Anomaly Detection of IoT Cyberattacks in Smart Cities Using Federated Learning and Split Learning
Abstract
1. Introduction
- Application of federated learning to smart cities enables decentralized anomaly detection while safeguarding data privacy.
- Extension of privacy preservation capabilities with split learning enhances both privacy and efficiency.
- Comprehensive evaluation using real-world smart city datasets provides valuable insights into effectiveness.
- Performance comparison with existing algorithms offers a thorough analysis of efficiency.
- Utilizing a suite of performance metrics, including precision, recall, F-1 score, accuracy, and training/deployment time, facilitates a holistic assessment of the approach.
2. Materials and Methods
2.1. Related Works
2.2. Methodology
2.2.1. Smart City Infrastructure for Anomaly Detection
- IoT devices at the edge layer of a smart city IoT network incorporate various devices, including sensors, cameras, and connected vehicles. These devices generate vast data, capturing traffic, air quality, energy usage, and more information. While enhancing city operations, they are also susceptible to cyber threats.
- Fog Layer (the cybersecurity hub) bridges IoT devices and cloud services. It consists of a distributed computing resource network, including servers and gateways. Positioned strategically within the city, its primary role is data processing and analysis and ensuring security. Within the fog layer, machine learning plays a pivotal role in securing the smart city’s IoT infrastructure. Data generated by IoT devices are continuously collected, cleaned, normalized, and structured for analysis. Once data are prepared, relevant features are captured for meaningful information and pattern analysis. Machine learning algorithms are then fed these data to train the models and to understand device behaviors and network patterns. Potential threats or anomalies, such as distributed denial of service (DDoS) attacks or unusual data traffic, are caused by deviations in network traffic and device behavior. These anomalies are detected in real time, and as these are detected, the system can raise alerts and take necessary actions to mitigate the threat. As many models are adaptive, they can adapt to new data patterns.
- Reducing latency and bandwidth usage. Machine learning in the fog layer minimizes latency and conserves bandwidth. By processing and filtering data locally, only important information is sent to the cloud, which enhances security and optimizes resource utilization in the smart city infrastructure. Hence, the fog layer, powered by machine learning for real-time anomaly detection, is an integral component of a smart city’s cybersecurity hub. The fog layer protects the interconnected systems configuring smart cities by continuously monitoring and mitigating anomalies.

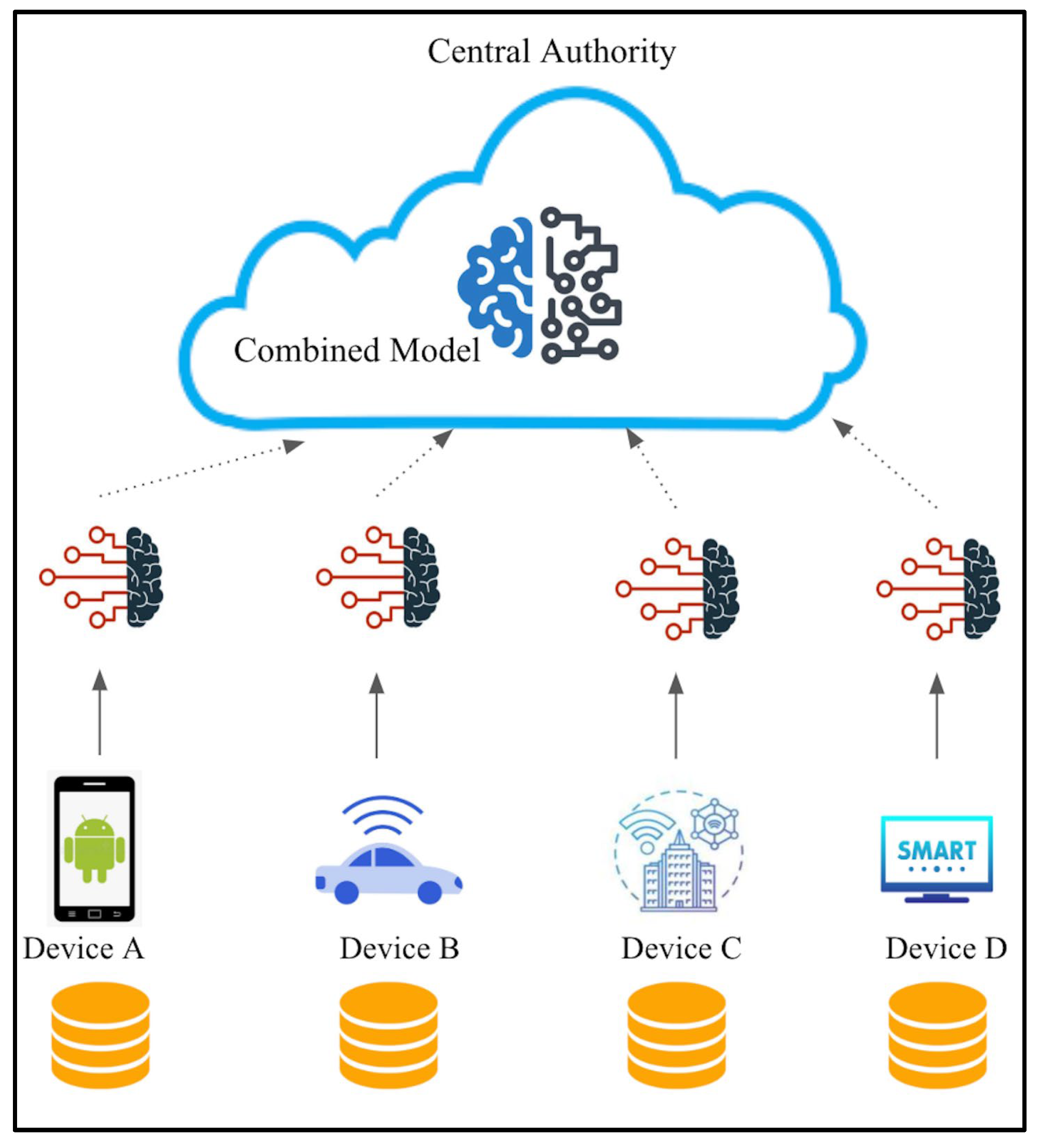
2.2.2. Federated Learning
- In smart cities, data privacy is paramount. Federated learning ensures that data remain on the edge devices, eliminating the need to transfer raw data over the network and minimizing privacy risks.
- Federated learning allows real-time model updates at the edge, minimizing latency. This is essential for timely cyberattack detection and response, especially in traffic management or public safety scenarios.
- By conducting frequent model updates, federated learning significantly reduces network bandwidth usage. This is crucial in smart cities where data transmission can strain network resources.
- The local models on edge devices learn from local data and collaborate to improve a global model. This collective learning enhances the model’s accuracy and adaptability.
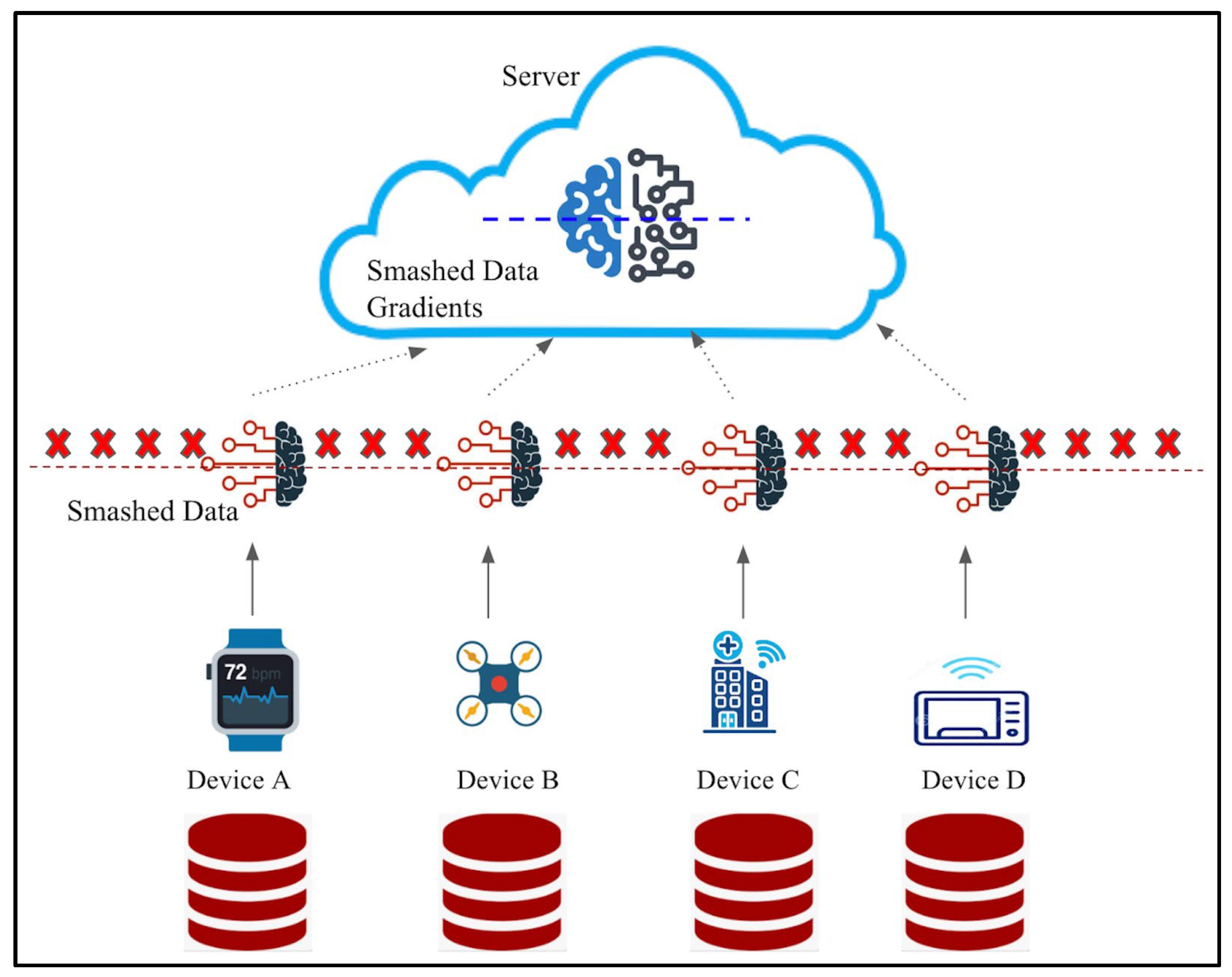
2.2.3. Split Learning
3. Results and Observations
3.1. Datasets
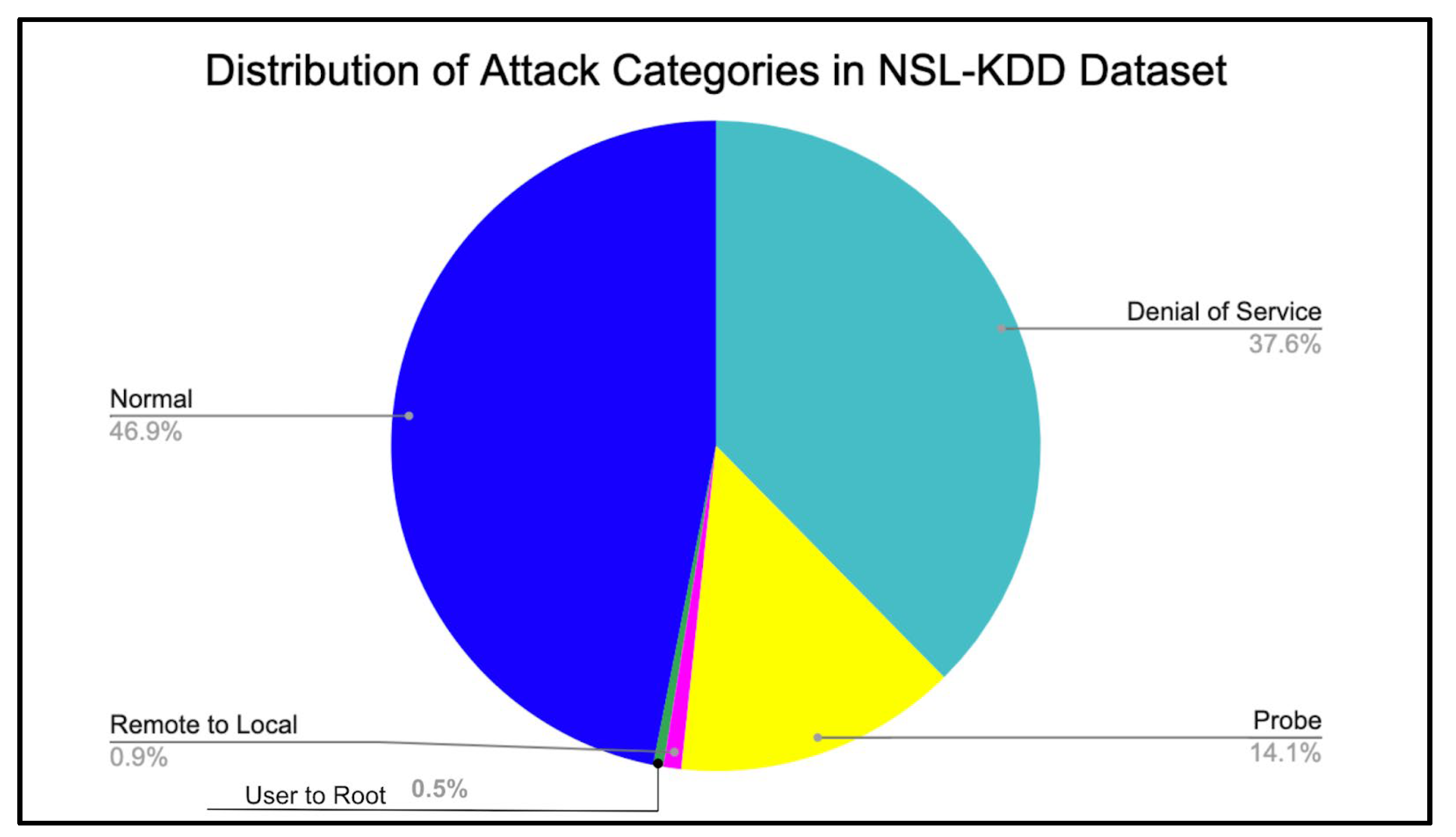
- Network-Based Intrusion Detection Dataset (NSL-KDD) [25] contains a diverse set of network traffic data, including normal network activities and various types of network intrusions or attacks. It has 125,973 data points for the training dataset and 22,544 for the test dataset. The network intrusions are categorized as normal (non-intrusion) traffic), denial of service (DoS) attacks, probe attacks, user-to-root (U2R) attacks (e.g., unauthorized access attempts), and remote-to-local (R2L) attacks (e.g., unauthorized remote access). The primary attributes or features of the dataset are connection record, protocol type, service, flag, etc. There are 41 features in total.
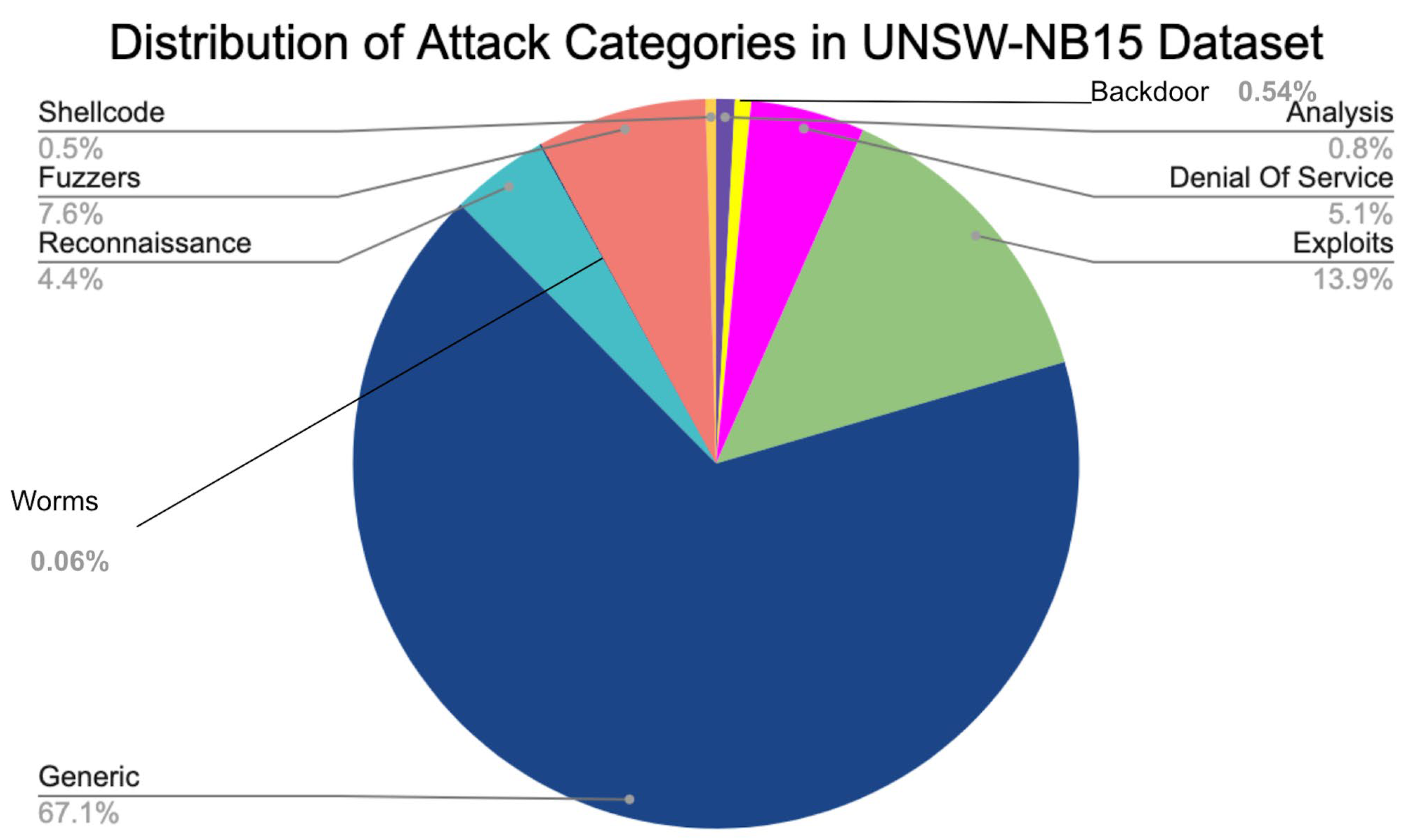
- UNSW-NB15—University of New South Wales—Network Behavior 2015 dataset [26] incorporates 175,341 data points in the training set and 82,332 in the test set. The dataset includes diverse network traffic data comprising benign and malicious network activities and various network intrusions or cyberattacks. The dataset incorporates nine different types of attacks, some of which are exploits, shellcode, worms, generic, etc. Forty-nine features describe the dataset, including attributes like protocol type, service, source and destination IP addresses, and source and destination ports.
3.2. Performance Metrics for Evaluation
- Accuracy: Accuracy measures the overall correctness of predictions
- Accuracy = Number of Correct Prediction/Total Number of Predictions;
- Precision: Precision focuses on the quality of positive predictions
- Precision = True Positives/(True Positives + False Positives);
- Recall: Recall measures the ability to identify all actual positive instances.
- Recall = True Positives/(True Positives + False Negatives);
- F1 Score: The F1 score is the harmonic mean of precision and recall, providing a balanced assessment;
- F1 Score = 2 ∗ Precision ∗ Recall/(Precision + Recall)
- Time-to-Run: Time-to-run represents the computational efficiency of the intrusion detection system. It measures the time taken to process the dataset, perform feature extraction, and make predictions. Minimizing running time is crucial for real-time or near-real-time intrusion detection systems in smart cities, where timely responses to threats are essential.
3.3. Results
3.4. Comparative Analysis
- Performance of Anomaly Detection Methods—The study comprehensively evaluated various anomaly detection methods, including classical machine learning algorithms (e.g., naive Bayes, logistic regression, and decision trees), ensemble models (e.g., random forests and XGBoost), and deep learning models (e.g., ANN and CNN). It observed that the performance varied significantly across these methods.
- Deploying Federated Learning—Federated learning demonstrated promising results concerning IoT anomaly detection. It exhibited strong potential for maintaining data privacy while achieving satisfactory accuracy despite longer training times.
- Deploying Split Learning—Split learning showcased the ability to safeguard sensitive information within IoT environments while delivering significantly high accuracy.
- Training Time—It is observed that the raining times associated with privacy-preserving techniques like federated learning and split learning are relatively high compared to the other models. This may be attributed to several factors ranging from model complexity to the number of devices.
- Multiple Datasets—Two different datasets were considered: NSL-KDD and UNSW-NB15, and the models exhibited consistent performance across both datasets.
- Evaluation Parameters—The analysis adopted accuracy, precision, recall, and F1 scores to evaluate the model performance. The models were also compared based on training times.
4. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
References
- Rashid, M.M.; Kamruzzaman, J.; Hassan, M.M.; Imam, T.; Wibowo, S.; Gordon, S.; Fortino, G. Adversarial training for deep learning-based cyberattack detection in IoT-based smart city applications. Comput. Secur. 2022, 120, 102783. [Google Scholar] [CrossRef]
- Priyadarshini, I.; Alkhayyat, A.; Gehlot, A.; Kumar, R. Time series analysis and anomaly detection for trustworthy smart homes. Comput. Electr. Eng. 2022, 102, 108193. [Google Scholar] [CrossRef]
- Priyadarshini, I.; Mohanty, P.; Alkhayyat, A.; Sharma, R.; Kumar, S. SDN and application layer DDoS attacks detection in IoT devices by attention-based Bi-LSTM-CNN. Trans. Emerg. Telecommun. Technol. 2023, 34, e4758. [Google Scholar] [CrossRef]
- Thapa, C.; Chamikara MA, P.; Camtepe, S.A. Advancements of federated learning towards privacy preservation: From federated learning to split learning. Fed. Learn. Syst. Towards Next Gener. AI 2021, 79–109. [Google Scholar]
- Ajao, L.A.; Apeh, S.T. Secure edge computing vulnerabilities in smart cities sustainability using petri net and genetic algorithm-based reinforcement learning. Intell. Syst. Appl. 2023, 18, 200216. [Google Scholar] [CrossRef]
- Rashid, M.M.; Kamruzzaman, J.; Hassan, M.M.; Imam, T.; Gordon, S. Cyberattacks detection in iot-based smart city applications using machine learning techniques. Int. J. Environ. Res. Public Health 2020, 17, 9347. [Google Scholar] [CrossRef]
- Mukherjee, D. Detection of data-driven blind cyber-attacks on smart grid: A deep learning approach. Sustain. Cities Soc. 2023, 92, 104475. [Google Scholar] [CrossRef]
- Almuqren, L.; Aljameel, S.S.; Alqahtani, H.; Alotaibi, S.S.; Hamza, M.A.; Salama, A.S. A White Shark Equilibrium Optimizer with a Hybrid Deep-Learning-Based Cybersecurity Solution for a Smart City Environment. Sensors 2023, 23, 7370. [Google Scholar] [CrossRef]
- Alsaade, F.W.; Al-Adhaileh, M.H. Cyber attack detection for self-driving vehicle networks using deep autoencoder algorithms. Sensors 2023, 23, 4086. [Google Scholar] [CrossRef]
- Ding, W.; Abdel-Basset, M.; Mohamed, R. DeepAK-IoT: An effective deep learning model for cyberattack detection in IoT networks. Inf. Sci. 2023, 634, 157–171. [Google Scholar] [CrossRef]
- Sharma, A.; Babbar, H. BoT-IoT: Detection of Attacks in IoT-Cybersecurity for Smart Transportation. In Proceedings of the 2023 8th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 1–3 June 2023; pp. 522–527. [Google Scholar]
- Ajao, L.A.; Apeh, S.T. Blockchain Integration with Machine Learning for Securing Fog Computing Vulnerability in Smart City Sustainability. In Proceedings of the 2023 1st International Conference on Advanced Innovations in Smart Cities (ICAISC), Jeddah, Saudi Arabia, 23–25 January2023; pp. 1–6. [Google Scholar]
- Alrayes, F.S.; Asiri, M.M.; Maashi, M.; Salama, A.S.; Hamza, M.A.; Ibrahim, S.S.; Zamani, A.S.; Alsaid, M.I. Intrusion Detection Using Chaotic Poor and Rich Optimization with Deep Learning Model for Smart City Environment. Sustainability 2023, 15, 6902. [Google Scholar] [CrossRef]
- Al-Taleb, N.; Saqib, N.A. Towards a hybrid machine learning model for intelligent cyber threat identification in smart city environments. Appl. Sci. 2022, 12, 1863. [Google Scholar] [CrossRef]
- Bilakanti, H.; Pasam, S.; Palakollu, V.; Utukuru, S. Anomaly detection in IoT environment using machine learning. Secur. Priv. 2024, e366. [Google Scholar] [CrossRef]
- Lin, C.; Du, B.; Sun, L.; Li, L. Hierarchical Context Representation and Self-adaptive Thresholding for Multivariate Anomaly Detection. IEEE Trans. Knowl. Data Eng. 2024, 1–12. [Google Scholar] [CrossRef]
- Mitropoulou, K.; Kokkinos, P.; Soumplis, P.; Varvarigos, E. Anomaly Detection in Cloud Computing using Knowledge Graph Embedding and Machine Learning Mechanisms. J. Grid Comput. 2024, 22, 6. [Google Scholar] [CrossRef]
- Jithish, J.; Alangot, B.; Mahalingam, N.; Yeo, K.S. Distributed Anomaly Detection in Smart Grids: A Federated Learning-Based Approach. IEEE Access 2023, 11, 7157–7179. [Google Scholar] [CrossRef]
- Dang, T.B.; Le, D.T.; Nguyen, T.D.; Kim, M.; Choo, H. Monotone split and conquer for anomaly detection in IoT sensory data. IEEE Internet Things J. 2021, 8, 15468–15485. [Google Scholar] [CrossRef]
- Nassif, A.B.; Talib, M.A.; Nasir, Q.; Dakalbab, F.M. Machine learning for anomaly detection: A systematic review. IEEE Access 2021, 9, 78658–78700. [Google Scholar] [CrossRef]
- Takiguchi, Y.; Shiono, S. Split Training Method to Generate Data Driven Model for Gas Turbine Engine Anomaly Detection. In Turbo Expo: Power for Land, Sea, and Air. Am. Soc. Mech. Eng. 2020, 84140, V005T05A027. [Google Scholar]
- Nixon, C.; Sedky, M.; Hassan, M. SALAD: An Exploration of Split Active Learning based Unsupervised Network Data Stream Anomaly Detection using Autoencoders. TechRxiv 2021. [Google Scholar]
- Dragoi, M.; Burceanu, E.; Haller, E.; Manolache, A.; Brad, F. AnoShift: A distribution shift benchmark for unsupervised anomaly detection. Adv. Neural Inf. Process. Syst. 2022, 35, 32854–32867. [Google Scholar]
- Zhang, H.; Xiao, Z.; Gu, J.; Liu, Y. A network anomaly detection algorithm based on semi-supervised learning and adaptive multiclass balancing. J. Supercomput. 2023, 79, 20445–20480. [Google Scholar] [CrossRef]
- NSL-KDD Dataset. Available online: http://nsl.cs.unb.ca/nsl-kdd/ (accessed on 30 November 2023).
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, ACT, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar]
- Kasongo, S.M. A deep learning technique for intrusion detection system using a Recurrent Neural Networks based framework. Comput. Commun. 2023, 199, 113–125. [Google Scholar] [CrossRef]
- Jahromi, A.N.; Karimipour, H.; Dehghantanha, A. An ensemble deep federated learning cyber-threat hunting model for Industrial Internet of Things. Comput. Commun. 2023, 198, 108–116. [Google Scholar] [CrossRef]
- Alazab, A.; Khraisat, A.; Singh, S.; Jan, T. Enhancing Privacy-Preserving Intrusion Detection through Federated Learning. Electronics 2023, 12, 3382. [Google Scholar] [CrossRef]
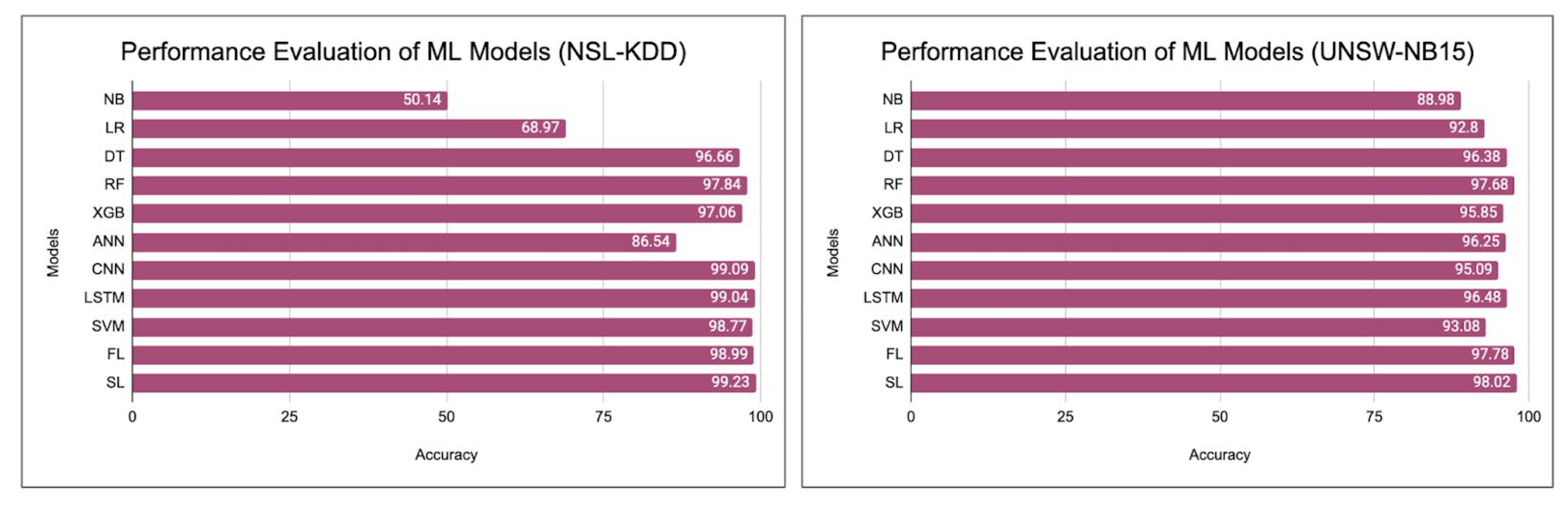
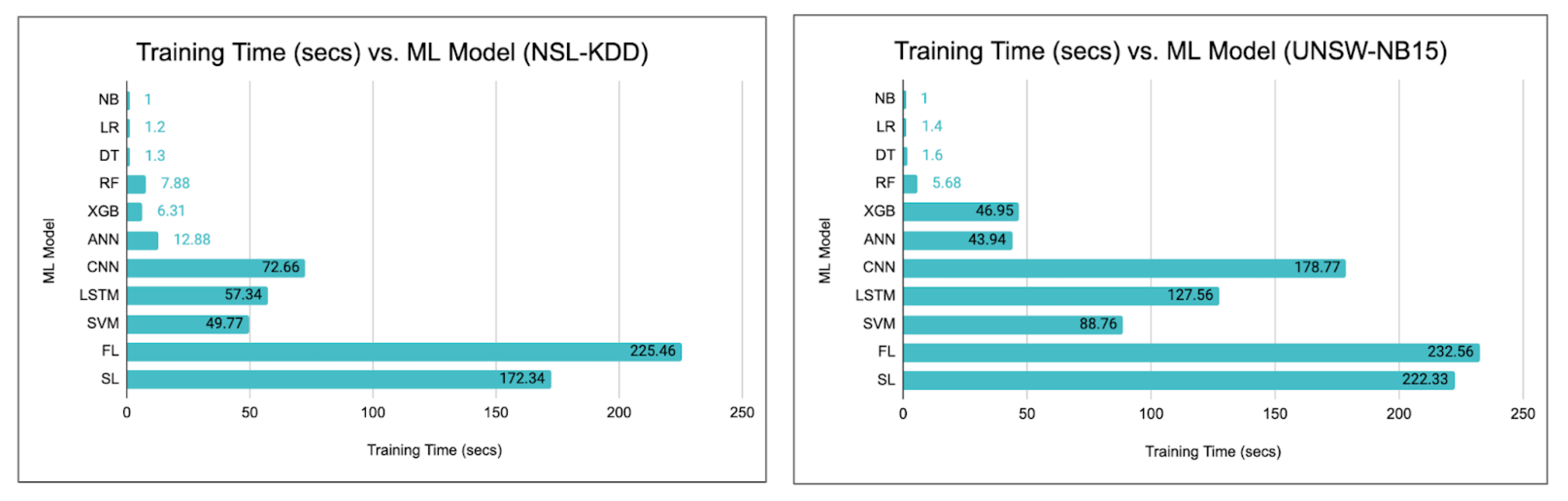
| Models | Accuracy | Precision | Recall | F-1 Score | Time-to-Run (s) |
|---|---|---|---|---|---|
| NB | 50.14 | 56.87 | 49.46 | 50.42 | Less than 5 |
| LR | 68.97 | 75.07 | 62.76 | 67.86 | Less than 5 |
| DT | 96.66 | 96.91 | 95.65 | 96.64 | Less than 5 |
| RF | 97.84 | 98.32 | 93.96 | 96.99 | 7.88 |
| XGB | 97.06 | 97.55 | 94.04 | 96.28 | 6.31 |
| ANN | 86.54 | 89.89 | 80.77 | 87.66 | 12.88 |
| CNN | 99.09 | 99.23 | 93.28 | 99.12 | 72.66 |
| LSTM | 99.04 | 99.87 | 91.72 | 99.10 | 57.34 |
| SVM | 98.77 | 98.89 | 93.84 | 97.68 | 49.77 |
| FL | 98.99 | 99.32 | 93.22 | 98.24 | 225.46 |
| SL | 99.23 | 99.64 | 98.68 | 99.29 | 172.34 |
| Models | Accuracy | Precision | Recall | F-1 Score | Time-to-Run (s) |
|---|---|---|---|---|---|
| NB | 88.98 | 88.87 | 88.80 | 88.83 | Less than 5 |
| LR | 92.80 | 92.97 | 92.80 | 92.09 | Less than 5 |
| DT | 96.38 | 96.38 | 96.32 | 96.44 | Less than 5 |
| RF | 97.68 | 97.69 | 97.68 | 97.68 | 5.68 |
| XGB | 95.85 | 95.86 | 95.85 | 95.85 | 46.95 |
| ANN | 96.25 | 96.66 | 96.32 | 96.03 | 43.94 |
| CNN | 95.09 | 95.03 | 95.01 | 95.03 | 178.77 |
| LSTM | 96.48 | 96.32 | 96.44 | 96.46 | 127.56 |
| SVM | 93.08 | 92.77 | 93.55 | 92.79 | 88.76 |
| FL | 97.78 | 97.64 | 97.56 | 97.89 | 232.56 |
| SL | 98.02 | 98.12 | 98.02 | 98.11 | 222.33 |
| Author and Year | Research | Methodologies/Parameters | Results |
|---|---|---|---|
| Ding et al., 2023 [10] | Detecting cyberattacks using Deep learning | RSR, TRB, and DB on TON-IoT, Edge-IIoTset, and UNSW-NB15 datasets | Accuracy~90.57%, 94.96%, and 98.41% |
| Sharma and Babbar, 2023 [11] | Detecting cyberattacks in smart transportation | Rf, NB, and DT on BoT-IoT dataset | RF shows the highest accuracy of 91% |
| Alrayes et al., 2023 [13] | Deep learning with chaotic poor and rich optimization for intrusion detection in smart city environment | Butterfly optimization algorithm (BOA) and deep sparse autoencoder (DSAE) on CICIDS dataset | Accuracy is 98.53% |
| Lin et al., 2024 [16] | Multivariate anomaly detection framework | Hierarchical context representation learning with deep learning methods | Proposed method shows precision values 0.90, 0.89, and 0.90 on three different datasets. |
| Mitropoulou et al., 2024 [17] | Anomaly detection in cloud computing | Knowledge graph embedding with isolation forest and CBLOF | Precision values for the methods proposed are 0.79 and 0.62. |
| Jithish et al., 2023 [18] | Distributed anomaly detection in smart grids | Federated learning compared against other algorithms | Federated learning with convolutional neural networks achieve highest accuracy of 0.989 |
| Dang et al., 2021 [19] | Anomaly detection in IoT sensory data | Monotone split and conquer (MSC) technique | Increased accuracy by 8%, reduced false-positive rate by 5% |
| Nixon et al., 2021 [22] | Anomaly detection in network data streams | Split active learning with autoencoders | Highest accuracy achieved is 98.78% |
| Dragoi et al., 2022 [23] | Network intrusion detection with data shifting | Protocol splitting technique, AnoShift | ROC curve shows best performance for local outlier factor, 91.50 |
| Zhang et al., 2023 [24] | Detecting anomalous network traffic | Semi-supervised learning and adaptive multiclass balancing | Precision and recall enhanced up to 5.7%, |
| Kasongo, 2023 [27] | Intrusion detection in IoT | Recurrent neural network, LSTM, gated recurrent units on NSL-KDD and UNSW-NB15 | XGB-LSTM achieved highest accuracy~88.13% on NSL-KDD XGB-RNN achieved highest accuracy~86.93% on UNSW-NB15 |
| Jahromi et al., 2023 [28] | Cyber-threat hunting model for industrial internet of things | Ensemble-based deep federated learning | Accuracy~94% to 99% |
| Alazab et al., 2023 [29] | Privacy-preserving intrusion detection | Federated learning on NSL-KDD dataset | 97.77% Accuracy |
| Proposed Work | Anomaly detection in IoT devices in smart city | Federated learning, split learning, classical ML models, ensembles, deep learning models on NSL-KDD and UNSW-NB15 | Federated learning achieves accuracy of 98.99% and 97.78%. Split learning achieves an accuracy of 99.23% and 98.02%, respectively. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Priyadarshini, I. Anomaly Detection of IoT Cyberattacks in Smart Cities Using Federated Learning and Split Learning. Big Data Cogn. Comput. 2024, 8, 21. https://doi.org/10.3390/bdcc8030021
Priyadarshini I. Anomaly Detection of IoT Cyberattacks in Smart Cities Using Federated Learning and Split Learning. Big Data and Cognitive Computing. 2024; 8(3):21. https://doi.org/10.3390/bdcc8030021
Chicago/Turabian StylePriyadarshini, Ishaani. 2024. "Anomaly Detection of IoT Cyberattacks in Smart Cities Using Federated Learning and Split Learning" Big Data and Cognitive Computing 8, no. 3: 21. https://doi.org/10.3390/bdcc8030021
APA StylePriyadarshini, I. (2024). Anomaly Detection of IoT Cyberattacks in Smart Cities Using Federated Learning and Split Learning. Big Data and Cognitive Computing, 8(3), 21. https://doi.org/10.3390/bdcc8030021








