1. Introduction
It is difficult to conceptualize corruption from a social science standpoint because it can apply to a wide range of social activities and actions that will or will not be considered morally or even legally repugnant, depending on a specific set of cultural factors or beliefs [
1]. However, according to other academics, corruption is an unpleasant and damaging behavior committed by people, such as unlawful gratitude, abusing a public position for personal benefit, or misusing public authority for one’s benefit [
2,
3]. It is a cancer for political, social, and economic reform and is sometimes referred to as a “worm inside the body of society” [
4]. From the beginning of human history to the present time, corruption has been considered one major unavoidable social disease and has been associated with human being interactions [
5]. It has been a socio-economic phenomenon or social threat that is rarely visible and is difficult to measure; however, theoretical discussions have tackled this phenomenon with enthusiasm but, due to the lack of firsthand real data, have rarely produced substantial results [
6,
7]. From minor violations or acts of unlawful remuneration to extensive mass theft by public authorities, corruption is a multifaceted topic and also has a significant negative impact on sustainable development and is known to cause inefficiencies, diversion of basic resources, and inequality as a result of such impacts [
8,
9]. The historical and cultural backgrounds of nations throughout the world have made great contributions to the intensity of corruption diffusion [
10]. Since low corruption levels are related to high levels of institutional and social trust, the terms corruption and institutional quality play a fundamental role in a country’s socioeconomic development and overall welfare [
11,
12,
13].
To develop the data and test their theories, sociologists who investigate the curse of corruption need to have a thorough understanding of history, society, language, and impacts from at least one intricate and detailed illustration [
14]. The following conditions can be identified as mechanisms by which to mitigate corruption, even though complete eradication remains unattainable: a strong commitment to governance coupled with a spiritual engagement in the advancement of national and bureaucratic objectives; effective administration, along with suitable structural reforms within governmental frameworks and regulations to minimize the emergence of corruption; favorable historical and sociological contexts; the establishment of a robust anti-corruption value system; leadership from influential groups characterized by high moral and intellectual integrity; and a well-informed public capable of critically evaluating and responding to unfolding events [
14].
Numerous scholars have developed and examined mathematical models pertaining to system dynamics in a variety of fields, such as the natural sciences, social sciences, and other fields [
15,
16]. While some studies have used fractional order derivatives, such as investigations [
17,
18], others have used integer order modeling, such as studies [
19], to study real-world scenarios. Since its initial construction and analysis in 1975, the mathematical modeling of corruption has drawn the attention of numerous scholars due to its detrimental effects on society [
5]. The diffusion of corruption has been the subject of numerous mathematical model studies, including [
4,
20,
21]. We reviewed a number of studies in order to develop and evaluate our suggested fractional-order corruption diffusion model.
The rationale behind reviewing these studies was to determine the fundamental ideas of mathematical modeling, theories, methods, and methodologies, as well as to pinpoint any gaps or limitations. A six-compartmental fractional order optimal control problem for corruption diffusion dynamics was developed and examined by Bonyah Ebenezer [
5]. The study did not conduct a cost-effectiveness analysis or divide the compromised individuals into two groups: ignorant and aware. Using optimum control strategies, Athithan et al. [
21] investigated a corruption dissemination dynamical system. The cost-benefit of their suggested controlling activities was not evaluated, and their model, the standard SIR model, did not consider the different corruption statuses of people, such as their aware and unaware status. Danford, Oscar [
22], “Corruption dynamics in Tanzania: Modeling the effects of control strategies”. A deterministic corruption diffusion dynamical system that considered the possible optimal control activities was developed and examined by Fantaye et al. [
23]. Both the cost-benefit investigation of their suggested control activities and the different corruption statuses of individuals, such as their aware and unaware status, were not considered by their model. The study’s conclusions demonstrated that the best way to stop corruption from spreading was through prevention and punishment. An epidemiological corruption model with an immunity clause in Nigeria was developed and studied by Gweryina et al. [
20]. Although they conducted both qualitative and quantitative analysis, they did not carry out a cost-benefit investigation. To investigate a corruption issue throughout the community, the study carried out by Alemneh et al. [
24] investigated a corruption diffusion dynamical system with controlling activities. An investigation of cost-effectiveness was not conducted in their study. Tesfaye et al. [
25] developed and examined the diffusion dynamics of stochastic corruption with transient immunity. Their four-class approach omitted cost-effectiveness analysis and optimum control theory. A dynamical system for corruption diffusion that took media coverage into consideration was developed and examined by Birhanu et al. [
4]. Since their model took into account the effect of media coverage, it is unique when compared to other studies in the field. It did not, however, carry out cost-effectiveness analysis or optimal control. According to what we learned from the literature evaluation, no other researcher built a corruption diffusion dynamical system that takes into consideration both the conscious and uninformed classes. This study’s distinctiveness is ensured by the fact that it completed the cost-benefit for the proposed control activities investigation.
Our proposed study’s primary goal is to use a fractional order derivative approach in conjunction with the optimum control principle and cost-benefit investigation to examine how the proposed control measures affect the corruption diffusion problem. By taking into account three time-dependent regulating strategies, this paper primarily examines the corruption optimal control dynamical system with a fractional order derivatives approach. Additionally, there are corrupted and unaware and corrupted and aware subgroups within the human population of the corrupted group. Preventing corruption and improving the lives of those who are corrupted, both aware and unaware, are the controlling methods that we took into consideration. In order to investigate the most cost-benefit control activity to reduce and control the corruption diffusion, we numerically simulated the reconstructed control problem and conducted a cost-effectiveness investigation. The following parts comprise the remaining portion of this work:
Section 2 defines the basic concepts of fractional calculus;
Section 3 formulates and analyzes the fractional order model for corruption diffusion;
Section 4 reformulates the fractional order control problem;
Section 5 presents the results of the numerical simulation;
Section 6 provides the cost-benefit investigation; and
Section 7 concludes and provides future directions for the proposed study.
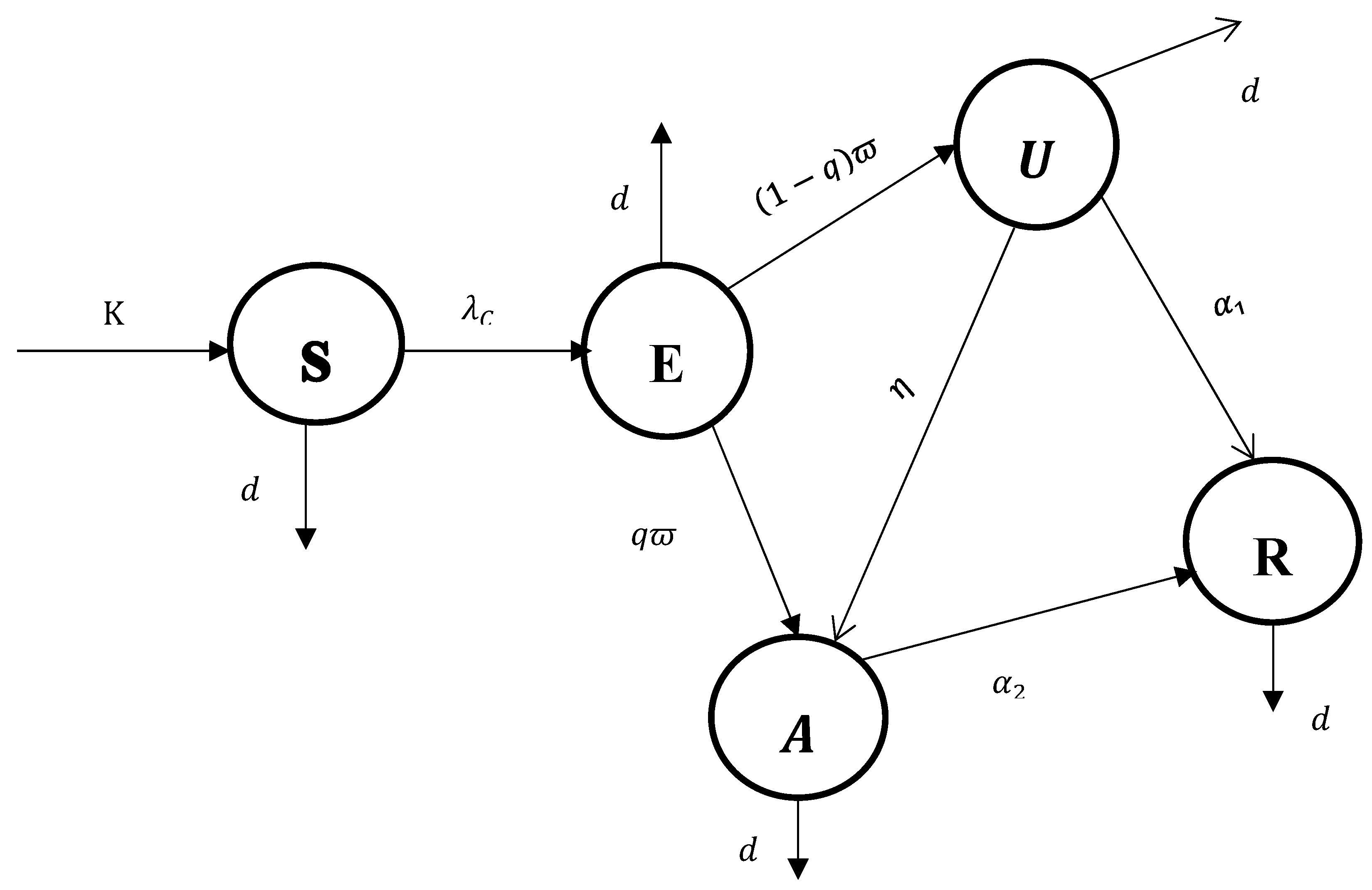
4. Theoretical Investigation of the Control Dynamics
Here, let us modify the corruption diffusion dynamical system (3) by considering three time-based control techniques. To express the control measures incorporated into the corruption diffusion dynamics in the community, we denoted the functions as the protection control activity, as the improvement activity, and as the improvement activity, such that 0 and are the Lebesgue measurable controlling functions.
Measures to prevent corruption. The degree of the corruption prevention mechanism, or the efforts carried out to stop people from engaging in corrupt practices, is denoted by the control activity .
Corruption Improvement Techniques: The time-dependent control measures for unaware and aware corrupted persons are represented by and , respectively.
The new optimal control dynamical system for the dynamical system (3) is reconstructed as:
where
,
,
,
and the set
, which contains control techniques where
is the last moment to put control measures into action. The goal of constructing the control dynamical system is, at the expense of implementing control techniques, to raise the repentant people number and decrease the number of exposed people, unaware corrupted people, and aware corrupted people. In order to reduce the corrupted people, we construct the objective function denoted by
System (15) minimizes , and in order to regulate the corrupted people number and the expense of applying protection and improvement control activities. The final time is represented by the constant in this section, the coefficients and are positive constants, and the costs relative to protection and improvement activities, , and , correspond to the controls , and , respectively. Additionally, the units of integrand are balanced. The purpose is to minimize the objective function and determine the ideal values of the controls so that the state trajectories are solutions of (15) in the specified time range with starting data. The cost associated with exposed individuals is denoted by the phrase “” in the cost functional, the cost associated with moderately corrupted persons by the term “”, and the cost associated with severely corrupted individuals by the term “”. Additionally, is the last time the control measures are applied, and and are constants that are non-negative and indicate the cost for the triple control activities implementation and the related attempts to reduce the diffusion of corruption, respectively, for .
Subject to the dynamical system represented by (14) with the given initial criteria, the goal of the corruption diffusion dynamical system (14) is to find the optimal value of the control activity that minimizes the objective function described as . The controlling vector is , and the acceptable controls are the set .
Existence and Suitability of Control Techniques: It is possible to rewrite the corruption diffusion dynamical system (3) with (4) as
where
symbolizes the variables,
represents control activities of the model (14), and
Here, we must demonstrate the existence of the three ideal control techniques by proving the following conditions: the collection of control functions is a convex set, a bounded set, and a closed set, the control trajectories are non-empty, and is constrained by the control variables and state variables, and on the collection is convex.
Note that: The requirements listed below are predicated using definitions from the manuscript: as per the collection, the definition is a convex set, a bounded set, and a closed set. Since for , the system dynamics (14) solutions are uniquely constrained based on similar criteria applied in the system dynamics (3). The solution for the system dynamics (3) with the supplied initial population is non-empty with control functions values of , and in the admissible control set described above.
Theorem 6. The function represented by meets at the corruption diffusion system dynamics solution , where , , and .
Proof. Let us describe
as
where
. Based on the conditions of the matrix
, we get
and, because we have demonstrated that the solution is bounded,
. With the same approach, one can prove that
.□
Theorem 7. We construct a function described by in the admissible control zone , which is convex, and k is a non-negative parameter that exists and that satisfies .
Proof. For function
one can obtain the matching matrix (Hessian), which is provided as
Consequently, is strictly convex in , since described above is a positive definite diagonal matrix in the area . Let , then . Hence, we establish the required proof.□
Theorem 8. The model-associated solutions as well as the optimal control point that minimize on the collection so that .
The requirement for optimality is, according to [
17], the optimality necessary condition that the optimal control issues (14) and (15) must satisfy comes from Pontryagin’s Maximum Principle. Additionally, it is satisfied by transforming into a function (Hamiltonian function) that minimizes regard to the control activities
. The following is the derivation of the equivalent Hamiltonian for (14) and (15):
where the co-state or adjoint variables are
and
at time t.
Theorem 9. Given solutions at and solutions of the system dynamics (14) that minimize the function illustrated in (15) in the region , there exist adjoints , and such that s:
where
Then, for previously specified function H system’s transversality criteria,
at
and the previously specified function H. Additionally, the best control parameters (
,
,
) that minimize
over
are given by:
where
adjoint variables, satisfying (14)–(16) with the following transversality conditions:
and
Proof. Using similar approaches used in reference [
19,
36], applying the Pontryagins Maximum Principle, we can determine that the convexity of the integrand of
with respect to controls
and
, the boundedness of the state solutions, and the Lipschitz property of the state system with respect to the state variables all lead to the existence of an optimal solution with the corresponding optimal control result represented by:
C, C, C, C and C = . Thus, the optimality conditions are obtained by differentiating the Hamiltonian function with respect to the control variables and : . □
5. Results of Numerical Simulations
For quantitative validation of the theoretical investigation described in the previous sections, particularly the optimal control system dynamics (14), this study carried out simulations using numerical approaches by considering the values for the corruption diffusion system dynamics parameter values represented in
Table 2 below.
Performing simulations for the corruption diffusion dynamics optimal control system (14) is fundamental to the vital pictorial view and verifies the qualitative (theoretical) investigation of the proposed dynamical system with optimal control strategies. Therefore, by modeling the execution of the potential strategy combinations of the suggested control measures, we report the simulation results of the study in this section. Considering
Table 2 above, the optimal control system dynamics (14) were simulated using MATLAB 2016a and the usual Runge-Kutta numerical approach. Three scenarios, the application of single control activity, dual control activities, and triple control activities with assumed cost weight parameter values, were created from the potential combination strategies of the suggested control measures as
,
,
,
and with various starting population numbers. We used the fractional order constant
to numerically simulate the system dynamics variables in the optimum control system dynamics (14) for investigating the effects of the proposed control activities in the following three scenarios and possible methods in each of the scenarios.
Scenario A (Implement single control measure)
- ➢
Strategy 1: practicing the protection control measures, such as education, media awareness, etc. (i.e., ).
Scenario B (Implement double control measures)
- ➢
Strategy 2: practicing the improvement control measures, such as education, fear of punishments, etc. () for unaware corrupted individuals.
Scenario C (Implement triple control measures)
- ➢
Strategy 3: practicing the protection control measures, such as education, media awareness, etc. Practicing the improvement control measures, such as education, fear of punishments, etc., for both unaware and aware corrupted people, which means , and .
The effect of the strategy (i.e.,
,
, and
) known as the corruption prevention mechanism, by setting
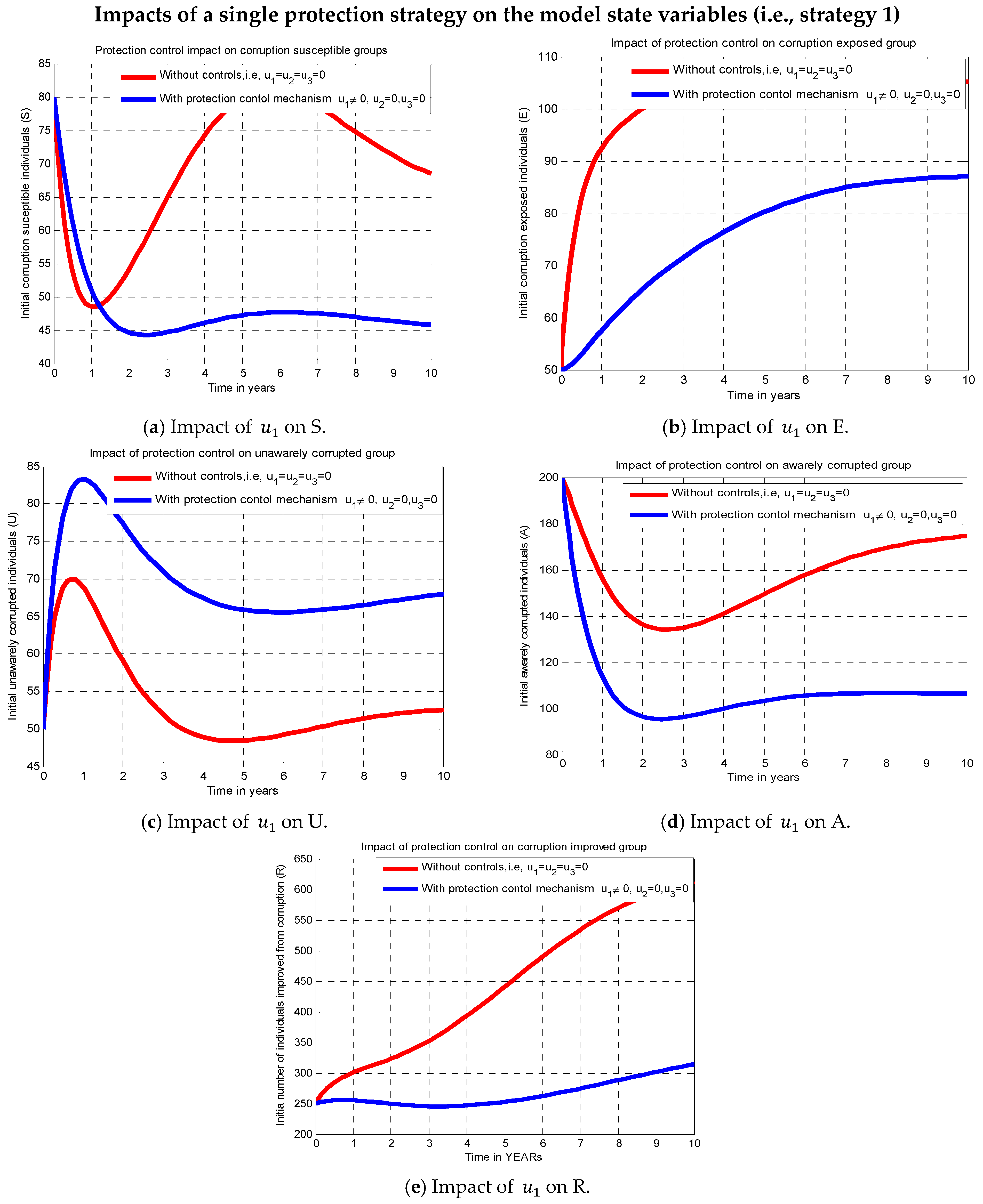
, is examined in this subsection through numerical simulations where protection or improvement control strategies were not applied and when the corruption diffusion prevention strategy (strategy 1) was applied.
Figure 2a–e each display a graphical interpretation that illustrates how the preventative method affects the dynamics of corruption diffusion. All susceptible, exposed, unaware corrupted, aware corrupted, and enhanced persons are drastically reduced when the protection control strategy
is used, in contrast to the simulation scenario in which no control strategies were used.
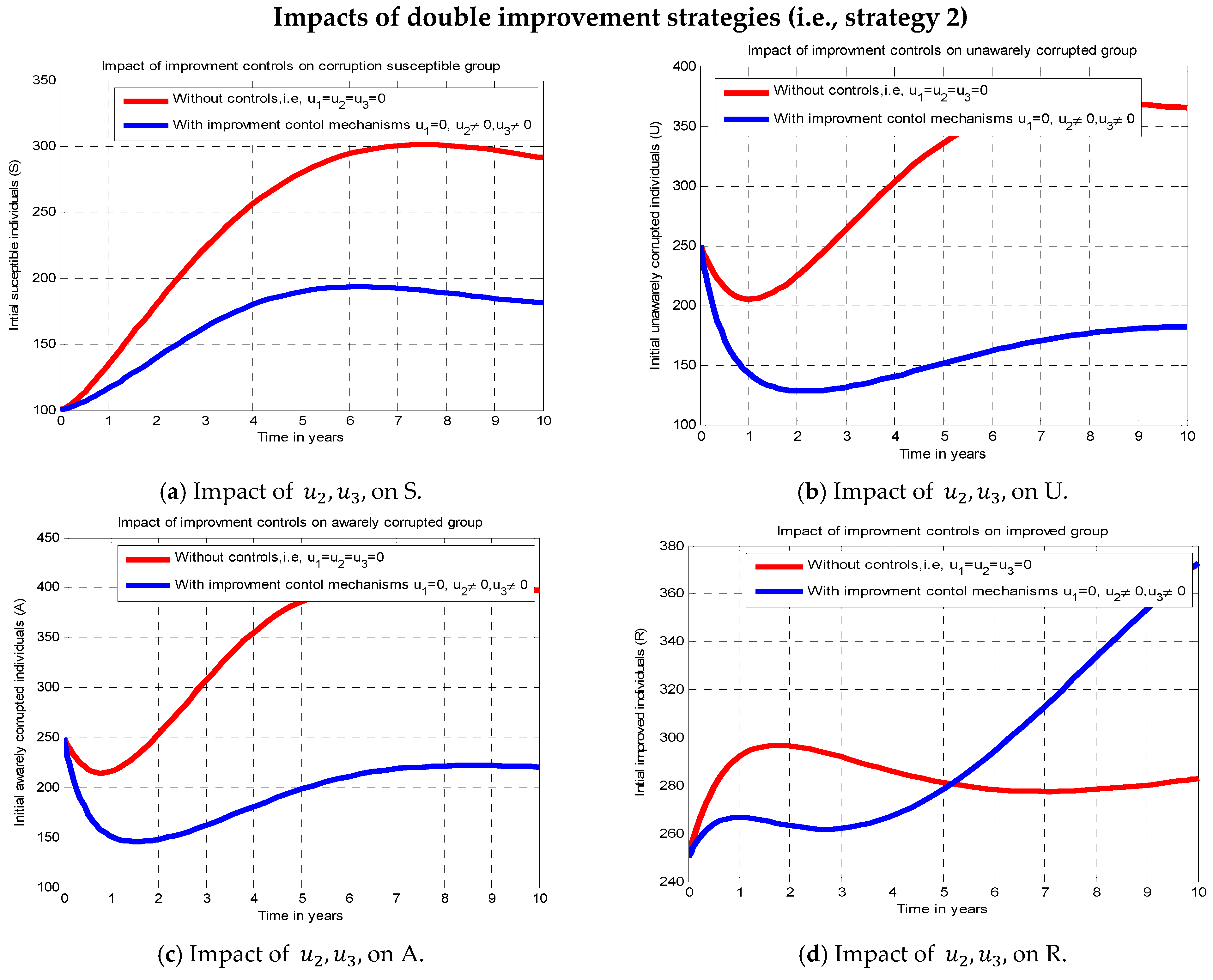
In this subsection, we conduct numerical simulations using the improvement strategies
and
, i.e., strategy 2), and without using the corruption protection control strategy
). According to the simulation revealed in
Figure 3 above,
Figure 3a indicates that the number of people in the exposed class decreased somewhat in comparison to
Figure 2b.
Figure 3b,c confirm the effect of using double improvement strategies and show a rapid decline in comparison to the results in
Figure 2c and
Figure 2d, respectively. The impact of using double improvement control procedures is confirmed in
Figure 3d, which also demonstrates that as improvement strategies rise, so does the number of people who are rescued from corrupted activities.
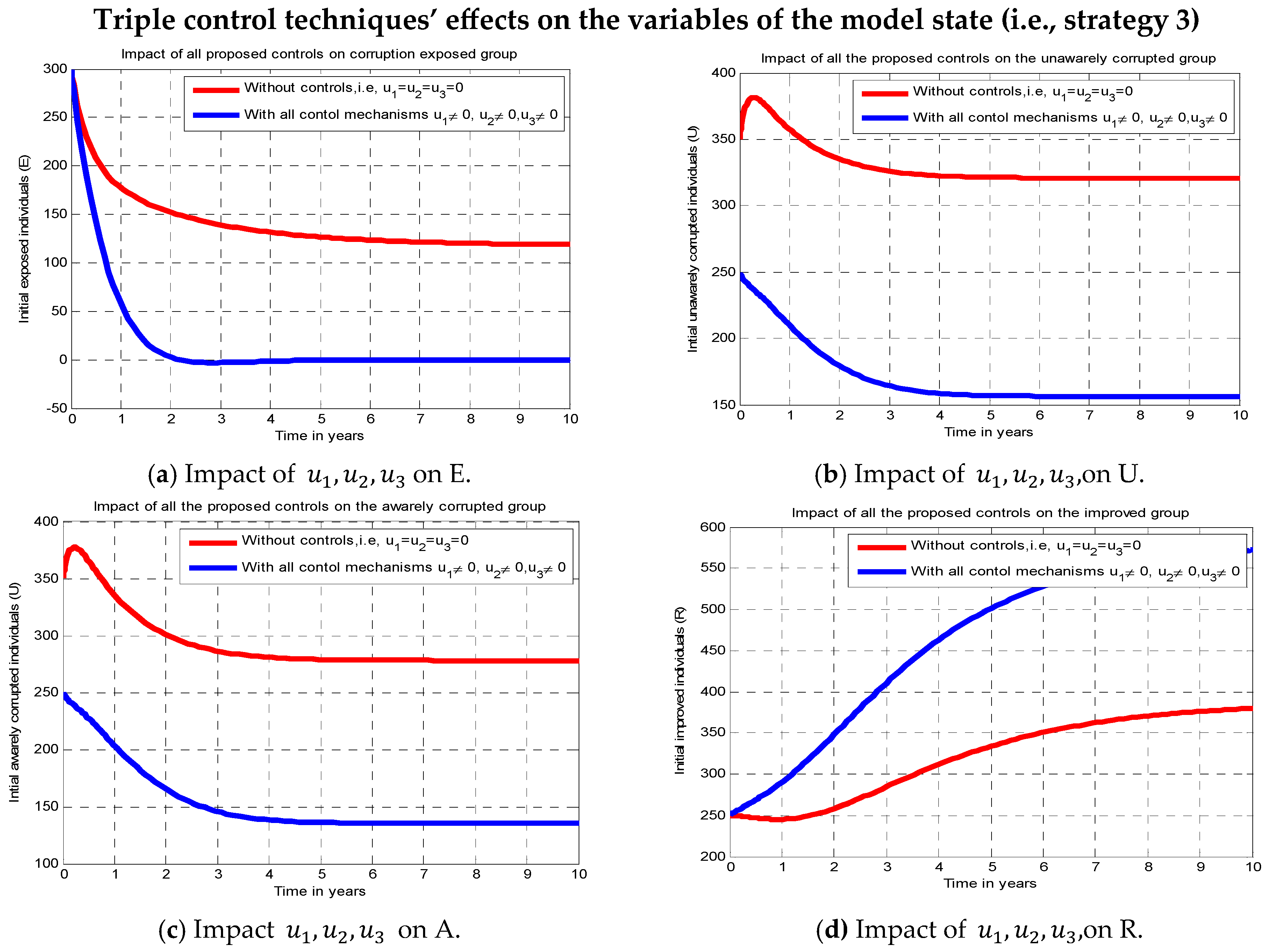
In this subsection, we conduct numerical simulations both with and without the implementation of all suggested regulating techniques
and
(strategy 3) at the same time. We can examine the impacts of various control tactics on the system dynamic variables corruption status based on the results shown in
Figure 4. All of the suggested controlling strategies have a significant result in reducing the exposed people by simulating without implementing all of the suggested control strategies, and by implementing any other control strategies, as shown in
Figure 4a.
Figure 4b illustrates the impact of putting all of the suggested controlling strategies into practice using the number of people who are unaware of corruption. This has a significant result in reducing people who are unaware and corrupted in comparison to the numbers shown in
Figure 2c and
Figure 3b, respectively. As compared to the corrupted people depicted in
Figure 2d and
Figure 3c, respectively,
Figure 4c illustrates the impact of all suggested controlling strategies on the number of aware corrupted individuals and significantly reduces that number. In contrast to the number of repented persons depicted in
Figure 2e and
Figure 3d, respectively,
Figure 4d illustrates the influence of all suggested control activities on the repented (improved) individuals and significantly increases repented people. Lastly, we can see from
Figure 4 that, after ten years, corrupted people in the population significantly decline if all potential regulating activities
and
i.e., using strategy 3) are put into practice. Additionally, this approach is the most successful in reducing and controlling the dynamics of corruption dissemination in the population when compared to other approaches.
Figure 5 above reveals that whenever the fractional order constant decreases, the number of unaware and corrupted individuals decreases due to the memory effect of the fractional order derivative.