The Evolution of Intelligent Transportation Systems: Analyzing the Differences and Similarities between IoV and IoFV
Abstract
1. Introduction
2. Background
2.1. VANET
2.2. FANET
2.3. IoV
2.4. IoFV
3. Building Blocks of Vehicular Networks
3.1. Sensors
3.2. Onboard Units
3.3. Base Stations
3.4. Clouds
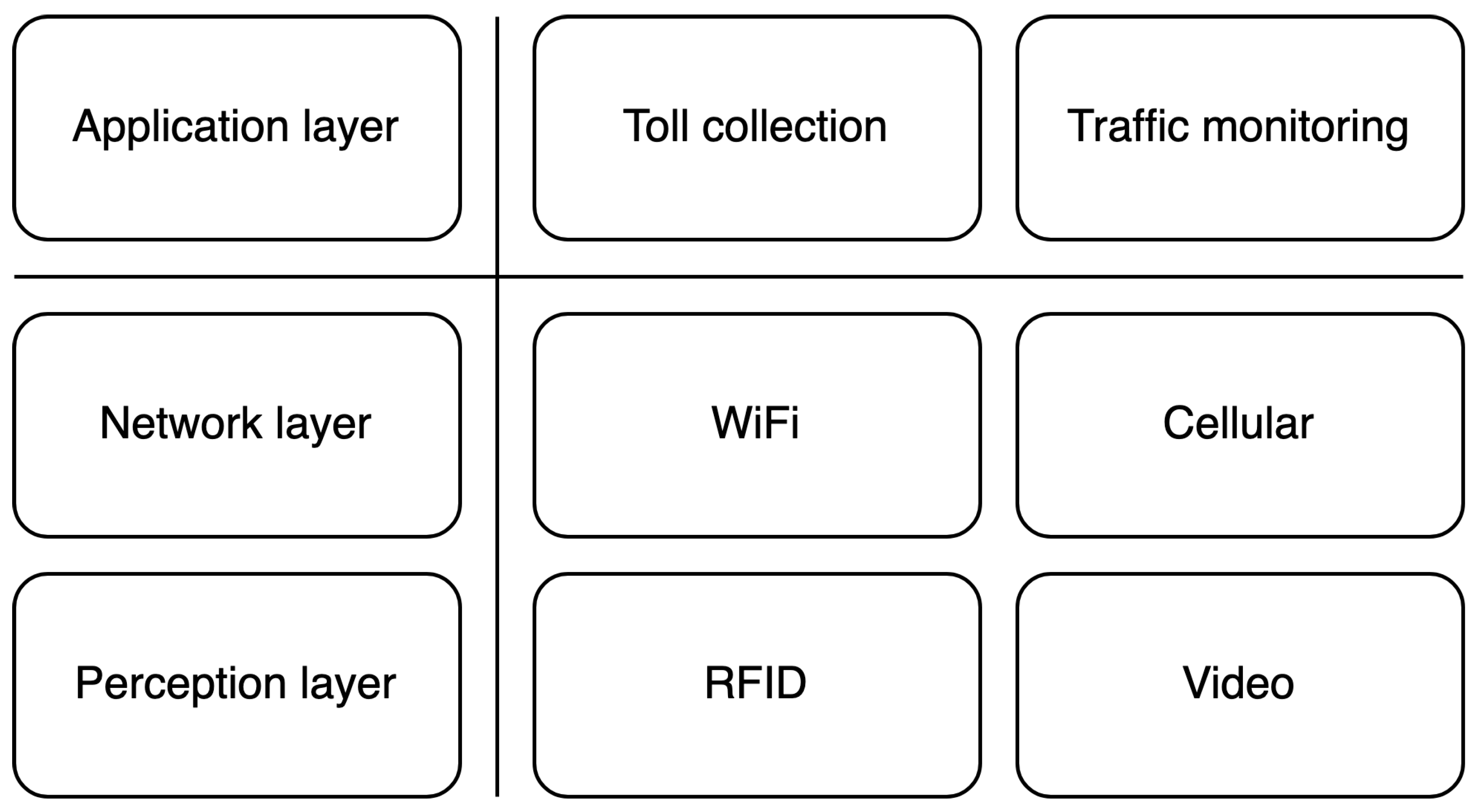
4. Layered Models
4.1. Sensory Layer
4.2. Communication Layer
4.3. Cognitive Layer
4.4. Application Layer
5. Communication in Vehicular Networks
5.1. Communication Models
5.2. Communication Types
- Direct communication: The usage of direct communication is possible in cases when vehicles are intended to communicate with base stations. In this scenario, vehicles are not able to communicate directly with each other due to the centralization of a network [66]. This type uses base stations as central nodes, thereby simplifying network architectures. A significant disadvantage is the possible failure of a central node, which would result in a failure of the whole network. Furthermore, due to limiting the communication only to a central node, the network may be prone to performance issues such as bottlenecks and is not suitable for dynamic environments [67].
- Satellite and cellular networks: Communication via satellite and cellular networks plays a vital role in interconnecting multiple vehicles. While satellite networks are suitable for communication in geographically distant nodes and find their use especially in flying vehicle networks, their use is also viable for ground vehicles in areas with sparse infrastructure and outside of cities, where there may not be other means of communication either directly to other vehicles or to an underlying infrastructure in the case that a vehicle is located outside of the coverage of cellular or other wireless networks [68]. On the other hand, cellular network coverage can provide fast and seamless communication in areas with sufficient coverage and is widely used in both ground and aerial vehicles [69]. Compared to satellite networks, cellular networks offer greater data transfer speed, lower latency—which is especially true in new generation networks such as 5G or beyond-5G networks—and a lower cost of operation [70].
- Ad hoc networks: In order to mitigate the disadvantages of the previous methods of communication, vehicular networks implement ad hoc networks. This approach was the primordial method of communication in earlier vehicular networks. Building on the MANET, nodes in the network with this type of communication enable nodes to communicate directly with each other without a need for centralization of the network’s components [71]. The usage of such a method is convenient, especially with more vehicles, with each viewed as an end system in proximity, thereby allowing them to remain connected even in the case that a vehicle reaches a point without a coverage of centralized components [72]. This method finds applications in both ground and aerial vehicle networks. Even though this approach to communication has several benefits in comparison to the previously discussed methods, its usage may be hindered by the rapidly changing dynamic topology of such a network. To alleviate those drawbacks, some works are focusing on designing routing protocols for those networks with the goal of fast and reliable delivery of data while lowering the cost of operation and energy consumption [51].
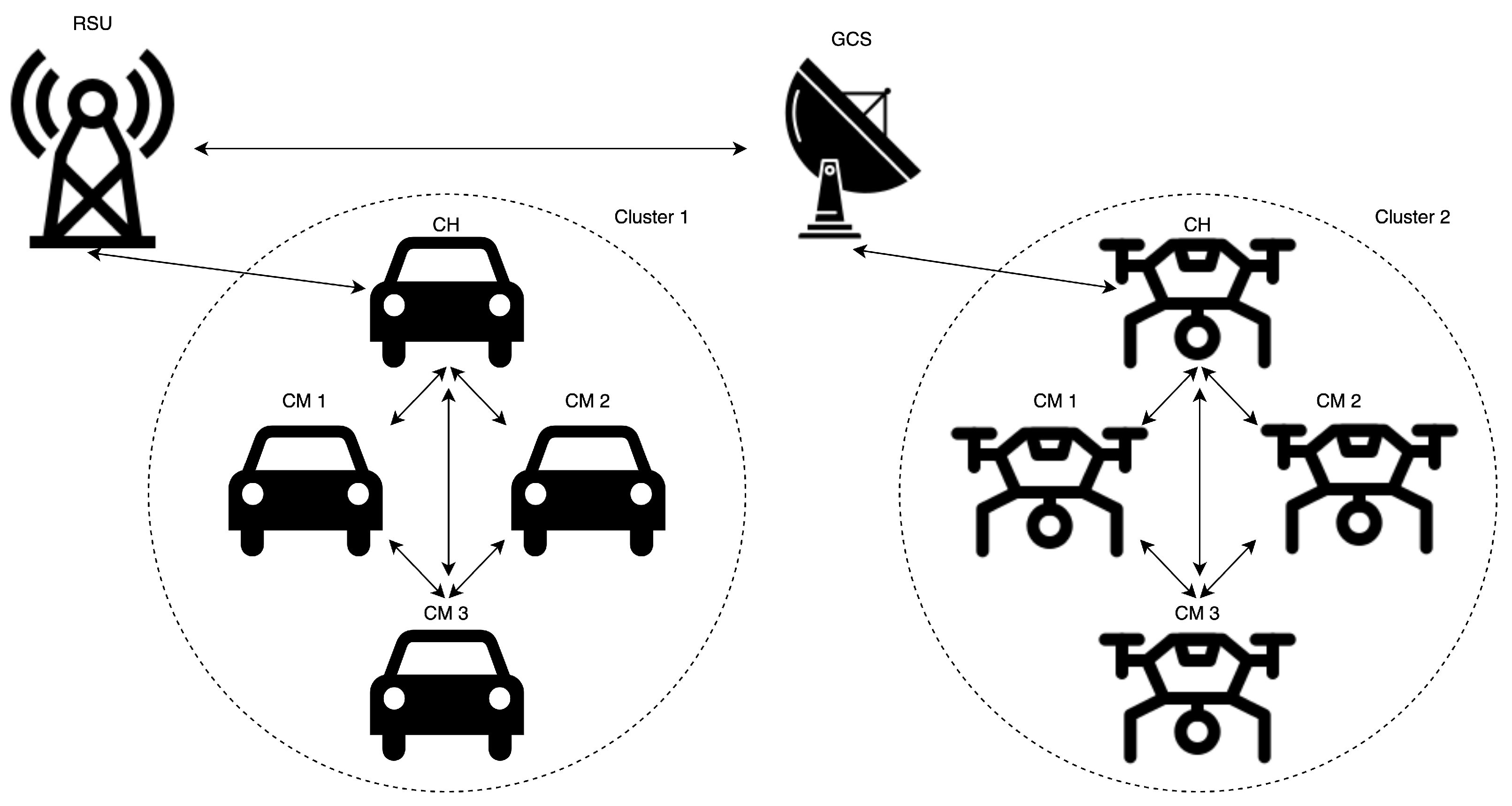
5.3. Clustering in Communication
- Discovery: In this stage, vehicles joining the network periodically broadcast messages reporting their state as unclustered along with the data required to assign the vehicle to a cluster.
- CH selection: Upon receiving broadcast messages from neighboring nodes, a vehicle will elect an appropriate node based on the gathered data.
- Notification: After a CH is elected, it announces its state to the other vehicles by broadcasting to the unclustered nodes.
- Association: Subsequently, other nodes request to join the cluster and change their state to clustered.
- Maintenance: Both the CH and CM monitor the communication state with each other. If the link is lost, a CM will change its state to unclustered and attempt to join a different cluster.
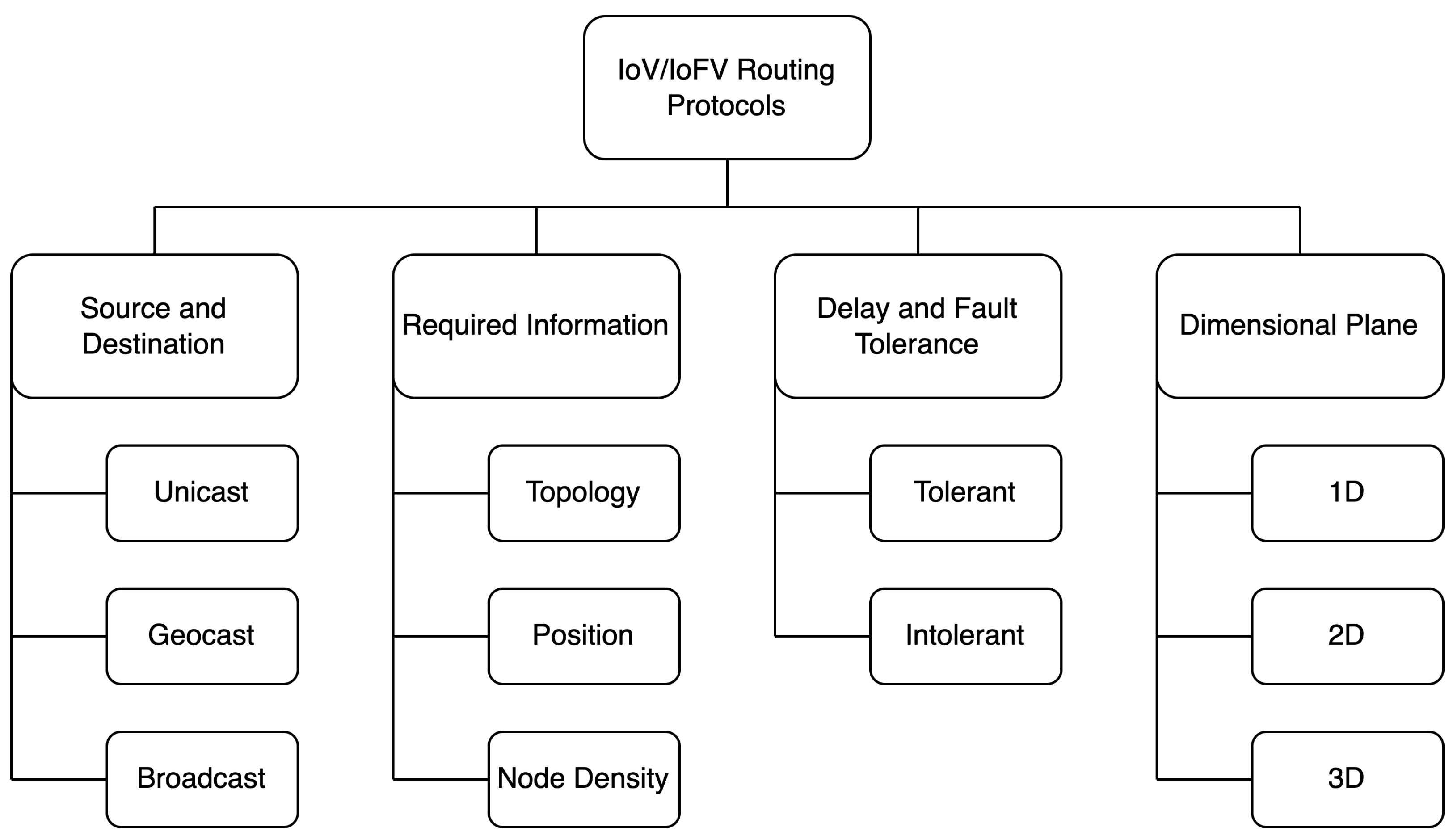
5.4. Routing
| Algorithm | WoS | Scopus | Year | Citations WoS | Citations Scopus | Reference |
|---|---|---|---|---|---|---|
| PSO | Yes | Yes | 2019 | 1 | 1 | [91] |
| PSO | Yes | Yes | 2021 | 1 | 1 | [92] |
| PSO | Yes | Yes | 2021 | 2 | 3 | [93] |
| PSO | Yes | Yes | 2020 | 2 | 3 | [94] |
| PSO | Yes | Yes | 2021 | 6 | 8 | [95] |
| PSO | Yes | Yes | 2020 | 6 | 8 | [96] |
| F-Ant | Yes | Yes | 2018 | 29 | 39 | [97] |
| Glow-Worm Swarm | Yes | Yes | 2022 | 1 | 0 | [98] |
| Glow-Worm Swarm | Yes | Yes | 2018 | 5 | 4 | [99] |
| ACO | Yes | Yes | 2022 | 18 | 27 | [100] |
| Firefly | Yes | Yes | 2019 | 6 | 5 | [101] |
6. Computing in Vehicular Networks
6.1. Onboard
6.2. Edge and Fog
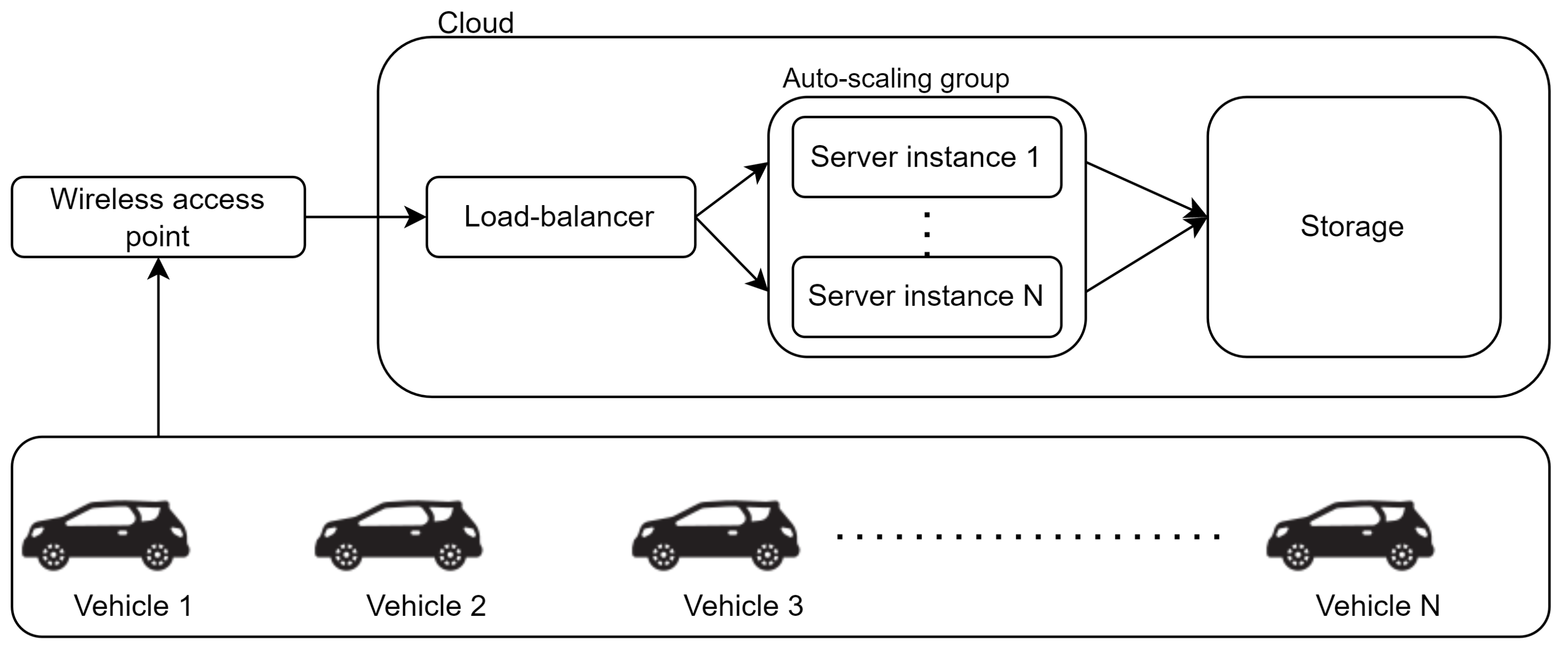
6.3. Cloud
7. Security
- Authentication is the verification of a user’s identity so that the person or system trying to access resources is actually who they say they are.
- Authorization is the granting of permission to access resources. If a person is authenticated, the authorization process determines which parts of the system and resources are accessible to that person and what actions he or she can perform.
- Auditing is the process of recording information about who logged into the system and when, which resources were used, and what actions were performed. It is therefore about monitoring user activity and preventing illegal activities.
7.1. Countermeasures
- Wi-Fi jamming: This is the most common method used, and it operates at a frequency of 2.4 GHz. It is the jamming of wireless transmission signals sent between devices connected to a given Wi-Fi network [142]. It is also used, for example, to protect the network from unauthorized access. The disadvantage is that such interference is visible and can be easily detected. Also, the interference is quite limited, and nearby frequencies are interfered with in addition to the target frequency [143].
- Replay: This attack consists of repeated data transmission between two devices without the data being modified in any way. The attacker intercepts the original communication and later retransmits it to gain unauthorized access [144]. For connected vehicles, it can also be used to break the encryption key while replaying the ARP protocol. It is mainly used when the connection between the vehicle and other devices is secure [145].
- Buffer overflow: This is an attack intended to fill the vehicle’s memory buffer with more data than it can process. Such data overflow can cause the vehicle to malfunction and execute arbitrary code, which is exploited to gain control of the device [146].
- DoS: This is performed either by deauthentication or Wi-Fi jamming, which causes devices in the vehicular networks to crash [147].
- ARP cache poisoning (ARP spoofing): An attacker sends spoofed ARP messages into the network in order to deceive other devices trying to communicate with the device. These spoofed ARP messages contain a physical MAC address to which other devices will send their messages. However, this MAC address is spoofed and it is the attacker’s device, which gives him access to the data being sent and allows him to modify it and send it on. In vehicular networks, it is used to send malicious scripts repeatedly [148].
7.2. Threats
- GPS signal manipulation: The GPS signal is crucial for navigation applications. It is transmitted by satellites orbiting the Earth. However, there is a vulnerability on Earth known as“GPS spoofing.” This refers to the act of generating a GPS signal to manipulate the GPS receiver in a target device. The person behind the spoofing has access to information about the GPS signal from satellites. The person uses it to create a manipulated version, thus giving them control over the target device [149]. This poses a risk for vehicles (UAVs) and unmanned ground vehicles that follow predetermined routes [150]. GPS spoofing could potentially lead to the theft of assets or result in unsafe cargo delivery, such as biological weapons or explosives.
- Malware and data interception: The wireless and remote control methods used for piloting UAVs and unmanned ground vehicles are not completely secure. Hackers can secretly implant a message into the vehicle’s memory by installing malware without detection in the system that controls the ground station [151]. Additionally, since these vehicles often monitor objects, their unsecured wireless transmission of sensor data makes them susceptible to hackers inserting malware.
- Wi-Fi interference: When deauthentication processes occur between an access point and a vehicle controller, it opens up opportunities for hijacking UAVs and unmanned ground vehicles. When hackers disrupt the Wi-Fi frequency of a drone, they manipulate it to connect to a network without authorization [152].
- Technical issues and nature: There are factors that can lead to crashes of UAVs and unmanned ground vehicles, such as the loss of connectivity, inexperienced piloting, or unfavorable weather conditions. These incidents can cause damage to property. Ref. [153] studied how these risks can even result in injuries. Additionally, technical problems like motors overheating or batteries exploding in temperatures can pose risks. Inadequate security measures in the design of these vehicles may also contribute to the loss of control, thus further escalating harm [154].
- Privacy concerns: As the popularity of UAVs and unmanned ground vehicles increases, so does the concern surrounding privacy [155]. Equipped with cameras and sensors, these vehicles have the capability to capture high-quality images and collect data that may intrude upon an individual’s privacy without their consent. Privacy concerns extend further when considering the risk of hackers gaining control over a vehicle’s cameras and gaining access to data from military zones or private residences for purposes such as identity theft, blackmailing, or illegal activities [156].
8. Use Cases and Applications
8.1. Agriculture
8.2. Warehouses and Logistics
8.3. Healthcare
8.4. Space Exploration
8.5. Search and Rescue
8.6. Other Applications of Drones and Autonomous Ground Vehicles
- Tourism, commerce, and cinematography: Drones play a pivotal role in the realms of tourism [181], commerce, and cinematography [182]. They provide high-quality images, thereby offering new perspectives to attract tourists and promote destinations at a whole new level. In cinematography, drones offer a cost-effective means to capture special shots that might be physically and financially challenging with alternative equipment.
- Underwater operations: Both aerial drones and unmanned underwater vehicles (UOVs) contribute significantly to monitoring marine life. Aerial drones can be used to survey coastlines and assess environmental conditions, while underwater drones are employed in surveys, checking underwater infrastructure, and searching for oil and gas. The advantage of underwater drones lies in their ability to withstand the dangerous and harsh conditions beneath the water’s surface. Advancements in this technology are anticipated, thereby enabling more sophisticated research and exploration of deep sea locations [183].
- Traffic monitoring: Drones and autonomous ground vehicles have proven effective in traffic and accident monitoring, thus quickly providing necessary footage through high-quality cameras [184]. They find applications in areas with a high frequency of accidents, thereby assisting in assigning blame or facilitating decision making. Beyond traffic, these autonomous systems are utilized to monitor crowds at protests or refugee movements, therbey contributing to public safety [185].
- Military applications: In military contexts, both drones and autonomous ground vehicles serve various purposes, from simple surveillance and reconnaissance to more complex tasks. They play a role in targeted killing through artificial intelligence, thereby reducing the risk to personnel. However, concerns about the misuse of such technologies for personal gain, potentially leading to property damage or harm to innocent lives, have been raised.
9. Challenges
9.1. Regulations
9.2. Integration
10. Conclusions and Future Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AU | Application Unit |
| UAV | Unmanned Aerial Vehicle |
| VANET | Vehicular Ad Hoc Network |
| MANET | Mobile Ad Hoc Network |
| FANET | Flying Ad Hoc Network |
| WLAN | Wireless Local Area Network |
| IoT | Internet of Things |
| DSRC | Dedicated Short-Range Communication |
| IoV | Internet of Vehicles |
| IoFV | Internet of Flying Vehicles |
| 5G | Fifth-Generation Network |
| V2 | Vehicle-to-Vehicle |
| V2I | Vehicle-to-Infrastructure |
| V2X | Vehicle-to-Everything |
| CCAS | Cooperative Collision Avoidance System |
| CAS | Collision Avoidance System |
| C-ITS | Cooperative Intelligent Transportation Systems |
| OBU | Onboard Unit |
| RSU | Roadside Unit |
| CH | Cluster Head |
| CM | Cluster Member |
| CG | Cluster Gateway |
| ITS | Intelligent Transportation System |
| GPS | Global Positioning System |
| LiDAR | Light Detection and Ranging |
References
- Raghavan, K.; Ooi, K.J.; Tan, Q.Y.; Bhuiyan, M.A.; Kumar, B.V.; Yuen, C.W.; Reaz, M.B. Smart Traffic Systems Guided by Principles of Traffic Circuit Theorems. In Proceedings of the 2020 IEEE 8th R10 Humanitarian Technology Conference (R10-HTC), Kuching, Malaysia, 1 December 2020; pp. 1–5. [Google Scholar]
- Saleem, M.; Abbas, S.; Ghazal, T.M.; Khan, M.m.A.; Sahawneh, N.; Ahmad, M. Smart cities: Fusion-based intelligent traffic congestion control system for vehicular networks using machine learning techniques. Egypt. Inform. J. 2022, 23, 417–426. [Google Scholar] [CrossRef]
- Yasin, J.N.; Mohamed, S.A.; Haghbayan, M.H.; Heikkonen, J.; Tenhunen, H.; Plosila, J. Unmanned aerial vehicles (uavs): Collision avoidance systems and approaches. IEEE Access 2020, 8, 105139–105155. [Google Scholar] [CrossRef]
- Byun, H.S.; Rhim, J.K. A Study on Accident Prevention through Analysis of Industrial Drone Accidents and Their Causes. J. Korean Soc. Saf. 2019, 34, 88–95. [Google Scholar]
- Arafat, M.Y.; Moh, S. Routing protocols for unmanned aerial vehicle networks: A survey. IEEE Access 2019, 7, 99694–99720. [Google Scholar] [CrossRef]
- Ali, E.S.; Hasan, M.K.; Hassan, R.; Saeed, R.A.; Hassan, M.B.; Islam, S.; Nafi, N.S.; Bevinakoppa, S. Machine learning technologies for secure vehicular communication in internet of vehicles: Recent advances and applications. Secur. Commun. Netw. 2021, 2021, 8868355. [Google Scholar] [CrossRef]
- Danba, S.; Bao, J.; Han, G.; Guleng, S.; Wu, C. Toward collaborative intelligence in IoV systems: Recent advances and open issues. Sensors 2022, 22, 6995. [Google Scholar] [CrossRef] [PubMed]
- Alladi, T.; Kohli, V.; Chamola, V.; Yu, F.R.; Guizani, M. Artificial intelligence (AI)-empowered intrusion detection architecture for the internet of vehicles. IEEE Wirel. Commun. 2021, 28, 144–149. [Google Scholar] [CrossRef]
- Al-Heety, O.S.; Zakaria, Z.; Ismail, M.; Shakir, M.M.; Alani, S.; Alsariera, H. A comprehensive survey: Benefits, services, recent works, challenges, security, and use cases for sdn-vanet. IEEE Access 2020, 8, 91028–91047. [Google Scholar] [CrossRef]
- Singh, A.; Patil, D.; Omkar, S. Eye in the sky: Real-time drone surveillance system (dss) for violent individuals identification using scatternet hybrid deep learning network. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, Salt Lake City, UT, USA, 18–23 June 2018; pp. 1629–1637. [Google Scholar]
- Hafeez, A.; Husain, M.A.; Singh, S.; Chauhan, A.; Khan, M.T.; Kumar, N.; Chauhan, A.; Soni, S. Implementation of drone technology for farm monitoring & pesticide spraying: A review. Inf. Process. Agric. 2022, 10, 192–203. [Google Scholar]
- Alsamhi, S.H.; Afghah, F.; Sahal, R.; Hawbani, A.; Al-qaness, M.A.; Lee, B.; Guizani, M. Green internet of things using UAVs in B5G networks: A review of applications and strategies. Ad Hoc Netw. 2021, 117, 102505. [Google Scholar] [CrossRef]
- Jamil, S.; Rahman, M. A Comprehensive Survey of Digital Twins and Federated Learning for Industrial Internet of Things (IIoT), Internet of Vehicles (IoV) and Internet of Drones (IoD). Appl. Syst. Innov. 2022, 5, 56. [Google Scholar] [CrossRef]
- Cheng, J.; Cao, C.; Zhou, M.; Liu, C.; Gao, S.; Jiang, C. A dynamic evolution mechanism for IoV community in an urban scene. IEEE Internet Things J. 2020, 8, 7521–7530. [Google Scholar] [CrossRef]
- Zeng, Q.; Tang, Y.; Yu, Z.; Xu, W. A geographical routing protocol based on link connectivity analysis for urban VANETs. J. Internet Technol. 2020, 21, 41–49. [Google Scholar]
- Chehri, A.; Chehri, H.; Hakim, N.; Saadane, R. Realistic 5.9 GHz DSRC vehicle-to-vehicle wireless communication protocols for cooperative collision warning in underground mining. In Smart Transportation Systems 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 133–141. [Google Scholar]
- Wang, P.; Chen, C.M.; Kumari, S.; Shojafar, M.; Tafazolli, R.; Liu, Y.N. HDMA: Hybrid D2D message authentication scheme for 5G-enabled VANETs. IEEE Trans. Intell. Transp. Syst. 2020, 22, 5071–5080. [Google Scholar] [CrossRef]
- Ji, B.; Zhang, X.; Mumtaz, S.; Han, C.; Li, C.; Wen, H.; Wang, D. Survey on the internet of vehicles: Network architectures and applications. IEEE Commun. Stand. Mag. 2020, 4, 34–41. [Google Scholar] [CrossRef]
- Sharma, S.; Kaul, A. VANETs cloud: Architecture, applications, challenges, and issues. Arch. Comput. Methods Eng. 2021, 28, 2081–2102. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANet security challenges and solutions: A survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Lee, M.; Atkison, T. Vanet applications: Past, present, and future. Veh. Commun. 2021, 28, 100310. [Google Scholar] [CrossRef]
- Yogarayan, S. Wireless Ad Hoc Network of MANET, VANET, FANET and SANET: A Review. J. Telecommun. Electron. Comput. Eng. 2021, 13, 13–18. [Google Scholar]
- Chriki, A.; Touati, H.; Snoussi, H.; Kamoun, F. FANET: Communication, mobility models and security issues. Comput. Netw. 2019, 163, 106877. [Google Scholar] [CrossRef]
- Khan, I.U.; Qureshi, I.M.; Aziz, M.A.; Cheema, T.A.; Shah, S.B.H. Smart IoT control-based nature inspired energy efficient routing protocol for flying ad hoc network (FANET). IEEE Access 2020, 8, 56371–56378. [Google Scholar] [CrossRef]
- Albu-Salih, A.T.; Khudhair, H.A. ASR-FANET: An adaptive SDN-based routing framework for FANET. Int. J. Electr. Comput. Eng. 2021, 11, 4403–4412. [Google Scholar] [CrossRef]
- Bujari, A.; Palazzi, C.E.; Ronzani, D. FANET application scenarios and mobility models. In Proceedings of the 3rd Workshop on Micro Aerial Vehicle Networks, Systems, and Applications, Niagara Falls, NY, USA, 23 June 2017; pp. 43–46. [Google Scholar]
- De Rango, F.; Potrino, G.; Tropea, M.; Santamaria, A.F.; Fazio, P. Scalable and ligthway bio-inspired coordination protocol for FANET in precision agriculture applications. Comput. Electr. Eng. 2019, 74, 305–318. [Google Scholar] [CrossRef]
- Hakimi, A.; Yusof, K.M.; Azizan, M.A.; Azman, M.A.A.; Hussain, S.M. A Survey on Internet of Vehicle (IoV): A pplications & Comparison of VANETs, IoV and SDN-IoV. ELEKTRIKA-J. Electr. Eng. 2021, 20, 26–31. [Google Scholar]
- Benalia, E.; Bitam, S.; Mellouk, A. Data dissemination for Internet of vehicle based on 5G communications: A survey. Trans. Emerg. Telecommun. Technol. 2020, 31, e3881. [Google Scholar] [CrossRef]
- Kim, S.K.A. Enhanced IoV security network by using blockchain governance game. Mathematics 2021, 9, 109. [Google Scholar] [CrossRef]
- Sharma, S.; Ghanshala, K.K.; Mohan, S. A security system using deep learning approach for internet of vehicles (IoV). In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 8–10 November 2018; pp. 1–5. [Google Scholar]
- Ang, L.M.; Seng, K.P.; Ijemaru, G.K.; Zungeru, A.M. Deployment of IoV for smart cities: Applications, architecture, and challenges. IEEE Access 2018, 7, 6473–6492. [Google Scholar] [CrossRef]
- Zaidi, S.; Atiquzzaman, M.; Calafate, C.T. Internet of flying things (IoFT): A survey. Comput. Commun. 2021, 165, 53–74. [Google Scholar] [CrossRef]
- Garg, T.; Kagalwalla, N.; Churi, P.; Pawar, A.; Deshmukh, S. A survey on security and privacy issues in IoV. Int. J. Electr. Comput. Eng. 2020, 10, 5409–5419. [Google Scholar] [CrossRef]
- Raja, G.; Dhanasekaran, P.; Anbalagan, S.; Ganapathisubramaniyan, A.; Bashir, A.K. SDN-enabled traffic alert system for IoV in smart cities. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 1093–1098. [Google Scholar]
- Kurt, G.K.; Khoshkholgh, M.G.; Alfattani, S.; Ibrahim, A.; Darwish, T.S.; Alam, M.S.; Yanikomeroglu, H.; Yongacoglu, A. A vision and framework for the high altitude platform station (HAPS) networks of the future. IEEE Commun. Surv. Tutorials 2021, 23, 729–779. [Google Scholar] [CrossRef]
- Khan, I.U.; Shah, S.B.H.; Wang, L.; Aziz, M.A.; Stephan, T.; Kumar, N. Routing protocols & unmanned aerial vehicles autonomous localization in flying networks. Int. J. Commun. Syst. 2021, 4885. [Google Scholar]
- Guerna, A.; Bitam, S.; Calafate, C.T. Roadside unit deployment in internet of vehicles systems: A survey. Sensors 2022, 22, 3190. [Google Scholar] [CrossRef] [PubMed]
- Qiu, J.; Chen, Y.; Zhang, X.; Liu, Q.; Li, W.; Pei, Y.; Liu, L. Standardization evolution and typical solutions of IoV. In Proceedings of the 2019 28th Wireless and Optical Communications Conference (WOCC), Beijing, China, 9–10 May 2019; pp. 1–4. [Google Scholar]
- Jayapandian, N. Cloud enabled smart firefighting drone using internet of things. In Proceedings of the 2019 International Conference on Smart Systems and Inventive Technology (ICSSIT), Tirunelveli, India, 27–29 November 2019; pp. 1079–1083. [Google Scholar]
- Dureja, A.; Sangwan, S. A Review: Efficient Transportation—Future Aspects of IoV. In Proceedings of the ETCCS 2020, Evolving Technologies for Computing, Communication and Smart World, Noida, India, 31 January–1 February 2020; pp. 97–108. [Google Scholar]
- Bindu, R.; Preethi Sejal, M.; Chetan, H. A Survey Paper on Evolution of Vanet Towards IOV. In Proceedings of the Optical and Wireless Technologies: Proceedings of OWT 2021, Jaipur, India, 17–20 March 2021; Springer: Berlin/Heidelberg, Germany, 2022; pp. 99–113. [Google Scholar]
- Sadiku, M.N.; Tembely, M.; Musa, S.M. Internet of vehicles: An introduction. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2018, 8, 11. [Google Scholar] [CrossRef]
- Liu, K.; Xu, X.; Chen, M.; Liu, B.; Wu, L.; Lee, V.C. A hierarchical architecture for the future internet of vehicles. IEEE Commun. Mag. 2019, 57, 41–47. [Google Scholar] [CrossRef]
- Chen, M.; Tian, Y.; Fortino, G.; Zhang, J.; Humar, I. Cognitive internet of vehicles. Comput. Commun. 2018, 120, 58–70. [Google Scholar] [CrossRef]
- Alouache, L.; Nguyen, N.; Aliouat, M.; Chelouah, R. Toward a hybrid SDN architecture for V2V communication in IoV environment. In Proceedings of the 2018 Fifth International Conference on Software Defined Systems (SDS), Barcelona, Spain, 23–26 April 2018; pp. 93–99. [Google Scholar]
- Contreras-Castillo, J.; Zeadally, S.; Guerrero-Ibañez, J.A. Internet of vehicles: Architecture, protocols, and security. IEEE Internet Things J. 2017, 5, 3701–3709. [Google Scholar] [CrossRef]
- Muhammad, A.; Saqib, M.; Song, W.C. Sensor virtualization and data orchestration in internet of vehicles (iov). In Proceedings of the 2021 IFIP/IEEE International Symposium on Integrated Network Management (IM), Bordeaux, France, 17–21 May 2021; pp. 998–1003. [Google Scholar]
- Hichri, Y.; Dahi, S.; Fathallah, H. Candidate architectures for emerging IoV: A survey and comparative study. Des. Autom. Embed. Syst. 2021, 25, 237–263. [Google Scholar] [CrossRef]
- Pozna, C.; Precup, R.E.; Földesi, P. A Novel Pose Estimation Algorithm for Robotic Navigation. Robot. Auton. Syst. 2015, 63, 10–21. [Google Scholar] [CrossRef]
- Gasmi, R.; Aliouat, M. Vehicular ad hoc networks versus internet of vehicles-a comparative view. In Proceedings of the 2019 International Conference on Networking and Advanced Systems (ICNAS), Annaba, Algeria, 26–27 June 2019; pp. 1–6. [Google Scholar]
- Hasan, K.F.; Kaur, T.; Hasan, M.M.; Feng, Y. Cognitive internet of vehicles: Motivation, layered architecture and security issues. In Proceedings of the 2019 International Conference on Sustainable Technologies for Industry 4.0 (STI), Dhaka, Bangladesh, 24–25 December 2019; pp. 1–6. [Google Scholar]
- Hasan, K.F.; Overall, A.; Ansari, K.; Ramachandran, G.; Jurdak, R. Security, privacy and trust: Cognitive internet of vehicles. arXiv 2021, arXiv:2104.12878. [Google Scholar]
- Dias Santana, G.M.; Cristo, R.S.d.; Lucas Jaquie Castelo Branco, K.R. Integrating cognitive radio with unmanned aerial vehicles: An overview. Sensors 2021, 21, 830. [Google Scholar] [CrossRef]
- Aftab, F.; Khan, A.; Zhang, Z. Hybrid self-organized clustering scheme for drone based cognitive Internet of Things. IEEE Access 2019, 7, 56217–56227. [Google Scholar] [CrossRef]
- Arooj, A.; Farooq, M.S.; Umer, T.; Shan, R.U. Cognitive internet of vehicles and disaster management: A proposed architecture and future direction. Trans. Emerg. Telecommun. Technol. 2022, 33, e3625. [Google Scholar] [CrossRef]
- Chen, C.; Liu, L.; Qiu, T.; Jiang, J.; Pei, Q.; Song, H. Routing with traffic awareness and link preference in internet of vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 23, 200–214. [Google Scholar] [CrossRef]
- Arooj, A.; Farooq, M.S.; Akram, A.; Iqbal, R.; Sharma, A.; Dhiman, G. Big data processing and analysis in internet of vehicles: Architecture, taxonomy, and open research challenges. Arch. Comput. Methods Eng. 2022, 29, 793–829. [Google Scholar] [CrossRef]
- Ouahouah, S.; Bagaa, M.; Prados-Garzon, J.; Taleb, T. Deep-reinforcement-learning-based collision avoidance in uav environment. IEEE Internet Things J. 2021, 9, 4015–4030. [Google Scholar] [CrossRef]
- Ullah, Z.; Al-Turjman, F.; Mostarda, L. Cognition in UAV-aided 5G and beyond communications: A survey. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 872–891. [Google Scholar] [CrossRef]
- Li, X.; Gao, X.; Liu, Y.; Huang, G.; Zeng, M.; Qiao, D. Overlay cognitive radio-assisted NOMA intelligent transportation systems with imperfect SIC and CEEs. Chin. J. Electron. 2023, 32, 1258–1270. [Google Scholar]
- Proos, D.P.; Carlsson, N. Performance comparison of messaging protocols and serialization formats for digital twins in IoV. In Proceedings of the 2020 IFIP Networking Conference (Networking), Paris, France, 22–26 June 2020; pp. 10–18. [Google Scholar]
- Sanguesa, J.A.; Barrachina, J.; Fogue, M.; Garrido, P.; Martinez, F.J.; Cano, J.C.; Calafate, C.T.; Manzoni, P. Sensing traffic density combining V2V and V2I wireless communications. Sensors 2015, 15, 31794–31810. [Google Scholar] [CrossRef]
- Peter, M.N.; Rani, M.P. V2V Communication and Authentication: The Internet of Things Vehicles (Iotv). Wirel. Pers. Commun. 2021, 120, 231–247. [Google Scholar] [CrossRef]
- Wang, Y.; Hu, X.; Guo, L.; Yao, Z. Research on V2I/V2V Hybrid Multi-hop Edge Computing Offloading Algorithm in IoV Environment. In Proceedings of the 2020 IEEE 5th International Conference on Intelligent Transportation Engineering (ICITE), Beijing, China, 11–13 September 2020; pp. 336–340. [Google Scholar]
- Duan, W.; Gu, J.; Wen, M.; Zhang, G.; Ji, Y.; Mumtaz, S. Emerging technologies for 5G-IoV networks: Applications, trends and opportunities. IEEE Netw. 2020, 34, 283–289. [Google Scholar] [CrossRef]
- Cheng, J.; Yuan, G.; Zhou, M.; Gao, S.; Liu, C.; Duan, H.; Zeng, Q. Accessibility analysis and modeling for IoV in an urban scene. IEEE Trans. Veh. Technol. 2020, 69, 4246–4256. [Google Scholar] [CrossRef]
- Li, X.; Feng, W.; Wang, J.; Chen, Y.; Ge, N.; Wang, C.X. Enabling 5G on the ocean: A hybrid satellite-UAV-terrestrial network solution. IEEE Wirel. Commun. 2020, 27, 116–121. [Google Scholar] [CrossRef]
- Wu, Q.; Xu, J.; Zeng, Y.; Ng, D.W.K.; Al-Dhahir, N.; Schober, R.; Swindlehurst, A.L. A comprehensive overview on 5G-and-beyond networks with UAVs: From communications to sensing and intelligence. IEEE J. Sel. Areas Commun. 2021, 39, 2912–2945. [Google Scholar] [CrossRef]
- Zeng, Y.; Wu, Q.; Zhang, R. Accessing from the sky: A tutorial on UAV communications for 5G and beyond. Proc. IEEE 2019, 107, 2327–2375. [Google Scholar] [CrossRef]
- Obaidat, M.; Khodjaeva, M.; Holst, J.; Ben Zid, M. Security and privacy challenges in vehicular ad hoc networks. In Connected Vehicles in the Internet of Things: Concepts, Technologies and Frameworks for the IoV; Springer: Berlin/Heidelberg, Germany, 2020; pp. 223–251. [Google Scholar]
- Sharma, S.; Ghanshala, K.K.; Mohan, S. Blockchain based internet of vehicles (IoV): An efficient secure ad hoc vehicular networking architecture. In Proceedings of the 2019 IEEE 2nd 5G World Forum (5GWF), Dresden, Germany, 30 September–2 October 2019; pp. 452–457. [Google Scholar]
- Li, B.; Deng, X.; Deng, Y. Mobile-edge computing-based delay minimization controller placement in SDN-IoV. Comput. Netw. 2021, 193, 108049. [Google Scholar] [CrossRef]
- Jamalzadeh, M.; Maadani, M.; Mahdavi, M. EC-MOPSO: An edge computing-assisted hybrid cluster and MOPSO-based routing protocol for the Internet of Vehicles. Ann. Telecommun. 2022, 77, 491–503. [Google Scholar] [CrossRef]
- Sennan, S.; Ramasubbareddy, S.; Balasubramaniyam, S.; Nayyar, A.; Kerrache, C.A.; Bilal, M. MADCR: Mobility aware dynamic clustering-based routing protocol in Internet of Vehicles. China Commun. 2021, 18, 69–85. [Google Scholar] [CrossRef]
- Cheng, F.; Shao, C. Research on Artificial Fish Swarm Clustering Algorithm in Urban Internet of Vehicles. In Proceedings of the 2020 IEEE International Conference on Smart Internet of Things (SmartIoT), Beijing, China, 14–16 August 2020; pp. 328–332. [Google Scholar]
- Ebadinezhad, S.; Dereboylu, Z.; Ever, E. Clustering-based modified ant colony optimizer for internet of vehicles (CACOIOV). Sustainability 2019, 11, 2624. [Google Scholar] [CrossRef]
- Khan, M.F.; Aadil, F.; Maqsood, M.; Bukhari, S.H.R.; Hussain, M.; Nam, Y. Moth flame clustering algorithm for internet of vehicle (MFCA-IoV). IEEE Access 2018, 7, 11613–11629. [Google Scholar] [CrossRef]
- Aadil, F.; Ahsan, W.; Rehman, Z.U.; Shah, P.A.; Rho, S.; Mehmood, I. Clustering algorithm for internet of vehicles (IoV) based on dragonfly optimizer (CAVDO). J. Supercomput. 2018, 74, 4542–4567. [Google Scholar] [CrossRef]
- Gasmi, R.; Aliouat, M.; Seba, H. Geographical Information Based Clustering Algorithm for Internet of Vehicles. In Proceedings of the International Conference on Machine Learning for Networking, Paris, France, 24–26 November 2020; pp. 107–121. [Google Scholar]
- Mahmood, A.; Siddiqui, S.A.; Sheng, Q.Z.; Zhang, W.E.; Suzuki, H.; Ni, W. Trust on wheels: Towards secure and resource efficient IoV networks. Computing 2022, 104, 1337–1358. [Google Scholar] [CrossRef]
- Senouci, O.; Harous, S.; Aliouat, Z. An efficient weight-based clustering algorithm using mobility report for IoV. In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 8–10 November 2018; pp. 614–620. [Google Scholar]
- Senouci, O.; Harous, S.; Aliouat, Z. A new heuristic clustering algorithm based on RSU for internet of vehicles. Arab. J. Sci. Eng. 2019, 44, 9735–9753. [Google Scholar] [CrossRef]
- Shivaraman, N.; Ramanathan, S.; Shanker, S.; Easwaran, A.; Steinhorst, S. Decoric: Decentralized connected resilient iot clustering. In Proceedings of the 2020 29th International Conference on Computer Communications and Networks (ICCCN), Honolulu, HI, USA, 3–6 August 2020; pp. 1–10. [Google Scholar]
- Wang, S.; Chen, G.; Jiang, Y.; You, X. A Cluster-based V2V Approach for Mixed Data Dissemination in Urban Scenario of IoVs. IEEE Trans. Veh. Technol. 2022, 72, 2907–2920. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Idrees, M.M.; Lloret, J.; Bosch, I. Self-assessment based clustering data dissemination for sparse and dense traffic conditions for internet of vehicles. IEEE Access 2020, 8, 10363–10372. [Google Scholar] [CrossRef]
- Ji, B.; Zhang, M.; Xing, L.; Li, X.; Li, C.; Han, C.; Wen, H. Research on optimal intelligent routing algorithm for IoV with machine learning and smart contract. Digit. Commun. Netw. 2023, 9, 47–55. [Google Scholar] [CrossRef]
- Yang, H.; Liu, H.; Luo, C.; Wu, Y.; Li, W.; Zomaya, A.Y.; Song, L.; Xu, W. Vehicle-key: A secret key establishment scheme for LoRa-enabled IoV communications. In Proceedings of the 2022 IEEE 42nd International Conference on Distributed Computing Systems (ICDCS), Bologna, Italy, 10–13 July 2022; pp. 787–797. [Google Scholar]
- Harrabi, S.; Jaafar, I.B.; Ghedira, K. Survey on IoV Routing Protocols. Wirel. Pers. Commun. 2023, 128, 791–811. [Google Scholar] [CrossRef]
- Alouache, L.; Nguyen, N.; Aliouat, M.; Chelouah, R. Survey on IoV routing protocols: Security and network architecture. Int. J. Commun. Syst. 2019, 32, e3849. [Google Scholar] [CrossRef]
- Dhurandher, S.K.; Singh, J.; Woungang, I.; Gupta, M.; Sabharwal, N. Geometric Shapes-based PSO Approach for Routing in Vehicular Networks. In Proceedings of the 2019 IEEE AFRICON, Accra, Ghana, 25–27 September 2019; pp. 1–7. [Google Scholar]
- BrijilalRuban, C.; Paramasivan, B. Energy Efficient Enhanced OLSR Routing Protocol Using Particle Swarm Optimization with Certificate Revocation Scheme for VANET. Wirel. Pers. Commun. 2021, 121, 2589–2608. [Google Scholar] [CrossRef]
- Ramasamy, V.; Srirangan, J.; Ramalingam, P. Fuzzy and position particle swarm optimized routing in VANET. Int. J. Electr. Comput. Eng. Syst. 2021, 12, 199–206. [Google Scholar] [CrossRef]
- AL-Shammari, M.Q.; Muniyandi, R.C. Optimised tail-based routing for VANETs using multi-objective particle swarm optimisation with angle searching. Int. J. Adv. Comput. Sci. Appl. 2020, 11. [Google Scholar] [CrossRef]
- Javadpour, A.; Rezaei, S.; Sangaiah, A.K.; Slowik, A.; Mahmoodi Khaniabadi, S. Enhancement in quality of routing service using metaheuristic PSO algorithm in VANET networks. Soft Comput. 2023, 27, 2739–2750. [Google Scholar] [CrossRef]
- Husain, A.; Singh, S.P.; Sharma, S. PSO optimized geocast routing in VANET. Wirel. Pers. Commun. 2020, 115, 2269–2288. [Google Scholar] [CrossRef]
- Fatemidokht, H.; Kuchaki Rafsanjani, M. F-Ant: An effective routing protocol for ant colony optimization based on fuzzy logic in vehicular ad hoc networks. Neural Comput. Appl. 2018, 29, 1127–1137. [Google Scholar] [CrossRef]
- Saravana Kumar, N.; Pagadala, P.K.; Vijayakumar, V.; Kavinya, A. Multi Objective Glow Swarm Based Situation and Quality Aware Routing in VANET. Wirel. Pers. Commun. 2022, 125, 879–895. [Google Scholar] [CrossRef]
- Rewadkar, D.; Doye, D. FGWSO-TAR: Fractional glowworm swarm optimization for traffic aware routing in urban VANET. Int. J. Commun. Syst. 2018, 31, e3430. [Google Scholar] [CrossRef]
- Gawas, M.A.; Govekar, S.S. A novel selective cross layer based routing scheme using ACO method for vehicular networks. J. Netw. Comput. Appl. 2019, 143, 34–46. [Google Scholar] [CrossRef]
- Singh, G.D.; Prateek, M.; Kumar, S.; Verma, M.; Singh, D.; Lee, H.N. Hybrid genetic firefly algorithm-based routing protocol for VANETs. IEEE Access 2022, 10, 9142–9151. [Google Scholar] [CrossRef]
- Saini, T.K.; Sharma, S.C. Prominent unicast routing protocols for Mobile Ad hoc Networks: Criterion, classification, and key attributes. Ad Hoc Netw. 2019, 89, 58–77. [Google Scholar] [CrossRef]
- Bhoi, S.K.; Sahu, P.K.; Singh, M.; Khilar, P.M.; Sahoo, R.R.; Swain, R.R. Local traffic aware unicast routing scheme for connected car system. IEEE Trans. Intell. Transp. Syst. 2019, 21, 2360–2375. [Google Scholar] [CrossRef]
- Bousbaa, F.Z.; Kerrache, C.A.; Mahi, Z.; Tahari, A.E.K.; Lagraa, N.; Yagoubi, M.B. GeoUAVs: A new geocast routing protocol for fleet of UAVs. Comput. Commun. 2020, 149, 259–269. [Google Scholar] [CrossRef]
- Gallego-Tercero, L.R.; Menchaca-Mendez, R.; Rivero-Angeles, M.E.; Menchaca-Mendez, R. Efficient time-stable geocast routing in delay-tolerant vehicular ad-hoc networks. IEEE Access 2020, 8, 171034–171048. [Google Scholar] [CrossRef]
- Boucetta, S.I.; Johanyák, Z.C. Optimized Ad-hoc Multi-hop Broadcast Protocol for Emergency Message Dissemination in Vehicular Ad-hoc Networks. Acta Polytech. Hung. 2022, 19, 23–42. [Google Scholar] [CrossRef]
- Nahar, A.; Sikarwar, H.; Das, D. Csbr: A cosine similarity based selective broadcast routing protocol for vehicular ad-hoc networks. In Proceedings of the 2020 IFIP Networking Conference (Networking), Paris, France, 22–26 June 2020; pp. 404–412. [Google Scholar]
- LiWang, M.; Hosseinalipour, S.; Gao, Z.; Tang, Y.; Huang, L.; Dai, H. Allocation of computation-intensive graph jobs over vehicular clouds in IoV. IEEE Internet Things J. 2019, 7, 311–324. [Google Scholar] [CrossRef]
- Tan, C.; Li, X.; Luan, T.H.; Gu, B.; Qu, Y.; Gao, L. Digital twin based remote resource sharing in internet of vehicles using consortium blockchain. In Proceedings of the 2021 IEEE 94th Vehicular Technology Conference (VTC2021-Fall), Virtual, 27 September–28 October 2021; pp. 1–6. [Google Scholar]
- Raza, S.; Wang, S.; Ahmed, M.; Anwar, M.R. A survey on vehicular edge computing: Architecture, applications, technical issues, and future directions. Wirel. Commun. Mob. Comput. 2019, 2019, 3159762. [Google Scholar] [CrossRef]
- Ahmed, M.; Haskell-Dowland, P. Secure Edge Computing: Applications, Techniques and Challenges; CRC Press: Boca Raton, FL, USA, 2021. [Google Scholar]
- Singh, J.; Singh, G.; Aggarwal, G. Inclusion of Aerial Computing in Internet of Things: Prospects and Applications. In Proceedings of the 2022 Third International Conference on Intelligent Computing Instrumentation and Control Technologies (ICICICT), Kannur, India, 11–12 August 2022; pp. 1664–1669. [Google Scholar]
- Sodhro, A.H.; Obaidat, M.S.; Abbasi, Q.H.; Pace, P.; Pirbhulal, S.; Fortino, G.; Imran, M.A.; Qaraqe, M. Quality of service optimization in an IoT-driven intelligent transportation system. IEEE Wirel. Commun. 2019, 26, 10–17. [Google Scholar] [CrossRef]
- Kadhim, A.J.; Naser, J.I. Proactive load balancing mechanism for fog computing supported by parked vehicles in IoV-SDN. China Commun. 2021, 18, 271–289. [Google Scholar] [CrossRef]
- Li, Y.; Li, H.; Xu, G.; Xiang, T.; Lu, R. Practical Privacy-Preserving Federated Learning in Vehicular Fog Computing. IEEE Trans. Veh. Technol. 2022, 71, 4692–4705. [Google Scholar] [CrossRef]
- Wang, H.; Liu, T.; Kim, B.; Lin, C.W.; Shiraishi, S.; Xie, J.; Han, Z. Architectural design alternatives based on cloud/edge/fog computing for connected vehicles. IEEE Commun. Surv. Tutorials 2020, 22, 2349–2377. [Google Scholar] [CrossRef]
- Nazih, O.; Benamar, N.; Lamaazi, H.; Chaoui, H. Challenges and future directions for security and privacy in vehicular fog computing. In Proceedings of the 2022 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakheer, Bahrain, 20–21 November 2022; pp. 693–699. [Google Scholar]
- Rihan, M.; Elwekeil, M.; Yang, Y.; Huang, L.; Xu, C.; Selim, M.M. Deep-VFog: When artificial intelligence meets fog computing in V2X. IEEE Syst. J. 2020, 15, 3492–3505. [Google Scholar] [CrossRef]
- Cui, M.; Han, D.; Wang, J.; Li, K.C.; Chang, C.C. ARFV: An efficient shared data auditing scheme supporting revocation for fog-assisted vehicular ad-hoc networks. IEEE Trans. Veh. Technol. 2020, 69, 15815–15827. [Google Scholar] [CrossRef]
- Akyildiz, O.; Kök, I.; Okay, F.Y.; Özdemir, S. A P4-assisted task offloading scheme for Fog networks: An intelligent transportation system scenario. Internet Things 2023, 22, 100695. [Google Scholar] [CrossRef]
- Saleem, M.A.; Mahmood, K.; Kumari, S. Comments on “AKM-IoV: Authenticated key management protocol in fog computing-based internet of vehicles deployment”. IEEE Internet Things J. 2020, 7, 4671–4675. [Google Scholar] [CrossRef]
- Al Ridhawi, I.; Aloqaily, M.; Boukerche, A. Comparing fog solutions for energy efficiency in wireless networks: Challenges and opportunities. IEEE Wirel. Commun. 2019, 26, 80–86. [Google Scholar] [CrossRef]
- Ampatzidis, Y.; Partel, V.; Costa, L. Agroview: Cloud-based application to process, analyze and visualize UAV-collected data for precision agriculture applications utilizing artificial intelligence. Comput. Electron. Agric. 2020, 174, 105457. [Google Scholar] [CrossRef]
- Nasir, A.A. Latency optimization of UAV-enabled MEC system for virtual reality applications under rician fading channels. IEEE Wirel. Commun. Lett. 2021, 10, 1633–1637. [Google Scholar] [CrossRef]
- Zhou, Y.; Pan, C.; Yeoh, P.L.; Wang, K.; Elkashlan, M.; Vucetic, B.; Li, Y. Communication-and-computing latency minimization for UAV-enabled virtual reality delivery systems. IEEE Trans. Commun. 2020, 69, 1723–1735. [Google Scholar] [CrossRef]
- Herich, D.; Vaščák, J. Multi-vehicle SLAM in IoV Networks. In Proceedings of the 2022 Cybernetics & Informatics (K&I), Visegrad, Hungary, 11–14 September 2022; pp. 1–6. [Google Scholar]
- Fotouhi, A.; Qiang, H.; Ding, M.; Hassan, M.; Giordano, L.G.; Garcia-Rodriguez, A.; Yuan, J. Survey on UAV cellular communications: Practical aspects, standardization advancements, regulation, and security challenges. IEEE Commun. Surv. Tutorials 2019, 21, 3417–3442. [Google Scholar] [CrossRef]
- Karim, S.M.; Habbal, A.; Chaudhry, S.A.; Irshad, A. Architecture, protocols, and security in IoV: Taxonomy, analysis, challenges, and solutions. Secur. Commun. Netw. 2022, 2022, 1131479. [Google Scholar] [CrossRef]
- Campanile, L.; Iacono, M.; Marulli, F.; Mastroianni, M. Privacy regulations challenges on data-centric and iot systems: A case study for smart vehicles. In Proceedings of the IoTBDS, Prague, Czech Republic, 7–9 May 2020; pp. 507–518. [Google Scholar]
- Liu, J.; Wang, X.A.; Liu, Z.; Wang, H.; Yang, X. Privacy-preserving public cloud audit scheme supporting dynamic data for unmanned aerial vehicles. IEEE Access 2020, 8, 79428–79439. [Google Scholar] [CrossRef]
- Ahmed, I.; Jeon, G.; Ahmad, A. Deep learning-based intrusion detection system for internet of vehicles. IEEE Consum. Electron. Mag. 2021, 12, 117–123. [Google Scholar] [CrossRef]
- Fu, W.; Xin, X.; Guo, P.; Zhou, Z. A practical intrusion detection system for Internet of vehicles. China Commun. 2016, 13, 263–275. [Google Scholar] [CrossRef]
- Fotohi, R.; Abdan, M.; Ghasemi, S. A self-adaptive intrusion detection system for securing UAV-to-UAV communications based on the human immune system in UAV networks. J. Grid Comput. 2022, 20, 22. [Google Scholar] [CrossRef]
- Whelan, J.; Sangarapillai, T.; Minawi, O.; Almehmadi, A.; El-Khatib, K. Novelty-based intrusion detection of sensor attacks on unmanned aerial vehicles. In Proceedings of the 16th ACM Symposium on QoS and Security for Wireless and Mobile Networks, Alicante Spain, 16–20 November 2020; pp. 23–28. [Google Scholar]
- Basan, E.; Lapina, M.; Mudruk, N.; Abramov, E. Intelligent intrusion detection system for a group of UAVs. In Proceedings of the Advances in Swarm Intelligence: 12th International Conference, ICSI 2021, Qingdao, China, 17–21 July 2021; Proceedings, Part II 12. Springer: Berlin/Heidelberg, Germany, 2021; pp. 230–240. [Google Scholar]
- Ullah, Z.; Al-Turjman, F.; Moatasim, U.; Mostarda, L.; Gagliardi, R. UAVs joint optimization problems and machine learning to improve the 5G and Beyond communication. Comput. Netw. 2020, 182, 107478. [Google Scholar] [CrossRef]
- Li, X.; Zhao, T.; Arora, R.; Liu, H.; Hong, M. On faster convergence of cyclic block coordinate descent-type methods for strongly convex minimization. J. Mach. Learn. Res. 2018, 18, 1–24. [Google Scholar]
- Sharma, D.; Rashid, A.; Gupta, S.; Gupta, S.K. A functional encryption technique in UAV integrated HetNet: A proposed model. Int. J. Simul.-Sci. Technol 2019, 20, 7.1–7.7. [Google Scholar] [CrossRef]
- Xu, F.; Ahmad, S.; Ahmed, M.; Raza, S.; Khan, F.; Ma, Y.; Khan, W.U. Beyond Encryption: Exploring the Potential of Physical Layer Security in UAV Networks. J. King Saud-Univ.-Comput. Inf. Sci. 2023, 35, 101717. [Google Scholar] [CrossRef]
- Samad, A.; Alam, S.; Mohammed, S.; Bhukhari, M. Internet of vehicles (IoV) requirements, attacks and countermeasures. In Proceedings of the 12th INDIACom, INDIACom-2018, 5th International Conference on “Computing for Sustainable Global Development” IEEE Conference, New Delhi, India, 14–16 March 2018; pp. 1–4. [Google Scholar]
- He, Z.; Zou, E.; Guan, C.; Pang, B.; Tang, G.; Ding, J. Research and Application of 5G Remote Control UAV with Aerial Electronic Fence. Proc. J. Physics: Conf. Ser. 2023, 2419, 012109. [Google Scholar] [CrossRef]
- Wang, Q.; Dai, H.N.; Wang, H.; Xu, G.; Sangaiah, A.K. UAV-enabled friendly jamming scheme to secure industrial Internet of Things. J. Commun. Netw. 2019, 21, 481–490. [Google Scholar] [CrossRef]
- Hussain, A.; Abughanam, N.; Sciancalepore, S.; Yaacoub, E.; Mohamed, A. Jammer Localization in the Internet of Vehicles: Scenarios, Experiments, and Evaluation. In Proceedings of the 12th International Conference on the Internet of Things, Delft, The Netherlands, 7–10 November 2022; pp. 73–80. [Google Scholar]
- Xi, N.; Li, W.; Jing, L.; Ma, J. ZAMA: A ZKP-based anonymous mutual authentication scheme for the IoV. IEEE Internet Things J. 2022, 9, 22903–22913. [Google Scholar] [CrossRef]
- Chen, C.M.; Xiang, B.; Liu, Y.; Wang, K.H. A secure authentication protocol for internet of vehicles. IEEE Access 2019, 7, 12047–12057. [Google Scholar] [CrossRef]
- Pitchai, M.P.; Ramachandran, M.; Al-Turjman, F.; Mostarda, L. Intelligent Framework for Secure Transportation Systems Using Software-Defined-Internet of Vehicles. Comput. Mater. Contin. 2021, 68, 3947. [Google Scholar] [CrossRef]
- Vasconcelos, G.; Miani, R.S.; Guizilini, V.C.; Souza, J.R. Evaluation of dos attacks on commercial wi-fi-based uavs. Int. J. Commun. Netw. Inf. Secur. 2019, 11, 212–223. [Google Scholar] [CrossRef]
- Watkins, L.; Ramos, J.; Snow, G.; Vallejo, J.; Robinson, W.H.; Rubin, A.D.; Ciocco, J.; Jedrzejewski, F.; Liu, J.; Li, C. Exploiting multi-vendor vulnerabilities as back-doors to counter the threat of rogue small unmanned aerial systems. In Proceedings of the 1st ACM MobiHoc Workshop on Mobile IoT Sensing, Security, and Privacy, Los Angeles, CA, USA, 26 June 2018; pp. 1–6. [Google Scholar]
- Sakiz, F.; Sen, S. A survey of attacks and detection mechanisms on intelligent transportation systems: VANETs and IoV. Ad Hoc Netw. 2017, 61, 33–50. [Google Scholar] [CrossRef]
- Li, M.; Kou, Y.; Xu, Y.; Liu, Y. Design and field test of a GPS spoofer for UAV trajectory manipulation. In Proceedings of the China Satellite Navigation Conference (CSNC) 2018 Proceedings, Harbin, China, 23–25 May 2018; Volume II; pp. 161–173. [Google Scholar]
- Shrivastava, A. Distributed Denial of Service (DDoS) Attack on Unmanned Aerial Vehicle. Ph.D. Thesis, Delhi Technological University, New Delhi, India, 2022. [Google Scholar]
- Jameii, S.M.; Zamirnaddafi, R.S.; Rezabakhsh, R. Internet of Flying Things security: A systematic review. Concurr. Comput. Pract. Exp. 2022, 34, e7213. [Google Scholar] [CrossRef]
- Shafiee, M.; Zhou, Z.; Mei, L.; Dinmohammadi, F.; Karama, J.; Flynn, D. Unmanned aerial drones for inspection of offshore wind turbines: A mission-critical failure analysis. Robotics 2021, 10, 26. [Google Scholar] [CrossRef]
- Hussain, S.A.; Yusof, K.M.; Hussain, S.M.; Singh, A.V. A review of quality of service issues in Internet of Vehicles (IoV). In Proceedings of the 2019 Amity International Conference on Artificial Intelligence (AICAI), Dubai, United Arab Emirates, 4–6 February 2019; pp. 380–383. [Google Scholar]
- Zavvos, E.; Gerding, E.H.; Yazdanpanah, V.; Maple, C.; Stein, S. Privacy and Trust in the Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 23, 10126–10141. [Google Scholar] [CrossRef]
- Dahmane, S.; Yagoubi, M.B.; Kerrache, C.A.; Lorenz, P.; Lagraa, N.; Lakas, A. Toward a Secure Edge-Enabled and Artificially Intelligent Internet of Flying Things Using Blockchain. IEEE Internet Things Mag. 2022, 5, 90–95. [Google Scholar] [CrossRef]
- Mfenjou, M.L.; Ari, A.A.A.; Abdou, W.; Spies, F. Methodology and trends for an intelligent transport system in developing countries. Sustain. Comput. Inform. Syst. 2018, 19, 96–111. [Google Scholar] [CrossRef]
- Hahn, D.; Munir, A.; Behzadan, V. Security and privacy issues in intelligent transportation systems: Classification and challenges. IEEE Intell. Transp. Syst. Mag. 2019, 13, 181–196. [Google Scholar] [CrossRef]
- Rejeb, A.; Abdollahi, A.; Rejeb, K.; Treiblmaier, H. Drones in agriculture: A review and bibliometric analysis. Comput. Electron. Agric. 2022, 198, 107017. [Google Scholar] [CrossRef]
- Pathak, H.; Kumar, G.; Mohapatra, S.; Gaikwad, B.; Rane, J. Use of drones in agriculture: Potentials, Problems and Policy Needs. Icar-Natl. Inst. Abiotic Stress Manag. 2020, 300, 4–15. [Google Scholar]
- Chyrva, I.; Jermy, M.; Strand, T.; Richardson, B. Evaluation of the pattern of spray released from a moving multicopter. Pest Manag. Sci. 2023, 79, 1483–1499. [Google Scholar] [CrossRef] [PubMed]
- Bai, Y.; Zhang, B.; Xu, N.; Zhou, J.; Shi, J.; Diao, Z. Vision-based navigation and guidance for agricultural autonomous vehicles and robots: A review. Comput. Electron. Agric. 2023, 205, 107584. [Google Scholar] [CrossRef]
- Ghobadpour, A.; Monsalve, G.; Cardenas, A.; Mousazadeh, H. Off-road electric vehicles and autonomous robots in agricultural sector: Trends, challenges, and opportunities. Vehicles 2022, 4, 843–864. [Google Scholar] [CrossRef]
- Moshref-Javadi, M.; Winkenbach, M. Applications and Research avenues for drone-based models in logistics: A classification and review. Expert Syst. Appl. 2021, 177, 114854. [Google Scholar] [CrossRef]
- Sah, B.; Gupta, R.; Bani-Hani, D. Analysis of barriers to implement drone logistics. Int. J. Logist. Res. Appl. 2021, 24, 531–550. [Google Scholar] [CrossRef]
- Manjrekar, A.; Jha, D.S.; Jagtap, P.; Yadav, V. Warehouse inventory management with cycle counting using drones. In Proceedings of the 4th International Conference on Advances in Science & Technology (ICAST2021), Bahir Dar, Ethiopia, 27–29 August 2021. [Google Scholar]
- Deja, M.; Siemiątkowski, M.S.; Vosniakos, G.C.; Maltezos, G. Opportunities and challenges for exploiting drones in agile manufacturing systems. Procedia Manuf. 2020, 51, 527–534. [Google Scholar] [CrossRef]
- Ali, S.S.; Khan, S.; Fatma, N.; Ozel, C.; Hussain, A. Utilisation of drones in achieving various applications in smart warehouse management. Benchmarking Int. J. 2023. [CrossRef]
- Zhang, T. Toward automated vehicle teleoperation: Vision, opportunities, and challenges. IEEE Internet Things J. 2020, 7, 11347–11354. [Google Scholar] [CrossRef]
- Alkouz, B.; Bouguettaya, A.; Mistry, S. Swarm-based drone-as-a-service (sdaas) for delivery. In Proceedings of the 2020 IEEE International Conference on Web Services (ICWS), Beijing, China, 19–23 October 2020; pp. 441–448. [Google Scholar]
- Baldisseri, A.; Siragusa, C.; Seghezzi, A.; Mangiaracina, R.; Tumino, A. Truck-based drone delivery system: An economic and environmental assessment. Transp. Res. Part D Transp. Environ. 2022, 107, 103296. [Google Scholar] [CrossRef]
- Nyaaba, A.A.; Ayamga, M. Intricacies of medical drones in healthcare delivery: Implications for Africa. Technol. Soc. 2021, 66, 101624. [Google Scholar] [CrossRef]
- Euchi, J. Do drones have a realistic place in a pandemic fight for delivering medical supplies in healthcare systems problems? Chin. J. Aeronaut. 2021, 34, 182–190. [Google Scholar] [CrossRef]
- Khalid, M.; Awais, M.; Singh, N.; Khan, S.; Raza, M.; Malik, Q.B.; Imran, M. Autonomous transportation in emergency healthcare services: Framework, challenges, and future work. IEEE Internet Things Mag. 2021, 4, 28–33. [Google Scholar] [CrossRef]
- Rahman, M.M.; Khatun, F.; Sami, S.I.; Uzzaman, A. The evolving roles and impacts of 5G enabled technologies in healthcare: The world epidemic COVID-19 issues. Array 2022, 14, 100178. [Google Scholar] [CrossRef] [PubMed]
- Carr, C.; Samnani, M.; Tani, J.; McKaig, J.; Hammons, E.; Newman, D.J.; Ho, K.; Ekblaw, A.; Truelove, N. Space Drones: An Opportunity to Include, Engage, Accelerate, and Advance. EHT Zurich 2020. [Google Scholar]
- De Simone, C.; Ceci, F.; Alaimo, C. Data Ecosystem and Data Value Chain: An Exploration of Drones Technology Applications. In Sustainable Digital Transformation: Paving the Way Towards Smart Organizations and Societies; Springer: Berlin/Heidelberg, Germany, 2022; pp. 203–218. [Google Scholar]
- Galvez-Serna, J.; Vanegas, F.; Gonzalez, F.; Flannery, D. Towards a probabilistic based autonomous UAV mission planning for planetary exploration. In Proceedings of the 2021 IEEE Aerospace Conference (50100), Big Sky, MT, USA, 6–13 March 2021; pp. 1–8. [Google Scholar]
- Feraru, V.A.; Andersen, R.E.; Boukas, E. Towards an autonomous UAV-based system to assist search and rescue operations in man overboard incidents. In Proceedings of the 2020 IEEE International Symposium on Safety, Security, and Rescue Robotics (SSRR), Abu Dhabi, United Arab Emirates, 4–6 November 2020; pp. 57–64. [Google Scholar]
- Valsan, A.; Parvathy, B.; GH, V.D.; Unnikrishnan, R.; Reddy, P.K.; Vivek, A. Unmanned aerial vehicle for search and rescue mission. In Proceedings of the 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI) (48184), Tirunelveli, India, 15–17 June 2020; pp. 684–687. [Google Scholar]
- Ilkhanizadeh, S.; Golabi, M.; Hesami, S.; Rjoub, H. The potential use of drones for tourism in crises: A facility location analysis perspective. J. Risk Financ. Manag. 2020, 13, 246. [Google Scholar] [CrossRef]
- Ashtari, A.; Stevšić, S.; Nägeli, T.; Bazin, J.C.; Hilliges, O. Capturing subjective first-person view shots with drones for automated cinematography. ACM Trans. Graph. 2020, 39, 1–14. [Google Scholar] [CrossRef]
- Wang, G.; Yang, Y.; Wang, S. Ocean thermal energy application technologies for unmanned underwater vehicles: A comprehensive review. Appl. Energy 2020, 278, 115752. [Google Scholar] [CrossRef]
- Bisio, I.; Garibotto, C.; Haleem, H.; Lavagetto, F.; Sciarrone, A. A systematic review of drone based road traffic monitoring system. IEEE Access 2022, 10, 101537–101555. [Google Scholar] [CrossRef]
- Ahmed, H.U.; Huang, Y.; Lu, P.; Bridgelall, R. Technology developments and impacts of connected and autonomous vehicles: An overview. Smart Cities 2022, 5, 382–404. [Google Scholar] [CrossRef]
- Burd, J.T. Regulatory sandboxes for safety assurance of autonomous vehicles. Univ. Pa. J. Law Public Aff. 2021, 7, 194. [Google Scholar]
- Mahmood, Z. Connected vehicles in the IoV: Concepts, technologies and architectures. In Connected Vehicles in the Internet of Things: Concepts, Technologies and Frameworks for the IoV; Springer: Berlin/Heidelberg, Germany, 2020; pp. 3–18. [Google Scholar]
- Jones, T. International Commercial Drone Regulation and Drone Delivery Services; Technical Report; RAND: Santa Monica, CA, USA, 2017. [Google Scholar]
- Calandrillo, S.; Oh, J.; Webb, A. Deadly drones: Why faa regulations miss the mark on drone safety. Stan. Tech. L. Rev. 2020, 23, 182. [Google Scholar]
- Konert, A.; Dunin, T. A harmonized european drone market?–new EU rules on unmanned aircraft systems. Adv. Sci. Technol. Eng. Syst. J. 2020, 5, 93–99. [Google Scholar] [CrossRef]
- Shafik, W.; Matinkhah, S.M.; Shokoor, F. Cybersecurity in unmanned aerial vehicles: A review. Int. J. Smart Sens. Intell. Syst. 2023, 16. [Google Scholar] [CrossRef]
- Attrey, A.; Lesher, M.; Lomax, C. The Role of Sandboxes in Promoting Flexibility and Innovation in the Digital Age; OECD: Paris, France, 2020. [Google Scholar]
- Konert, A.; Kotliński, M. U-Space–Civil Liability for damages caused by Unmanned Aircraft. Transp. Res. Procedia 2020, 51, 304–312. [Google Scholar] [CrossRef]
- De Naeyer, V.S. Implementing Cooperative Intelligent Transportation Systems: A Maturity Model for Assessing the Readiness of Cities. Available online: https://digikogu.taltech.ee/et/Download/372dcfcf-214f-406d-b1b9-f01999c927b2/Koostalitavatejanutikatetranspordissteemidera.pdf (accessed on 14 January 2024).
- Shrestha, R.; Bajracharya, R.; Kim, S. 6G enabled unmanned aerial vehicle traffic management: A perspective. IEEE Access 2021, 9, 91119–91136. [Google Scholar] [CrossRef]
- Gohar, A.; Nencioni, G. The role of 5G technologies in a smart city: The case for intelligent transportation system. Sustainability 2021, 13, 5188. [Google Scholar] [CrossRef]
- Yuan, T.; Da Rocha Neto, W.; Rothenberg, C.E.; Obraczka, K.; Barakat, C.; Turletti, T. Machine learning for next-generation intelligent transportation systems: A survey. Trans. Emerg. Telecommun. Technol. 2022, 33, e4427. [Google Scholar] [CrossRef]
- Chen, S.; Hu, J.; Shi, Y.; Zhao, L.; Li, W. A vision of C-V2X: Technologies, field testing, and challenges with Chinese development. IEEE Internet Things J. 2020, 7, 3872–3881. [Google Scholar] [CrossRef]
- Rymer, N.; Moore, A.; Young, S.; Glaab, L.; Smalling, K.; Consiglio, M. Demonstration of two extended visual line of sight methods for urban UAV operations. In Proceedings of the AIAA AVIATION 2020 FORUM, Online, 15–19 June 2020; p. 2889. [Google Scholar]
- Alkadi, R.; Shoufan, A. Unmanned aerial vehicles traffic management solution using crowd-sensing and blockchain. IEEE Trans. Netw. Serv. Manag. 2022, 20, 201–215. [Google Scholar] [CrossRef]
- Li, X.; Gong, L.; Liu, X.; Jiang, F.; Shi, W.; Fan, L.; Gao, H.; Li, R.; Xu, J. Solving the last mile problem in logistics: A mobile edge computing and blockchain-based unmanned aerial vehicle delivery system. Concurr. Comput. Pract. Exp. 2022, 34, e6068. [Google Scholar] [CrossRef]
- Guillermo, B.; Jan, V.; Han, V.; Irena, K. Smart building and district retrofitting for intelligent urban environments. In Intelligent Environments; Elsevier: Amsterdam, The Netherlands, 2023; pp. 395–420. [Google Scholar]
- Gholamhosseinian, A.; Seitz, J. Vehicle classification in intelligent transport systems: An overview, methods and software perspective. IEEE Open J. Intell. Transp. Syst. 2021, 2, 173–194. [Google Scholar] [CrossRef]
- Nogar, S.M. Autonomous landing of a uav on a moving ground vehicle in a gps denied environment. In Proceedings of the 2020 IEEE International Symposium on Safety, Security, and Rescue Robotics (SSRR), Abu Dhabi, United Arab Emirates, 4–6 November 2020; pp. 77–83. [Google Scholar]
- Gonzalez, R.A.; Ferro, R.E.; Liberona, D. Government and governance in intelligent cities, smart transportation study case in Bogotá Colombia. Ain Shams Eng. J. 2020, 11, 25–34. [Google Scholar] [CrossRef]

| Feature | VANET | FANET | IoV | IoFV |
|---|---|---|---|---|
| Type of network | Vehicular | Flying | Vehicular | Flying |
| Communication range | Short | Medium to Long | Short to Medium | Medium to Long |
| Mobility | Road-based | Air-based | Road-based | Air-based |
| Infrastructure | Roadside units | Limited ground infrastructure | Roadside units, Cloud | Ground stations, Cloud |
| Challenges | Signal obstruction, | Limited energy, | Signal interference, | Limited energy, |
| Interference, | Collision avoidance | Dynamic topology changes, | Communication security concerns | |
| Dynamic topology changes | Security concerns | |||
| Applications | Intelligent Transportation Systems, | Surveillance, | Traffic management, | Surveillance, |
| Emergency services | Environmental monitoring | Fleet management, | Environmental monitoring, | |
| Safety applications | Disaster response |
| Reference | Layers | Applications |
|---|---|---|
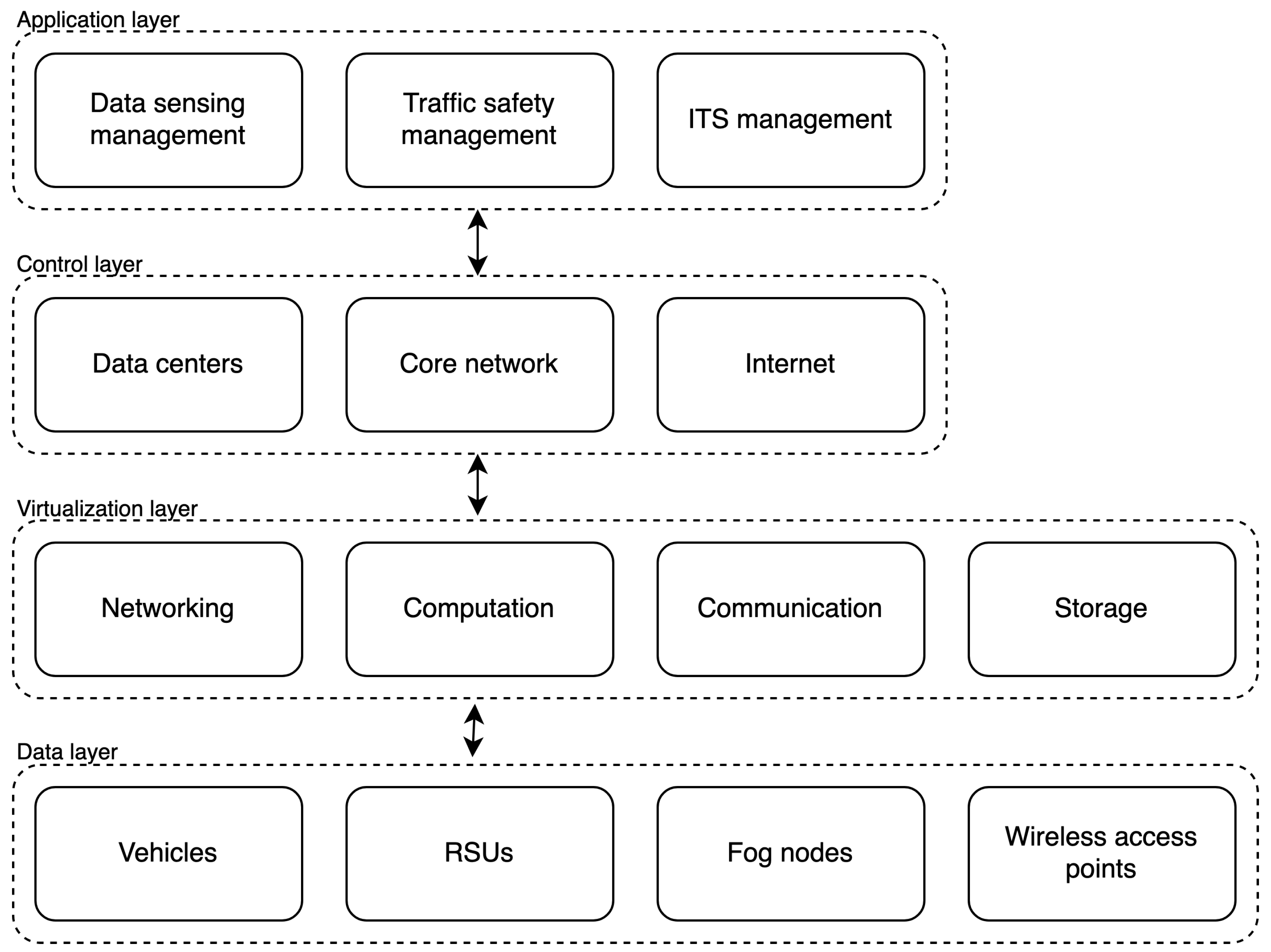
| [44] | Data, Virtualization, Control, Application | See-Through, Collision Warning |
| [45] | Sensing, Communication, Cognition, Control, Application | Safety, Transportation Management |
| [46] | Perception, Communication, Application | Vehicle Collaboration |
| [47] | User, Data Acquisition, Filtering, Communication, Control, Processing | Traffic Efficiency, Safety |
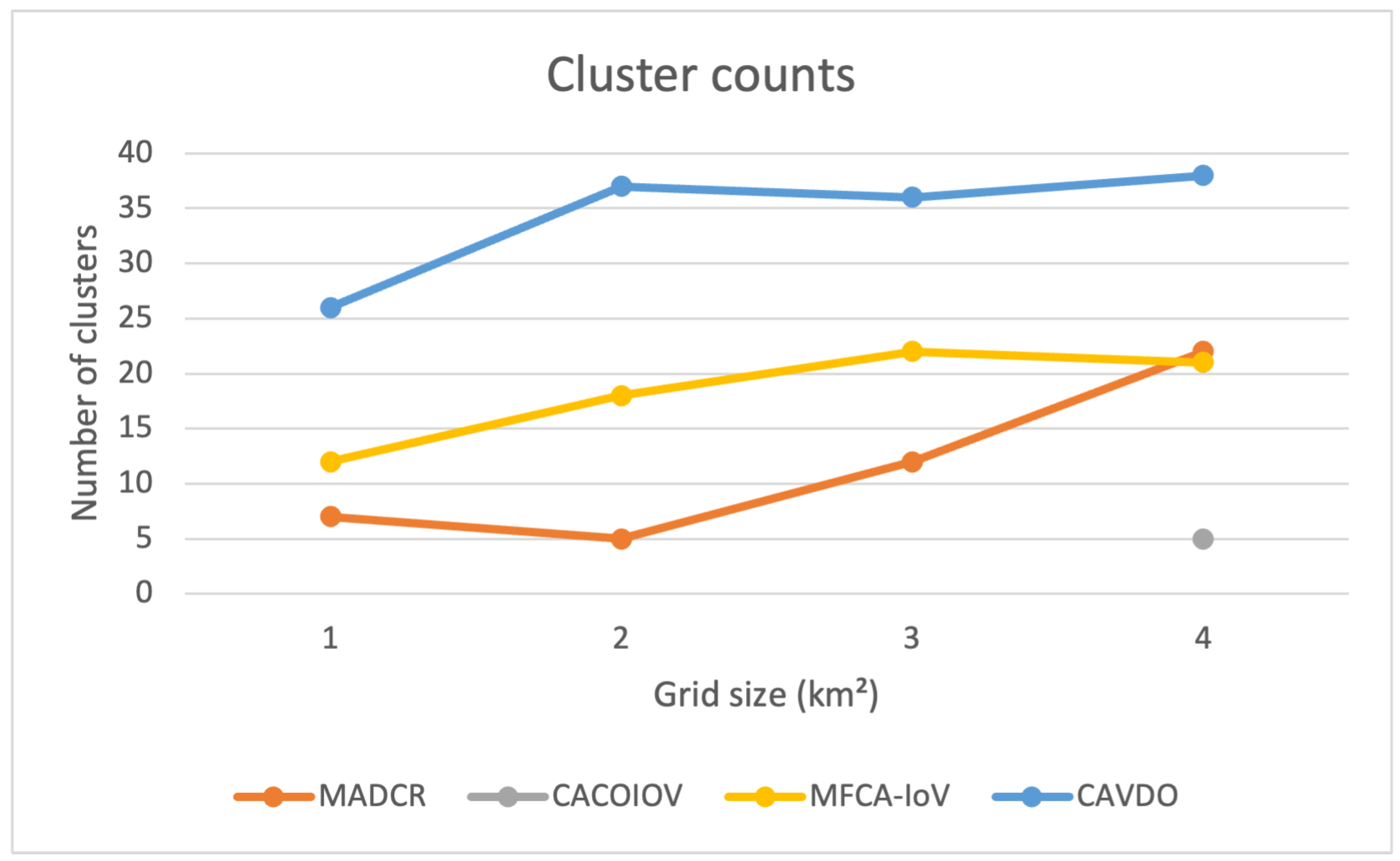
| System | Algorithm | WoS | Scopus | Year | Citations WoS | Citations Scopus | Reference |
|---|---|---|---|---|---|---|---|
| EC-MOPSO | PSO | Yes | Yes | 2022 | 2 | 1 | [74] |
| MADCR | MOA | Yes | Yes | 2021 | 7 | 11 | [75] |
| AFS Clustering | AFS | No | Yes | 2020 | - | 3 | [76] |
| CACOIOV | ACO | Yes | Yes | 2019 | 13 | 19 | [77] |
| MFCA-IoV | MFO | Yes | Yes | 2019 | 31 | 38 | [78] |
| CAVDO | DFO | Yes | Yes | 2018 | 52 | 64 | [79] |
| Parameter | EC-MOPSO | MADCR | AFS Clustering | CACOIOV | MFCA-IoV | CAVDO |
|---|---|---|---|---|---|---|
| Grid size (km × km) | 1 | 1, 2, 3, 4 | 1 | 4 | 1, 2, 3, 4 | 1, 2, 3, 4 |
| Vehicles (count) | 50–100 | 30–60 | 30–60 | 40–200 | 30–60 | 30–60 |
| Speed (km/h) | 30–100 | 72–108 | 30–50 | 79.2–108 | 79.2–108 | 79.2–108 |
| Communication Range (m) | 200 | Dynamic | 100–600 | Dynamic | Dynamic | Dynamic |
| Mobility Model | Urban | Freeway | Urban | Freeway | Freeway | Freeway |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Herich, D.; Vaščák, J. The Evolution of Intelligent Transportation Systems: Analyzing the Differences and Similarities between IoV and IoFV. Drones 2024, 8, 34. https://doi.org/10.3390/drones8020034
Herich D, Vaščák J. The Evolution of Intelligent Transportation Systems: Analyzing the Differences and Similarities between IoV and IoFV. Drones. 2024; 8(2):34. https://doi.org/10.3390/drones8020034
Chicago/Turabian StyleHerich, Dušan, and Ján Vaščák. 2024. "The Evolution of Intelligent Transportation Systems: Analyzing the Differences and Similarities between IoV and IoFV" Drones 8, no. 2: 34. https://doi.org/10.3390/drones8020034
APA StyleHerich, D., & Vaščák, J. (2024). The Evolution of Intelligent Transportation Systems: Analyzing the Differences and Similarities between IoV and IoFV. Drones, 8(2), 34. https://doi.org/10.3390/drones8020034







