEEE Trans. Intell. Veh. 2024, 9, 568–578. [Google Scholar] [CrossRef]
- Fu, X.W.; Pan, J.; Wang, H.X.; Gao, X.G. A formation maintenance and reconstruction method of UAV swarm based on distributed control. Aerosp. Sci. Technol. 2020, 104, 105981. [Google Scholar] [CrossRef]
- Xu, C.T.; Zhang, K.; Jiang, Y.S.; Niu, S.T.; Yang, T.; Song, H.B. Communication Aware UAV Swarm Surveillance Based on Hierarchical Architecture. Drones 2021, 5, 33. [Google Scholar] [CrossRef]
- Hu, B.B.; Zhang, H.T.; Shi, Y. Cooperative label-free moving target fencing for second-order multi-agent systems with rigid formation. Automatica 2023, 148, 110788. [Google Scholar] [CrossRef]
- Lin, J.; Wang, Y.N.; Miao, Z.Q.; Fan, S.W.; Wang, H.S. Robust Observer-Based Visual Servo Control for Quadrotors Tracking Unknown Moving Targets. IEEE/ASME Trans. Mech. 2023, 28, 1268–1279. [Google Scholar] [CrossRef]
- Zhang, Y.; Wen, Y.Y.; Li, F.F.; Chen, Y.Y. Distributed Observer-Based Formation Tracking Control of Multi-Agent Systems with Multiple Targets of Unknown Periodic Inputs. Unmanned Syst. 2019, 7, 15–23. [Google Scholar] [CrossRef]
- An, B.H.; Wang, B.; Fan, H.J.; Liu, L.; Hu, H.; Wang, Y.J. Fully distributed prescribed performance formation control for UAVs with unknown maneuver of leader. Aerosp. Sci. Technol. 2022, 130, 107886. [Google Scholar] [CrossRef]
- Chen, L.M.; Li, C.J.; Guo, Y.N.; Ma, G.F.; Li, Y.N.; Xiao, B. Formation–containment control of multi-agent systems with communication delays. ISA Trans. 2022, 128, 32–43. [Google Scholar] [CrossRef]
- Wang, Y.H.; Liu, C. Distributed finite-time adaptive fault-tolerant formation–containment control for USVs with dynamic event-triggered mechanism. Ocean. Eng. 2023, 280, 114524. [Google Scholar] [CrossRef]
- Ju, S.; Wang, J.; Dou, L.Y. Enclosing Control for Multiagent Systems with a Moving Target of Unknown Bounded Velocity. IEEE Trans. Cybern. 2022, 52, 11561–11570. [Google Scholar] [CrossRef]
- Zhang, J.T.; Shao, X.L.; Zhang, W.D. Cooperative Enclosing Control with Modified Guaranteed Performance and Aperiodic Communication for Unmanned Vehicles: A Path-Following Solution. IEEE Trans. Ind. Electron. 2024, 71, 943–953. [Google Scholar] [CrossRef]
- Chen, Z.Y. A cooperative target-fencing protocol of multiple vehicles. Automatica 2019, 107, 591–594. [Google Scholar] [CrossRef]
- Kou, L.W.; Xiang, J. Target fencing control of multiple mobile robots using output feedback linearization. Acta Autom. Sin. 2020, 48, 1–7. [Google Scholar]
- Wen, L.D.; Zhen, Z.Y.; Wan, T.C.; Hu, Z.; Yan, C. Distributed cooperative fencing scheme for UAV swarm based on self-organized behaviors. Aerosp. Sci. Technol. 2023, 138, 108327. [Google Scholar] [CrossRef]
- Yu, J.L.; Dong, X.W.; Li, Q.D.; Ren, Z. Practical time-varying output formation tracking for high-order multi-agent systems with collision avoidance, obstacle dodging and connectivity maintenance. J. Frankl. Inst. 2019, 256, 5898–5926. [Google Scholar] [CrossRef]
- Xie, S.T.; Hu, J.Y.; Bhowmick, P.; Ding, Z.T.; Arvin, F. Distributed Motion Planning for Safe Autonomous Vehicle Overtaking via Artificial Potential Field. IEEE Trans. Intell. Transp. Syst. 2022, 23, 21531–21547. [Google Scholar] [CrossRef]
- Li, Q.; Wei, J.Y.; Gou, Q.X.; Niu, Z.Q. Distributed adaptive fixed-time formation control for second-order multi-agent systems with collision avoidance. Inform. Sci. 2021, 564, 27–44. [Google Scholar] [CrossRef]
- Rai, A.; Mou, S.S. Safe Region Multi-Agent Formation Control with Velocity Tracking. Syst. Control Lett. 2024, 186, 105776. [Google Scholar] [CrossRef]
- Mondal, A.; Behera, L.; Sahoo, S.R.; Shukla, A. A novel multi-agent formation control law with collision avoidance. IEEE/CAA J. Autom. Sin. 2017, 4, 558–568. [Google Scholar] [CrossRef]
- Mondal, A.; Bhowmick, C.; Behera, L.; Jamshidi, M. Trajectory tracking by multiple agents in formation with collision avoidance and connectivity assurance. IEEE Syst. J. 2017, 12, 2449–2460. [Google Scholar] [CrossRef]
- Wen, G.H.; Lam, J.; Fu, J.J.; Wang, S. Distributed MPC-Based Robust Collision Avoidance Formation Navigation of Constrained Multiple USVs. IEEE Trans. Intell. Veh. 2024, 9, 1804–1816. [Google Scholar] [CrossRef]
- Park, S.; Lee, S.-M. Formation Reconfiguration Control with Collision Avoidance of Nonholonomic Mobile Robots. IEEE Rob. Autom. Lett. 2023, 8, 7905–7912. [Google Scholar] [CrossRef]
- Vargas, S.M.; Becerra, H.; Hayet, J.B. MPC-based distributed formation control of multiple quadcopters with obstacle avoidance and connectivity maintenance. Control Eng. Pract. 2022, 121, 105054. [Google Scholar] [CrossRef]
- Dai, L.; Cao, Q.; Xia, Y.Q.; Gao, Y.L. Distributed MPC for formation of multi-agent systems with collision avoidance and obstacle avoidance. J. Frankl. Inst. 2017, 354, 2068–2085. [Google Scholar] [CrossRef]
- Xidias, E.K.; Azariadis, P.N. Computing collision-free motions for a team of robots using formation and non-holonomic constraints. Robot. Auton. Syst. 2016, 82, 15–23. [Google Scholar] [CrossRef]
- Sui, Z.Z.; Pu, Z.Q.; Yi, J.Q.; Wu, S.G. Formation Control with Collision Avoidance Through Deep Reinforcement Learning Using Model-Guided Demonstration. IEEE Trans. Neural Netw. Learn. Syst. 2021, 32, 2358–2372. [Google Scholar] [CrossRef] [PubMed]
- Pan, C.; Peng, Z.H.; Liu, L.; Wang, D. Data-driven distributed formation control of under-actuated unmanned surface vehicles with collision avoidance via model-based deep reinforcement learning. Ocean. Eng. 2023, 267, 113166. [Google Scholar] [CrossRef]
- Yang, S.; Bai, W.W.; Li, T.S.; Shi, Q.; Yang, Y.; Wu, Y.; Philip Chen, C.L. Neural-network-based formation control with collision, obstacle avoidance and connectivity maintenance for a class of second-order nonlinear multi-agent systems. Neurocomputing 2021, 439, 243–255. [Google Scholar] [CrossRef]
- Peng, Z.H.; Wang, D.; Li, T.S.; Han, M. Output-Feedback Cooperative Formation Maneuvering of Autonomous Surface Vehicles with Connectivity Preservation and Collision Avoidance. IEEE Trans. Cybern. 2019, 50, 2527–2535. [Google Scholar] [CrossRef] [PubMed]
- Cong, Y.Z.; Du, H.B.; Jin, Q.C.; Zhu, W.W.; Lin, X.Z. Formation control for multiquadrotor aircraft: Connectivity preserving and collision avoidance. Int. J. Robust Nonlinear Control 2020, 30, 2352–2366. [Google Scholar] [CrossRef]
- Dong, C.; Ye, Q.Z.; Dai, S.L. Neural-network-based adaptive output-feedback formation tracking control of USVs under collision avoidance and connectivity maintenance constraints. Neurocomputing 2020, 401, 101–112. [Google Scholar] [CrossRef]
- Wang, J.; Wong, W.-C.; Luo, X.Y.; Li, X.L.; Guan, X.P. Connectivity-maintained and specified-time vehicle platoon control systems with disturbance observer. Int. J. Robust Nonlinear Control 2021, 31, 7844–7861. [Google Scholar] [CrossRef]
- Wang, J.N.; Xin, M. Integrated Optimal Formation Control of Multiple Unmanned Aerial Vehicles. IEEE Trans. Control Syst. Technol. 2013, 21, 1731–1744. [Google Scholar] [CrossRef]
- Basin, M.; Yu, P.; Shtessel, Y. Finite- and fixed-time differentiators utilising HOSM techniques. IET Control Theory Appl. 2017, 11, 1144–1152. [Google Scholar] [CrossRef]
- Zuo, Z.Y.; Song, J.W.; Tian, B.L.; Basin, M. Robust Fixed-Time Stabilization Control of Generic Linear Systems with Mismatched Disturbances. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 759–768. [Google Scholar] [CrossRef]
- Qiao, Y.T.; Huang, X.X.; Yang, B.; Geng, F.L.; Wang, B.H.; Hao, M.R.; Li, S. Formation Tracking Control for Multi-Agent Systems with Collision Avoidance and Connectivity Maintenance. Drones 2022, 6, 419. [Google Scholar] [CrossRef]






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, H.; Yang, X.; Zhang, Y.; Jiang, Z. Cooperative Target Fencing Control for Unmanned Aerial Vehicle Swarm with Collision, Obstacle Avoidance, and Connectivity Maintenance. Drones 2024, 8, 317. https://doi.org/10.3390/drones8070317
Yu H, Yang X, Zhang Y, Jiang Z. Cooperative Target Fencing Control for Unmanned Aerial Vehicle Swarm with Collision, Obstacle Avoidance, and Connectivity Maintenance. Drones. 2024; 8(7):317. https://doi.org/10.3390/drones8070317
Chicago/Turabian StyleYu, Hao, Xiuxia Yang, Yi Zhang, and Zijie Jiang. 2024. "Cooperative Target Fencing Control for Unmanned Aerial Vehicle Swarm with Collision, Obstacle Avoidance, and Connectivity Maintenance" Drones 8, no. 7: 317. https://doi.org/10.3390/drones8070317
APA StyleYu, H., Yang, X., Zhang, Y., & Jiang, Z. (2024). Cooperative Target Fencing Control for Unmanned Aerial Vehicle Swarm with Collision, Obstacle Avoidance, and Connectivity Maintenance. Drones, 8(7), 317. https://doi.org/10.3390/drones8070317





