Weaponization of the Growing Cybercrimes inside the Dark Net: The Question of Detection and Application
Abstract
1. Introduction
- Comprehensive Review: We provide an exhaustive review of the emerging criminal activities on the Dark Web, assessing their social, economic, and ethical impacts.
- Challenges Identification: We identify and discuss the various challenges and obstacles associated with detecting and tracing criminals on the Dark Net.
- Analytical Techniques: We evaluate established techniques and methods used by law enforcement and cybersecurity professionals to locate and apprehend perpetrators.
- Research Insights: By addressing two primary research questions, we offer valuable insights into the nature of threats on the Dark Net and the efficacy of current countermeasures.
- Future Recommendations: We propose future measures to mitigate crime threats, suggesting improvements in crime monitoring and locating technologies.
- -
- This paper presents a comprehensive examination of the emerging criminal activities taking place on the Dark Web, along with the resulting impacts on social, economic, and ethical structures.
- -
- Additionally, the study discusses the challenges and obstacles associated with identifying and tracing perpetrators of these crimes, as well as the various techniques and methods utilized to locate them and their offenses, including their limitations.
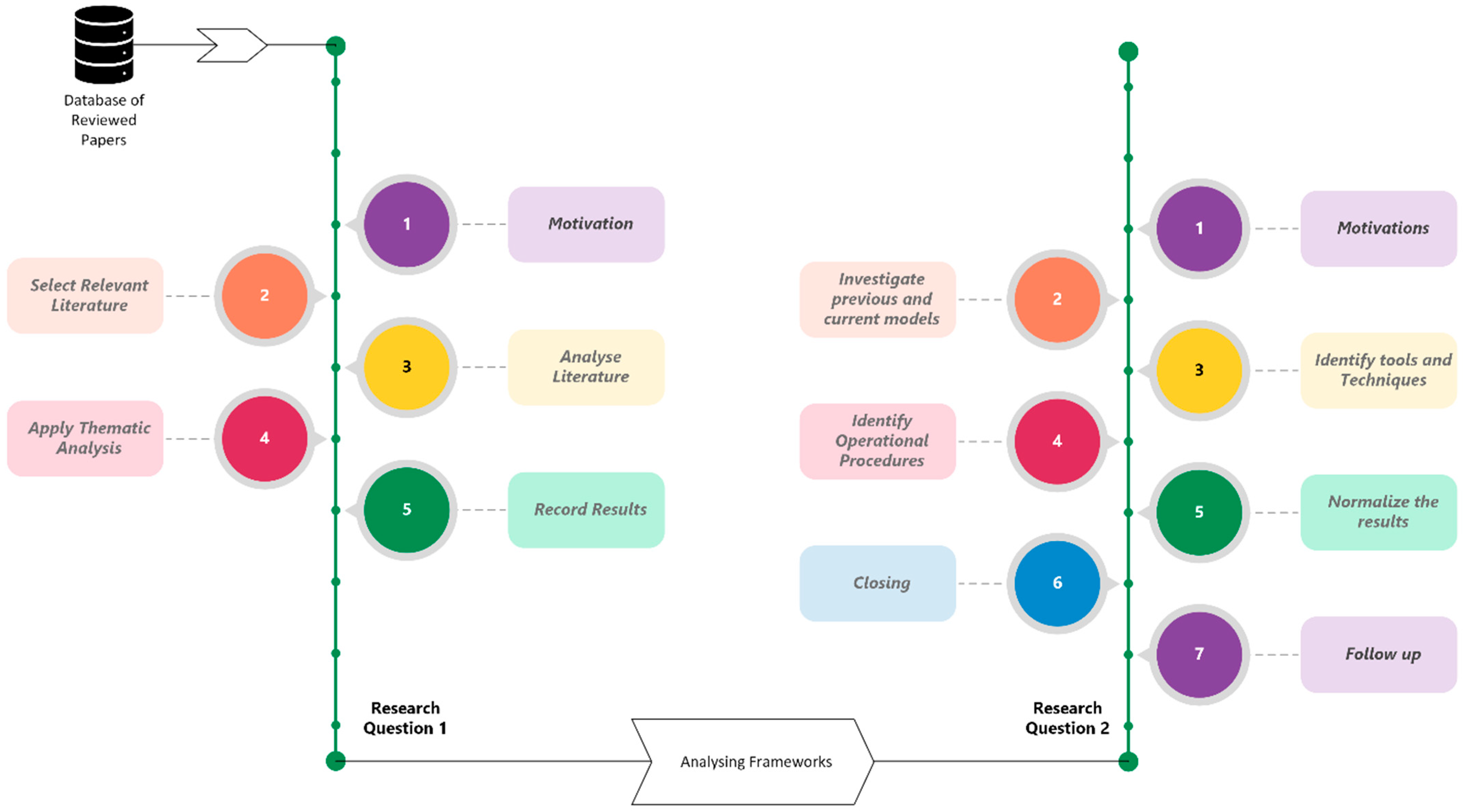
2. Review Methodology
2.1. Research Questions
2.2. Search Strings and Criteria
2.3. Data Extraction and Synthesis
3. Demographic Information
- Primary Studies
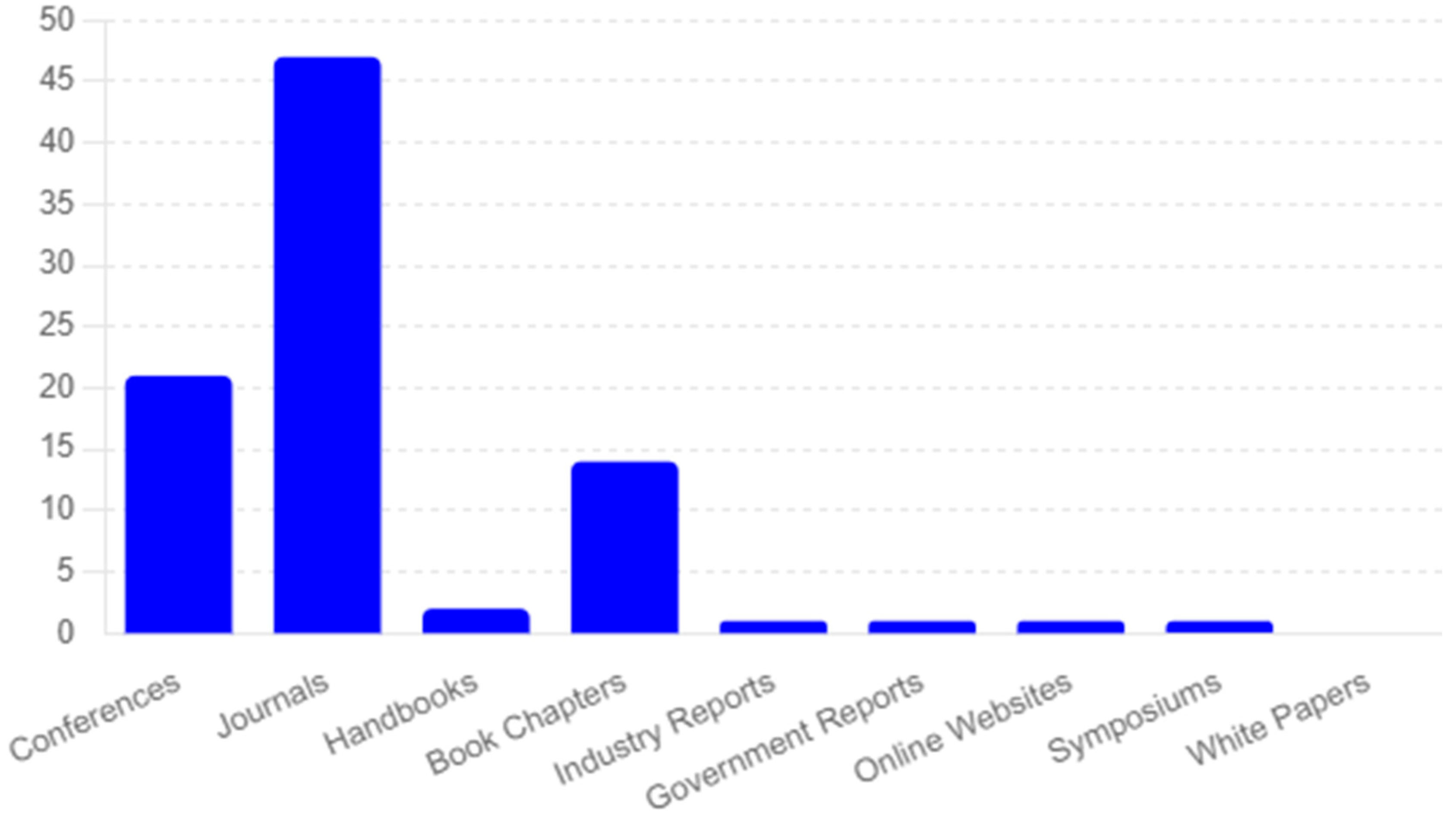
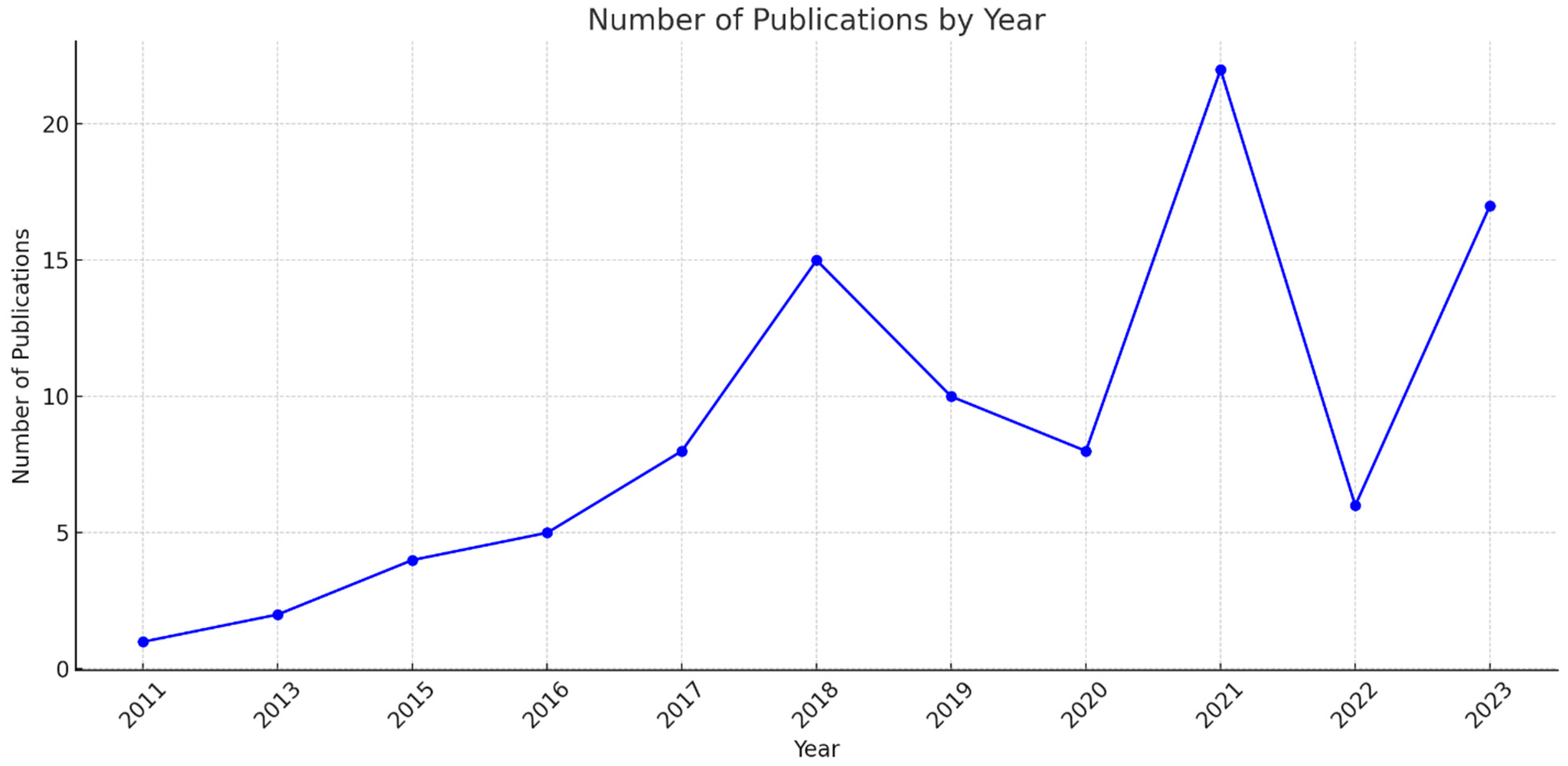
3.1. Types of Publications
3.2. Publications by Year
3.3. Publication Sources and Countries
4. Findings
4.1. Activities on the Dark Web
- Illegal Marketplaces: The Dark Web is notorious for illegal marketplaces that sell a wide range of illicit goods and services, such as drugs, weapons, counterfeit documents, stolen data, and hacking tools.
- Cybercrime-as-a-Service: Criminals offer various hacking services on the Dark Web, such as DDoS attacks, malware creation, and phishing campaigns for a fee.
- Identity Theft: Criminals can buy or sell stolen personal information, such as credit card numbers, social security numbers, and passwords, on the Dark Web.
- Child Exploitation: The Dark Web hosts illegal websites that exploit children, such as child pornography and human trafficking.
- Money Laundering: Criminals use the Dark Web to launder money by exchanging cryptocurrencies or converting illegal funds into legitimate assets.
- Espionage: Nation-states and other actors can use the Dark Web to conduct espionage activities, such as stealing sensitive data or launching cyber-attacks on critical infrastructure.
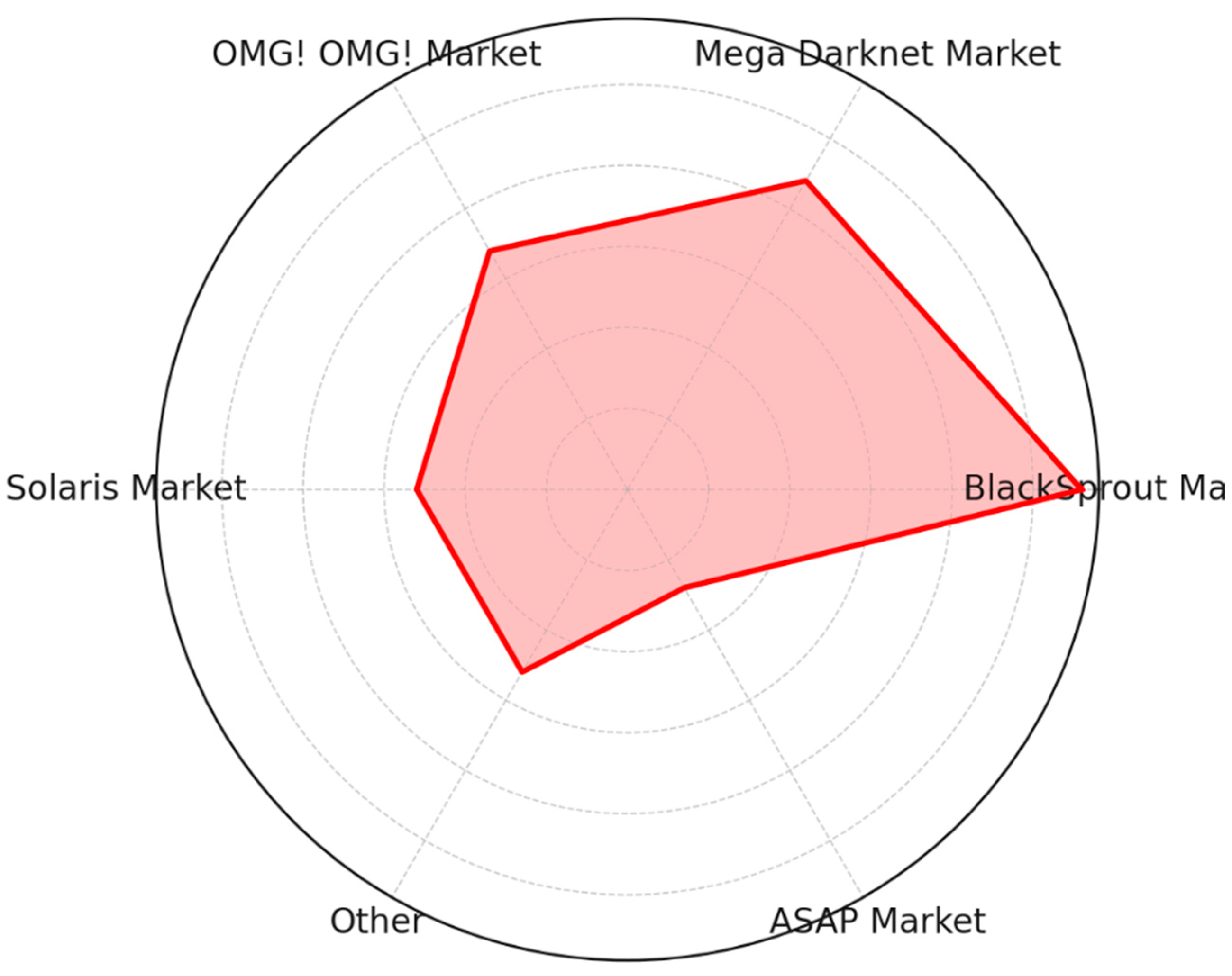
4.1.1. Illegal Marketplaces
- -
- -
- According to a report by Chainalysis, the total revenue generated from Dark Net marketplaces in 2020 was USD 1.7 billion, with most transactions involving drugs, fraud, and stolen data [25].
- -
- The same report found that the Dark Net market revenue from cryptocurrencies increased by over 60% in 2020, with Bitcoin being the most used cryptocurrency for transactions on these marketplaces.
- -
- The most sold drugs on Dark Net marketplaces include marijuana, cocaine, and opioids like fentanyl [59].
4.1.2. Cybercrime-as-a-Service
4.1.3. Identity Theft
4.1.4. Child Exploitation
- -
- In the study ‘Protecting Children’s Rights: A Comparative Analysis between Vietnam and the Legal Models of the European Union and Hungary’ [78], it was revealed that over 2200 individuals were identified in cases related to child abuse, underscoring the pervasive issue of child exploitation within these regions.
- -
- The research ‘Online Child Sexual Exploitation and Abuse: Criminal Justice Pathways of Police-Reported Incidents in Canada, 2014 to 2020’ [79] highlights the critical issue of online child exploitation in Canada, detailing the pathways through the criminal justice system for such cases over a six-year period.
- -
- An anthropological investigation titled ‘An Anthropological Investigation of Assam—the Human Trafficking Hub of India?’ [80] examines Assam’s significant challenges with human trafficking and exploitation, particularly affecting vulnerable local children and women.
- -
- A correlational study aimed at analyzing the knowledge and attitude towards early marriage among parents in selected rural areas of Kolhapur District [81] identifies child marriage as a critical form of exploitation, highlighting the need for increased awareness and education among parents to protect children’s rights.
4.1.5. Money Laundering
4.1.6. Espionage
- -
- The WannaCry attack in 2017 not only disrupted IT systems but also had tangible effects on healthcare services, particularly within the UK’s National Health Service (NHS). A study analyzing the impact of WannaCry on the NHS found a notable decrease in hospital activity, including a 6% drop in total admissions per day during the attack. Emergency admissions decreased by 4% and elective admissions by 9%, and there were significantly fewer A&E attendances and outpatient services. The economic value of reduced activity in infected trusts during the attack week was estimated at GBP 5.9 million. If all trusts had been affected similarly, the total value of lost activity could have amounted to GBP 35 million [90].
- -
- In another case, in 2018, the United States Department of Justice indicted 12 Russian intelligence officers for their involvement in hacking the Democratic National Committee during the 2016 US presidential election. The hackers used the Dark Web to communicate and exchange stolen information, and they were able to evade detection for several years [91].
4.2. Tracking the Criminals on the Dark Web
- Data Mining: This involves using advanced data analysis tools to collect and analyze large volumes of data from various sources on the Dark Web, such as online marketplaces, forums, and social media platforms [43]. The data can include keywords, images, and metadata, which can be used to identify patterns and links between criminal activities and the individuals involved.
- Blockchain Analysis: Many illegal transactions on the Dark Web are conducted using cryptocurrencies like Bitcoin, which offer a high degree of anonymity [50]. However, all transactions on the blockchain are publicly recorded, and this data can be used to trace the flow of funds and identify individuals involved in criminal activities.
- Social Engineering: This involves using psychological manipulation techniques to trick criminals into revealing their identities or locations [93]. Social engineering tactics can include phishing emails, fake social media accounts, and other types of online impersonation.
- Law Enforcement Collaboration: Law enforcement agencies around the world are increasingly collaborating to share information and resources to locate and arrest criminals on the Dark Web [30]. This includes the use of international arrest warrants, extradition agreements, and joint task forces.
- Dark Web Crawlers: These are automated tools that search the Dark Web for specific keywords or phrases and can help identify illegal activities, marketplaces, and individuals involved in criminal activities. While Deep Web crawling is included under data mining due to its broader focus on non-indexed online content, Dark Web crawling is separately categorized because it specifically targets encrypted and anonymized networks such as TOR. This requires specialized techniques and tools distinct from those used for general data mining, emphasizing the unique challenges and methodologies associated with investigating the Dark Web [24].
- Human Intelligence: While technology can help locate criminals on the Dark Web, it is often human intelligence that provides the most valuable information [17]. This can include tips from informants, undercover agents, and whistleblowers.
4.2.1. Data Mining
- -
- Keyword Search: Data mining tools can be used to search for specific keywords or phrases that are associated with criminal activities [24]. These keywords can include terms related to drug trafficking, human trafficking, weapons smuggling, and other illegal activities. By collecting data on these keywords, law enforcement agencies can identify the individuals and groups involved in these activities and take appropriate action.
- -
- Image Recognition: Data mining tools can also be used to recognize and analyze images posted on the Dark Web [20]. For example, images of weapons, drugs, and other illegal items can be identified and used to track down the individuals involved in their sale and distribution.
- -
- Network Analysis: Data mining tools can be used to identify patterns and links between individuals and groups involved in criminal activities on the Dark Web. By analyzing the network of connections between these individuals, law enforcement agencies can identify the most influential players and take targeted action to disrupt their activities [94].
- -
- Sentiment Analysis: Data mining tools can also be used to analyze the sentiment of online discussions related to criminal activities [95]. This can help law enforcement agencies identify potential threats and take proactive measures to prevent them from occurring.
- -
- Deep Web Crawling: Data mining tools can be used to crawl the Deep Web, which includes parts of the Dark Web that are not easily accessible using standard search engines [40]. By collecting data from these hidden areas, law enforcement agencies can gain a more complete understanding of the criminal activities taking place on the Dark Web.
4.2.2. Blockchain Analysis
- -
- Address Clustering: Blockchain analysis tools can be used to cluster together different addresses that are owned by the same individual or entity [31]. This can help law enforcement agencies to identify the parties involved in a particular transaction or activity on the blockchain.
- -
- Transaction Tracing: Blockchain analysis tools can also be used to trace the flow of funds on the blockchain. By following the trail of transactions, law enforcement agencies can identify the source and destination of funds, and the individuals and entities involved in the transaction [44].
- -
- Taint Analysis: Taint analysis is a technique used to identify the origin of tainted funds on the blockchain. Tainted funds are those that have been used for criminal activities, such as drug trafficking or money laundering. By analyzing the transactions involving tainted funds, law enforcement agencies can track down the individuals and entities involved in these activities [96].
- -
- Pattern Recognition: Blockchain analysis tools can be used to identify patterns in the transactions on the blockchain. For example, patterns may emerge in the amounts of funds transferred or in the timing of transactions. By analyzing these patterns, law enforcement agencies can identify potential criminal activity and take appropriate action.
- -
- Blockchain Data Mining: Blockchain data mining involves analyzing the blockchain to identify trends and patterns that may be indicative of criminal activity. This can involve analyzing the metadata associated with transactions, such as the time and location of transactions, as well as the types of transactions taking place [97].
4.2.3. Social Engineering
- -
- Phishing Attacks: Phishing attacks are a type of social engineering attack that involves sending fraudulent emails or messages in order to trick individuals into divulging sensitive information. By sending phishing emails or messages to Dark Web users, law enforcement agencies can potentially obtain information about the individuals and groups involved in criminal activities.
- -
- Impersonation: Impersonation is another social engineering technique that can be used to track criminals. Law enforcement agencies may create fake profiles or personas in order to gain the trust of Dark Web users and obtain information about criminal activities.
- -
- Spear Phishing: Spear phishing is a more targeted type of phishing attack that is directed at specific individuals or groups. By sending spear phishing emails or messages to Dark Web users, law enforcement agencies can potentially obtain more detailed information about the individuals and groups involved in criminal activities.
- -
- Vishing: Vishing is a type of social engineering attack that involves using voice communication to trick individuals into divulging sensitive information [98]. Law enforcement agencies may use vishing techniques to obtain information about criminal activities on the Dark Web.
- -
- Reverse Social Engineering: Reverse social engineering is a technique that involves manipulating individuals into taking certain actions, such as clicking on a link or downloading a file, in order to track their activities. Law enforcement agencies may use reverse social engineering techniques to track the activities of Dark Web users.
4.2.4. Law Enforcement Collaboration
- -
- Information Sharing: Law enforcement agencies can share information and intelligence about criminal activities on the Dark Web. This can include information about criminal networks, modus operandi, and tactics. By sharing information, law enforcement agencies can build a more complete picture of criminal activities on the Dark Web and identify potential targets for investigation.
- -
- Joint Investigations: Law enforcement agencies can collaborate on joint investigations into criminal activities on the Dark Web. By combining their resources and expertise, law enforcement agencies can conduct more effective investigations and improve their chances of tracking down criminals.
- -
- International Cooperation: Many criminal activities on the Dark Web are international in scope. Law enforcement agencies can work together across international borders to share information and intelligence, conduct joint investigations, and bring criminals to justice.
- -
- Cross-Agency Training: Law enforcement agencies can provide training and support to one another on how to investigate and track criminals on the Dark Web. This can include training on technical tools and techniques, as well as sharing best practices for investigating and prosecuting cybercrime.
- -
- Task Forces: Law enforcement agencies can form task forces to focus on specific types of criminal activities on the Dark Web. For example, task forces can be established to investigate child exploitation, drug trafficking, or money laundering on the Dark Web. By pooling their resources and expertise, task forces can conduct more targeted and effective investigations.
4.2.5. Dark Web Crawlers
- -
- Data Collection: Dark Web crawlers can be used to collect data from the Dark Web, including information about criminal activities, criminal networks, and potential targets for investigation. Crawlers can be configured to scrape specific websites, forums, and chat rooms for information, and the data collected can be used to build a more complete picture of criminal activities on the Dark Web.
- -
- Analysis: Once data have been collected, Dark Web crawlers can be used to analyze the data and identify patterns and trends. This analysis can help law enforcement agencies to identify potential targets for investigation and to build a case against individuals involved in criminal activities on the Dark Web.
- -
- Threat Intelligence: Dark Web crawlers can also be used to gather threat intelligence, including information about emerging threats and vulnerabilities on the Dark Web. This information can be used to inform law enforcement strategies and to develop new tools and techniques for investigating criminal activities on the Dark Web.
- -
- Automated Alerts: Dark Web crawlers can be configured to provide automated alerts when certain keywords or topics are detected. For example, a crawler could be configured to send an alert when it detects mentions of a specific criminal network or the sale of a particular illegal item on the Dark Web. These alerts can help law enforcement agencies to respond quickly to emerging threats and to gather intelligence about criminal activities.
4.2.6. Human Intelligence
- -
- Undercover Operations: Law enforcement agencies can use undercover agents to infiltrate criminal networks on the Dark Web. These agents can gather intelligence on criminal activities and help to identify key players in the network. Undercover operations can be risky, but they can provide valuable information that would be difficult to obtain through other means.
- -
- Informants: Informants are individuals who provide information to law enforcement agencies in exchange for some form of benefit or protection. Informants can be particularly valuable on the Dark Web, where anonymity is a key factor. By providing information about criminal activities, informants can help law enforcement agencies to identify targets for investigation and build a case against individuals involved in criminal activities on the Dark Web.
- -
- Community Outreach: Law enforcement agencies can also engage with communities that are vulnerable to exploitation on the Dark Web, such as victims of online child sexual exploitation. By building trust with these communities, law enforcement agencies can gather valuable information about criminal activities on the Dark Web and provide support to victims.
- -
- Collaboration: Collaboration between law enforcement agencies can also be a valuable source of HUMINT. By sharing information and resources, agencies can work together to identify and track criminals on the Dark Web. Collaboration can also help to build a more complete picture of criminal activities on the Dark Web, making it easier to identify and disrupt criminal networks.
4.3. Summative Evaluation of the Studies
5. Discussion
6. Limitations and Threats to Validity
7. Economic and Ethical Impacts
8. Conclusions and Future Research Directions
8.1. Conclusions
8.2. Future Research Directions
8.2.1. Development of Advanced Detection Technologies
8.2.2. Enhancement of Blockchain Analytics
8.2.3. Strengthening International Collaboration
8.2.4. Ethical and Legal Frameworks
8.2.5. Socio-Economic Impact Studies
8.2.6. Policy and Technological Innovation
8.3. Final Thoughts
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lawrence, S.; Giles, C.L. Searching the World Wide Web. Science 1998, 280, 98–100. [Google Scholar] [CrossRef] [PubMed]
- Kaur, S.; Randhawa, S. Dark Web: A Web of Crimes. Wirel. Pers. Commun. 2020, 112, 2131–2158. [Google Scholar] [CrossRef]
- Al Nabki, M.W.; Fidalgo, E.; Alegre, E.; de Paz, I. Classifying Illegal Activities on Tor Network Based on Web Textual Contents. In Long Papers, Proceedings of the 15th Conference of the European Chapter of the Association for Computational Linguistics, Valencia, Spain, 3–7 April 2017; Association for Computational Linguistics: Valencia, Spain, 2017; Volume 1, pp. 35–43. Available online: https://aclanthology.org/E17-1004 (accessed on 17 March 2023).
- Sharma, S.; Sharma, P. Dark Web and Trading of Illegal Drugs. J. Forensic Sci. Crim. Investig. 2018, 9, 555766. [Google Scholar]
- Davis, S.; Arrigo, B. The Dark Web and anonymizing technologies: Legal pitfalls, ethical prospects, and policy directions from radical criminology. Crime Law Soc. Chang. 2021, 76, 367–386. [Google Scholar] [CrossRef]
- Kavallieros, D.; Myttas, D.; Kermitsis, E.; Lissaris, E.; Giataganas, G.; Darra, E. Understanding the Dark Web. In Dark Web Investigation; Akhgar, B., Gercke, M., Vrochidis, S., Gibson, H., Eds.; Security Informatics and Law Enforcement; Springer International Publishing: Cham, Switzerland, 2021; pp. 3–26. [Google Scholar] [CrossRef]
- Montieri, A.; Ciuonzo, D.; Aceto, G.; Pescapé, A. Anonymity Services Tor, I2P, JonDonym: Classifying in the Dark. In Proceedings of the 2017 29th International Teletraffic Congress (ITC 29), Genoa, Italy, 4–8 September 2017; Volume 1, pp. 81–89. [Google Scholar] [CrossRef]
- Dredge, S. What Is Tor? A Beginner’s Guide to the Privacy Tool. The Guardian. 5 November 2013. Available online: https://www.theguardian.com/technology/2013/nov/05/tor-beginners-guide-nsa-browser (accessed on 3 March 2024).
- Tan, Q.; Wang, X.; Shi, W.; Tang, J.; Tian, Z. An Anonymity Vulnerability in Tor. IEEE/ACM Trans. Netw. 2022, 30, 2574–2587. [Google Scholar] [CrossRef]
- Luong, H.T. Foundations and trends in the darknet-related criminals in the last 10 years: A systematic literature review and bibliometric analysis. Secur. J. 2023. [Google Scholar] [CrossRef]
- Ruiz Ródenas, J.M.; Pastor-Galindo, J.; Gómez Mármol, F. A general and modular framework for dark web analysis. Cluster Comput. 2023. [Google Scholar] [CrossRef]
- Sarkar, G.; Shukla, S.K. Behavioral analysis of cybercrime: Paving the way for effective policing strategies. J. Econ. Criminol. 2023, 2, 100034. [Google Scholar] [CrossRef]
- Mengist, W.; Soromessa, T.; Legese, G. Method for conducting systematic literature review and meta-analysis for environmental science research. MethodsX 2020, 7, 100777. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S. Guidelines for performing Systematic Literature Reviews in Software Engineering; 2007; Volume 2. Available online: https://www.scirp.org/reference/ReferencesPapers?ReferenceID=1555797 (accessed on 21 May 2024).
- Chen, H. Dark Web: Exploring and Mining the Dark Side of the Web. In Proceedings of the 2011 European Intelligence and Security Informatics Conference, Athens, Greece, 12–14 September 2011; pp. 1–2. [Google Scholar] [CrossRef]
- Bahamazava, K.; Nanda, R. The shift of DarkNet illegal drug trade preferences in cryptocurrency: The question of traceability and deterrence. Forensic Sci. Int. Digit. Investig. 2022, 40, 301377. [Google Scholar] [CrossRef]
- Basheer, R.; Alkhatib, B. Threats from the Dark: A Review over Dark Web Investigation Research for Cyber Threat Intelligence. J. Comput. Netw. Commun. 2021, 2021, e1302999. [Google Scholar] [CrossRef]
- Bergman, J.; Popov, O.B. Exploring Dark Web Crawlers: A Systematic Literature Review of Dark Web Crawlers and Their Implementation. IEEE Access 2023, 11, 35914–35933. [Google Scholar] [CrossRef]
- Bermudez Villalva, D.A.; Onaolapo, J.; Stringhini, G.; Musolesi, M. Under and over the surface: A comparison of the use of leaked account credentials in the Dark and Surface Web. Crime Sci. 2018, 7, 17. [Google Scholar] [CrossRef]
- Biswas, R.; Fidalgo, E.; Alegre, E. Recognition of service domains on TOR dark net using perceptual hashing and image classification techniques. In Proceedings of the 8th International Conference on Imaging for Crime Detection and Prevention (ICDP 2017), Madrid, Spain, 13–15 December 2017; pp. 7–12. [Google Scholar] [CrossRef]
- Cherqi, O.; Mezzour, G.; Ghogho, M.; El Koutbi, M. Analysis of Hacking Related Trade in the Darkweb. In Proceedings of the 2018 IEEE International Conference on Intelligence and Security Informatics (ISI), Miami, FL, USA, 8–10 November 2018; pp. 79–84. [Google Scholar] [CrossRef]
- Chertoff, M. A public policy perspective of the Dark Web. J. Cyber Policy 2017, 2, 26–38. [Google Scholar] [CrossRef]
- Dalins, J.; Wilson, C.; Carman, M. Criminal motivation on the dark web: A categorisation model for law enforcement. Digit. Investig. 2018, 24, 62–71. [Google Scholar] [CrossRef]
- Dalvi, A.; Paranjpe, S.; Amale, R.; Kurumkar, S.; Kazi, F.; Bhirud, S.G. SpyDark: Surface and Dark Web Crawler. In Proceedings of the 2021 2nd International Conference on Secure Cyber Computing and Communications (ICSCCC), Jalandhar, India, 21–23 May 2021; pp. 45–49. [Google Scholar] [CrossRef]
- ElBahrawy, A.; Alessandretti, L.; Rusnac, L.; Goldsmith, D.; Teytelboym, A.; Baronchelli, A. Collective dynamics of dark web marketplaces. Sci. Rep. 2020, 10, 18827. [Google Scholar] [CrossRef] [PubMed]
- Faccia, A.; Moşteanu, N.R.; Cavaliere, L.P.L.; Mataruna-Dos-Santos, L.J. Electronic Money Laundering, The Dark Side of Fintech: An Overview of the Most Recent Cases. In Proceedings of the 2020 12th International Conference on Information Management and Engineering, Amsterdam, The Netherlands, 16–18 September 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 29–34. [Google Scholar] [CrossRef]
- Fronzetti Colladon, A.; Remondi, E. Using social network analysis to prevent money laundering. Expert Syst. Appl. 2017, 67, 49–58. [Google Scholar] [CrossRef]
- Gehl, R.W. Power/freedom on the dark web: A digital ethnography of the Dark Web Social Network. New Media Soc. 2016, 18, 1219–1235. [Google Scholar] [CrossRef]
- Georgoulias, D.; Pedersen, J.M.; Falch, M.; Vasilomanolakis, E. A qualitative mapping of Darkweb marketplaces. In Proceedings of the 2021 APWG Symposium on Electronic Crime Research (eCrime), Boston, MA, USA, 1–3 December 2021; pp. 1–15. [Google Scholar] [CrossRef]
- Ghappour, A. Searching Places Unknown: Law Enforcement Jurisdiction on the Dark Web. Stan. L. Rev. 2017, 69, 1075. Available online: https://heinonline.org/HOL/Page?handle=hein.journals/stflr69&id=1101&div=&collection= (accessed on 2 March 2024). [CrossRef]
- Ghosh, S.; Das, A.; Porras, P.; Yegneswaran, V.; Gehani, A. Automated Categorization of Onion Sites for Analyzing the Darkweb Ecosystem. In Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Halifax, NS, Canada, 13–17 August 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 1793–1802. [Google Scholar] [CrossRef]
- Godawatte, K.; Raza, M.; Murtaza, M.; Saeed, A. Dark Web Along With The Dark Web Marketing And Surveillance. In Proceedings of the 2019 20th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT), Gold Coast, Australia, 5–7 December 2019; pp. 483–485. [Google Scholar] [CrossRef]
- Harviainen, J.T.; Haasio, A.; Hämäläinen, L. Drug traders on a local dark web marketplace. In Proceedings of the 23rd International Conference on Academic Mindtrek, Tampere, Finland, 29–30 January 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 20–26. [Google Scholar] [CrossRef]
- Hayes, D.R.; Cappa, F.; Cardon, J. A Framework for More Effective Dark Web Marketplace Investigations. Information 2018, 9, 186. [Google Scholar] [CrossRef]
- Hiramoto, N.; Tsuchiya, Y. Measuring dark web marketplaces via Bitcoin transactions: From birth to independence. Forensic Sci. Int. Digit. Investig. 2020, 35, 301086. [Google Scholar] [CrossRef]
- Jacka, K. Beyond the Surface Web: How Criminals Are Utilising the Internet to Commit Crimes. In Digital Transformation in Policing: The Promise, Perils and Solutions; Montasari, R., Carpenter, V., Masys, A.J., Eds.; Advanced Sciences and Technologies for Security Applications; Springer International Publishing: Cham, Switzerland, 2023; pp. 109–118. [Google Scholar] [CrossRef]
- Kadoguchi, M.; Hayashi, S.; Hashimoto, M.; Otsuka, A. Exploring the Dark Web for Cyber Threat Intelligence using Machine Leaning. In Proceedings of the 2019 IEEE International Conference on Intelligence and Security Informatics (ISI), Shenzhen, China, 1–3 July 2019; pp. 200–202. [Google Scholar] [CrossRef]
- Kermitsis, E.; Kavallieros, D.; Myttas, D.; Lissaris, E.; Giataganas, G. Dark Web Markets. In Dark Web Investigation; Akhgar, B., Gercke, M., Vrochidis, S., Gibson, H., Eds.; Security Informatics and Law Enforcement; Springer International Publishing: Cham, Switzerland, 2021; pp. 85–118. [Google Scholar] [CrossRef]
- Kloess, J.A.; van der Bruggen, M. Trust and Relationship Development Among Users in Dark Web Child Sexual Exploitation and Abuse Networks: A Literature Review From a Psychological and Criminological Perspective. Trauma Violence Abus. 2023, 24, 1220–1237. [Google Scholar] [CrossRef] [PubMed]
- Koloveas, P.; Chantzios, T.; Tryfonopoulos, C.; Skiadopoulos, S. A Crawler Architecture for Harvesting the Clear, Social, and Dark Web for IoT-Related Cyber-Threat Intelligence. In Proceedings of the 2019 IEEE World Congress on Services (SERVICES), Milan, Italy, 8–13 July 2019; Volume 2642-939X, pp. 3–8. [Google Scholar] [CrossRef]
- Kruisbergen, E.W.; Leukfeldt, E.R.; Kleemans, E.R.; Roks, R.A. Money talks money laundering choices of organized crime offenders in a digital age. J. Crime Justice 2019, 42, 569–581. [Google Scholar] [CrossRef]
- Leonidou, P.; Salamanos, N.; Farao, A.; Aspri, M.; Sirivianos, M. A Qualitative Analysis of Illicit Arms Trafficking on Darknet Marketplaces. In Proceedings of the 18th International Conference on Availability, Reliability and Security, Benevento, Italy, 29 August–1 September 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 1–9. [Google Scholar] [CrossRef]
- Marin, E.; Shakarian, J.; Shakarian, P. Mining Key-Hackers on Darkweb Forums. In Proceedings of the 2018 1st International Conference on Data Intelligence and Security (ICDIS), South Padre Island, TX, USA, 8–10 April 2018; pp. 73–80. [Google Scholar] [CrossRef]
- Raman, R.; Kumar Nair, V.; Nedungadi, P.; Ray, I.; Achuthan, K. Darkweb research: Past, present, and future trends and mapping to sustainable development goals. Heliyon 2023, 9, e22269. [Google Scholar] [CrossRef]
- Rawat, R.; Mahor, V.; Chirgaiya, S.; Garg, B. Artificial Cyber Espionage Based Protection of Technological Enabled Automated Cities Infrastructure by Dark Web Cyber Offender. In Intelligence of Things: AI-IoT Based Critical-Applications and Innovations; Al-Turjman, F., Nayyar, A., Devi, A., Shukla, P.K., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 167–188. [Google Scholar] [CrossRef]
- Rawat, R.; Rajawat, A.S.; Mahor, V.; Shaw, R.N.; Ghosh, A. Dark Web—Onion Hidden Service Discovery and Crawling for Profiling Morphing, Unstructured Crime and Vulnerabilities Prediction. In Innovations in Electrical and Electronic Engineering; Mekhilef, S., Favorskaya, M., Pandey, R.K., Shaw, R.N., Eds.; In Lecture Notes in Electrical Engineering; Springer: Singapore, 2021; pp. 717–734. [Google Scholar] [CrossRef]
- Staley, B.; Montasari, R. A Survey of Challenges Posed by the Dark Web. In Artificial Intelligence in Cyber Security: Impact and Implications: Security Challenges, Technical and Ethical Issues, Forensic Investigative Challenges; Montasari, R., Jahankhani, H., Eds.; Advanced Sciences and Technologies for Security Applications; Springer International Publishing: Cham, Switzerland, 2021; pp. 203–213. [Google Scholar] [CrossRef]
- Tavabi, N.; Bartley, N.; Abeliuk, A.; Soni, S.; Ferrara, E.; Lerman, K. Characterizing Activity on the Deep and Dark Web. In Proceedings of the Companion Proceedings of The 2019 World Wide Web Conference, San Francisco, CA, USA, 13–17 May 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 206–213. [Google Scholar] [CrossRef]
- Tounsi, W.; Rais, H. A survey on technical threat intelligence in the age of sophisticated cyber attacks. Comput. Secur. 2018, 72, 212–233. [Google Scholar] [CrossRef]
- Tsuchiya, Y.; Hiramoto, N. Dark web in the dark: Investigating when transactions take place on cryptomarkets. Forensic Sci. Int. Digit. Investig. 2021, 36, 301093. [Google Scholar] [CrossRef]
- van der Bruggen, M.; Blokland, A. A Crime Script Analysis of Child Sexual Exploitation Material Fora on the Darkweb. Sex. Abus. 2021, 33, 950–974. [Google Scholar] [CrossRef]
- Vyas, P.; Vyas, G.; Chauhan, A.; Rawat, R.; Telang, S.; Gottumukkala, M. Anonymous Trading on the Dark Online Marketplace: An Exploratory Study. In Using Computational Intelligence for the Dark Web and Illicit Behavior Detection; IGI Global: Hershey, PA, USA, 2022; pp. 272–289. [Google Scholar] [CrossRef]
- Warner, C. Law Enforcement and Digital Policing of the Dark Web: An Assessment of the Technical, Ethical and Legal Issues. In Applications for Artificial Intelligence and Digital Forensics in National Security; Montasari, R., Ed.; Advanced Sciences and Technologies for Security Applications; Springer Nature Switzerland: Cham, Switzerland, 2023; pp. 105–115. [Google Scholar] [CrossRef]
- Weimann, G. Terrorist Migration to the Dark Web. Perspect. Terror. 2016, 10, 40–44. Available online: https://www.jstor.org/stable/26297596 (accessed on 5 March 2024).
- Yannikos, Y.; Schäfer, A.; Steinebach, M. Monitoring Product Sales in Darknet Shops. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Zulkarnine, A.T.; Frank, R.; Monk, B.; Mitchell, J.; Davies, G. Surfacing collaborated networks in dark web to find illicit and criminal content. In Proceedings of the 2016 IEEE Conference on Intelligence and Security Informatics (ISI), Tucson, AZ, USA, 28–30 September 2016; pp. 109–114. [Google Scholar] [CrossRef]
- Drug Statistics—Worldometer. Available online: https://www.worldometers.info/drugs/ (accessed on 3 March 2024).
- United Nations: Office on Drugs and Crime. Drug trafficking. Available online: https://www.unodc.org/unodc/en/drug-trafficking/index.html (accessed on 3 March 2024).
- Broadhurst, R.; Ball, M.; Trivedi, H. Fentanyl availability on darknet markets. Trends Issues Crime Crim. Justice 2020, 590, 1–14. [Google Scholar] [CrossRef]
- Mirea, M.; Wang, V.; Jung, J. The not so dark side of the darknet: A qualitative study. Secur. J. 2019, 32, 102–118. [Google Scholar] [CrossRef]
- Office of Public Affairs, United States Department of Justice. AlphaBay, the Largest Online “Dark Market”, Shut Down. Available online: https://www.justice.gov/opa/pr/alphabay-largest-online-dark-market-shut-down (accessed on 3 March 2024).
- Broséus, J.; Rhumorbarbe, D.; Mireault, C.; Ouellette, V.; Crispino, F.; Décary-Hétu, D. Studying illicit drug trafficking on Darknet markets: Structure and organisation from a Canadian perspective. Forensic Sci. Int. 2016, 264, 7–14. [Google Scholar] [CrossRef] [PubMed]
- Manky, D. Cybercrime as a service: A very modern business. Comput. Fraud. Secur. 2013, 2013, 9–13. [Google Scholar] [CrossRef]
- Singh, J.; Rahman, N.A. Cybercrime-As-A-Service (Malware). In Proceedings of the 2023 International Conference on Evolutionary Algorithms and Soft Computing Techniques (EASCT), Bangalore, India, 20–21 October 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Hyslip, T.S. Cybercrime-as-a-Service Operations. In The Palgrave Handbook of International Cybercrime and Cyberdeviance; Holt, T.J., Bossler, A.M., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 815–846. [Google Scholar] [CrossRef]
- Hyslip, T.S.; Holt, T.J. Assessing the Capacity of DRDoS-For-Hire Services in Cybercrime Markets. Deviant Behav. 2019, 40, 1609–1625. [Google Scholar] [CrossRef]
- Santanna, J.J.; van Rijswijk-Deij, R.; Hofstede, R.; Sperotto, A.; Wierbosch, M.; Granville, L.Z.; Pras, A. Booters—An analysis of DDoS-as-a-service attacks. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 243–251. [Google Scholar] [CrossRef]
- Alwashali, A.A.M.A.; Rahman, N.A.A.; Ismail, N. A Survey of Ransomware as a Service (RaaS) and Methods to Mitigate the Attack. In Proceedings of the 2021 14th International Conference on Developments in eSystems Engineering (DeSE), Sharjah, United Arab Emirates, 7–10 December 2021; pp. 92–96. [Google Scholar] [CrossRef]
- Ben-Asher, N.; Gonzalez, C. Effects of cyber security knowledge on attack detection. Comput. Hum. Behav. 2015, 48, 51–61. [Google Scholar] [CrossRef]
- Huang, K.; Siegel, M.; Madnick, S. Systematically Understanding the Cyber Attack Business: A Survey. ACM Comput. Surv. 2018, 51, 1–36. [Google Scholar] [CrossRef]
- Cybercrime-as-a-Service: Tackling a Rapidly Professionalising Industry. Trend Micro. Available online: https://www.trendmicro.com/en_gb/research/22/k/cybercrime-as-a-service-tackling-a-rapidly-professionalising-industry.html (accessed on 4 March 2024).
- Shelley, L.I. Dark Commerce: How a New Illicit Economy Is Threatening Our Future; Princeton University Press: Princeton, NJ, USA, 2018. [Google Scholar]
- Hummer, D.; Byrne, J.M. Handbook on Crime and Technology; Edward Elgar Publishing: Cheltenham, UK, 2023. [Google Scholar]
- Identity Theft Resource Center®’s 2020 Annual Data Breach Report Reveals 19 Percent Decrease in Breaches. Available online: https://www.idtheftcenter.org/post/identity-theft-resource-centers-2020-annual-data-breach-report-reveals-19-percent-decrease-in-breaches/ (accessed on 4 March 2024).
- Sapienza, A.; Bessi, A.; Damodaran, S.; Shakarian, P.; Lerman, K.; Ferrara, E. Early Warnings of Cyber Threats in Online Discussions. In Proceedings of the 2017 IEEE International Conference on Data Mining Workshops (ICDMW), New Orleans, LA, USA, 18–21 November 2017; pp. 667–674. [Google Scholar] [CrossRef]
- Raven, A.; Akhgar, B.; Abdel Samad, Y. Case Studies: Child Sexual Exploitation. In Dark Web Investigation; Akhgar, B., Gercke, M., Vrochidis, S., Gibson, H., Eds.; Security Informatics and Law Enforcement; Springer International Publishing: Cham, Switzerland, 2021; pp. 249–266. [Google Scholar] [CrossRef]
- Anjum, A.; Kaur, D.C.; Kondapalli, S.; Hussain, M.A.; Begum, A.U.; Hassen, S.M.; Adam Boush, D.M.S.; Benjeed, A.O.S.; Osman Abdalraheem, D.M.H. A Mysterious and Darkside of The Darknet: A Qualitative Study. Rochester, NY, USA, 20 December 2021. Available online: https://papers.ssrn.com/abstract=4167244 (accessed on 4 March 2024).
- Giang, H.T.T.; Herger, D.E.C. Protecting Children’s Rights: A Comparative Analysis between Vietnam and the Legal Models of the European Union and Hungary. Available online: https://md.ajk.pte.hu/sites/default/files/publications/PROTECTING%20CHILDREN%27S%20RIGHTS%20.pdf (accessed on 21 May 2024).
- Ibrahim, D. Online Child Sexual Exploitation and Abuse: Criminal Justice Pathways of Police-Reported Incidents in Canada, 2014 to 2020/by Dyna Ibrahim. 2023. Available online: https://policycommons.net/artifacts/4250149/online-child-sexual-exploitation-and-abuse/5059039/ (accessed on 4 March 2024).
- Kalita, B.; Sahani, R. An Anthropological Investigation of Assam—The Human Trafficking Hub of India? Hum. Rights Rev. 2023, 24, 545–566. [Google Scholar] [CrossRef]
- Jadhav, T. A Correlational Study to analyze the knowledge and attitude towards early marriage among parents at selected rural areas, Kolhapur District. A V Pub Int. J. Nurs. Med. Res. 2023, 2, 121–129. [Google Scholar] [CrossRef]
- Rebe, N. Regulating Cyber Technologies: Privacy Vs Security; World Scientific: London, UK, 2023. [Google Scholar]
- van Wegberg, R.; Oerlemans, J.-J.; van Deventer, O. Bitcoin money laundering: Mixed results? An explorative study on money laundering of cybercrime proceeds using bitcoin. J. Financ. Crime 2018, 25, 419–435. [Google Scholar] [CrossRef]
- Wronka, C. “Cyber-laundering”: The change of money laundering in the digital age. J. Money Laund. Control. 2021, 25, 330–344. [Google Scholar] [CrossRef]
- Benton, D.; Ryder, N. Terrorism Financing, the United Kingdom, and the Financial Action Task Force: A Series of Omissions or Missed Opportunities? In Sustainable Finance and Financial Crime; Dion, M., Ed.; Sustainable Finance; Springer International Publishing: Cham, Switzerland, 2023; pp. 353–374. [Google Scholar] [CrossRef]
- Bederna, Z.; Szadeczky, T. Cyber espionage through Botnets. Secur. J. 2020, 33, 43–62. [Google Scholar] [CrossRef]
- Adkins, G. Red Teaming the Red Team: Utilizing Cyber Espionage to Combat Terrorism. J. Strateg. Secur. 2013, 6, 1–9. Available online: https://www.jstor.org/stable/26485051 (accessed on 5 March 2024). [CrossRef]
- Denker, K.; Schäfer, M.; Steinebach, M. Darknets as Tools for Cyber Warfare. In Information Technology for Peace and Security: IT Applications and Infrastructures in Conflicts, Crises, War, and Peace; Reuter, C., Ed.; Springer Fachmedien: Wiesbaden, Germany, 2019; pp. 107–135. [Google Scholar] [CrossRef]
- Lemieux, F.; Lemieux, F. National Security Intelligence in the Five Eyes Countries. In Intelligence and State Surveillance in Modern Societies; Emerald Publishing Limited: Leeds, UK, 2018; pp. 33–67. [Google Scholar] [CrossRef]
- Ghafur, S.; Kristensen, S.; Honeyford, K.; Martin, G.; Darzi, A.; Aylin, P. A retrospective impact analysis of the WannaCry cyberattack on the NHS. Npj Digit. Med. 2019, 2, 98. [Google Scholar] [CrossRef] [PubMed]
- Office of Public Affairs, United States Department of Justice. Grand Jury Indicts 12 Russian Intelligence Officers for Hacking Offenses Related to the 2016 Election. Available online: https://www.justice.gov/opa/pr/grand-jury-indicts-12-russian-intelligence-officers-hacking-offenses-related-2016-election (accessed on 5 March 2024).
- Horan, C.; Saiedian, H. Cyber Crime Investigation: Landscape, Challenges, and Future Research Directions. J. Cybersecur. Priv. 2021, 1, 580–596. [Google Scholar] [CrossRef]
- Krombholz, K.; Hobel, H.; Huber, M.; Weippl, E. Advanced social engineering attacks. J. Inf. Secur. Appl. 2015, 22, 113–122. [Google Scholar] [CrossRef]
- Alharbi, A.; Faizan, M.; Alosaimi, W.; Alyami, H.; Agrawal, A.; Kumar, R.; Khan, R.A. Exploring the Topological Properties of the Tor Dark Web. IEEE Access 2021, 9, 21746–21758. [Google Scholar] [CrossRef]
- Abbasi, A.; Chen, H. Affect Intensity Analysis of Dark Web Forums. In Proceedings of the 2007 IEEE Intelligence and Security Informatics, New Brunswick, NJ, USA, 23–24 May 2007; pp. 282–288. [Google Scholar] [CrossRef]
- Tovanich, N.; Cazabet, R. Pattern Analysis of Money Flows in the Bitcoin Blockchain. In Complex Networks and Their Applications XI; Cherifi, H., Mantegna, R.N., Rocha, L.M., Cherifi, C., Miccichè, S., Eds.; Studies in Computational Intelligence; Springer International Publishing: Cham, Switzerland, 2023; pp. 443–455. [Google Scholar] [CrossRef]
- Faisal, T.; Courtois, N.; Serguieva, A. The Evolution of Embedding Metadata in Blockchain Transactions. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Alkhalil, Z.; Hewage, C.; Nawaf, L.; Khan, I. Phishing Attacks: A Recent Comprehensive Study and a New Anatomy. Front. Comput. Sci. 2021, 3, 563060. Available online: https://www.frontiersin.org/articles/10.3389/fcomp.2021.563060 (accessed on 5 March 2024). [CrossRef]
- Unver, A. Digital Open Source Intelligence and International Security: A Primer. Rochester, NY, USA, 15 July 2018. Available online: https://papers.ssrn.com/abstract=3331638 (accessed on 5 March 2024).




| Criterion | Inclusion Criterions |
|---|---|
| 1 | A study concentrates on crimes related to the Dark Web, highlighting their nature, consequences, and evaluating techniques to combat them. |
| 2 | A study is centered around tracing technologies and techniques used to locate cyber criminals operating on the Dark Web, with a focus on enhancing cyber security. |
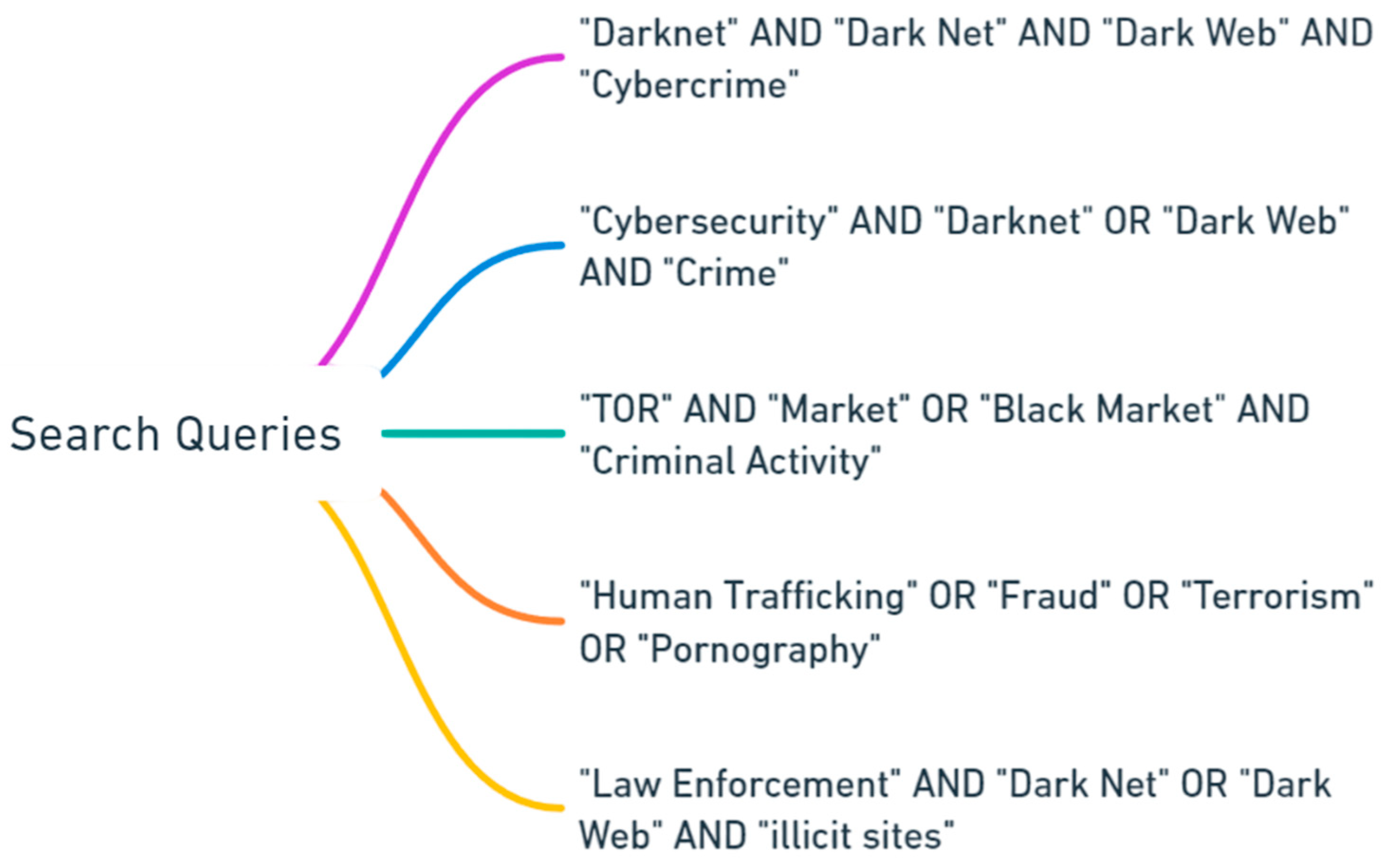
| 3 | The search terms listed in Figure 1 use the search syntax operations of AND & OR. When using AND, both keywords must be present in the search results, whereas with OR, at least one of the keywords must be present in the search results. |
| 4 | Studies must be in English language. |
| 5 | Included studies from journals, conferences, and case studies must be from 2011 to 2023. |
| Criterion | Exclusion Criterions |
|---|---|
| 1 | Exclude articles that mention Dark Net without discussing the detection or tracing of criminals or crimes. |
| 2 | Exclude articles that do not discuss the Dark Net but are only related to cybersecurity. |
| 3 | Remove articles that have been found in more than one digital library or authored by the same author to avoid duplication of data. |
| SLR | Item | Description |
|---|---|---|
| 1 | Type | Publication Type (e.g., journal, conference). |
| 2 | Authors | Authors of the Article. |
| 3 | Year | Year of the Publication. |
| 4 | Title | Title of the Publication. |
| 5 | Source | Source of Publication (e.g., ACM Digital Library). |
| 6 | RQ1 | Emerging crime threats on the Dark Net. |
| 7 | RQ2 | Methods used to find the perpetrators of crimes on the Dark Net. |
| Authors | Paper | Contribution |
|---|---|---|
| [10] | Foundations and trends on Dark Net-related criminals in the last 10 years: a systematic literature review and bibliometric analysis | This paper makes a pioneering contribution by combining a systematic literature review with bibliometric analysis to map out the evolution of Dark Net-related crime research over the past decade, highlighting significant contributions from the Global South and identifying key areas for future study. |
| [3] | Classifying Illegal Activities on Tor Network Based on Web Textual Contents | This paper introduces “Dark Net Usage Text Addresses” (DUTA), a novel dataset of Dark Net domains that enables a systematic approach to categorize Tor hidden services. Through rigorous sampling and classification of Tor network addresses, our analysis reveals the efficacy of combining TFIDF word representation with logistic regression, achieving high cross-validation accuracy and macro F1 scores, providing a solid foundation for tools that could assist in identifying illicit activities on the Deep Web. |
| [16] | The shift of Dark Net illegal drug trade preferences in cryptocurrency: The question of traceability and deterrence | This study utilizes temporal topic modeling and sentiment analysis on ClearNet forum data to uncover the enduring preference for Bitcoin among Dark Net market users until Monero’s privacy enhancements in 2017 shifted the cryptocurrency landscape. |
| [17] | Threats from the Dark: A Review of Dark Web Investigation Research for Cyber Threat Intelligence | This review delineates the pivotal role of Dark Web content analysis in Cyber Threat Intelligence, providing an extensive survey of contemporary methodologies, tools, and challenges, and charting a course for future research in the domain. |
| [18] | Exploring Dark Web Crawlers: A Systematic Literature Review of Dark Web Crawlers and Their Implementation | This paper provides a comprehensive systematic literature review on Dark Web crawlers, detailing their common programming practices and tools, and introduces an innovative Tor-based crawling model, validated through experiments, to enhance the efficacy of digital investigations within anonymous communication networks. |
| [19] | Under and over the surface: A comparison of the use of leaked account credentials in the Dark and Surface Web | This study contrasts the criminal patterns of stolen account credentials’ usage in the Surface Web with those on the Dark Web by deploying Gmail honey accounts, revealing distinct malicious behaviors in each realm and offering valuable insights into the dynamics of cybercrime across diverse web environments. |
| [20] | Recognition of service domains on TOR Dark Net using perceptual hashing and image classification techniques | This paper introduces DUSI, a unique image-based dataset of TOR services and presents a framework utilizing Perceptual Hashing and Bag of Visual Words to accurately identify various services on the TOR network through visual content, with Perceptual Hashing emerging as a highly effective approach for service detection. |
| [15] | Exploring and Mining the Dark Side of the Web | This talk explores the latest in Terrorism Informatics, highlighting the Dark Web project’s advancements in web mining and analysis for tracking online terrorist activity, supported by a vast database of extremist content. |
| [21] | Analysis of Hacking-Related Trade on the Dark Web | This study presents an exploratory analysis of the hacking trade in Dark Web marketplaces, revealing a profit-driven market that generated over USD 26 million, with the majority of products priced under USD 150, indicating the ease of access to cybercrime tools and the presence of a highly organized infrastructure. |
| [22] | A public policy perspective of the Dark Web | This paper provides an insightful overview of the Dark Web’s history and current governmental interventions, offering policy recommendations to balance regulation with user values, critical for informed debate and effective global Dark Web policy development. |
| [23] | Criminal motivation on the dark web: A categorisation model for law enforcement | Introducing the Tor-use Motivation Model (TMM), this study presents a nuanced two-dimensional classification approach tailored for law enforcement, effectively bridging the gap between broad taxonomies and detailed criminal behavior analysis on the Dark Web. |
| [24] | SpyDark: Surface and Dark Web Crawler | SpyDark, an innovative tool, enables users to collect and analyze information from both the surface and Dark Web, leveraging crawler and NLP models to classify web pages by relevance based on user-defined queries. |
| [5] | The Dark Web and anonymizing technologies: Legal pitfalls, ethical prospects, and policy directions from radical criminology | This article examines the Dark Web’s dual-edged nature, aiming to illuminate its complexities for policymakers and propose informed legal and ethical strategies to navigate its challenges and harness its potential responsibly. |
| [25] | Collective dynamics of Dark Web marketplaces | This study delves into the dynamics of Dark Web marketplaces, revealing how user migration to coexisting platforms following marketplace closures ensures the systemic resilience of the illicit trade ecosystem despite individual marketplace fragility. |
| [26] | Electronic Money Laundering: The Dark Side of Fintech: An Overview of the Most Recent Cases | This paper presents a systematic review of money laundering in the FinTech sector, examining common patterns, the European legal framework, and recent fraud cases to assess if economic behaviors align with legality and if FinTech tools can detect illicit activities. |
| [27] | Using social network analysis to prevent money laundering | This study leverages network analytic techniques on a factoring company’s data, revealing that social network metrics can predict client risk profiles, with riskier entities engaging in larger, more frequent, and cross-sector transactions, often from peripheral network positions. |
| [28] | Power/freedom on the Dark Web: A digital ethnography of the Dark Web Social Network | This ethnographic essay investigates the Dark Web Social Network, highlighting its complex interplay of anonymity and sociality, its stance against illegal content, and the unique blend of techno-elitism, revealing a nuanced exploration of power and freedom within the digital underground. |
| [29] | A qualitative mapping of Dark Web marketplaces | This paper offers a comprehensive mapping of Dark Web marketplaces, examining their operational mechanisms and features through qualitative analysis, aiming to uncover vulnerabilities in the cyber security landscape and strategize their disruption. |
| [30] | Searching Places Unknown: Law Enforcement Jurisdiction on the Dark Web | The employment of hacking tools by law enforcement to track Dark Web users challenges the boundaries between criminal procedure and international law, as traditional surveillance methods become ineffective against anonymized online activities. |
| [31] | Automated Categorization of Onion Sites for Analyzing the Dark Web Ecosystem | This paper introduces ATOL, an advanced analysis tool within the LIGHTS infrastructure, designed for thematic assessment of Dark Web content, enhancing the capability to identify and monitor illicit sites through novel keyword discovery, classification, and clustering techniques, demonstrating significant performance gains in content categorization. |
| [32] | Dark Web, Along With The Dark Web Marketing And Surveillance | This paper delves into the utilization of the Dark Web for criminal and terrorist activities, exploring how law enforcement agencies globally navigate and surveil the Dark Web to counteract these threats, while also discussing secure access methods and safety precautions for users. |
| [33] | Drug traders on a local Dark Web marketplace | This article employs habitus and way of life concepts to analyze the cultural and socioeconomic dimensions of Finnish Dark Web drug users’ lives, using qualitative and quantitative analysis of forum posts from Sipulitori to reveal diverse drug-related lifestyles and inform future research on Dark Web forums. |
| [34] | A Framework for More Effective Dark Web Marketplace Investigations | This research presents an innovative analytical framework for Dark Web scraping using AppleScript, proving effective in a case study to unveil vendor identities and listings on a marketplace, offering significant insights for academics and investigators into the clandestine operations of Dark Web marketplaces. |
| [35] | Measuring Dark Web marketplaces via Bitcoin transactions: From birth to independence | This study tracks the evolution and transaction volumes of seven major Dark Web marketplaces, revealing their transition to more advanced anonymity tools by 2016 and the continuous user migration that sustains the Dark Web’s illicit economy. |
| [36] | Beyond the Surface Web: How Criminals Are Utilizing the Internet to Commit Crimes | This research explores the dual-edged nature of online anonymity and cryptocurrencies, delving into their use in criminal activities and the ethical challenges faced by the criminal justice system, while questioning if digital forensics can meet the evolving demands of cyber investigations. |
| [37] | Exploring the Dark Web for Cyber Threat Intelligence using Machine Leaning | This paper proposes a novel approach using machine learning and natural language processing to extract and analyze valuable intelligence from Dark Web forums, aiming to enhance the prediction and prevention of increasingly sophisticated cyber-attacks. |
| [2] | Dark Web: A Web of Crimes | This paper provides a comprehensive overview of the Dark Web, detailing its features, advantages, disadvantages, and the browsers used to access it, while also highlighting the criminal activities it harbors, aiming to raise awareness and promote preventive measures against such illicit actions. |
| [6] | Understanding the Dark Web | This chapter delineates the distinctions and interrelations between the Surface Web, Deep Web, and Dark Web, explores the architecture and technologies of major Dark Nets like Tor, I2P, and Freenet, and addresses the complexities law enforcement agencies encounter in combating crime and terrorism within these anonymous realms. |
| [38] | Dark Web Markets | This chapter explores the distinctions and connections between the Surface Web, Deep Web, and Dark Web, delves into the infrastructure of key Dark Nets like Tor, I2P, and Freenet, and examines the impact of law enforcement on the Dark Web, highlighting the challenges of using anonymity technologies in the battle against online crime and terrorism. |
| [39] | Trust and Relationship Development Among Users in Dark Web Child Sexual Exploitation and Abuse Networks: A Literature Review From a Psychological and Criminological Perspective | This literature review delves into the dynamics of trust and relationship building within online networks on the Dark Web, focusing on the sexual exploitation and abuse of children, highlighting the complex interplay of social and technical factors that underpin these illicit communities. |
| [40] | A Crawler Architecture for Harvesting the Clear, Social, and Dark Web for IoT-Related Cyber-Threat Intelligence | This study introduces a cutting-edge crawling architecture that efficiently harvests cyber-threat intelligence from diverse web layers, employing machine learning and statistical language models to prioritize relevant security information, showcasing its potential through an open-source toolkit and crowdsourced evaluation. |
| [41] | Money talks money laundering choices of organized crime offenders in a digital age | This study delves into the financial strategies of organized crime, highlighting a universal preference for cash across both traditional and cybercrime, while noting a distinct utilization of financial innovations like cryptocurrencies primarily within IT-related criminal activities. |
| [42] | A Qualitative Analysis of Illicit Arms Trafficking on Dark Net Marketplaces | This qualitative study explores the landscape of illegal arms trafficking on the Dark Web, utilizing a custom crawler to analyze data from ten marketplaces, revealing a well-organized trade in military-grade weapons and corroborating previous institutional reports on the ease of access and variety of firearms available. |
| [43] | Mining Key-Hackers on Dark Web Forums | This study introduces a novel approach for identifying key hackers in Dark Web forums using a blend of content, social networks, and seniority analyses, complemented by a reputation-based validation method, demonstrating that a hybridized model enhances key-hacker detection and can be generalized across different forums. |
| [7] | Anonymity Services Tor, I2P, JonDonym: Classifying in the Dark | This paper demonstrates the effectiveness of machine-learning classifiers in distinguishing between different anonymity networks (Tor, I2P, JonDonym) and identifying the specific applications generating encrypted traffic, achieving remarkable accuracies using only statistical features from a 2017 public dataset. |
| [44] | Dark Web research: Past, present, and future trends and mapping to sustainable development goals | This bibliometric analysis of Dark Web research over the past decade identifies four key areas of focus—network security, cybercrime and cryptography, machine learning and AI, drug trafficking and cryptomarkets—while highlighting the challenge it poses to achieving the UN’s SDGs, particularly SDG 16, and underscores the need for interdisciplinary approaches to develop effective countermeasures. |
| [45] | Artificial Cyber Espionage-Based Protection of Technological Enabled Automated Cities Infrastructure by Dark Web Cyber Offender | This work examines the evolving landscape of cybersecurity in the era of IoT, highlighting the dual use of technology by both security experts and infiltrators, and explores advanced strategies for protecting against cyber threats, emphasizing the critical role of identifying and countering digital criminals, particularly through the Dark Web. |
| [46] | Dark Web—Onion Hidden Service Discovery and Crawling for Profiling Morphing, Unstructured Crime, and Vulnerabilities Prediction | This research delves into the underbelly of the Dark Web, highlighting its role as a hub for various illegal activities, and outlines methodologies for crawling and analyzing its content to understand the patterns and behaviors of cybercriminals and terrorists, thereby shedding light on the challenges faced by law enforcement in combating these hidden crimes. |
| [11] | A general and modular framework for Dark Web analysis | This study introduces a versatile and scalable framework for Dark Web analysis, employing a microservice architecture with Docker Swarm, Kafka, ELK Stack, and PostgreSQL, successfully scraping over 84,000 unique onion domains, showcasing its efficacy in integrating diverse analytical workflows. |
| [47] | A Survey of Challenges Posed by the Dark Web | This study proposes a flexible and scalable framework for Dark Web analysis, demonstrating its efficacy in scraping over 84,000 unique onion domains. |
| [9] | An Anonymity Vulnerability in Tor | This paper introduces novel Trapper Attacks that exploit vulnerabilities in Tor to deanonymize user activities, demonstrating their effectiveness in real-world Tor networks with a success rate exceeding 99% and minimal false positives. |
| [48] | Characterizing Activity on the Deep and Dark Web | This paper investigates the Deep and Dark Web (d2web), where illicit activities thrive, using a large dataset of forum messages spanning over a year. By employing topic modeling techniques like LDA and a non-parametric HMM, it uncovers hidden patterns and similarities across forums, facilitating the identification of anomalous events. |
| [49] | A survey on technical threat intelligence in the age of sophisticated cyber attacks | This paper elucidates the nuances of threat intelligence, particularly focusing on Technical Threat Intelligence (TTI), while addressing challenges in sharing and standardizing threat information to enhance security efficacy. |
| [50] | Dark web in the dark: Investigating when transactions take place on cryptomarkets | This study investigates the temporal patterns of illegal transactions on leading cryptomarkets, revealing heightened activity during night-time hours and on weekdays, particularly Mondays through Wednesdays. Additionally, it suggests that law enforcement operations like Operation Onymous may not significantly disrupt cryptomarket activity or alter transaction patterns in the short term. |
| [51] | A Crime Script Analysis of Child Sexual Exploitation Material Fora on the Dark Web | This study employs a crime script analysis to unravel the sequential steps involved in Child Sexual Exploitation Material (CSEM) crimes within Dark Web communities, shedding light on the intricate process, from accessing illicit fora to post-activity behaviors. The findings underscore the challenges posed by Dark Web platforms in facilitating and shaping the commission of such crimes, providing insights for targeted law enforcement interventions. |
| [52] | Anonymous Trading on the Dark Online Marketplace: An Exploratory Study | This chapter delves into the realm of anonymous trading on the Dark Web, leveraging the Silkroad 2.0 dataset to dissect the nuances of illicit e-commerce. Through thematic analysis of drug-related discourse on Twitter, it unveils the global scope of illegal trading activities and underscores the susceptibility of adolescent populations to social media drug trafficking. |
| [53] | Law Enforcement and Digital Policing of the Dark Web: An Assessment of the Technical, Ethical, and Legal Issues | This chapter delves into the intricate challenges faced by law enforcement agencies in policing the Dark Web, highlighting the critical need for enhanced cyber threat intelligence, ethical considerations, and cross-border collaboration. It underscores the imperative of maintaining a delicate balance between law enforcement efforts and individual civil liberties, emphasizing the importance of deploying unpredictable policing techniques to effectively combat digital crime. |
| [54] | Terrorist Migration to the Dark Web | This paper explores recent trends in terrorist utilization of the Dark Web, highlighting its role in facilitating their operations while evading detection and law enforcement efforts. |
| [55] | Monitoring Product Sales in Dark Net Shops | This paper proposes a monitoring approach for tracking product sales on the Dark Net, leveraging anonymity networks like Tor and cryptocurrencies such as Bitcoin. By collecting Bitcoin addresses and product data from hidden services on Tor, the study aims to analyze blockchain transactions corresponding to specific sales in these Dark Net shops, offering insights into criminal activities while presenting opportunities for law enforcement and researchers alike. |
| [56] | Surfacing collaborated networks on the Dark Web to find illicit and criminal content | This paper addresses the proliferation of illegal activities on the Tor network, highlighting challenges in automated monitoring and the development of a modified web crawler termed the “Dark Crawler” to navigate the Dark Web. Initial findings reveal the presence of extremist and terrorist content and its interconnectedness, shedding light on the facilitation of Dark Web crimes by popular websites owithin the Dark Web ecosystem. |
| Our study | Weaponization of the Growing Cybercrimes Inside the Dark Net: The Question of Detection and Application | This study fills significant gaps in the existing literature by providing a comprehensive review of the weaponization of cybercrimes on the Dark Web. Unlike previous studies that primarily focused on categorizing illegal activities or analyzing specific detection methodologies, our research holistically examines the lifecycle of these cybercrimes from their weaponization to their detection and impact assessment. By synthesizing insights from 88 relevant articles and incorporating the latest data from 2024 and backwards, we address the lack of comprehensive evaluations found in works like “Foundations and Trends on the Dark Net-Related Criminals in the Last 10 Years” and “Threats from the Dark: A Review over Dark Web Investigation Research for Cyber Threat Intelligence.” Our study provides actionable recommendations for policymakers, cybersecurity professionals, and law enforcement agencies to enhance efforts in combating weaponized cybercrimes on the Dark Web, thus proposing future measures for improved crime monitoring and locating technologies. |
| Journal | Country |
|---|---|
| Journal of Strategic Security | United States |
| Frontiers in Computer Science | Switzerland |
| Forensic Science International: Digital Investigation | United Kingdom |
| Journal of Computer Networks and Communications | Egypt |
| Security Journal | United States |
| Computers in Human Behavior | United Kingdom |
| Crime Science | United Kingdom |
| Journal of Cyber Policy | United Kingdom |
| Crime, Law, and Social Change | Netherlands |
| Scientific Reports | United Kingdom |
| Expert Systems with Applications | United Kingdom |
| Journal of Cybersecurity and Privacy | Switzerland |
| Deviant Behavior | United Kingdom |
| Trauma, Violence, & Abuse | United Kingdom |
| Journal of Information Security and Applications | United Kingdom |
| Computer Fraud and Security | United Kingdom |
| Heliyon | Netherlands |
| Journal of Economic Criminology | United Kingdom |
| Computers and Security | United Kingdom |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Adel, A.; Norouzifard, M. Weaponization of the Growing Cybercrimes inside the Dark Net: The Question of Detection and Application. Big Data Cogn. Comput. 2024, 8, 91. https://doi.org/10.3390/bdcc8080091
Adel A, Norouzifard M. Weaponization of the Growing Cybercrimes inside the Dark Net: The Question of Detection and Application. Big Data and Cognitive Computing. 2024; 8(8):91. https://doi.org/10.3390/bdcc8080091
Chicago/Turabian StyleAdel, Amr, and Mohammad Norouzifard. 2024. "Weaponization of the Growing Cybercrimes inside the Dark Net: The Question of Detection and Application" Big Data and Cognitive Computing 8, no. 8: 91. https://doi.org/10.3390/bdcc8080091
APA StyleAdel, A., & Norouzifard, M. (2024). Weaponization of the Growing Cybercrimes inside the Dark Net: The Question of Detection and Application. Big Data and Cognitive Computing, 8(8), 91. https://doi.org/10.3390/bdcc8080091





