Security and Privacy Threats and Requirements for the Centralized Contact Tracing System in Korea
Abstract
1. Introduction
2. Related Works
2.1. Case Study of Contact Tracing for COVID-19 in Korea
2.2. Case Study on COVID-19 Contact Tracing in Taiwan
2.3. Analysis and Comparison of Privacy in Contact Tracing Apps
2.4. Case Study of COVID-19 Contact Tracing Mobile Application in Singapore
2.5. Differences and Contributions of This Paper
3. Data Processing Model for a Centralized Contact Tracing System
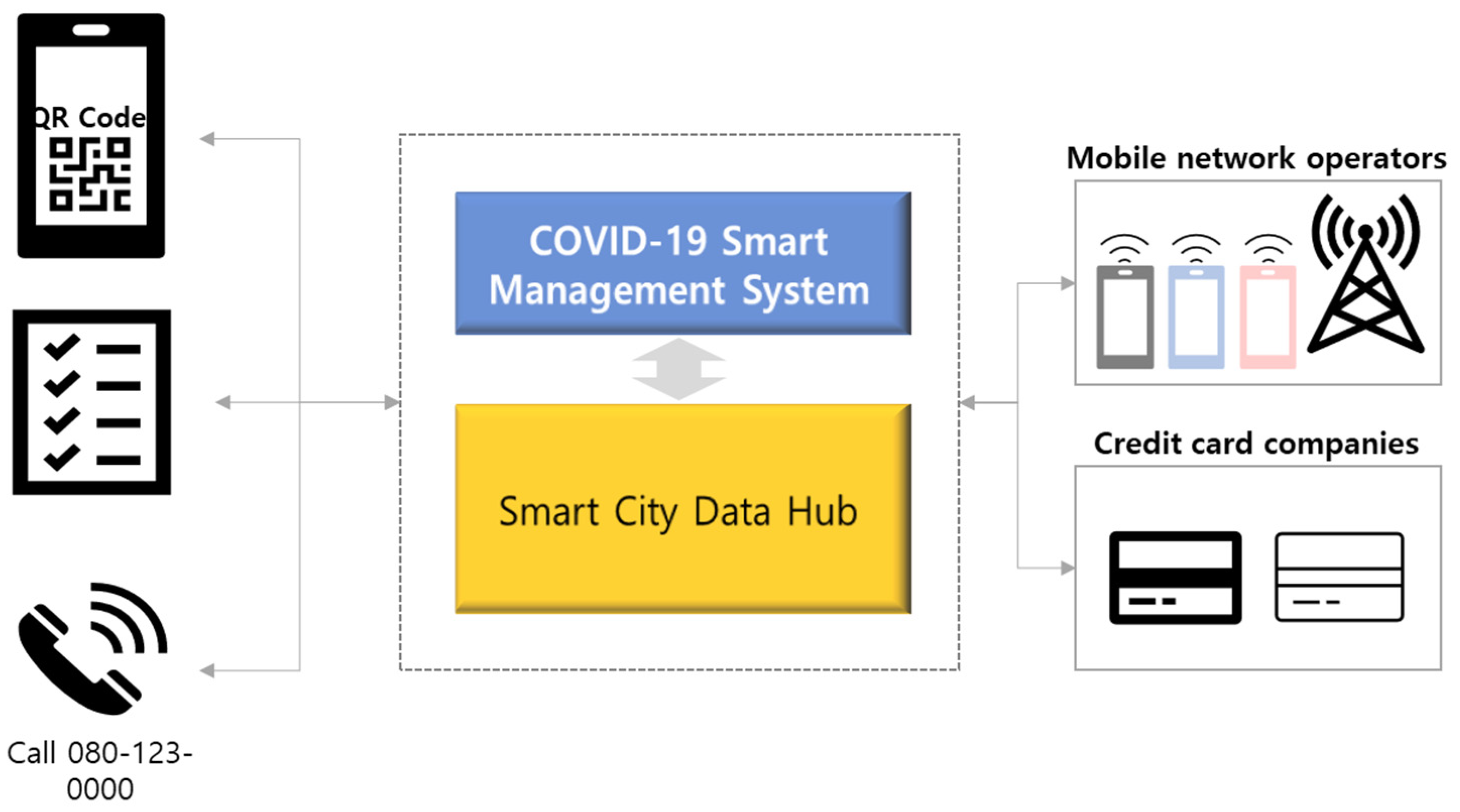
3.1. Korea’s COVID-19 Smart Management System (SMS) [22]
- QR-code-based electronic access list used when entering specific facilities;
- Handwritten list;
- Collected mobile phone numbers recorded by people calling with phone numbers issued by local governments when entering specific facilities.
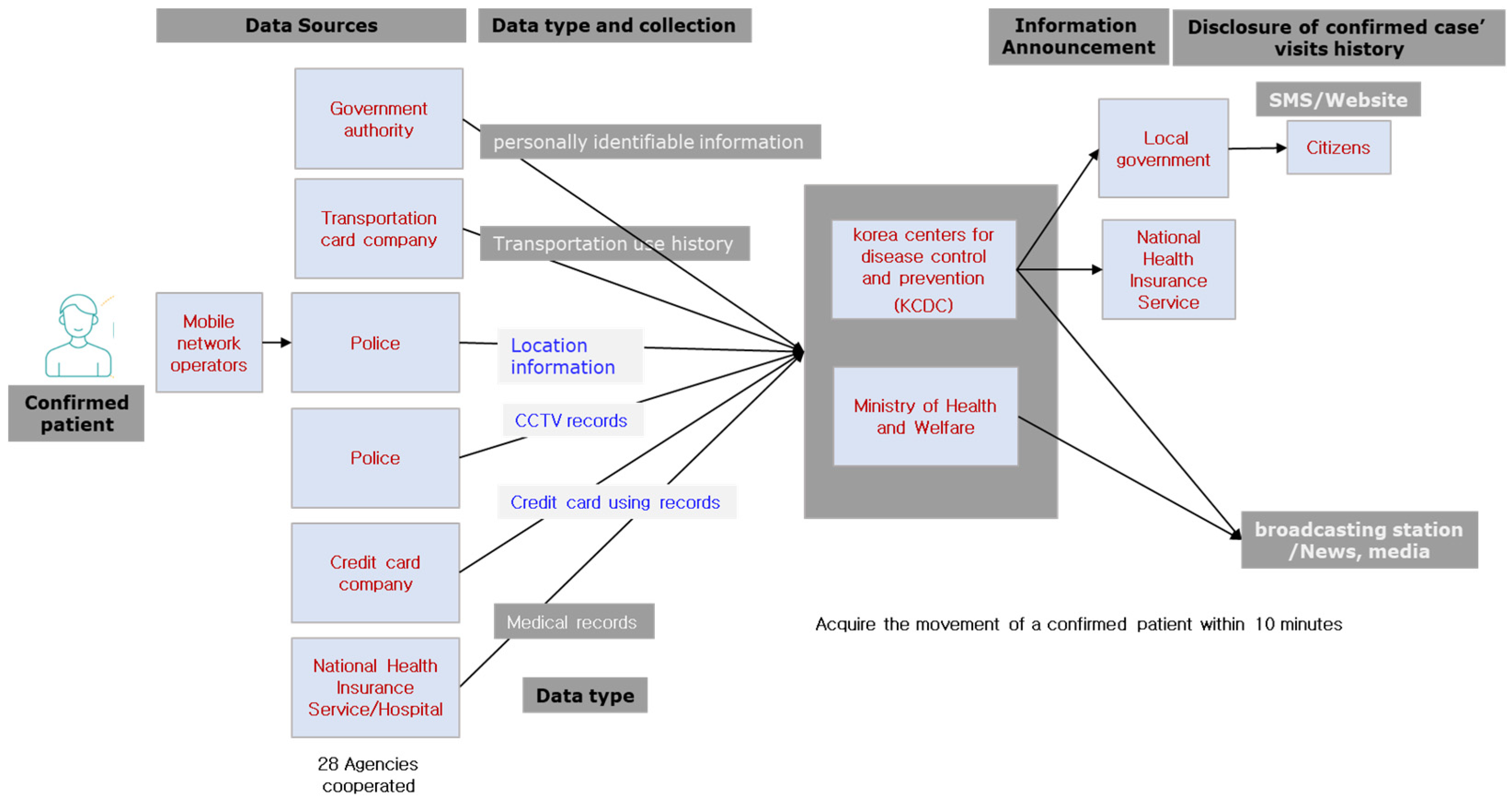
3.2. Data Processing Model
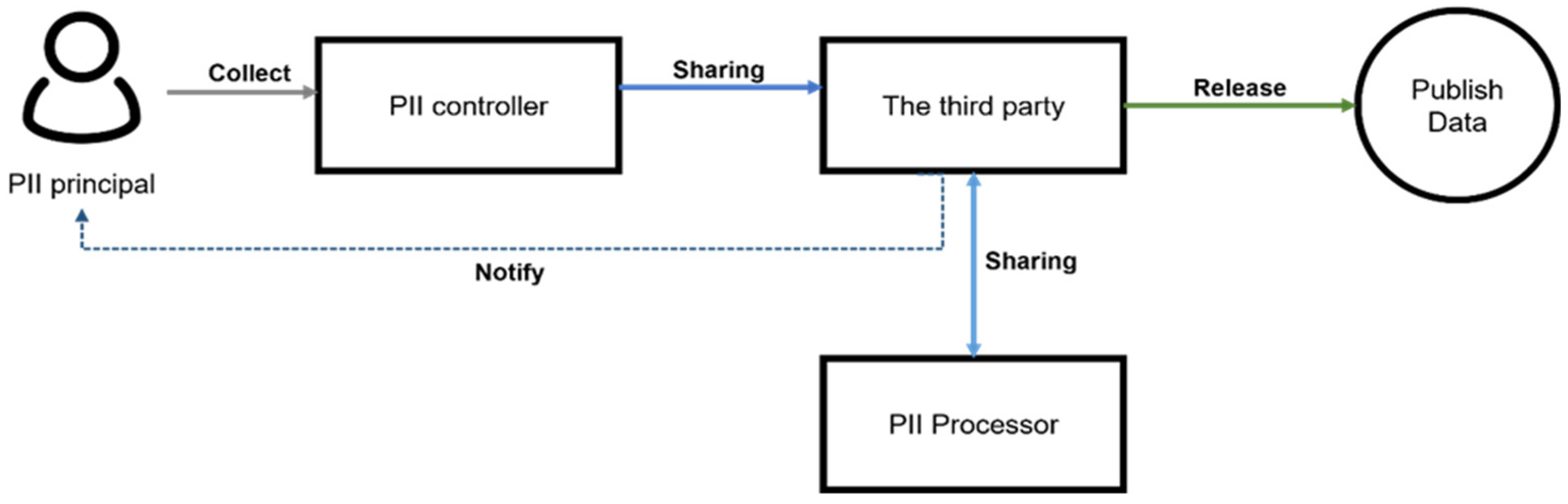
- PII: PII is data such as the phone number or credit card number of a data subject, the place where a credit card is used, and the location of the mobile base station.
- PII principal: A stakeholder who provides PII to classify whether they are a contact of an epidemic patient or is diagnosed as positive for an infectious disease. PII may include epidemic information and other information that could help to identify a recent contact including geological information. A PII principal could receive notification of exposure to an epidemic patient from the third party.
- PII controller: A stakeholder who collects PII and shares it to a third party. The collected information can be directly related to infection information such as diagnosis or other information to track a patient/contact path to identify other contacts [26], though a PII controller may need additional consent from a PII principal to use such data in this system. Medical institutions or private service providers related to geological/financial services can be PII controllers in this model.
- Third Party: A stakeholder receiving information from the PII controllers, who takes measures to prevent and manage epidemics and has an obligation to disclose information to share the status of outbreak and spread. Organizations could be a third party such as the Korea Centers for Disease Control and Prevention (KCDC), which oversees all health data processing, as well as local governments that carry out quarantine measures for infected persons/contacts [24].
- PII Processor: A stakeholder who processes data on behalf of a third party and can process data analysis, integration, and de-identification on behalf of a third party. If a third party operates a health information system by their own, a PII processor could help to establish or maintain such information systems [24]. PII processors include data service providers [24].
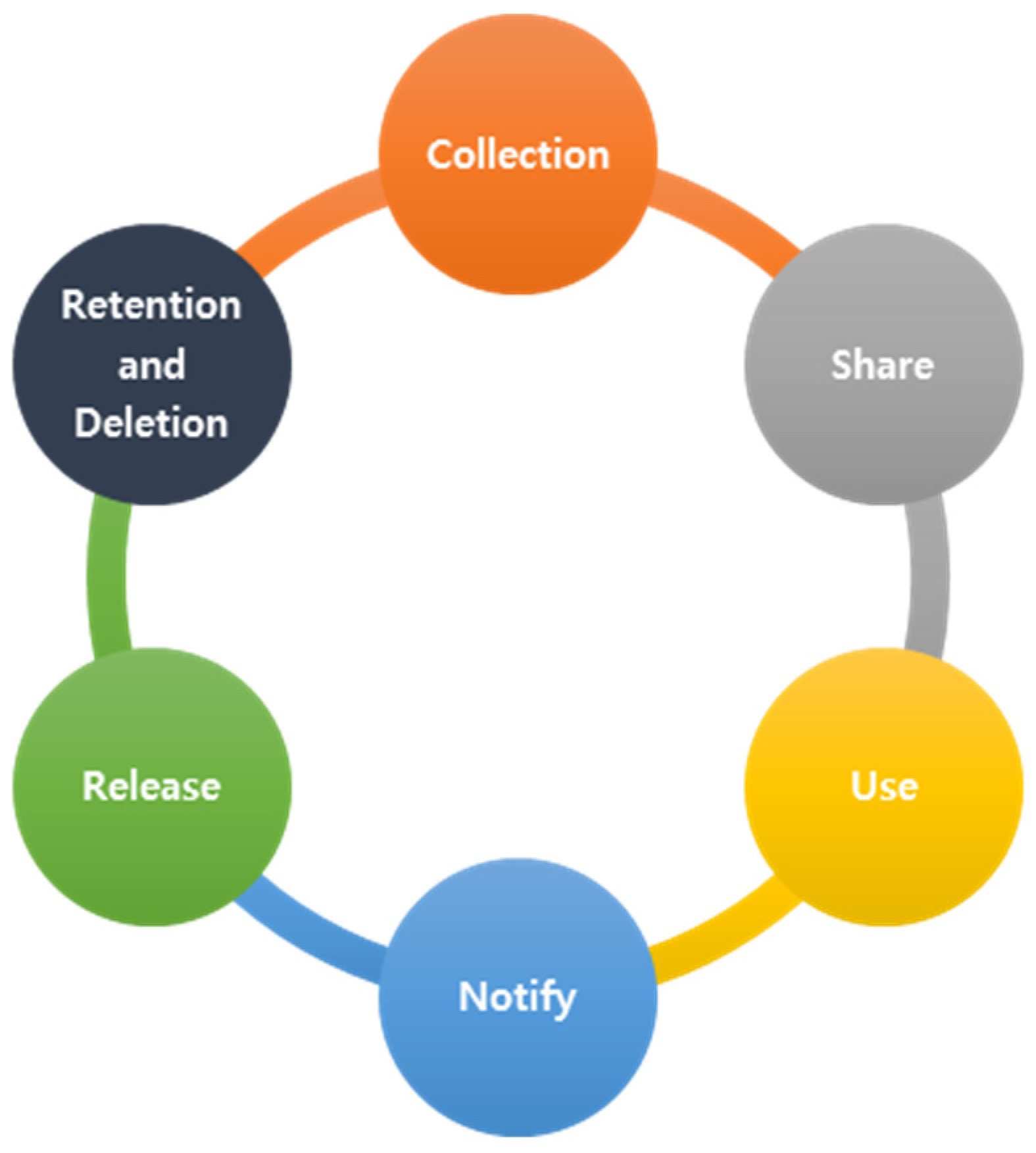
3.3. Data Processing Life Cycle
- Data Collection
- Data Sharing
- Data Notification
- Data Release
- Data Retention and Deletion
4. Security and Privacy Threats and Requirements
4.1. Security Threats and Requirements in ITU-T X.1121
- Additional threat: Lost/stolen terminal
- Corresponding requirement: If a terminal is lost, people will not be able to receive the information related to it when they become a close contact. Therefore, various notification methods, such as e-mail notification, etc., for the recipient, that is, the closer contact, should be improved.
4.2. Security and Privacy Threats for the Contact Tracing System in Korea
- ST1.
- Compromise of data confidentiality: threats to data being disclosed or available to the unintended entity;
- ST2.
- Compromise of data integrity: threats to data being changed or destructed improperly;
- ST3.
- Compromise of data availability: threats to data being accessed or used by unauthorized third parties;
- ST4.
- Data recovery due to insufficient data deletion: threats to data being recovered from data storage, due to insufficient data deletion;
- ST5.
- Degradation in data quality when processing: threats of data being corrupted or redundant due to processing on data such as de-identification and a failure to identify past or present physical proximity;
- ST6.
- Malicious activities by internal attackers: threats of data being maliciously leaked by internal attackers from inside;
- ST7.
- Use of unsecured tunneling protocol: protocol attacks caused by using versions to be vulnerable to communication protocols;
- ST8.
- Lost/stolen terminal: threats to lost or stolen terminal such as mobiles;
- PT1.
- Data use for purposes other than infectious disease responses: threats to data being used for purposes other than the prevention, management, and treatment of infectious diseases;
- PT2.
- Unauthorized data transfer to third party: threats of data being acquired or provided to unauthorized third party by false or other fraudulent means or methods;
- PT3.
- Insufficient legal and regulation grounds for PII processing: threats of insufficient legal grounds for collection of PII;
- PT4.
- Excessive data processing beyond the intended purposes: threats of data being collected unreasonably because of too many attributes for the original purpose;
- PT5.
- Data collection without the consent of a PII principal: threats in a process of collection when prior consent of a PII principal is not being obtained;
- PT6.
- De-identification risk of re-identified data: the potential that some supposedly anonymous or pseudonymous data sets could be being de-anonymized to recover the identities of users [32];
- PT7.
- Identification of a specific data from publicly announced data: threats to leak specific PII by using and combining publicly announced information or data such as the movement routes of people with infectious diseases;
- PT8.
- Leakage of PII on a handwritten list: threat to leakage of a specific PII being written on a handwritten list when an individual enters various facilities.
4.3. Mapping Security and Privacy Threats to LINDDUN and STRIDE Threat Models
- L (Linkability): An adversary is able to link two items of interest without knowing the identity of the data subjects involved [33];
- I (Identifiability): An adversary is able to identify a data subject from a set of data subjects through an item of interest [33];
- N (Non-repudiation): The data subject is unable to deny a claim [33];
- D (Detectability): An adversary is able to distinguish whether an item of interest about a data subject exists or not, regardless of being able to read the contents itself [33];
- D (information Disclosure): An adversary is able to learn the content of an item of interest about a data subject [33];
- U (content Unawareness): The data subject is unaware of the collection, processing, storage, or sharing activities and the corresponding purposes of their personal data [33];
- N (policy and consent Non-compliance): The processing, storage, or handling of personal data is not compliant with legislation, regulation, and/or policy [33].
- S (Spoofing): Spoofing or “identity spoofing” is a scenario in which a user X pretends to be a user Y by changing their identity or data and, thus, gains illegal access to data [35];
- T (Tampering): Tampering refers to the change of data by an illegal person who is not authorized to modify them [35];
- R (Repudiation): Repudiation relies on the fact that a security system must always be able to trace the entity responsible for any illegitimate modification and illegal access of resource or account [35];
- I (Information disclosure): Information disclosure assists an attacker or malicious user in accessing confidential information that they are not permitted to view [35];
- D (Denial of service): A denial-of-service (DoS) attack is an attempt to disturb a resource, network, or system in such a way that an intended and valid user would not be able to use it [35];
- E (Elevation of privilege): Elevation of privilege is the category of attacks in which an intruder gains authorization to access more than what has been granted originally [35].
4.4. Security and Privacy Requirements for the Contact Tracing System in Korea
- SR1. Processing based on legal and regulation grounds: There are seven types of PII data to collect (location data, personally identifiable information, medical and prescription records, immigration records, credit/debit and prepaid card transaction data, public transportation use records, and CCTV images); however, only necessary information should be collected, and the consent of the data subject should be checked. In this case, if it is required or permitted by law, the above may not be considered. When providing to a third party, it is necessary to identify whether there is any personal information to be provided and to review what kind of disadvantage there is to the information subject if the information subject does not agree.
- SR2. Minimizing data collection: Obtaining the consent of the data subject is of the highest priority. PII should be collected and used only within the scope of the agreed purpose (conclusion and implementation), and multiple pieces of PII with similar characteristics should not be collected for the same purpose. Information automatically generated in the process of using a website, such as cookies, should be collected minimally.
- SR3. Ensuring individual rights of PII: When the PII controller collects PII with the consent of the data subject, the following needs to be ensured: (1) the contents of the consent, (2) the fact that the data subject has the right to refuse consent, and (3) the contents of the disadvantage if there is a disadvantage due to the refusal of consent should be specified specifically. In addition, the consent of the data subject is premised on a substantive right of choice. Even if the information subject does not agree to the optional items, a service provider cannot refuse to provide the service [35].
- SR4. Strong access control: Data access rights for each component of the PII processing model should be set, and a system should be established so that the data can be accessed according to the level of authority.
- SR5. Use of a strong encryption mechanism: Access control and restriction on PII, encryption technology, or equivalent measures that can safely store and transmit PII should be applied.
- SR6. Providing data integrity: In the process of sending PII (data sharing), passwords, bio information, and unique identification information must be encrypted before transmission. They must be encrypted and stored. The encryption technique used when data transmission is transmitted must be using a symmetric key encryption algorithm or a public key encryption algorithm; when data are stored in the system, they must be stored using a one-way encryption algorithm such as a hash function.
- SR7. Data backup for availability: Due to the characteristics of PII, media such as a tape or external USB are judged to be inappropriate, so it is considered appropriate to store data on media such as a disk or in the cloud. Even when backing up PII, it is necessary to store encrypted data rather than plain text; in the case of data storage, data should be located on the internal network rather than on an external network or DMZ.
- SR8. Use of a complete data-deletion mechanism: After the PII controller achieves the purpose for the user’s PII, when the retention and use period ends, a PII controller should destroy the PII without delay [22,36]. When PII is destroyed, it must be destroyed in a way that cannot be restored or reproduced.
- SR9. Data processing only for the intended purposes: In the case of establishing an internal management plan to block the use of data for anything other than the intended purpose and requesting an external party to process PII, the purpose for which the PII processor can process PII must be determined in advance.
- SR10. Prevention from inside attacks: Since it is impossible to apply security policies to internal attackers with a firewall, security procedures should be clarified and checked regarding whether they are being continuously implemented.
- SR11. Use of de-identification techniques: The appropriateness of data de-identification measures should be evaluated to ensure that necessary identification information is used after de-identification measures. Measures to monitor the possibility of re-identification of de-identified information should be taken, and, when outsourcing the processing of pseudonymous information, the contract should include notification of the prohibition of re-identification, restrictions on re-supply/re-entrustment, and notification of the risk of re-identification.
- SR12. Use of a strong end-to-end encryption protocol with authentication such as SSH (Secure Shell): The latest version of the secure and secure tunneling protocol should be made sure to provide encrypted communication sessions. SR12 can counter ST2 and ST7 threats.
- SR13. Use of data anonymization: All information collected for tracking is converted into anonymous information and announced. SR13 can counter PT7 threats.
- SR14. Providing various notification methods: If a terminal is lost, people will not be able to receive the information related to it when they become a close contact. Therefore, various notification methods, such as e-mail notification, etc., for the recipient, that is, the closer contact, should be improved.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Shahroz, M.; Ahmad, F.; Younis, M.S.; Ahmad, N.; Kamel Boulos, M.N.; Vinuesa, R.; Qadir, J. COVID-19 digital contact tracing applications and techniques: A review post initial deployments. Transp. Eng. 2021, 5, 100072. [Google Scholar] [CrossRef]
- World Health Organization. Available online: https://innov.afro.who.int/global-innovation/robert-robust-and-privacy-preserving-proximity-tracing-protocol-1827 (accessed on 25 September 2022).
- Github. Available online: https://github.com/DP-3T/documents (accessed on 25 September 2022).
- Hogan, K.; Macedo., B.; Macha., V.; Barman., A.; Jiang., X. Contact Tracing Apps: Lessons Learned on Privacy, Autonomy, and the Need for Detailed and Thoughtful Implementation. JMIR Med. Inform. 2021, 9, 27449. [Google Scholar] [CrossRef] [PubMed]
- Boutet., A.; Castelluccia., C.; Cunche., M.; Lauradou., C.; Roca., V.; Baud., A.; Raverdy., P. Desire: Leveraging the Best of Centralized and Decentralized Contact Tracing Systems. Digit. Threat. Res. Pract. 2022, 3, 1–20. [Google Scholar] [CrossRef]
- Giuseppe, G.; Tim, H.; Davy, P.; Wouter, J.; Aysajan, A.; Mustafa, A.M. PIVOT: PrIVate and effective cOntact Tracing. IEEE Internet Things J. 2021, 9, 22466–22489. [Google Scholar] [CrossRef]
- Johannes, M.; Kretzschmar, M. Contact tracing—Old models and new challenges. Infect. Dis. Model. 2021, 6, 222–231. [Google Scholar] [CrossRef]
- Park, S.; Choi, G.J.; Ko, H. Information Technology–Based Tracing Strategy in Response to COVID-19 in South Korea—Privacy Controversies. JAMA Netw. Open 2020, 323, 2129–2130. [Google Scholar] [CrossRef] [PubMed]
- Jian, S.-H.; Cheng, H.-Y.; Huang, X.-T.; Liu, D.-P. Contact tracing with digital assistance in Taiwan’s COVID-19 outbreak response. Intern. J. Infect. Dis. 2020, 101, 348–352. [Google Scholar] [CrossRef] [PubMed]
- Garrett, P.M.; Wang, Y.-W.; White, J.P.; Kashima, Y.; Dennis, S.; Yang, C.-T. High acceptance of COVID-19 Tracing Technologies in Taiwan: A nationally representative survey analysis. Int. J. Environ. Res. Public Health 2022, 19, 3323. [Google Scholar] [CrossRef] [PubMed]
- Yanji, P.; Dongyue, C. Privacy Analysis and Comparison of Pandemic Contact Tracing Apps. KSII Trans. Internet Inf. Syst. 2021, 15, 4145–4162. [Google Scholar] [CrossRef]
- Cho, H.; Ippolito, D.; Yu, Y.W. Contact Tracing Mobile Apps for COVID-19: Privacy Considerations and Related Trade-offs. arXiv 2020, arXiv:2003.11511. [Google Scholar] [CrossRef]
- UK Health Security Agency. NHS COVID-19 App. 13 May 2022. Available online: https://www.gov.uk/government/collections/nhs-covid-19-app (accessed on 23 September 2022).
- Liang, F. COVID-19 and Health Code: How Digital Platforms Tackle the Pandemic in China. Soc. Media Soc. 2020, 6, 2056305120947657. [Google Scholar] [CrossRef] [PubMed]
- Bay, J.; Kek, J.; Tan, A.; Hau, C.S.; Yongquan, L.; Tan, J.; Quy, T.A. BlueTrace: A Privacy-Preserving Protocol for Community-Driven Contact Tracing across Borders; Government Technology Agency: Singapore, 2020.
- PEPP-PP. PEPP-PT Documentation. 2020. Available online: https://github.com/pepp-pt/pepp-pt-documentation (accessed on 23 September 2022).
- Troncoso, C.; Payer, M.; Hubaux, J.P.; Salathé, M.; Larus, J.; Bugnion, E.; Lueks, W.; Stadler, T.; Pyrgelis, A.; Antonioli, D.; et al. Decentralized Privacy-Preserving Proximity Tracing. arXiv 2020, arXiv:2005.12273. [Google Scholar] [CrossRef]
- Small, L.S.; John, H.; Matt, H.; Nathaniel, L. Summary of Bluetooth Contact Tracing Options. 2020. Available online: https://www.dta.mil.nz/assets/Publications/Bluetooth-Contact-Tracing-Options.pdf (accessed on 23 September 2022).
- Google. Exposure Notifications: Help Slow the Spread of COVID-19, with One Step on Your Phone. 2020. Available online: https://www.google.com/covid19/exposurenotifications/ (accessed on 23 September 2022).
- Kintvedt, M.N. COVID-19 Tracing Apps as a Legal Problem: An Investigation of the Norwegian ‘Smittestopp’ App. Oslo Law Rev. 2021, 8, 69–87. [Google Scholar] [CrossRef]
- Jhanwar, M.P.; Sarkar, S. Phyct: Privacy Preserving Hybrid Contact Tracing. IACR Cryptol. ePrint Arch. 2020, 2020, 793. [Google Scholar]
- Development Asia. COVID-19 Smart Management System (SMS) in Korea. Available online: https://events.development.asia/system/files/materials/2020/04/202004-covid-19-smart-management-system-sms-republic-korea.pdf (accessed on 25 September 2022).
- Reliable Ministry of Government legislation Korean Law Information Center. Infectious Disease Control and Prevention Act. Available online: https://www.law.go.kr/%EB%B2%95%EB%A0%B9/%EA%B0%90%EC%97%BC%EB%B3%91%EC%9D%98%EC%98%88%EB%B0%A9%EB%B0%8F%EA%B4%80%EB%A6%AC%EC%97%90%EA%B4%80%ED%95%9C%EB%B2%95%EB%A5%A0 (accessed on 25 September 2022).
- ICT Standardization Committee. TTAK.KO-12.0376:Privacy Protection Guidelines for Infectious Diseases Control and Prevention. Available online: https://committee.tta.or.kr/data/standard_view.jsp?order=t.publish_date&by=desc&nowPage=1&pk_num=TTAK.KO-12.0376&commit_code=TC5 (accessed on 25 September 2022).
- Jeon, H. Official Operation of the ‘COVID-19 Epidemiological Investigation System’ on the 26th and Identify the Movement of Confirmed Patients. 2020. Available online: https://www.news1.kr/articles/?3884765 (accessed on 24 September 2022).
- LX Spatial Information Research Institute. Available online: https://lxsiri.re.kr/frt/biz/bbs/selectBoardArticle.do?bbsId=BBSMSTR_000000000221&nttId=7323 (accessed on 27 April 2022).
- International Organization for Standardization (ISO). ISO/IEC 29100:2011; Information Technology—Security Techniques—Privacy Framework. Available online: https://www.iso.org/standard/45123.html (accessed on 25 September 2022).
- Korea Disease Control and Prevention Agency. Available online: https://www.kdca.go.kr/contents.es?mid=a20301110100 (accessed on 28 April 2022).
- Korea Policy Briefings. Available online: https://www.korea.kr/news/policyNewsView.do?newsId=148895400#sitemap-layer (accessed on 25 September 2022).
- Ministry of Land, Infrastructure and Transport (MOLIT). Available online: http://www.mohw.go.kr/react/al/sal0301vw.jsp?PAR_MENU_ID=04&MENU_ID=0403&CONT_SEQ=359845 (accessed on 25 September 2022).
- International Telecommunication Union(ITU-T). ITU-T X.1121: Framework of Security Technologies for Mobile End-To-End Data Communications. Available online: https://www.itu.int/rec/T-REC-X.1121/en (accessed on 24 September 2022).
- Google Cloud. Available online: https://cloud.google.com/blog/products/identity-security/taking-charge-of-your-data-understanding-re-identification-risk-and-quasi-identifiers-with-cloud-dlp (accessed on 1 May 2022).
- LIDDUN. Available online: https://www.linddun.org/linddun (accessed on 12 February 2022).
- Khan, S.A. A STRIDE Model based Threat Modelling using Unified and-Or Fuzzy Operator for Computer Network Security. Int. J. Comput. Netw. Technol. 2017, 5, 13–20. [Google Scholar] [CrossRef] [PubMed]
- Lee, I.; Keh., J.S. Cross-Border Transfers of Personal Data and Practical Implications. J. Korean L. 2017, 17, 33–52. [Google Scholar]
- Korea Legislation Research Institute. Personal Information Protection Act. Available online: https://elaw.klri.re.kr/eng_service/lawView.do?hseq=53044&lang=ENG (accessed on 15 July 2022).
| Contents of This Paper | This Paper | 2.1 | 2.2 | 2.3 | 2.4 |
|---|---|---|---|---|---|
| Privacy modeling of contact tracing system | ○ | ☓ | ☓ | ☓ | ☓ |
| Security and privacy threats analysis | ○ | ☓ | ☓ | ○ | ○ |
| Security and privacy requirements mapping | ○ | ☓ | ☓ | ○ | ○ |
| Contact tracing technology based method | QR code Credit card | Not mentioned | Bluetooth | Bluetooth GPS | Bluetooth |
| Comparison of a centralized and decentralized model | ☓ | ☓ | ○ | ○ | ☓ |
| Country or Authors | Examples of Contact Tracing Systems or Applications | Approach |
|---|---|---|
| Korea | Korea COVID-19 smart management system | Centralized |
| UK | NHS contact tracing app [13] | Centralized |
| China | Health Code [14] | Centralized |
| Singapore | TraceTogether (OpenTrace/BlueTrace) [12,15] | Centralized |
| EU | PEPP-PP [16] | Centralized |
| EU | DP-3T [17] | Decentralized |
| TCN Coalition | TCN [18] | Decentralized |
| Google/Apple | Google–Apple Exposure Notification application programming interface (API) [19] | Decentralized |
| Norway | Smittestopp [20] | Centralized Decentralized |
| Mahabir Prasad Jhanwar, Sumanta Sarkar | PHyCT (Privacy preserving Hybrid Contact Tracing) [21] | Hybrid |
| Giuseppe Garofalo, Tim Van hamme, et al. | PIVOT (PrIVate and effective cOntact Tracing) [6] | Hybrid |
| Claude Castelluccia, Nataliia Bielova, et al. | DESIRE (a novel exposure notification system that leverages the best of centralized and decentralized systems) [5] | Hybrid |
| Threat | Eavesdropping | Communication Jamming | Shoulder Surfing | Lost/Stolen Terminal | Unprepared Shutdown | Misreading/ Input Error | |
|---|---|---|---|---|---|---|---|
| Requirement | |||||||
| Identity management | X | ||||||
| Communication data confidentiality | X | ||||||
| Stored data confidentiality | X | ||||||
| Communication data integrity | |||||||
| Stored data integrity | X | ||||||
| Entity authentication | X | ||||||
| Message authentication | |||||||
| Access control | X | ||||||
| Non-repudiation | |||||||
| Anonymity | X | ||||||
| Privacy | X | X | X | ||||
| Usability | X | ||||||
| Availability | X | X | |||||
| Stakeholders | Security and Privacy Threats | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ST1 | ST2 | ST3 | ST4 | ST5 | ST6 | ST7 | ST8 | PT1 | PT2 | PT3 | PT4 | PT5 | PT6 | PT7 | PT8 | |
| PII Controller | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | |||||
| Third Party | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ||||||
| PII Processor | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | |||||||
| No. | Threats | L | I | N | D | D | U | N |
|---|---|---|---|---|---|---|---|---|
| ST1 | Compromised data confidentiality | ○ | ||||||
| ST2 | Compromised data integrity | ○ | ||||||
| ST3 | Compromised data availability | ○ | ||||||
| ST4 | Data recovery due to insufficient data deletion | ○ | ||||||
| ST5 | Degradation in data quality when processing | ○ | ○ | |||||
| ST6 | Malicious actions by internal attackers | ○ | ○ | ○ | ||||
| ST7 | Risk of using unsecure tunneling protocol | ○ | ||||||
| ST8 | Lost/stolen terminal | ○ | ||||||
| PT1 | Data use for purposes other than infectious-disease responses | ○ | ||||||
| PT2 | Data transfer to unauthorized third party | ○ | ||||||
| PT3 | Insufficient legal basis for PII collection | ○ | ||||||
| PT4 | Excessive data collection and use beyond purpose | ○ | ○ | |||||
| PT5 | Data collection without consent of PII principal | ○ | ○ | ○ | ||||
| PT6 | Risk of re-identification due to data combination | ○ | ○ | |||||
| PT7 | Threats to know a specific subject of information using publicly announced information | ○ | ○ | |||||
| PT8 | Leakage of PII on the handwritten list | ○ | ○ | ○ |
| No. | Threats | S | T | R | I | D | E |
|---|---|---|---|---|---|---|---|
| ST1 | Compromised data confidentiality | ○ | |||||
| ST2 | Compromised data integrity | ○ | ○ | ||||
| ST3 | Compromised data availability | ○ | |||||
| ST4 | Data recovery due to insufficient data deletion | ○ | |||||
| ST5 | Degradation in data quality when processing | ○ | |||||
| ST6 | Malicious actions by internal attackers | ○ | |||||
| ST7 | Risk of using unsecured tunneling protocol | ○ | ○ | ||||
| ST8 | Lost/stolen terminal | ○ | ○ | ○ |
| Security and Privacy Threats | Security Requirements | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| SR1 | SR2 | SR3 | SR4 | SR5 | SR6 | SR7 | SR8 | SR9 | SR10 | SR11 | SR12 | SR13 | SR14 | |
| ST1 | ○ | ○ | ||||||||||||
| ST2 | ○ | ○ | ||||||||||||
| ST3 | ○ | ○ | ||||||||||||
| ST4 | ○ | |||||||||||||
| ST5 | ○ | |||||||||||||
| ST6 | ○ | |||||||||||||
| ST7 | ○ | |||||||||||||
| ST8 | ○ | |||||||||||||
| PT1 | ○ | |||||||||||||
| PT2 | ○ | |||||||||||||
| PT3 | ○ | ○ | ||||||||||||
| PT4 | ○ | ○ | ○ | |||||||||||
| PT5 | ○ | ○ | ||||||||||||
| PT6 | ○ | |||||||||||||
| PT7 | ○ | |||||||||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, S.; Youm, H.-Y. Security and Privacy Threats and Requirements for the Centralized Contact Tracing System in Korea. Big Data Cogn. Comput. 2022, 6, 143. https://doi.org/10.3390/bdcc6040143
Park S, Youm H-Y. Security and Privacy Threats and Requirements for the Centralized Contact Tracing System in Korea. Big Data and Cognitive Computing. 2022; 6(4):143. https://doi.org/10.3390/bdcc6040143
Chicago/Turabian StylePark, Sungchae, and Heung-Youl Youm. 2022. "Security and Privacy Threats and Requirements for the Centralized Contact Tracing System in Korea" Big Data and Cognitive Computing 6, no. 4: 143. https://doi.org/10.3390/bdcc6040143
APA StylePark, S., & Youm, H.-Y. (2022). Security and Privacy Threats and Requirements for the Centralized Contact Tracing System in Korea. Big Data and Cognitive Computing, 6(4), 143. https://doi.org/10.3390/bdcc6040143






