1. Introduction
The Internet of Drone Things (IoDT) was created to control the airspace using drones; it is also called UAVs (unmanned aerial vehicles) combined with the Internet of Vehicles (IoV), which is a highly promising technology and creates huge benefits in both industrial and academic research. The IoV is an Internet-connected, self-organizing vehicular network that is capable of performing effective communication, and it can provide high road safety and self-navigation. However, IoV-based networks suffer from certain flaws, such as link disconnections, improper resource allocation, and high computational costs. In order to overcome this drawback, unmanned aerial vehicles (UAVs) are combined with it.
Recently, VANETs were entered into super-fast networks with dynamically varying topology, which increased the energy consumption and routing overhead of the network. In order to overcome these drawbacks, drones were introduced in VANET-based networks. Drones are interconnected devices, so they can communicate among themselves. A drone maintains two network structures: UAV–UAV communication and UAV–infrastructure communication [
1]. In general, drones are equipped with various sensors, cameras, GPS, signal transmitters, etc., and they are used for various applications, such as confidential communication, inaccessible surveillance, environmental observance, yield observance, farming, and disaster monitoring [
2]. Drone-assisted VANETs maintain a heterogeneous structure, where the vehicular network is connected to the drones. The communication of this kind of network establishes vehicle-to-vehicle (V2V), vehicle-to-drone (V2D), and drone-to-drone (D2D) communication. Drone-aided VANETs provide more opportunities and functionalities to control network traffic. The major roles of drones are to provide temporal traffic indications, predict road traffic, define mobility patterns, pathway optimization, and intelligent vehicle connectivity [
3]. Drones help to establish optimal places for ground vehicle communication [
4], as applying drones to ground vehicle communication results in the increase in delay. So, it is essential to control delay using optimization in communication between the drones and the vehicles [
5].
Drones were introduced in VANETs to improve the performance of VANETs in terms of congestion avoidance, energy consumption reduction, and security purposes. Due to the large-scale deployment of VANETs, it is very easy for attackers to enter into the network. Drones help to guarantee the integrity of the network [
6]. They help to secure confidential information and the movement trajectories of the vehicles [
7]. If the privacy of the network is high, then it becomes very complicated to attract vehicle users to enter into the network [
8]. In order to achieve the complete benefits of the drone-aided VANET architecture, several issues need to be focused on. Initially, threats are high in VANETs because of their mobile nature. Various attackers can control the network during transmission. So, it is essential to improve the trust ability of the network. In a dynamic environment, it is difficult to control the congestion of the network. Due to high congestion, there is a possibility for the occurrence of high overhead and connectivity loss during communication. These are major issues that need to be addressed in drone-based VANETs. In this study, the challenges of drone-based VANETs are investigated, and the major contributions of this research study are as follows:
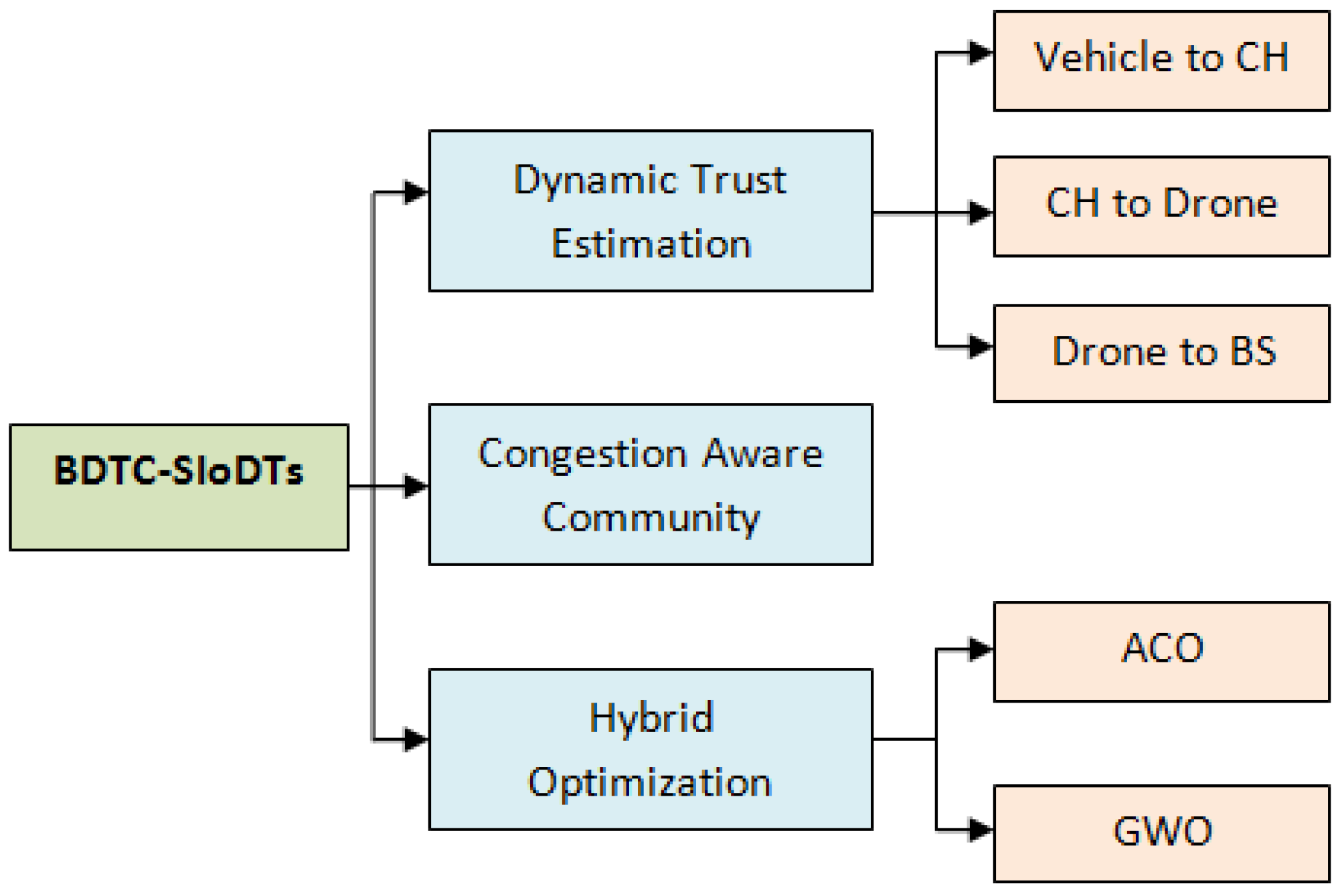
In this paper, the main aim is to improve the effectiveness of the drone-based Internet of Vehicles communication by reducing the congestion and energy consumption and by increasing the security, which were considered the major drawbacks in earlier research. For that purpose, bio-inspired dynamic trust and congestion-aware zone-based secured community with hybrid optimization is performed.
Initially, to improve the coverage area of the network, heterogeneous drone-based VANETs are constructed, which includes vehicles, cluster head (CH), and drones.
To protect the network from the malicious activities and to reduce the energy consumption and delay in the proposed method, triple-layer trust construction, congestion-aware community construction, and hybrid optimization is performed.
Initially, to improve the security, triple-layer trust construction is performed through a dynamic trust estimation process. Here, the trust for vehicle to CH, for CH to drone, and for drone to BS are concentrated.
Secondly, congestion is controlled through a congestion-aware community construction method. Finally, in order to reduce energy consumption and routing overhead, hybrid optimization is performed with the combination of ACO and GWO algorithms.
In the performance analysis section (
Section 5), the evaluation of the proposed work is performed using various attacks such as flooding attack, insider attack, wormhole attacks, and position falsification attack. The considered parameters for the performance analysis are energy efficiency, packet delivery ratio, routing overhead, end-to-end delay, packet loss, and throughput.
2. Related Works
In this related work section, the drawbacks present in the drone-based vehicular networks are analyzed. The authors of [
9] developed a method to improve the quality of service (QoS) of various VANET applications called data scheduling through game theory. Through this method, delay is reduced and throughput is increased. However, this method fails to reduce the routing overhead during transmission. The authors of [
10] presented an approach called the collaborative network coverage enhancement scheme (CONEC) to cover the uncovered area. Via this method, optimal places are provided to UAVs using particle swarm optimization (PSO). The packet delivery ratio and throughput are improved using this method. However, using PSO in UAVs increased the overhead in the network. The authors of [
11] introduced a novel approach, namely a bio-inspired and traffic-aware mix-zone placement model for a drone-based network. Through this method, the privacy level of the network is increased. The other parameters, such as overhead and efficiency, are not considered in this research. The authors of [
12] proposed a secure and lightweight drone access protocol to reduce the running time cost and communication cost of the network. To provide security for the dynamically varying vehicles, deep learning algorithms are used, and it is based on the key exchange protocol with XOR operator and hash functions. The accuracy level is high in this network; however, it fails to achieve high efficiency during communication.
The authors of [
13] presented an approach to improve the superiority and flexibility of the drone called a collaborative communication scheme, which was developed to solve the traffic-related issues in VANETs. Through this method, the throughput and packet delivery ratio of the network is improved. However, this method mainly concentrates on the optimization problem; it is not up to the level, so this increases the overhead. The authors of [
14] presented a model to improve the efficiency of the drone communication in emergency areas. GPS-based geo-tracking and geographic navigation are performed to improve the routing performance, and a heuristic algorithm is implemented to improve the communication speed and performance as it helps to transmit the data in an optimal path. The authors of [
15] proposed an adequate connection between drones with the help of improved particle swarm optimization (IPSO). Through this method, high coverage and quality is achieved, but it fails to concentrate on security and overhead. The authors of [
16] proposed an efficient privacy preserving authentication method for IoDs. This method reduces the authentication cost and improves the privacy and efficiency of the network. However, there is no proof for the reduction in overhead. The authors of [
17] presented a model to analyze the probability distribution of vehicles to drones in a bi-directional manner. This method reduces the network delay but fails to improve the efficiency, throughput, and delivery ratio. The authors of [
18] developed a novel approach to reduce the energy consumption and delay called Non-Orthogonal Multiple Access (NOMA), which is mainly utilized for the process of bandwidth allocation. The additional methods which are used to improve the clustering-based UAVs network are K-means clustering and truncated Gaussian distribution. This method greatly reduced the power consumption and delay, but packet loss occurred due to the lack of security in the network. The authors of [
19] proposed a proactive UAVs placement in RSU-assisted VANETs. The optimal UAV placement is performed using the particle swarm optimization (PSO) process, but it fails to achieve maximum efficiency during the process of communication.
The authors of [
20] presented a UAVs-assisted VANETs-based edge detection, which is the deep-learning-based optimal deployment of the UAVs, mainly to reduce the energy consumption and delay of the network. However, due to multiple traffic jams, the packet loss in this network is moderate. The authors of [
21] developed an effective communication model for the UAV networks through hybrid automatic repeat request protocol to control the congestion in the network. However, the communication is ineffective due to the lack of security. The authors of [
22] proposed a reinforcement learning-based trajectory control for UAVs that increase the stability of the network by protecting the network from the jamming, but it fails to reduce the energy consumption. The authors of [
23] proposed a bio-inspired UVDTN network to improve the quality of service (QoS) of the urban VANETs. The algorithms which are used in this process are social spider optimization (SSO) and store carry forward (SCF) process. The results show that this method achieves low delay and overhead but fails to achieve high efficiency. The authors of [
24] proposed a NOMA-based resource allocation in vehicular communication using game theory. The simulation results achieve moderate efficiency.
The authors of [
25] developed an authentication and key agreement (AKA) scheme to improve the privacy of the drones-based network. Through this method, the communication and computational cost are reduced. However, it fails to concentrate on other parameters such as efficiency, overhead, throughput, etc. The authors of [
26] introduced a method to avoid the congestion called fog-assisted smooth packet distribution. This method improves the packet delivery ratio and reduces the overhead but fails to improve the security of the network. The authors of [
27] developed a trust-and-priority-based drone-assisted IoV. Through this method, the overhead and delay are reduced, packet delivery ratio and efficiency are high, but the throughput achieved by this network is moderate. The advantages and disadvantages of these earlier studies are shown in
Table 1.
By analyzing all these earlier studies, it is understood that the major drawbacks in the drone-based VANETs are congestion, high overhead, and security. In [
25], AKA authentication is performed, which fails to achieve lower congestion and overhead. Hence, the major focus is security, but the huge number of vehicles with dynamic mobility pattern leads to high delay, congestion, and packet loss. The authors of [
26] focus on the congestion control of the vehicles during the process of communication which provides a way to some of the misbehaviors that is reflected in the increases of packet loss, overhead, and energy consumption. In [
27], the trust and priority of the network is the focus, but there is no optimal path between the source and the destination during communication, which leads to ineffective communication. These are major drawbacks from the earlier research works. So, in this research, Bio-inspired Dynamic Trust and Congestion-Aware Zone-based Secured Internet of Drone Things (BDTC-SIoDTs) is proposed which concentrates on security, congestion avoidance, and overhead control, and a detailed description of the proposed BDTC-SIoDTs is given in the following sections.
3. Preliminaries
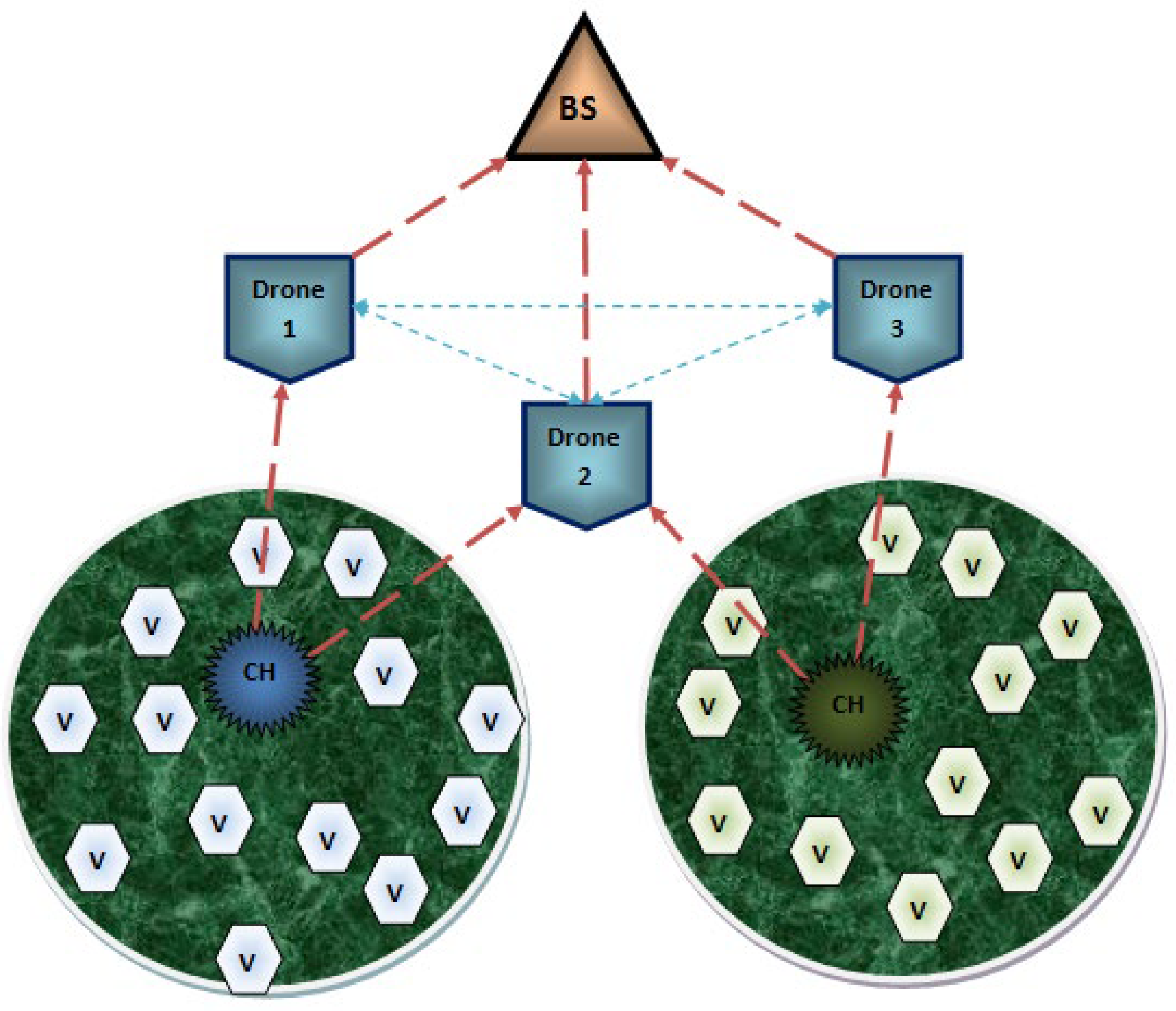
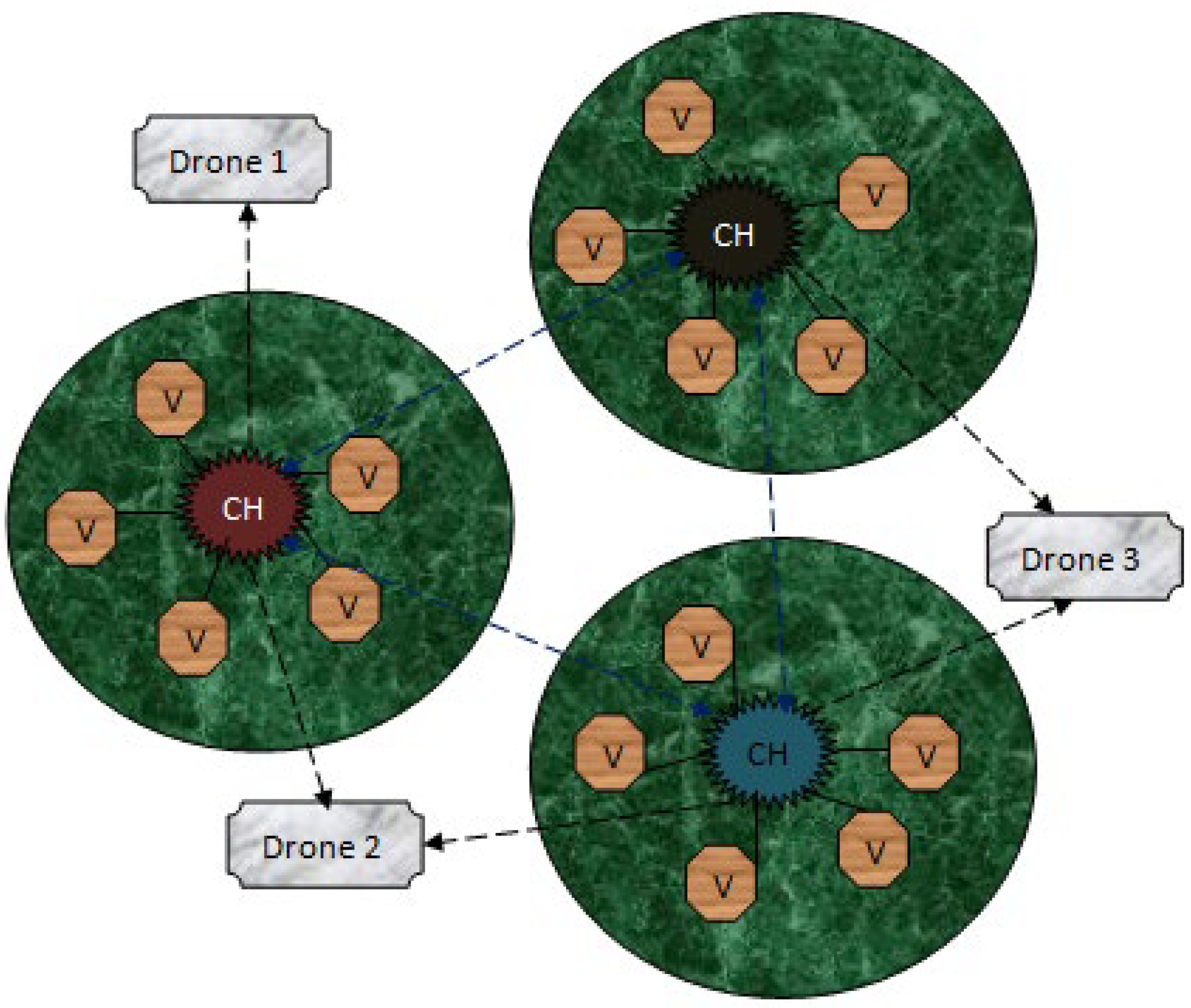
The proposed system is designed in terms of including the data communication among the Internet of Drone Things (IoDTs), vehicle-to-CH (V-CH) communication, CH-to-drone (CH-D) communication, and drone-to-drone (D-D) communication, and the transmission is concluded by transmitting the information to the Base Station (BS). Additionally, it shares the information about the drone routing model as well as the design threads present in IoDTs. The systematic structure of the network is shown in
Figure 1. At the initial stage, these communication models are elaborated, then following that, the designed routing protocol for these communications are discussed. The general transmission structure is that the vehicle transmits the information to the CH; subsequently, the CH transfers the data to the drones. Finally, the BS collects the data from the respective drone. The transmission region is divided into zones, and one or two drones will monitor each zone. Some of the special qualities of a drone are that it is able to cover a huge coverage space and it monitors the dense traffic conditions; hence, it contains its own Global Positioning Systems (GPS) as well as the digital maps.
3.1. Internet of Vehicles
Each vehicle present in the system communicates through a wireless medium. The inbuilt components of each vehicle consist of an on-board unit (OBU), tamperproof device (TPD), and graphical user interface (GUI). In this type of communication model, vehicle–vehicle communication does not occur. All the vehicles are designed to transmit the data packets to the cluster head (CH). The CH collects the data packets from the vehicles which are present in its coverage space and then continues the process further.
3.2. Vehicle-To-CH (V-CH) Communication
A cluster head (CH) is created in the network to aggregate all the data packets from the vehicles in short-range communication so as to reduce the traffic congestion. Following that, the aggregated data packets are transmitted to the drones that are present in the transmission range of the CH.
3.3. CH-To-Drone (CH-D) Communication
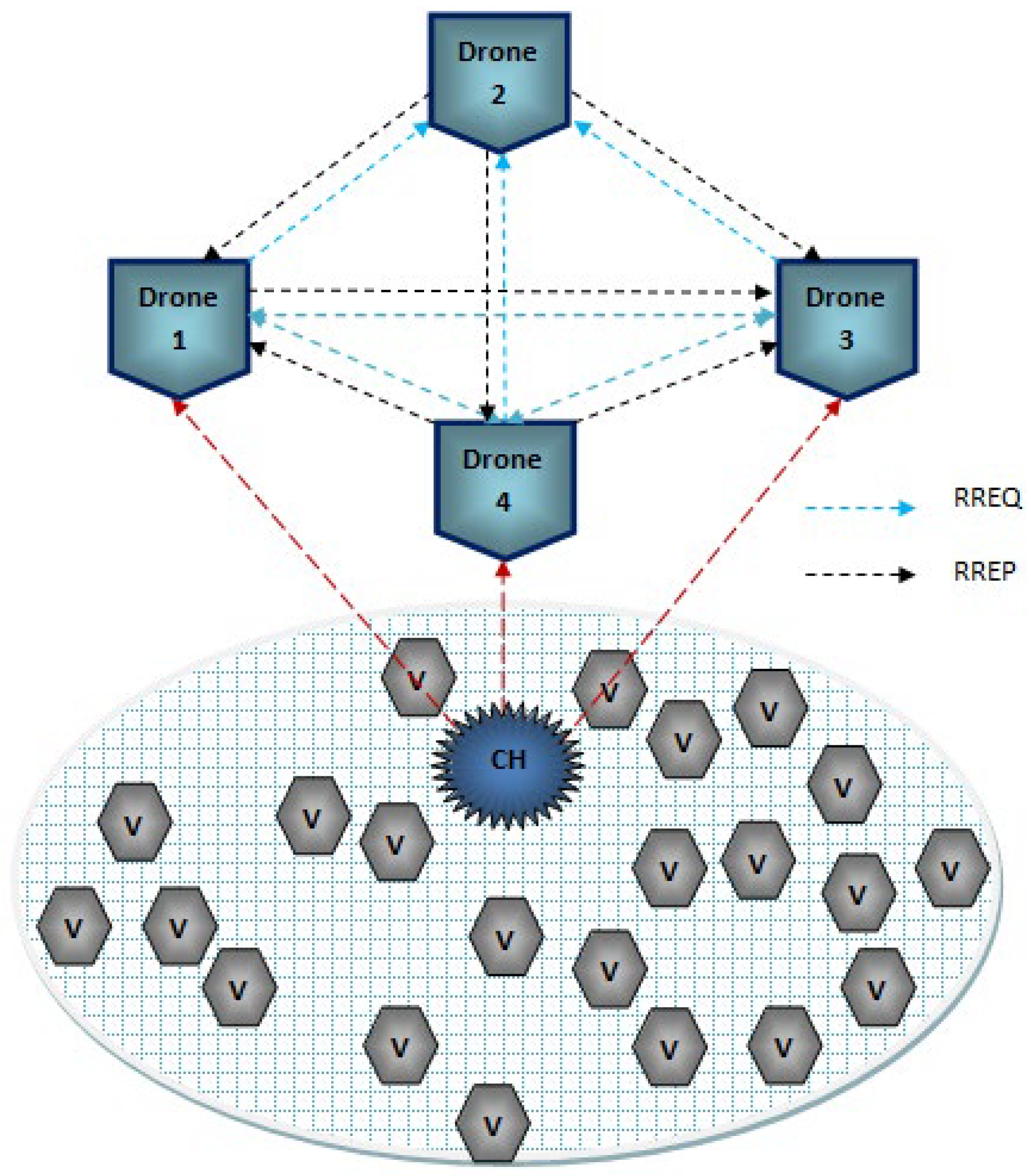
The collected information from the vehicles is transmitted from the CH to the drone. Hence, the drone does not require any infrastructure to provide service to the CH because the principle of BS is to provide the essential utilities to process the communication among the network, and it also avoids direct data collection. Next to the BS, the drone maintains high energy so that it is able to cover huge densely populated areas. All the communication from the CH to BS is only through the drones. Due to its high quality, it is able to build an obstacle-free environment. The routing process of CH-D is described in
Figure 2.
3.4. Drone-To-Drone (D-D) Communication
In order to reduce the obstacles handled by the vehicles, drones are introduced to manage the huge dynamic varying constraints. Drones are highly qualified to solve the traffic-related issues of vehicles due to its routing model. In general, drones are unmanned aerial vehicles (UAVs) which are controlled using the onboard computers. Drones are fully automatic and are able to work without any intervention from humans. Some of the inbuilt components of drones are kinds of smart IoT devices such as distance sensor, ultrasonic sensor, thermal sensor, GPS system, motors, transmitter and receiver, battery, range measuring sensor, radio sensor, and chemical sensor. Reliable transmission can be easily achieved using the drones in the network. There is some ideal process present during the process of data transmission among the drones which is not similar to the transmission among vehicles or CHs. Drones support very limited protocols, which can establish connectivity in a smart way.
3.5. Drone Routing
The traditional routing model is not suitable for drone routing; hence, hybrid routing [
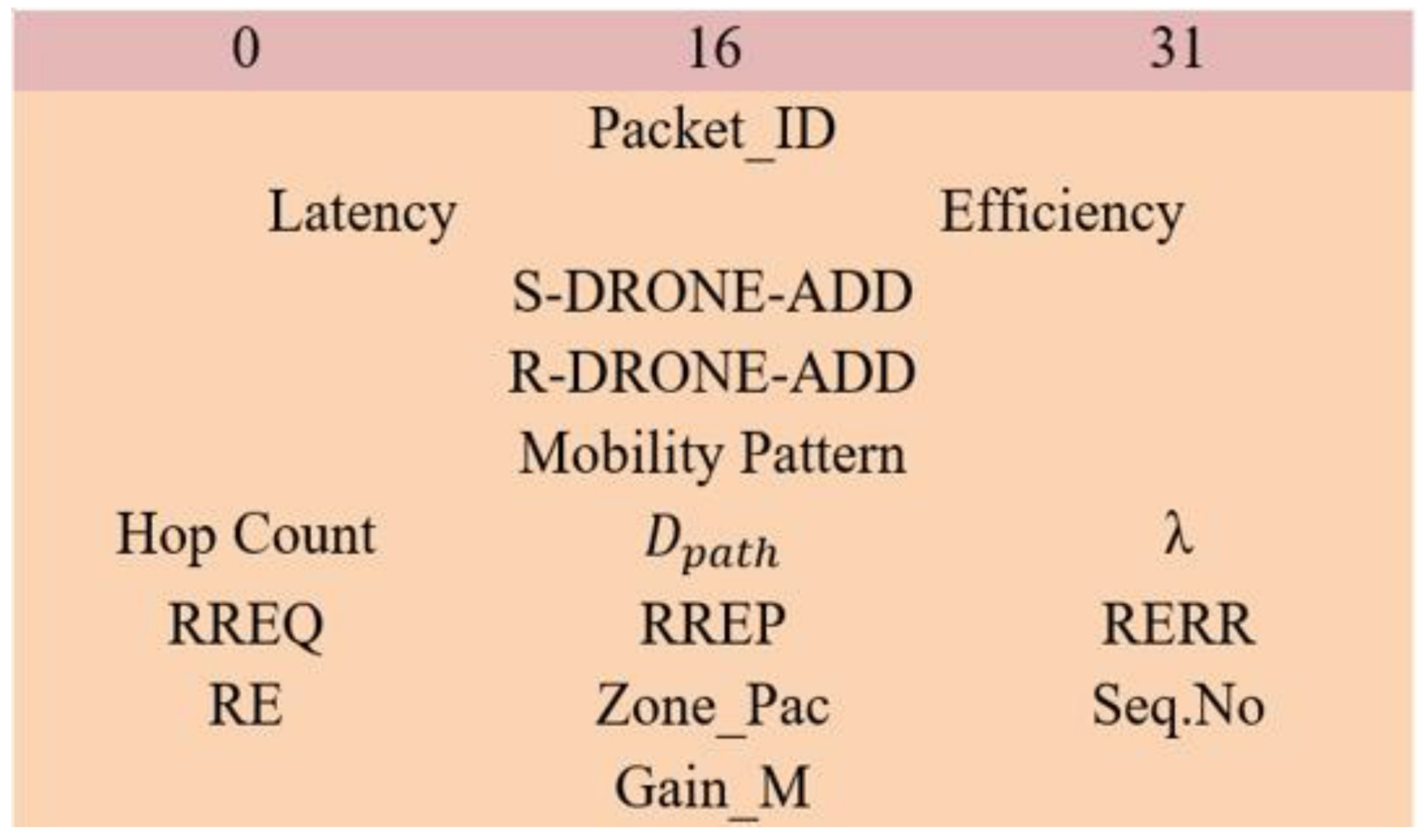
28] is used, which is the zone routing protocol (ZRP). This protocol is mainly designed to reduce the routing overhead, where the control packets maintain a static packet size. Here, connectivity is established using a prediction approach. The network coverage space is divided into several zones, and each zone is monitored by one or two drones. The major phases of the protocol are route request (RREQ), route reply (RREP), route expiration (RE), and route error (RERR). The packet structure of the ZRP routing protocol is shown in
Figure 3.
In the ZRP protocol, the sender broadcast the RREQ packet, the control packet size ranges from 0 to 31, the S-DRONE-ADD represents the sender drone address, and the R-DRONE-ADD represents the receiver drone address. The inbuilt parameters, which are calculated directly from the control packets, are latency and efficiency. The possible pathway to reach the receiver is noted in the mobility pattern. Once the delay is so high or the efficiency of the packet reaches below its threshold, then the packet gets dropped automatically. Hop count represents the intermediate hops total count of the packet. Additionally, some other basic information is packet_ID, sequence number (Seq. No), and zone packets (Zone_Pac). After the broadcast of the RREQ packet, through certain hops, the packet must reach the receiver. Using certain parameters, the hops will update the packet such as momentum, latency, location, travel path, and efficiency. Here, RE represents the route expiration, and it happens on certain conditions when the efficiency of the route reaches below its threshold efficiency. Once the RREQ packet reaches the receiver, the total gain measurement (
) is calculated, which is mathematically expressed below:
In Equation (1), the
denotes the gain obtained during the connectivity of the route,
denotes the total number of routes measured by the single drone, λ denotes the actual allocation of the drone, and the latency and efficiency are the core parameters used for the measurement of gain. Following the gain measurement, the receiver generates the RREP packet and sends it back to the sender. The optimal path to transfer the RREP packet is chosen as the route with the highest gain measurements. The RREP packet also maintains the general information, such as packet_ID, sequence number (Seq. No), and zone packets (Zone_Pac). During the process of transmission of the RREP packet to route, expiration may occur at the time the route revival model is initiated and select the route with the next best gain measurement to transmit the RREP packet. If any connectivity issues occur due to the geographical changes of the drones at that time, a route error (RERR) packet is generated so as to recreate the route discovery. Due to this process of zone creation, link failures are easily identified. The process of drone routing is described in Algorithm 1.
| Algorithm 1. Drone Routing |
Each S-DRONE broadcasts RREQ,
Type → Packets,
Details → Packet_ID, Latency, Efficiency,
Hold → Mobility Pattern,
Seq. No = extract from packet,
Hop Count = extract from packet,
= extract from packet,
Begin_If
{
Generate RREQ then broadcast,
Continue until reaches the destination,
} end_if
Else declare RE
Gain calculation according to Equation (1)
End |
3.6. Thread Model
In a vehicle-based network, massive devices get interlinked to perform the required operation according to their application. For that reason, it is easy for the attacker to introduce several security threads here to misuse confidential information. So, it is essential for any kind of VANET network to ensure the security level. In this research, the considered attacks for analysis are flooding attacks, insider attacks, wormhole attack, and position falsification attacks.
3.6.1. Flooding Attack
In general, flooding is a kind of attack that generates extra traffic that is reflected in the increase in bandwidth, energy consumption, and so on [
29]. Data flooding increases the routing overhead by generating unwanted packets and broadcasting those packets to all the vehicles in the network. In route flooding, the malicious vehicles transmit false route requests to their neighbors so that the data can get lost by sending it to a non-existing vehicle.
3.6.2. Insider Attack
Insider attack directly affects the OBU system of the vehicles, and it copies the identity certificate of any vehicle so that the attacker can easily join the network [
30]. Therefore, the OBUs become fully unsafe. Using this attacker makes it possible to monitor the other vehicles, so that the attacker can hack any vehicle using that identity certificate to collect the required material from it. After collecting the material, the attacker can replicate any innocent vehicle and then vanish from the network.
3.6.3. Wormhole Attack
This attack performs a topology modification operation among the vehicles and provides a false shortest path from the source to the destination during the process of communication, which is reflected in the increase in traffic and congestion in the network [
31]. As a result, during data transmission, an attacker vehicle summarizes the information and transmits it to the cooperative vehicle. Then, two attackers transmit the information through a false optimal path which acts as a tunnel secret path so that the information will only transfer through the tunnel path and will not get broadcasted as normal information.
3.6.4. Position Falsification Attack
Creating false positions in VANETs is a serious issue that directly affects network safety applications. Hence, in general, VANETs-based applications highly trust the reliable positioning system of VANETs. This attack is reflected in the reduction in packet delivery ratio performance and affects the stability as well as the reliability of the system of VANETs.
5. Results and Discussion
For the process of simulation experimentation, NS2.35 software is used which consists of two input languages, such as Tool Command Language (TCL) used as a front-end programming language and C++ as a back-end programming language. To view the structural outcome, NAM (Network Animator) is used. To analyze the results, a trace file is generated. The formula used to separate particular data from the trace file is performed using the Perl file and awk files. The simulation coverage area is set as 2000 m × 3000 m. Additionally, the number of vehicles present in the network is 200 vehicles. The considered input parameters for the process of simulation are given in
Table 3 below.
The parameters which are considered for the analysis of the results are energy efficiency (%), packet delivery ratio (%), routing overhead (packets), end-to-end delay (packets), packet loss (packets), and throughput (kbps). The evaluation proceeds through two scenarios: the first scenario is according to the variation of the calculated performance speed of various attacks, such as flooding attacks, insider attacks, wormhole attacks, and position falsification attacks, of the proposed BDTC-SIOVTs. In the second scenario, the considered parameters of the proposed BDTC-SIOVTs are compared with earlier works such as LAKA-IOD [
16], NCAS-IOD [
17], and TPDA-IOV [
18].
5.1. Performance Analysis according to the Speed and Attacks
The parameters used for this analysis concerning the varying speed from 50 km/h to 300 km/h are energy efficiency, packet delivery ratio, routing overhead, end-to-end delay, packet loss, and throughput. The performance analysis of the proposed BDTC-SIOVTs is performed using the following attacks.
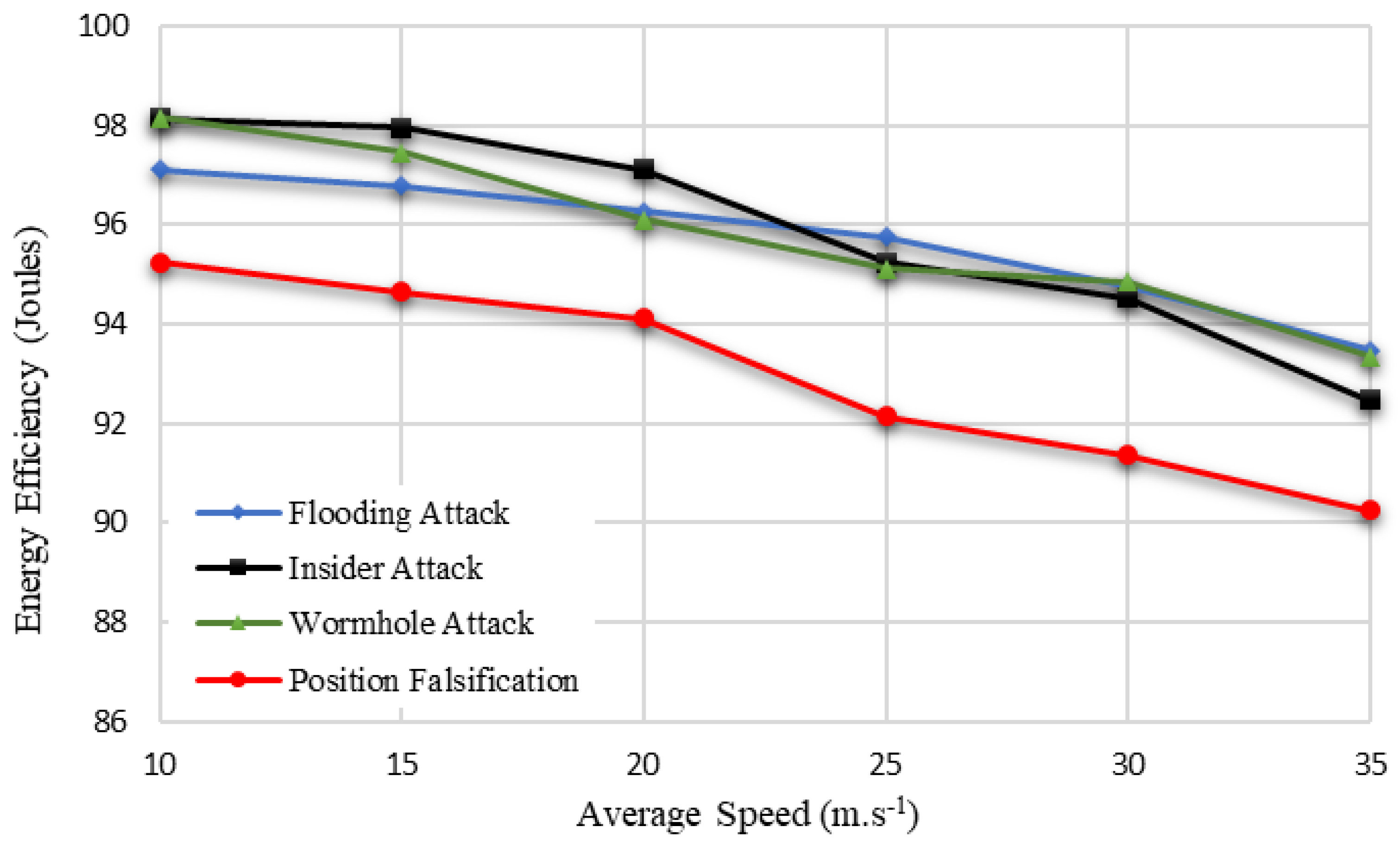
Figure 7 clearly indicates the energy efficiency calculation of the proposed BDTC-SIOVTs according to varying speeds, and it is compared between various attacks. From the graph, it is understood that the performance of proposed BDTC-SIOVTs is high for attacks such as flooding attacks, insider attack, and wormhole attack, and the efficiency of the proposed BDTC-SIOVTs is low in the case of the position falsification attack. The proposed BDTC-SIOVTs is the combination of dynamic trust and hybrid optimization methods which play a better role in the other attacks but still need some betterment in terms of position falsification attacks.
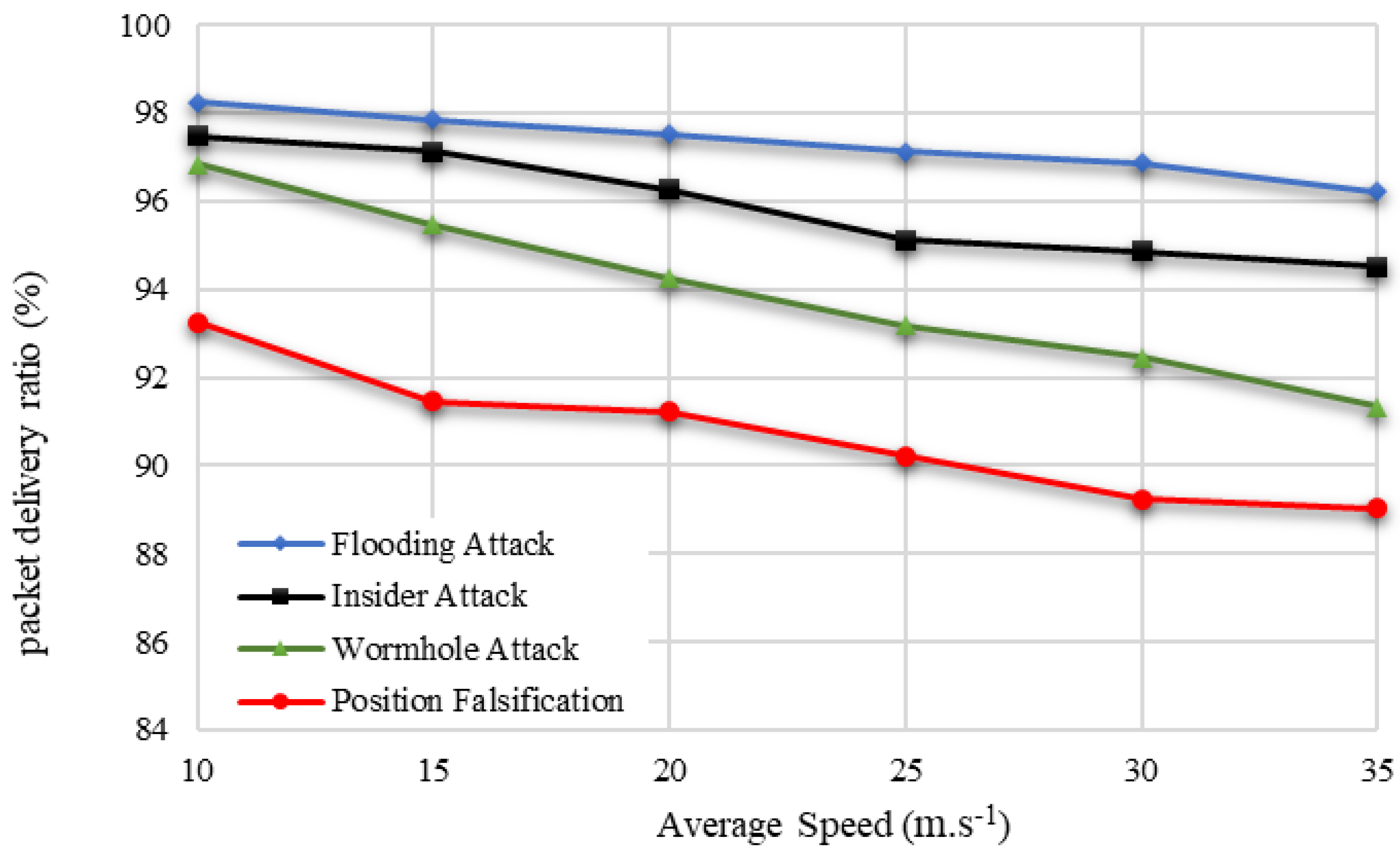
The proposed BDTC-SIOVTs produced a high packet delivery ratio with attacks such as flooding attacks and insider attacks. The packet delivery ratio of the proposed network with the wormhole attack and position falsification attack are comparatively low when compared to others, and it is demonstrated in
Figure 8.
Hence, the core idea of the proposed BDTC-SIOVTs is to reduce the overhead so that the idea of dynamic trust-based clustering and the hybrid optimization is combined. The hybrid optimization method greatly helps to reduce the routing overhead even during the presence of attacks in the network. The proposed BDTC-SIOVTs produced a low routing overhead for all the attacks, which is shown in
Figure 9.
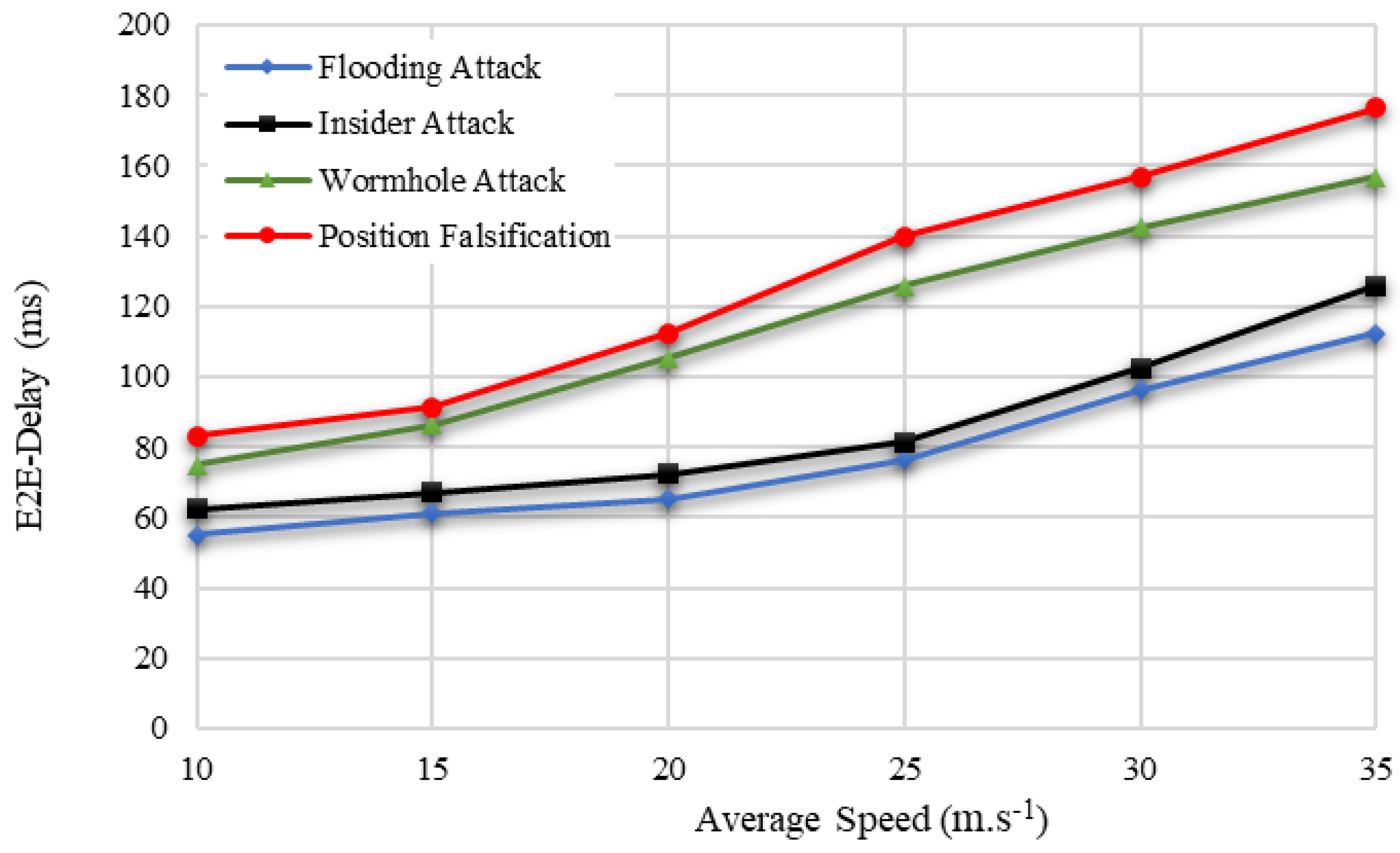
The proposed BDTC-SIOVTs produced a low end-to-end delay with attacks such as flooding attacks and insider attacks. The end-to-end delay of the proposed network with wormhole attacks and position falsification attacks is comparatively high when compared others, and it is graphically represented in
Figure 10.
The proposed BDTC-SIOVTs are the clustered drone-based model that highly concentrates to reduce the loss of packets so that it can support the transmission of confidential messages. The packet loss calculation of the proposed BDTC-SIOVTs is low with all the attacks, and it is shown in
Figure 11.
Hence, throughput is considered to be an important parameter because it represents the overall quantity of data transmission and its ability. So, the perfect network must provide high throughput even in the presence of any kind of attacks. This is highly concentrated in the proposed BDTC-SIOVTs. From
Figure 12, it is proved that the throughput utility is high for the proposed BDTC-SIOVTs for all types of attacks. This is the major advantage of the proposed BDTC-SIOVTs method. A detailed discussion of the results is given in the following section.
5.2. Subsection Dynamic Trust Estimation
In this section, the considered parameters such as energy efficiency, packet delivery ratio, routing overhead, end-to-end delay, packet loss, and throughput are analyzed in detail concerning speed (10–35 m.s
−1), with the presence of certain attacks such as the flooding attack, insider attack, wormhole attack, and position falsification attack. The simulation values are shown in
Table 4 and
Table 5 below.
The efficiency in terms of attacks is flooding attack (97% to 93%), insider attack (98% to 92%), wormhole attack (98% to 93%), and position falsification attack (95% to 90%). From this measure, it is understood that an increase in speed reduces the efficiency of the network. The proposed method produced high efficiency with the presence of certain attacks such as flooding attacks, insider attacks, and wormhole attacks. Unfortunately, the efficiency received with the position falsification attack is a little low compared with the other attacks.
The increase in speed reduces the packet delivery ratio, which in terms of attacks, are flooding attacks (98% to 96%), insider attacks (97% to 94%), wormhole attacks (96% to 91%), and position falsification attacks (93% to 89%). The proposed BDTC-SIOVTs produced a high packet delivery ratio with the presence of certain attacks such as flooding attacks, insider attacks, and wormhole attacks. However, the ratio received with the position falsification attack is a little low compared with the other attacks. The increase in speed increases the overhead, which in terms of attacks, are flooding attack (196 to 964) packets, insider attack (254 to 1025) packets, wormhole attack (316 to 1125) packets, and position falsification attack (345 to 1245) packets. The proposed BDTC-SIOVTs produced a low overhead for all the attacks present in the network.
The increase in speed increases the delay, which in terms of attacks, are flooding attack (55 to 112) ms, insider attack (62 to 125) ms, wormhole attack (75 to 156) ms, and position falsification attack (83 to 176) ms. The proposed BDTC-SIOVTs produced a low delay for all the attacks present in the network. However, there is a variation in the attack performances. The proposed BDTC-SIOVTs produced much better results for flooding and insider attacks when compared with the wormhole and position falsification attack.
The increase in speed increases the packet loss, which in terms of attacks, are flooding attacks (102 to 235) packets, insider attacks (144 to 245) packets, wormhole attacks (165 to 275) packets, and position falsification attacks (171 to 282) packets. The proposed BDTC-SIOVTs produced a low loss of packets for all the attacks present in the network. The increase in speed reduces the throughput, which in terms of attacks, are flooding attacks (998 to 756) kbps, insider attacks (925 to 721) kbps, wormhole attacks (857 to 694) kbps, and position falsification attacks (825 to 691) kbps. The proposed BDTC-SIOVTs produced a high throughput for all the attacks present in the network, but according to the increase in speed, there is some gradual reduction in throughput.
5.3. Comparative Analysis according to Varying Number of Vehicles
The parameters used for the vehicle-based analysis are energy efficiency, packet delivery ratio, routing overhead, end-to-end delay, packet loss, and throughput. The performance of the proposed BDTC-SIOVTs is compared with earlier research such as LAKA-IOD, NCAS-IOD, and TPDA-IOV.
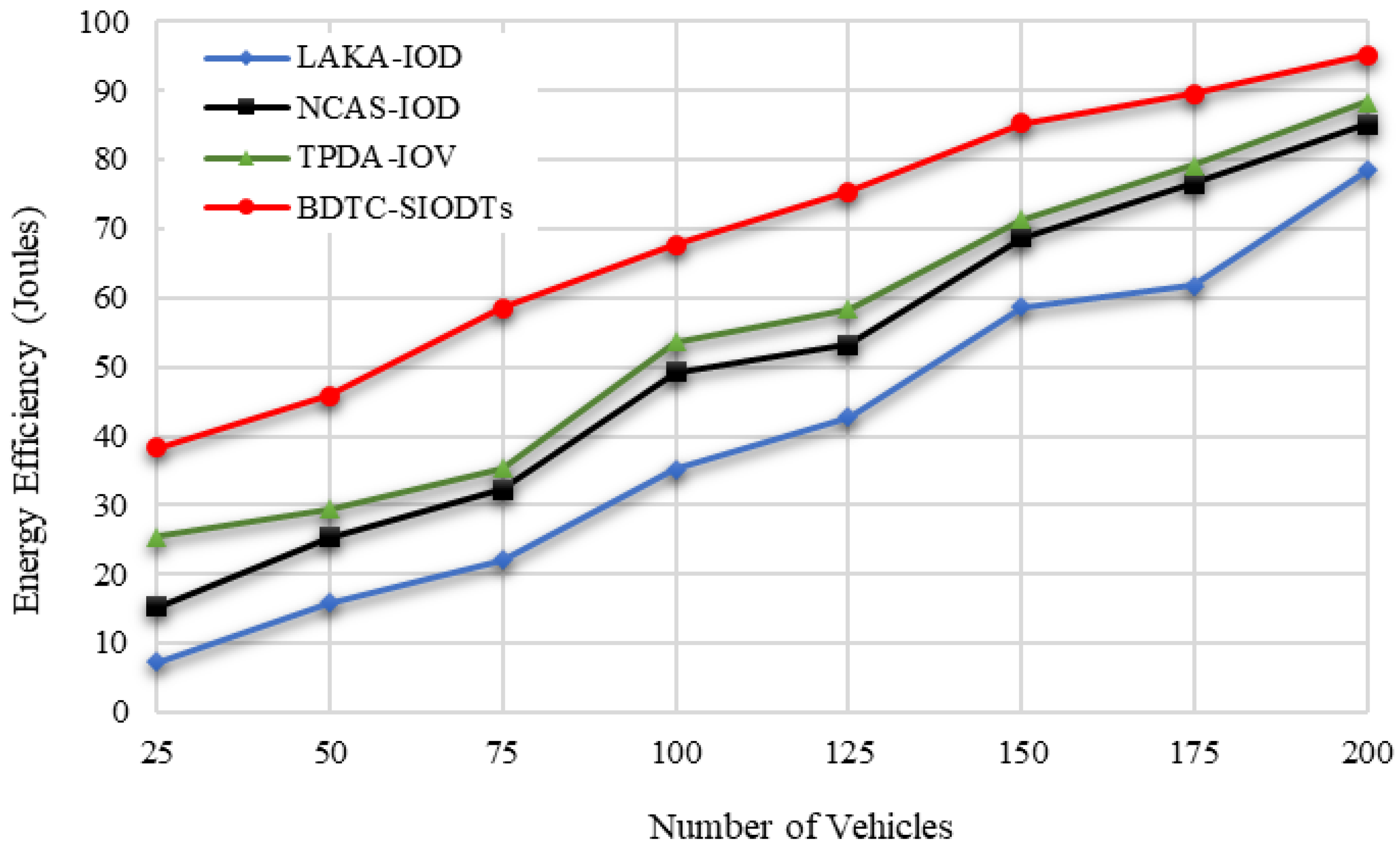
In
Figure 13, it is attested that the energy efficiency of the proposed BDTC-SIOVTs is higher than the earlier methods. The cause for this achievement is that the proposed BDTC-SIOVTs are the combined enhanced trust-based clustering and hybrid optimization. This optimization method is the permutation of the ACO and GWO algorithms, which helps to overcome the drawback in the high-speed VANETs.
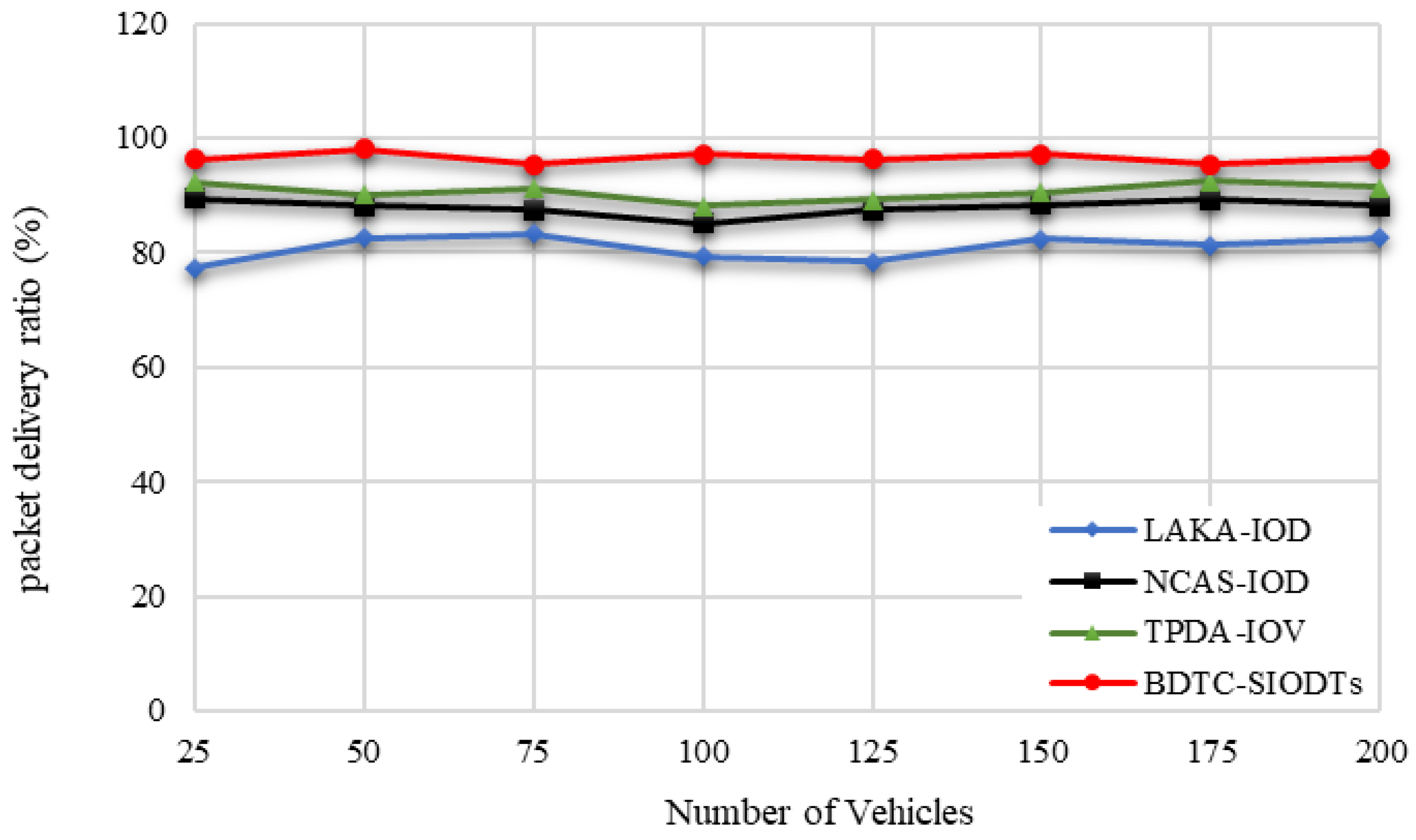
In cluster-based VANETs networks, cluster has a major role in data gathering. So, it is essential to secure cluster communication from the external environment. For that reason, in the proposed BDTC-SIOVTs, dynamic trust-based clustering is initiated so that the packets which get transmitted through the CH are highly secured and there is no way for packet loss to be reflected in the increase in the packet delivery ratio of the proposed BDTC-SIOVTs, which is illustrated in
Figure 14.
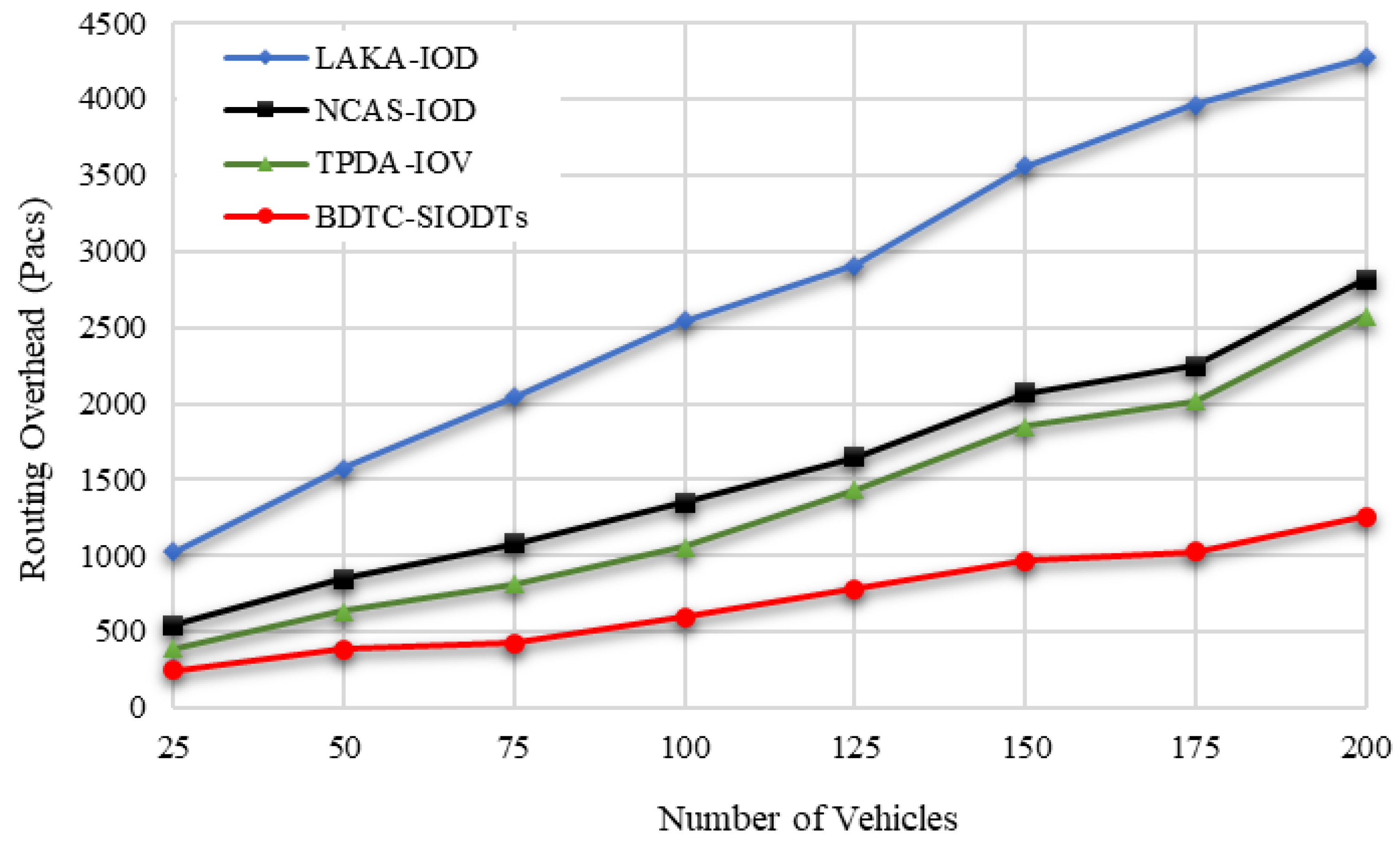
From
Figure 15, it is understood that the proposed BDTC-SIOVTs provide a noteworthy decrement in the overhead performance when compared with others. This is because, in the proposed BDTC-SIOVTs, the data aggregation is performed through CHs and drones. The trust model which is used here is highly dynamic and effective. So, it is very hard for the external force to trouble this network and collect the information. Additionally, it is a high-speed VANETs so even with congestion, overhead can occur. To escape from this condition, hybrid optimization is used. Congestion will occur during the initial stage of data transfer and when vehicles leave and join the cluster. Both these conditions are monitored by the ACO algorithm and GSO algorithm. As the result, the overhead produced by the proposed BDTC-SIOVTs is lower than the LAKA-IOD, NCAS-IOD, and TPDA-IOV methods.
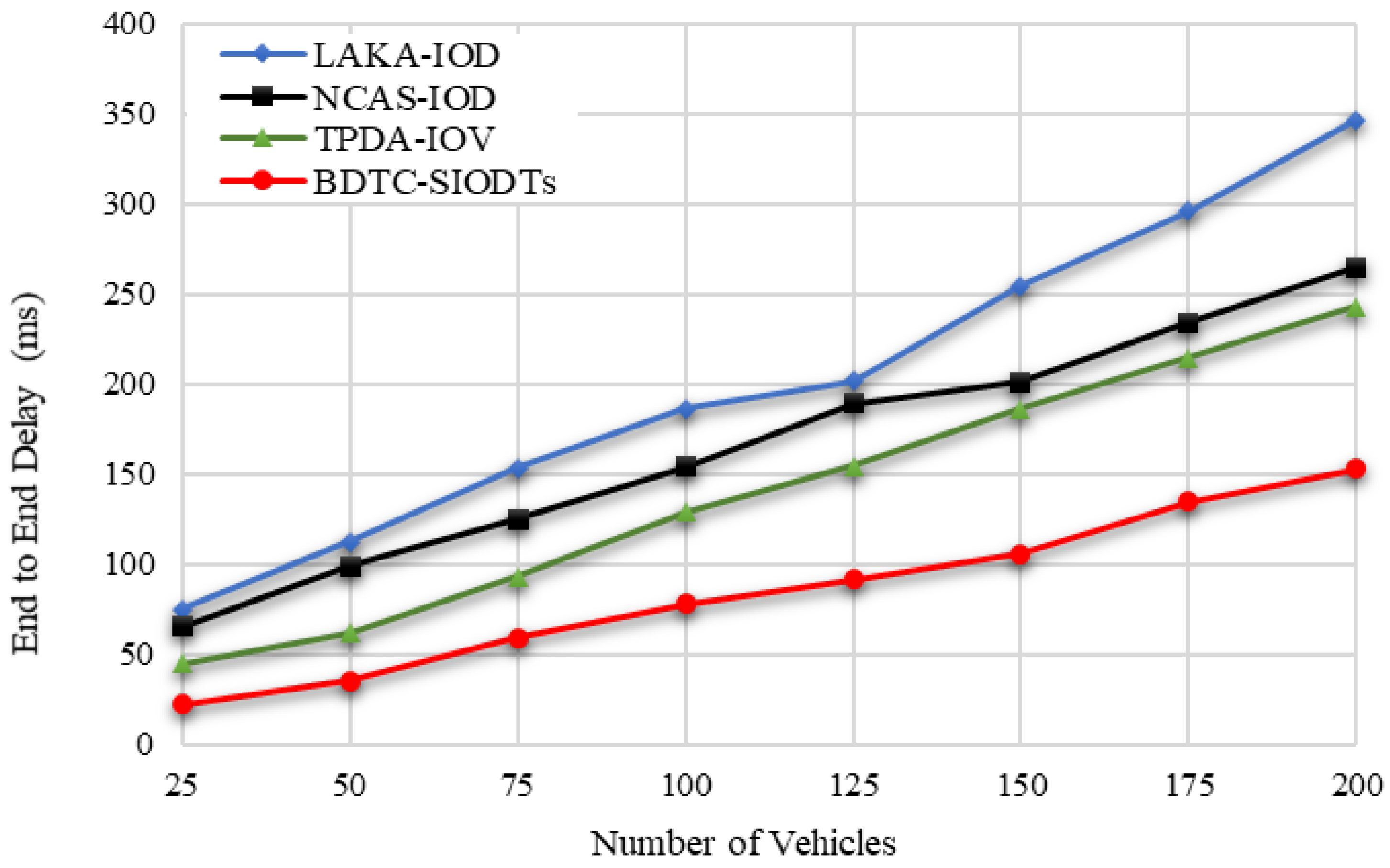
Due to the high overhead, the end-to-end delay is increased. Hence, the BDTC-SIOVTs method produced low overhead, which is reflected in the lower performance of the delay when compared with the earlier works, which are shown in
Figure 16.
Here, in the proposed BDTC-SIOVTs for the initial transmission, ant-based optimization is used and when vehicles leave the cluster and join another cluster, GWO optimization is used. This shift greatly controls the routing overhead of those results in the reduction in packet loss during transmission, which is represented in
Figure 17.
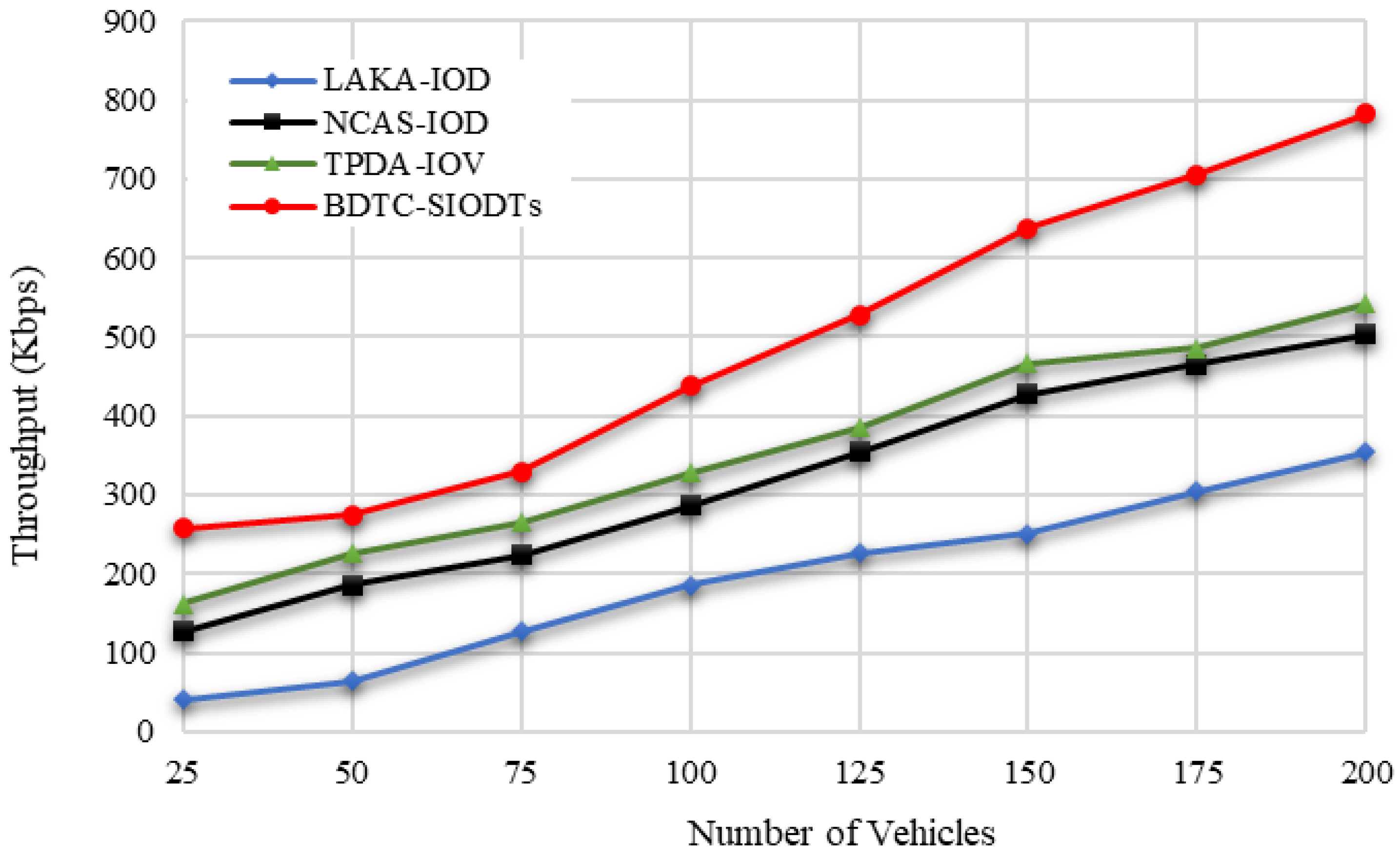
From the graphical outcome in
Figure 18, it is proved that the throughput achieved by the proposed BDTC-SIOVTs is higher than the others. A detailed discussion of the results is given in the following section.
5.4. Results and Discussion according to Varying Number of Vehicles
In this section, the considered parameters such as energy efficiency, packet delivery ratio, routing overhead, end-to-end delay, packet loss, and throughput are analyzed in detail concerning vehicles. The simulation values are shown in
Table 6 and
Table 7.
In terms of the number of vehicles, the energy efficiency measured by the pro-posed BDTC-SIOVTs is 95%, and for the earlier works, it is LAKA-IOD (78%), NCAS-IOD (85%), and TPDA-IOV (88%). So, it is understood that the proposed BDTC-SIOVTs achieve 7% to 17% better energy efficiency when compared with the earlier works. According to the number of vehicles, the packet delivery ratio measured by the proposed BDTC-SIOVTs is 96%, and for the earlier works, it is LAKA-IOD (82%), NCAS-IOD (88%), and TPDA-IOV (91%). So, it is understood that the proposed BDTC-SIOVTs achieve 5% to 14% better packet delivery ratio when compared with the earlier works. Both the efficiency and delivery ratio of the proposed BDTC-SIOVTs are high, and this is achieved using the concept of enhanced trust and hybrid optimization with the combination of ACO and GWO. However, the earlier approaches concentrate on either security or optimization, so it is essential to concentrate on both to achieve effective communication.
Concerning the number of vehicles, the routing overhead measured by the proposed BDTC-SIOVTs is 1256 packets, and for the earlier works, it is LAKA-IOD (4276 packets), NCAS-IOD (2816 packets), and TPDA-IOV (2576 packets). So, it is understood that the proposed BDTC-SIOVTs produce 1300 packets to 3000 packets lower routing overhead when compared with the earlier works. According to the number of vehicles, the routing end-to-end delay measured by the proposed BDTC-SIOVTs is 153ms, and for the earlier works, it is LAKA-IOD (346 ms), NCAS-IOD (265 ms), and TPDA-IOV (243 ms). So, it is understood that the proposed BDTC-SIOVTs produce 90 ms to 200 ms lower end-to-end delay when compared with the earlier works. Hence, the LAKA-IOD method provides security under the random oracle model in the IoD environment, and it highly improves the communication and computational cost of the network to achieve better performance, but this lightweight scheme is not highly suitable for a network with huge dynamic mobility. The NCAS-IOD method uses a smooth massage dissemination scheme which is highly concentrated on the network congestion control so that, during the process of deployment and message, the energy consumption and delay are low, but later on during the process of communication, packet loss occurred due to a lack of security in the network. In the TPDA-IOV method, the process of decision making and trust evaluation is mainly concentrated so that it reduces the overhead delay at the initial stage, but there is no optimal solution between the source and the destination that leads to moderate overhead and delay during communication.
According to the number of vehicles, the packet loss measured by the proposed BDTC-SIOVTs is 282 packets, and for the earlier works, it is LAKA-IOD (457 packets), NCAS-IOD (361 packets), and TPDA-IOV (346 packets). So, it is understood that the proposed BDTC-SIOVTs produce around 140 packets to 270 packets lower loss of packets when compared with the earlier works. In terms of the number of vehicles, the throughput measured by the proposed BDTC-SIOVTs is 782 Kbps, and for the earlier works, it is LAKA-IOD (354 Kbps), NCAS-IOD (502 Kbps), and TPDA-IOV (542 Kbps). So, it is understood that the proposed BDTC-SIOVTs achieve around 240 Kbps to 400 Kbps better throughput when compared with the earlier works. Throughput of the proposed BDTC-SIOVTs is high and it is achieved using the concept of enhanced trust with hybrid optimization during transmission.
6. Conclusions
This research proposed a novel Bio-inspired Dynamic Trusted Congestion-Aware Zone-based Internet of Drone Things (BDTC-SIOVTs) to provide trust estimation and congestion control. To secure the data transmission from the network threads, a triple-layer trust model is performed through the dynamic trust estimation method. To improve the network mobility, the congestion-aware community is constructed which predicts the congestion, and to reduce the routing overhead, hybrid optimization is performed. Using these methods, the network is protected from security issues and traffic-oriented issues. The performance analysis is performed using two scenarios, such as (i) the performance analysis with varying speed from 10 m.s−1 to 35 m.s−1 and with varying attacks. The performance of the proposed BDTC-SIOVTs is high in terms of parameters such as energy efficiency, packet delivery ratio, and throughput for the other attacks. However, the overall performance is comparatively low for the position falsification attack, which is the major limitation of this research. It needs some more attention in the future.
In the second scenario (ii), the performance is calculated in terms of vehicles, and it is compared with the earlier works. The energy efficiency of the proposed BDTC-SIOVTs is 7% to 17% higher, packet delivery ratio is 5% to 14% better, routing overhead is 1300 packets to 3000 packets lower, end-to-end delay is 90 ms to 200 ms lower, packet loss is around 140 packets to 270 packets lower, and throughput is 240 Kbps to 400 Kbps higher than the earlier methods, such as LAKA-IOD, NCAS-IOD, and TPDA-IOV. The proposed BDTC-SIOVTs is more feasible because of the presence of drones in it; however, the consumption of energy needs to be concentrated further, though it achieved some further enhancement in performance. In future research, the proposed BDTC-SIOVTs will be applied in satellite-assisted drone-enabled VANETs.