A Data Normalization Technique for Detecting Cyber Attacks on UAVs
Abstract
:1. Introduction
- Collection of data from UAV subsystems and sensors;
- Data aggregation for further analysis;
- Normalization of collected data;
- Recording data in a format convenient for further use.
- Attacks on integrity: This kind of attack leads to changes in the original information or the initial state of the system, which can produce distortions of information and violations of the properties of the system [7].
- Attacks on availability: These attacks block the operation of services, resources and executive mechanisms, or they prevent the ability to access necessary resources [8].
- Attacks on confidentiality: These attacks are aimed at obtaining information about the system. They do not implement any active actions aimed at violating the functionality of the system, but they only receive valuable information about it [9].
- Resource exhaustion attacks: Such attacks aim to increase the use of UAV resources. Although UAV functionality may not be violated, power consumption increases [10].
- Access attacks: These are similar to confidentiality attacks, but instead of passively obtaining information about the system, an access attack actively intrudes the system to obtain intelligence information [11].
- An experimental study of the impact of attacks on UAV parameters;
- A software module for collecting data from UAVs;
- A technique for normalizing and presenting data for detecting attacks on UAVs.
2. Materials and Methods
2.1. Ontological Model of the UAV Data Collection System for Attack Detection
2.2. Formalization of the Attack Model
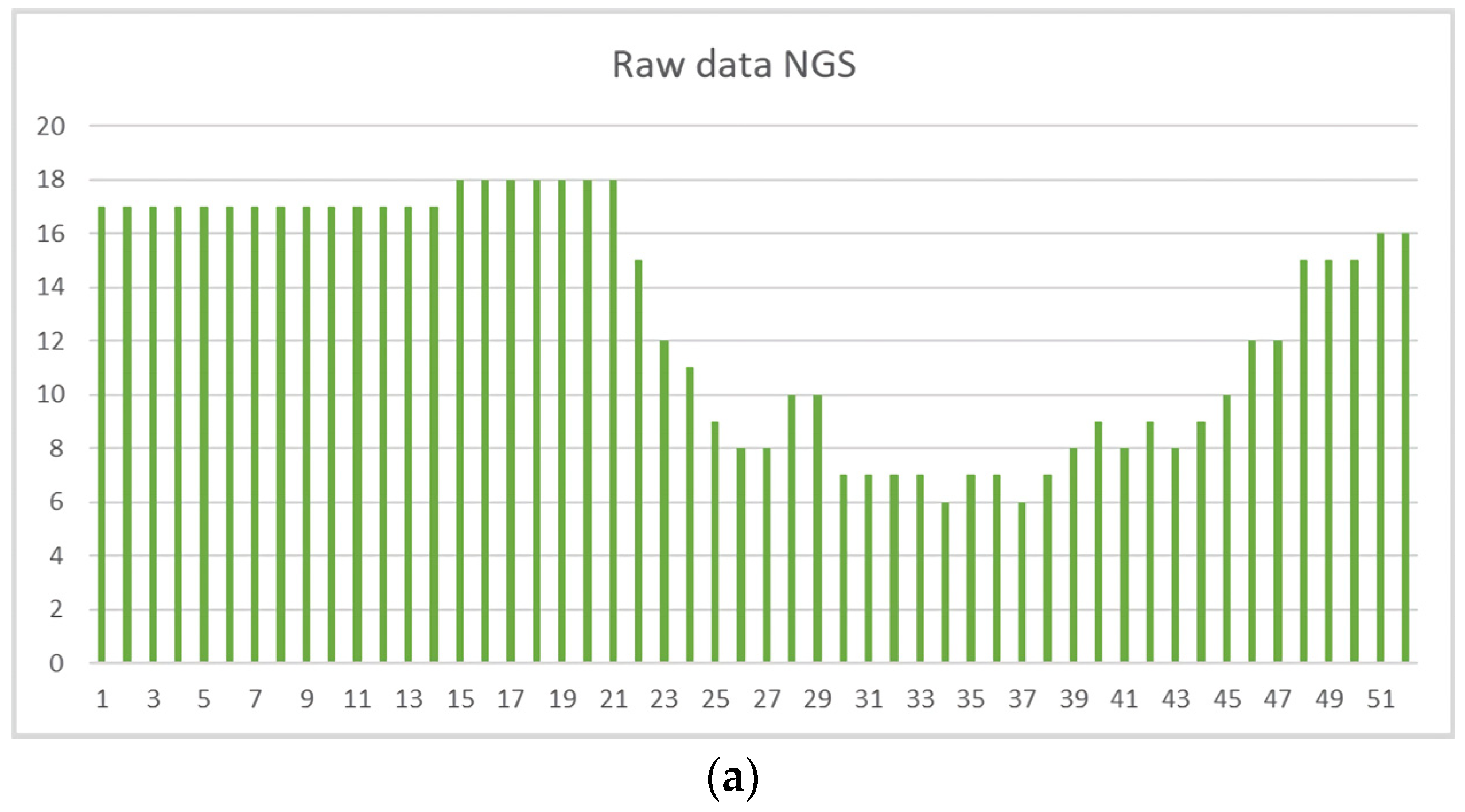
2.3. Raw Data Normalization Technique for Detecting Attacks on UAVs
- The data collection module receives cyber-physical parameters from the flight controller.
- The resulting data flow is recorded in the database for further processing.
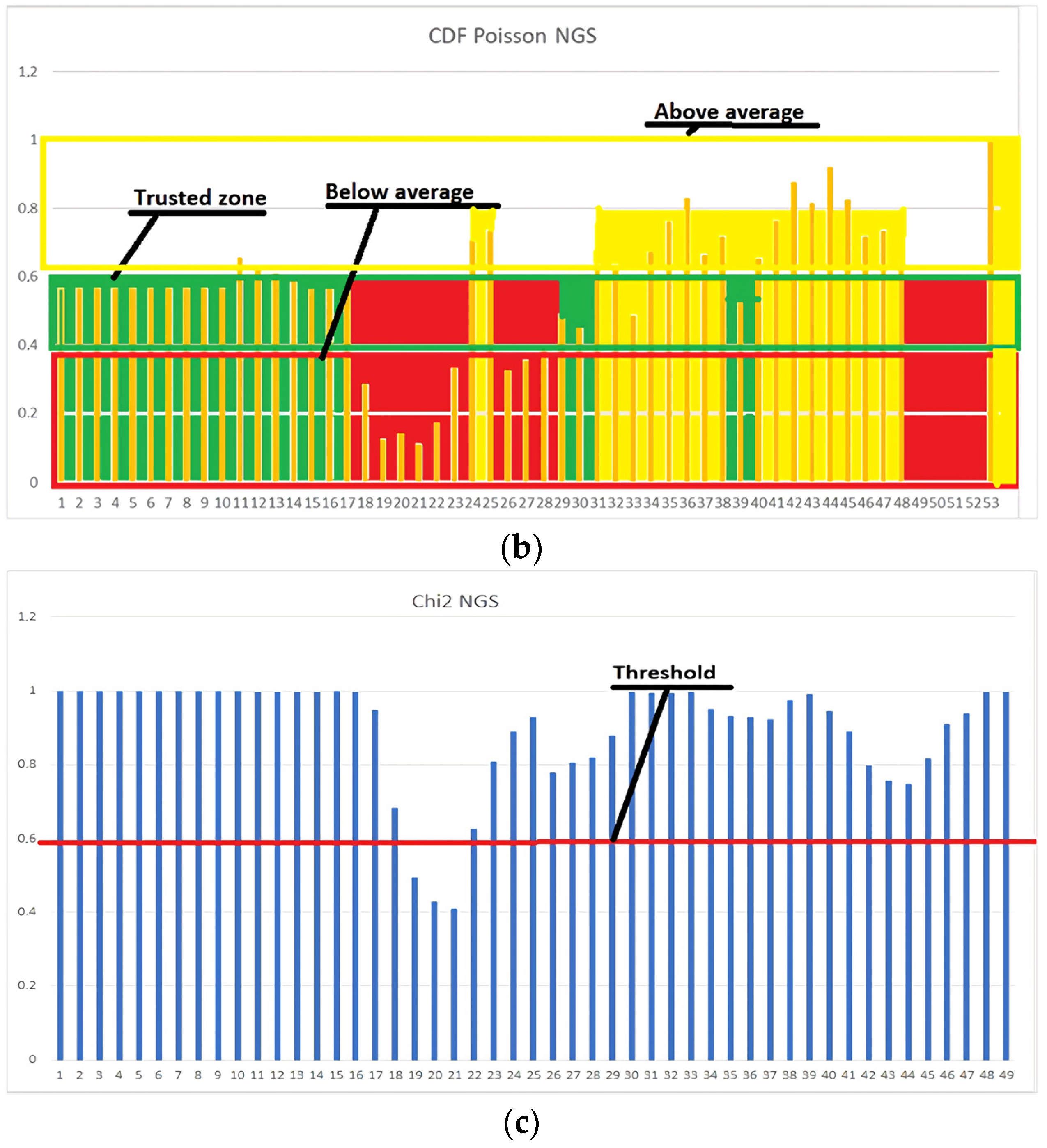
- The data normalization module uses Equation (2) from Table 2 to determine the presence of critical changes in the data set.
- If Condition 1 of Equation (6) is fulfilled for χ2, then the data set can be classified as normal.
- If Condition 1 of Equation (6) is not fulfilled for χ2, then Condition 2 is checked for the cumulative distribution of Poisson according to Equation (3) from Table 2.
- If Condition 2 for the cumulative distribution of Poisson is fulfilled, then we identify the set of data as abnormal.
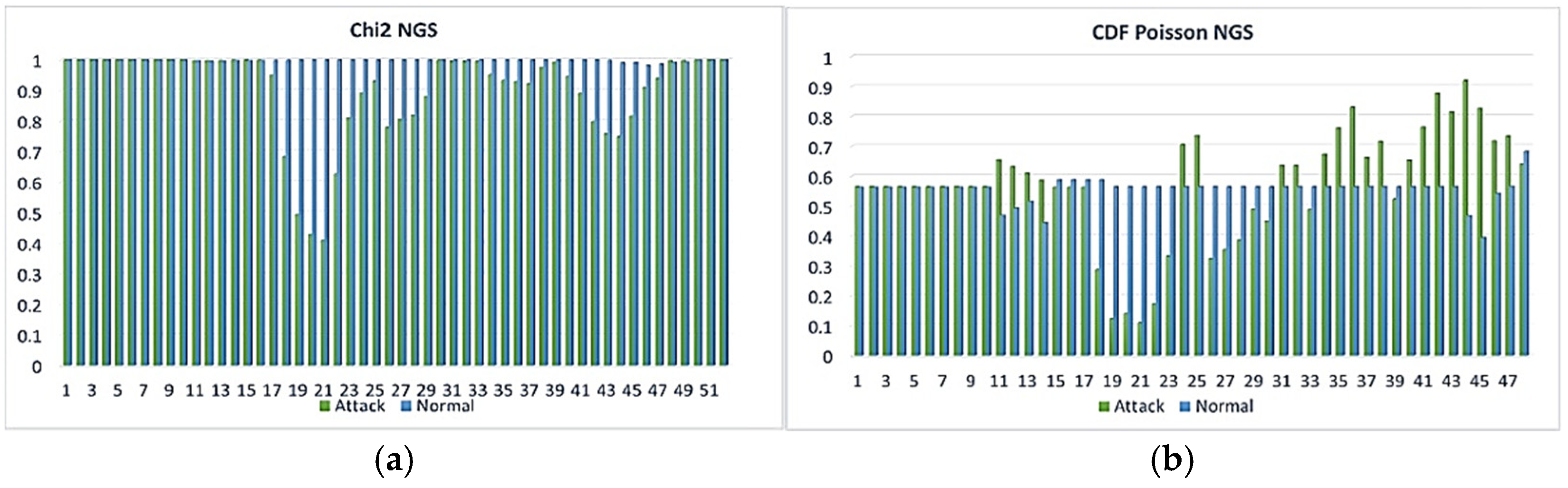
- If Steps 5 and 6 are performed for the latitude, longitude and flight speed parameters, then we can conclude that there is a Spoofing attack in progress [28].
- If Steps 5 and 6 are performed for the signal level, flight height and flight speed parameters, then we can conclude that there is a Jamming attack in progress [28].
- The results are written into the database.
3. Results
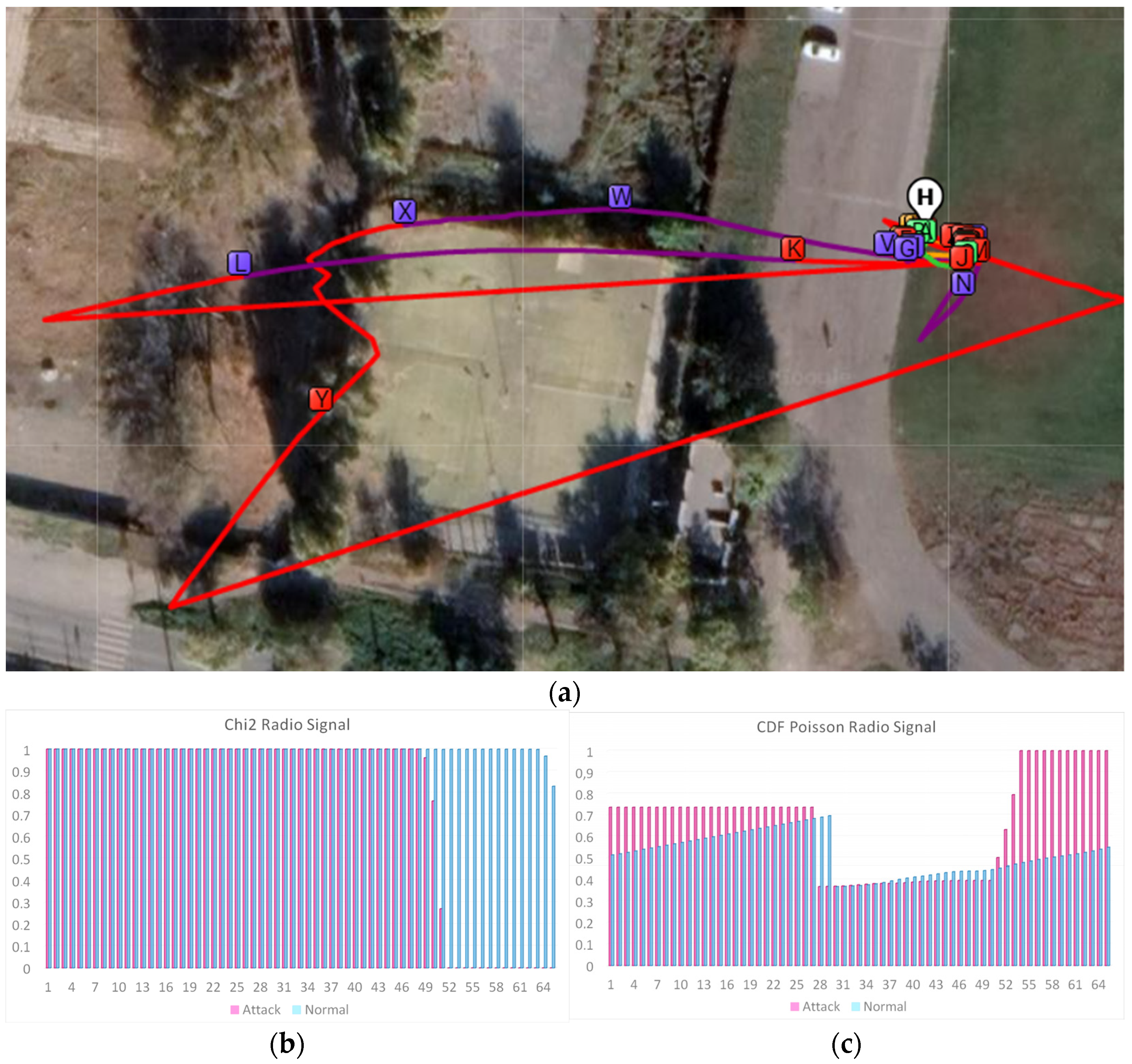
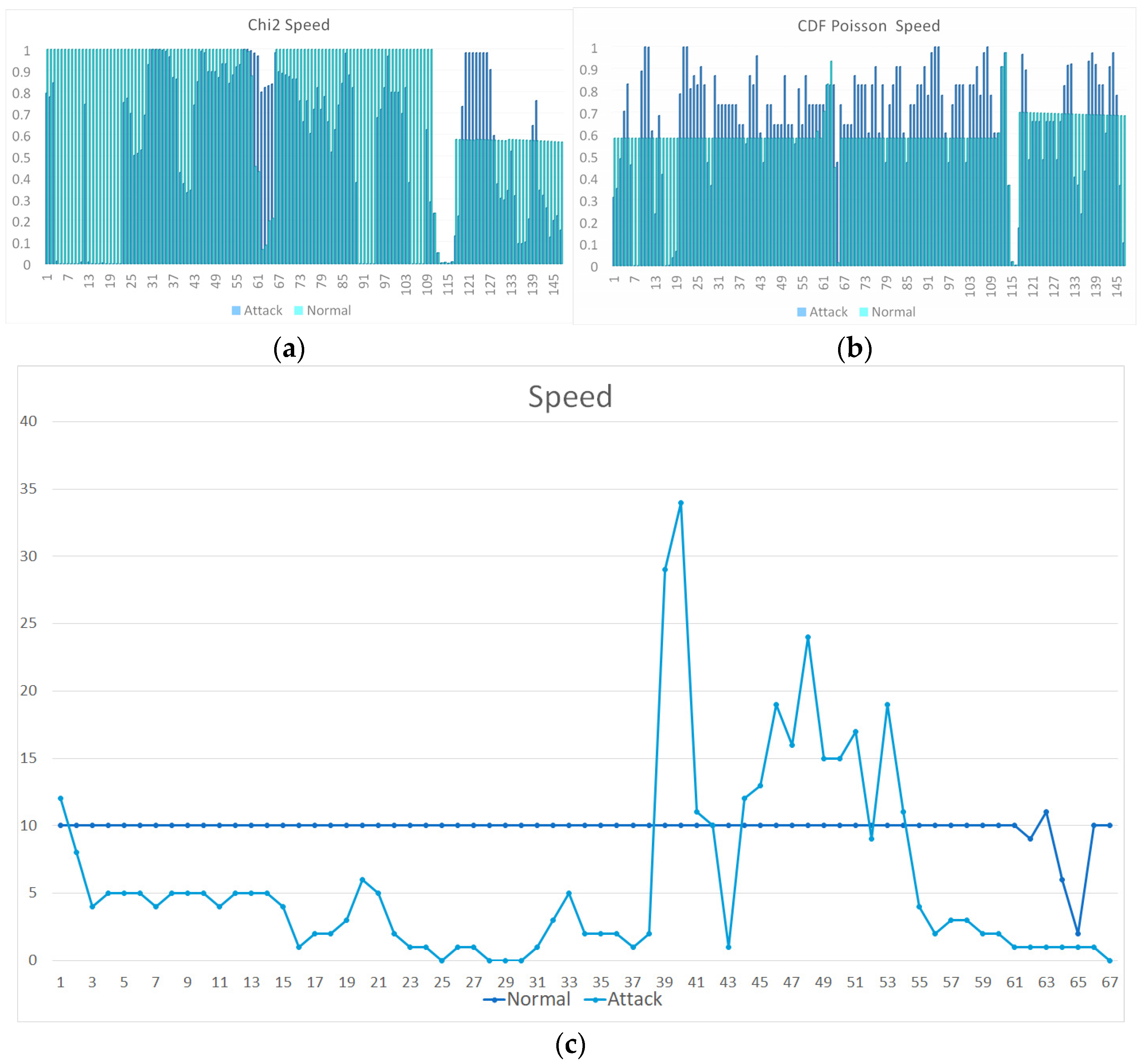
3.1. Attack Scenarios
3.2. Analysis of Experimental Data
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Biermann, E.; Cloete, E.; Venter, L.M. A comparison of intrusion detection systems. Comput. Secur. 2001, 20, 676–683. [Google Scholar] [CrossRef]
- Debar, H.; Dacier, M.; Wespi, A. Towards a taxonomy of intrusion-detection systems. Comput. Netw. 1999, 31, 805–822. [Google Scholar] [CrossRef]
- Zdrodowska, M.; Dardzińska, A.; Kasperczuk, A. Using data mining tools in wall-following robot navigation data set. In Proceedings of the 2020 International Conference Mechatronic Systems and Materials (MSM 2020), Bialystok, Poland, 1–3 July 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Li, M.; Wang, H.; Li, J. Mining conditional functional dependency rules on big data. Big Data Min. Anal. 2020, 3, 68–84. [Google Scholar] [CrossRef]
- Nguyen, V.-L.; Lin, P.-C.; Hwang, R.-H. Energy depletion attacks in low power wireless networks. IEEE Access 2019, 7, 51915–51932. [Google Scholar] [CrossRef]
- Hooper, M.; Tian, Y.; Zhou, R.; Cao, B.; Lauf, A.P.; Watkins, L.; Robinson, W.H.; Alexis, W. Securing commercial WiFi-based UAVs from common security attacks. In Proceedings of the 2016 IEEE Military Communications Conference (MILCOM 2016), Baltimore, MD, USA, 1–3 November 2016; pp. 1213–1218. [Google Scholar] [CrossRef]
- Maxa, J.-A.; Mahmoud, M.S.B.; Larrieu, N. Performance evaluation of a new secure routing protocol for UAV Ad hoc Network. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC 2019), San Diego, CA, USA, 8–12 September 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Jue, L.; Weiwei, Y. Hierarchical reinforcement learning framework for secure UAV communication in the presence of multiple UAV adaptive eavesdroppers. In Proceedings of the 2020 IEEE 6th International Conference on Computer and Communications (ICCC 2020), Chengdu, China, 11–14 December 2020; pp. 1532–1536. [Google Scholar] [CrossRef]
- Li, T.; Zhang, J.; Obaidat, M.S.; Lin, C.; Lin, Y.; Shen, Y.; Ma, J. Energy-efficient and secure communication towards UAVs networks. IEEE Internet Things J. 2022, 9, 10061–10076. [Google Scholar] [CrossRef]
- Tanabe, M.; Aida, M. Preventing resource exhaustion attacks in Ad Hoc networks. In Proceedings of the 8th International Symposium on Autonomous Decentralized Systems (ISADS’07), Sedona, AZ, USA, 21–23 March 2007; pp. 543–548. [Google Scholar] [CrossRef]
- Din, N.; Waheed, A.; Zareei, M.; Alanazi, F. An improved identity-based generalized signcryption scheme for secure multi-access edge computing empowered flying Ad Hoc networks. IEEE Access 2021, 9, 120704–120714. [Google Scholar] [CrossRef]
- Zhang, R.; Condomines, J.-P.; Lochin, E. A multifractal analysis and machine learning based intrusion detection system with an application in a UAS/RADAR system. Drones 2022, 6, 21. [Google Scholar] [CrossRef]
- Aissou, G.; Slimane, H.O.; Benouadah, S.; Kaabouch, N. Tree-based supervised machine learning models for detecting GPS spoofing attacks on UAS. In Proceedings of the 2021 IEEE 12th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON 2021), New York, NY, USA, 1–4 December 2021; pp. 0649–0653. [Google Scholar] [CrossRef]
- Aissou, G.; Benouadah, S.; Alami, H.E.; Kaabouch, N. Instance-based supervised machine learning models for detecting GPS spoofing attacks on UAS. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC 2022), Las Vegas, NV, USA, 26–29 January 2022; pp. 0208–0214. [Google Scholar] [CrossRef]
- Khoei, T.T.; Ismail, S.; Kaabouch, N. Dynamic selection techniques for detecting GPS spoofing attacks on UAVs. Sensors 2022, 22, 662. [Google Scholar] [CrossRef] [PubMed]
- Whelan, J.; Sangarapillai, T.; Minawi, O.; Almehmadi, A.M.; El-Khatib, K.M. Novelty-based intrusion detection of sensor attacks on unmanned aerial vehicles. In Proceedings of the 16th ACM Symposium on QoS and Security for Wireless and Mobile Networks (Q2SWinet’20), Alicante, Spain, 16–20 November 2020; pp. 23–28. [Google Scholar] [CrossRef]
- Tippenhauer, N.O.; Pöpper, C.; Rasmussen, K.B.; Capkun, S. On the requirements for successful GPS spoofing attacks. In Proceedings of the 18th ACM conference on Computer and Communications Security (CCS’11), Chicago, IL, USA, 17–21 October 2011; pp. 75–86. [Google Scholar] [CrossRef]
- Kerns, A.J.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Unmanned aircraft capture and control via GPS spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Basan, E.; Makarevich, O.; Lapina, M.; Mecella, M. Analysis of the impact of a GPS spoofing attack on a UAV. CEUR Workshop Proc. 2022, 3094, 6–16. Available online: http://ceur-ws.org/Vol-3094/invited_paper.pdf (accessed on 26 August 2022).
- Park, K.H.; Park, E.; Kim, H.K. Unsupervised intrusion detection system for unmanned aerial vehicle with less labeling effort. In Information Security Applications—21st International Conference, WISA 2020, Revised Selected Papers; You, I., Ed.; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer Science and Business Media Deutschland GmbH: Cham, Switzerland, 2020; Volume 12583, LNCS; pp. 45–58. [Google Scholar] [CrossRef]
- Wang, P. Speech separation for aerodrome traffic control recordings by auxiliary function based independent vector analysis. In Proceedings of the 2019 IEEE 1st International Conference on Civil Aviation Safety and Information Technology (ICCASIT 2019), Kunming, China, 17–19 October 2019; pp. 12–16. [Google Scholar] [CrossRef]
- Penglong, L.; Yi, D.; Songjiang, D.; Ding, L.; Ziwei, J.; Yong, X. A method of rapid distortion correction for UAV image based on GPU-CPU co-processing technology. In Proceedings of the 2018 IEEE International Geoscience and Remote Sensing Symposium (IGARSS 2018), Valencia, Spain, 22–27 July 2018; pp. 5720–5723. [Google Scholar] [CrossRef]
- Basan, E.; Abramov, E.; Basyuk, A.; Sushkin, N. Spoofing attack detection method for UAV navigation system. Inform. Autom. 2021, 20, 1368–1394. [Google Scholar] [CrossRef]
- Sedjelmaci, H.; Senouci, S.M.; Ansari, N. Intrusion detection and ejection framework against lethal attacks in UAV-aided networks: A Bayesian game-theoretic methodology. IEEE Trans. Intell. Transport. Syst. 2016, 18, 1143–1153. [Google Scholar] [CrossRef]
- Forthofer, R.N.; Lee, E.S.; Hernandez, M. Biostatistics: A Guide to Design, Analysis, and Discovery, 2nd ed.; Academic Press: San Diego, CA, USA, 2007; p. 502. [Google Scholar] [CrossRef]
- Abeywickrama, H.V.; Jayawickrama, B.A.; He, Y.; Dutkiewicz, E. Empirical power consumption model for UAVs. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall 2018), Chicago, IL, USA, 27–30 August 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Mehrooz, G.; Ebeid, E.; Schneider-Kamp, P. System design of an open-source cloud-based framework for internet of drones application. In Proceedings of the 22nd Euromicro Conference on Digital System Design (DSD 2019), Kallithea, Greece, 28–30 August 2019; pp. 572–579. [Google Scholar] [CrossRef]
- Gamec, J.; Basan, E.; Basan, A.; Nekrasov, A.; Fidge, C.; Sushkin, N. An adaptive protection system for sensor networks based on analysis of neighboring nodes. Sensors 2021, 21, 6116. [Google Scholar] [CrossRef] [PubMed]
- Basan, E.; Basan, A.; Nekrasov, A.; Fidge, C.; Gamec, J.; Gamcová, M. A Self-Diagnosis Method for Detecting UAV Cyber Attacks Based on Analysis of Parameter Changes. Sensors 2021, 21, 509. [Google Scholar] [CrossRef] [PubMed]
- Basan, E.; Basan, A.; Nekrasov, A.; Fidge, C.; Sushkin, N.; Peskova, O. GPS-spoofing attack detection technology for UAVs based on Kullback–Leibler divergence. Drones 2022, 6, 8. [Google Scholar] [CrossRef]
- Basan, E.; Basan, A.; Nekrasov, A. Method for detecting abnormal activity in a group of mobile robots. Sensors 2019, 19, 4007. [Google Scholar] [CrossRef] [PubMed] [Green Version]
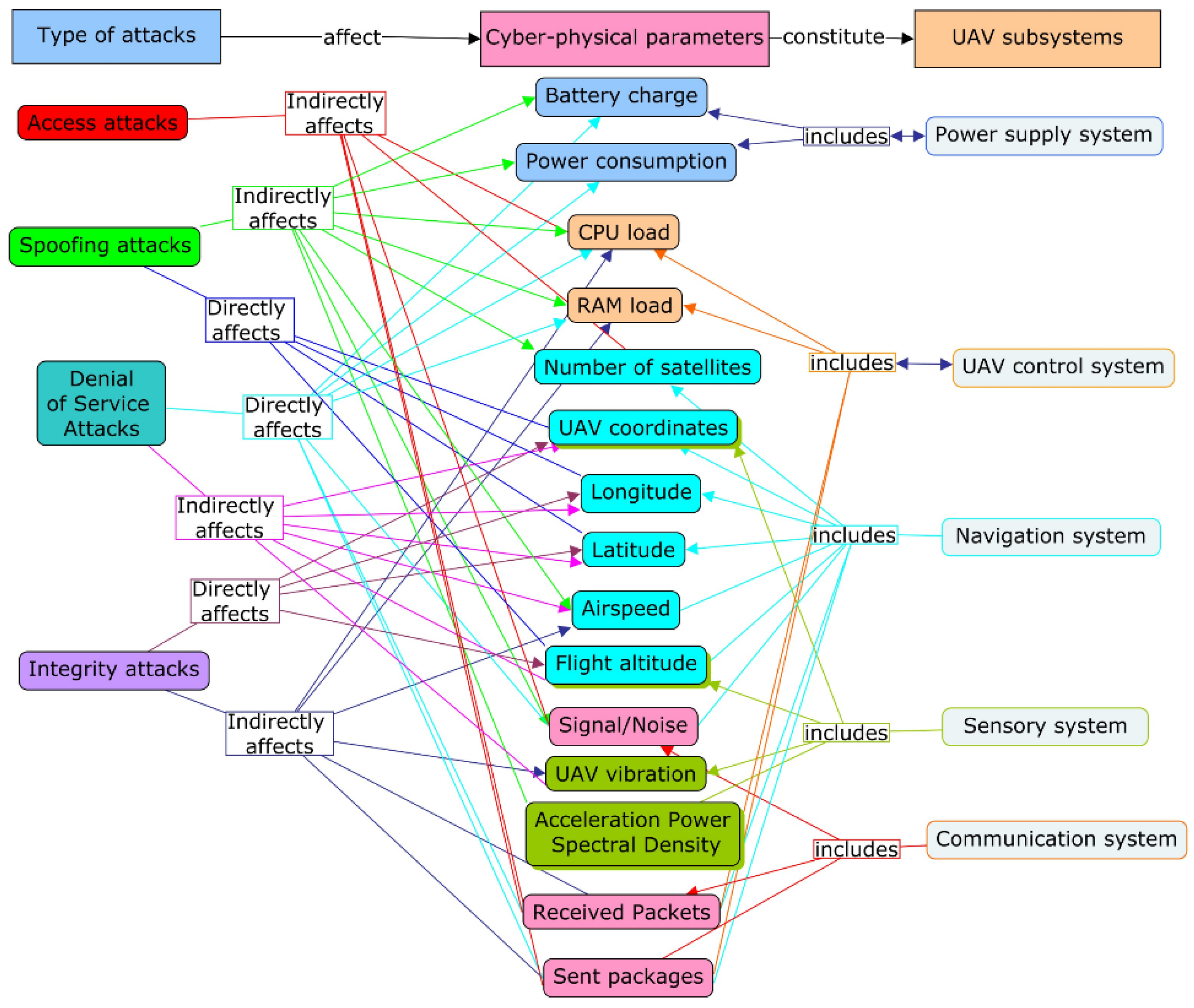



| Attack Type An | Attacks Ni | Consequences Cmn | Subsystem Sjn |
|---|---|---|---|
| Access attacks (Reconnaissance attacks) AAn1 | Password brute force AAi1 |
|
|
| RF analysis AAi2 |
|
| |
| Analysis of communication channels AAi3 |
|
| |
| Detection via physical channels AAi4 |
|
| |
| UAV physical interception AAi5 |
|
| |
| Access to interfaces AAi6 |
|
| |
| Integrity attacks IAn2 | Transmitted data modification IAi1 |
|
|
| False data injection IAi2 |
|
| |
| Replay attack IAi3 |
|
| |
| Black hole attack IAi4 |
|
| |
| Message disclaimer IAi5 |
|
| |
| Firmware modification IAi6 |
|
| |
| Modification of hardware components IAi7 |
|
| |
| Modification of operating system files IAi8 |
|
| |
| UAV control source replacement IAi9 |
|
| |
| Denial of Service Attacks DAn3 | Jamming the control channel DAi1 |
|
|
| Jamming the navigation channel DAi2 |
|
| |
| Request Flood Attack DAi3 |
|
| |
| Connection reset DAi4 |
|
| |
| UAV physical accessibility violation DAi5 |
|
| |
| Hijacking of aircraft DAi6 |
|
|
| No. | Name of Equation | Equation | Description |
|---|---|---|---|
| 1 | Average value for a cyber-physical parameter in the range of a sliding window | n is the sample size, is the sampling options, is the sliding window for a given time interval of values and equals n. | |
| 2 | is the statistic value for the chi-squared (χ2) distribution. | Pij is the actual frequency in the i-th line, j-th column; Eij = is the expected frequency in the i-th row, j-th column; r is the number of rows; and c is the number of columns. | |
| 3 | Cumulative function for Poisson distribution [25] | The cumulative distribution function for Poisson returns the probability that the outcome is less than or equal to . |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Basan, E.; Basan, A.; Nekrasov, A.; Fidge, C.; Abramov, E.; Basyuk, A. A Data Normalization Technique for Detecting Cyber Attacks on UAVs. Drones 2022, 6, 245. https://doi.org/10.3390/drones6090245
Basan E, Basan A, Nekrasov A, Fidge C, Abramov E, Basyuk A. A Data Normalization Technique for Detecting Cyber Attacks on UAVs. Drones. 2022; 6(9):245. https://doi.org/10.3390/drones6090245
Chicago/Turabian StyleBasan, Elena, Alexandr Basan, Alexey Nekrasov, Colin Fidge, Evgeny Abramov, and Anatoly Basyuk. 2022. "A Data Normalization Technique for Detecting Cyber Attacks on UAVs" Drones 6, no. 9: 245. https://doi.org/10.3390/drones6090245
APA StyleBasan, E., Basan, A., Nekrasov, A., Fidge, C., Abramov, E., & Basyuk, A. (2022). A Data Normalization Technique for Detecting Cyber Attacks on UAVs. Drones, 6(9), 245. https://doi.org/10.3390/drones6090245







