The Dataset for Optimal Circulant Topologies
Abstract
1. Introduction
2. The Problem of the Synthesis of Circulant Topologies
- Iterations in which the topologies, being formed and denoted by indices, are performed (Figure 2).
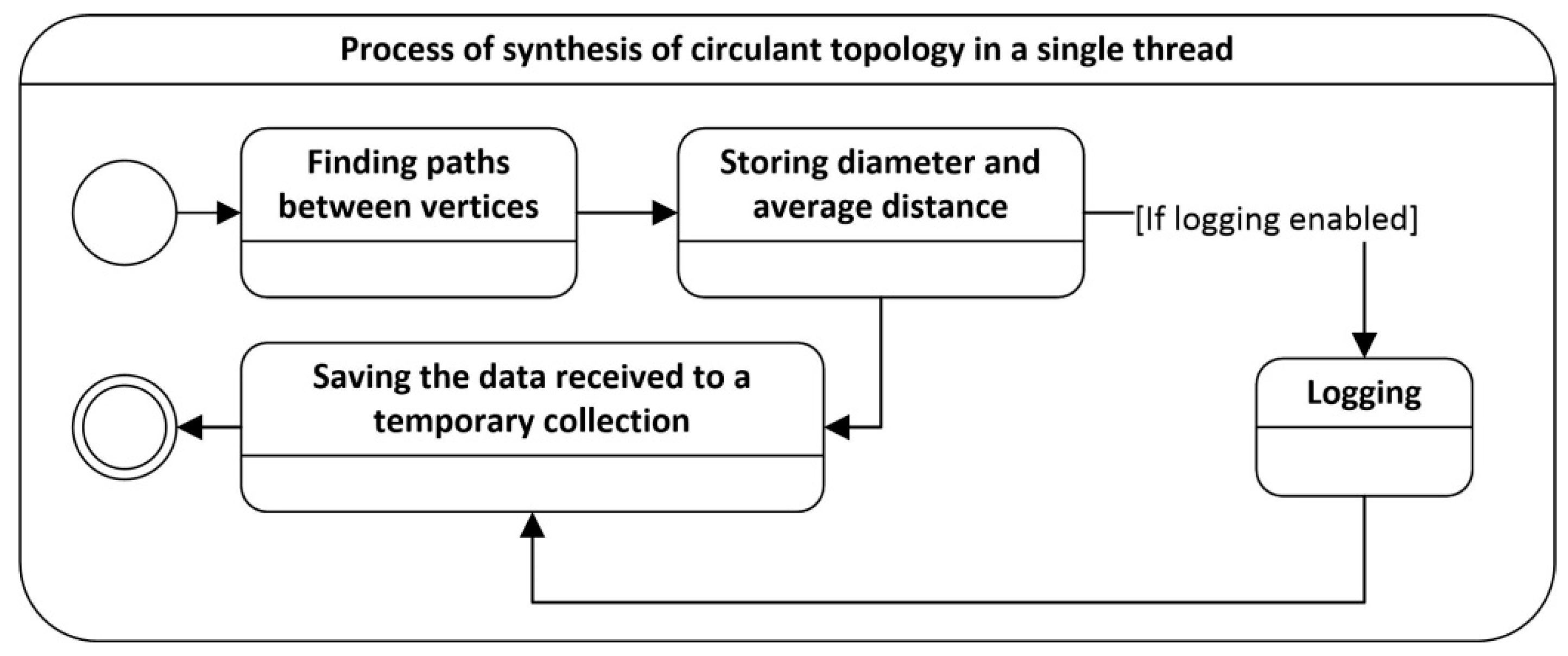
- For every received signature of the topology at every step of the iteration, the analysis of the obtained topology is carried out (Figure 3).
- The parameters of the topology are calculated (Figure 4).
- The topology is evaluated according to the introduced optimality criterion defined by objective function (Figure 4).
- Reducing the number of variants for enumerating possible parametric descriptions of topologies.
- Improving the speed of calculation of the diameter and MPL between the nodes.
- Reducing the forming time and memory cost of adjacency matrices, or abandoning them as a whole.
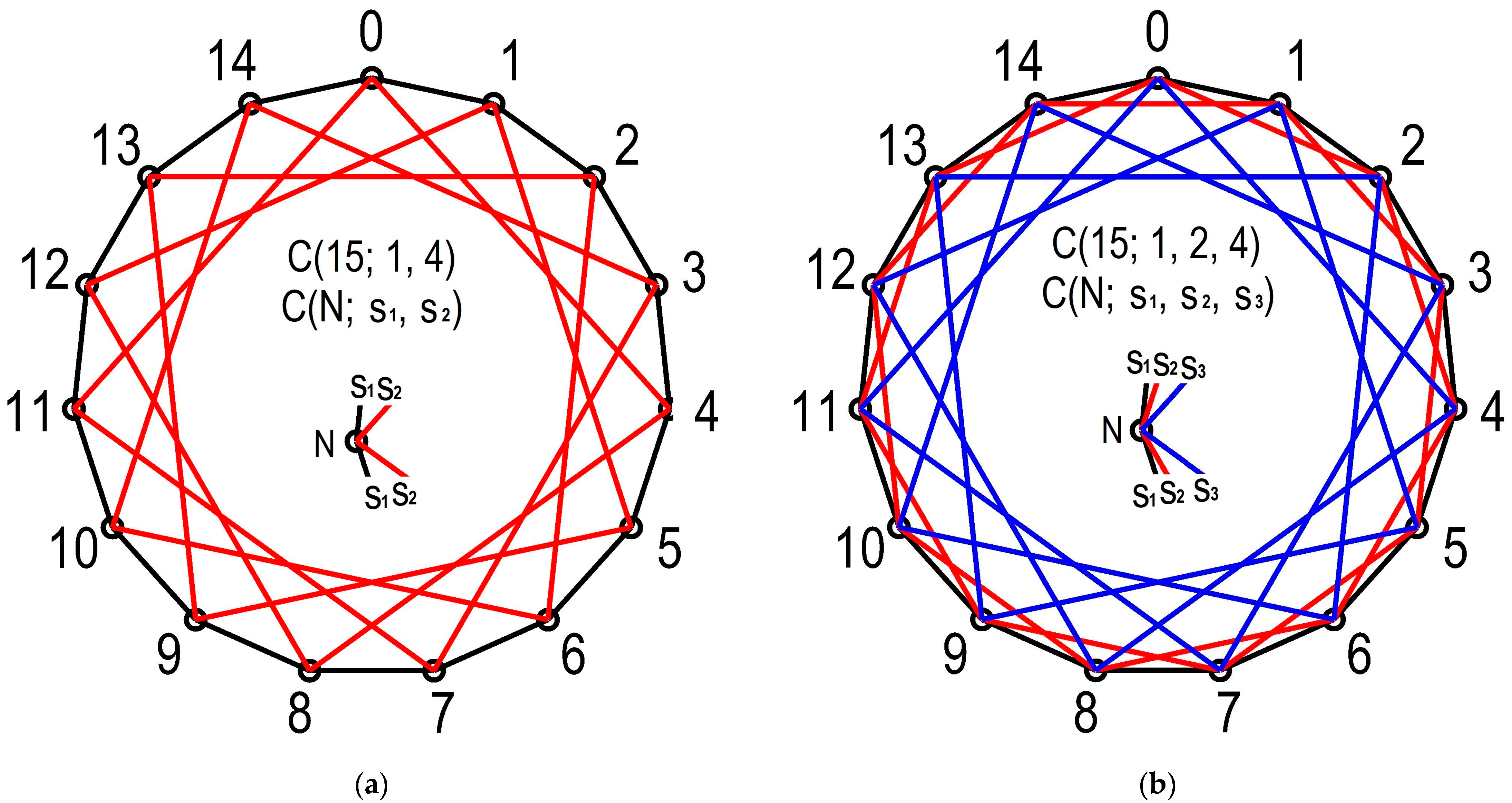
Considering Features of Circulant Graphs to Reduce the Number of Variants in an Exhaustive Search Algorithm
3. Software Description
3.1. Software Architecture
- Library for the synthesis of optimal circulant topologies.
- Console application for interacting with the library.
- Console application for evaluating synthesis time and validating results.
3.2. Description of the Features of the Software
- nodesDescription describes the number of nodes within which the topologies will be synthesized; this parameter can be specified as a range or can be listed with a comma.
- dimension sets the number of generators which will take part in the compilation of a parametric description of circulant topologies and is used for synthesis.
- threadCount is responsible for the number of threads allocated for synthesis; the application dynamically monitors the commands passed to it by the user or the program that launched the application (for example, the application can be paused or stopped); so, at least two threads are allocated for working: one for the commands, the other for synthesis. Other parameters which are responsible for the format of the output data include: logging of the synthesis process, saving intermediate results of the synthesis with signatures of non-optimal topologies, user identifier, and storing the information.
- NodesDescription is responsible for checking the progress save file; if, in the current task, the value of the nodesDescription parameter from the first file (its structure is described above) completely coincides with NodesDescription, the synthesis progress will be restored from the breakpoint; otherwise, this file will be ignored and overwritten when the application continues to work.
- NotCheckedConfig contains the vector of generators of the circulant topology from which it will be necessary to begin the search.
- GoodConfigs are the best topologies found at the time when the program has been stopped; with the continuation of the work, these topologies will be considered optimal by default.
- Dimension is determined by a given number of generators of the circulant topology.
- Diameter is the minimum diameter of the topology at the time when the program has been stopped.
- AverageDiameter is the minimum MPL at the time when the program has stopped working.
- CurrentNodesCount is the current number of nodes from which the task is to be continued.
4. Illustrative Examples
4.1. Evaluation of the Results
4.2. Comparison with Other Solutions
4.3. Validation of the Topologies Generated
4.4. Dataset
5. Use Case
5.1. New Topologies Search Speedup
5.2. The Analysis of Routing Algorithms for Circulant Topologies
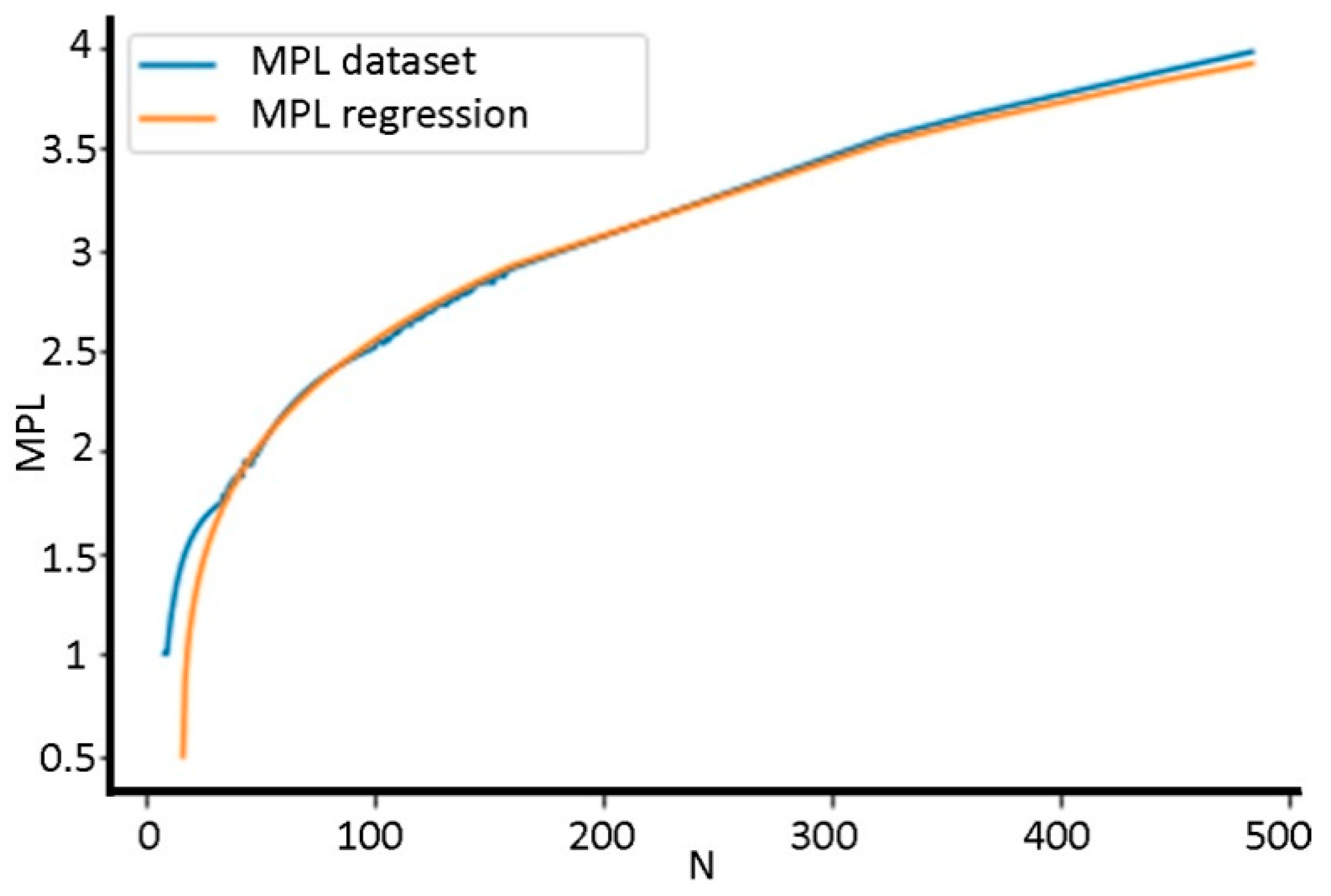
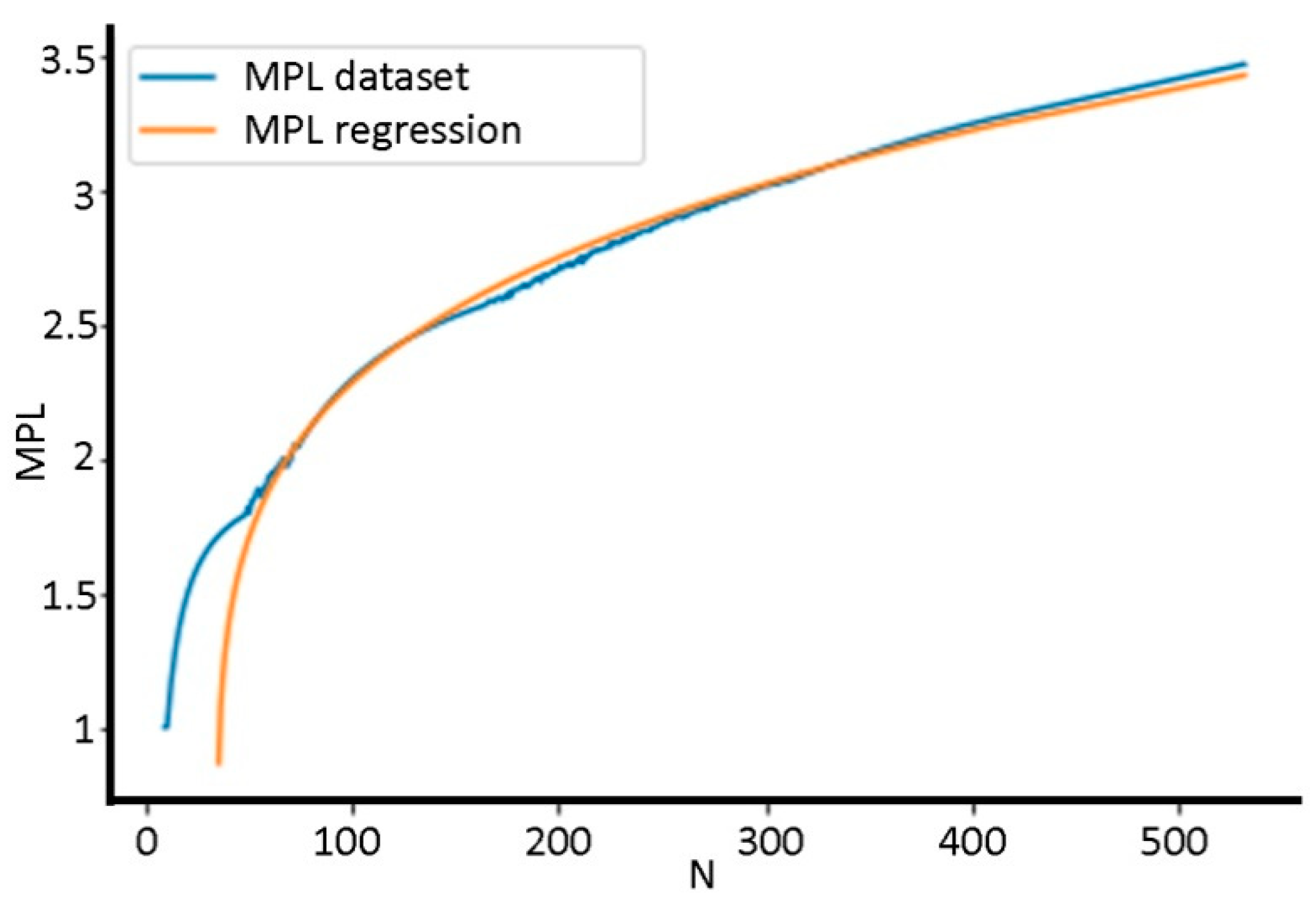
5.3. Regression Analysis
6. Conclusions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Lu, R. Fast Methods for Designing Circulant Network Topology with High Connectivity and Survivability. J. Cloud Comput. 2016, 5, 5. [Google Scholar] [CrossRef]
- Benmessaoud Gabis, A.; Koudil, M. NoC Routing Protocols—Objective-Based Classification. J. Syst. Archit. 2016, 66–67, 14–32. [Google Scholar] [CrossRef]
- Baby, N.; Mathew, S.; Abraham, S.; Ravindranath, S.; Sanju, V. Network on Chip Simulator: Design, Implementation and Comparison of Mesh, Torus and RiCoBiT Topologies. In Proceedings of the 2016 2nd International Conference on Next Generation Computing Technologies, NGCT 2016, Dehradun, India, 14–16 October 2016; pp. 46–50. [Google Scholar] [CrossRef]
- Lau, F.C.M.; Chen, G. Optimal Layouts of Midimew Networks. IEEE Trans. Parallel Distrib. Syst. 1996, 7, 954–961. [Google Scholar] [CrossRef]
- Huang, X.; Ramos, A.F.; Deng, Y. Optimal circulant graphs as low-latency network topologies. J. Supercomput. 2022, 78, 13491–13510. [Google Scholar] [CrossRef]
- Deng, Y.; Guo, M.; Ramos, A.F.; Huang, X.; Xu, Z.; Liu, W. Optimal low-latency network topologies for cluster performance enhancement. J. Supercomput. 2020, 76, 9558–9584. [Google Scholar] [CrossRef]
- Puente, V.; Izu, C.; Beivide, R.; Gregorio, J.A.; Vallejo, F.; Prellezo, J.M. The Adaptive Bubble Router. J. Parallel Distrib. Comput. 2001, 61, 1180–1208. [Google Scholar] [CrossRef]
- Yang, Y.; Funahashi, A.; Jouraku, A.; Nishi, H.; Amano, H.; Sueyoshi, T. Recursive Diagonal Torus: An Interconnection Network for Massively Parallel Computers. IEEE Trans. Parallel Distrib. Syst. 2001, 12, 701–715. [Google Scholar] [CrossRef]
- Beivide, R.; Martínez, C.; Izu, C.; Gutierrez, J.; Gregorio, J.Á.; Miguel-Alonso, J. Chordal Topologies for Interconnection Networks. In High Performance Computing, Proceedings of the 5th International Symposium, ISHPC 2003, Tokyo, Japan, 20–22 October 2003; Springer: Berlin, Germany, 2003; Volume 2858. [Google Scholar] [CrossRef]
- Atajan, T.; Otsuka, N.; Yong, X. Counting the Number of Spanning Trees in a Class of Double Fixed-Step Loop Networks. Appl. Math. Lett. 2010, 23, 291–298. [Google Scholar] [CrossRef]
- Liestman, A.L.; Opatrny, J.; Zaragozá, M. Network Properties of Double and Triple Fixed Step Graphs. Int. J. Found. Comput. Sci. 1998, 09, 57–76. [Google Scholar] [CrossRef]
- Attrah, N.H.; Abdul-Majeed, G.H.; Abdullah, M.Z. Implementation of Chordal Ring Network Topology to Enhance the Performance of Wireless Broadband Network. EUREKA. Phys. Eng. 2021, 2021, 11–18. [Google Scholar] [CrossRef]
- Bulut, A.; Hacioglu, I. Asymptotic Energy of Connected Cubic Circulant Graphs. AKCE Int. J. Graphs Comb. 2021, 18, 25–28. [Google Scholar] [CrossRef]
- Azeem, M.; Imran, M.; Nadeem, M. Sharp Bounds on Partition Dimension of Hexagonal Möbius Ladder. J. King Saud Univ.—Sci. 2022, 34, 101779. [Google Scholar] [CrossRef]
- Newman, M.E.J. The Structure and Function of Complex Networks. SIAM Rev. 2003, 45, 167–256. [Google Scholar] [CrossRef]
- Chen, B.; Xiao, W.; Parhami, B. Diameter Formulas for a Class of Undirected Double-Loop Networks. J. Interconnect. Networks 2005, 6, 1–15. [Google Scholar] [CrossRef]
- Zerovnik, J.; Pisanski, T. Computing the Diameter in Multiple-Loop Networks. J. Algorithms 1993, 14, 226–243. [Google Scholar] [CrossRef]
- Loudiki, L.; Kchikech, M.; Essaky, E.H. Diameter Formulas for a Class of Undirected Multi-Loop Networks. arXiv 2022. [Google Scholar] [CrossRef]
- Monakhova, E.A. A Survey on Undirected Circulant Graphs. Discret. Math. Algorithms Appl. 2012, 4, 1250002. [Google Scholar] [CrossRef]
- Romanov, A.Y.; Romanova, I.I.; Glukhikh, A.Y. Development of a Universal Adaptive Fast Algorithm for the Synthesis of Circulant Topologies for Networks-on-Chip Implementations. In Proceedings of the 2018 IEEE 38th International Conference on Electronics and Nanotechnology (ELNANO), Kyiv, Ukraine, 24–26 April 2018; IEEE: New York, NY, USA, 2018; pp. 110–115. [Google Scholar] [CrossRef]
- Herrada, E.; Balcazar, J.L.; Arruabarrena, A. Optimal distance networks of low degree for parallel computers. IEEE Trans. Comput. 1991, 40, 1109–1124. [Google Scholar] [CrossRef]
- Park, J.-H.; Chwa, K.-Y. Recursive Circulant: A New Topology for Multicomputer Networks. In Proceedings of the International Symposium on Parallel Architectures, Algorithms and Networks (ISPAN), Kanazawa, Japan, 14–16 December 1994; IEEE Computer Society Press: New York, NY, USA, 1994; pp. 73–80. [Google Scholar] [CrossRef]
- Cheng, D.-W.; Yao, K.-H.; Hsieh, S.-Y. Constructing Independent Spanning Trees on Generalized Recursive Circulant Graphs. IEEE Access 2021, 9, 74028–74037. [Google Scholar] [CrossRef]
- Stojmenovic, I. Multiplicative circulant networks. Topological properties and communication algorithms. Discr. Appl. Math. 1997, 77, 281–305. [Google Scholar] [CrossRef]
- Lewis, R.R. Analysis and Construction of Extremal Circulant and Other Abelian Cayley Graphs. The Open University: Hong Kong, China, 2021. [Google Scholar] [CrossRef]
- Hu, W.; Fey, M.; Zitnik, M.; Dong, Y.; Ren, H.; Liu, B.; Catasta, M.; Leskovec, J. Open Graph Benchmark: Datasets for Machine Learning on Graphs. Adv. Neural Inf. Process Syst. 2020, 33, 22118–22133. [Google Scholar] [CrossRef]
- Manevich, R.; Polishuk, L.; Cidon, I.; Kolodny, A. Designing Single-Cycle Long Links in Hierarchical NoCs. Microprocess. Microsyst. 2014, 38, 814–825. [Google Scholar] [CrossRef]
- Ogras, U.Y.; Marculescu, R.; Lee, H.G.; Chang, N. Communication Architecture Optimization: Making the Shortest Path Shorter in Regular Networks-on-Chip. In Proceedings of the Design, Automation and Test in Europe, Munich, Germany, 6–10 March 2006. [Google Scholar] [CrossRef]
- Elspas, B.; Turner, J. Graphs with Circulant Adjacency Matrices. J. Comb. Theory 1970, 9, 3. [Google Scholar] [CrossRef]
- Saldaña, M.; Shannon, L.; Chow, P. The Routability of Multiprocessor Network Topologies in FPGAs. In Proceedings of the Internation Symposium on Field Programmable Gate Arrays—FPGA’06, Monterey, CA, USA, 22–24 February 2006; ACM Press: New York, NY, USA, 2006; p. 232. [Google Scholar] [CrossRef]
- Loudiki, L.; Kchikech, M.; Essaky, E.H. A New Approach for Computing the Distance and the Diameter in Circulant Graphs. arXiv 2022. [Google Scholar] [CrossRef]
- Dijkstra, E.W. A Note on Two Problems in Connexion with Graphs. Numer. Math. 1959, 1, 269–271. [Google Scholar] [CrossRef]
- Hart, P.E.; Nilsson, N.J.; Raphael, B. A Formal Basis for the Heuristic Determination of Minimum Cost Paths. IEEE Trans. Syst. Sci. Cybern. 1968, 4, 100–107. [Google Scholar] [CrossRef]
- Abbott, S.; Bottcher, A.; Grudsky, S.M. Toeplitz Matrices, Asymptotic Linear Algebra and Functional Analysis. Math. Gaz. 2000, 84, 572. [Google Scholar] [CrossRef]
- Boesch, F.; Tindell, R. Circulants and Their Connectivities. J. Graph Theory 1984, 8, 487–499. [Google Scholar] [CrossRef]
- Optimal Circulant Topologies Dataset. Available online: https://doi.org/10.5281/zenodo.7265637 (accessed on 3 March 2023).
- Tamimi, A.A. Comparison Studies for Different Shortest Path Algorithms. Int. J. Comput. Technol. 2015, 14, 5979–5986. [Google Scholar] [CrossRef]
- Romanov, A.Y. Development of Routing Algorithms in Networks-on-Chip Based on Ring Circulant Topologies. Heliyon 2019, 5, e01516. [Google Scholar] [CrossRef]
- Monakhova, E.A.; Monakhov, O.G.; Mukhoed, E.V. Genetic Construction of Optimal Circulant Network Designs. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin, Germany, 1999; Volume 1596, pp. 215–233. [Google Scholar] [CrossRef]
- Robic, B. Optimal Routing in 2-Jump Circulant Networks; Univ. Cambridge: Cambridge, UK, 1996. [Google Scholar] [CrossRef]
- Chen, B.-X.; Meng, J.-X.; Xiao, W.-J. A constant time optimal routing algorithm for undirected double-loop networks. Lect. Notes Comp. Sci. 2005, 3794, 308–316. [Google Scholar] [CrossRef]
- Gomez, D.; Gutierrez, J.; Ibeas, A.; Martinez, C.; Beivide, R. On Finding a Shortest Path in Circulant Graphs with Two Jumps. Lect. Notes Comp. Sci. 2005, 3595, 777–786. [Google Scholar] [CrossRef]
- Dobravec, T.; Zerovnik, J.; Robic, B. An Optimal Message Routing Algorithm for Circulant Networks. J. Syst. Arch. 2006, 52, 298–306. [Google Scholar] [CrossRef]
- Perez-Roses, H.; Bras-Amoros, M.; Serradilla-Merinero, J.M. Greedy Routing in Circulant Networks. Graphs Comb. 2022, 8, 86. [Google Scholar] [CrossRef]
- Das, S.; Karfa, S.; Biswas, S. Formal Modeling of Network-on-Chip Using CFSM and its Application in Detecting Deadlock. IEEE Trans. Very Large Scale Integr. Syst. 2020, 28, 1016–1029. [Google Scholar] [CrossRef]
- Nadeem, M.; Imran, M.; Siddiqui, H.M.; Azeem, M. Fault Tolerance Designs of Interconnection Networks. Peer-to-Peer Netw. Appl. 2023, 1, 1–10. [Google Scholar] [CrossRef]
- Romanov, A.; Myachin, N.; Sukhov, A. Fault-Tolerant Routing in Networks-on-Chip Using Self-Organizing Routing Algorithms. In Proceedings of the IECON 2021—47th Annual Conference of the IEEE Industrial Electronics Society, Toronto, ON, Canada, 13–16 October 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Montgomery, D.C.; Peck, E.A.; Vining, G.G. Introduction to Linear Regression Analysis, 6th ed.; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2021. [Google Scholar]
- Freedman, D. Statistical Models: Theory and Practice, 2nd ed.; Cambridge University Press: Cambridge, UK, 2009. [Google Scholar] [CrossRef]





| Notation | Description |
|---|---|
| NoC | Network-on-Chip |
| Circulant graph signature | |
| Number of nodes | |
| Circulant graph dimension | |
| , | Circulant graph generator |
| MPL | Mean Path Length |
| GCG | Greedy Circulants Generator |
| MAE | Mean Absolute Error |
| PPMCC | Pearson Product-Moment Correlation Coefficient |
| Number of Nodes | Number of Iterations | Estimated Time (Dijkstra’s Algorithm) | Estimated Time (GCG) | Acceleration |
|---|---|---|---|---|
| 100 | 1224 | 2 ± 0.5 s | 2 ± 0.5 s | 100% |
| 500 | 31,124 | 1 min 19 ± 10 s | 1 min 8 ± 15 s | 116% |
| 750 | 70,124 | 3 min 45 ± 30 s | 2 min 49 ± 20 s | 133% |
| 1000 | 124,749 | 8 min 39 ± 60 s | 5 min 51 ± 30 s | 148% |
| 2500 | 780,624 | 3 h 15 ± 10 min | 1 h 16 ± 20 min | 203% |
| 5000 | 3,123,749 | 56 ± 3 h | 18 ± 2 h | 312% |
| 10,000 | 12,497,499 | 39 ± 3 days | 11 ± 1 days | 358% |
| 20,000 | 49,994,999 | 1 year 7 ± 1 month | 6 ± 1 month | 340% |
| 50,000 | 312,487,499 | 65 ± 3 years | 18 ± 1 year | 345% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Romanov, A. The Dataset for Optimal Circulant Topologies. Big Data Cogn. Comput. 2023, 7, 80. https://doi.org/10.3390/bdcc7020080
Romanov A. The Dataset for Optimal Circulant Topologies. Big Data and Cognitive Computing. 2023; 7(2):80. https://doi.org/10.3390/bdcc7020080
Chicago/Turabian StyleRomanov, Aleksandr. 2023. "The Dataset for Optimal Circulant Topologies" Big Data and Cognitive Computing 7, no. 2: 80. https://doi.org/10.3390/bdcc7020080
APA StyleRomanov, A. (2023). The Dataset for Optimal Circulant Topologies. Big Data and Cognitive Computing, 7(2), 80. https://doi.org/10.3390/bdcc7020080








