Assessment of Security KPIs for 5G Network Slices for Special Groups of Subscribers
Abstract
:1. Introduction
2. Review of the Literature
Problem Statement
- Analysis of key performance indicators of 5G cellular networks.
- Selection of optimal indicators that describe the state of cyber security in the cellular network.
- Development of a mathematical apparatus to evaluate safety KPIs.
- Improvement of the 4G/5G network core to ensure continuous monitoring of security KPIs.
- Development of an algorithm and pseudocode for continuous monitoring and evaluation of safety KPIs.
3. Definition of Performance and Security KPIs
- A thousand-fold increase in mobile data volume per unit area.
- Ten to a hundred times more connected devices.
- Ten to a hundred times higher average user data rate.
- A tenfold reduction in energy consumption.
- End-to-end latency of less than one millisecond.
- Universal 5G access, even in low-density regions.
- 1.
- Security concerns:
- Spectrum vulnerability—the use of shared and unlicensed spectrum in 5G networks can make them susceptible to interference and jamming, which can disrupt government and IoT communications.
- Cyberattacks—with more connected devices and a larger attack surface, the risk of cyberattacks, such as distributed denial of service (DDoS) attacks, increases, potentially affecting government and IoT services.
- Device Vulnerabilities—IoT devices often have limited security features and can be vulnerable to hacking, compromising data security.
- 2.
- Privacy Concerns:
- Data privacy—the massive amount of data generated by IoT devices, including personal information, can raise concerns about data privacy and unauthorized access, particularly in government applications.
- Data Localization—governments may require data to be stored within their borders, creating challenges for global IoT deployments.
- 3.
- Compatibility and Interoperability:
- Legacy systems—Integrating 5G with existing communication systems can be challenging, particularly for government agencies with legacy infrastructure.
- IoT standards—The lack of universal IoT standards can hinder interoperability and create compatibility issues.
- 4.
- Risks to the supply chain:
- Vendor Dependencies: Relying on specific vendors for 5G infrastructure or IoT devices can create supply chain vulnerabilities, especially if the vendors are from countries with conflicting interests.
- 5.
- Regulatory and Compliance Challenges:
- Spectrum Regulations—Regulations and licensing for spectrum use can vary by region, complicating IoT device deployment and government communication systems.
- Security and Privacy Regulations—Compliance with data security and privacy regulations, such as GDPR or HIPAA, can be complex, especially in cross-border scenarios.
- Incident Response Time: Measures the time taken to detect and respond to security incidents, such as network breaches or unauthorized access attempts.
- Mean Time to Detect (MTTD): Measures the average time to detect security incidents or anomalies within the 5G network.
- Mean Time to Respond (MTTR): Measures the average time it takes to respond and resolve security incidents or vulnerabilities identified within the 5G network.
- Network availability: Measures the percentage of time the 5G network is available and operational without any security-related disruptions.
- Network Resilience: Measures the ability of the 5G network to withstand and recover from security attacks or incidents without significant impact on network performance.
- Authentication Failure Rate: Measures the percentage of failed authentication attempts within the 5G network, which can indicate potential security breaches or unauthorized access attempts.
- Intrusion Detection and Prevention Effectiveness: Measures the accuracy and effectiveness of intrusion detection and prevention systems deployed within the 5G network in detecting and blocking security threats.
- Data Leakage Rate: Measures the occurrence of data leaks or unauthorized access to sensitive information within the 5G network.
- Compliance with Security Standards: Measures the level of compliance with security standards and regulations relevant to 5G networks, such as the 3GPP security specifications or industry best practices.
- Security Patch Management: Measures the frequency and timeliness of applying security patches and updates to network equipment and software within the 5G network.
4. Development of Architecture
5. The Offered Model
- -
- network layers: , is the number of these layers.
- -
- , is a subset KPI for cyber security systems (Table 2).
- 1.
- Initialization (Constructor):
- 2.
- Input Data:
- 3.
- Checking Security KPIs:
- 4.
- Alerting:
- 5.
- Creating an Organization and Using the Class:
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Pateria, J.; Ahuja, L.; Som, S.; Seth, A. Applying Clustering to Predict Attackers Trace in Deceptive Ecosystem by Harmonizing Multiple Decoys Interactions Logs. Int. J. Inf. Technol. Comput. Sci. 2023, 15, 35–44. [Google Scholar] [CrossRef]
- Khaleefah, A.D.; Al-Mashhadi, H.M. Methodologies, Requirements and Challenges of Cybersecurity Frameworks: A Review. Int. J. Wirel. Microw. Technol. 2023, 13, 1–13. [Google Scholar] [CrossRef]
- 5G Network Slice Management. Available online: https://www.3gpp.org/technologies/slice-management (accessed on 10 July 2023).
- 5G-Trials—From 5G Experiments to Business Validation. Available online: https://5g-drive.eu/ (accessed on 9 September 2023).
- 5G-MoNArch: 5G Mobile Network Architecture for Diverse Services, Use Cases, and Applications in 5G and Beyond. Available online: https://5g-ppp.eu/5g-monarch/ (accessed on 17 June 2022).
- Juniper Networks Whitepaper. Managing 5G Slice Quality of Service End-to-End. Available online: https://www.juniper.net/content/dam/www/assets/flyers/us/en/managing-5g-slice-quality-of-service-end-to-end.pdf (accessed on 22 April 2021).
- Hallé, C. Why Network Slicing Requires Active Monitoring, Passive Monitoring AND True APM. Available online: https://accedian.com/blog/why-network-slicing-requires-active-monitoring-passive-monitoring-and-true-apm/ (accessed on 16 November 2020).
- Emblasoft. Innovate, Validate, Operate. Available online: https://emblasoft.com/ (accessed on 6 December 2022).
- 5G Network Slicing Self-Management White Paper. Available online: https://www-file.huawei.com/-/media/corporate/pdf/news/5g-network-slicing-self-management-white-paper.pdf?la=en (accessed on 19 October 2020).
- Wichary, T.; Mongay Batalla, J.; Mavromoustakis, C.X.; Żurek, J.; Mastorakis, G. Network Slicing Security Controls and Assurance for Verticals. Electronics 2022, 11, 222. [Google Scholar] [CrossRef]
- Ogidiaka, E.; Ogwueleka, F.N.; Irhebhude, M.E. Game-Theoretic Resource Allocation Algorithms for Device-to-Device Communications in Fifth Generation Cellular Networks: A Review. Int. J. Inf. Eng. Electron. Bus. 2021, 13, 44–51. [Google Scholar] [CrossRef]
- Mallipudi, C.C.; Chandra, S.; Prakash, P.; Arya, R.; Husain, A.; Qamar, S. Reinforcement Learning Based Efficient Power Control and Spectrum Utilization for D2D Communication in 5G Network. Int. J. Comput. Netw. Inf. Secur. 2023, 15, 13–24. [Google Scholar] [CrossRef]
- Majeed, A.; Alnajim, A.M.; Waseem, A.; Khaliq, A.; Naveed, A.; Habib, S.; Islam, M.; Khan, S. Deep Learning-Based Symptomizing Cyber Threats Using Adaptive 5G Shared Slice Security Approaches. Future Internet 2023, 15, 193. [Google Scholar] [CrossRef]
- Zahoor, S.; Ahmad, I.; Othman, M.; Mamoon, A.; Rehman, A.U.; Shafiq, M.; Hamam, H. Comprehensive Analysis of Network Slicing for the Developing Commercial Needs and Networking Challenges. Sensors 2022, 22, 6623. [Google Scholar] [CrossRef]
- De Jesus Martins, R.; Wickboldt, J.A.; Granville, L.Z. Assisted Monitoring and Security Provisioning for 5G Microservices-Based Network Slices with SWEETEN. J. Netw. Syst. Manag. 2023, 31, 36. [Google Scholar] [CrossRef]
- Kuklinski, S.; Tomaszewski, L.; Kolakowski, R.; Chemouil, P. 6G-LEGO: A framework for 6G network slices. J. Commun. Netw. 2021, 23, 442–453. [Google Scholar] [CrossRef]
- Kukliński, S.; Tomaszewski, L. Key Performance Indicators for 5G network slicing. In Proceedings of the IEEE Conference on Network Softwarization (NetSoft), Paris, France, 24–28 June 2019; pp. 464–471. [Google Scholar] [CrossRef]
- El Azzaoui, A.; Singh, S.K.; Pan, Y.; Park, J.H. Block5GIntell: Blockchain for AI-Enabled 5G Networks. IEEE Access 2020, 8, 145918–145935. [Google Scholar] [CrossRef]
- Suomalainen, J.; Juhola, A.; Shahabuddin, S.; Mammela, A.; Ahmad, I. Machine Learning Threatens 5G Security. IEEE Access 2020, 8, 190822–190842. [Google Scholar] [CrossRef]
- Zhang, S. An Overview of Network Slicing for 5G. IEEE Wirel. Commun. 2019, 26, 111–117. [Google Scholar] [CrossRef]
- Koumaras, H.; Tsolkas, D.; Gardikis, G.; Gomez, P.M.; Frascolla, V.; Triantafyllopoulou, D.; Emmelmann, M.; Koumaras, V.; Osma, M.L.G.; Munaretto, D.; et al. 5GENESIS: The Genesis of a flexible 5G Facility. In Proceedings of the 2018 IEEE 23rd International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Barcelona, Spain, 17–19 September 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Doukoglou, T.; Gezerlis, V.; Trichias, K.; Kostopoulos, N.; Vrakas, N.; Bougioukos, M.; Legouable, R. Vertical Industries Requirements Analysis & Targeted KPIs for Advanced 5G Trials. In Proceedings of the 2019 European Conference on Networks and Communications (EuCNC), Valencia, Spain, 18–21 June 2019; pp. 95–100. [Google Scholar] [CrossRef]
- Gupta, M.; Legouable, R.; Rosello, M.M.; Cecchi, M.; Alonso, J.R.; Lorenzo, M.; Kosmatos, E.; Boldi, M.R.; Carrozzo, G. The 5G EVE End-to-End 5G Facility for Extensive Trials. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Boero, L.; Bruschi, R.; Davoli, F.; Marchese, M.; Patrone, F. Satellite Networking Integration in the 5G Ecosystem: Research Trends and Open Challenges. IEEE Netw. 2018, 32, 9–15. [Google Scholar] [CrossRef]
- Banović-Ćurguz, N.; Ilišević, D. Mapping of QoS/QoE in 5G Networks. In Proceedings of the 2019 42nd International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 20–24 May 2019; pp. 404–408. [Google Scholar] [CrossRef]
- Christopoulou, M.; Xilouris, G.; Sarlas, A.; Koumaras, H.; Kourtis, M.-A.; Anagnostopoulos, T. 5G Experimentation: The Experience of the Athens 5GENESIS Facility. In Proceedings of the 2021 IFIP/IEEE International Symposium on Integrated Network Management (IM), Bordeaux, France, 17–21 May 2021; pp. 783–787. [Google Scholar]
- Saha, N.; James, A.; Shahriar, N.; Boutaba, R.; Saleh, A. Demonstrating Network Slice KPI Monitoring in a 5G Testbed. In Proceedings of the NOMS 2022–2022 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 25–29 April 2022; pp. 1–3. [Google Scholar] [CrossRef]
- Xie, M.; Gonzalez, A.J.; Gronsund, P.; Lonsethagen, H.; Waldemar, P.; Tranoris, C.; Denazis, S.; Elmokashfi, A. Practically Deploying Multiple Vertical Services into 5G Networks with Network Slicing. IEEE Netw. 2022, 36, 32–39. [Google Scholar] [CrossRef]
- Lagen, S.; Bojovic, B.; Koutlia, K.; Zhang, X.; Wang, P.; Qu, Q. QoS Management for XR Traffic in 5G NR: A Multi-Layer System View & End-to-End Evaluation. IEEE Commun. Mag. 2023, 1–7. [Google Scholar] [CrossRef]
- Vordonis, D.; Giannopoulos, D.; Papaioannou, P.; Tranoris, C.; Denazis, S.; Rahav, R.; Altman, B.; Bosneag, A.-M.; Jain, S.; Margolin, U.; et al. Monitoring and Evaluation of 5G Key Performance Indicators in Media Vertical Applications. In Proceedings of the 2022 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Athens, Greece, 5–8 September 2022; pp. 203–208. [Google Scholar] [CrossRef]
- Bolla, R.; Bruschi, R.; Davoli, F.; Lombardo, C.; Pajo, J.F.; Siccardi, B. Machine-Learning-Based 5G Network Function Scaling via Black- and White-Box KPIs. In Proceedings of the 21st Mediterranean Communication and Computer Networking Conference (MedComNet), Island of Ponza, Italy, 13–15 June 2023; pp. 143–150. [Google Scholar] [CrossRef]
- Pinto, A.; Santaromita, G.; Fiandrino, C.; Giustiniano, D.; Esposito, F. Characterizing Location Management Function Performance in 5G Core Networks. In Proceedings of the IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Phoenix, AZ, USA, 14–16 November 2022; pp. 66–71. [Google Scholar] [CrossRef]
- Abdellatif, A.A.; Mohamed, A.; Erbad, A.; Guizani, M. Dynamic Network Slicing and Resource Allocation for 5G-and-Beyond Networks. In Proceedings of the 2022 IEEE Wireless Communications and Networking Conference (WCNC), Austin, TX, USA, 10–13 April 2022; pp. 262–267. [Google Scholar] [CrossRef]
- Beaubrun, R. Technical Challenges and Categorization of 5G Mobile Services. In Proceedings of the 2022 Thirteenth International Conference on Ubiquitous and Future Networks (ICUFN), Barcelona, Spain, 5–8 July 2022; pp. 345–350. [Google Scholar] [CrossRef]
- De Gaudenzi, R.; Luise, M.; Sanguinetti, L. The Open Challenge of Integrating Satellites into (Beyond-) 5G Cellular Networks. IEEE Netw. 2022, 36, 168–174. [Google Scholar] [CrossRef]
- Fkih, F.; Al-Turaif, G. Threat Modelling and Detection Using Semantic Network for Improving Social Media Safety. Int. J. Comput. Netw. Inf. Secur. 2023, 15, 39–53. [Google Scholar] [CrossRef]
- Shaikh, N.S.; Yasin, A.; Fatima, R. Ontologies as Building Blocks of Cloud Security. Int. J. Inf. Technol. Comput. Sci. 2022, 14, 52–61. [Google Scholar] [CrossRef]
- Redefining Security KPIs for 5G Service Providers. Available online: https://www.helpnetsecurity.com/2019/11/19/5g-security-kpis/ (accessed on 19 November 2019).
- Help Net Security. Average Data Breach Cost Has Risen to $3.92 Million. Available online: https://www.helpnetsecurity.com/2019/07/24/data-breach-cost/ (accessed on 24 July 2011).
- Avkurova, Z.; Gnatyuk, S.; Abduraimova, B.; Fedushko, S.; Syerov, Y.; Trach, O. Models for early web-attacks detection and intruders identification based on fuzzy logic. Procedia Comput. Sci. 2022, 198, 694–699. [Google Scholar] [CrossRef]
- Aurobindo, S. An introduction to intrusion detection. Crossroads 1996, 2, 3–7. [Google Scholar]
- Kuypers, M.A.; Maillart, T.; Paté-Cornell, E. An Empirical Analysis of Cyber Security Incidents at a Large Organization; Department of Management Science and Engineering, Stanford University, School of Information: Stanford, CA, USA, 2016. [Google Scholar]
- Doerrfeld, B. 5 Mean-Time Reliability Metrics to Follow. 7 July 2022. Available online: https://devops.com/5-mean-time-reliability-metrics-to-follow (accessed on 7 July 2023).
- Hou, L.; Lao, Y.; Wang, Y.; Zhang, Z.; Zhang, Y.; Li, Z. Modeling freeway incident response time: A mechanism-based approach. Transp. Res. Part C Emerg. Technol. 2013, 28, 87–100. [Google Scholar] [CrossRef]
- Oggerino, C. High Availability Network Fundamentals; Cisco Press: Indianapolis, IN, USA, 2001; 25p, ISBN 1-58713-017-3. [Google Scholar]
- Azenkot, S.; Rector, K.; Ladner, R.; Wobbrock, J. PassChords: Secure multi-touch authentication for blind people. In Proceedings of the 14th international ACM SIGACCESS conference on Computers and Accessibility, Boulder, CO, USA, 22–24 October 2012; pp. 159–166. [Google Scholar]
- Campos, L.M.; Ribeiro, L.; Karydis, I.; Karagiannis, S.; Pedro, D.; Martins, J.; Marques, C.; Armada, A.G.; Leal, R.P.; Lopez-Morales, M.J.; et al. Reference Scenarios and Key Performance Indicators for 5G Ultra-dense Networks. In Proceedings of the 12th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Porto, Portugal, 20–22 July 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Patel, A.; Qassim, Q.; Wills, C. A survey of intrusion detection and prevention systems. Inf. Manag. Comput. Secur. 2010, 18, 277–290. [Google Scholar] [CrossRef]
- Alneyadi, S.; Sithirasenan, E.; Muthukkumarasamy, V. A survey on data leakage prevention systems. J. Netw. Comput. Appl. 2016, 62, 137–152. [Google Scholar] [CrossRef]
- Lobato, A.G.P.; Lopez, M.A.; Sanz, I.J.; Cardenas, A.A.; Duarte, O.C.M.; Pujolle, G. An adaptive real-time architecture for zero-day threat detection. In Proceedings of the IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Kitchen, J.T.; Coogan, D.R.; Christian, K.H. The Evolution of Legal Risks Pertaining to Patch Management and Vulnerability Management. Duq. L. Rev. 2021, 59, 269. [Google Scholar]
- Susanto, H.; Almunawar, M.N. Information Security Management Systems: A Novel Framework and Software as a Tool for Compliance with Information Security Standard; CRC Press: Boca Raton, FL, USA, 2018; 302p, ISBN 1771885777. [Google Scholar]
- Perez, R.; Garcia-Reinoso, J.; Zabala, A.; Serrano, P.; Banchs, A. A monitoring framework for multi-site 5G platforms. In Proceedings of the IEEE European Conference on Networks and Communications (EuCNC), Dubrovnik, Croatia, 15–18 June 2020; pp. 52–56. [Google Scholar] [CrossRef]
- Porambage, P.; Miche, Y.; Kalliola, A.; Liyanage, M.; Ylianttila, M. Secure Keying Scheme for Network Slicing in 5G Architecture. In Proceedings of the IEEE Conference on Standards for Communications and Networking (CSCN), Granada, Spain, 28–30 October 2019; pp. 1–6. [Google Scholar] [CrossRef]
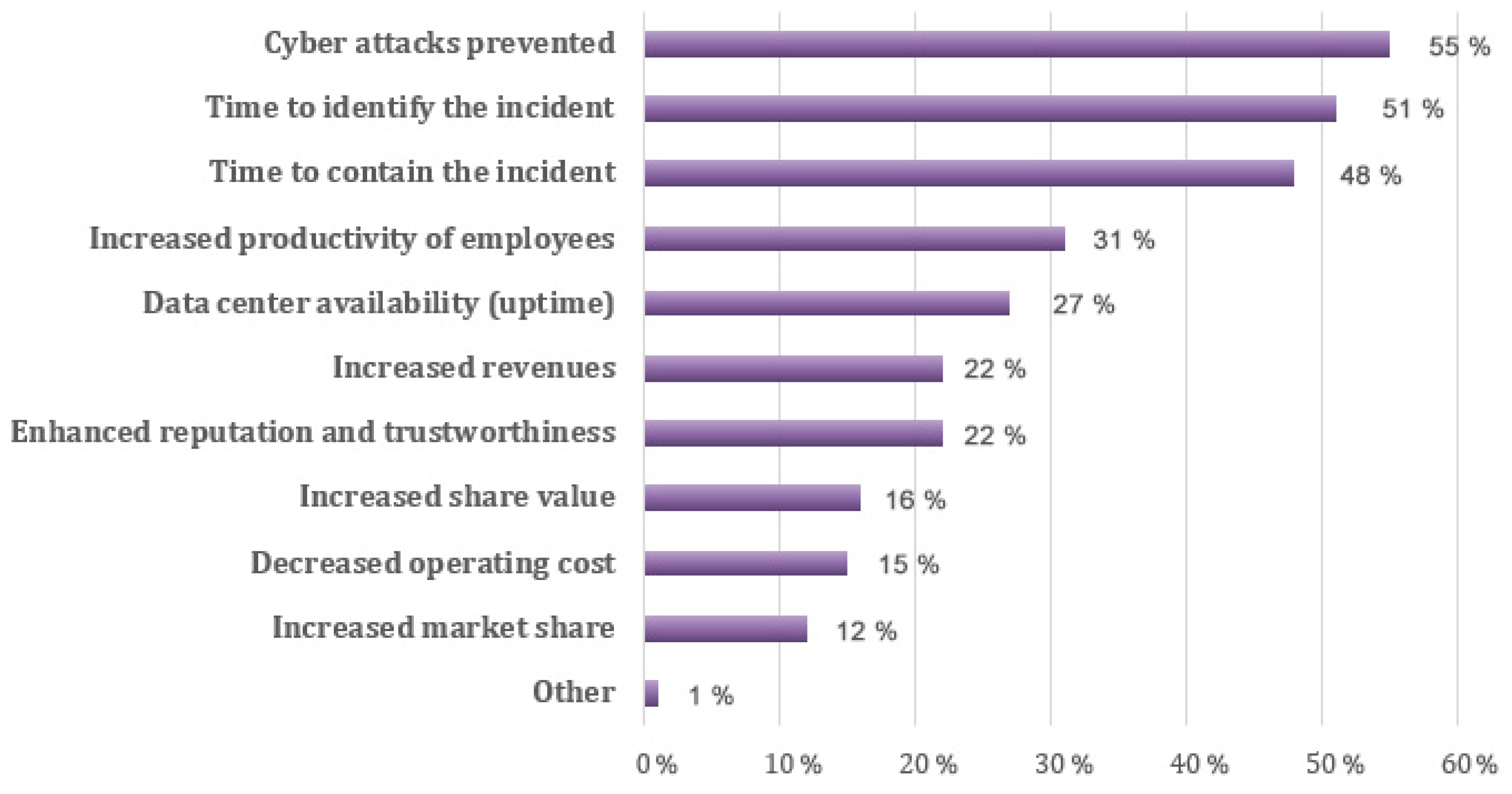
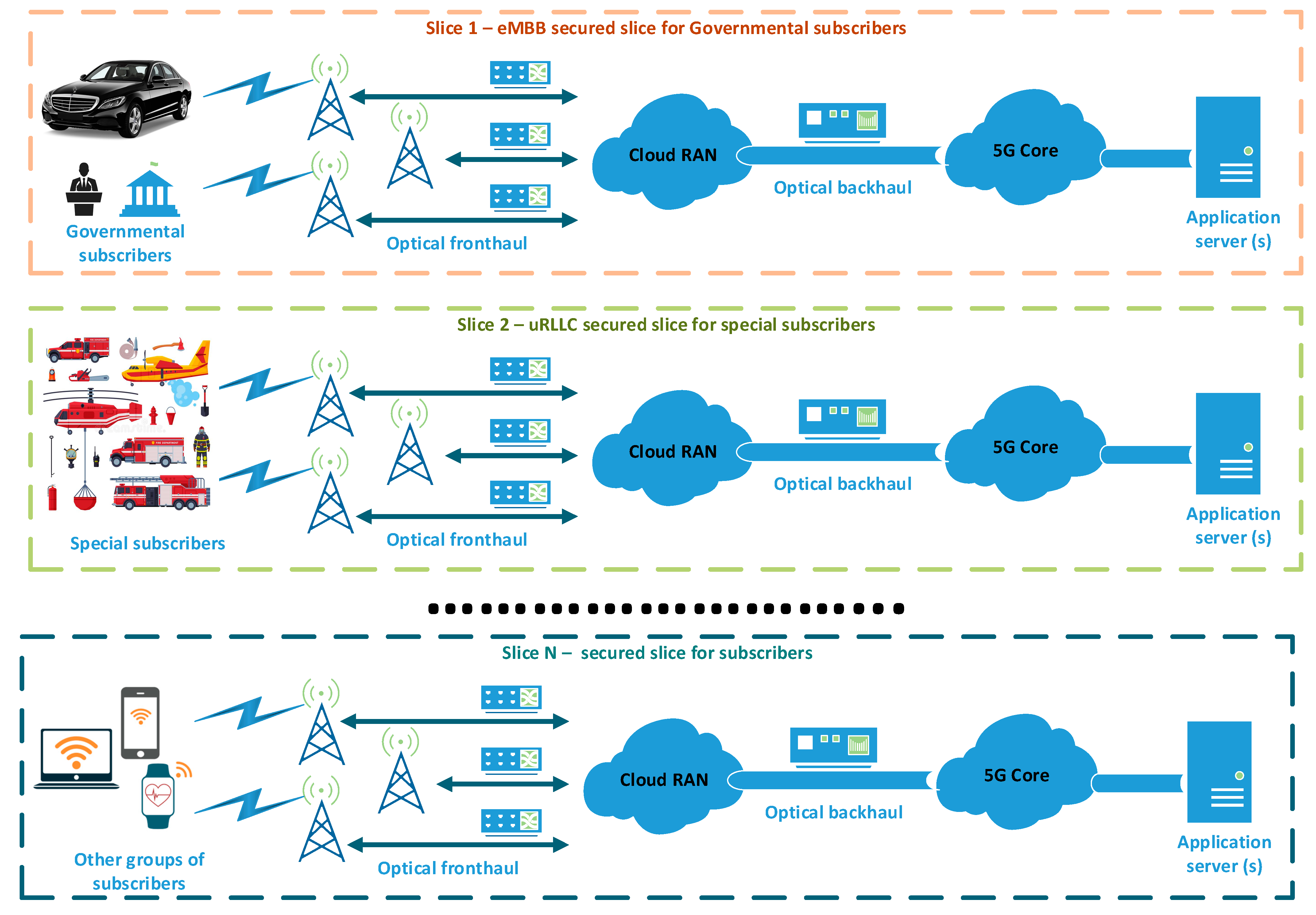
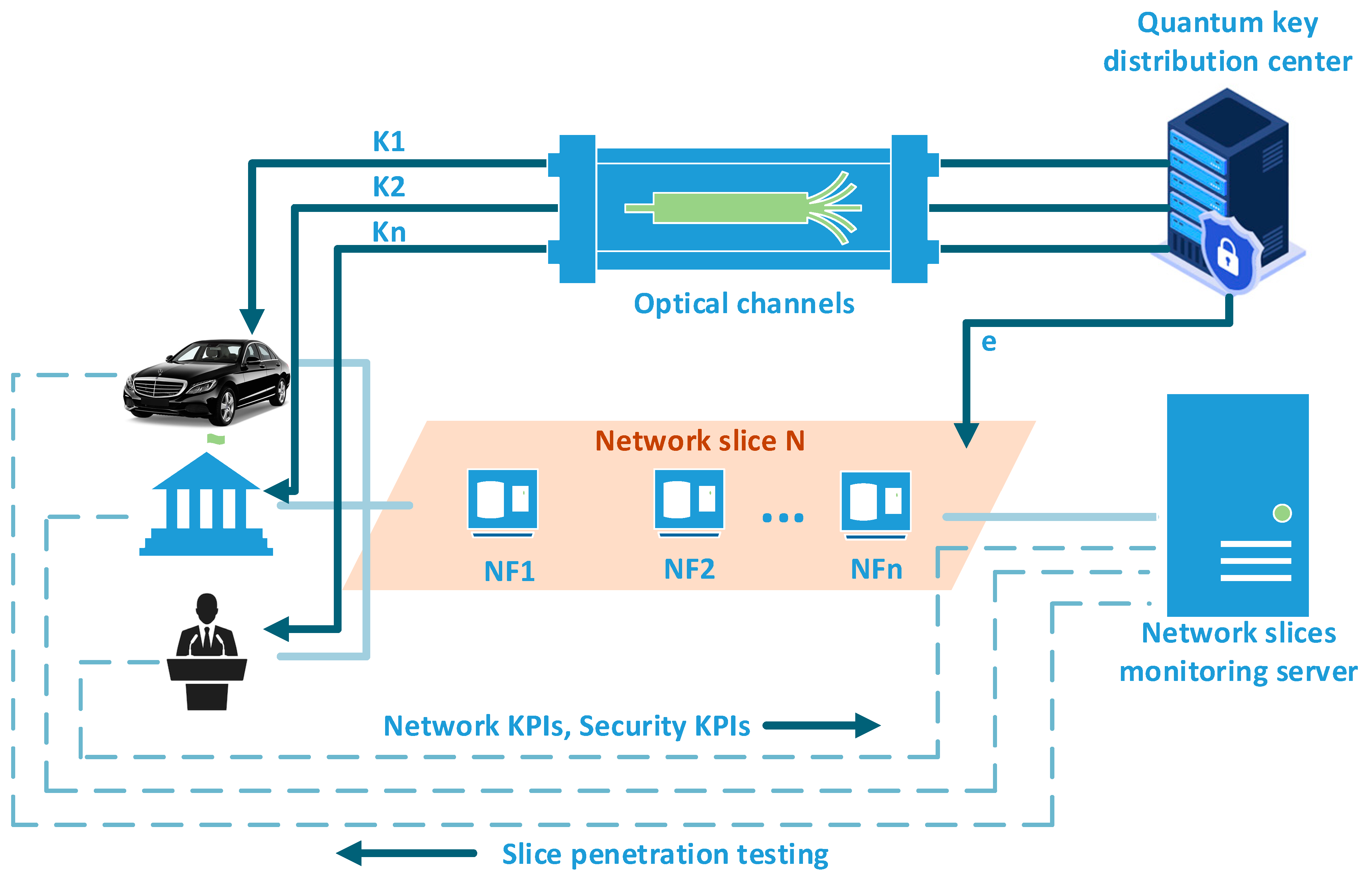
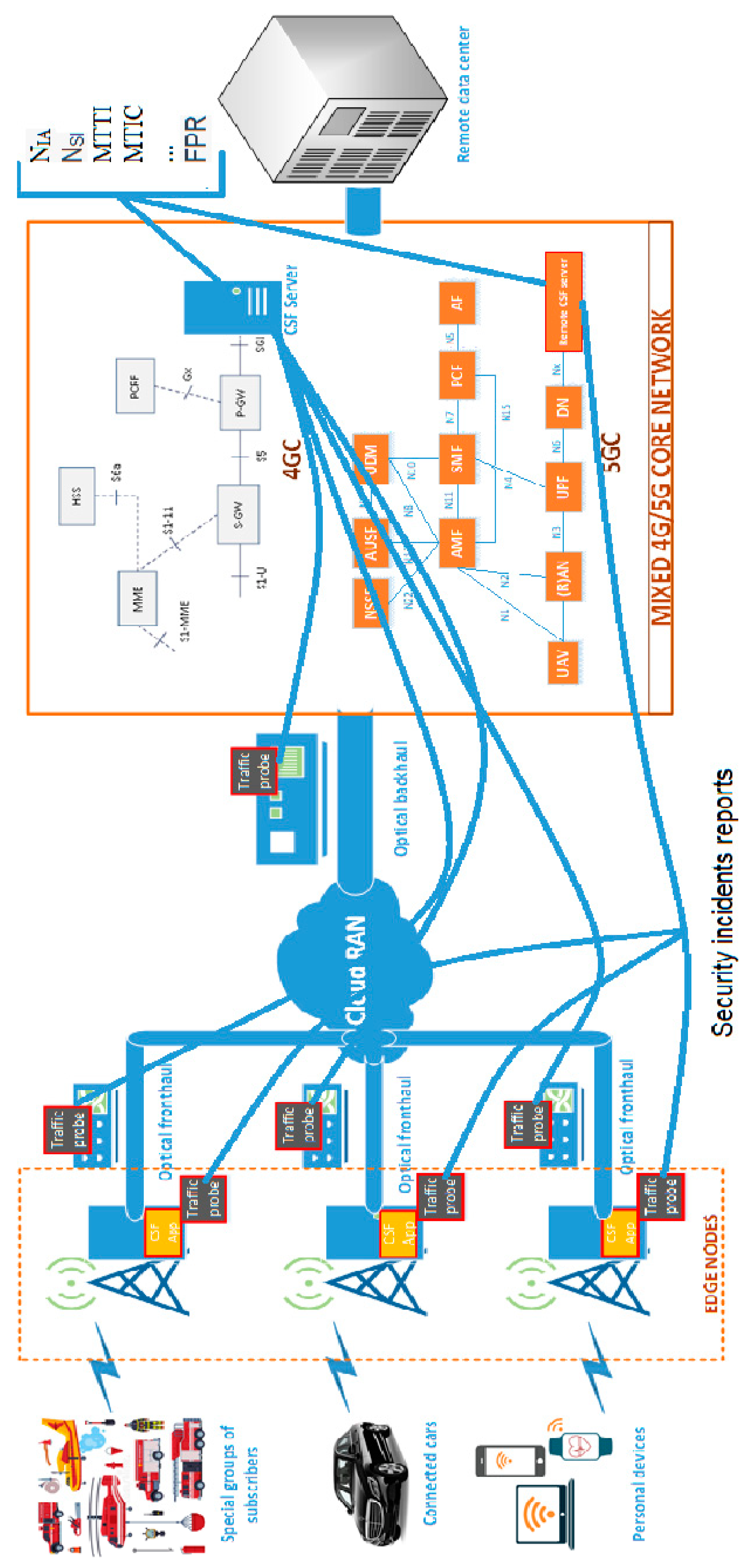
| # Challenge | Security Threat | Target Point/Network Element | Effected Technology | Links | Privacy | ||
|---|---|---|---|---|---|---|---|
| SDN | NFV | Cloud | |||||
| DoS attack | Centralized control elements | + | + | + | ||
| Hijacking attacks | SDN controller, hypervisor | + | + | |||
| Signaling storms | 5G core network elements | + | + | |||
| Resource (slice) theft | Hypervisor, shared cloud resources | + | + | |||
| Configuration attacks | SDN (virtual) switches, routers | + | + | |||
| Saturation attacks | SDN controller and switches | + | ||||
| Penetration attacks | Virtual resources, clouds | + | + | |||
| User identity theft | User information data bases | + | + | |||
| TCP level attacks | SDN controller-switch communication | + | + | |||
| Man-in-the-middle attack | SDN controller-communication | + | + | + | ||
| Reset and IP spoofing | Control channels | + | ||||
| Scanning attacks | Open air interfaces | + | + | |||
| Security keys exposure | Unencrypted channels | + | ||||
| Semantic information attacks | Subscriber location | + | + | |||
| Timing attacks | Subscriber location | + | + | |||
| Boundary attacks | Subscriber location | + | ||||
| IMSI catching attacks | Base station, identity registers | + | + | |||
| The Type of 5G Performance Requirement | Minimum KPI Requirement and Category |
|---|---|
| Peak Spectral Efficiency | The downlink spectral efficiency is 30 bits per second per hertz (bps/Hz), whereas the uplink spectral efficiency is 15 bits per second per hertz (bps/Hz). (eMBB) |
| Peak Data Rate | The downlink speed for data transmission is 20 Gbps, while the uplink speed is 10 Gbps. (eMBB) |
| Area Traffic Capacity | In an indoor hotspot, the downlink data rate is 10 Mbps per square meter. (eMBB test environment) |
| Data Rate of User Experience | The downlink speed for data transmission is 100 Mbps, while the uplink speed is 50 Mbps. (eMBB) |
| Connection Density | 106 devices/Km2 (mMTC) |
| Latency (Control Plane) | The specified target latency is 20 milliseconds, with 10 milliseconds being the encouraged latency whenever possible. (eMBB, URLLC) |
| Latency (User Plane) | The specified latency requirement for enhanced mobile broadband (eMBB) is 4 milliseconds, whereas for ultrareliable low latency communications (URLLC), the latency target is 1 millisecond. (eMBB, URLLC) |
| Average Spectral Efficiency | Indoor coverage area with high-speed Internet: Download (DL) speed of 9 Mbps and upload (UL) speed of 6.75 Mbps. Dense urban coverage area: Download (DL) speed of 7.8 Mbps and upload (UL) speed of 5.4 Mbps. Rural coverage area: Download (DL) speed of 3.3 Mbps and Upload (UL) speed of 1.6 Mbps. (eMBB) |
| Reliability | 1 × 10−5 the probability of successfully transmitting a layer-2 protocol data unit (PDU) consisting of 32 bytes in a 1 millisecond timeframe in an urban macro-URLLC test environment with edge channel coverage quality. (URLLC) |
| Energy Efficiency | Demonstrating Efficient Data Transmission (Loaded Case): The effectiveness of data transmission can be assessed by evaluating the “average spectral efficiency” metric. Minimizing Energy Consumption (No-Data Case): This test case aims to support a high sleep ratio and long sleep duration to achieve low energy consumption. It is designed to optimize the system for scenarios without data transmission. (eMBB) |
| Mobility | In a dense urban environment, the maximum speed considered is up to 30 Km/h, while in a rural setting it can reach up to 500 Km/h. (eMBB) |
| Mobility Interruption Time | 0 ms (eMBB, URLLC) |
| Bandwidth (Maximum Aggregated System) | For operation in high-frequency bands (above 6 GHz), the minimum required bandwidth is at least 100 MHz, while the maximum supported bandwidth can reach up to 1 GHz. (IMT-2020) |
| The Type of 5G Security Requirement | Minimum Security KPI Requirements | Formula/Symbol | Challenges Addressed (from Table 1) |
|---|---|---|---|
| Intrusion Attempts [42] | As a cybersecurity operative, you must monitor intrusion attempts on your organization’s network. Similarly, you can regularly review your firewall logs to see if anyone has unauthorized access to the network. | NIA | 1–3, 5–7, 9–17 |
| Number of Security Incidents [43] | This KPI quantifies the total number of security incidents or breaches detected in the 5G network over a specific period. Monitoring this metric helps to track the security posture and identify trends or patterns. | NSI | 1–17 |
| Mean Time to Identification (MTTI) [43] | The whole process must take a maximum of 12 h. | , where: —sum of identification times; —number of incidents. | 1–17 |
| Mean Time To Contain (MTIC) [43] | The entire process must take a maximum of 12 h. | , where: —sum of contain times —number of incidents. | 1–17 |
| Mean Time to Recover (MTTR) [44] | This KPI measures the average recovery time from a security incident or breach. A shorter MTTR indicates effective incident response and recovery capabilities, minimizing impact on network operations. | , where: —total time taken to recover from incidents —number of incidents. | 1–17 |
| Incident Response Time [43] | Aim for a rapid incident response time to ensure timely detection and mitigation of security incidents. A specific target can be set, such as responding to critical incidents within a defined timeframe (e.g., within 1 h). | , where: —time of incident resolution; —time of incident detection. | 1–3, 5–7, 9–17 |
| Mean Time to Detect (MTTD) [45] | Strive to minimize the average time taken to detect security incidents. Setting a target, such as keeping the MTTD below a certain threshold (e.g., within 30 min), can help promptly identify potential threats. | , where: —sum of detection times; —number of incidents. | 1–3, 5–7, 9–17 |
| Mean Time to Respond (MTTRes) [45] | The aim is to minimize the average time taken to respond and resolve security incidents. Establishing a target, such as keeping the MTTR below a specific value (e.g., within 2 h), can help expedite incident resolution. | , where: —sum of respond times; —number of incidents. | 1–3, 5–7, 9–17 |
| Network Availability [46] | Aim for high network availability to minimize disruptions due to security incidents. Setting a target, such as maintaining network availability at a high percentage (e.g., 99.99%), ensures that security events do not significantly impact network services. | , where: —total uptime; —total time. | 1–3, 9, 11 |
| Authentication Failure Rate [47] | Try to keep the authentication failure rate as low as possible. Although the acceptable rate may depend on the specific network context, aiming for a minimal failure rate (for example, less than 1%) helps reduce the risk of unauthorized access. | , where: —number of authentication failures; —total number of authentication attempts. | 10, 17 |
| Intrusion Detection and Prevention Effectiveness [48] | Implement robust intrusion detection and prevention systems with high accuracy rates. Regularly assess and monitor the effectiveness of these systems, with a goal of a high detection and prevention rate (for example, above 95%). | , , where: —number of true positives; —number of false positives; —total number of actual intrusions. | 4, 7, 8, 10, 17 |
| Data Leakage Rate [49] | Aim for a minimal data leakage rate within the 5G network. This can be achieved through solid access controls, encryption, and monitoring mechanisms. Setting a target, such as keeping the data leakage rate below a specific value (e.g., 0.5%), helps ensure data protection. | , where: —number of data leakage incidents; —total volume of data handled. | 13 |
| Threat Detection Time [50] | This KPI measures the time it takes to detect and identify a security threat or intrusion on the 5G network. A shorter detection time indicates a more proactive and effective security system. | , where: —time of threat detection; —time of threat occurrence. | 1–17 |
| Patching and Vulnerability Management [51] | This KPI evaluates the time to apply security patches and updates to address known vulnerabilities in the 5G network infrastructure. Correct patching helps minimize the risk of exploitation. Time taken to apply patches and updates | PVMT | 1–17 |
| Compliance with Security Standards [52] | This KPI evaluates the extent to which the 5G network adheres to relevant cybersecurity standards and regulations. Compliance with standards such as the 3GPP security specifications ensures a robust security posture. | , where: —number of compliance requirements met; —total number of compliance requirements. | 1–17 |
| Security KPIs | Network Slice-Type Thresholds | |||
|---|---|---|---|---|
| Slice 1 (i.e., eMBB) | Slice 2 (i.e., MCC) | … | Slice N | |
| NIA | NIA1 | NIA2 | … | NIAN |
| NSI | NSI1 | NSI2 | … | NSI2 |
| MTTI | MTTI1 | MTTI2 | … | MTTIN |
| MTTR | MTTR1 | MTTR2 | … | MTTRN |
| MTTD | MTTD1 | MTTD2 | … | MTTDN |
| MTTRes | MTTRes1 | MTTRes2 | … | MTTResN |
| NA | NA1 | NA2 | … | NA3 |
| AFR | AFR1 | AFR2 | … | AFRN |
| TPR | TPR1 | TPR2 | … | TPRN |
| FPR | FPR1 | FPR2 | … | FPRN |
| DLR | DLR1 | DLR2 | … | DLRN |
| TDT | TDT1 | TDT2 | … | TDTN |
| PVMT | PVMT1 | PVMT2 | … | PVMTN |
| CR | CR1 | CR2 | … | CRN |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Odarchenko, R.; Iavich, M.; Iashvili, G.; Fedushko, S.; Syerov, Y. Assessment of Security KPIs for 5G Network Slices for Special Groups of Subscribers. Big Data Cogn. Comput. 2023, 7, 169. https://doi.org/10.3390/bdcc7040169
Odarchenko R, Iavich M, Iashvili G, Fedushko S, Syerov Y. Assessment of Security KPIs for 5G Network Slices for Special Groups of Subscribers. Big Data and Cognitive Computing. 2023; 7(4):169. https://doi.org/10.3390/bdcc7040169
Chicago/Turabian StyleOdarchenko, Roman, Maksim Iavich, Giorgi Iashvili, Solomiia Fedushko, and Yuriy Syerov. 2023. "Assessment of Security KPIs for 5G Network Slices for Special Groups of Subscribers" Big Data and Cognitive Computing 7, no. 4: 169. https://doi.org/10.3390/bdcc7040169
APA StyleOdarchenko, R., Iavich, M., Iashvili, G., Fedushko, S., & Syerov, Y. (2023). Assessment of Security KPIs for 5G Network Slices for Special Groups of Subscribers. Big Data and Cognitive Computing, 7(4), 169. https://doi.org/10.3390/bdcc7040169








